Uncover Malicious Infrastructure
Before Anyone Else
Uncover Malicious Infrastructure
Before Anyone Else
Uncover Malicious Infrastructure
Before Anyone Else
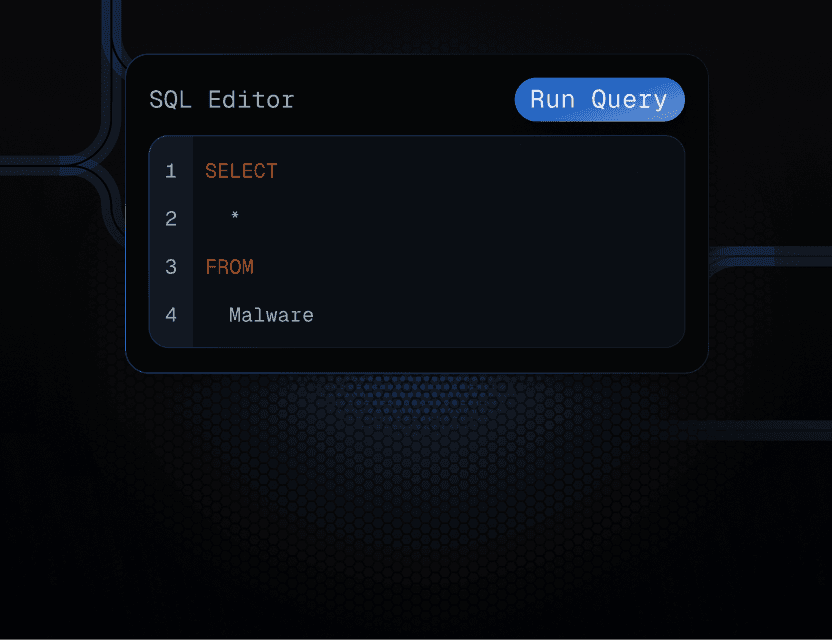
Hunt.io maps active C2 servers, payload hosts, phishing kits and exposed assets using first-party scanning and validation to reveal threats others miss.
Hunt.io maps active C2 servers, payload hosts, phishing kits and exposed assets using first-party scanning and validation to reveal threats others miss.
Trusted By Industry Leaders

Trusted By Industry Leaders

Trusted By Industry Leaders

Trusted By Industry Leaders

Powerful Threat Hunting
Powerful Threat Hunting
Powerful Threat Hunting
Our flagship malicious infrastructure feed uses first party validation and our own scanning to hunt, amplify and monitor malicious infrastructure.
Our flagship malicious infrastructure feed uses first party validation and our own scanning to hunt, amplify and monitor malicious infrastructure.
Our flagship malicious infrastructure feed uses first party validation and our own scanning to hunt, amplify and monitor malicious infrastructure.
solution from us
Uncover and Track
Adversary Infrastructure Fast
Uncover and Track
Adversary Infrastructure Fast
Uncover and Track
Adversary Infrastructure Fast
Hunt.io's proprietary technologies deliver actionable intelligence faster and with greater accuracy than any competitor.
Hunt.io's proprietary technologies deliver actionable intelligence faster and with greater accuracy than any competitor.
Hunt.io's proprietary technologies deliver actionable intelligence faster and with greater accuracy than any competitor.
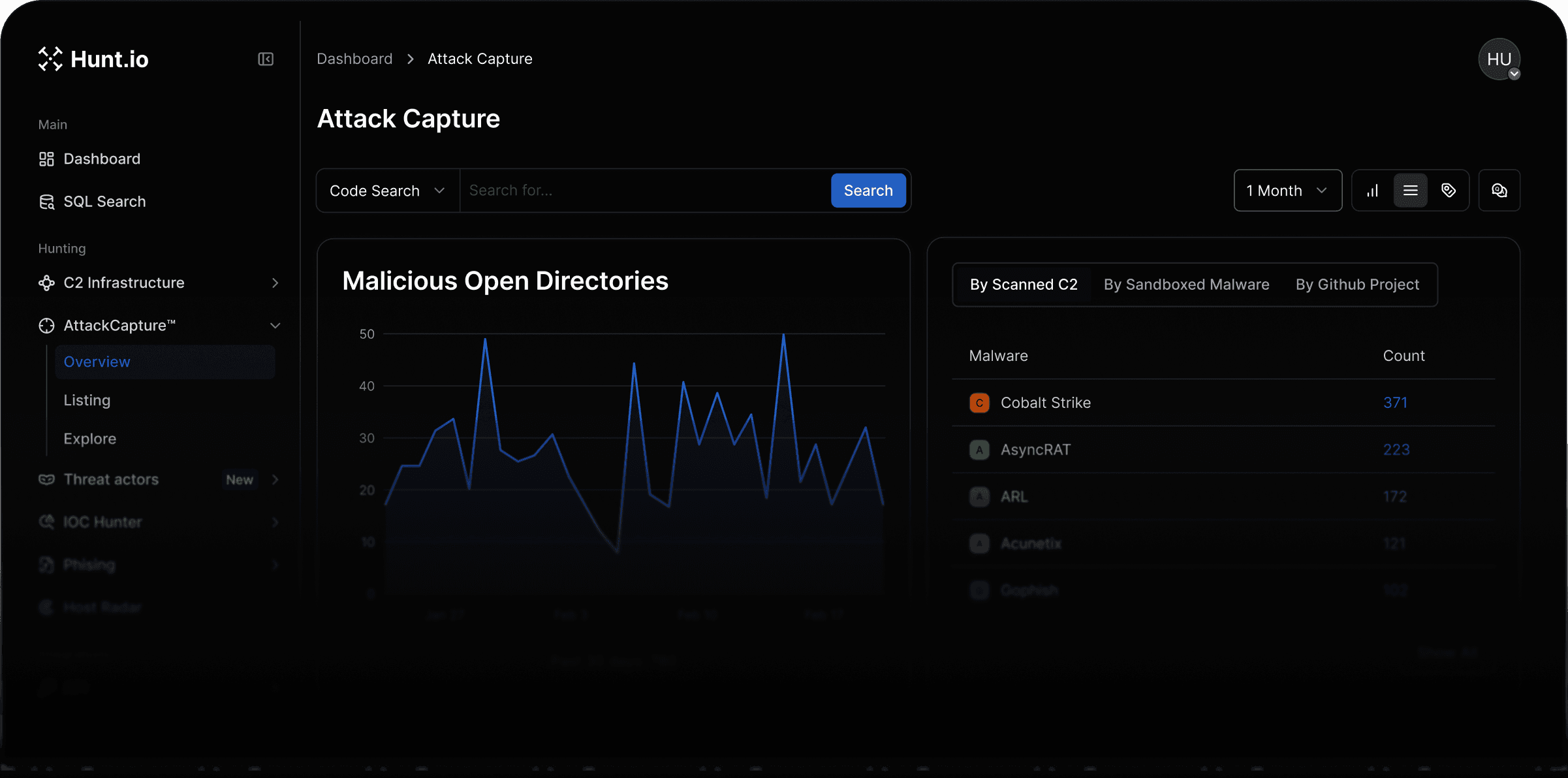
AttackCapture™
C2 Infrastructure
IOC Hunter
Phishing Infrastructure

Open Directory Intelligence
Automatically uncover open directories, payloads, attacker tooling before they're weaponized.
Reduced Analysis Time
Convert exposed directory findings into actionable defense measures by understanding the full scope of attack tools, techniques, and infrastructure.
Proactive Threat Discovery
Quickly identify new attack methods, zero-day exploits, and malicious infrastructure before they're widely documented in traditional threat feeds.
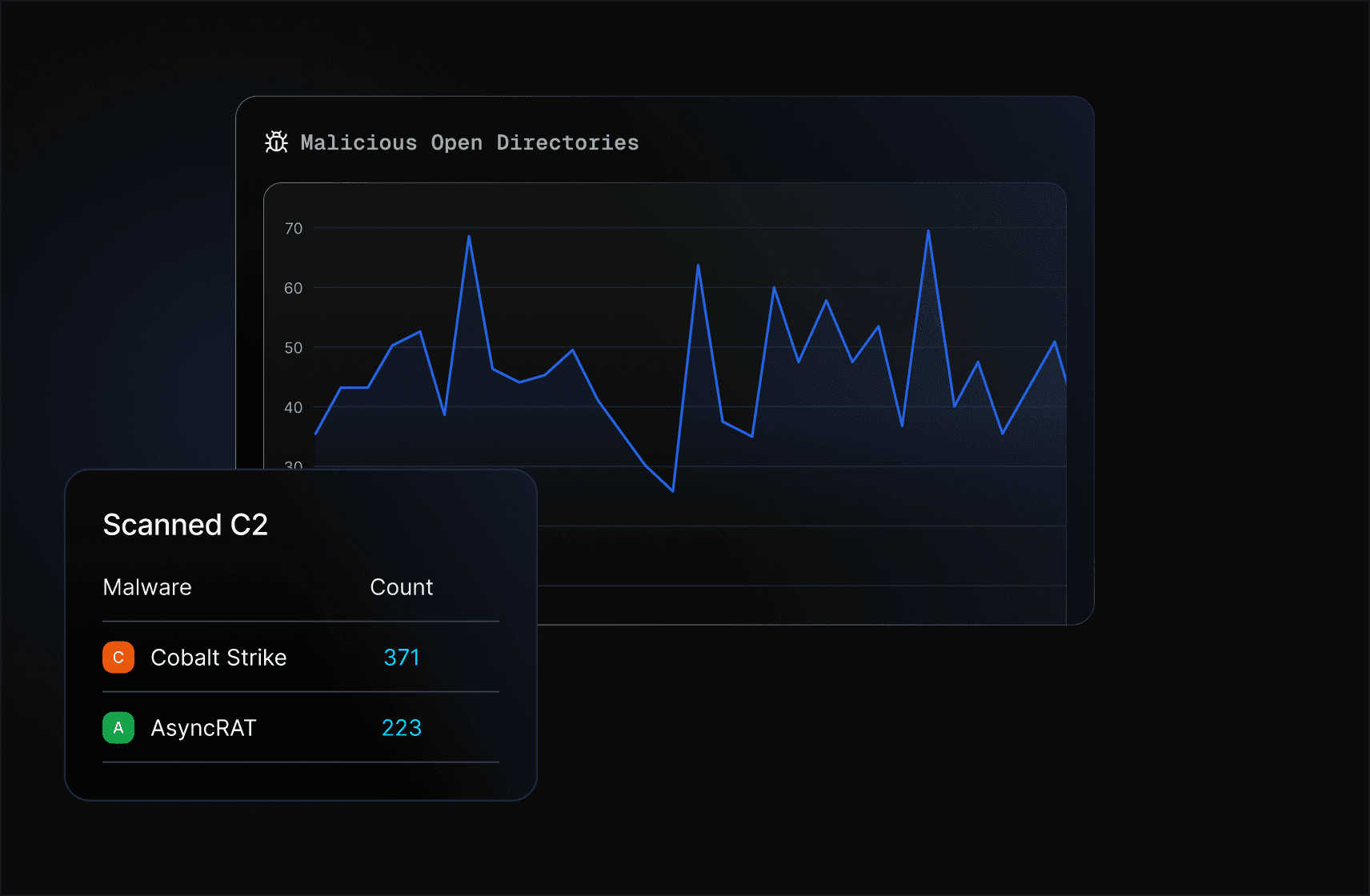
AttackCapture™
C2 Infrastructure
IOC Hunter
Phishing Infrastructure

Exposed directory & attack surface discovery
Automatically uncover open directories, payloads, attacker tooling before they're weaponized.

Reduced Analysis Time
Convert exposed directory findings into actionable defense measures by understanding the full scope of attack tools, techniques, and infrastructure.
Proactive Threat Discovery
Quickly identify new attack methods, zero-day exploits, and malicious infrastructure before they're widely documented in traditional threat feeds.
Track abused hosting providers
and expose adversary infrastructure
Track abused hosting providers
and expose adversary infrastructure
Track abused hosting providers
and expose adversary infrastructure
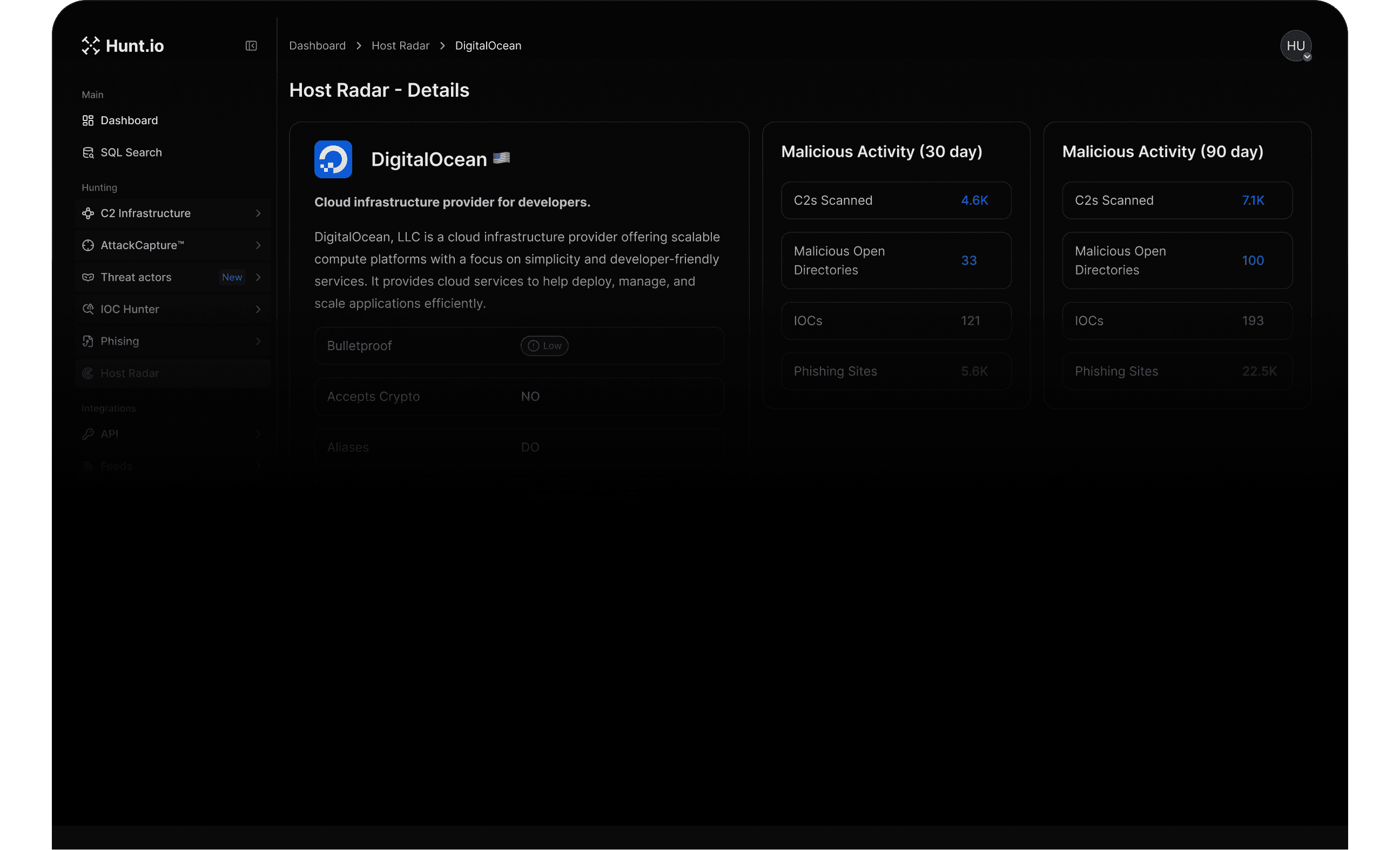
HostRadar scans the internet continuously, ties domains and IPs to hosting providers, and turns every weak point into a pivot for threat hunting at scale.
HostRadar scans the internet continuously, ties domains and IPs to hosting providers, and turns every weak point into a pivot for threat hunting at scale.
HostRadar scans the internet continuously, ties domains and IPs to hosting providers, and turns every weak point into a pivot for threat hunting at scale.
testimonials
Security teams
love our data
Security teams
love our data
Security teams
love our data
Hunt.io proprietary technologies deliver actionable intelligence with greater speed and accuracy than any other platform.
Hunt.io proprietary technologies deliver actionable intelligence with greater speed and accuracy than any other platform.
“
AttackCapture™ tags make it easy to identify very specific things like Cobalt Strike servers or pentest tools when I’m short on time and can’t manually explore open directories.
“

Justin Elze
CTO @TrustedSec
“
AttackCapture™ tags make it easy to identify very specific things like Cobalt Strike servers or pentest tools when I’m short on time and can’t manually explore open directories.
“

Justin Elze
CTO @TrustedSec
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.