HTTP
HTTP
Users can query first-party HTTP data to identify threat actors and malicious activity.
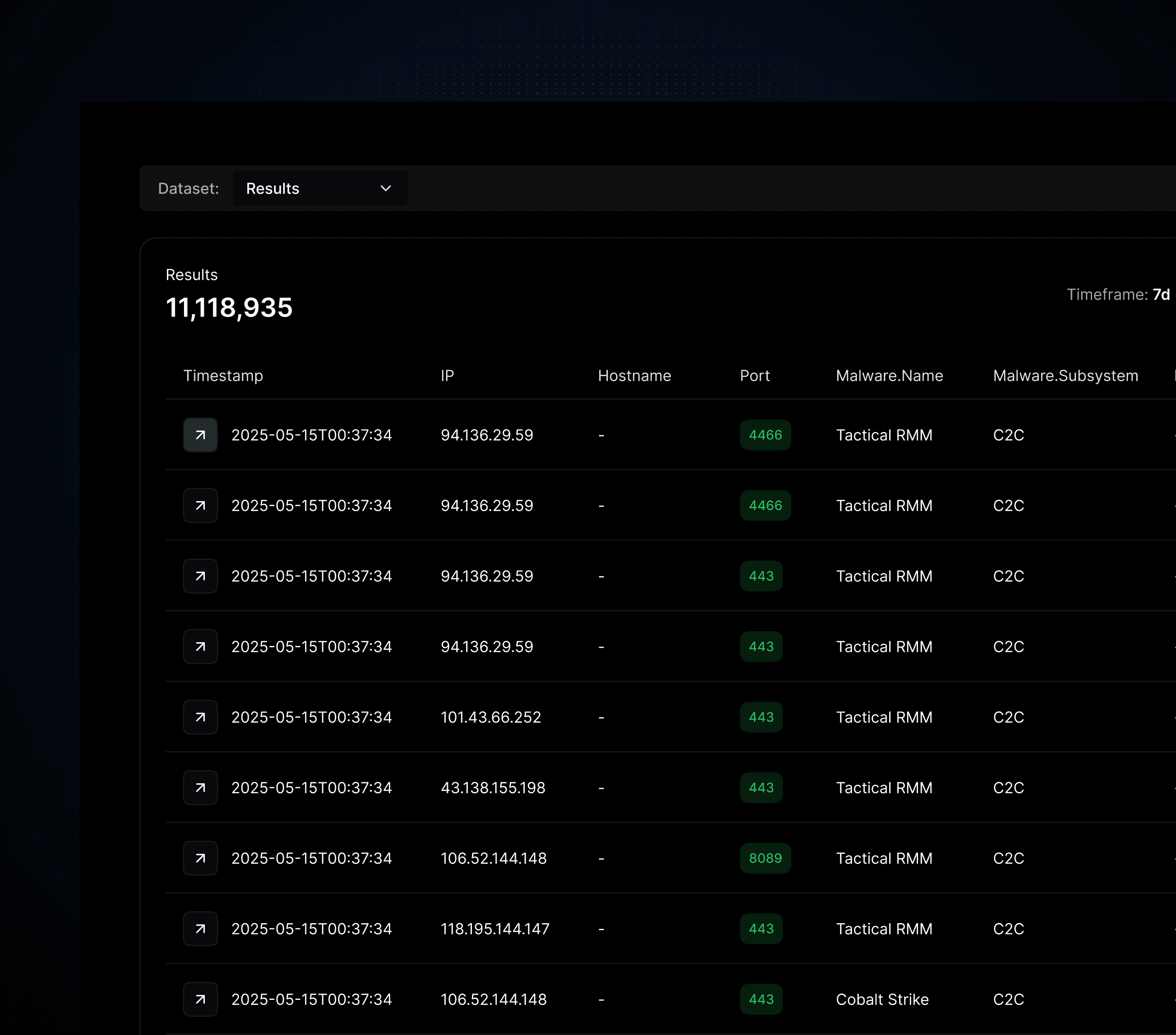
Malware
Users can query the Hunt database of confirmed C2 servers and build detailed statistics on threat actor activity.
Certificates
Users can query first-party certificate data, allowing users to track and identify malicious certificates.
HoneyPot
Users can query honeypot data and obtain detailed stats on internet scanning activity.
Open Directories
Users can query the Hunt database of past and present open directories. This helps discover malware, exploits and attack tooling.
Phishing
Query an extensive list of phishing sites to identify and track phishing kits and threat actor tooling.
The malware database contains 48 searchable fields on confirmed C2 servers discovered by Hunt.
Users can view current C2s and configurations for a specific family, or use the data to build detailed statistics about how and where a malware is being hosted.