



AttackCapture™
AttackCapture™
AttackCapture™
A dedicated investigation layer to uncover attacker tooling and active threats within exposed directories.
A dedicated investigation layer to uncover attacker tooling and active threats within exposed directories.
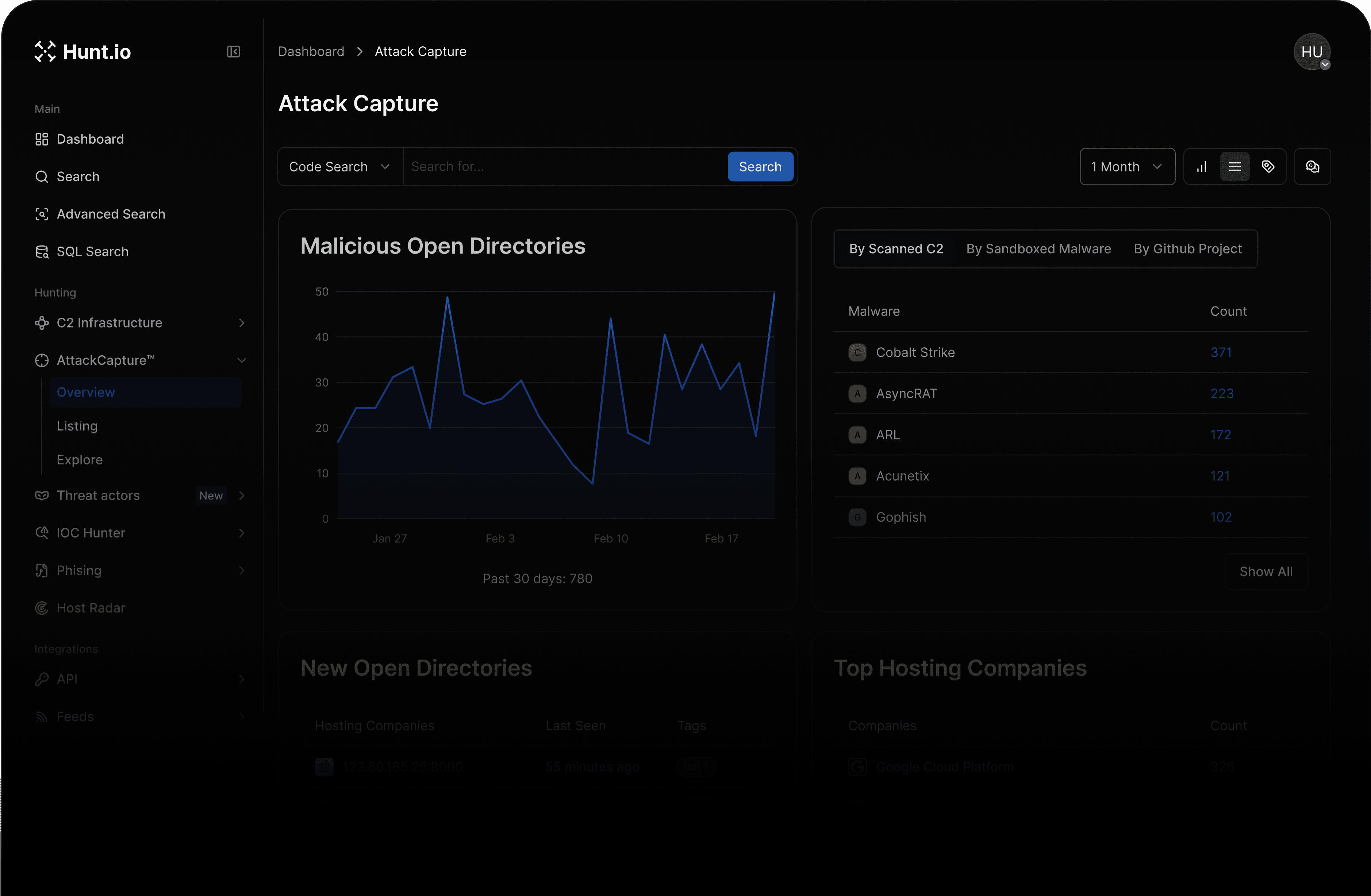



Turn Open Directories
into Actionable Intelligence
Turn Open Directories
into Actionable Intelligence
Turn Open Directories
into Actionable Intelligence

MITRE ATT&CK® Techniques
We now list MITRE ATT&CK® Techniques on each open directory and sandboxed item.
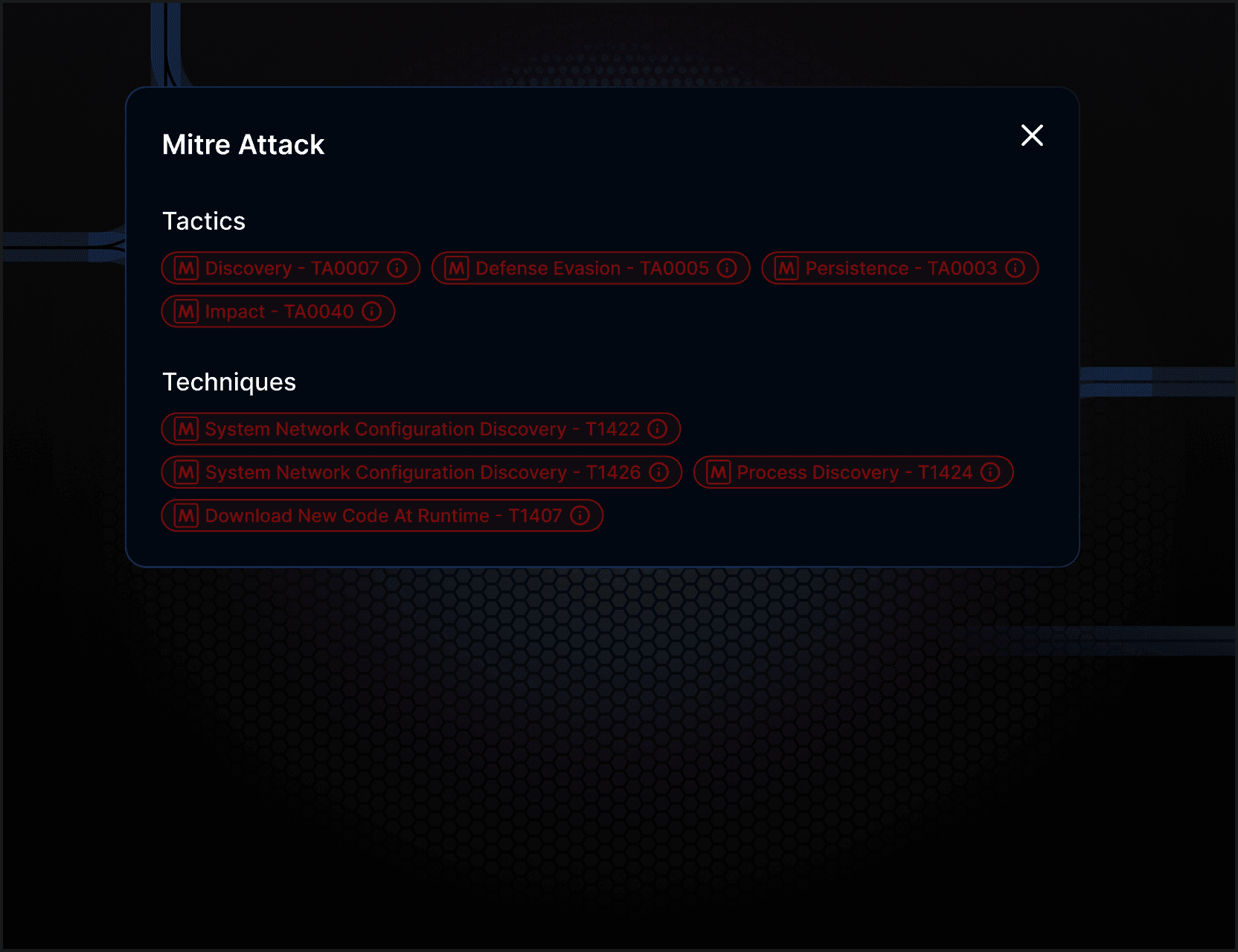

MITRE ATT&CK® Techniques
We now list MITRE ATT&CK® Techniques on each open directory and sandboxed item.


MITRE ATT&CK® Techniques
We now list MITRE ATT&CK® Techniques on each open directory and sandboxed item.


Full Text Code Searching
Search all the code and text files across our entire archive for patterns to find unique exploits, reverse shells and more.
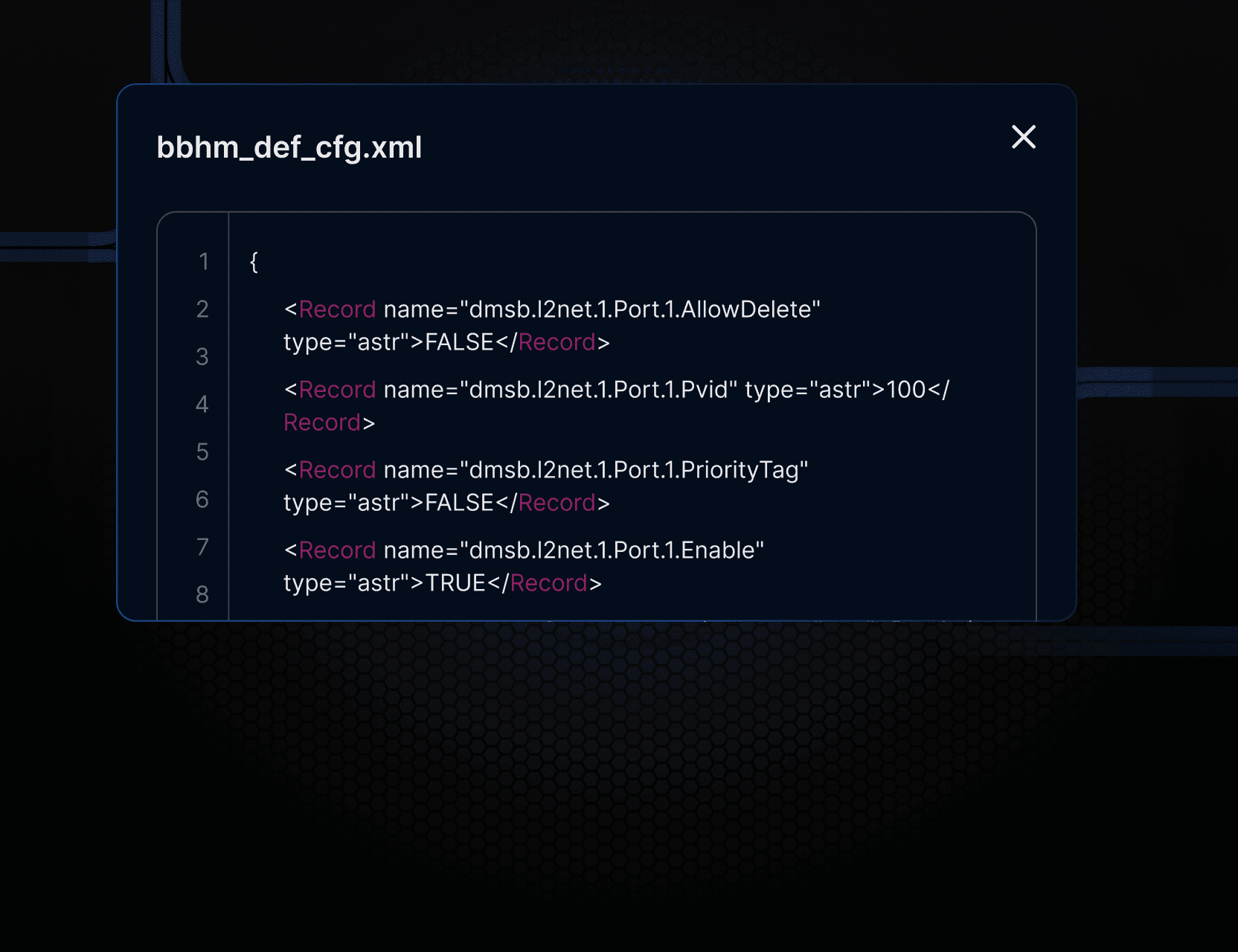

Full Text Code Searching
Search all the code and text files across our entire archive for patterns to find unique exploits, reverse shells and more.


Full Text Code Searching
Search all the code and text files across our entire archive for patterns to find unique exploits, reverse shells and more.


Flagging of Credentials
Credentials are now automatically located inside of attacker content to help you correlate directories and narrow the unique attributes of the attacker.
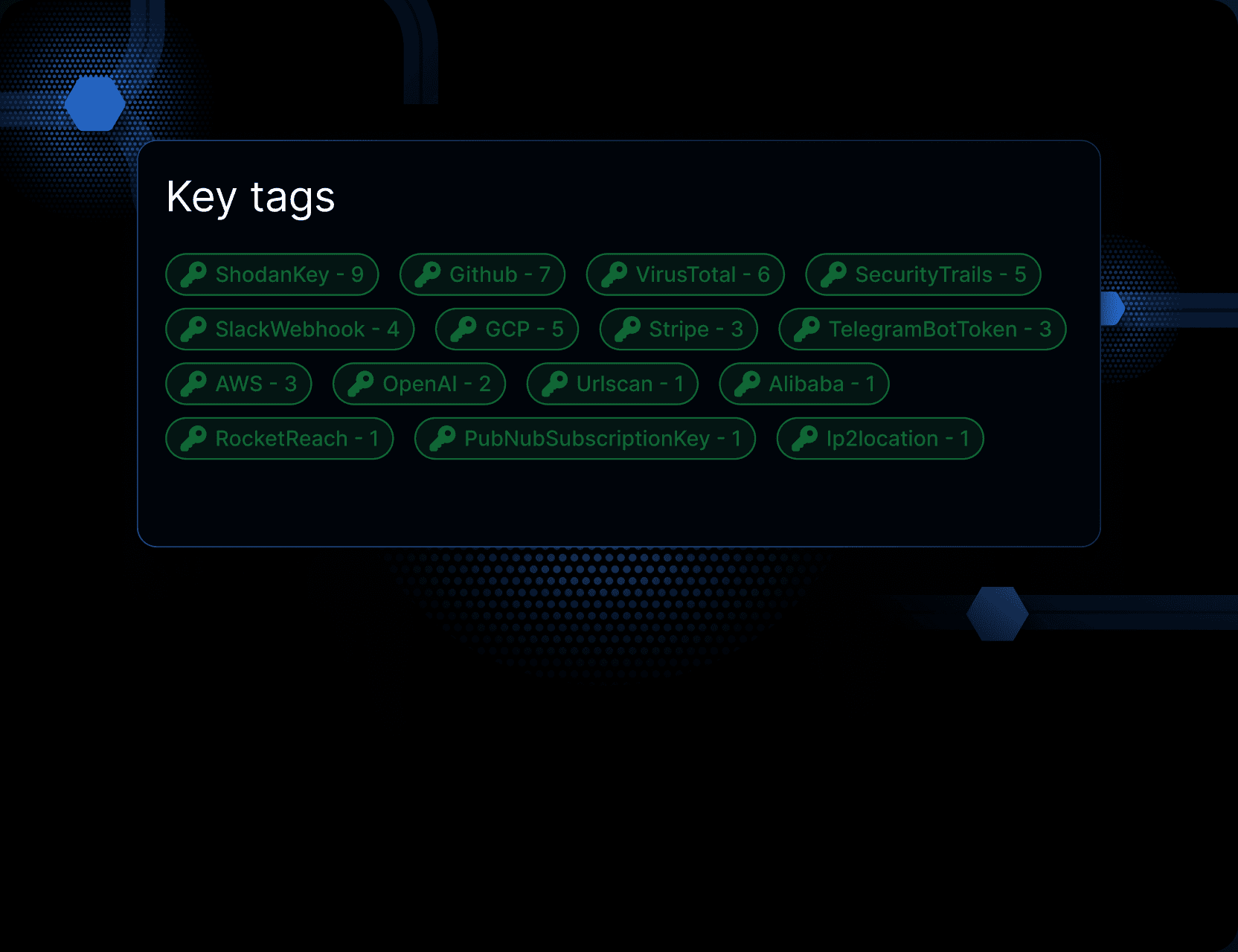

Flagging of Credentials
Credentials are now automatically located inside of attacker content to help you correlate directories and narrow the unique attributes of the attacker.


Flagging of Credentials
Credentials are now automatically located inside of attacker content to help you correlate directories and narrow the unique attributes of the attacker.


More Files Sandboxed
we are now automatically sandboxing many more file types and will continue to add coverage.


More Files Sandboxed
we are now automatically sandboxing many more file types and will continue to add coverage.


More Files Sandboxed
we are now automatically sandboxing many more file types and will continue to add coverage.


Attack files by Scan Signature
These are fully identified servers behaving like C2s to allow you to explore the actual files on the server.
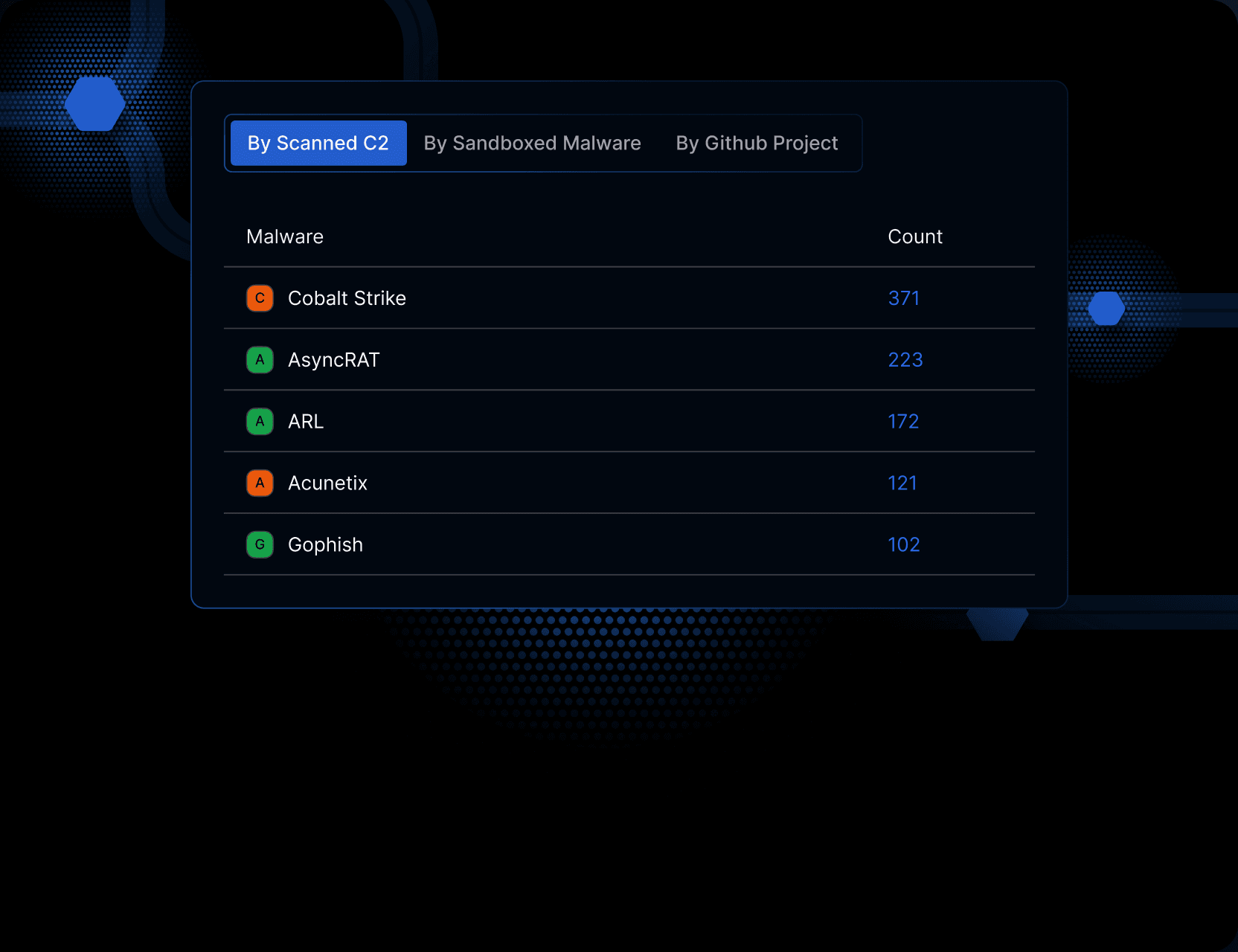

Attack files by Scan Signature
These are fully identified servers behaving like C2s to allow you to explore the actual files on the server.


Attack files by Scan Signature
These are fully identified servers behaving like C2s to allow you to explore the actual files on the server.


Editorial Observations
Our team now puts hand written descriptions analyzing novel and important directories to save you time and narrow down things you're interested in.


Editorial Observations
Our team now puts hand written descriptions analyzing novel and important directories to save you time and narrow down things you're interested in.


Editorial Observations
Our team now puts hand written descriptions analyzing novel and important directories to save you time and narrow down things you're interested in.

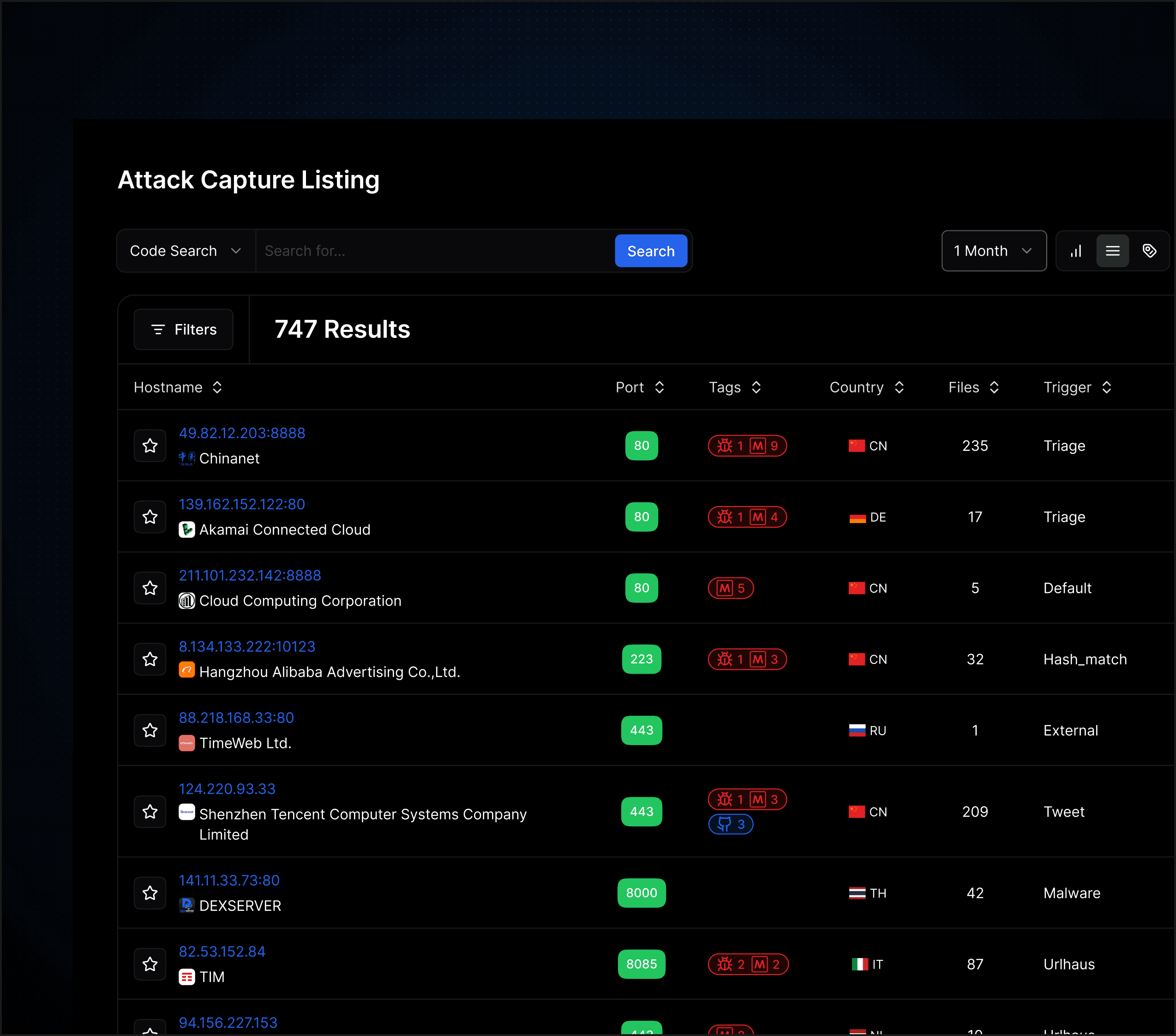


AttackCapture™ Counter Intelligence
AttackCapture™ Counter Intelligence
AttackCapture™ Counter Intelligence
AttackCapture™ enables you to uncover and mitigate potential cyber threats within exposed directories. With this feature, you can detect malicious open directories, secure sandbox malware, download comprehensive file archives, identify exploit kits and reconnaissance tools, discover log files and potential victims, and access downloads of malware and unseen exploits.
faq
faq
faq
Frequently
asked questions
Frequently
asked questions
Frequently
asked questions
What is AttackCapture used for?
AttackCapture is used to investigate exposed attacker directories and analyze the files, tooling, and artifacts left behind on live malicious infrastructure.
What is AttackCapture used for?
AttackCapture is used to investigate exposed attacker directories and analyze the files, tooling, and artifacts left behind on live malicious infrastructure.
What is AttackCapture used for?
AttackCapture is used to investigate exposed attacker directories and analyze the files, tooling, and artifacts left behind on live malicious infrastructure.
What kind of data does AttackCapture analyze?
AttackCapture analyzes files found in exposed directories, including malware, scripts, credentials, logs, exploit tooling, and other attacker-related artifacts.
What kind of data does AttackCapture analyze?
AttackCapture analyzes files found in exposed directories, including malware, scripts, credentials, logs, exploit tooling, and other attacker-related artifacts.
What kind of data does AttackCapture analyze?
AttackCapture analyzes files found in exposed directories, including malware, scripts, credentials, logs, exploit tooling, and other attacker-related artifacts.
How does AttackCapture help threat investigations?
It allows analysts to explore real attacker files, search code and text across archives, correlate credentials, and map activity using MITRE ATT&CK techniques.
How does AttackCapture help threat investigations?
It allows analysts to explore real attacker files, search code and text across archives, correlate credentials, and map activity using MITRE ATT&CK techniques.
How does AttackCapture help threat investigations?
It allows analysts to explore real attacker files, search code and text across archives, correlate credentials, and map activity using MITRE ATT&CK techniques.
What makes AttackCapture different from indicator-based tools?
Instead of focusing only on indicators, AttackCapture provides direct access to attacker-hosted files, enabling deeper investigation into how campaigns actually operate.
What makes AttackCapture different from indicator-based tools?
Instead of focusing only on indicators, AttackCapture provides direct access to attacker-hosted files, enabling deeper investigation into how campaigns actually operate.
What makes AttackCapture different from indicator-based tools?
Instead of focusing only on indicators, AttackCapture provides direct access to attacker-hosted files, enabling deeper investigation into how campaigns actually operate.
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.
