Announcing Hunt 2.5 Powerful Pivots for Better Threat Hunting
Announcing Hunt 2.5 Powerful Pivots for Better Threat Hunting
Published on
Aug 21, 2025



We're excited to roll out Hunt 2.5, a release shaped around one idea: making pivots the natural way to investigate. From IP records to HuntSQL™ queries to file hashes in AttackCapture™, this update turns scattered data into a connected threat context you can move through without friction.
Here's a quick snapshot of what's new:
| Feature | What's New? |
|---|---|
| Data Improvements | Updated IP database with continuous updates |
| HuntSQL™ | Added the Pivots table for related artifacts, more than 50+ certificate fields, and an “Add to Query” button for faster query expansion |
| Phishing | New phishing feed now available as a download option, and Phishing Kits SHA256 Pivoting |
| Bug Fixes | URL parsing and clearer HuntSQL memory error handling |
HuntSQL™
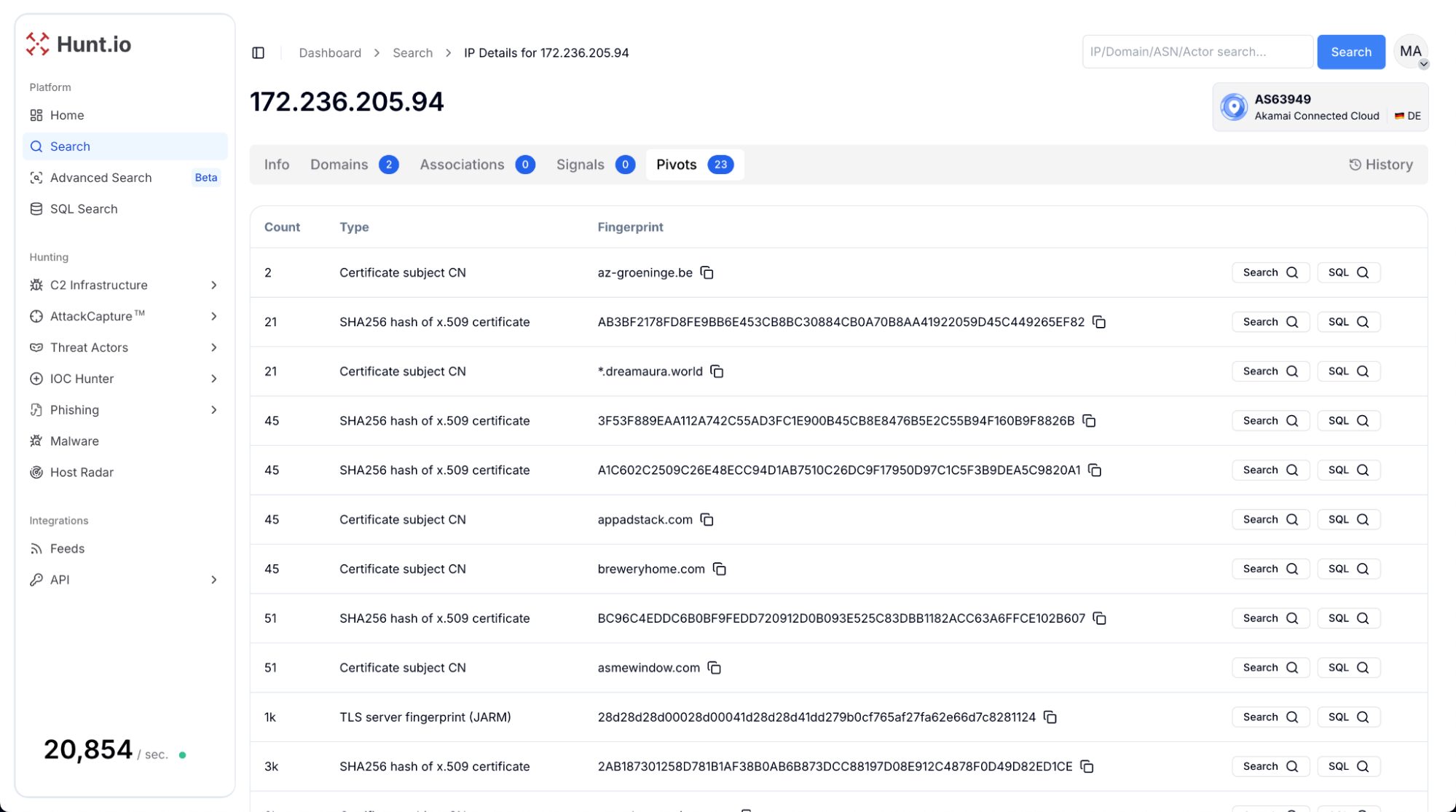
New Pivots table: this new table shows related intelligence artifacts linked to an IP, such as certificate subjects, certificate hashes, and TLS fingerprints. Each entry includes occurrence counts and fingerprint values, with options to pivot directly into Advanced Search or SQL Search.
This allows analysts to quickly expand investigations, uncover related domains or certificates, and move seamlessly between high-level overviews and detailed queries
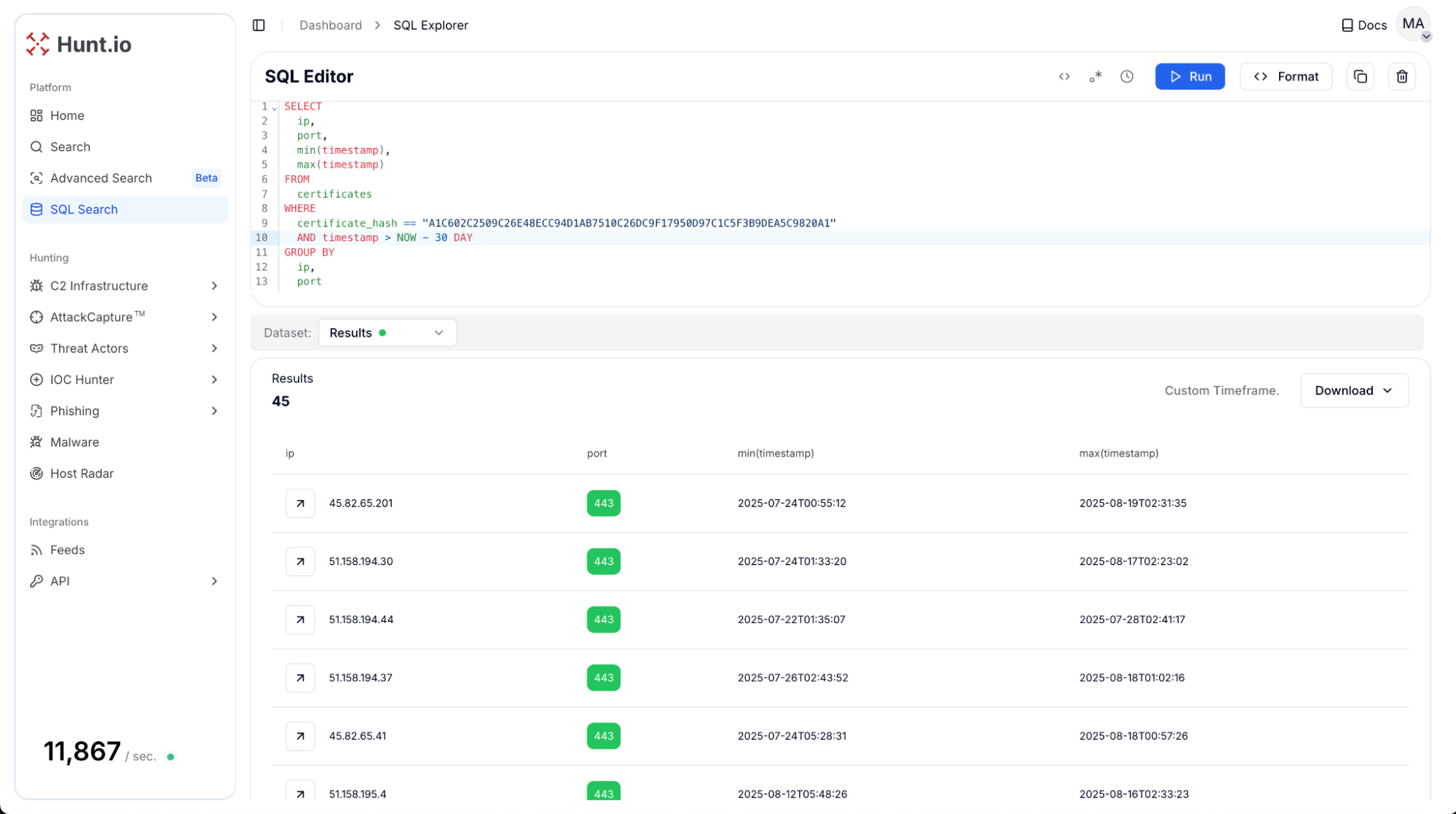
Add to Query button for quick pivots: The SQL search result overlay includes an "Add to Query" button, allowing users to quickly expand their query and apply new conditions based on returned field values. The button appears on hover, making it easy to build more precise queries directly from results.
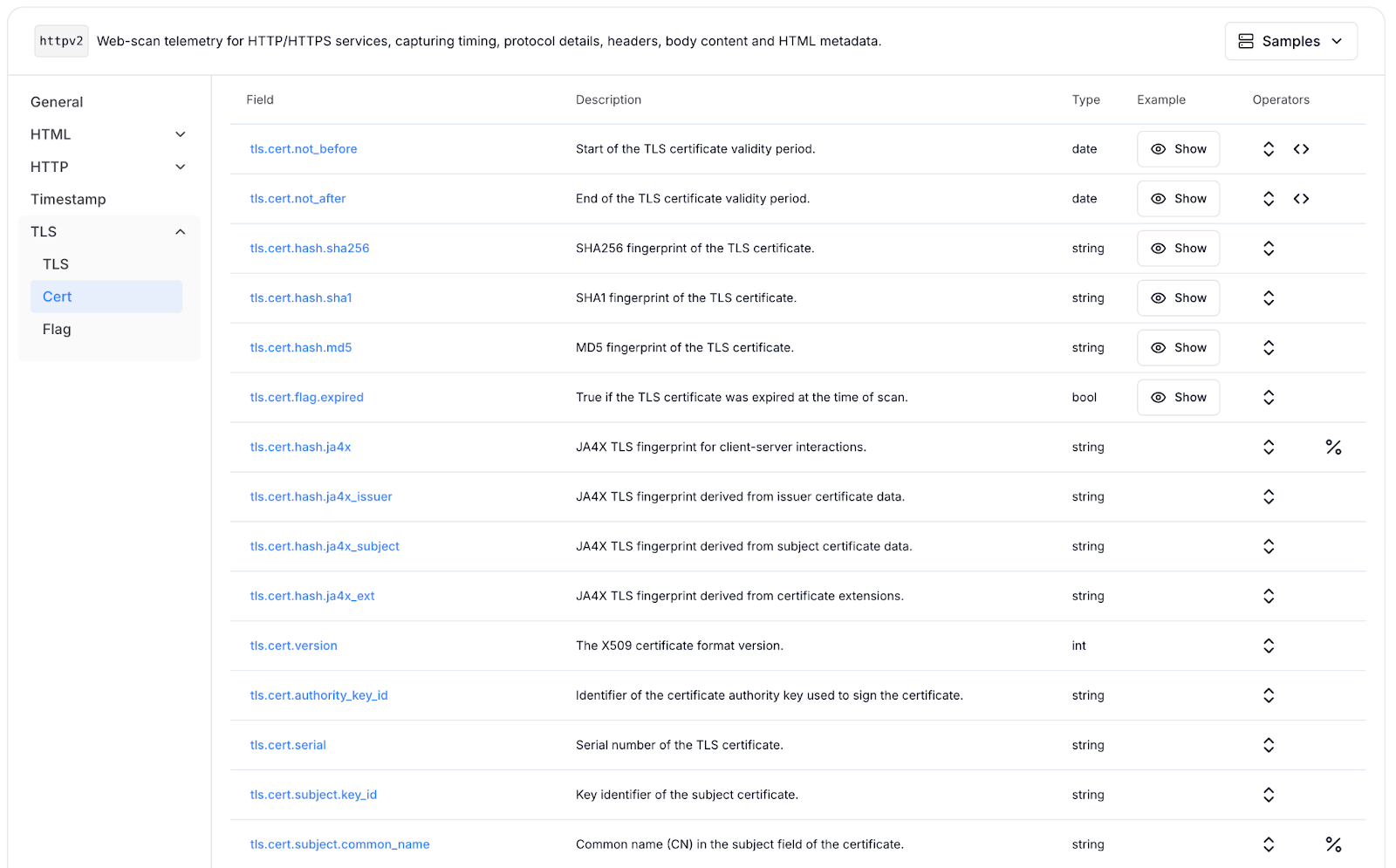
New Certificate Fields: Pivot on all certificate fields alongside HTTP data in one HuntSQL query. httpv2 now includes the full TLS certificate record with 50+ fields, removing a limitation in our earlier versions.
General Updates
Full-screen app: The app now takes advantage of the full viewport for a cleaner, more spacious layout. A subtle border has been added to the navigation bar to separate it from the rest of the page, improving visual structure and usability.
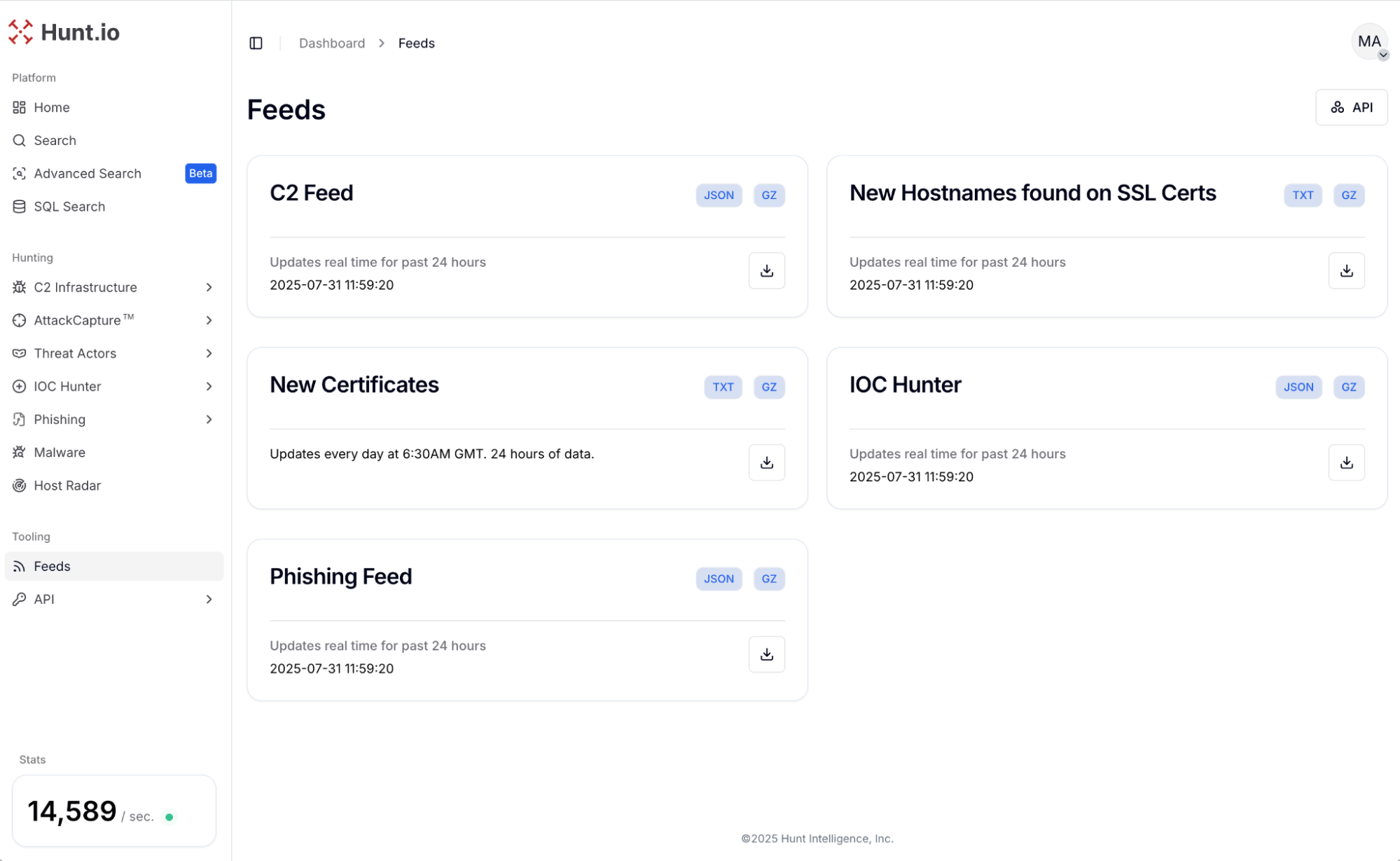
New phishing feed: available for download from our Feeds page. It includes data such as incident ID, status, first seen time, host or IP group, the exact malicious URL, brand tags, phishing kit name and description when present.
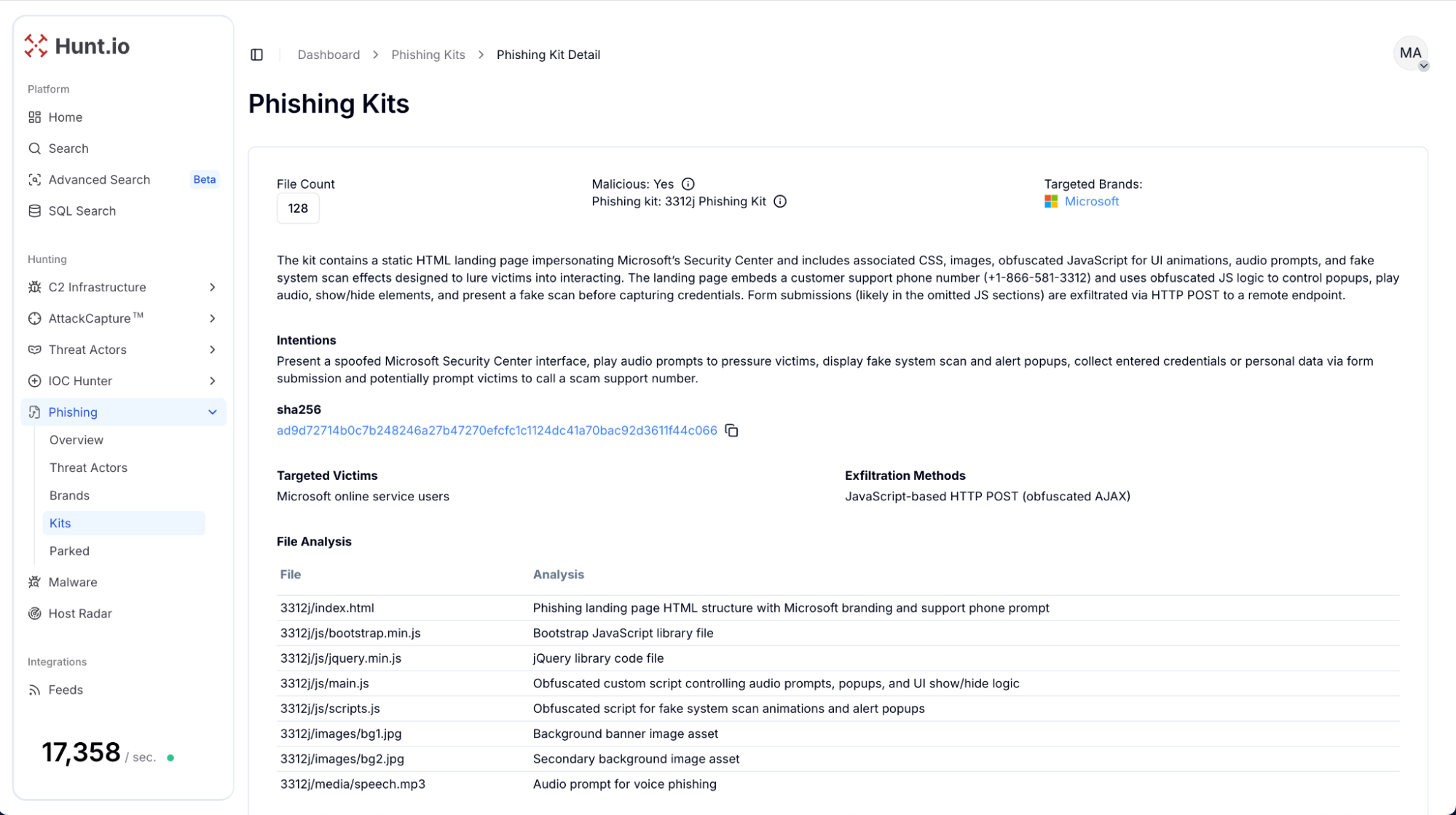
Phishing Kits SHA256 Pivoting: clicking on the SHA256 link redirects to the new Attack Capture Extracted Zip File Manager page, showing related file information to the hash.
Updated IP database: is now fully up to date and will remain up to date thanks to our partnership with IPInfo.
Update SAML integration: to add default user permissions, email verification timestamp, and allow forwarding session cookies across subdomains.
Bug Fixes
Bug fix for incorrectly parsing URL parameter for the phishing brand URLs listing page.
Added handling for database query memory limit exceeded error to return 413 code with query too large message
HuntSQL: Added a proper message for the database query memory limit exceeded error
This release takes Hunt another step forward in making threat investigations fluid and practical. Dive into the new pivots and see how they streamline the way you connect the dots.
We're excited to roll out Hunt 2.5, a release shaped around one idea: making pivots the natural way to investigate. From IP records to HuntSQL™ queries to file hashes in AttackCapture™, this update turns scattered data into a connected threat context you can move through without friction.
Here's a quick snapshot of what's new:
| Feature | What's New? |
|---|---|
| Data Improvements | Updated IP database with continuous updates |
| HuntSQL™ | Added the Pivots table for related artifacts, more than 50+ certificate fields, and an “Add to Query” button for faster query expansion |
| Phishing | New phishing feed now available as a download option, and Phishing Kits SHA256 Pivoting |
| Bug Fixes | URL parsing and clearer HuntSQL memory error handling |
HuntSQL™
New Pivots table: this new table shows related intelligence artifacts linked to an IP, such as certificate subjects, certificate hashes, and TLS fingerprints. Each entry includes occurrence counts and fingerprint values, with options to pivot directly into Advanced Search or SQL Search.
This allows analysts to quickly expand investigations, uncover related domains or certificates, and move seamlessly between high-level overviews and detailed queries

Add to Query button for quick pivots: The SQL search result overlay includes an "Add to Query" button, allowing users to quickly expand their query and apply new conditions based on returned field values. The button appears on hover, making it easy to build more precise queries directly from results.
New Certificate Fields: Pivot on all certificate fields alongside HTTP data in one HuntSQL query. httpv2 now includes the full TLS certificate record with 50+ fields, removing a limitation in our earlier versions.

General Updates
Full-screen app: The app now takes advantage of the full viewport for a cleaner, more spacious layout. A subtle border has been added to the navigation bar to separate it from the rest of the page, improving visual structure and usability.

New phishing feed: available for download from our Feeds page. It includes data such as incident ID, status, first seen time, host or IP group, the exact malicious URL, brand tags, phishing kit name and description when present.

Phishing Kits SHA256 Pivoting: clicking on the SHA256 link redirects to the new Attack Capture Extracted Zip File Manager page, showing related file information to the hash.

Updated IP database: is now fully up to date and will remain up to date thanks to our partnership with IPInfo.
Update SAML integration: to add default user permissions, email verification timestamp, and allow forwarding session cookies across subdomains.
Bug Fixes
Bug fix for incorrectly parsing URL parameter for the phishing brand URLs listing page.
Added handling for database query memory limit exceeded error to return 413 code with query too large message
HuntSQL: Added a proper message for the database query memory limit exceeded error
This release takes Hunt another step forward in making threat investigations fluid and practical. Dive into the new pivots and see how they streamline the way you connect the dots.
Related Post
Product News

Jul 15, 2025
•
4
min read
Hunt 2.4 adds archive-aware search, deeper SQL visibility, and improved phishing intel to make threat hunting faster, clearer, and more powerful.
Read Article
Product News
Product News

Jul 15, 2025
•
4
min read
Hunt 2.4 adds archive-aware search, deeper SQL visibility, and improved phishing intel to make threat hunting faster, clearer, and more powerful.
Read Article
Product News
Product News

Jun 25, 2025
•
5
min read
Hunt 2.3 is here: analyst-driven insights, easier pivots, better phishing workflows, and full SSO support for enterprise teams.
Read Article
Product News
Product News

Jun 25, 2025
•
5
min read
Hunt 2.3 is here: analyst-driven insights, easier pivots, better phishing workflows, and full SSO support for enterprise teams.
Read Article
Product News
Product News

Jun 12, 2025
•
5
min read
Explore Hunt 2.2: Auto-unpack zips in AttackCapture™, smarter SQL with WHOIS and Nmap, and full IP history consolidation, track abused hosting with Host Radar, and more.
Read Article
Product News
Product News

Jun 12, 2025
•
5
min read
Explore Hunt 2.2: Auto-unpack zips in AttackCapture™, smarter SQL with WHOIS and Nmap, and full IP history consolidation, track abused hosting with Host Radar, and more.
Read Article
Product News
Find the threat
before it finds you
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Find the threat
before it finds you
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Find the threat
before it finds you
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Resources
©2025 Hunt Intelligence, Inc.