Expose Hidden Threats.
Stop Attacks.
Expose Hidden Threats.
Stop Attacks.
Expose Hidden Threats.
Stop Attacks.
Expose Hidden Threats.
Stop Attacks.
Threat actors hide behind global infrastructure. Hunt.io delivers high-fidelity threat data to link IOCs, trace movements, and reveal what others miss.
Threat actors hide behind global infrastructure. Hunt.io delivers high-fidelity threat data to link IOCs, trace movements, and reveal what others miss.
Threat actors hide behind global infrastructure. Hunt.io delivers high-fidelity threat data to link IOCs, trace movements, and reveal what others miss.
Trusted by Industry Leaders
Trusted by Industry Leaders



Security Teams Struggle With...
Security Teams Struggle With...
Security Teams Struggle With...
We’ve talked to hundreds of SOC teams. These are the problems we keep hearing, and exactly what Hunt.io is built to solve.
We’ve talked to hundreds of SOC teams. These are the problems we keep hearing, and exactly what Hunt.io is built to solve.

See Hunt.io in Action
See Hunt.io in Action
See Hunt.io in Action
Experience how Hunt.io can transform your threat intelligence capabilities with our interactive demo platform.
Experience how Hunt.io can transform your threat intelligence capabilities with our interactive demo platform.
✔
Discover hidden threats in your network
Discover hidden threats in your network
✔
Track adversary infrastructure in real-time
Track adversary infrastructure in real-time
✔
Receive actionable alerts before attacks occur
Receive actionable alerts before attacks occur
✔
Integrate seamlessly with your existing security stack
Integrate seamlessly with your existing security stack



C2 Detection
C2 Detection
C2 Detection
A smarter way to detect, contextualize, and track infrastructure threats at scale. Scanned and validated on a daily basis, with malicious C2s reported in real time, helping you stay ahead of compromised infrastructure.
A smarter way to detect, contextualize, and track infrastructure threats at scale. Scanned and validated on a daily basis, with malicious C2s reported in real time, helping you stay ahead of compromised infrastructure.
✔
High Fidelity Block Grade Intelligence
High Fidelity Block Grade Intelligence
Low false positive rates provides you the confidence to block malicious infrastructure before it is weaponized.
Low false positive rates provides you the confidence to block malicious infrastructure before it is weaponized.
✔
IP Enrichment
IP Enrichment
Investigate suspicious activity quickly with enriched IP information to determine the threat levels.
Investigate suspicious activity quickly with enriched IP information to determine the threat levels.
✔
Proactive Threat Hunting
Proactive Threat Hunting
Leverage unique fingerprints like JA4 to identify additional infrastructure that is being stockpiled for future attacks.
Leverage unique fingerprints like JA4 to identify additional infrastructure that is being stockpiled for future attacks.
AttackCapture™
AttackCapture™
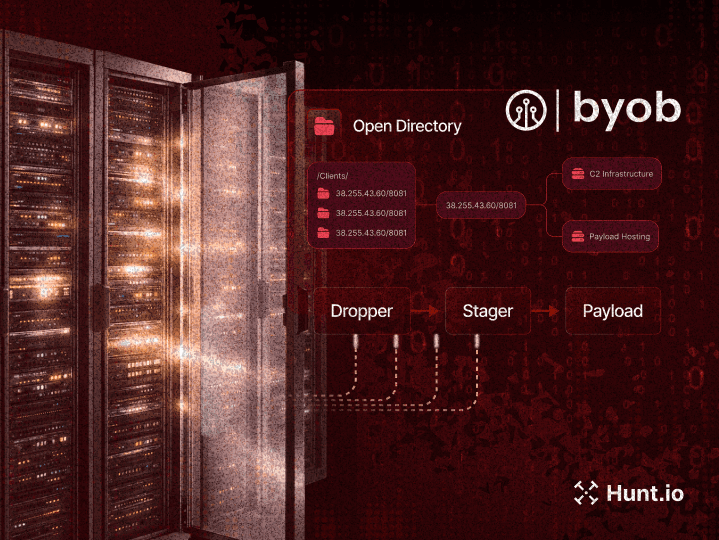
Discover hidden threats in exposed directories. Identify exploits, file paths, attacker tools, and even GitHub references, automatically surfaced so you can focus on what matters most.
Discover hidden threats in exposed directories. Identify exploits, file paths, attacker tools, and even GitHub references, automatically surfaced so you can focus on what matters most.
✔
Proactive Threat Discovery
Proactive Threat Discovery
Quickly identify new attack methods, zero-day exploits, and malicious infrastructure before they're widely documented in traditional threat feeds.
Quickly identify new attack methods, zero-day exploits, and malicious infrastructure before they're widely documented in traditional threat feeds.
✔
Improved Attribution
Improved Attribution
Correlate attacks across multiple open directories using common files, techniques, or credentials to build comprehensive threat actor profiles
Correlate attacks across multiple open directories using common files, techniques, or credentials to build comprehensive threat actor profiles
✔
Reduced Analysis Time
Reduced Analysis Time
Convert exposed directory findings into actionable defense measures by understanding the full scope of attack tools, techniques, and infrastructure.
Convert exposed directory findings into actionable defense measures by understanding the full scope of attack tools, techniques, and infrastructure.
Uncover and Track Adversary Infrastructure Fast
Uncover and Track Adversary Infrastructure Fast
Uncover and Track Adversary Infrastructure Fast
Hunt.io proprietary technologies deliver actionable intelligence with greater speed and accuracy than any other platform.
Hunt.io proprietary technologies deliver actionable intelligence with greater speed and accuracy than any other platform.
IOC Hunter
Extracts and enriches IOCs from trusted research to help you investigate faster, pivot deeper, and block threats with confidence.
Threat Actor Intelligence
Host Radar

IOC Hunter
Extracts and enriches IOCs from trusted research to help you investigate faster, pivot deeper, and block threats with confidence.

Threat Actor Intelligence
Host Radar
IOC Hunter
Extracts and enriches IOCs from trusted research to help you investigate faster, pivot deeper, and block threats with confidence.

Threat Actor Intelligence
Host Radar
IOC Hunter
Extracts and enriches IOCs from trusted research to help you investigate faster, pivot deeper, and block threats with confidence.

Threat Actor Intelligence
Host Radar
IOC Hunter
Extracts and enriches IOCs from trusted research to help you investigate faster, pivot deeper, and block threats with confidence.
Threat Actor Intelligence
Host Radar

What Industry Leaders Are Saying About Hunt.io
What Industry Leaders Are Saying About Hunt.io
What Industry Leaders Are Saying About Hunt.io
See how Hunt.io helps leading researchers detect malicious infrastructure and track threat actor activity in real time.
See how Hunt.io helps leading researchers detect malicious infrastructure and track threat actor activity in real time.
"I've spent a lot of time this year hunting open directories with @Huntio. On four occasions, I had to contact pentesters to take down exposed folders."

Justin Elze
CTO @ TrustedSec
"Using @Huntio to hunt for Lazarus/APT38 clusters is an effective way to understand which crypto-related companies are targeted by this threat actor."

Michael Koczwara
Founder @ IntelOps
"Hunt.io cuts through the noise and shows security teams what matters. Real infrastructure, real threats, real time, with the context they need to respond quickly."

Grant Whiting
Partner @ IQT
"Using @Huntio, our team uncovered malicious - and often covert - infrastructure leveraged by threat actors to disguise their operations within normal communication channels. We can identify, investigate, and pivot across live adversary infrastructure, revealing previously unknown IOCs."

Michael Rossi
Sr. Threat Researcher
"Using findings from Hunt.io's open directories intelligence I was able to identify, investigate, and respond to new malware threats faster than ever. Their platform is amazing!"

Joseph Harrison
Threat Operations Lead @ EY
"I've spent a lot of time this year hunting open directories with @Huntio. On four occasions, I had to contact pentesters to take down exposed folders."

Justin Elze
CTO @ TrustedSec
"Using @Huntio to hunt for Lazarus/APT38 clusters is an effective way to understand which crypto-related companies are targeted by this threat actor."

Michael Koczwara
Founder @ IntelOps
"Hunt.io cuts through the noise and shows security teams what matters. Real infrastructure, real threats, real time, with the context they need to respond quickly."

Grant Whiting
Partner @ IQT
"Using @Huntio, our team uncovered malicious - and often covert - infrastructure leveraged by threat actors to disguise their operations within normal communication channels. We can identify, investigate, and pivot across live adversary infrastructure, revealing previously unknown IOCs."

Michael Rossi
Sr. Threat Researcher
"Using findings from Hunt.io's open directories intelligence I was able to identify, investigate, and respond to new malware threats faster than ever. Their platform is amazing!"

Joseph Harrison
Threat Operations Lead @ EY
"Using @Huntio to hunt for Lazarus/APT38 clusters is an effective way to understand which crypto-related companies are targeted by this threat actor."

Michael Koczwara
Founder @ IntelOps
"Hunt.io cuts through the noise and shows security teams what matters. Real infrastructure, real threats, real time, with the context they need to respond quickly."

Grant Whiting
Partner @ IQT
"I've spent a lot of time this year hunting open directories with @Huntio. On four occasions, I had to contact pentesters to take down exposed folders."

Justin Elze
CTO @ TrustedSec
"Using @Huntio, our team uncovered malicious - and often covert - infrastructure leveraged by threat actors to disguise their operations within normal communication channels. We can identify, investigate, and pivot across live adversary infrastructure, revealing previously unknown IOCs."

Michael Rossi
Sr. Threat Researcher
"Using findings from Hunt.io's open directories intelligence I was able to identify, investigate, and respond to new malware threats faster than ever. Their platform is amazing!"

Joseph Harrison
Threat Operations Lead @ EY
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.