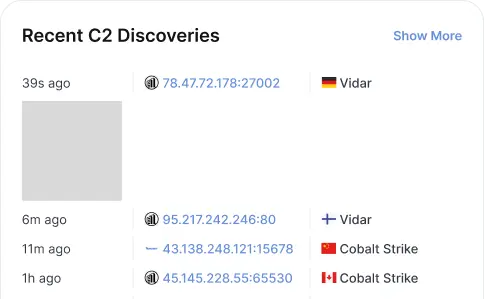
C2 Infrastructure Feed
Our flagship malicious infrastructure feed uses first party validation and our own scanning to hunt, amplify and monitor malicious infrastructure.
Book Your Demo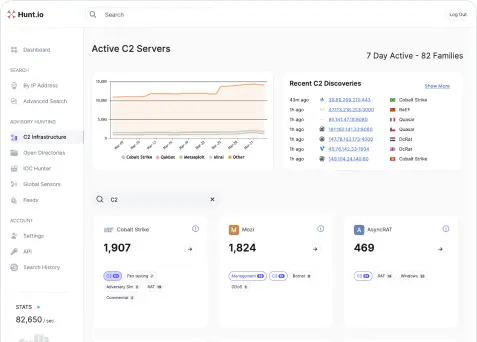
Features


Real-Time
Built from the ground up, no amount of effort is too much to find malicious infrastructure in real-time.


125+ Families
Our in-house research team hand crafts templates and reverses software used by advisories.


Complete & Supported
Hunt can pivot off of these IOCs as a starting point to make sure you never hit a dead end in an investigation.


Blocking + Netflow grade
Categories are included to fit with in any existing pipeline and either block, warn or run victimology through netflow confidently.
Stop Running Your Own C2 Pipelines
Replace your C2 Pipeline Confidently
You can replace or augment your Command and Control detection pipeline using the Hunt C2 Infrastructure Feed. Stop taxing your internal team to just find a subset of C2s using old pipelines and trying to manage quotas with other vendors. Confidently work with Hunt.io today to increase coverage, accuracy and be fully supported.