ProxyLogon and ProxyShell Used to Target Government Mail Servers in Asia, Europe, and South America
ProxyLogon and ProxyShell Used to Target Government Mail Servers in Asia, Europe, and South America
Published on
Nearly three years after ProxyLogon and ProxyShell wreaked widespread havoc on Microsoft Exchange servers, the Hunt Research Team identified a server likely exploiting these vulnerabilities to gain initial access and steal sensitive communications.
Affected entities were spread across multiple regions, encompassing a seemingly targeted range of government sectors. For example, we found numerous folders named after email addresses associated with the Afghanistan Arg (Presidential Palace), and within those folders were hundreds of conversations between officials, including the defense, interior, and protocol ministries.
In this post, we’ll explore our findings, which began with an open directory, and hypothesize possible motives of the threat actor.
Quick Refresher on ProxyLogon & ProxyShell
First disclosed in 2021, the targeted Exchange Servers we’ll discuss later in this post are/were vulnerable to ProxyLogon and ProxyShell. The former exploits a server-side request forgery (SSRF) flaw, where attackers send a specific web request with an XML payload to Exchange Web Services (EWS) API endpoint. Doing so enables the actor to execute operations on the victim's mailbox without needing to authenticate.
ProxyShell consists of three vulnerabilities (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207). Successful exploitation allows an unauthenticated attacker to execute commands on the server via port 443. At a high level, the threat actor leverages legitimate services such as Autodiscover and the Messaging Application Programming Interface (MAPI) to obtain a user's distinguished name (DN) and security identifier (SID).
With the SID, the attacker can forge an access token to communicate with EWS, impersonating the target user.
Below, we’ll discuss the server hosting the files that caught our attention and tipped us off to the previously mentioned vulnerabilities.
Initial Discovery: A Modern Digital Heist
Our research discovered a server hosted on DigitalOcean at IP address 167.71.173_239, exposing an open directory on port 8111. What initially grabbed our attention wasn't the email addresses visible on the misconfigured Python 3.11.6 SimpleHTTP server but rather the sheer volume of files - a staggering 3,923, as illustrated in Figure 1.
 Figure 1: Screenshot of the suspicious open directory in Hunt
Figure 1: Screenshot of the suspicious open directory in HuntTo safeguard those targeted, we will obscure the email addresses in this blog and on the Hunt platform. What may have caught your attention is the very first folder in the directory titled “阿富汗,” which translates to Afghanistan from Simplified Chinese. While it may be tempting to speculate, we’ll refrain from making assumptions as anyone can use translation tools to label folders in any language they choose. This folder alone contains 761 files and is 149 MB in size.
We identified the folder labeled “La” as having a similar number of files and standing for Laos. The actor(s) have organized some of the folders by the countries targeted. We are unsure if this directory is used to share stolen emails with other infrastructure or if server administrators separated data for easy searching amongst the many files.
As depicted in the top right of Figure 1, our scanners first detected the directory on June 24th. The server administrators likely noticed the misconfiguration because, within less than 12 hours of our initial discovery, port 8111 stopped responding to requests, but not before Hunt could download most of the hosted files.
Figure 2 shows the rest of the server, including a hidden .git directory, which we can infer represents the presence of open-source software and several Python files, which we’ll cover below.
 Figure 2: The remaining directory contents, including a .git folder and Python files
Figure 2: The remaining directory contents, including a .git folder and Python filesUpon analyzing the Python files, we discovered that the threat actor had copied and pasted open-source exploit code into a file named "run.py." This exploit allows the attacker to access user emails, search through them, and download them. Figures 3 and 4 depict the Python file downloaded by Hunt and the publicly available code, highlighting the similarities.
 Figure 3: Run.py code with overlaps from the GitHub repository
Figure 3: Run.py code with overlaps from the GitHub repository Figure 4: Code from exchange_ssrf_attacks.py (Source: GitHub)
Figure 4: Code from exchange_ssrf_attacks.py (Source: GitHub)In late 2021, TrendMicro highlighted a loader named "Squirrelwaffle," a term introduced by Talos Intelligence. This loader utilized the same exploit code seen in Figure 4 to distribute malicious spam, resulting in Cobalt Strike or Qbot infections.
Analyzing the other ports on the server, we noticed that an instance of the Acunetix Web Vulnerability Scanner was also present on port 13443, with a certificate bearing a unique common name. Figure 5 illustrates the SSL history for the IP address.
 Figure 5: SSL History showing the Acunetix certificate. (Try it in Hunt)
Figure 5: SSL History showing the Acunetix certificate. (Try it in Hunt)Using the Advanced Search feature, we can pivot on the certificate common name and JA4X hash. The image below shows the results of that pivot, with just 23 servers across the internet sharing the same cert data.
 Figure 6: Snippet of pivot results on Acunetix certificate common name
Figure 6: Snippet of pivot results on Acunetix certificate common nameWhen tracking adversary infrastructure, a low number of results like this usually suggests potential links, but further analysis is necessary to confirm any connections.
Hunt users can analyze the full results of the search here.
Targeted Countries
Afghanistan
Within the Afghanistan-titled folder were 15 sub-folders named after email addresses under the arg.gov_af domain used by presidential palace personnel. Five were email addresses belonging to individuals currently or previously working for the now Taliban-ruled administration.
The remaining addresses were linked to IT maintenance accounts, administrators, the office of the Chief of Staff for Media, the Protocol Minister, and the Ministries of Defense and Interior.
Each sub-folder contained varying numbers of .eml files, named in the format item-[number].eml, with what appear to be authentic email communications.
The small number of offices targeted and the specific emails stolen suggest the attacker or their handlers had a particular data set in mind.
Below are examples of the emails found within these folders. The content has been intentionally sanitized to avoid impeding response efforts and to prevent disclosing sensitive information.
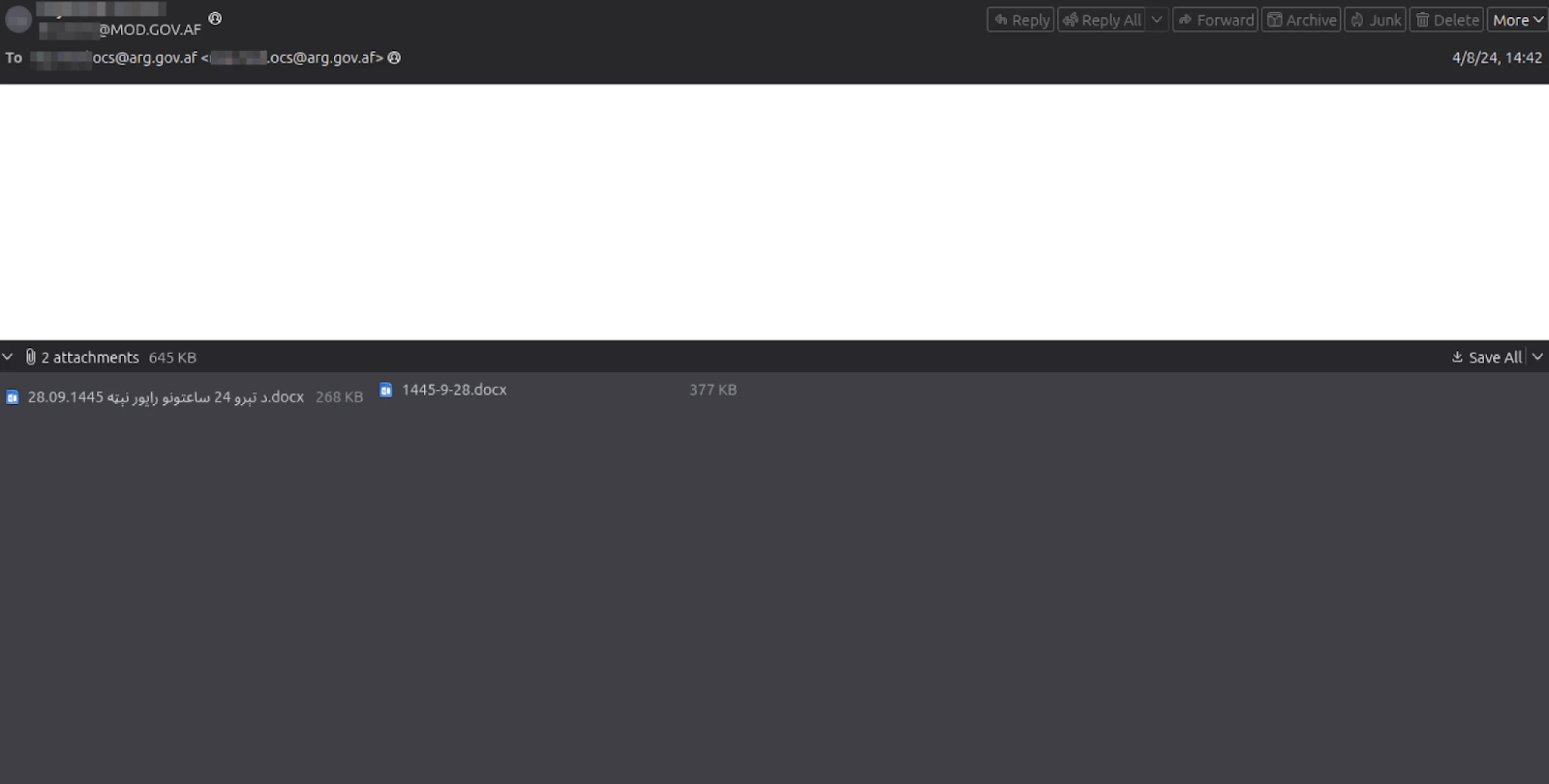 Figure 7: Screenshot of an empty email containing a daily activity report purported to be from a member of the Ministry of Defense
Figure 7: Screenshot of an empty email containing a daily activity report purported to be from a member of the Ministry of Defense Figure 8: Criminal incident reports shared between an official in the Ministry of Interior and an Office of Chief of Staff representative
Figure 8: Criminal incident reports shared between an official in the Ministry of Interior and an Office of Chief of Staff representative Figure 9: Screenshot of communications regarding infrastructure upgrades at the Prime Minister’s office
Figure 9: Screenshot of communications regarding infrastructure upgrades at the Prime Minister’s officeThe emails displayed in the figures above date back two months, with the most recent being approximately two weeks old. This suggests the actor likely maintains access to the mail servers and continues to actively search for valuable information.
Georgia (country)
From our analysis of the Python files “bp.py” and “fuzz.py,” we determined that the Special Investigation Section (SIS) of Georgia, sis.gov_ge, was a target. The SIS, an independent authority, investigates crimes law enforcement and government officials commit.
bp.py executes the publicly available "exchange_ssrf_attacks.py" against the SIS mail server. It iterates over each email address in '_list' and calls the email_command function for each address.
 Figure 10: Screenshot of bp.py searching for email addresses associated with the Georgian Special Investigation Service
Figure 10: Screenshot of bp.py searching for email addresses associated with the Georgian Special Investigation ServiceAdditionally, "fuzz.py" shows that the script was modified to target the Laos Statistics Bureau's mail infrastructure, with the SIS mail server entry commented out.
 Figure 11: The fuzz.py script targeting both Georgia and Laos
Figure 11: The fuzz.py script targeting both Georgia and Laos*No email addresses or email files were seen for the SIS server.
Argentina
Similar to the targeting of Georgia's SIS, we discovered a Python script named "burp.py" and a text file likely containing the script's output, "emails.txt," aimed at the Argentine Army General Staff's Exchange server.
The domain "cge.mil_ar" represents "Estado Mayor General del Ejército," highlighting a targeted attempt to infiltrate Argentina's military leadership's communication channels.
 Figure 12: Snippet of burp.py targeting the Exchange Server of the Argentinian Army. Note the Chinese language comments in the script
Figure 12: Snippet of burp.py targeting the Exchange Server of the Argentinian Army. Note the Chinese language comments in the script Figure 13: Contents of emails.txt file containing numerous Argentine military email addresses
Figure 13: Contents of emails.txt file containing numerous Argentine military email addressesLaos
Further server analysis revealed 65 email addresses from the Laos Statistics Bureau (LSB), whose domain is lsb.gov_la. Another 20 addresses were found in the “La/” folder. Similar to the Afghanistan folder, the collection included individual emails and those of administrators and IT services.
Many of the emails found within the multiple subfolders were older (2018 ~) and included notifications of quarantined emails. Some recent communications included invites to ASEAN events and run-of-the-mill spam messages. It’s currently unclear if the actor intentionally downloaded the quarantine notices to monitor which messages were blocked or if the emails were caught up during mass downloading.
 Figure 14: Screenshot of quarantine summary email
Figure 14: Screenshot of quarantine summary email Figure 15: Email invite to a supposed ASEAN event in July 2024
Figure 15: Email invite to a supposed ASEAN event in July 2024Although we found no post-exploitation tools on the server, the above underscores the importance of diligent patch management. Malicious actors do not always shift to the latest exploits; they often revisit unpatched older vulnerabilities if necessary to complete objectives.
Conclusion
In conclusion, our findings revealed a server with an open directory, exposing thousands of files and targeting government offices in Afghanistan, Laos, Georgia, and Argentina. Python scripts exploited known vulnerabilities, leveraging open-source code to infiltrate systems.
While the server was only exposed briefly and targeted a limited number of government entities, it highlights a critical issue: threat actors continue to exploit older vulnerabilities and adapt their tactics.
Hunt's Open Directories feature offers unmatched visibility into active threats, allowing security professionals to prioritize and respond confidently. Request a demo today to enhance your threat-hunting capabilities.
Indicators
| Indicator Type | Details |
|---|---|
| Open Directory IP Address | 167.71.173_239 |
| Port | 8111 |
| Acunetix Certificate SHA-1 Fingerprint | efbfbd12efbfbd69efbfbd6b45efbfbd76efbfbd0befbfbd2eefbfbd |
| Python Script SHA-256 Hashes | run.py - 016344d35f6f217f9f8b483dacb8154b45139355bcc45a3f94910351b5df42b5 fuzz.py - f527ea33f22293d99a5687fc13595c84830d6f2c52add1f08e49fbf607458251 burp.py-934e9336d45771a74de544be31e3dc8ec624891c5fc95a36d9ec124b39c4e5c7 bp.py - 4ad4d5edd434f8269cdf5511667364962dff7f2535ae13cd8102c6acde061a19 |
Nearly three years after ProxyLogon and ProxyShell wreaked widespread havoc on Microsoft Exchange servers, the Hunt Research Team identified a server likely exploiting these vulnerabilities to gain initial access and steal sensitive communications.
Affected entities were spread across multiple regions, encompassing a seemingly targeted range of government sectors. For example, we found numerous folders named after email addresses associated with the Afghanistan Arg (Presidential Palace), and within those folders were hundreds of conversations between officials, including the defense, interior, and protocol ministries.
In this post, we’ll explore our findings, which began with an open directory, and hypothesize possible motives of the threat actor.
Quick Refresher on ProxyLogon & ProxyShell
First disclosed in 2021, the targeted Exchange Servers we’ll discuss later in this post are/were vulnerable to ProxyLogon and ProxyShell. The former exploits a server-side request forgery (SSRF) flaw, where attackers send a specific web request with an XML payload to Exchange Web Services (EWS) API endpoint. Doing so enables the actor to execute operations on the victim's mailbox without needing to authenticate.
ProxyShell consists of three vulnerabilities (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207). Successful exploitation allows an unauthenticated attacker to execute commands on the server via port 443. At a high level, the threat actor leverages legitimate services such as Autodiscover and the Messaging Application Programming Interface (MAPI) to obtain a user's distinguished name (DN) and security identifier (SID).
With the SID, the attacker can forge an access token to communicate with EWS, impersonating the target user.
Below, we’ll discuss the server hosting the files that caught our attention and tipped us off to the previously mentioned vulnerabilities.
Initial Discovery: A Modern Digital Heist
Our research discovered a server hosted on DigitalOcean at IP address 167.71.173_239, exposing an open directory on port 8111. What initially grabbed our attention wasn't the email addresses visible on the misconfigured Python 3.11.6 SimpleHTTP server but rather the sheer volume of files - a staggering 3,923, as illustrated in Figure 1.
 Figure 1: Screenshot of the suspicious open directory in Hunt
Figure 1: Screenshot of the suspicious open directory in HuntTo safeguard those targeted, we will obscure the email addresses in this blog and on the Hunt platform. What may have caught your attention is the very first folder in the directory titled “阿富汗,” which translates to Afghanistan from Simplified Chinese. While it may be tempting to speculate, we’ll refrain from making assumptions as anyone can use translation tools to label folders in any language they choose. This folder alone contains 761 files and is 149 MB in size.
We identified the folder labeled “La” as having a similar number of files and standing for Laos. The actor(s) have organized some of the folders by the countries targeted. We are unsure if this directory is used to share stolen emails with other infrastructure or if server administrators separated data for easy searching amongst the many files.
As depicted in the top right of Figure 1, our scanners first detected the directory on June 24th. The server administrators likely noticed the misconfiguration because, within less than 12 hours of our initial discovery, port 8111 stopped responding to requests, but not before Hunt could download most of the hosted files.
Figure 2 shows the rest of the server, including a hidden .git directory, which we can infer represents the presence of open-source software and several Python files, which we’ll cover below.
 Figure 2: The remaining directory contents, including a .git folder and Python files
Figure 2: The remaining directory contents, including a .git folder and Python filesUpon analyzing the Python files, we discovered that the threat actor had copied and pasted open-source exploit code into a file named "run.py." This exploit allows the attacker to access user emails, search through them, and download them. Figures 3 and 4 depict the Python file downloaded by Hunt and the publicly available code, highlighting the similarities.
 Figure 3: Run.py code with overlaps from the GitHub repository
Figure 3: Run.py code with overlaps from the GitHub repository Figure 4: Code from exchange_ssrf_attacks.py (Source: GitHub)
Figure 4: Code from exchange_ssrf_attacks.py (Source: GitHub)In late 2021, TrendMicro highlighted a loader named "Squirrelwaffle," a term introduced by Talos Intelligence. This loader utilized the same exploit code seen in Figure 4 to distribute malicious spam, resulting in Cobalt Strike or Qbot infections.
Analyzing the other ports on the server, we noticed that an instance of the Acunetix Web Vulnerability Scanner was also present on port 13443, with a certificate bearing a unique common name. Figure 5 illustrates the SSL history for the IP address.
 Figure 5: SSL History showing the Acunetix certificate. (Try it in Hunt)
Figure 5: SSL History showing the Acunetix certificate. (Try it in Hunt)Using the Advanced Search feature, we can pivot on the certificate common name and JA4X hash. The image below shows the results of that pivot, with just 23 servers across the internet sharing the same cert data.
 Figure 6: Snippet of pivot results on Acunetix certificate common name
Figure 6: Snippet of pivot results on Acunetix certificate common nameWhen tracking adversary infrastructure, a low number of results like this usually suggests potential links, but further analysis is necessary to confirm any connections.
Hunt users can analyze the full results of the search here.
Targeted Countries
Afghanistan
Within the Afghanistan-titled folder were 15 sub-folders named after email addresses under the arg.gov_af domain used by presidential palace personnel. Five were email addresses belonging to individuals currently or previously working for the now Taliban-ruled administration.
The remaining addresses were linked to IT maintenance accounts, administrators, the office of the Chief of Staff for Media, the Protocol Minister, and the Ministries of Defense and Interior.
Each sub-folder contained varying numbers of .eml files, named in the format item-[number].eml, with what appear to be authentic email communications.
The small number of offices targeted and the specific emails stolen suggest the attacker or their handlers had a particular data set in mind.
Below are examples of the emails found within these folders. The content has been intentionally sanitized to avoid impeding response efforts and to prevent disclosing sensitive information.
 Figure 7: Screenshot of an empty email containing a daily activity report purported to be from a member of the Ministry of Defense
Figure 7: Screenshot of an empty email containing a daily activity report purported to be from a member of the Ministry of Defense Figure 8: Criminal incident reports shared between an official in the Ministry of Interior and an Office of Chief of Staff representative
Figure 8: Criminal incident reports shared between an official in the Ministry of Interior and an Office of Chief of Staff representative Figure 9: Screenshot of communications regarding infrastructure upgrades at the Prime Minister’s office
Figure 9: Screenshot of communications regarding infrastructure upgrades at the Prime Minister’s officeThe emails displayed in the figures above date back two months, with the most recent being approximately two weeks old. This suggests the actor likely maintains access to the mail servers and continues to actively search for valuable information.
Georgia (country)
From our analysis of the Python files “bp.py” and “fuzz.py,” we determined that the Special Investigation Section (SIS) of Georgia, sis.gov_ge, was a target. The SIS, an independent authority, investigates crimes law enforcement and government officials commit.
bp.py executes the publicly available "exchange_ssrf_attacks.py" against the SIS mail server. It iterates over each email address in '_list' and calls the email_command function for each address.
 Figure 10: Screenshot of bp.py searching for email addresses associated with the Georgian Special Investigation Service
Figure 10: Screenshot of bp.py searching for email addresses associated with the Georgian Special Investigation ServiceAdditionally, "fuzz.py" shows that the script was modified to target the Laos Statistics Bureau's mail infrastructure, with the SIS mail server entry commented out.
 Figure 11: The fuzz.py script targeting both Georgia and Laos
Figure 11: The fuzz.py script targeting both Georgia and Laos*No email addresses or email files were seen for the SIS server.
Argentina
Similar to the targeting of Georgia's SIS, we discovered a Python script named "burp.py" and a text file likely containing the script's output, "emails.txt," aimed at the Argentine Army General Staff's Exchange server.
The domain "cge.mil_ar" represents "Estado Mayor General del Ejército," highlighting a targeted attempt to infiltrate Argentina's military leadership's communication channels.
 Figure 12: Snippet of burp.py targeting the Exchange Server of the Argentinian Army. Note the Chinese language comments in the script
Figure 12: Snippet of burp.py targeting the Exchange Server of the Argentinian Army. Note the Chinese language comments in the script Figure 13: Contents of emails.txt file containing numerous Argentine military email addresses
Figure 13: Contents of emails.txt file containing numerous Argentine military email addressesLaos
Further server analysis revealed 65 email addresses from the Laos Statistics Bureau (LSB), whose domain is lsb.gov_la. Another 20 addresses were found in the “La/” folder. Similar to the Afghanistan folder, the collection included individual emails and those of administrators and IT services.
Many of the emails found within the multiple subfolders were older (2018 ~) and included notifications of quarantined emails. Some recent communications included invites to ASEAN events and run-of-the-mill spam messages. It’s currently unclear if the actor intentionally downloaded the quarantine notices to monitor which messages were blocked or if the emails were caught up during mass downloading.
 Figure 14: Screenshot of quarantine summary email
Figure 14: Screenshot of quarantine summary email Figure 15: Email invite to a supposed ASEAN event in July 2024
Figure 15: Email invite to a supposed ASEAN event in July 2024Although we found no post-exploitation tools on the server, the above underscores the importance of diligent patch management. Malicious actors do not always shift to the latest exploits; they often revisit unpatched older vulnerabilities if necessary to complete objectives.
Conclusion
In conclusion, our findings revealed a server with an open directory, exposing thousands of files and targeting government offices in Afghanistan, Laos, Georgia, and Argentina. Python scripts exploited known vulnerabilities, leveraging open-source code to infiltrate systems.
While the server was only exposed briefly and targeted a limited number of government entities, it highlights a critical issue: threat actors continue to exploit older vulnerabilities and adapt their tactics.
Hunt's Open Directories feature offers unmatched visibility into active threats, allowing security professionals to prioritize and respond confidently. Request a demo today to enhance your threat-hunting capabilities.
Indicators
| Indicator Type | Details |
|---|---|
| Open Directory IP Address | 167.71.173_239 |
| Port | 8111 |
| Acunetix Certificate SHA-1 Fingerprint | efbfbd12efbfbd69efbfbd6b45efbfbd76efbfbd0befbfbd2eefbfbd |
| Python Script SHA-256 Hashes | run.py - 016344d35f6f217f9f8b483dacb8154b45139355bcc45a3f94910351b5df42b5 fuzz.py - f527ea33f22293d99a5687fc13595c84830d6f2c52add1f08e49fbf607458251 burp.py-934e9336d45771a74de544be31e3dc8ec624891c5fc95a36d9ec124b39c4e5c7 bp.py - 4ad4d5edd434f8269cdf5511667364962dff7f2535ae13cd8102c6acde061a19 |
Related Posts
Related Posts
Related Posts


