The Complete Guide to Hunting Cobalt Strike - Part 3: Automated C2 Infrastructure Discovery
The Complete Guide to Hunting Cobalt Strike - Part 3: Automated C2 Infrastructure Discovery
Published on
Jan 6, 2026



Over the first two parts of this series, we've looked at Cobalt Strike from different angles. Part 1 walked through how exposed open directories can leak tooling, and Part 2 showed how structured HuntSQL queries help map out live C2 activity. With that foundation set, this third part focuses on something most teams want but rarely have time to build themselves: automated Cobalt Strike discovery inside the Hunt.io interface.
Instead of inspecting IPs one by one, our platform gives you a wider lens. The C2 Overview, C2 Listing view, and pivot panels highlight long-running servers, reused certificates, repeated header signatures, and full clusters of related infrastructure with almost no manual work.
This gives you a real-time look at how Cobalt Strike behaves at scale and how quickly a single detection can grow into a full map of coordinated C2 assets. Let's get into it.
Automated Detection in the C2 Dashboard
The best way to kick things off is with the C2 Overview dashboard. It gives us a clear, high-level read on malware families (including Cobalt Strike) activities without getting bogged down in individual IPs.
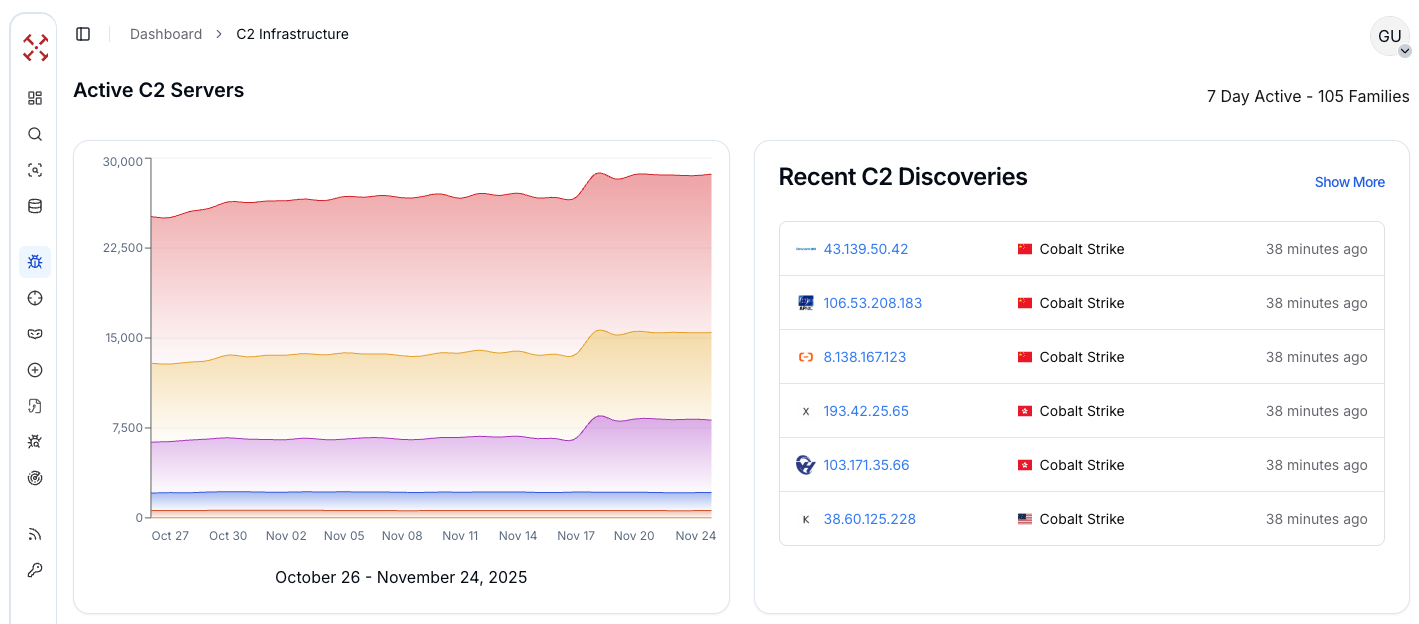 Figure 1: C2 Overview Dashboard with real-time live C2 detections
Figure 1: C2 Overview Dashboard with real-time live C2 detectionsOn the right side, we can quickly spot recently detected Cobalt Strike servers. Clicking any of them opens the active Cobalt Strike instances page, where we can follow C2 activity over time. Between 800 and 1,000 IPs are actively running Cobalt Strike infrastructure, and what really stands out is how steady this activity stays throughout the month.
There is no major spike or dramatic drop-off. Activity continues at a steady baseline, which indicates something important: this threat is sustained and persistent.
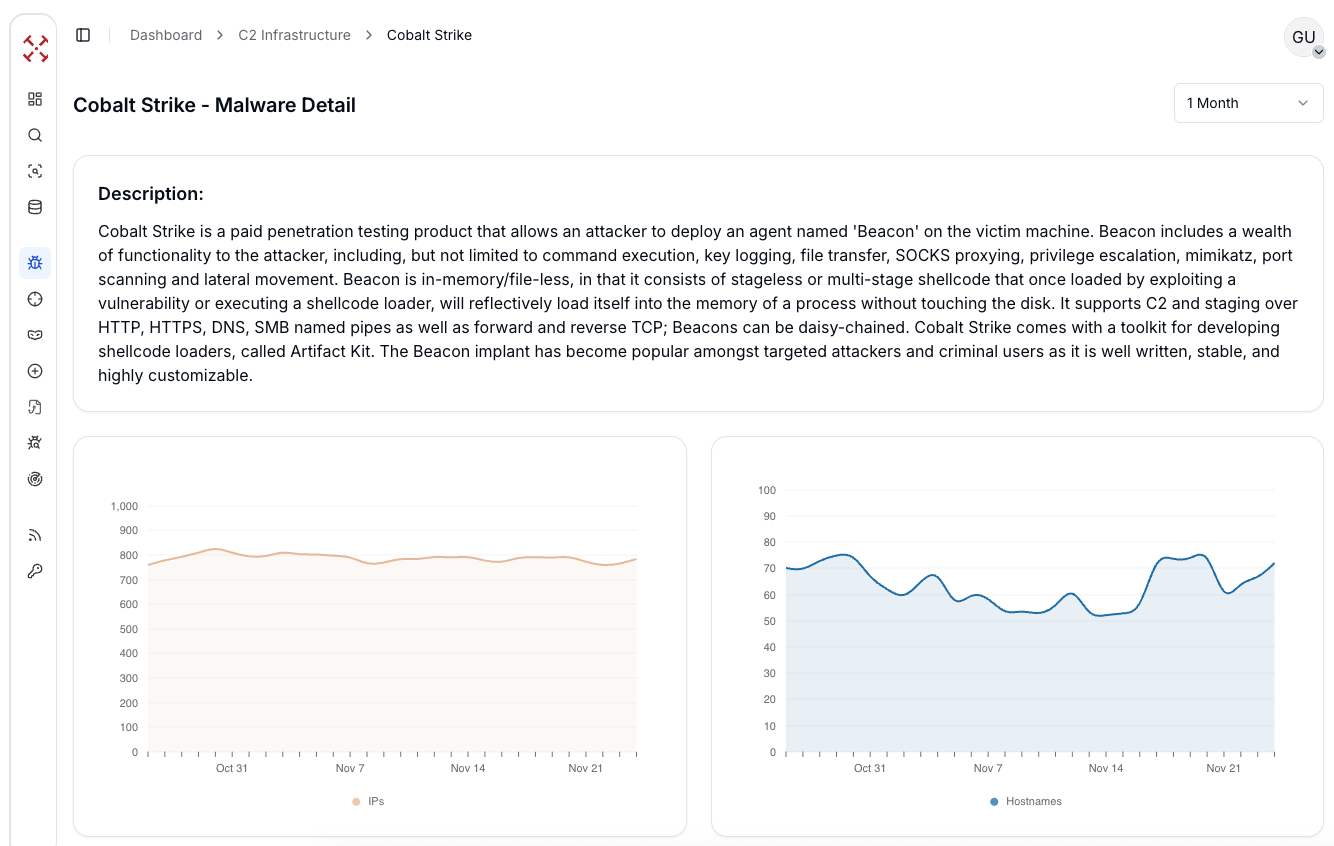 Figure 2: Global Cobalt Strike activity
Figure 2: Global Cobalt Strike activityNext to that is the hostname trend, hovering around 60 to 90 active hostnames tied to these Cobalt Strike servers. There's some fluctuation, but nothing out of the ordinary. This shows that threat actors are rotating their infrastructure slightly, without significant disruption.
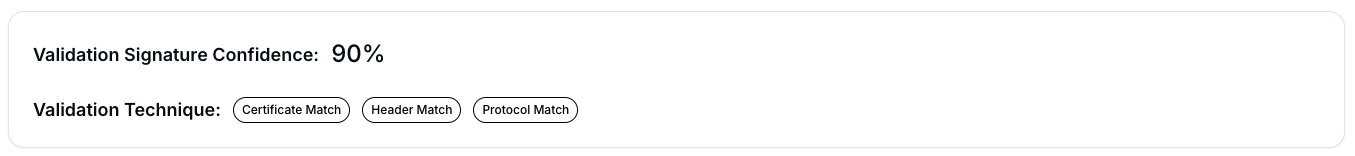
The real game changer is the 90% validation confidence score. Hunt.io does not take guesses; certificate matching, header analysis, and protocol inspection are applied to every detection. This ensures that flagged activity is legitimate, with no false positives cluttering the alert queue.
Cobalt Strike Listing View
The C2 Listing view gives us a comprehensive picture of Cobalt Strike activity. The dashboard displays 2,400 confirmed detections, consolidated in a single view. It pulls together IP addresses, ports, countries of operation, and hosting companies in one place.
What makes this view particularly useful are the filtering options. Detections can be narrowed down by malware family, ASN, port number, or TLD, allowing patterns to emerge. Analysis reveals that certain hosting providers appear repeatedly, while specific ports such as 8443 and 8444 experience constant activity from active beacons. These patterns indicate how threat actors operate and where infrastructure is being deployed.
The breakdown of Cobalt Strike detections shows 1,467 confirmed instances across multiple categories: 57 tagged as C2 infrastructure, 6 marked as Penetration Testing Tools, 9 flagged for Command and Control operations, and 12 identified as cross-platform capable.
There's also 1 classified specifically as a Team Server, which is the command center where operators control everything. Then on the unverified side, there are another 801 Cobalt Strike detections that haven't been fully confirmed yet, but are showing all the same patterns. These unverified ones have 57 C2 instances, 6 Penetration Testing Tools, 9 Command and Control tagged, and 20 cross-platform variants.
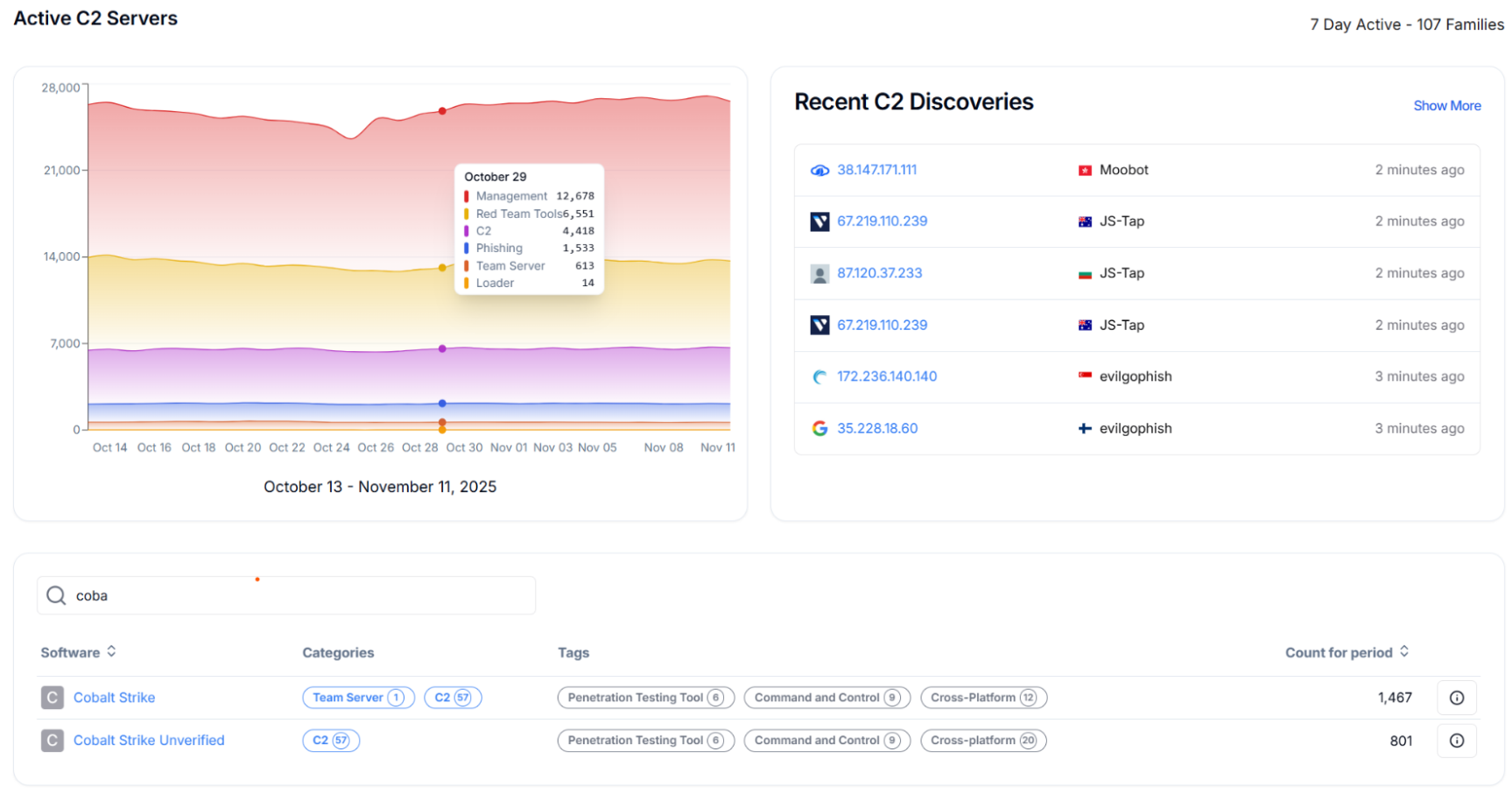 Figure 3: C2 Listing view showing confirmed detections with IPs, ports, and hosting providers.
Figure 3: C2 Listing view showing confirmed detections with IPs, ports, and hosting providers.The presence of a high number of cross-platform instances in the unverified category, 20 compared to 12 in the confirmed set, suggests that threat actors are actively working to expand their infrastructure across different operating systems.
Combined, that's over 2,200 Cobalt Strike-related detections. Some are locked in as confirmed threats, others are still being assessed, but they're all following the same playbook. They're all abusing legitimate security tools for malicious purposes, and they're all spreading across Windows, Linux, and Mac environments to cast as wide a net as possible.
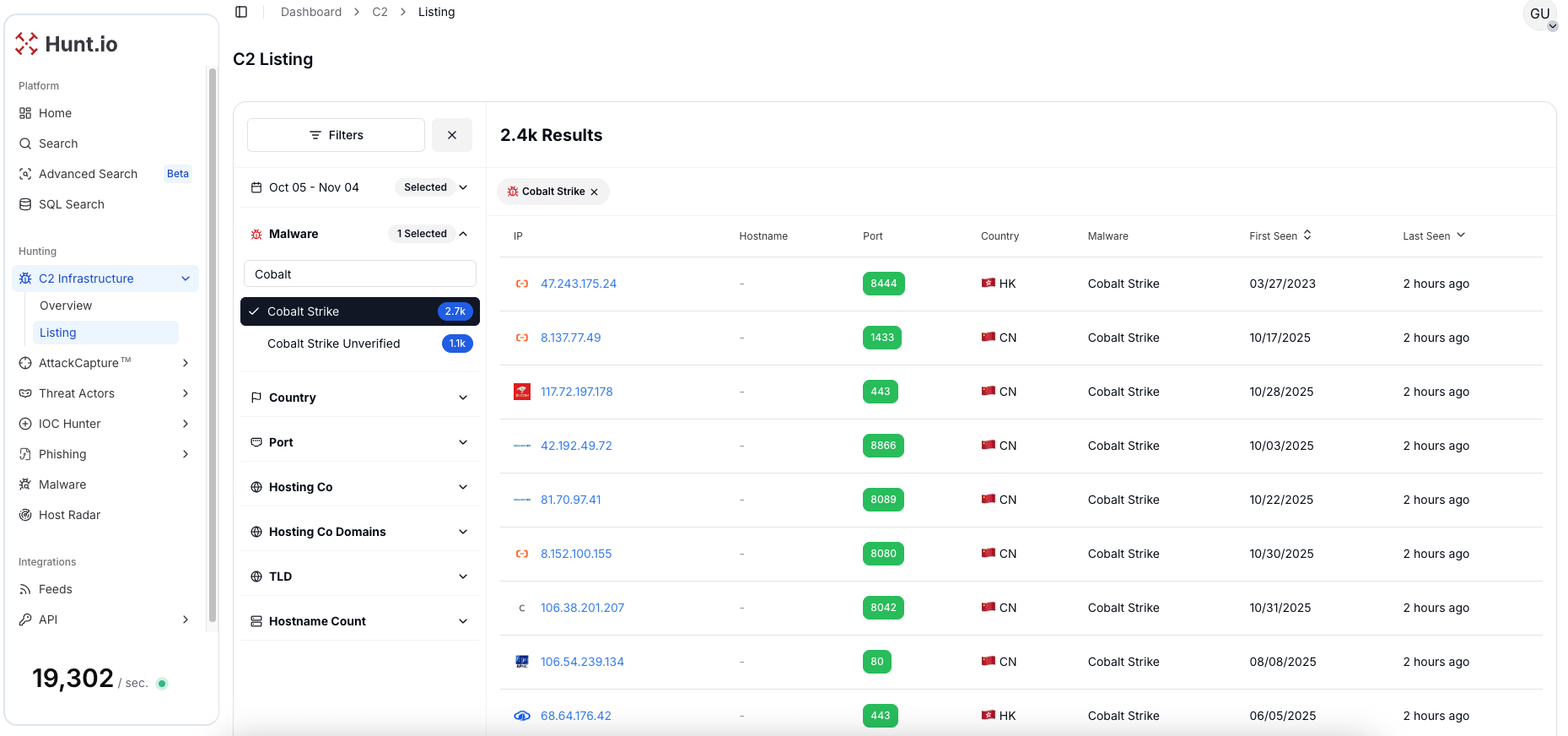 Figure 4:Breakdown of confirmed and unverified cross-platform Cobalt Strike instances.
Figure 4:Breakdown of confirmed and unverified cross-platform Cobalt Strike instances.After reviewing global trends and recurring behaviors, the real value lies in focusing on one detection and following where it leads.
Investigating a Single Detection
In this view, we're looking at data from October 5th through November 4th, 2025, filtered specifically for Cobalt Strike. The left panel gives us the filters we need to narrow things down. There are 2.7k confirmed Cobalt Strike results and approximately 1.1k unverified ones. We can filter by country, port, hosting company, or other relevant criteria to slice the data as needed.
This view gives us a practical workspace for understanding how C2 infrastructure behaves. It allows quick identification of active ports, frequently abused hosting providers, and regions with concentrated activity.
One notable IP address, 47.243.175[.]24, quickly caught our attention during the analysis. It is registered to Alibaba (US) Technology Co., Ltd. in Hong Kong and is considered high risk by the security community due to confirmed Cobalt Strike activity across multiple ports.
At first glance, the server appears standard, running SSH and Nginx web servers on ports 80 and 888. Deeper analysis, however, reveals suspicious activity on ports 8443 and 8444, consistent with Cobalt Strike command-and-control (C2) traffic, indicating potential malicious use.
While Cobalt Strike itself is a legitimate tool for penetration testing, threat actors frequently abuse it to control compromised machines and move laterally within networks.
![Figure 5: High-risk IP 47.243.175[.]24 showing timeline, domains, and pivot indicators.](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/11-2025/The+Complete+Guide+to+Hunting+Cobalt+Strike+-+Part+3+Automated+C2+Infrastructure+Discovery+-+figure+5.png) Figure 5: High-risk IP 47.243.175[.]24 showing timeline, domains, and pivot indicators.
Figure 5: High-risk IP 47.243.175[.]24 showing timeline, domains, and pivot indicators.The timeline is particularly noteworthy. This IP has been tied to Cobalt Strike activity since September 2023 and is still active as of November 2025. This represents more than two years of continuous operation, suggesting persistent, well-maintained infrastructure rather than a short-term compromise.
We’re able to track this with confidence because the verification work happens automatically in our platform. Confirmed detections are supported by certificate analysis and protocol matching, providing reliable findings without reliance on incomplete data.
The IP detail view enables navigation between different layers of intelligence without repeating searches. Tabs at the top allow access to all connected data points.
In the first image, the Domains tab shows that this IP, 47.243.175[.]24, is associated with three domains within the rxjh[.]online infrastructure. From there, we focus on the Pivots tab, which highlights four critical indicators that help minimize false positives.
![Figure 6: Domains related to 47.243.175[.]24](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/11-2025/The+Complete+Guide+to+Hunting+Cobalt+Strike+-+Part+3+Automated+C2+Infrastructure+Discovery+-+figure+6.png) Figure 6: Domains related to 47.243.175[.]24
Figure 6: Domains related to 47.243.175[.]24Pivoting Across Indicators
First, the Certificate Issuer CN and Certificate Subject CN are both tied to mail.live.com, with 31 detections each. This is noteworthy because mail.live.com is a legitimate Microsoft service, yet the presence of these certificates on a known Cobalt Strike IP is a red flag.
When a legitimate service certificate is repurposed on malicious infrastructure, it is typically done intentionally. The 31 detections provide confidence that this is not random noise.
We then pivot to the X.509 certificate with 300 detections. The higher detection count indicates that this certificate fingerprint has been observed across multiple connections and infrastructure components. The 300 instances of the same certificate hash suggest systematic use rather than a one-off occurrence.
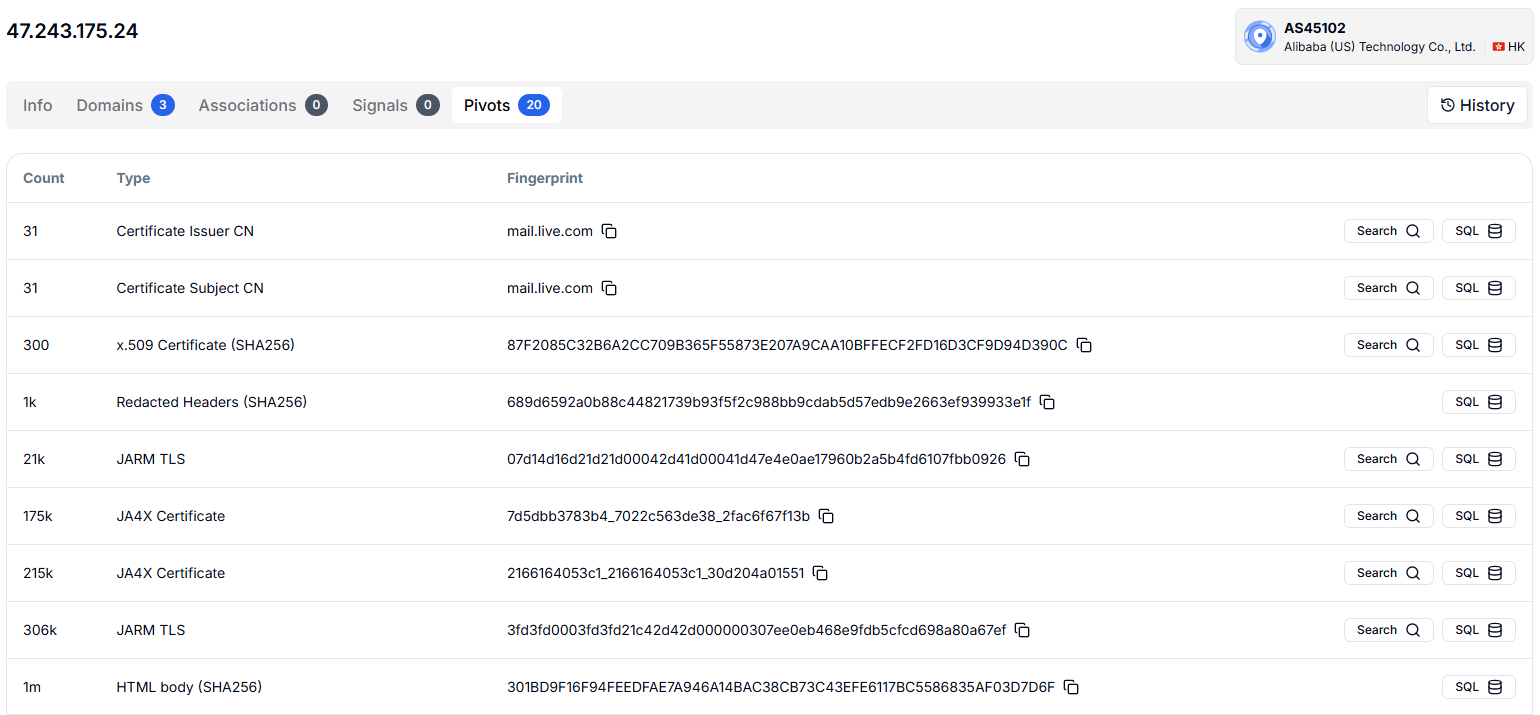 Figure 7: Certificate pivots including Issuer CN, Subject CN, and X.509 hashes across detections.
Figure 7: Certificate pivots including Issuer CN, Subject CN, and X.509 hashes across detections.Finally, the Redacted Headers SHA256 hash, with over 1,000 detections, demonstrates a clear pattern. These instances of the same header signature indicate that the platform has tracked this across significant volumes of traffic associated with this operator, providing strong validation.
We focus on these four pivots because their detection counts give us high confidence, and we stick to high-confidence indicators instead of chasing every possible connection.
When other IPs share the same Certificate Issuer CN, X.509 certificate, or Redacted Headers at similar detection volumes, it indicates infrastructure linked to the same threat actor. The detection counts serve as evidence that these are genuine clusters of coordinated infrastructure, not false positives.
Once we've identified the key pivots from the initial IP, the next step is to scale up. Checking each indicator by hand doesn't work, so we use the SQL Editor to query all infrastructure connected to these signatures.
Identifying Infrastructure Patterns
Our first query targets the certificate indicators we already identified. It looks for any instances with the mail.live.com certificate issuer or the flagged X.509 certificate hash, going 30 days back to capture recent activity.
This single search returned multiple IPs across different ports, each with its own activity timeline. Some were on port 11112, others on 443 or 4434. The variations in ports suggest that threat actors are distributing their infrastructure across multiple services to evade detection.
SELECT
ip,
port,
min(timestamp),
max(timestamp)
FROM
certificates
WHERE
(
issuer.common_name == "mail.live.com"
or certificate_hash == "87F2085C32B6A2CC709B365F55873E207A9CAA10BFFECF2FD16D3CF9D94D390C"
)
AND timestamp > NOW - 30 DAY
GROUP BY ip, port
CopyOutput example:
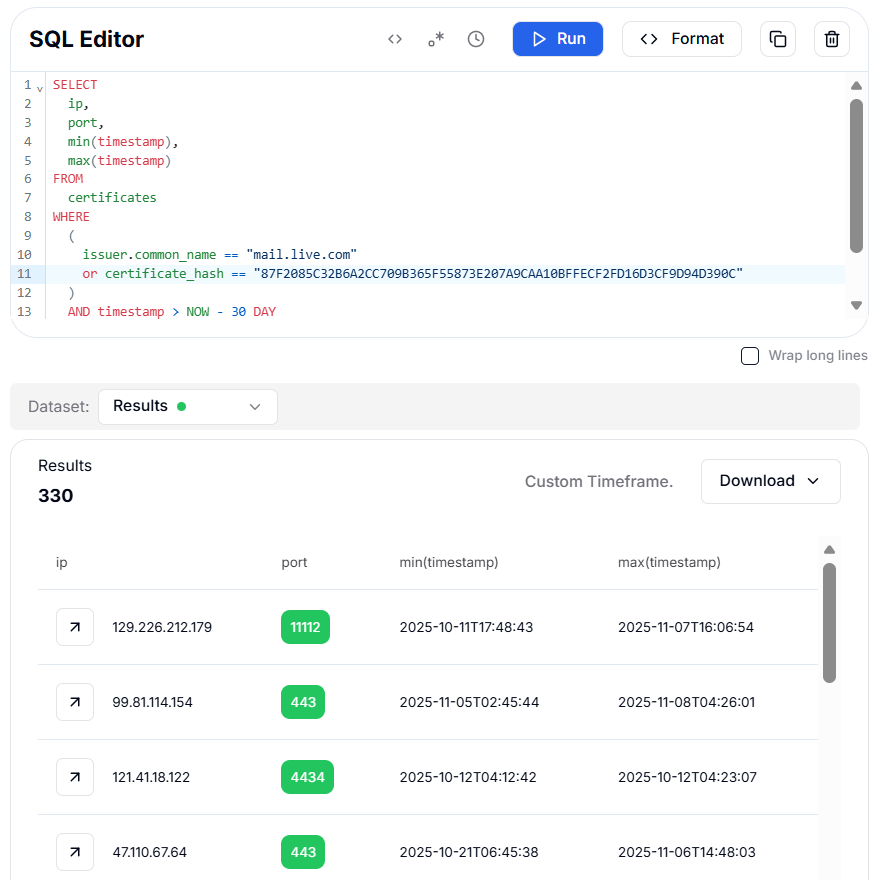 Figure 8: Query targeting the certificate indicators with the mail.live.com certificate issuer or the flagged X.509 certificate hash
Figure 8: Query targeting the certificate indicators with the mail.live.com certificate issuer or the flagged X.509 certificate hashIn the second query, we focus on the Redacted Headers SHA256 signature we saw earlier, with over 1,000 detections. We crafted a HuntSQL query to identify all IPs observed with that header signature in the last 30 days and grouped the results by IP and port to analyze its distribution.
SELECT
ip,
port,
min(timestamp),
max(timestamp)
FROM
httpv2
WHERE
http.headers.redacted.hash.sha256 == "689d6592a0b88c44821739b93f5f2c988bb9cdab5d57edb9e2663ef939933e1f"
AND timestamp > NOW - 30 DAY
GROUP BY
ip,
port
CopyOutput example:
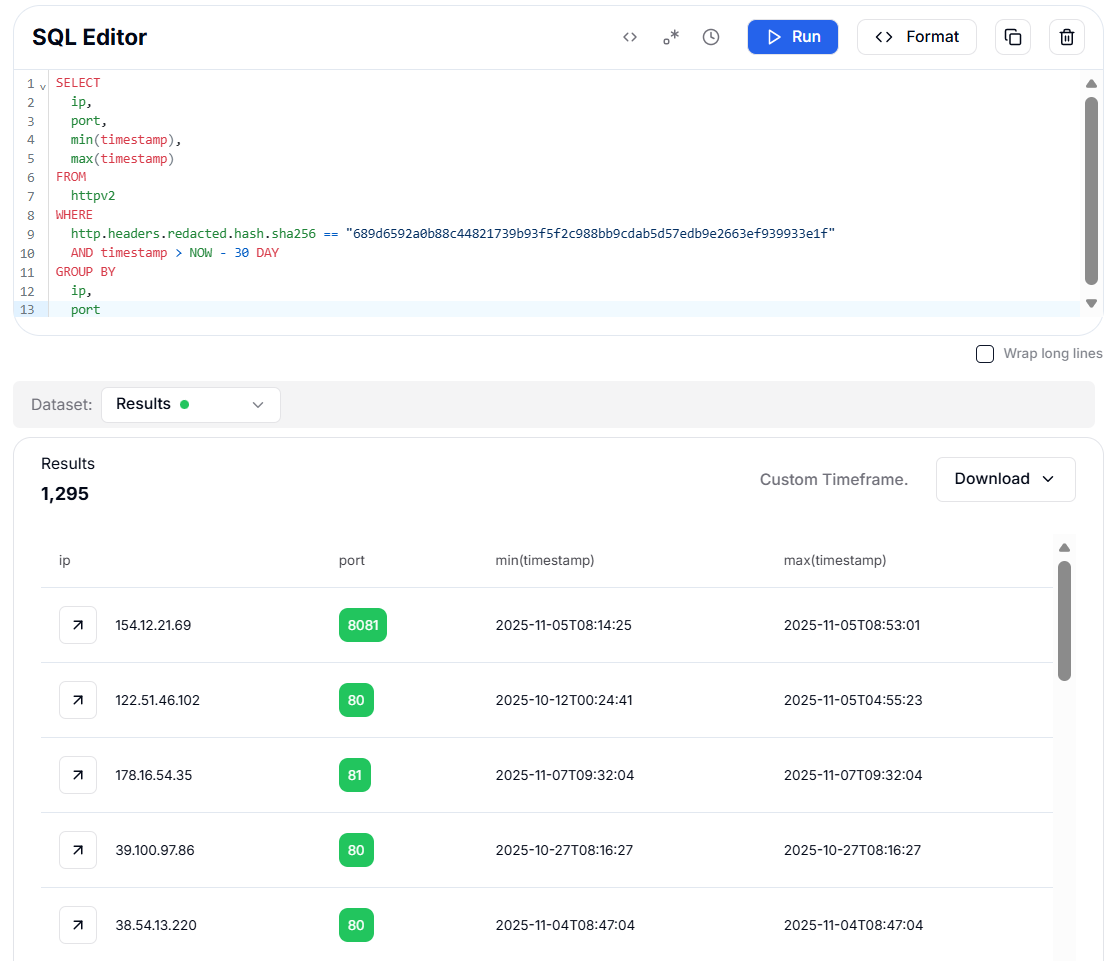 Figure 9: Query targeting Redacted Headers SHA256 signature
Figure 9: Query targeting Redacted Headers SHA256 signaturePivoting from a single suspicious IP can quickly uncover more than a thousand related indicators. Hunt’s automated discovery, combined with HuntSQL search and these pivots, enables systematic collection of all infrastructure sharing the identified signatures and removes much of the guesswork from investigation.
Mitigation Strategies
Detecting and understanding Cobalt Strike infrastructure is only part of the challenge. The next step involves applying practical mitigation strategies to reduce exposure and limit the impact of C2 operations within an environment. The following measures can help organizations strengthen their defenses:
Enforce Network Segmentation: Limit lateral movement by isolating critical systems and applying strict access controls between network zones. This prevents Cobalt Strike beacons from easily communicating with command servers once an endpoint is compromised.
Monitor for Known C2 Indicators: Continuously monitor network traffic for suspicious ports such as 8443, 8444, 11112, and 4434, which are often used by Cobalt Strike. Implement threat intelligence feeds from Hunt.io or other sources to automatically flag IPs, domains, and certificate fingerprints associated with active C2 infrastructure.
Apply Strict Egress Filtering: Block unnecessary outbound connections and restrict external communication to trusted destinations. Egress controls make it significantly harder for Cobalt Strike payloads to reach their command servers and exfiltrate data.
Detect Beaconing Behavior: Deploy network detection and response (NDR) or intrusion detection systems (IDS) capable of identifying beacon-like traffic patterns. Look for regular, timed outbound connections or encrypted traffic over uncommon ports, which often indicate Cobalt Strike beacon activity.
Harden Endpoint Defenses: Use endpoint detection and response (EDR) solutions that can spot Cobalt Strike artifacts such as named pipes, process injection, and memory-resident modules. Regularly update endpoint agents and enable advanced telemetry for behavioral detection.
Validate Certificates and TLS Traffic: Inspect TLS certificates used in outbound connections. Cobalt Strike operators frequently reuse or spoof legitimate certificate data, such as mail.live.com. Certificate validation and fingerprint monitoring can help identify impersonated infrastructure early.
Implement Continuous Threat Hunting: Integrate automated Hunt.io queries into your hunting workflows to proactively discover related infrastructure. Regular threat hunts based on certificate hashes, header signatures, and behavioral patterns can uncover evolving C2 clusters before they are used in active campaigns.
Strengthen Incident Response Procedures: Prepare a playbook for detecting, isolating, and responding to Cobalt Strike activity. This should include rapid containment steps, forensic collection, and communication protocols to prevent further spread within the network.
Conclusion
Hunt.io C2 dashboard turns Cobalt Strike hunting from a tedious, manual task into a fast, visual process. We can see the full scope of activity at a glance, with automated detections based on certificate analysis and protocol inspection, plus detailed IP and domain views to trace connections across servers, providers, and regions.
Pivot instantly between indicators. Move from a single IP to related infrastructure sharing the same certificates, headers, or behaviors, and uncover coordinated C2 clusters in minutes. If you want to see how this looks in practice, book a demo today and try it inside the platform.
Cobalt Strike IOCs
The following indicators were confirmed during this investigation. These IOCs represent a combination of active samples and historical Cobalt Strike infrastructure observed through Hunt.io's automated detection.
| IP Address | City | ASN | Company |
|---|---|---|---|
| 35.77.170[.]224 | Tokyo | AS16509 | Amazon Data Services Japan |
| 61.135.130[.]191 | Beijing | AS4808 | China Unicom Beijing province network |
| 123.206.226[.]226 | Shanghai | AS45090 | Tencent cloud computing (Beijing) Co., Ltd. |
| 118.89.81[.]201 | Shanghai | AS45090 | Tencent cloud computing (Beijing) Co., Ltd. |
| 47.92.222[.]254 | Beijing | AS37963 | Aliyun Computing Co., LTD |
| 49.233.177[.]30 | Beijing | AS45090 | Tencent cloud computing (Beijing) Co., Ltd. |
| 8.131.103[.]16 | Beijing | AS37963 | Aliyun Computing Co.LTD |
| 47.108.63[.64] | Chengdu | AS37963 | Aliyun Computing Co., LTD |
| 47.100.63[.]226 | Shanghai | AS37963 | Aliyun Computing Co., LTD |
| 120.48.25[.]39 | Beijing | AS38365 | Beijing Baidu Netcom Science and Technology Co., Ltd. |
| 198.46.217[.]168 | Ashburn | AS36352 | HostPapa |
| 114.67.243[.]235 | Beijing | AS23724 | Beijing Jingdong 360 Degree E-commerce Co., Ltd. |
| 47.115.229[.163] | Shenzhen | AS37963 | Aliyun Computing Co., LTD |
| 99.81.114[.]154 | Dublin | AS16509 | Amazon Data Services Ireland Limited |
| 43.133.41[.]106 | Singapore | AS132203 | Asia Pacific Network Information Center, Pty. Ltd. |
| 47.92.233[.]242 | Beijing | AS37963 | Aliyun Computing Co., LTD |
| 113.207.49[.]133 | Chongqing | AS4837 | China Unicom Chongqing Province Network |
| 107.174.144[.]204 | Buffalo | AS36352 | RackNerd LLC |
| 120.53.107[.]202 | Beijing | AS45090 | Beijing Voda Telecom Technology Co. Ltd. |
| 156.225.20[.]77 | Hong Kong | AS401696 | Vapeline Technology |
| 8.136.1[.]42 | Hangzhou | AS37963 | Aliyun Computing Co.LTD |
| 1.94.228[.]130 | Beijing | AS55990 | Beijing Teletron Telecom Engineering Co., Ltd. |
| 106.55.60[.]141 | Guangzhou | AS45090 | Tencent cloud computing (Beijing) Co., Ltd. |
| 123.57.239[.]178 | Beijing | AS37963 | Aliyun Computing Co., LTD |
| 121.43.57[.]122 | Hangzhou | AS37963 | Aliyun Computing Co., LTD |
| 47.100.86[.]35 | Shanghai | AS37963 | Aliyun Computing Co., LTD |
| 8.137.149[.]67 | Chengdu | AS37963 | Aliyun Computing Co.LTD |
| 106.52.136[.]106 | Guangzhou | AS45090 | Tencent cloud computing (Beijing) Co., Ltd. |
| 165.154.225[.]50 | Hong Kong | AS142002 | Scloud Pte Ltd t/a Scloud Pte Ltd |
| 121.41.18[.]122 | Hangzhou | AS37963 | Aliyun Computing Co., LTD |
| 82.165.137[.]177 | Karlsruhe | AS8560 | IONOS SE |
| 81.70.37[.]146 | Beijing | AS45090 | Tencent Cloud Computing (Beijing) Co., Ltd |
| 52.24.111[.]103 | Boardman | AS16509 | Amazon Technologies Inc. |
| 203.91.76[.]95 | Hong Kong | AS400619 | AROSSCLOUD INC. |
| 137.220.194[.]49 | Tokyo | AS152194 | CTG Server Ltd. |
| 59.110.7[.]32 | Beijing | AS37963 | Aliyun Computing Co., LTD |
| 185.242.235[.]158 | Hong Kong | AS55933 | MeiPing HuLian |
| 129.226.212[.]179 | Singapore | AS132203 | - |
| 47.110.67[.]64 | Hangzhou | AS37963 | Aliyun Computing Co., LTD |
| 54.191.68[.]151 | Boardman | AS16509 | Amazon.com, Inc. |
| 81.70.197[.]166 | Beijing | AS45090 | Tencent Cloud Computing (Beijing) Co., Ltd |
| 46.17.41[.]9 | Mytishchi | AS51659 | LLC BAXET |
| 58.87.103[.]59 | Beijing | AS45090 | Tencent cloud computing (Beijing) Co., Ltd. |
| 38.38.251[.]151 | Hong Kong | AS139659 | PEG TECH INC |
| 31.59.41[.]163 | Helsinki | AS56971 | CGI GLOBAL LIMITED |
| 45.138.16[.]178 | Warsaw | AS210558 | 1337 Services GmbH |
| 45.158.8[.]189 | Muriaé | AS272547 | Tyna Host Datacenter no Brasil |
| 47.109.201[.]173 | Chengdu | AS37963 | Aliyun Computing Co., LTD |
| 45.135.118[.]251 | Hong Kong | AS932 | XNNET LIMITED |
| 198.46.234[.]37 | Dallas | AS36352 | RackNerd LLC |
| 123.57.38[.]20 | Beijing | AS37963 | Aliyun Computing Co., LTD |
Over the first two parts of this series, we've looked at Cobalt Strike from different angles. Part 1 walked through how exposed open directories can leak tooling, and Part 2 showed how structured HuntSQL queries help map out live C2 activity. With that foundation set, this third part focuses on something most teams want but rarely have time to build themselves: automated Cobalt Strike discovery inside the Hunt.io interface.
Instead of inspecting IPs one by one, our platform gives you a wider lens. The C2 Overview, C2 Listing view, and pivot panels highlight long-running servers, reused certificates, repeated header signatures, and full clusters of related infrastructure with almost no manual work.
This gives you a real-time look at how Cobalt Strike behaves at scale and how quickly a single detection can grow into a full map of coordinated C2 assets. Let's get into it.
Automated Detection in the C2 Dashboard
The best way to kick things off is with the C2 Overview dashboard. It gives us a clear, high-level read on malware families (including Cobalt Strike) activities without getting bogged down in individual IPs.
 Figure 1: C2 Overview Dashboard with real-time live C2 detections
Figure 1: C2 Overview Dashboard with real-time live C2 detectionsOn the right side, we can quickly spot recently detected Cobalt Strike servers. Clicking any of them opens the active Cobalt Strike instances page, where we can follow C2 activity over time. Between 800 and 1,000 IPs are actively running Cobalt Strike infrastructure, and what really stands out is how steady this activity stays throughout the month.
There is no major spike or dramatic drop-off. Activity continues at a steady baseline, which indicates something important: this threat is sustained and persistent.
 Figure 2: Global Cobalt Strike activity
Figure 2: Global Cobalt Strike activityNext to that is the hostname trend, hovering around 60 to 90 active hostnames tied to these Cobalt Strike servers. There's some fluctuation, but nothing out of the ordinary. This shows that threat actors are rotating their infrastructure slightly, without significant disruption.
The real game changer is the 90% validation confidence score. Hunt.io does not take guesses; certificate matching, header analysis, and protocol inspection are applied to every detection. This ensures that flagged activity is legitimate, with no false positives cluttering the alert queue.

Cobalt Strike Listing View
The C2 Listing view gives us a comprehensive picture of Cobalt Strike activity. The dashboard displays 2,400 confirmed detections, consolidated in a single view. It pulls together IP addresses, ports, countries of operation, and hosting companies in one place.
What makes this view particularly useful are the filtering options. Detections can be narrowed down by malware family, ASN, port number, or TLD, allowing patterns to emerge. Analysis reveals that certain hosting providers appear repeatedly, while specific ports such as 8443 and 8444 experience constant activity from active beacons. These patterns indicate how threat actors operate and where infrastructure is being deployed.
The breakdown of Cobalt Strike detections shows 1,467 confirmed instances across multiple categories: 57 tagged as C2 infrastructure, 6 marked as Penetration Testing Tools, 9 flagged for Command and Control operations, and 12 identified as cross-platform capable.
There's also 1 classified specifically as a Team Server, which is the command center where operators control everything. Then on the unverified side, there are another 801 Cobalt Strike detections that haven't been fully confirmed yet, but are showing all the same patterns. These unverified ones have 57 C2 instances, 6 Penetration Testing Tools, 9 Command and Control tagged, and 20 cross-platform variants.
 Figure 3: C2 Listing view showing confirmed detections with IPs, ports, and hosting providers.
Figure 3: C2 Listing view showing confirmed detections with IPs, ports, and hosting providers.The presence of a high number of cross-platform instances in the unverified category, 20 compared to 12 in the confirmed set, suggests that threat actors are actively working to expand their infrastructure across different operating systems.
Combined, that's over 2,200 Cobalt Strike-related detections. Some are locked in as confirmed threats, others are still being assessed, but they're all following the same playbook. They're all abusing legitimate security tools for malicious purposes, and they're all spreading across Windows, Linux, and Mac environments to cast as wide a net as possible.
 Figure 4:Breakdown of confirmed and unverified cross-platform Cobalt Strike instances.
Figure 4:Breakdown of confirmed and unverified cross-platform Cobalt Strike instances.After reviewing global trends and recurring behaviors, the real value lies in focusing on one detection and following where it leads.
Investigating a Single Detection
In this view, we're looking at data from October 5th through November 4th, 2025, filtered specifically for Cobalt Strike. The left panel gives us the filters we need to narrow things down. There are 2.7k confirmed Cobalt Strike results and approximately 1.1k unverified ones. We can filter by country, port, hosting company, or other relevant criteria to slice the data as needed.
This view gives us a practical workspace for understanding how C2 infrastructure behaves. It allows quick identification of active ports, frequently abused hosting providers, and regions with concentrated activity.
One notable IP address, 47.243.175[.]24, quickly caught our attention during the analysis. It is registered to Alibaba (US) Technology Co., Ltd. in Hong Kong and is considered high risk by the security community due to confirmed Cobalt Strike activity across multiple ports.
At first glance, the server appears standard, running SSH and Nginx web servers on ports 80 and 888. Deeper analysis, however, reveals suspicious activity on ports 8443 and 8444, consistent with Cobalt Strike command-and-control (C2) traffic, indicating potential malicious use.
While Cobalt Strike itself is a legitimate tool for penetration testing, threat actors frequently abuse it to control compromised machines and move laterally within networks.
![Figure 5: High-risk IP 47.243.175[.]24 showing timeline, domains, and pivot indicators.](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/11-2025/The+Complete+Guide+to+Hunting+Cobalt+Strike+-+Part+3+Automated+C2+Infrastructure+Discovery+-+figure+5.png) Figure 5: High-risk IP 47.243.175[.]24 showing timeline, domains, and pivot indicators.
Figure 5: High-risk IP 47.243.175[.]24 showing timeline, domains, and pivot indicators.The timeline is particularly noteworthy. This IP has been tied to Cobalt Strike activity since September 2023 and is still active as of November 2025. This represents more than two years of continuous operation, suggesting persistent, well-maintained infrastructure rather than a short-term compromise.
We’re able to track this with confidence because the verification work happens automatically in our platform. Confirmed detections are supported by certificate analysis and protocol matching, providing reliable findings without reliance on incomplete data.
The IP detail view enables navigation between different layers of intelligence without repeating searches. Tabs at the top allow access to all connected data points.
In the first image, the Domains tab shows that this IP, 47.243.175[.]24, is associated with three domains within the rxjh[.]online infrastructure. From there, we focus on the Pivots tab, which highlights four critical indicators that help minimize false positives.
![Figure 6: Domains related to 47.243.175[.]24](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/11-2025/The+Complete+Guide+to+Hunting+Cobalt+Strike+-+Part+3+Automated+C2+Infrastructure+Discovery+-+figure+6.png) Figure 6: Domains related to 47.243.175[.]24
Figure 6: Domains related to 47.243.175[.]24Pivoting Across Indicators
First, the Certificate Issuer CN and Certificate Subject CN are both tied to mail.live.com, with 31 detections each. This is noteworthy because mail.live.com is a legitimate Microsoft service, yet the presence of these certificates on a known Cobalt Strike IP is a red flag.
When a legitimate service certificate is repurposed on malicious infrastructure, it is typically done intentionally. The 31 detections provide confidence that this is not random noise.
We then pivot to the X.509 certificate with 300 detections. The higher detection count indicates that this certificate fingerprint has been observed across multiple connections and infrastructure components. The 300 instances of the same certificate hash suggest systematic use rather than a one-off occurrence.
 Figure 7: Certificate pivots including Issuer CN, Subject CN, and X.509 hashes across detections.
Figure 7: Certificate pivots including Issuer CN, Subject CN, and X.509 hashes across detections.Finally, the Redacted Headers SHA256 hash, with over 1,000 detections, demonstrates a clear pattern. These instances of the same header signature indicate that the platform has tracked this across significant volumes of traffic associated with this operator, providing strong validation.
We focus on these four pivots because their detection counts give us high confidence, and we stick to high-confidence indicators instead of chasing every possible connection.
When other IPs share the same Certificate Issuer CN, X.509 certificate, or Redacted Headers at similar detection volumes, it indicates infrastructure linked to the same threat actor. The detection counts serve as evidence that these are genuine clusters of coordinated infrastructure, not false positives.
Once we've identified the key pivots from the initial IP, the next step is to scale up. Checking each indicator by hand doesn't work, so we use the SQL Editor to query all infrastructure connected to these signatures.
Identifying Infrastructure Patterns
Our first query targets the certificate indicators we already identified. It looks for any instances with the mail.live.com certificate issuer or the flagged X.509 certificate hash, going 30 days back to capture recent activity.
This single search returned multiple IPs across different ports, each with its own activity timeline. Some were on port 11112, others on 443 or 4434. The variations in ports suggest that threat actors are distributing their infrastructure across multiple services to evade detection.
SELECT
ip,
port,
min(timestamp),
max(timestamp)
FROM
certificates
WHERE
(
issuer.common_name == "mail.live.com"
or certificate_hash == "87F2085C32B6A2CC709B365F55873E207A9CAA10BFFECF2FD16D3CF9D94D390C"
)
AND timestamp > NOW - 30 DAY
GROUP BY ip, port
CopyOutput example:
 Figure 8: Query targeting the certificate indicators with the mail.live.com certificate issuer or the flagged X.509 certificate hash
Figure 8: Query targeting the certificate indicators with the mail.live.com certificate issuer or the flagged X.509 certificate hashIn the second query, we focus on the Redacted Headers SHA256 signature we saw earlier, with over 1,000 detections. We crafted a HuntSQL query to identify all IPs observed with that header signature in the last 30 days and grouped the results by IP and port to analyze its distribution.
SELECT
ip,
port,
min(timestamp),
max(timestamp)
FROM
httpv2
WHERE
http.headers.redacted.hash.sha256 == "689d6592a0b88c44821739b93f5f2c988bb9cdab5d57edb9e2663ef939933e1f"
AND timestamp > NOW - 30 DAY
GROUP BY
ip,
port
CopyOutput example:
 Figure 9: Query targeting Redacted Headers SHA256 signature
Figure 9: Query targeting Redacted Headers SHA256 signaturePivoting from a single suspicious IP can quickly uncover more than a thousand related indicators. Hunt’s automated discovery, combined with HuntSQL search and these pivots, enables systematic collection of all infrastructure sharing the identified signatures and removes much of the guesswork from investigation.
Mitigation Strategies
Detecting and understanding Cobalt Strike infrastructure is only part of the challenge. The next step involves applying practical mitigation strategies to reduce exposure and limit the impact of C2 operations within an environment. The following measures can help organizations strengthen their defenses:
Enforce Network Segmentation: Limit lateral movement by isolating critical systems and applying strict access controls between network zones. This prevents Cobalt Strike beacons from easily communicating with command servers once an endpoint is compromised.
Monitor for Known C2 Indicators: Continuously monitor network traffic for suspicious ports such as 8443, 8444, 11112, and 4434, which are often used by Cobalt Strike. Implement threat intelligence feeds from Hunt.io or other sources to automatically flag IPs, domains, and certificate fingerprints associated with active C2 infrastructure.
Apply Strict Egress Filtering: Block unnecessary outbound connections and restrict external communication to trusted destinations. Egress controls make it significantly harder for Cobalt Strike payloads to reach their command servers and exfiltrate data.
Detect Beaconing Behavior: Deploy network detection and response (NDR) or intrusion detection systems (IDS) capable of identifying beacon-like traffic patterns. Look for regular, timed outbound connections or encrypted traffic over uncommon ports, which often indicate Cobalt Strike beacon activity.
Harden Endpoint Defenses: Use endpoint detection and response (EDR) solutions that can spot Cobalt Strike artifacts such as named pipes, process injection, and memory-resident modules. Regularly update endpoint agents and enable advanced telemetry for behavioral detection.
Validate Certificates and TLS Traffic: Inspect TLS certificates used in outbound connections. Cobalt Strike operators frequently reuse or spoof legitimate certificate data, such as mail.live.com. Certificate validation and fingerprint monitoring can help identify impersonated infrastructure early.
Implement Continuous Threat Hunting: Integrate automated Hunt.io queries into your hunting workflows to proactively discover related infrastructure. Regular threat hunts based on certificate hashes, header signatures, and behavioral patterns can uncover evolving C2 clusters before they are used in active campaigns.
Strengthen Incident Response Procedures: Prepare a playbook for detecting, isolating, and responding to Cobalt Strike activity. This should include rapid containment steps, forensic collection, and communication protocols to prevent further spread within the network.
Conclusion
Hunt.io C2 dashboard turns Cobalt Strike hunting from a tedious, manual task into a fast, visual process. We can see the full scope of activity at a glance, with automated detections based on certificate analysis and protocol inspection, plus detailed IP and domain views to trace connections across servers, providers, and regions.
Pivot instantly between indicators. Move from a single IP to related infrastructure sharing the same certificates, headers, or behaviors, and uncover coordinated C2 clusters in minutes. If you want to see how this looks in practice, book a demo today and try it inside the platform.
Cobalt Strike IOCs
The following indicators were confirmed during this investigation. These IOCs represent a combination of active samples and historical Cobalt Strike infrastructure observed through Hunt.io's automated detection.
| IP Address | City | ASN | Company |
|---|---|---|---|
| 35.77.170[.]224 | Tokyo | AS16509 | Amazon Data Services Japan |
| 61.135.130[.]191 | Beijing | AS4808 | China Unicom Beijing province network |
| 123.206.226[.]226 | Shanghai | AS45090 | Tencent cloud computing (Beijing) Co., Ltd. |
| 118.89.81[.]201 | Shanghai | AS45090 | Tencent cloud computing (Beijing) Co., Ltd. |
| 47.92.222[.]254 | Beijing | AS37963 | Aliyun Computing Co., LTD |
| 49.233.177[.]30 | Beijing | AS45090 | Tencent cloud computing (Beijing) Co., Ltd. |
| 8.131.103[.]16 | Beijing | AS37963 | Aliyun Computing Co.LTD |
| 47.108.63[.64] | Chengdu | AS37963 | Aliyun Computing Co., LTD |
| 47.100.63[.]226 | Shanghai | AS37963 | Aliyun Computing Co., LTD |
| 120.48.25[.]39 | Beijing | AS38365 | Beijing Baidu Netcom Science and Technology Co., Ltd. |
| 198.46.217[.]168 | Ashburn | AS36352 | HostPapa |
| 114.67.243[.]235 | Beijing | AS23724 | Beijing Jingdong 360 Degree E-commerce Co., Ltd. |
| 47.115.229[.163] | Shenzhen | AS37963 | Aliyun Computing Co., LTD |
| 99.81.114[.]154 | Dublin | AS16509 | Amazon Data Services Ireland Limited |
| 43.133.41[.]106 | Singapore | AS132203 | Asia Pacific Network Information Center, Pty. Ltd. |
| 47.92.233[.]242 | Beijing | AS37963 | Aliyun Computing Co., LTD |
| 113.207.49[.]133 | Chongqing | AS4837 | China Unicom Chongqing Province Network |
| 107.174.144[.]204 | Buffalo | AS36352 | RackNerd LLC |
| 120.53.107[.]202 | Beijing | AS45090 | Beijing Voda Telecom Technology Co. Ltd. |
| 156.225.20[.]77 | Hong Kong | AS401696 | Vapeline Technology |
| 8.136.1[.]42 | Hangzhou | AS37963 | Aliyun Computing Co.LTD |
| 1.94.228[.]130 | Beijing | AS55990 | Beijing Teletron Telecom Engineering Co., Ltd. |
| 106.55.60[.]141 | Guangzhou | AS45090 | Tencent cloud computing (Beijing) Co., Ltd. |
| 123.57.239[.]178 | Beijing | AS37963 | Aliyun Computing Co., LTD |
| 121.43.57[.]122 | Hangzhou | AS37963 | Aliyun Computing Co., LTD |
| 47.100.86[.]35 | Shanghai | AS37963 | Aliyun Computing Co., LTD |
| 8.137.149[.]67 | Chengdu | AS37963 | Aliyun Computing Co.LTD |
| 106.52.136[.]106 | Guangzhou | AS45090 | Tencent cloud computing (Beijing) Co., Ltd. |
| 165.154.225[.]50 | Hong Kong | AS142002 | Scloud Pte Ltd t/a Scloud Pte Ltd |
| 121.41.18[.]122 | Hangzhou | AS37963 | Aliyun Computing Co., LTD |
| 82.165.137[.]177 | Karlsruhe | AS8560 | IONOS SE |
| 81.70.37[.]146 | Beijing | AS45090 | Tencent Cloud Computing (Beijing) Co., Ltd |
| 52.24.111[.]103 | Boardman | AS16509 | Amazon Technologies Inc. |
| 203.91.76[.]95 | Hong Kong | AS400619 | AROSSCLOUD INC. |
| 137.220.194[.]49 | Tokyo | AS152194 | CTG Server Ltd. |
| 59.110.7[.]32 | Beijing | AS37963 | Aliyun Computing Co., LTD |
| 185.242.235[.]158 | Hong Kong | AS55933 | MeiPing HuLian |
| 129.226.212[.]179 | Singapore | AS132203 | - |
| 47.110.67[.]64 | Hangzhou | AS37963 | Aliyun Computing Co., LTD |
| 54.191.68[.]151 | Boardman | AS16509 | Amazon.com, Inc. |
| 81.70.197[.]166 | Beijing | AS45090 | Tencent Cloud Computing (Beijing) Co., Ltd |
| 46.17.41[.]9 | Mytishchi | AS51659 | LLC BAXET |
| 58.87.103[.]59 | Beijing | AS45090 | Tencent cloud computing (Beijing) Co., Ltd. |
| 38.38.251[.]151 | Hong Kong | AS139659 | PEG TECH INC |
| 31.59.41[.]163 | Helsinki | AS56971 | CGI GLOBAL LIMITED |
| 45.138.16[.]178 | Warsaw | AS210558 | 1337 Services GmbH |
| 45.158.8[.]189 | Muriaé | AS272547 | Tyna Host Datacenter no Brasil |
| 47.109.201[.]173 | Chengdu | AS37963 | Aliyun Computing Co., LTD |
| 45.135.118[.]251 | Hong Kong | AS932 | XNNET LIMITED |
| 198.46.234[.]37 | Dallas | AS36352 | RackNerd LLC |
| 123.57.38[.]20 | Beijing | AS37963 | Aliyun Computing Co., LTD |
Related Posts
Related Posts
Related Posts
©2026 Hunt Intelligence, Inc.
©2026 Hunt Intelligence, Inc.
©2025 Hunt Intelligence, Inc.