The Complete Guide to Hunting Cobalt Strike - Part 2: 10+ HuntSQL Recipes to Find Cobalt Strike
The Complete Guide to Hunting Cobalt Strike - Part 2: 10+ HuntSQL Recipes to Find Cobalt Strike
Published on
In Part 1, we showed how open directories and repeated certificates can reveal real Cobalt Strike infrastructure. In this second part, we're focusing on how to take those findings further with HuntSQL™.
Cobalt Strike continues to appear in campaigns run by APT groups, ransomware operators, and brokers who use it to maintain access and move across networks. With HuntSQL™, it's possible to search across datasets, connect beacon traits, and uncover related servers without adding noise.
Here we're sharing 10 practical HuntSQL™ recipes that help detect, group, and track Cobalt Strike infrastructure. Each one comes from real hunting scenarios, built to deliver clear and repeatable results.
Why Targeting Cobalt Strike Infrastructure Matters
Cobalt Strike is a commercial adversary-simulation framework originally built for red teams and penetration testers. At its core, it provides an interactive post-exploitation agent and a flexible command-and-control (C2) framework that supports command execution, file transfer, SOCKS proxying, credential harvesting, lateral movement, and customizable ("malleable") C2 profiles, effectively enabling an operator to emulate the full range of attacker post-exploit tactics.
According to the Insikt Group's "2024 Malicious Infrastructure Report", Cobalt Strike accounted for 65% of all command-and-control (C2) servers linked to offensive-security tools (OSTs). In the same report, across selected countries in Asia, Europe, and Africa, roughly 73% of all victims were attributed to infections involving AsyncRAT, QuasarRAT, and Cobalt Strike. According to Sophos' "Active Adversary Report" (1H 2024), Cobalt Strike was present in 13.68% of incident response cases, whereas the "2024 Global Threat Report" from Elastic indicates that off-the-shelf offensive tools like Cobalt Strike and Metasploit combined accounted for ≈ 54% of observed malware alerts.
So when you are able to consistently spot Cobalt Strike infrastructure, you are not just catching one framework. You are getting early visibility into a big portion of serious intrusions, from APT activity to ransomware operations. That is exactly the type of problem that benefits from structured, repeatable HuntSQL™ queries instead of one-off searches.
Enter HuntSQL™
At Hunt.io, our mission is to simplify your Cobalt Strike hunting. Using HuntSQL™, analysts can rapidly query, pivot, and correlate across multiple datasets, revealing Cobalt Strike fingerprints that might otherwise remain hidden.
Whether analyzing beacon metadata, SSL certificate reuse, or anomalous TLS handshakes, HuntSQL™ enables real-time threat infrastructure mapping without exposing sensitive environments to risk.
Let's now review the syntax and then walk through the recipes.
Syntax Overview
HuntSQL™ provides an enriched Malware Dataset, a compact, high-value inventory of scanner-observed command-and-control (C2) and malware infrastructure. It includes key attributes such as IP addresses, hostnames, ports, ASN, and organization information, scan provenance (including source, timestamp, and confidence), and classification tags.
For threat hunters, this dataset offers a unified view of malicious infrastructure that supports fast correlation, campaign clustering, and prioritization of active threats.
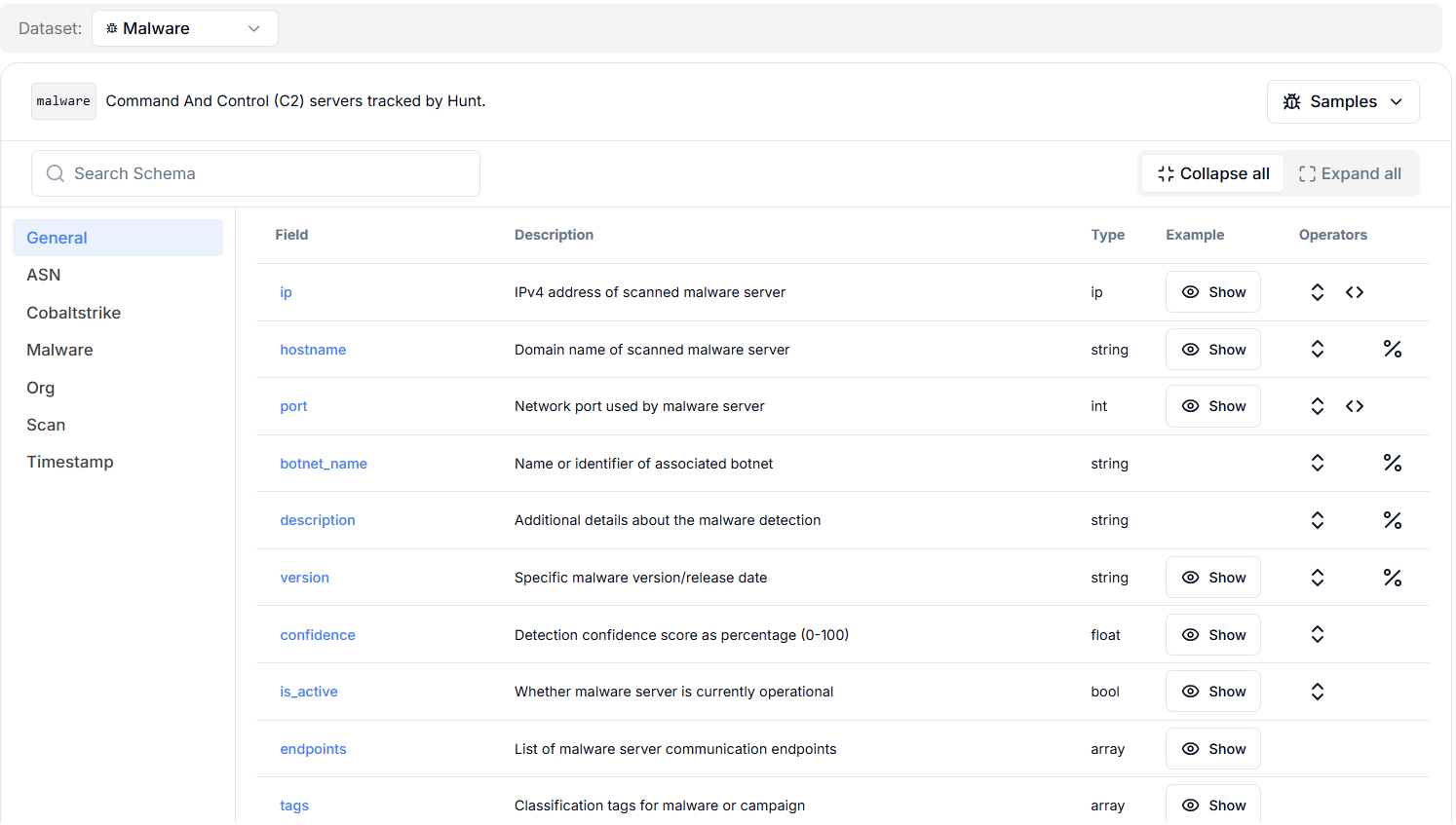 Figure 1. The malware dataset provides detailed fields related to 7 categories, including Generic fields, ASN, Cobalt Strike, Malware name, organization details, scan methods, and timestamp fields.
Figure 1. The malware dataset provides detailed fields related to 7 categories, including Generic fields, ASN, Cobalt Strike, Malware name, organization details, scan methods, and timestamp fields.Among the malware dataset, and for this scenario, the most valuable components are the Cobalt Strike fields, which provide a detailed fingerprinting model for detecting and investigating beacons.
The cobaltstrike.* fields capture both deterministic artifacts like the SHA256 public key and watermark or license ID, and behavioral traits such as domains, submit URIs, user-agent strings, sleeptime, jitter, and process injection targets.
These attributes are particularly valuable for identifying unique beacon configurations, correlating related servers, and mapping malicious infrastructure reuse across campaigns.
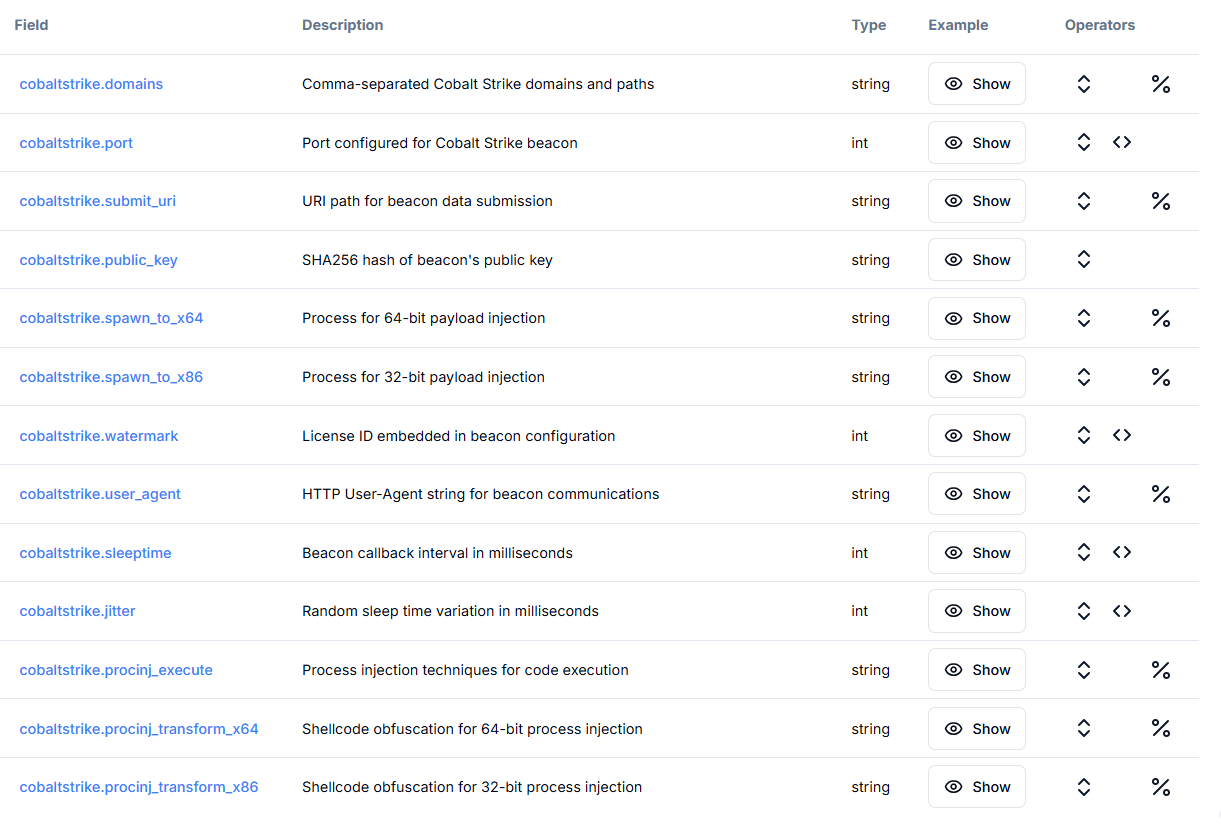 Figure 2. Hunt.io enriched Cobalt Strike fields within the Malware Dataset, which gives valuable information to pivot further to servers.
Figure 2. Hunt.io enriched Cobalt Strike fields within the Malware Dataset, which gives valuable information to pivot further to servers.Now that the structure of the dataset is clear, here's how its Cobalt Strike fields actually support the hunt:
Cluster and Attribute Infrastructure: Fields like cobaltstrike.public_key and cobaltstrike.watermark act as campaign-level fingerprints that allow hunters to connect infrastructure across time and intelligence sources.
Detecting Operational Behavior: Parameters such as cobaltstrike.sleeptime, cobaltstrike.jitter, and cobaltstrike.user_agent help identify beaconing activity and highlight potentially compromised systems in network telemetry.
Correlate Process Activity: Fields including cobaltstrike.spawn_to_x64, cobaltstrike.spawn_to_x86, and cobaltstrike.procinj_* link network evidence to endpoint processes, helping analysts validate execution behaviors or injection attempts.
These elements make the Hunt.io Malware Dataset a powerful resource for structured hunting. It enables analysts to pivot from network to endpoint, combine static and behavioral indicators, and perform accurate attribution, ultimately supporting faster detection and more effective response against Cobalt Strike-related threats.
With the dataset and fingerprints laid out, the next step is applying them in real hunts.
10+ ways to detect Cobalt Strike with HuntSQL™
The following section presents a collection of Cobalt Strike hunting recipes designed to transform Hunt.io's malware dataset into actionable intelligence. Each query demonstrates a practical method to identify, cluster, or attribute Cobalt Strike activity using enriched telemetry fields.
For a threat hunter or threat intel analyst, these "recipes" serve not only as detection patterns but also as analytical starting points, enabling deeper pivoting across infrastructure, behavioral, and cryptographic indicators to trace active beacon networks and their operators.
1. Identifying Prevalent Malware Frameworks in the Dataset
The first query aggregates all entries by malware.name to highlight the most frequently detected malware or offensive frameworks in the malware dataset.
SELECT
malware.name,
count(*) AS total
FROM
malware
GROUP BY
malware.name
ORDER BY
total DESC
CopyOutput example:
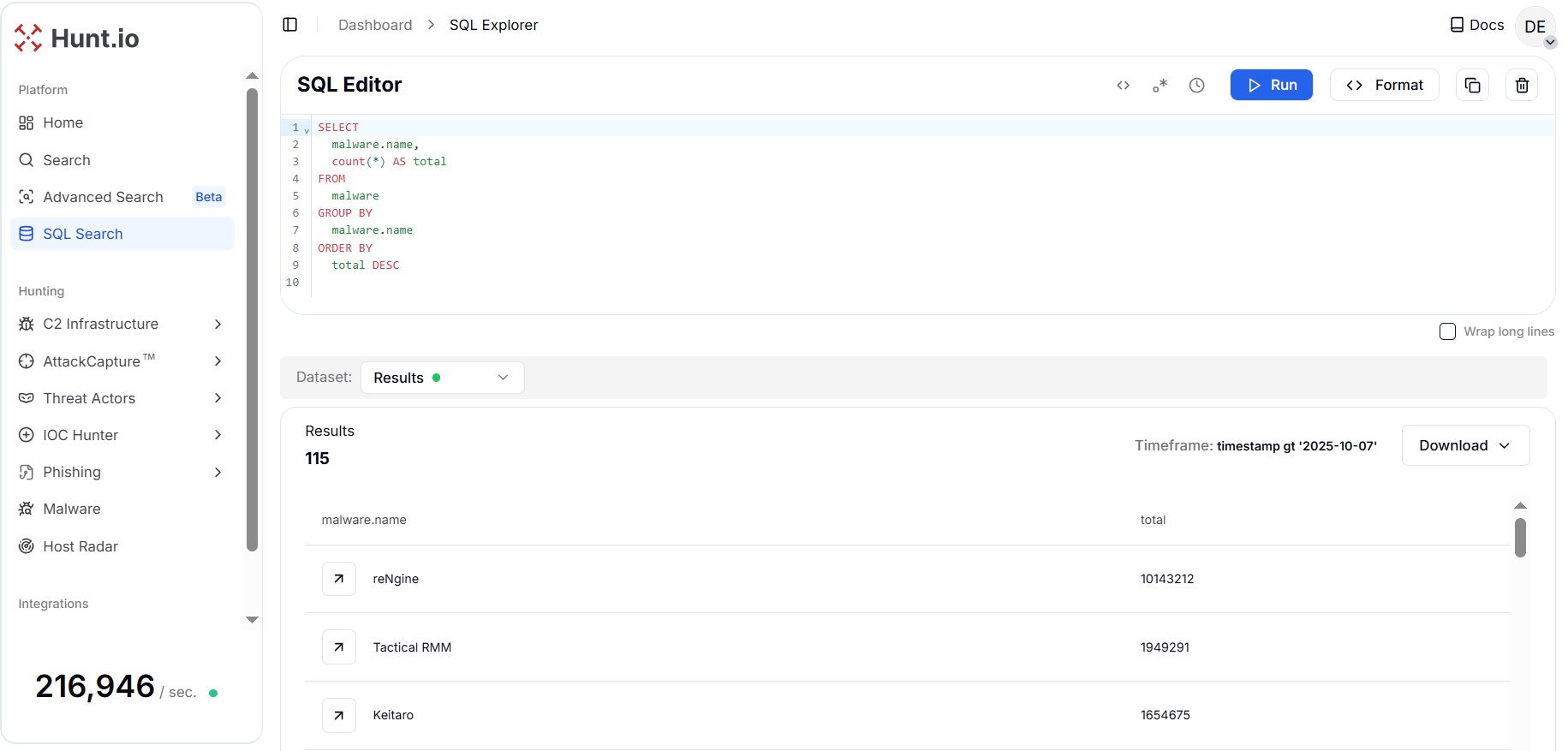 Figure 3. Distribution of detected malware families to prioritize hunt targets and separate benign tooling from adversary frameworks.
Figure 3. Distribution of detected malware families to prioritize hunt targets and separate benign tooling from adversary frameworks.The results reveal a landscape dominated by well-known tools and scanners such as reNgine, Tactical RMM, and Keitaro, while also showing significant representation from command-and-control frameworks, including Cobalt Strike (372,082 detections) and Cobalt Strike Unverified (78,693 detections).
This distribution provides an early indication of which tools are most active across observed infrastructures, helping analysts distinguish between legitimate red-team utilities and adversarial C2 frameworks.
From a threat hunting perspective, this query acts as a baseline reconnaissance step. It establishes visibility into the relative footprint of known malware families, allowing hunters to prioritize their investigations around high-impact frameworks like Cobalt Strike, Metasploit, and Pyramid C2.
2. Identifying Active Cobalt Strike Beacons Using Watermarks
This query focuses on isolating recent Cobalt Strike beacon activity by filtering records where the field cobaltstrike.watermark equals 1, a well-known default value found in cracked or pirated versions of the tool often used by threat actors. By limiting the timeframe to the last two months, the query highlights currently active infrastructures.
SELECT
timestamp.day,
ip,
port,
malware.name,
scan.uri,
cobaltstrike.watermark
FROM
malware
WHERE
cobaltstrike.watermark == '1'
AND timestamp > NOW - 2 MONTH
ORDER BY
timestamp.day DESC
CopyOutput example:
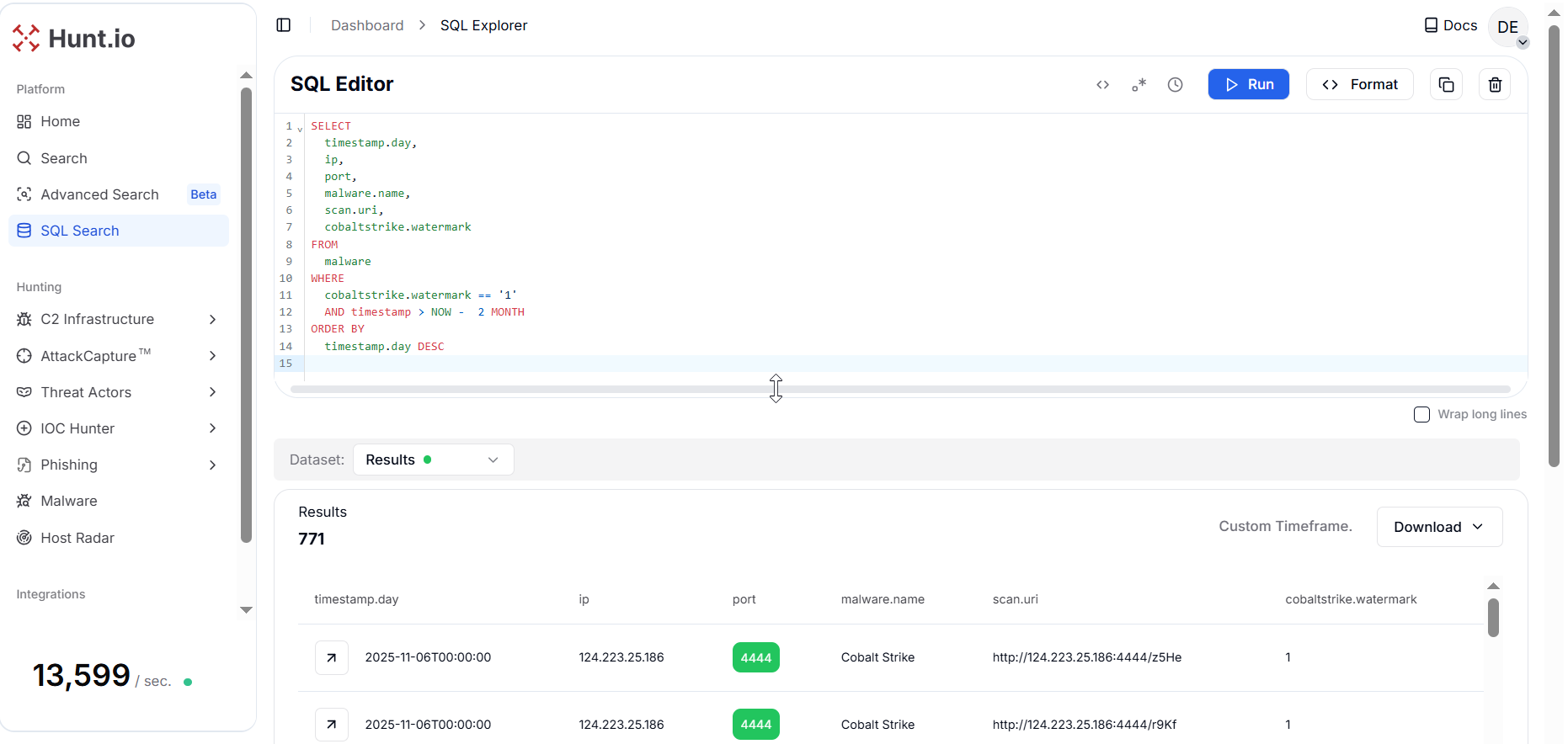 Figure 4. Recent sightings for watermark = 1 cluster and confirm live C2 servers by IP, port, and URI paths
Figure 4. Recent sightings for watermark = 1 cluster and confirm live C2 servers by IP, port, and URI pathsOne example in the results reveals multiple beacon endpoints hosted on the same IP address (124.223.25[.]186) over port 4444, each exposing different URI paths such as /JiWR, /tD6n, and /GbAr. This repetition across URIs and timestamps indicates that the same C2 server is actively serving multiple beacons, a strong sign of an operational and persistent Cobalt Strike setup.
Our IP Enrichment for 124.223.25[.]186 shows it belongs to Shenzhen Tencent Computer Systems Company Limited (AS45090) in Shanghai, China, and is flagged as high risk due to active Cobalt Strike activity.
The open port analysis shows multiple exposed services: SSH (22), HTTP (80) running Apache on Ubuntu, and notably ports 4444 and 50050, both associated with Cobalt Strike communications observed as recently as November 6, 2025.
![Figure 5. Hunt.io enrichment for 124.223.25[.]186 showing ASN, location, and active Cobalt Strike ports](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/11-2025/The+Complete+Guide+to+Hunting+Cobalt+Strike+-+Part+2+10%2B+HuntSQL+Recipes+for+Detecting+Cobalt+Strike+Infrastructure+-+figure+5.png) Figure 5. Hunt.io enrichment for 124.223.25[.]186 showing ASN, location, and active Cobalt Strike ports.
Figure 5. Hunt.io enrichment for 124.223.25[.]186 showing ASN, location, and active Cobalt Strike ports.For threat hunters, fields like IP and port pair assist in identifying the live command-and-control server, while URI paths can reveal beacon distribution patterns or automated tasking endpoints. The watermark itself is essential for clustering, as it allows correlation of multiple infrastructures operated by actors relying on the same cracked Cobalt Strike build.
3. Cobalt Strike Ports Distribution
This query aggregates the most frequently observed ports used by Cobalt Strike samples where the associated domain field is not empty. The goal is to identify which network ports are most commonly leveraged for beacon communications across different infrastructures.
SELECT
cobaltstrike.port,
count(*) AS Total
FROM
malware
WHERE
cobaltstrike.domains !=''
GROUP BY
cobaltstrike.port
ORDER BY
Total DESC
CopyOutput example:
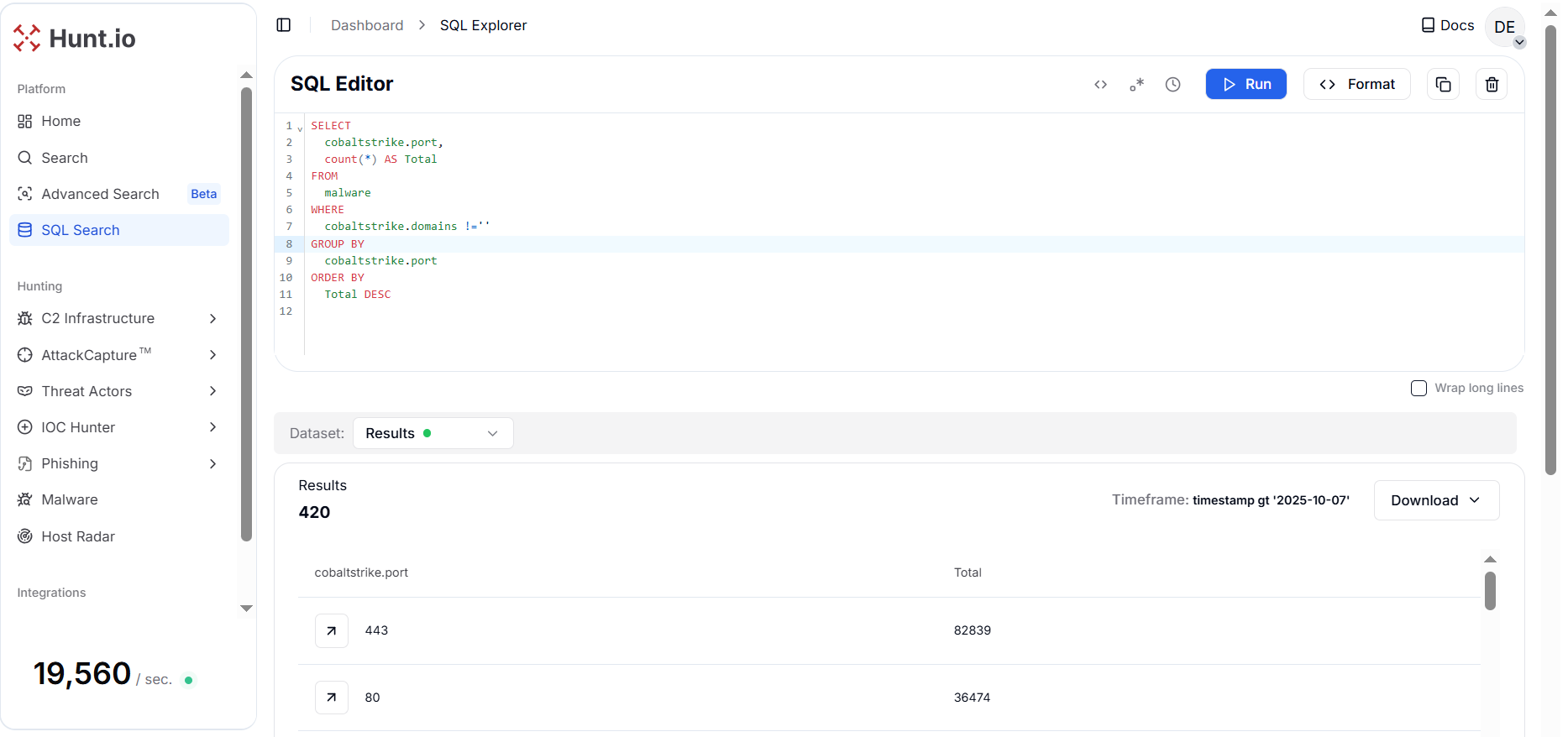 Figure 6. Common ports used by Cobalt Strike beacons that show how operators hide C2 on standard web ports to blend with normal traffic.
Figure 6. Common ports used by Cobalt Strike beacons that show how operators hide C2 on standard web ports to blend with normal traffic.The results highlight port 443 as the dominant channel (82,839 occurrences), followed by port 80, 8443, 8080, and 18443.
Practically speaking, this query emphasizes the importance of monitoring beacon communication over common web ports. Since Cobalt Strike frequently mimics regular HTTPS activity, defenders should look for anomalous TLS certificates, irregular traffic patterns, or consistent beacon intervals on these ports.
4. Identifying Cobalt Strike Clusters by Watermark and Public Key
This query focuses on grouping Cobalt Strike samples based on their watermark (license ID) and public key (unique beacon configuration hash). The purpose is to identify clusters of Cobalt Strike beacons that share the same configuration traits, which often indicate shared infrastructure or the same operator group.
SELECT
cobaltstrike.watermark,
cobaltstrike.public_key,
count(*) AS total
FROM
malware
WHERE
cobaltstrike.public_key !=''
GROUP BY
cobaltstrike.watermark,
cobaltstrike.public_key
ORDER BY
total DESC
CopyOutput example:
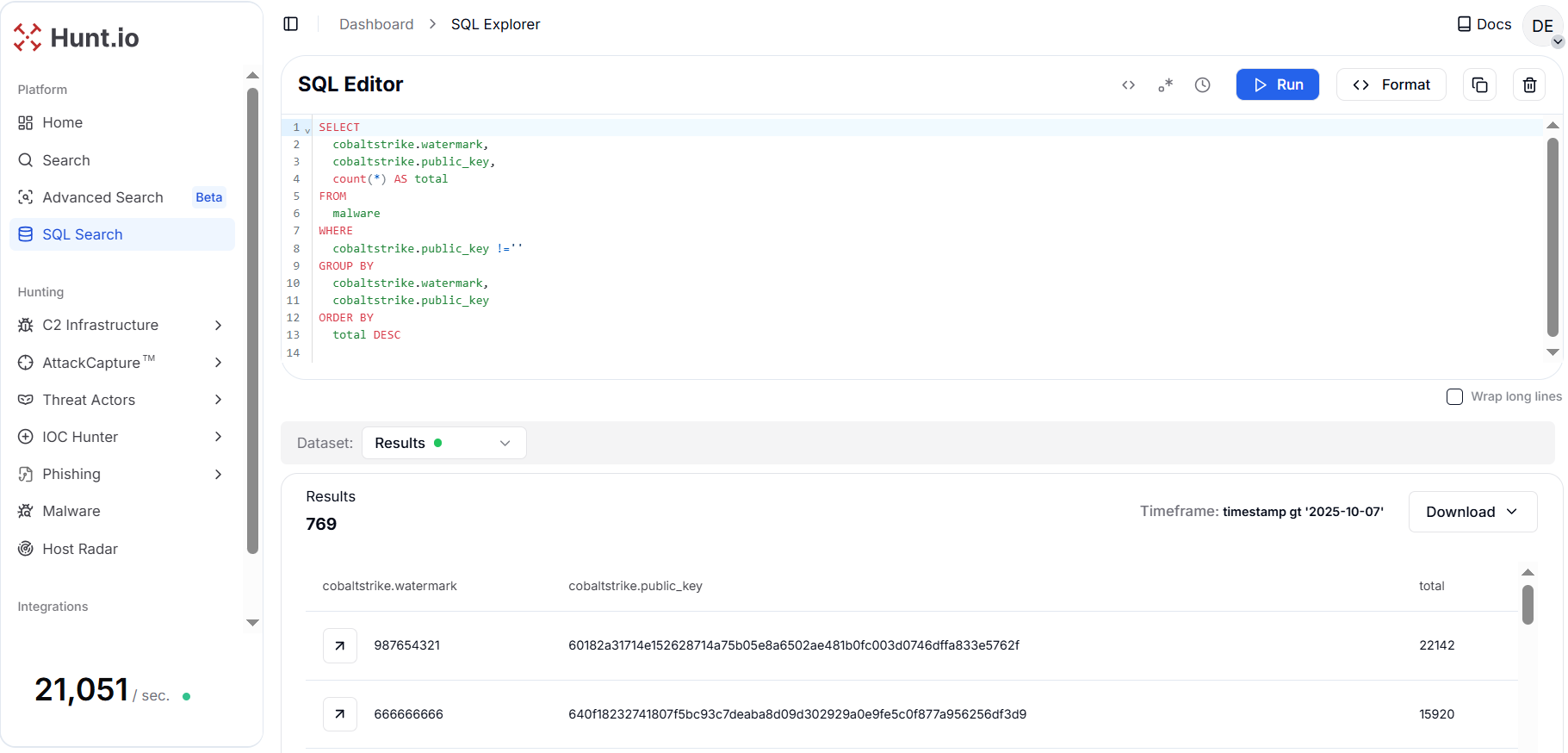 Figure 7. The combination of Watermark and public_key frequency provides a deterministic fingerprint for campaign clustering and cross-sighting.
Figure 7. The combination of Watermark and public_key frequency provides a deterministic fingerprint for campaign clustering and cross-sighting.The results reveal several recurring watermarks, such as 987654321 and 666666666, associated with multiple distinct public keys. The watermark 987654321 dominates with thousands of occurrences across multiple keys, suggesting that it may represent a widely reused cracked or pirated version of Cobalt Strike used by different threat actors.
For a threat hunter, the fields cobaltstrike.watermark and cobaltstrike.public_key are crucial pivots. The watermark can help attribute samples to known actor clusters or campaigns since some APTs and ransomware groups consistently reuse the same watermark.
For example, we performed a focused hunt starting from the Cobalt Strike watermark 1473793097, shared on the X platform by researcher @banthisguy9349. The HuntSQL™ query is designed to target this specific watermark, exclude empty hostnames, and display unique IP and hostname pairs:
SELECT
ip,
hostname
FROM
malware
WHERE
cobaltstrike.watermark = '1473793097'
AND hostname != ''
AND timestamp gt '2025-01-01'
GROUP BY
ip,
hostname
CopyOutput example:
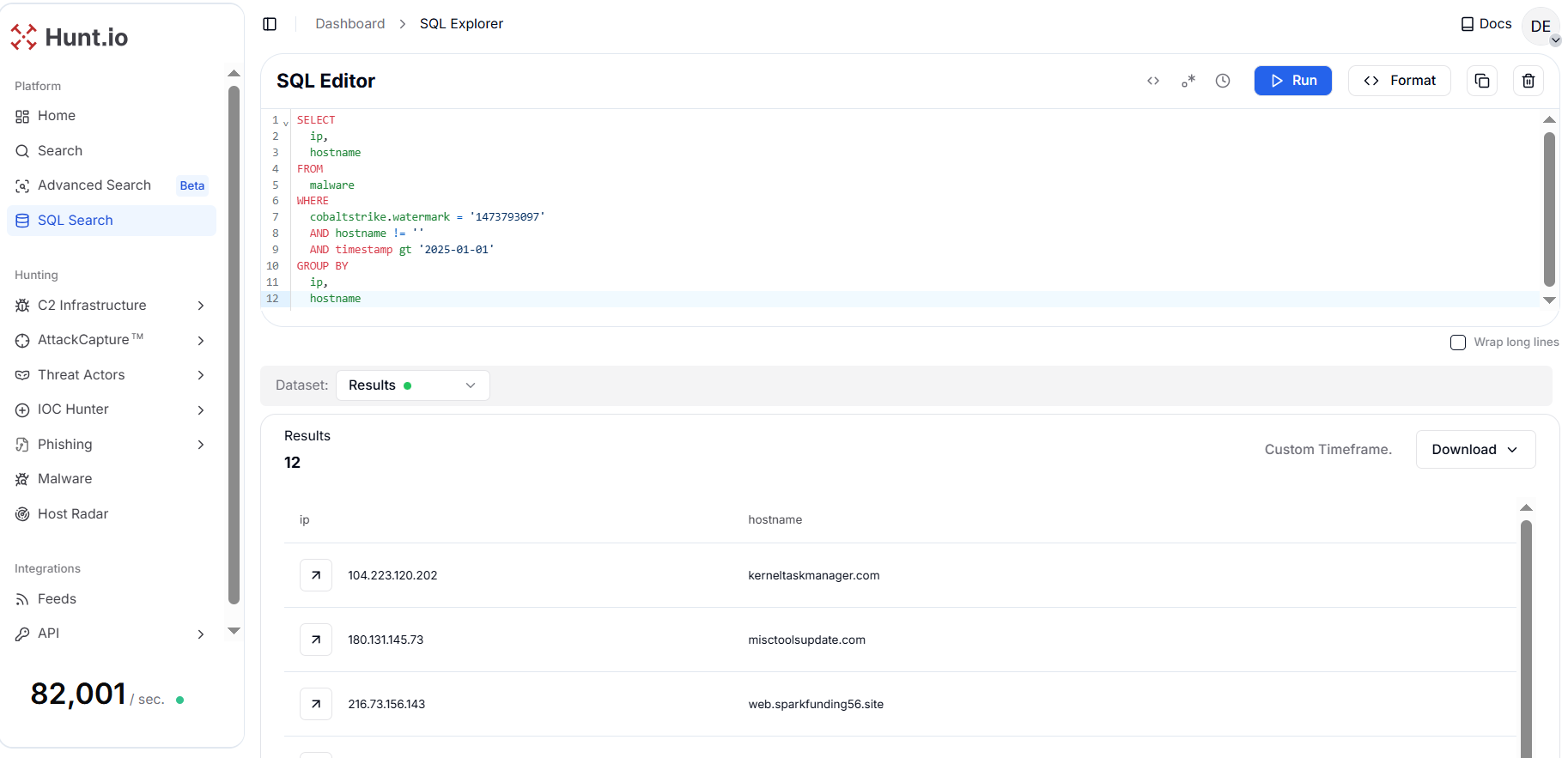 Figure 8. Pivot from a public watermark '1473793097' to discover 12 unique IP and domain pair that shows a compact example of open-source IOC validation.
Figure 8. Pivot from a public watermark '1473793097' to discover 12 unique IP and domain pair that shows a compact example of open-source IOC validation.The query returned 12 clustered IPs and hostnames, indicating potential C2 infrastructure related to Cobalt Strike watermark 1473793097. The results then inform containment strategies and detection rules focused on watermark, public_key, and rapidly changing hostnames.
5. Cobalt Strike Beacons Masquerading as WordPress Traffic
This query isolates Cobalt Strike servers that mimic legitimate WordPress infrastructure while using common browser-like user agents. By filtering for submit_uri patterns beginning with /wp% and user_agent strings containing "Mozilla," the query highlights beacon servers that disguise C2 communications as normal web traffic.
The inclusion of IP, port, malware.name, version, and user_agent fields allow analysts to directly observe version distribution and behavioral patterns across active Cobalt Strike instances.
SELECT
ip,
port,
malware.name,
version,
cobaltstrike.user_agent
FROM
malware
WHERE
cobaltstrike.submit_uri LIKE '/wp%'
AND cobaltstrike.user_agent LIKE '%Mozilla%'
AND timestamp gt '2025-01-01'
GROUP BY
ip,
port,
malware.name,
version,
cobaltstrike.user_agent
CopyOutput example:
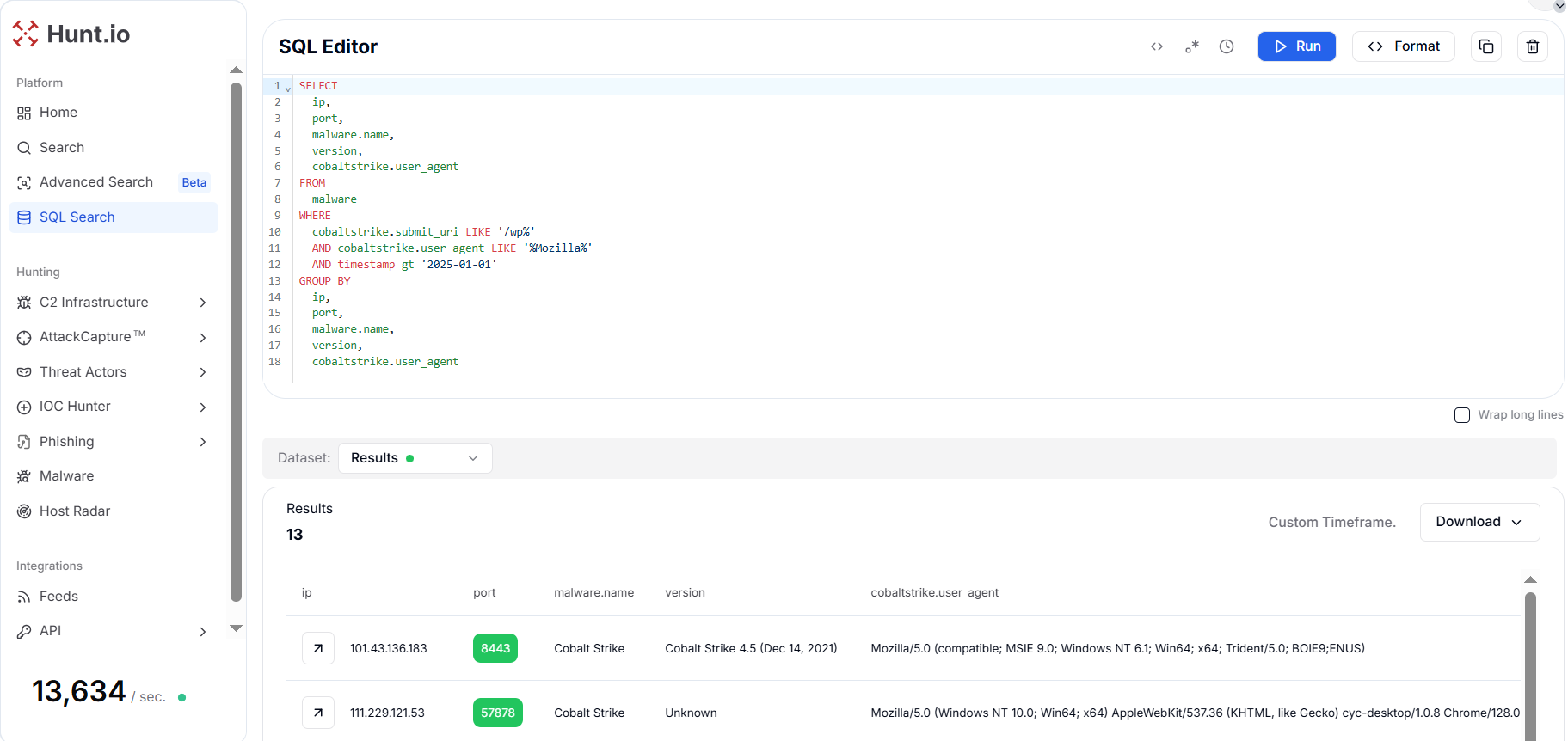 Figure 9. The WordPress-like submit URIs and browser UA operators use CMS paths to camouflage beacon callbacks.
Figure 9. The WordPress-like submit URIs and browser UA operators use CMS paths to camouflage beacon callbacks.The results reveal multiple Cobalt Strike versions (notably 4.5 and 4.9) operating on ports 443, 8443, 2087, and 50051 often associated with HTTPS or API communication. Many of these IPs consistently employ WordPress-like paths (e.g., /wp-admin/, /wp-content/) and spoofed Mozilla/5.0 user agents to blend with normal traffic, a known Cobalt Strike evasion tactic.
The user agent and URI patterns here make it easy to spot beacons trying to pass as WordPress or browser traffic. Additionally, the version field helps assess the operational maturity of the adversary by indicating which Cobalt Strike build is in use. Finally, submit_uri patterns such as /wp-admin/ or /wp-content/ provide meaningful pivots into web server logs, phishing repositories, or URL intelligence feeds.
Some operators reuse well-documented tricks, and one of the clearest examples was flagged in Palo Alto's reporting.
This query focuses on known operational patterns shared by Palo Alto Networks, where threat actors used the user agent Microsoft-CryptoAPI/6.1 combined with a submit URI containing "oscp" to disguise Cobalt Strike beacon activity as certificate revocation checks. These artifacts indicate an actor's attempt to blend C2 callbacks into normal Windows CryptoAPI behavior.
SELECT
ip
FROM
malware
WHERE
cobaltstrike.user_agent = 'Microsoft-CryptoAPI/6.1'
AND cobaltstrike.submit_uri LIKE '%oscp%'
AND timestamp gt '2025-01-01'
GROUP BY
ip
CopyOutput example:
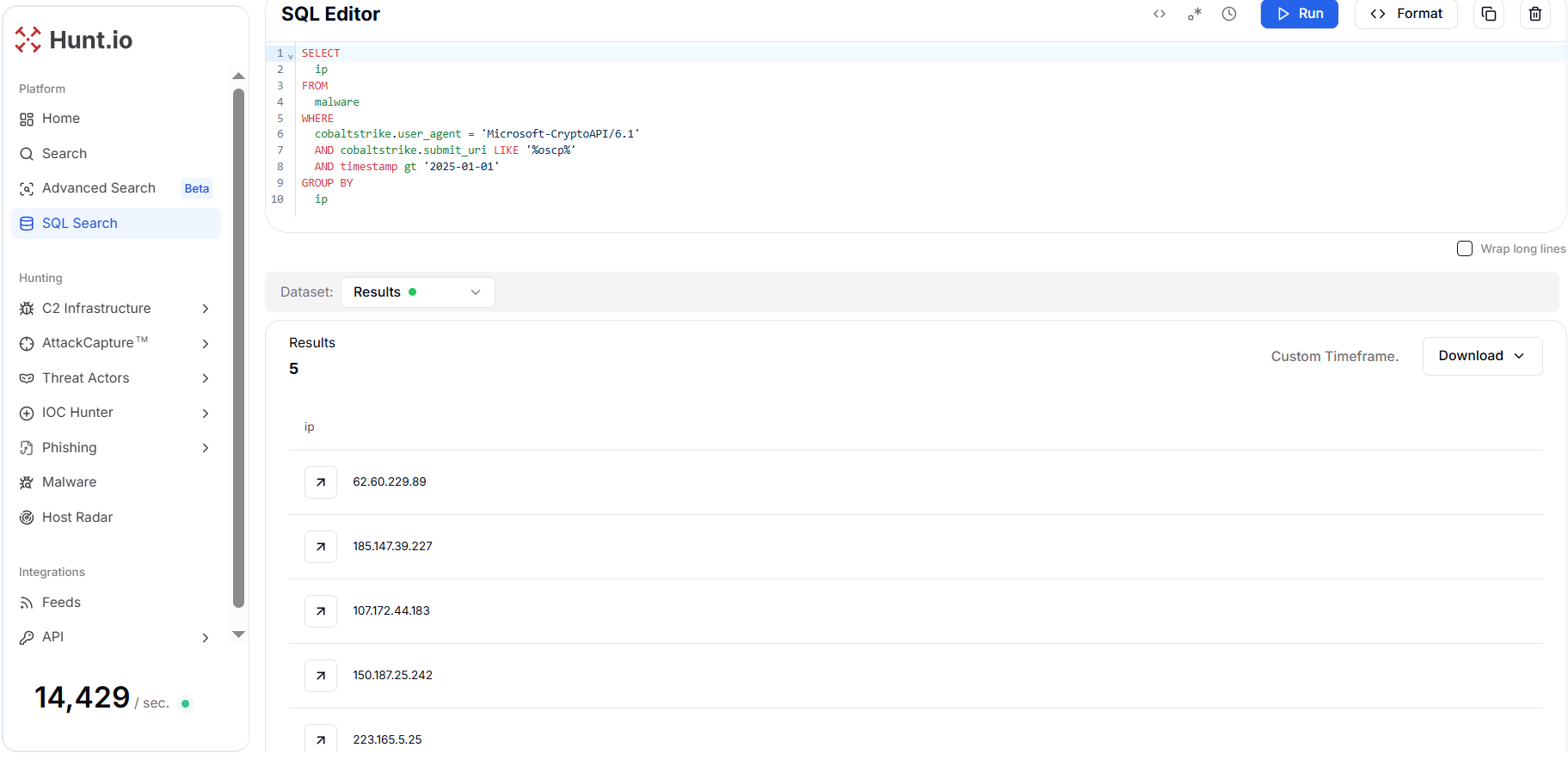 Figure 10. A pivot on 'Microsoft-CryptoAPI/6.1' User Agent with URI OSCP-style deception shows 5 unique IP Addresses as targeted detection pivot.
Figure 10. A pivot on 'Microsoft-CryptoAPI/6.1' User Agent with URI OSCP-style deception shows 5 unique IP Addresses as targeted detection pivot.The query results show five unique IP addresses associated with this behavior, indicating that multiple servers are reusing this same deception pattern across different infrastructure segments. These IPs likely belong to the same or related campaigns leveraging identical Cobalt Strike configurations for operational consistency.
6. Discover Callback Endpoints Using Action Verbs (login|post|submit)
This query hunts for Cobalt Strike submit URIs that contain common action verbs such as login, post, or submit, which adversaries often use to blend C2 callbacks with normal web application traffic.
SELECT
cobaltstrike.domains,
cobaltstrike.port,
cobaltstrike.submit_uri
FROM
malware
WHERE
cobaltstrike.submit_uri RLIKE '(login|post|submit)'
GROUP BY
cobaltstrike.domains,
cobaltstrike.port,
cobaltstrike.submit_uri
CopyOutput example:
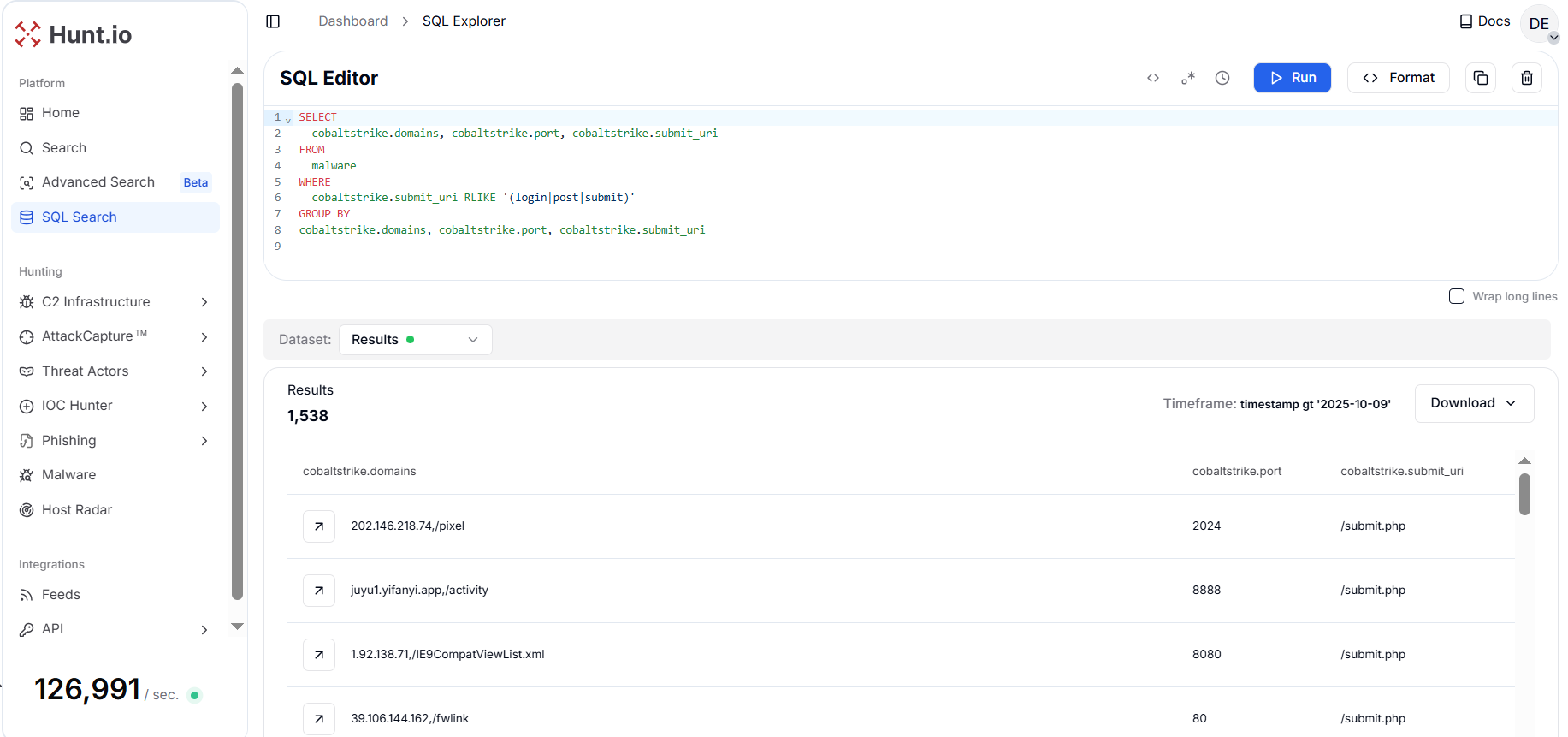 Figure 11. Search for action-verb URIs with high-yield heuristics to find beacons hiding as web app form endpoints.
Figure 11. Search for action-verb URIs with high-yield heuristics to find beacons hiding as web app form endpoints.The results show many distinct domain and path combinations that indicate a broad use of application-style endpoints across diverse hosters and ports, consistent with operator efforts to hide beacon traffic inside expected HTTP actions.
The submit, post, and login URIs are high-value heuristics for hunters because they mimic legitimate application behavior while serving as convenient upload/download points for beacons.
The key fields to pivot are cobaltstrike.domains (use passive DNS and domain history to find sibling hosts and registration patterns), cobaltstrike.port (check network flows and firewall logs for unusual traffic on nonstandard ports such as 9966, 2024, or 8888), and cobaltstrike.submit_uri (fetch the endpoint or review proxy captures for base64 payloads, form fields, or header stanzas that reveal beacon formats).
7. Detecting Cobalt Strike Beacons That Spawn into dllhost.exe
This query finds Cobalt Strike configurations where cobaltstrike.spawn_to_x64 references dllhost, flagging beacons that will inject into the legitimate Windows COM surrogate process.
SELECT
*
FROM
malware
WHERE
cobaltstrike.spawn_to_x64 LIKE '%dllhost%'
CopyOutput example:
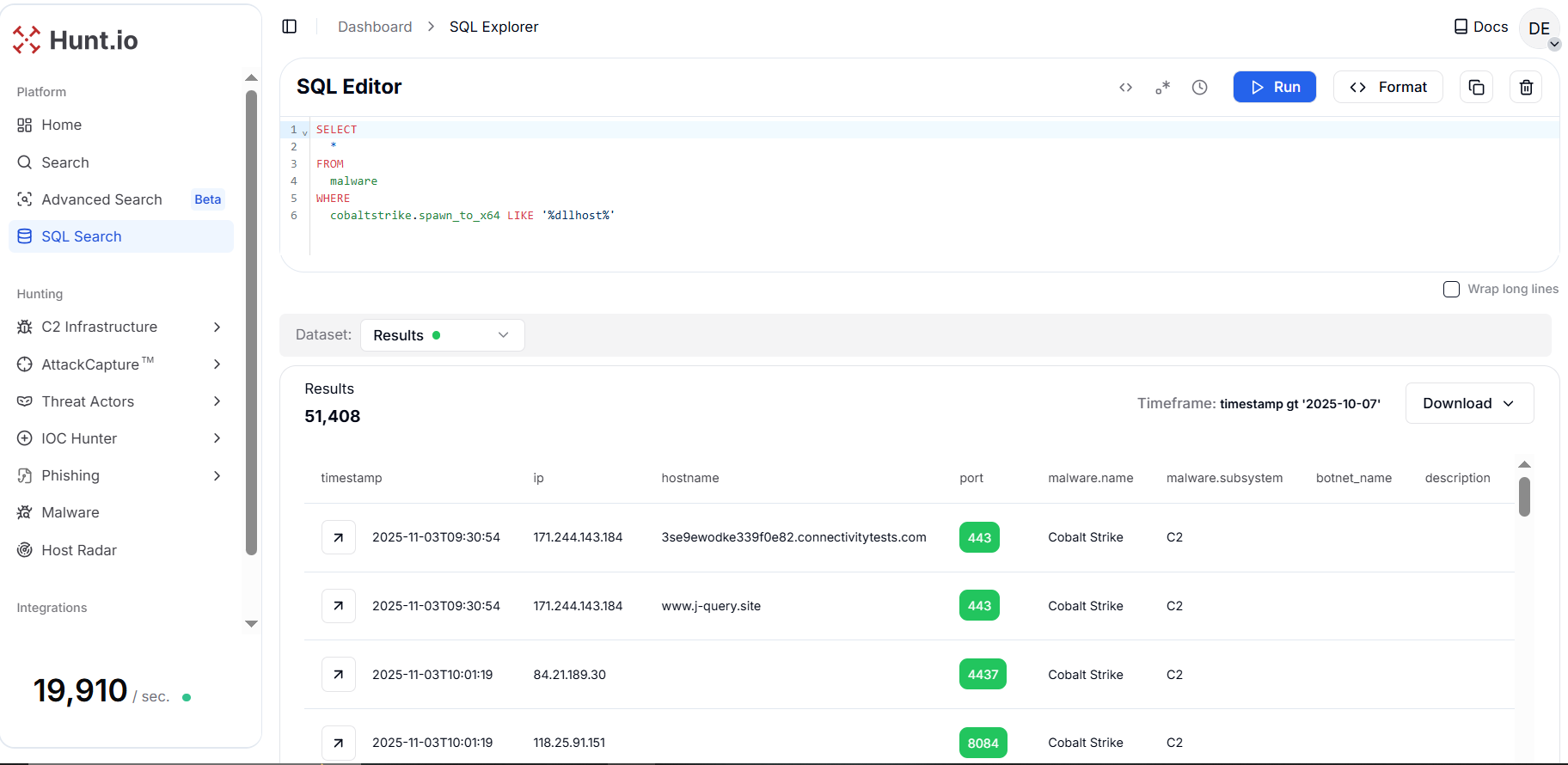 Figure 12. The dllhost.exe spawn target with a host-level artifact that converts network leads into high-confidence compromises.
Figure 12. The dllhost.exe spawn target with a host-level artifact that converts network leads into high-confidence compromises.With 51,408 hits since the query timeframe, the pattern is widespread and often paired with web-like submit URIs and common web ports, indicating operators are using dllhost.exe to hide execution while C2 traffic blends into normal HTTP/S flows.
From a threat hunting perspective, the query's results open multiple pivot points. Hunters can start by searching EDR or process creation telemetry for instances of dllhost.exe spawned by unusual parents or containing injected memory regions.
Moreover, cross-referencing the IP or Port and submit_uri values within proxy or network flow logs can help reconstruct the full C2 session, including beacon registration and tasking behavior. Similarly, cobaltstrike.submit_uri and cobaltstrike.domains highlight the callback paths used by the beacon to fetch payloads or communicate with the server, helping analysts identify network-based detection opportunities.
8. Beacon timing statistics (average and maximum sleeptime)
This query summarizes beacon callback intervals by reporting the average and maximum values of cobaltstrike.sleeptime across the malware dataset.
SELECT
avg(cobaltstrike.sleeptime),
max(cobaltstrike.sleeptime)
FROM
malware
CopyOutput example:
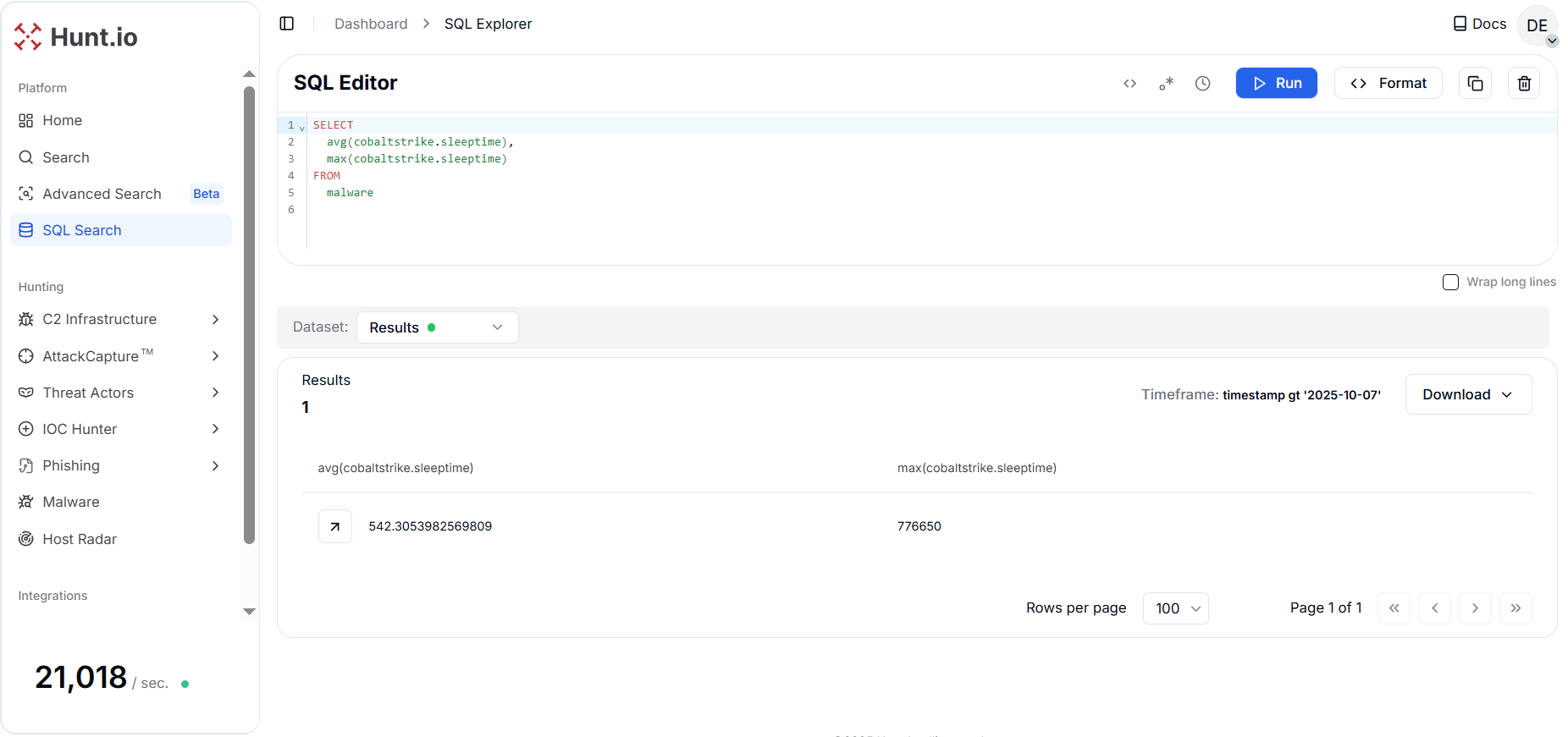 Figure 13. Beacon cadence overview, separating noisy, test, and stealthy implants by timing distribution across the whole malware dataset.
Figure 13. Beacon cadence overview, separating noisy, test, and stealthy implants by timing distribution across the whole malware dataset.The results (average ≈ 551 ms, max ≈ 776,650 ms) indicate a very wide distribution of configured sleep times from sub-second noisy beacons to long-interval, stealthy implants. For hunting purposes, the analyst can track the different Cobalt Strike beacon averages among a lot of hunted records.
9. ASN country distribution of Cobalt Strike servers using browser-like User-Agents
This query analyzes the geographical distribution of Cobalt Strike command-and-control (C2) servers that disguise their traffic with browser-style User-Agent strings containing Mozilla, Edge, or Chrome.
SELECT
asn.country_code,
count(*) AS total
FROM
malware
WHERE
cobaltstrike.user_agent RLIKE '(Mozilla|Edge|Chrome)'
GROUP BY
asn.country_code
ORDER BY
total DESC
CopyOutput example:
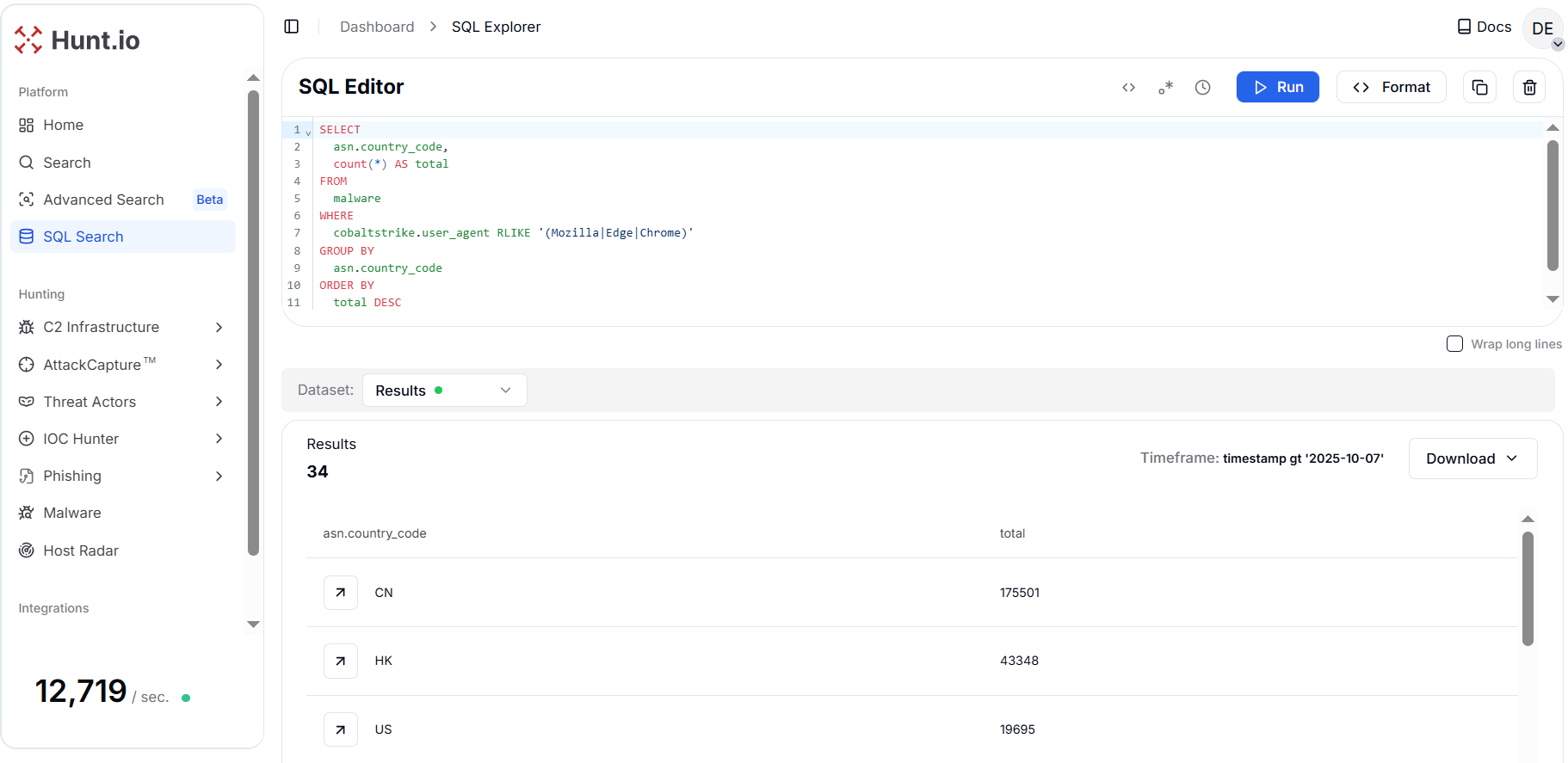 Figure 14. Geographic ASN view for browser-like beacons reveals hosting clusters and provider abuse trends.
Figure 14. Geographic ASN view for browser-like beacons reveals hosting clusters and provider abuse trends.The results show a strong concentration in China (CN) with 175,501 detections, followed by Hong Kong (HK), the United States (US), and Singapore (SG) regions frequently observed in both commercial VPS hosting and bulletproof infrastructure used by threat actors.
Adversaries often spoof legitimate browser agents to blend C2 traffic with normal web browsing. By correlating such fake agents with ASN country data, hunters can differentiate benign user traffic from C2 activity and identify hosting clusters that repeatedly appear in operations.
10. Watermark frequency and spread (campaign-scale indicator)
This query counts occurrences per cobaltstrike.watermark and reports how many unique IPs each watermark appears on, surfacing which license IDs or embedded markers are most widespread.
SELECT
cobaltstrike.watermark,
count(*) AS occurrences,
uniq(ip) AS ips
FROM
malware
WHERE
cobaltstrike.watermark >= 0
GROUP BY
cobaltstrike.watermark
ORDER BY
occurrences DESC
CopyOutput example:
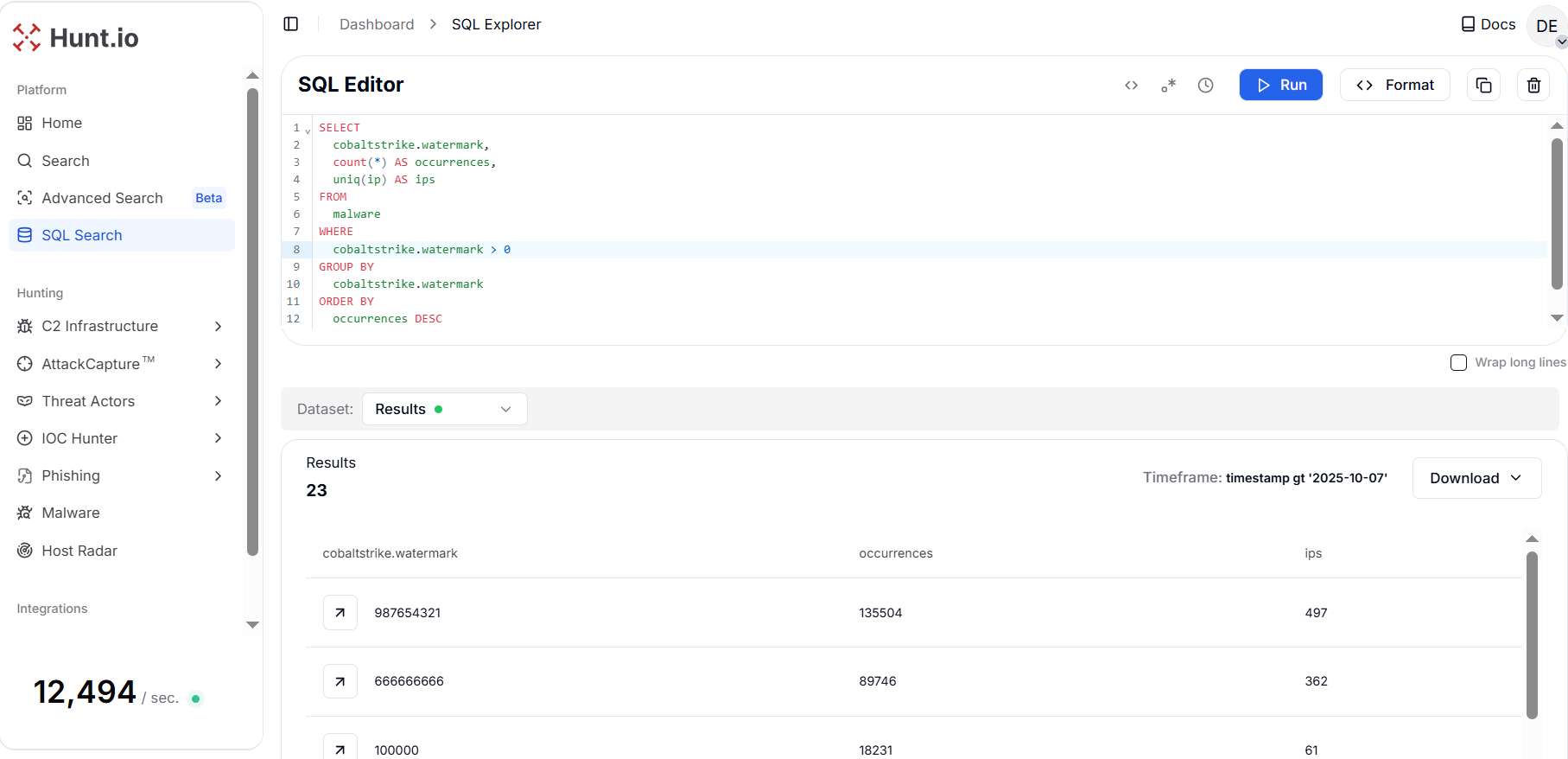 Figure 15. Watermark prevalence and unique IP spread use high-frequency watermarks to prioritize campaign hunts.
Figure 15. Watermark prevalence and unique IP spread use high-frequency watermarks to prioritize campaign hunts.The results show a massive spike at two prominent nonzero watermarks: 987654321 (135,504 occurrences / 497 IPs) and 666666666 (89,746 occurrences / 362 IPs).
For threat hunters, the watermark values are excellent campaign-level anchors. They can track unique IPs with watermark values in the malware dataset to hunt further Cobalt Strike IPs and narrow down their pivots.
11. Low sleep interval beacons (aggressive callback detection)
This query filters all Cobalt Strike entries where the sleeptime value is greater than 0 but less than 3000 milliseconds, sorting results in ascending order to surface the fastest-calling beacons first.
SELECT
ip,
cobaltstrike.sleeptime,
cobaltstrike.jitter,
timestamp
FROM
malware
WHERE
cobaltstrike.sleeptime > 0
AND cobaltstrike.sleeptime < 3000
ORDER BY
cobaltstrike.sleeptime ASC
LIMIT
200
CopyOutput example:
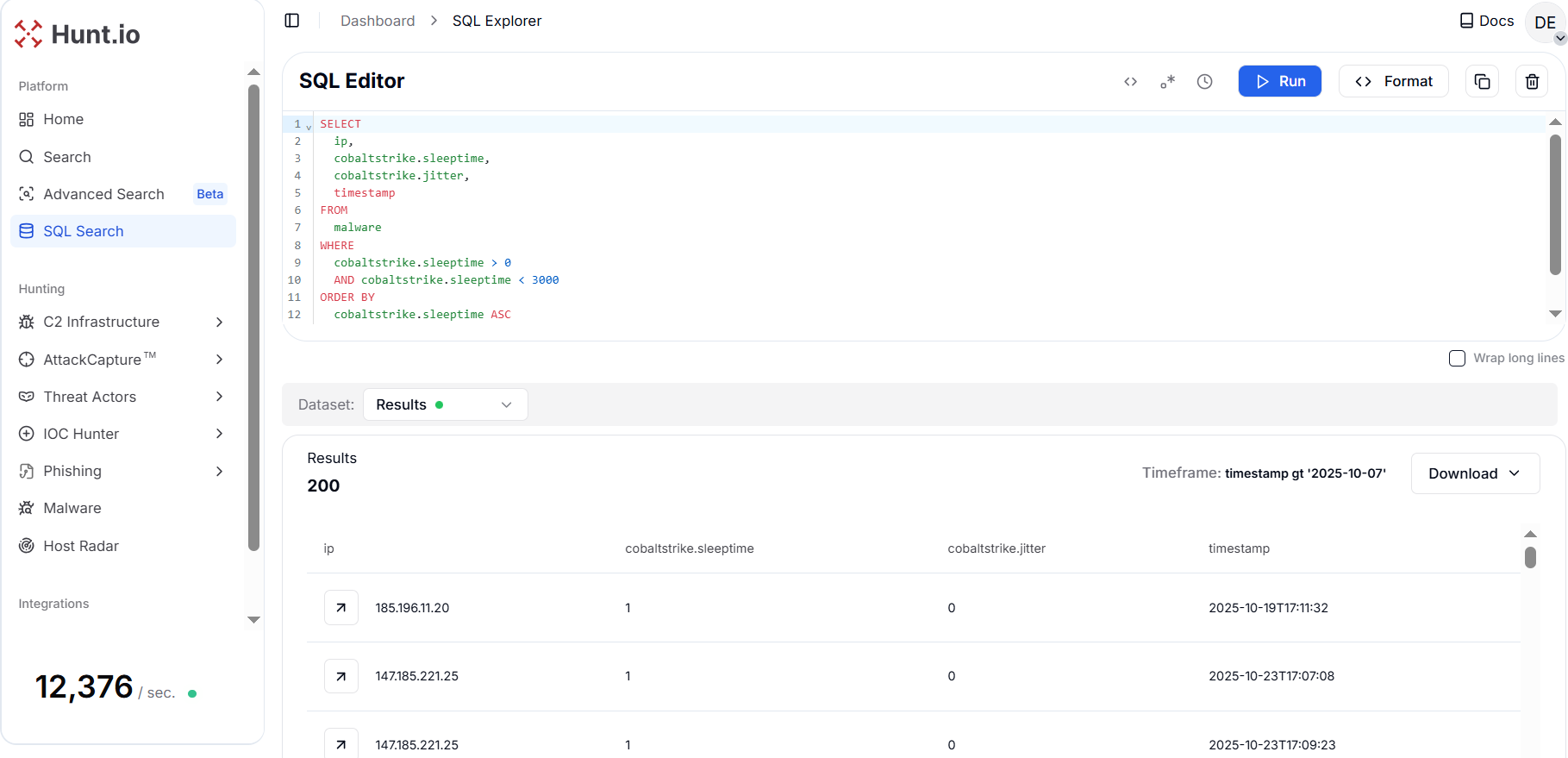 Figure 16. Very low sleep time beacons likely test or live operator sessions and are high-value for capture.
Figure 16. Very low sleep time beacons likely test or live operator sessions and are high-value for capture.The output reveals beacon configurations with extremely short intervals, as low as 1 millisecond and zero jitter, such as IPs 185.196.11[.]20 and 147.185.221[.]25. These configurations represent highly aggressive communication patterns, often associated with testing setups, misconfigurations, or active operations requiring near-real-time tasking.
For threat hunters, this is a valuable behavioral marker in the way that extremely low sleeptime values indicate either live operator sessions or automated staging beacons running in "debug" or "low-latency" mode.
12. ASN-Level Distribution of Cobalt Strike Beacons
This query examines the hosting infrastructure behind Cobalt Strike activity by grouping all detected beacons according to their Autonomous System Name (ASN). By aggregating based on asn.name, it highlights which network providers or hosting services are most frequently associated with Cobalt Strike command-and-control servers.
SELECT
asn.name,
count(*) AS beacons,
uniq(ip)
FROM
malware
WHERE
cobaltstrike.public_key != ''
GROUP BY
asn.name
ORDER BY
beacons DESC
CopyOutput example:
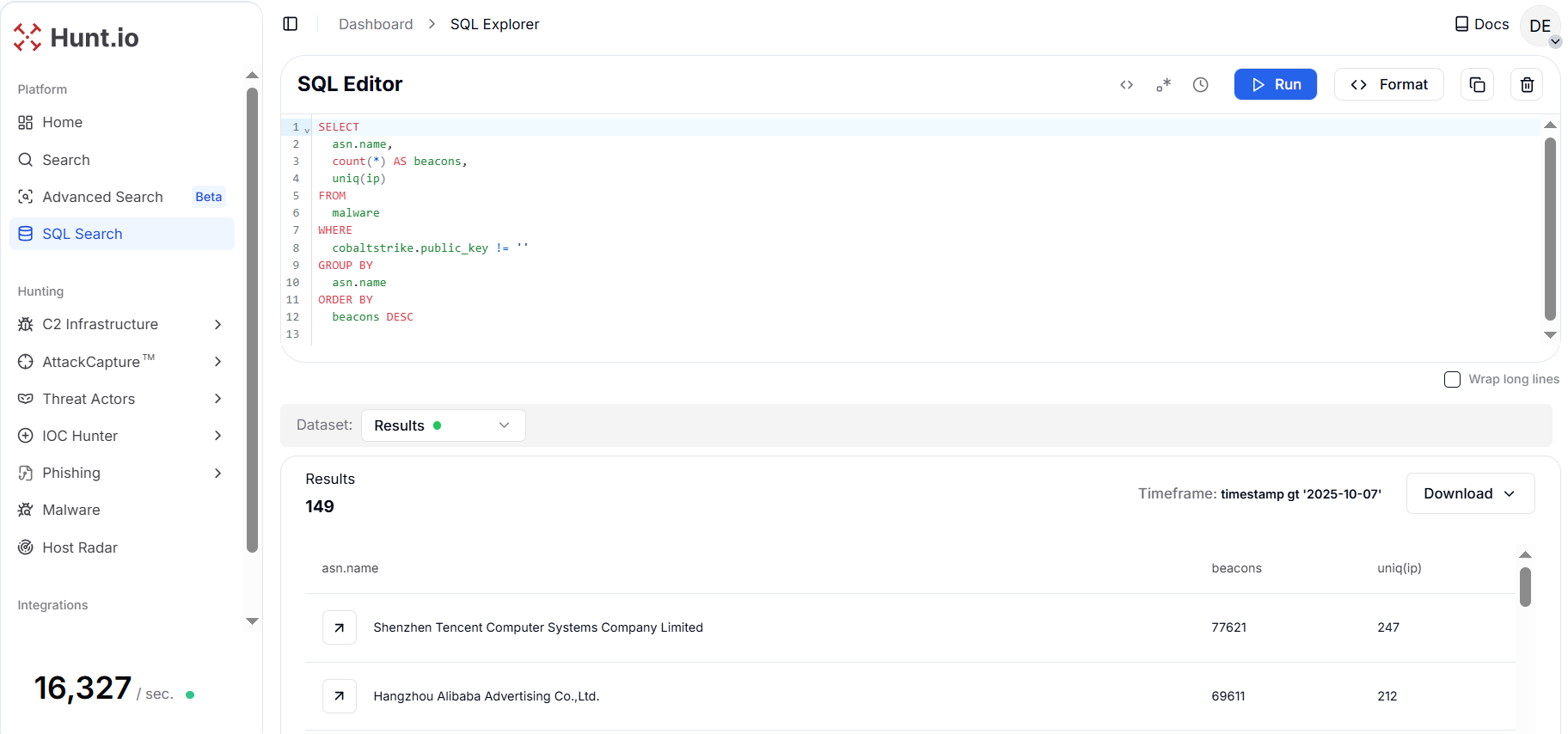 Figure 17. ASN aggregation for public_key-bearing beacons shows a strategic view for cloud provider-focused hunts that contains records per IP addresses and their unique count per hosting.
Figure 17. ASN aggregation for public_key-bearing beacons shows a strategic view for cloud provider-focused hunts that contains records per IP addresses and their unique count per hosting.The results show Shenzhen Tencent Computer Systems Company Limited leading with over 77,621 beacons across 247 unique IPs, followed by Hangzhou Alibaba Advertising Co., Ltd. with 67,000+ beacons and Tencent Building, Kejizhongyi Avenue with nearly 10,000 beacons.
For threat hunters, this view provides strategic intelligence into the infrastructure ecosystems supporting active or historical Cobalt Strike operations. For example, the clusters of activity within large Chinese cloud providers like Tencent and Alibaba indicate recurring use of these public hosting environments for staging and controlling beacon traffic.
Similarly, the repetitive detections from the same ASN can be escalated for cloud abuse reporting or regional threat intelligence sharing. Pivoting from these ASNs to related IP ranges, passive DNS entries, or TLS certificate reuse patterns can expose entire Cobalt Strike clusters operating under the same provider.
To show how these pivots come together in a real scenario, here's a profile-based hunt tied to a known Cobalt Strike configuration.
13. Tracking Cobalt Strike from the Lazarus Cobalt Strike Profile
In order to understand how a threat hunter crafts a HuntSQL™, we have picked up a Cobalt Strike profile from GitHub. The profile is linked with APT Lazarus, which has specified a 30,000 ms sleeptime, 20 ms jitter, Firefox 47 user-agent, WordPress-style and stager URIs (/view.jsp, psmon.dat, avgnt.dat), Nginx server headers, and a dllhost/imeklmg.exe spawn preference.
The HuntSQL™ query is designed with fields cobaltstrike.sleeptime, cobaltstrike.jitter, cobaltstrike.user_agent, cobaltstrike.submit_uri, cobaltstrike.domains, cobaltstrike.spawn_to_x64, cobaltstrike.procinj_transform_x64, and cobaltstrike.procinj_execute in the year 2024.
SELECT
ip, count(*) as total
FROM
malware
WHERE
timestamp BETWEEN '2024-01-01' AND '2024-12-31'
AND cobaltstrike.sleeptime = '30000'
AND cobaltstrike.jitter = '20'
AND cobaltstrike.user_agent = 'Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:47.0) Gecko/20100101 Firefox/47.0'
AND (
cobaltstrike.submit_uri LIKE '%psmon.dat%'
OR cobaltstrike.submit_uri LIKE '%avgnt.dat%'
OR cobaltstrike.domains LIKE '%/view.jsp%'
)
AND (
cobaltstrike.spawn_to_x64 LIKE '%imeklmg.exe%'
OR cobaltstrike.spawn_to_x86 LIKE '%imeklmg.exe%'
OR cobaltstrike.procinj_execute LIKE '%CreateRemoteThread%'
OR cobaltstrike.procinj_transform_x64 LIKE '%shorthand_or_marker%'
)
GROUP BY
ip
ORDER BY
total DESC
CopyOutput example:
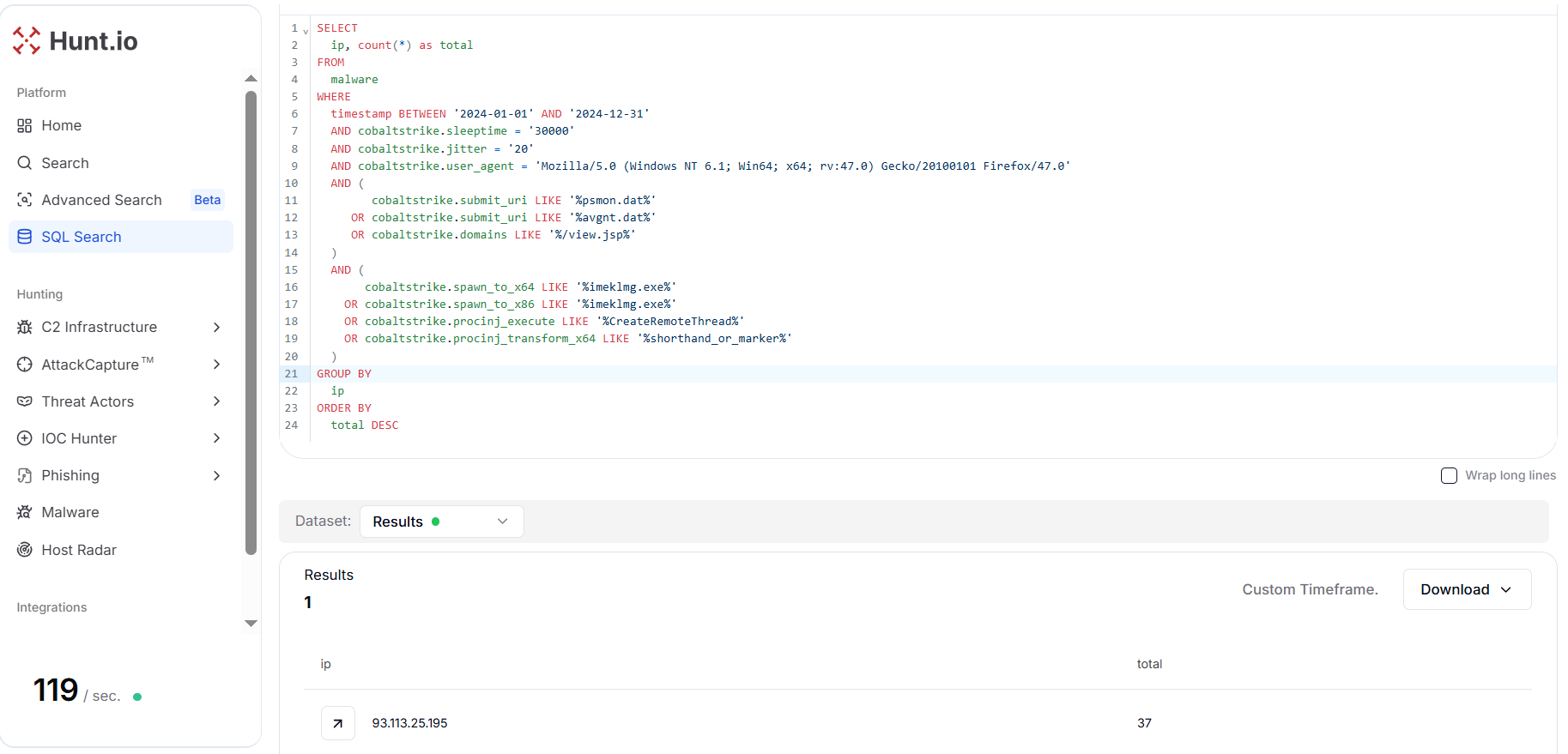 Figure 18. Profile-based hunt for Lazarus Group maps a Malleable C2 profile to an IP cluster and escalates with host and infrastructure pivot to disclose a server at 93.113.25.195 IP Address.
Figure 18. Profile-based hunt for Lazarus Group maps a Malleable C2 profile to an IP cluster and escalates with host and infrastructure pivot to disclose a server at 93.113.25.195 IP Address.The query returned a single, focused cluster: 93.113.25[.]195 with 37 matching sightings. This is a high-value lead because the profile's combination of timing, UA, submit URIs, and spawn targets is specific and tied to Lazarus-style tradecraft.
The host 93.113.25[.]195 resolves to AS214209 (Internet Magnate (Pty) Ltd), registered in Bucharest, Romania, and sits in the 93.113.25.0/24 block. Hunt.io flags the address as high risk with active Cobalt Strike activity and four associated domains, and it has been observed with an open TCP-wrapped service on port 443 as recently as 2025-11-07.
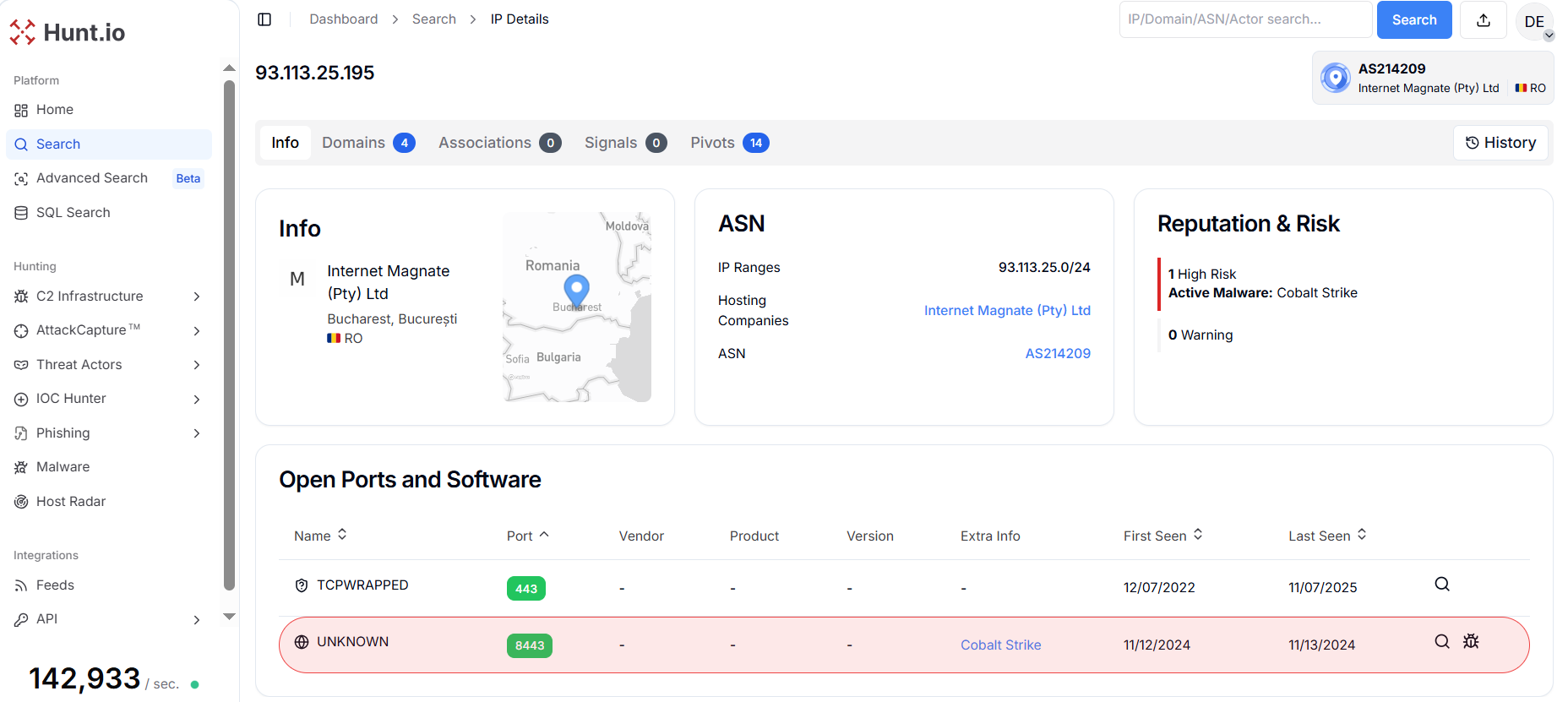 Figure 19. Hunt.io shows the IP Address "92.113.25.195" hosted over Internet Magnate (Pty) Ltd and has been linked with Cobalt Strike from 2024.
Figure 19. Hunt.io shows the IP Address "92.113.25.195" hosted over Internet Magnate (Pty) Ltd and has been linked with Cobalt Strike from 2024.The combination of a tight profile match (sleeptime/jitter/UA/submit_uri/spawn targets) and a high-risk ASN with multiple domain associations shifts the IP from a noisy hit to a prioritized investigative target.
These findings reinforce the need for a structured and consistent approach when working with Cobalt Strike telemetry. Even strong leads must be validated, enriched, and contextualized to avoid false confidence.
The next section outlines the best practices that support effective hunting, attribution, and detection.
Best Practices
Start wide before narrowing down: Running simple distribution queries, like the one that counts malware.name, gives you a quick sense of what's most active in the dataset and where Cobalt Strike fits in.
Lean on the strongest fingerprints first: Fields such as cobaltstrike.public_key and cobaltstrike.watermark usually give the cleanest pivots. They make it easy to see which servers belong together and which ones look like part of the same setup.
Use behavior to fill in the gaps: Tables like cobaltstrike.user_agent, cobaltstrike.sleeptime, and cobaltstrike.jitter help you spot beacons that try to blend in with normal traffic or follow odd timing patterns.
Check domains, ports, and paths to confirm activity: Combining cobaltstrike.domains, cobaltstrike.port, cobaltstrike.submit_uri, and scan.uri is a solid way to understand how a server is being used and whether its traffic matches typical Cobalt Strike behavior.
Connect network clues to execution clues: Fields like cobaltstrike.spawn_to_x64, spawn_to_x86, and the various procinj_* entries help you tie what you see in network data to how the beacon is meant to run on a host.
Once these practices are applied consistently, the patterns behind Cobalt Strike activity become predictable enough to summarize the key insights below.
Conclusion
HuntSQL™ turns raw scanner data into real hunting insight. With a few focused queries, it's possible to connect isolated Cobalt Strike detections, map beacon clusters, and uncover infrastructure that would otherwise stay hidden. These 10+ recipes are a starting point for analysts who want clear, data-backed pivots they can reuse and expand.
Part 2 focused on controlled, manual pivots. In Part 3, we'll explore how these exact workflows translate into automated clustering and detection inside Hunt.io.
If you want to see how this works in action, book a demo today and explore how Hunt.io helps you detect Cobalt Strike infrastructure automatically across the internet.
In Part 1, we showed how open directories and repeated certificates can reveal real Cobalt Strike infrastructure. In this second part, we're focusing on how to take those findings further with HuntSQL™.
Cobalt Strike continues to appear in campaigns run by APT groups, ransomware operators, and brokers who use it to maintain access and move across networks. With HuntSQL™, it's possible to search across datasets, connect beacon traits, and uncover related servers without adding noise.
Here we're sharing 10 practical HuntSQL™ recipes that help detect, group, and track Cobalt Strike infrastructure. Each one comes from real hunting scenarios, built to deliver clear and repeatable results.
Why Targeting Cobalt Strike Infrastructure Matters
Cobalt Strike is a commercial adversary-simulation framework originally built for red teams and penetration testers. At its core, it provides an interactive post-exploitation agent and a flexible command-and-control (C2) framework that supports command execution, file transfer, SOCKS proxying, credential harvesting, lateral movement, and customizable ("malleable") C2 profiles, effectively enabling an operator to emulate the full range of attacker post-exploit tactics.
According to the Insikt Group's "2024 Malicious Infrastructure Report", Cobalt Strike accounted for 65% of all command-and-control (C2) servers linked to offensive-security tools (OSTs). In the same report, across selected countries in Asia, Europe, and Africa, roughly 73% of all victims were attributed to infections involving AsyncRAT, QuasarRAT, and Cobalt Strike. According to Sophos' "Active Adversary Report" (1H 2024), Cobalt Strike was present in 13.68% of incident response cases, whereas the "2024 Global Threat Report" from Elastic indicates that off-the-shelf offensive tools like Cobalt Strike and Metasploit combined accounted for ≈ 54% of observed malware alerts.
So when you are able to consistently spot Cobalt Strike infrastructure, you are not just catching one framework. You are getting early visibility into a big portion of serious intrusions, from APT activity to ransomware operations. That is exactly the type of problem that benefits from structured, repeatable HuntSQL™ queries instead of one-off searches.
Enter HuntSQL™
At Hunt.io, our mission is to simplify your Cobalt Strike hunting. Using HuntSQL™, analysts can rapidly query, pivot, and correlate across multiple datasets, revealing Cobalt Strike fingerprints that might otherwise remain hidden.
Whether analyzing beacon metadata, SSL certificate reuse, or anomalous TLS handshakes, HuntSQL™ enables real-time threat infrastructure mapping without exposing sensitive environments to risk.
Let's now review the syntax and then walk through the recipes.
Syntax Overview
HuntSQL™ provides an enriched Malware Dataset, a compact, high-value inventory of scanner-observed command-and-control (C2) and malware infrastructure. It includes key attributes such as IP addresses, hostnames, ports, ASN, and organization information, scan provenance (including source, timestamp, and confidence), and classification tags.
For threat hunters, this dataset offers a unified view of malicious infrastructure that supports fast correlation, campaign clustering, and prioritization of active threats.
 Figure 1. The malware dataset provides detailed fields related to 7 categories, including Generic fields, ASN, Cobalt Strike, Malware name, organization details, scan methods, and timestamp fields.
Figure 1. The malware dataset provides detailed fields related to 7 categories, including Generic fields, ASN, Cobalt Strike, Malware name, organization details, scan methods, and timestamp fields.Among the malware dataset, and for this scenario, the most valuable components are the Cobalt Strike fields, which provide a detailed fingerprinting model for detecting and investigating beacons.
The cobaltstrike.* fields capture both deterministic artifacts like the SHA256 public key and watermark or license ID, and behavioral traits such as domains, submit URIs, user-agent strings, sleeptime, jitter, and process injection targets.
These attributes are particularly valuable for identifying unique beacon configurations, correlating related servers, and mapping malicious infrastructure reuse across campaigns.
 Figure 2. Hunt.io enriched Cobalt Strike fields within the Malware Dataset, which gives valuable information to pivot further to servers.
Figure 2. Hunt.io enriched Cobalt Strike fields within the Malware Dataset, which gives valuable information to pivot further to servers.Now that the structure of the dataset is clear, here's how its Cobalt Strike fields actually support the hunt:
Cluster and Attribute Infrastructure: Fields like cobaltstrike.public_key and cobaltstrike.watermark act as campaign-level fingerprints that allow hunters to connect infrastructure across time and intelligence sources.
Detecting Operational Behavior: Parameters such as cobaltstrike.sleeptime, cobaltstrike.jitter, and cobaltstrike.user_agent help identify beaconing activity and highlight potentially compromised systems in network telemetry.
Correlate Process Activity: Fields including cobaltstrike.spawn_to_x64, cobaltstrike.spawn_to_x86, and cobaltstrike.procinj_* link network evidence to endpoint processes, helping analysts validate execution behaviors or injection attempts.
These elements make the Hunt.io Malware Dataset a powerful resource for structured hunting. It enables analysts to pivot from network to endpoint, combine static and behavioral indicators, and perform accurate attribution, ultimately supporting faster detection and more effective response against Cobalt Strike-related threats.
With the dataset and fingerprints laid out, the next step is applying them in real hunts.
10+ ways to detect Cobalt Strike with HuntSQL™
The following section presents a collection of Cobalt Strike hunting recipes designed to transform Hunt.io's malware dataset into actionable intelligence. Each query demonstrates a practical method to identify, cluster, or attribute Cobalt Strike activity using enriched telemetry fields.
For a threat hunter or threat intel analyst, these "recipes" serve not only as detection patterns but also as analytical starting points, enabling deeper pivoting across infrastructure, behavioral, and cryptographic indicators to trace active beacon networks and their operators.
1. Identifying Prevalent Malware Frameworks in the Dataset
The first query aggregates all entries by malware.name to highlight the most frequently detected malware or offensive frameworks in the malware dataset.
SELECT
malware.name,
count(*) AS total
FROM
malware
GROUP BY
malware.name
ORDER BY
total DESC
CopyOutput example:
 Figure 3. Distribution of detected malware families to prioritize hunt targets and separate benign tooling from adversary frameworks.
Figure 3. Distribution of detected malware families to prioritize hunt targets and separate benign tooling from adversary frameworks.The results reveal a landscape dominated by well-known tools and scanners such as reNgine, Tactical RMM, and Keitaro, while also showing significant representation from command-and-control frameworks, including Cobalt Strike (372,082 detections) and Cobalt Strike Unverified (78,693 detections).
This distribution provides an early indication of which tools are most active across observed infrastructures, helping analysts distinguish between legitimate red-team utilities and adversarial C2 frameworks.
From a threat hunting perspective, this query acts as a baseline reconnaissance step. It establishes visibility into the relative footprint of known malware families, allowing hunters to prioritize their investigations around high-impact frameworks like Cobalt Strike, Metasploit, and Pyramid C2.
2. Identifying Active Cobalt Strike Beacons Using Watermarks
This query focuses on isolating recent Cobalt Strike beacon activity by filtering records where the field cobaltstrike.watermark equals 1, a well-known default value found in cracked or pirated versions of the tool often used by threat actors. By limiting the timeframe to the last two months, the query highlights currently active infrastructures.
SELECT
timestamp.day,
ip,
port,
malware.name,
scan.uri,
cobaltstrike.watermark
FROM
malware
WHERE
cobaltstrike.watermark == '1'
AND timestamp > NOW - 2 MONTH
ORDER BY
timestamp.day DESC
CopyOutput example:
 Figure 4. Recent sightings for watermark = 1 cluster and confirm live C2 servers by IP, port, and URI paths
Figure 4. Recent sightings for watermark = 1 cluster and confirm live C2 servers by IP, port, and URI pathsOne example in the results reveals multiple beacon endpoints hosted on the same IP address (124.223.25[.]186) over port 4444, each exposing different URI paths such as /JiWR, /tD6n, and /GbAr. This repetition across URIs and timestamps indicates that the same C2 server is actively serving multiple beacons, a strong sign of an operational and persistent Cobalt Strike setup.
Our IP Enrichment for 124.223.25[.]186 shows it belongs to Shenzhen Tencent Computer Systems Company Limited (AS45090) in Shanghai, China, and is flagged as high risk due to active Cobalt Strike activity.
The open port analysis shows multiple exposed services: SSH (22), HTTP (80) running Apache on Ubuntu, and notably ports 4444 and 50050, both associated with Cobalt Strike communications observed as recently as November 6, 2025.
![Figure 5. Hunt.io enrichment for 124.223.25[.]186 showing ASN, location, and active Cobalt Strike ports](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/11-2025/The+Complete+Guide+to+Hunting+Cobalt+Strike+-+Part+2+10%2B+HuntSQL+Recipes+for+Detecting+Cobalt+Strike+Infrastructure+-+figure+5.png) Figure 5. Hunt.io enrichment for 124.223.25[.]186 showing ASN, location, and active Cobalt Strike ports.
Figure 5. Hunt.io enrichment for 124.223.25[.]186 showing ASN, location, and active Cobalt Strike ports.For threat hunters, fields like IP and port pair assist in identifying the live command-and-control server, while URI paths can reveal beacon distribution patterns or automated tasking endpoints. The watermark itself is essential for clustering, as it allows correlation of multiple infrastructures operated by actors relying on the same cracked Cobalt Strike build.
3. Cobalt Strike Ports Distribution
This query aggregates the most frequently observed ports used by Cobalt Strike samples where the associated domain field is not empty. The goal is to identify which network ports are most commonly leveraged for beacon communications across different infrastructures.
SELECT
cobaltstrike.port,
count(*) AS Total
FROM
malware
WHERE
cobaltstrike.domains !=''
GROUP BY
cobaltstrike.port
ORDER BY
Total DESC
CopyOutput example:
 Figure 6. Common ports used by Cobalt Strike beacons that show how operators hide C2 on standard web ports to blend with normal traffic.
Figure 6. Common ports used by Cobalt Strike beacons that show how operators hide C2 on standard web ports to blend with normal traffic.The results highlight port 443 as the dominant channel (82,839 occurrences), followed by port 80, 8443, 8080, and 18443.
Practically speaking, this query emphasizes the importance of monitoring beacon communication over common web ports. Since Cobalt Strike frequently mimics regular HTTPS activity, defenders should look for anomalous TLS certificates, irregular traffic patterns, or consistent beacon intervals on these ports.
4. Identifying Cobalt Strike Clusters by Watermark and Public Key
This query focuses on grouping Cobalt Strike samples based on their watermark (license ID) and public key (unique beacon configuration hash). The purpose is to identify clusters of Cobalt Strike beacons that share the same configuration traits, which often indicate shared infrastructure or the same operator group.
SELECT
cobaltstrike.watermark,
cobaltstrike.public_key,
count(*) AS total
FROM
malware
WHERE
cobaltstrike.public_key !=''
GROUP BY
cobaltstrike.watermark,
cobaltstrike.public_key
ORDER BY
total DESC
CopyOutput example:
 Figure 7. The combination of Watermark and public_key frequency provides a deterministic fingerprint for campaign clustering and cross-sighting.
Figure 7. The combination of Watermark and public_key frequency provides a deterministic fingerprint for campaign clustering and cross-sighting.The results reveal several recurring watermarks, such as 987654321 and 666666666, associated with multiple distinct public keys. The watermark 987654321 dominates with thousands of occurrences across multiple keys, suggesting that it may represent a widely reused cracked or pirated version of Cobalt Strike used by different threat actors.
For a threat hunter, the fields cobaltstrike.watermark and cobaltstrike.public_key are crucial pivots. The watermark can help attribute samples to known actor clusters or campaigns since some APTs and ransomware groups consistently reuse the same watermark.
For example, we performed a focused hunt starting from the Cobalt Strike watermark 1473793097, shared on the X platform by researcher @banthisguy9349. The HuntSQL™ query is designed to target this specific watermark, exclude empty hostnames, and display unique IP and hostname pairs:
SELECT
ip,
hostname
FROM
malware
WHERE
cobaltstrike.watermark = '1473793097'
AND hostname != ''
AND timestamp gt '2025-01-01'
GROUP BY
ip,
hostname
CopyOutput example:
 Figure 8. Pivot from a public watermark '1473793097' to discover 12 unique IP and domain pair that shows a compact example of open-source IOC validation.
Figure 8. Pivot from a public watermark '1473793097' to discover 12 unique IP and domain pair that shows a compact example of open-source IOC validation.The query returned 12 clustered IPs and hostnames, indicating potential C2 infrastructure related to Cobalt Strike watermark 1473793097. The results then inform containment strategies and detection rules focused on watermark, public_key, and rapidly changing hostnames.
5. Cobalt Strike Beacons Masquerading as WordPress Traffic
This query isolates Cobalt Strike servers that mimic legitimate WordPress infrastructure while using common browser-like user agents. By filtering for submit_uri patterns beginning with /wp% and user_agent strings containing "Mozilla," the query highlights beacon servers that disguise C2 communications as normal web traffic.
The inclusion of IP, port, malware.name, version, and user_agent fields allow analysts to directly observe version distribution and behavioral patterns across active Cobalt Strike instances.
SELECT
ip,
port,
malware.name,
version,
cobaltstrike.user_agent
FROM
malware
WHERE
cobaltstrike.submit_uri LIKE '/wp%'
AND cobaltstrike.user_agent LIKE '%Mozilla%'
AND timestamp gt '2025-01-01'
GROUP BY
ip,
port,
malware.name,
version,
cobaltstrike.user_agent
CopyOutput example:
 Figure 9. The WordPress-like submit URIs and browser UA operators use CMS paths to camouflage beacon callbacks.
Figure 9. The WordPress-like submit URIs and browser UA operators use CMS paths to camouflage beacon callbacks.The results reveal multiple Cobalt Strike versions (notably 4.5 and 4.9) operating on ports 443, 8443, 2087, and 50051 often associated with HTTPS or API communication. Many of these IPs consistently employ WordPress-like paths (e.g., /wp-admin/, /wp-content/) and spoofed Mozilla/5.0 user agents to blend with normal traffic, a known Cobalt Strike evasion tactic.
The user agent and URI patterns here make it easy to spot beacons trying to pass as WordPress or browser traffic. Additionally, the version field helps assess the operational maturity of the adversary by indicating which Cobalt Strike build is in use. Finally, submit_uri patterns such as /wp-admin/ or /wp-content/ provide meaningful pivots into web server logs, phishing repositories, or URL intelligence feeds.
Some operators reuse well-documented tricks, and one of the clearest examples was flagged in Palo Alto's reporting.
This query focuses on known operational patterns shared by Palo Alto Networks, where threat actors used the user agent Microsoft-CryptoAPI/6.1 combined with a submit URI containing "oscp" to disguise Cobalt Strike beacon activity as certificate revocation checks. These artifacts indicate an actor's attempt to blend C2 callbacks into normal Windows CryptoAPI behavior.
SELECT
ip
FROM
malware
WHERE
cobaltstrike.user_agent = 'Microsoft-CryptoAPI/6.1'
AND cobaltstrike.submit_uri LIKE '%oscp%'
AND timestamp gt '2025-01-01'
GROUP BY
ip
CopyOutput example:
 Figure 10. A pivot on 'Microsoft-CryptoAPI/6.1' User Agent with URI OSCP-style deception shows 5 unique IP Addresses as targeted detection pivot.
Figure 10. A pivot on 'Microsoft-CryptoAPI/6.1' User Agent with URI OSCP-style deception shows 5 unique IP Addresses as targeted detection pivot.The query results show five unique IP addresses associated with this behavior, indicating that multiple servers are reusing this same deception pattern across different infrastructure segments. These IPs likely belong to the same or related campaigns leveraging identical Cobalt Strike configurations for operational consistency.
6. Discover Callback Endpoints Using Action Verbs (login|post|submit)
This query hunts for Cobalt Strike submit URIs that contain common action verbs such as login, post, or submit, which adversaries often use to blend C2 callbacks with normal web application traffic.
SELECT
cobaltstrike.domains,
cobaltstrike.port,
cobaltstrike.submit_uri
FROM
malware
WHERE
cobaltstrike.submit_uri RLIKE '(login|post|submit)'
GROUP BY
cobaltstrike.domains,
cobaltstrike.port,
cobaltstrike.submit_uri
CopyOutput example:
 Figure 11. Search for action-verb URIs with high-yield heuristics to find beacons hiding as web app form endpoints.
Figure 11. Search for action-verb URIs with high-yield heuristics to find beacons hiding as web app form endpoints.The results show many distinct domain and path combinations that indicate a broad use of application-style endpoints across diverse hosters and ports, consistent with operator efforts to hide beacon traffic inside expected HTTP actions.
The submit, post, and login URIs are high-value heuristics for hunters because they mimic legitimate application behavior while serving as convenient upload/download points for beacons.
The key fields to pivot are cobaltstrike.domains (use passive DNS and domain history to find sibling hosts and registration patterns), cobaltstrike.port (check network flows and firewall logs for unusual traffic on nonstandard ports such as 9966, 2024, or 8888), and cobaltstrike.submit_uri (fetch the endpoint or review proxy captures for base64 payloads, form fields, or header stanzas that reveal beacon formats).
7. Detecting Cobalt Strike Beacons That Spawn into dllhost.exe
This query finds Cobalt Strike configurations where cobaltstrike.spawn_to_x64 references dllhost, flagging beacons that will inject into the legitimate Windows COM surrogate process.
SELECT
*
FROM
malware
WHERE
cobaltstrike.spawn_to_x64 LIKE '%dllhost%'
CopyOutput example:
 Figure 12. The dllhost.exe spawn target with a host-level artifact that converts network leads into high-confidence compromises.
Figure 12. The dllhost.exe spawn target with a host-level artifact that converts network leads into high-confidence compromises.With 51,408 hits since the query timeframe, the pattern is widespread and often paired with web-like submit URIs and common web ports, indicating operators are using dllhost.exe to hide execution while C2 traffic blends into normal HTTP/S flows.
From a threat hunting perspective, the query's results open multiple pivot points. Hunters can start by searching EDR or process creation telemetry for instances of dllhost.exe spawned by unusual parents or containing injected memory regions.
Moreover, cross-referencing the IP or Port and submit_uri values within proxy or network flow logs can help reconstruct the full C2 session, including beacon registration and tasking behavior. Similarly, cobaltstrike.submit_uri and cobaltstrike.domains highlight the callback paths used by the beacon to fetch payloads or communicate with the server, helping analysts identify network-based detection opportunities.
8. Beacon timing statistics (average and maximum sleeptime)
This query summarizes beacon callback intervals by reporting the average and maximum values of cobaltstrike.sleeptime across the malware dataset.
SELECT
avg(cobaltstrike.sleeptime),
max(cobaltstrike.sleeptime)
FROM
malware
CopyOutput example:
 Figure 13. Beacon cadence overview, separating noisy, test, and stealthy implants by timing distribution across the whole malware dataset.
Figure 13. Beacon cadence overview, separating noisy, test, and stealthy implants by timing distribution across the whole malware dataset.The results (average ≈ 551 ms, max ≈ 776,650 ms) indicate a very wide distribution of configured sleep times from sub-second noisy beacons to long-interval, stealthy implants. For hunting purposes, the analyst can track the different Cobalt Strike beacon averages among a lot of hunted records.
9. ASN country distribution of Cobalt Strike servers using browser-like User-Agents
This query analyzes the geographical distribution of Cobalt Strike command-and-control (C2) servers that disguise their traffic with browser-style User-Agent strings containing Mozilla, Edge, or Chrome.
SELECT
asn.country_code,
count(*) AS total
FROM
malware
WHERE
cobaltstrike.user_agent RLIKE '(Mozilla|Edge|Chrome)'
GROUP BY
asn.country_code
ORDER BY
total DESC
CopyOutput example:
 Figure 14. Geographic ASN view for browser-like beacons reveals hosting clusters and provider abuse trends.
Figure 14. Geographic ASN view for browser-like beacons reveals hosting clusters and provider abuse trends.The results show a strong concentration in China (CN) with 175,501 detections, followed by Hong Kong (HK), the United States (US), and Singapore (SG) regions frequently observed in both commercial VPS hosting and bulletproof infrastructure used by threat actors.
Adversaries often spoof legitimate browser agents to blend C2 traffic with normal web browsing. By correlating such fake agents with ASN country data, hunters can differentiate benign user traffic from C2 activity and identify hosting clusters that repeatedly appear in operations.
10. Watermark frequency and spread (campaign-scale indicator)
This query counts occurrences per cobaltstrike.watermark and reports how many unique IPs each watermark appears on, surfacing which license IDs or embedded markers are most widespread.
SELECT
cobaltstrike.watermark,
count(*) AS occurrences,
uniq(ip) AS ips
FROM
malware
WHERE
cobaltstrike.watermark >= 0
GROUP BY
cobaltstrike.watermark
ORDER BY
occurrences DESC
CopyOutput example:
 Figure 15. Watermark prevalence and unique IP spread use high-frequency watermarks to prioritize campaign hunts.
Figure 15. Watermark prevalence and unique IP spread use high-frequency watermarks to prioritize campaign hunts.The results show a massive spike at two prominent nonzero watermarks: 987654321 (135,504 occurrences / 497 IPs) and 666666666 (89,746 occurrences / 362 IPs).
For threat hunters, the watermark values are excellent campaign-level anchors. They can track unique IPs with watermark values in the malware dataset to hunt further Cobalt Strike IPs and narrow down their pivots.
11. Low sleep interval beacons (aggressive callback detection)
This query filters all Cobalt Strike entries where the sleeptime value is greater than 0 but less than 3000 milliseconds, sorting results in ascending order to surface the fastest-calling beacons first.
SELECT
ip,
cobaltstrike.sleeptime,
cobaltstrike.jitter,
timestamp
FROM
malware
WHERE
cobaltstrike.sleeptime > 0
AND cobaltstrike.sleeptime < 3000
ORDER BY
cobaltstrike.sleeptime ASC
LIMIT
200
CopyOutput example:
 Figure 16. Very low sleep time beacons likely test or live operator sessions and are high-value for capture.
Figure 16. Very low sleep time beacons likely test or live operator sessions and are high-value for capture.The output reveals beacon configurations with extremely short intervals, as low as 1 millisecond and zero jitter, such as IPs 185.196.11[.]20 and 147.185.221[.]25. These configurations represent highly aggressive communication patterns, often associated with testing setups, misconfigurations, or active operations requiring near-real-time tasking.
For threat hunters, this is a valuable behavioral marker in the way that extremely low sleeptime values indicate either live operator sessions or automated staging beacons running in "debug" or "low-latency" mode.
12. ASN-Level Distribution of Cobalt Strike Beacons
This query examines the hosting infrastructure behind Cobalt Strike activity by grouping all detected beacons according to their Autonomous System Name (ASN). By aggregating based on asn.name, it highlights which network providers or hosting services are most frequently associated with Cobalt Strike command-and-control servers.
SELECT
asn.name,
count(*) AS beacons,
uniq(ip)
FROM
malware
WHERE
cobaltstrike.public_key != ''
GROUP BY
asn.name
ORDER BY
beacons DESC
CopyOutput example:
 Figure 17. ASN aggregation for public_key-bearing beacons shows a strategic view for cloud provider-focused hunts that contains records per IP addresses and their unique count per hosting.
Figure 17. ASN aggregation for public_key-bearing beacons shows a strategic view for cloud provider-focused hunts that contains records per IP addresses and their unique count per hosting.The results show Shenzhen Tencent Computer Systems Company Limited leading with over 77,621 beacons across 247 unique IPs, followed by Hangzhou Alibaba Advertising Co., Ltd. with 67,000+ beacons and Tencent Building, Kejizhongyi Avenue with nearly 10,000 beacons.
For threat hunters, this view provides strategic intelligence into the infrastructure ecosystems supporting active or historical Cobalt Strike operations. For example, the clusters of activity within large Chinese cloud providers like Tencent and Alibaba indicate recurring use of these public hosting environments for staging and controlling beacon traffic.
Similarly, the repetitive detections from the same ASN can be escalated for cloud abuse reporting or regional threat intelligence sharing. Pivoting from these ASNs to related IP ranges, passive DNS entries, or TLS certificate reuse patterns can expose entire Cobalt Strike clusters operating under the same provider.
To show how these pivots come together in a real scenario, here's a profile-based hunt tied to a known Cobalt Strike configuration.
13. Tracking Cobalt Strike from the Lazarus Cobalt Strike Profile
In order to understand how a threat hunter crafts a HuntSQL™, we have picked up a Cobalt Strike profile from GitHub. The profile is linked with APT Lazarus, which has specified a 30,000 ms sleeptime, 20 ms jitter, Firefox 47 user-agent, WordPress-style and stager URIs (/view.jsp, psmon.dat, avgnt.dat), Nginx server headers, and a dllhost/imeklmg.exe spawn preference.
The HuntSQL™ query is designed with fields cobaltstrike.sleeptime, cobaltstrike.jitter, cobaltstrike.user_agent, cobaltstrike.submit_uri, cobaltstrike.domains, cobaltstrike.spawn_to_x64, cobaltstrike.procinj_transform_x64, and cobaltstrike.procinj_execute in the year 2024.
SELECT
ip, count(*) as total
FROM
malware
WHERE
timestamp BETWEEN '2024-01-01' AND '2024-12-31'
AND cobaltstrike.sleeptime = '30000'
AND cobaltstrike.jitter = '20'
AND cobaltstrike.user_agent = 'Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:47.0) Gecko/20100101 Firefox/47.0'
AND (
cobaltstrike.submit_uri LIKE '%psmon.dat%'
OR cobaltstrike.submit_uri LIKE '%avgnt.dat%'
OR cobaltstrike.domains LIKE '%/view.jsp%'
)
AND (
cobaltstrike.spawn_to_x64 LIKE '%imeklmg.exe%'
OR cobaltstrike.spawn_to_x86 LIKE '%imeklmg.exe%'
OR cobaltstrike.procinj_execute LIKE '%CreateRemoteThread%'
OR cobaltstrike.procinj_transform_x64 LIKE '%shorthand_or_marker%'
)
GROUP BY
ip
ORDER BY
total DESC
CopyOutput example:
 Figure 18. Profile-based hunt for Lazarus Group maps a Malleable C2 profile to an IP cluster and escalates with host and infrastructure pivot to disclose a server at 93.113.25.195 IP Address.
Figure 18. Profile-based hunt for Lazarus Group maps a Malleable C2 profile to an IP cluster and escalates with host and infrastructure pivot to disclose a server at 93.113.25.195 IP Address.The query returned a single, focused cluster: 93.113.25[.]195 with 37 matching sightings. This is a high-value lead because the profile's combination of timing, UA, submit URIs, and spawn targets is specific and tied to Lazarus-style tradecraft.
The host 93.113.25[.]195 resolves to AS214209 (Internet Magnate (Pty) Ltd), registered in Bucharest, Romania, and sits in the 93.113.25.0/24 block. Hunt.io flags the address as high risk with active Cobalt Strike activity and four associated domains, and it has been observed with an open TCP-wrapped service on port 443 as recently as 2025-11-07.
 Figure 19. Hunt.io shows the IP Address "92.113.25.195" hosted over Internet Magnate (Pty) Ltd and has been linked with Cobalt Strike from 2024.
Figure 19. Hunt.io shows the IP Address "92.113.25.195" hosted over Internet Magnate (Pty) Ltd and has been linked with Cobalt Strike from 2024.The combination of a tight profile match (sleeptime/jitter/UA/submit_uri/spawn targets) and a high-risk ASN with multiple domain associations shifts the IP from a noisy hit to a prioritized investigative target.
These findings reinforce the need for a structured and consistent approach when working with Cobalt Strike telemetry. Even strong leads must be validated, enriched, and contextualized to avoid false confidence.
The next section outlines the best practices that support effective hunting, attribution, and detection.
Best Practices
Start wide before narrowing down: Running simple distribution queries, like the one that counts malware.name, gives you a quick sense of what's most active in the dataset and where Cobalt Strike fits in.
Lean on the strongest fingerprints first: Fields such as cobaltstrike.public_key and cobaltstrike.watermark usually give the cleanest pivots. They make it easy to see which servers belong together and which ones look like part of the same setup.
Use behavior to fill in the gaps: Tables like cobaltstrike.user_agent, cobaltstrike.sleeptime, and cobaltstrike.jitter help you spot beacons that try to blend in with normal traffic or follow odd timing patterns.
Check domains, ports, and paths to confirm activity: Combining cobaltstrike.domains, cobaltstrike.port, cobaltstrike.submit_uri, and scan.uri is a solid way to understand how a server is being used and whether its traffic matches typical Cobalt Strike behavior.
Connect network clues to execution clues: Fields like cobaltstrike.spawn_to_x64, spawn_to_x86, and the various procinj_* entries help you tie what you see in network data to how the beacon is meant to run on a host.
Once these practices are applied consistently, the patterns behind Cobalt Strike activity become predictable enough to summarize the key insights below.
Conclusion
HuntSQL™ turns raw scanner data into real hunting insight. With a few focused queries, it's possible to connect isolated Cobalt Strike detections, map beacon clusters, and uncover infrastructure that would otherwise stay hidden. These 10+ recipes are a starting point for analysts who want clear, data-backed pivots they can reuse and expand.
Part 2 focused on controlled, manual pivots. In Part 3, we'll explore how these exact workflows translate into automated clustering and detection inside Hunt.io.
If you want to see how this works in action, book a demo today and explore how Hunt.io helps you detect Cobalt Strike infrastructure automatically across the internet.
Related Posts
Related Posts
Related Posts