IOC Hunter turns trusted public research into validated IOCs you can immediately use in investigations.
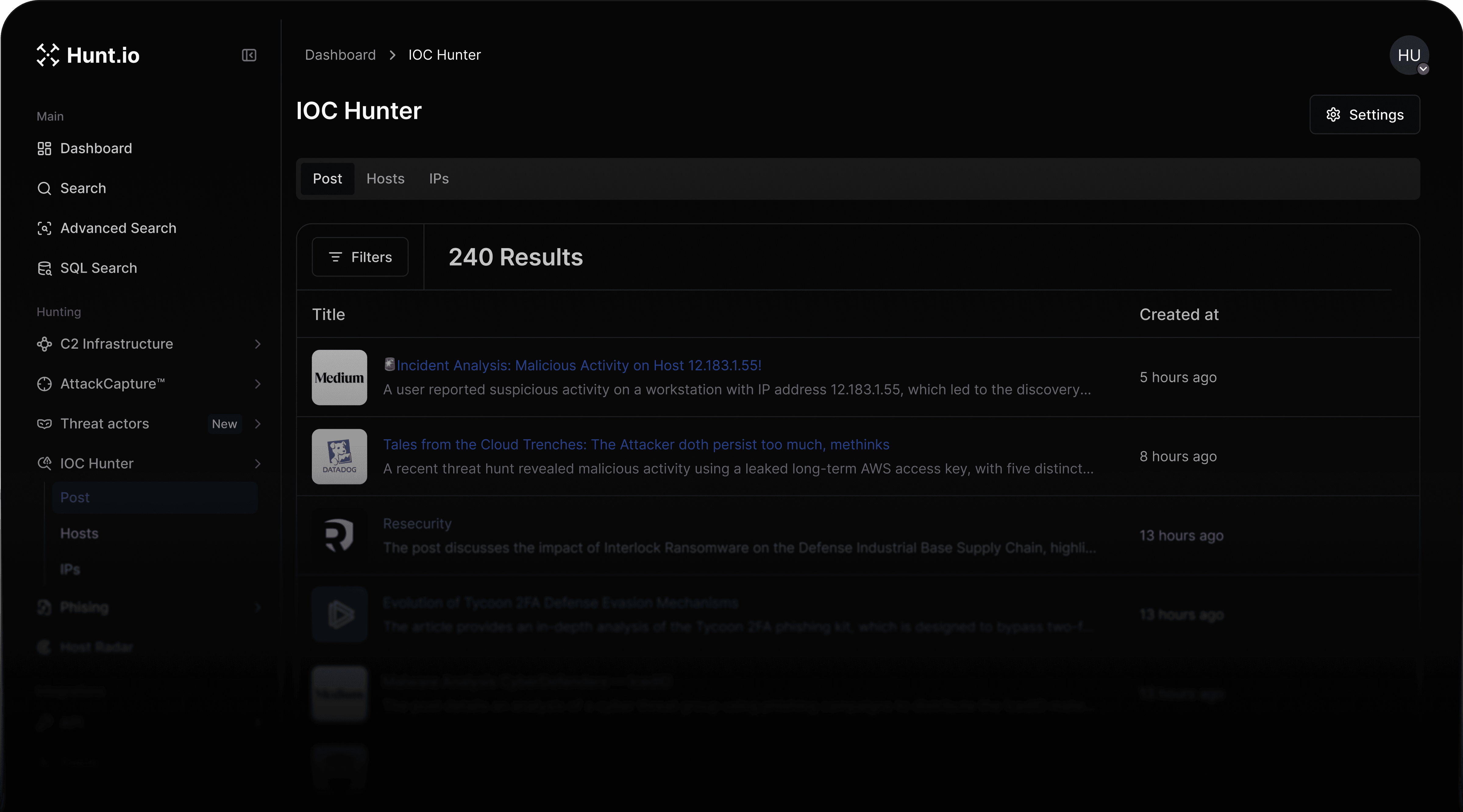
Built from the bottom up to find, validate, and interrupt hostile infrastructure in real time.
We curate the best and trusted applications to pull IOCs from.
LLM combined with Human in the Loop provides best of both worlds for speed and accuracy.
Hunt can pivot off of these IOCs as a starting point to make sure you never hit a dead end in an investigation.
All IOCs are pre- enriched with best of breed data to aid in Hunts.
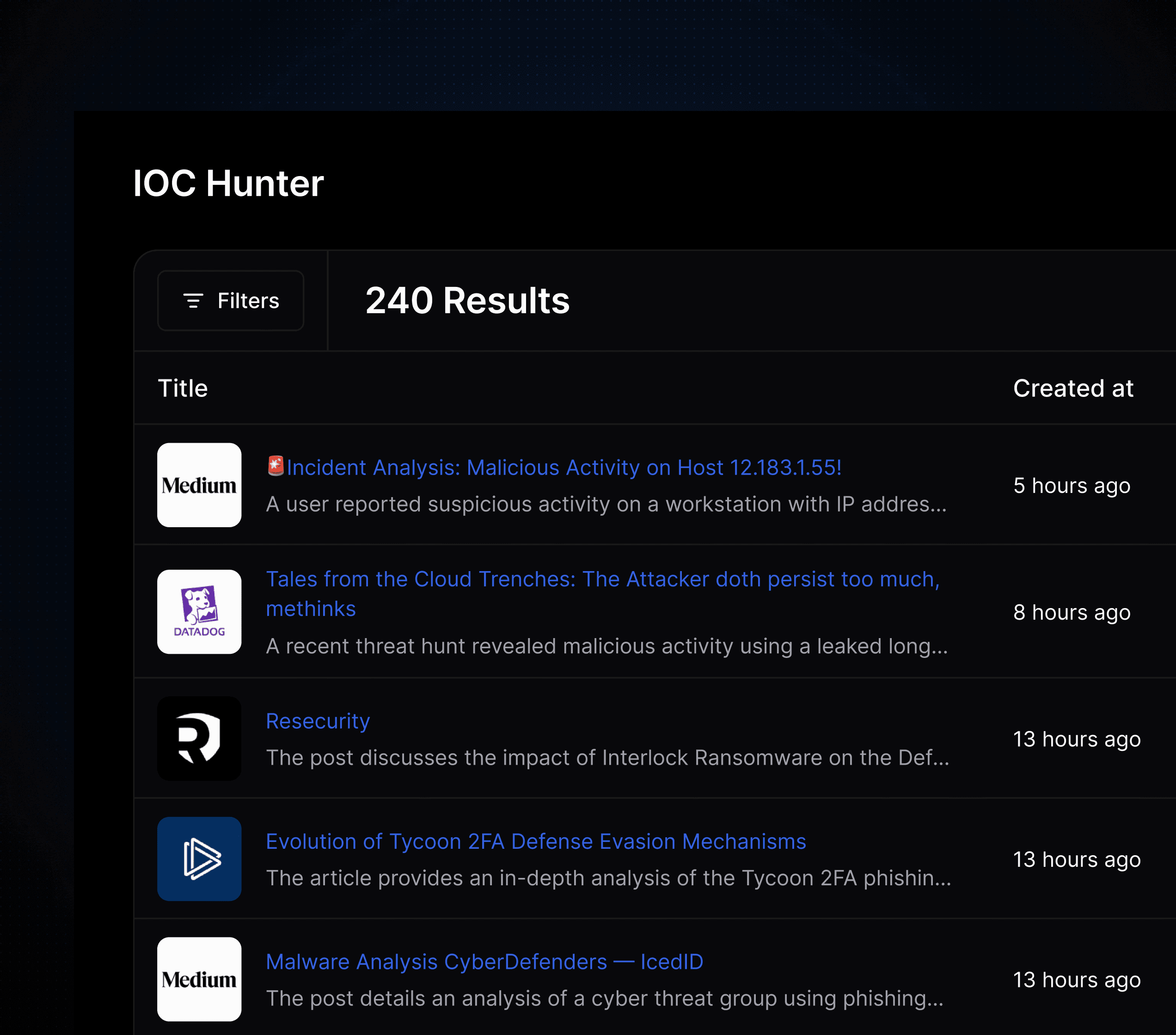
Pivot and Expansion
Bootstrap investigations by using research from other teams to narrow in on an incident or threat actor by expanding using their TTPs or ensuring that you don’t hit a dead end.
faq
What is IOC Hunter used for?
IOC Hunter is used to extract and validate IOCs from trusted public cyber research, turning reports into investigation-ready data.
Where do the IOCs come from?
IOCs are sourced from a curated set of trusted public research publications and processed before being made available.
How does IOC Hunter support threat investigations?
It provides validated IOCs that analysts can use as a starting point to pivot, enrich, and expand investigations without relying solely on raw research reports.
How are IOCs validated?
IOCs are processed using automated analysis combined with human review to balance speed, accuracy, and trust.


