Our partner plans are designed around predictable pricing, generous usage, and a roadmap shaped around integration, resale, and real-world use, not investor optics.
We beat Censys quotes by 25%+
Show us a 2025 or later threat intelligence Partner quote and we’ll beat it by 25% or more.
You won’t hit your usage ceiling
We guarantee hitting query and API limits isn’t something you’ll need to think about.
Flexible and friendly terms and conditions
Your agreement will include the features, ongoing support, and terms and conditions that make sense for you.
Easy to join (and leave)
We keep renewal terms straightforward and transparent.
A partner-centric product roadmap
Our roadmap is focused on coverage, data quality, and making it easy to integrate, embed, and resell.
We aren’t competing with you
We don’t want your customers or clients. We don’t want to build your product. We don’t want your scoop. We win when you win.
“
Hunt Intelligence reduced validation time by over 95 percent, enabling us to automate investigation workflows and scale detection without building or maintaining our own validation infrastructure.
“
Product Lead, Threat Detection
Threat Intelligence Platform

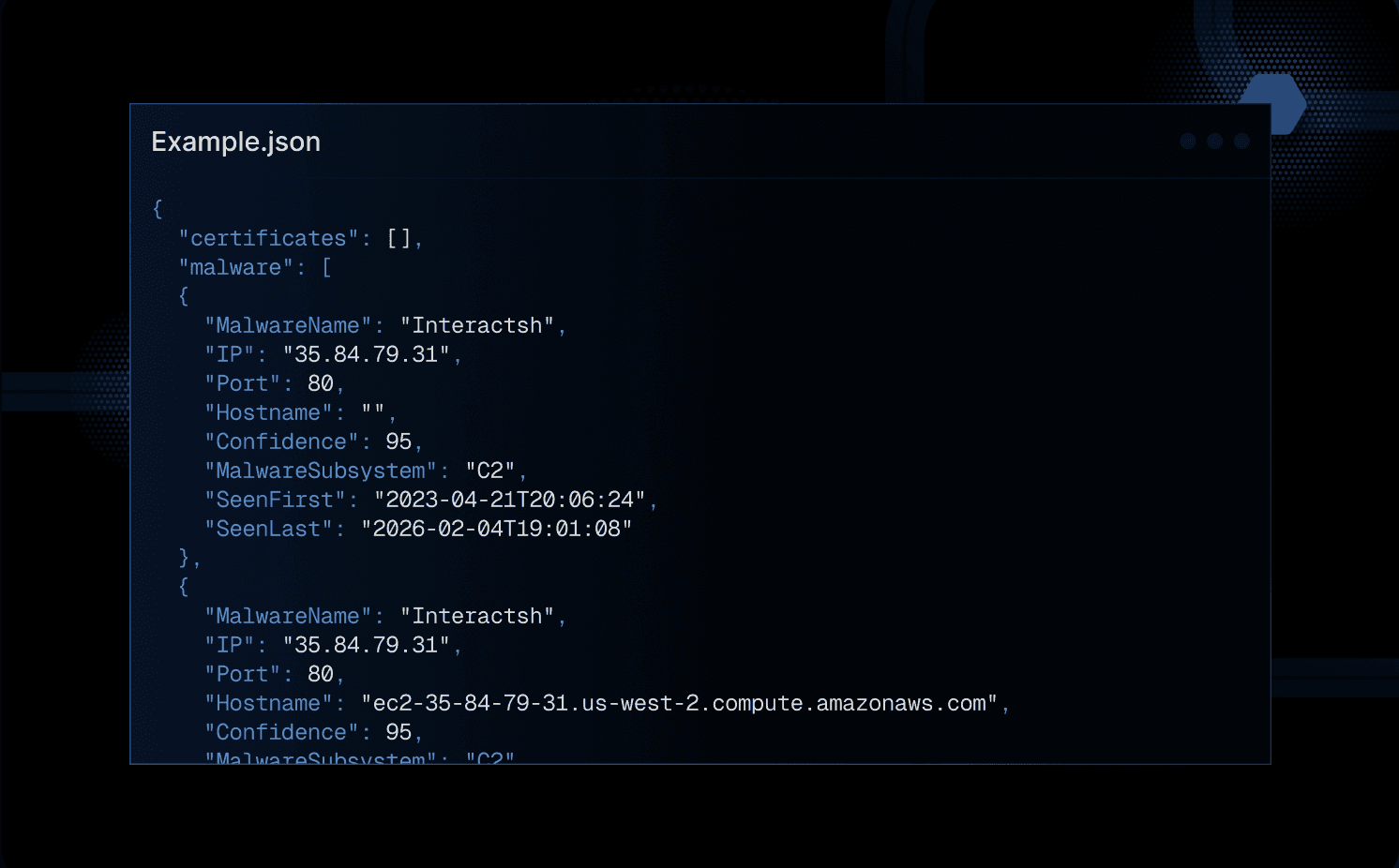
C2 Infrastructure Feed
Replace or augment your C2 detection pipeline with Hunt’s feed using first-party validation and our own scanning to hunt, amplify, and monitor malicious infrastructure
IOC Hunter
Investigate faster, pivot deeper, and block threats with confidence by extracting and enriching IOCs from trusted research.
HuntSQL™
Query Hunt’s database using SQL. Query first-party HTTP data, confirmed C2 servers, first-party certificate data, honeypot data, open directories, and phishing sites.
Phishing Infrastructure
Access an independent collection of heuristic analyses of weaponized, not-yet-weaponized, and benign websites. Pages are measured multiple times to understand an attack’s lifecycle.
AttackCapture ™
Uncover and mitigate potential cyber threats within exposed directories. Identify and automatically surface exploits, file paths, attacker tools, and even GitHub references.
Bulk Enrichment
Extract IPs, domains, and apex domains from any text file in three simple steps. Upload text files, automatically extract IP and domain, get back an enriched CSV
Operational Efficiency
95% less analyst validation for endpoint protection provider
~40% in savings by switching from Censys
70+ workflows automated monthly inside an XDR platform
Detection Coverage
10X increase in threat observables for an MDR provider
29k+ more live IP:Port detections than OSINT feeds
Nearly 3X broader malware family visibility through infrastructure discovery
Proactive Prevention
Targeted APT attack blocked at a global bank
Near real-time block-grade intelligence delivered to customers
Leveraged AttackCapture ™ to identify new threats before it was widely documented in traditional feeds

faq
How does Hunt.io compare to Censys for partners and OEMs?
We’re built as a partner-first alternative to Censys. Instead of optimizing for top-line revenue, we focus on predictable pricing, generous usage, and terms designed for integration, resale, and real-world use. Partners typically see lower costs and fewer usage constraints.
Will you compete with our product or go after our customers?
No. We don’t want your customers, we’re not trying to build your product, and we’re not competing for your deals. We win when your platform gets stronger using our data.
Are usage limits or API ceilings a concern for OEM integrations?
No. Hitting query or API limits isn’t something you should have to think about. Our partner plans are designed around generous usage so your product can scale without friction.
What data and capabilities are included for partners?
Partner plans include C2 Infrastructure Feed, IOC Hunter, HuntSQL, phishing infrastructure intelligence, AttackCapture™, IP enrichment APIs, custom feeds, and bulk enrichment. Everything is API-first and built to be integrated or embedded into your product.
Why shouldn’t we just build this ourselves?
We’re hearing that Censys’ pricing makes this a valid question. Our goal is to provide Hunt.io to partners at a price that makes the headache of building, maintaining, and improving a suite of products and services a non-starter. Schedule a Demo and then decide.