From Munitions to Malware: Interview with Joseph Harrison About His Path to Threat Intelligence
From Munitions to Malware: Interview with Joseph Harrison About His Path to Threat Intelligence
Published on

Cybersecurity threats rarely show themselves in obvious ways. They hide inside ordinary activity, borrowing legitimate tools, and waiting for the right moment to strike. Finding those traces requires not only strong technical skills but also the persistence to keep digging and the judgment to know when something doesn't quite add up.
That's the space Joseph Harrison works in every day. As a threat lead, he guides investigations, shapes detection strategies, and helps organizations stay one step ahead of adversaries who are constantly evolving their tactics. Part of his intuition comes from years of hands-on technical work, but another part traces back to his Air Force days, where attention to detail and discipline were not optional but essential.
In this interview, Joseph walks us through what that looks like in practice, from the challenges of separating signal from noise to the ways he and his team turn clues into defenses.

Can you share your earliest exposure to forensics and how your father influenced your transition from traditional to digital forensics?
Joseph: My earliest introduction to forensics was through my father, who worked as a detective. That, combined with my interest in technology and helping people, made me start thinking seriously about a career in criminal forensics. Over time, an increasing interest in computing led to an exploration of digital forensics, with guidance from my father regarding its place within the broader forensic discipline. As I dug deeper into digital forensics, I realized cybersecurity was where I really wanted to focus my career.
What led you to join the United States Air Force, and what role did you serve there?
Joseph: My primary motivation for joining the Air Force was to further my education. I was committed to pursuing a career in Cybersecurity, which required me to gain additional knowledge and earn a degree. The Air Force also provided valuable opportunities to develop essential soft skills such as followership, leadership, and other essential skills that continue to benefit me professionally.
During my service, I worked within the Munitions Systems career field, where I was responsible for building, inspecting, maintaining, and delivering all the munitions used by the base. Concurrently, I was studying Information Technology with a focus on Cybersecurity. My dedication to these studies was recognized by my superiors, who subsequently assigned me to a systems administration position within my unit in addition to my primary duties.
How did your experience as a Systems Administrator in the Air Force prepare you for your later work in cybersecurity and digital forensics?
Joseph: Two key experiences that contributed significantly were the development of attention to detail and a strong security mindset. In this position, responsibilities extended beyond system maintenance to precise tracking of munitions, regardless of quantity or size. This meticulous approach is directly applicable to cybersecurity and digital forensics, where identifying specific data among vast amounts of information is essential.
Additionally, the role reinforced the importance of a security-oriented perspective. Every user's credentials and access levels required verification, whether they were familiar or not. This practice aligns closely with established cybersecurity methodologies such as least privilege and zero trust principles.
Are there any particular lessons from your military service that you still apply to your work today?
Joseph: Beyond technical abilities, I consider the soft skills gained in the military my most valuable lessons. I attended leadership courses, led operations, mentored and trained others, and learned to work effectively within a diverse team.

You've been at EY for over three years. Can you walk us through what your typical day looks like as a Threat Detection Operations Lead?
Joseph: During my tenure at EY, I have gained over three years of experience as a Threat Detection & Response Senior Analyst. In my current capacity, I serve as the Operations Lead for a major healthcare client and provide senior analytical support to a government client. My day typically begins with reviewing emails and messages received overnight from our 24/7 monitoring operations. These communications often involve queries concerning investigation procedures, ticket management, triage issues, and technical challenges related to tools or log sources.
Subsequently, I address client deliverables and prepare presentations as required. In addition, I routinely conduct investigations into complex alerts and support clients with ticket resolutions. When clients' security teams face uncertainty regarding next steps after initial triage and investigation, I provide in-depth technical analysis and recommendations for remediation.
I lead threat hunting operations for my client, leveraging internal, open source, and client-provided threat intelligence to gather IOCs. Our team conducts at least two hunts weekly, using automation to process large volumes of IOCs, followed by manual review of findings. We also perform ad-hoc investigations to address emerging threats and ensure client risks are promptly managed.
A portion of my responsibilities includes developing and refining detection signatures, as well as tuning them according to client feedback and validation. I continuously develop new detections to address emerging threats.
Furthermore, I am dedicated to continuous improvement initiatives aimed at enhancing our clients' security posture, ranging from implementing new logging mechanisms to integrating advanced machine learning solutions such as UEBA. Notably, following our work piloting Splunk UEBA for a client, my senior manager and I presented on this topic at Splunk Conf25. You can find that talk here.
What are the biggest challenges you face in leading and optimizing SOC operations?
Joseph: Visibility is essential in SOC activities. The more detailed the logs, the stronger our detection and response capabilities become. However, enabling verbose logging can be costly for organizations, representing an ongoing challenge. Our objective is to prioritize and ingest logs that offer high value while maintaining low volume to manage costs efficiently, though this balance is not always achievable. We frequently collaborate with clients to reduce unnecessary log collection and optimize cost savings. Additionally, we offer recommendations and support for implementing solutions to enhance log source management.
From a technical standpoint, one persistent challenge within SOC operations across all organizations is addressing "Living off the Land" threats. These threats leverage native tools or legitimate applications for malicious purposes, enabling attackers to blend seamlessly with standard business operations.
This poses significant detection difficulties; for example, monitoring PowerShell usage often results in identifying numerous system administrators and backend processes employing the tool appropriately. Differentiating genuine activity from anomalies and suspicious behavior is complex and often requires extensive manual analysis, machine learning models, and other similar efforts.
Currently, we are partnering with a client on a large-scale initiative focused on threat hunting, detection development, and establishing future-oriented detection and prevention capabilities. I have identified nearly 250 unique indicators for our hunt and detection efforts, covering the most prevalent and high-risk activities. Nevertheless, there remain countless other tactics available to threat actors.

In your view, what distinguishes a great threat hunter from a good one?
Joseph: Standing out in threat hunting, digital forensics, SOC operations, and other cybersecurity tasks requires understanding the current threat landscape. My key advice to anyone is to stay updated on threats relevant to your sector.
This awareness helps you spot unusual data that may warrant deeper investigation, a crucial but challenging step. Focus on likely or emerging threats to your organization; as you learn their tactics, suspicious patterns will become more apparent and guide your investigations. You will start coming across things that just "feel off", and once you pull on those threads, you will be more likely to find malicious or suspicious activity.
You will start coming across things that just "feel off", and once you pull on those threads, you will be more likely to find malicious or suspicious activity.
Can you walk us through an example of a particularly challenging threat hunt you've conducted?
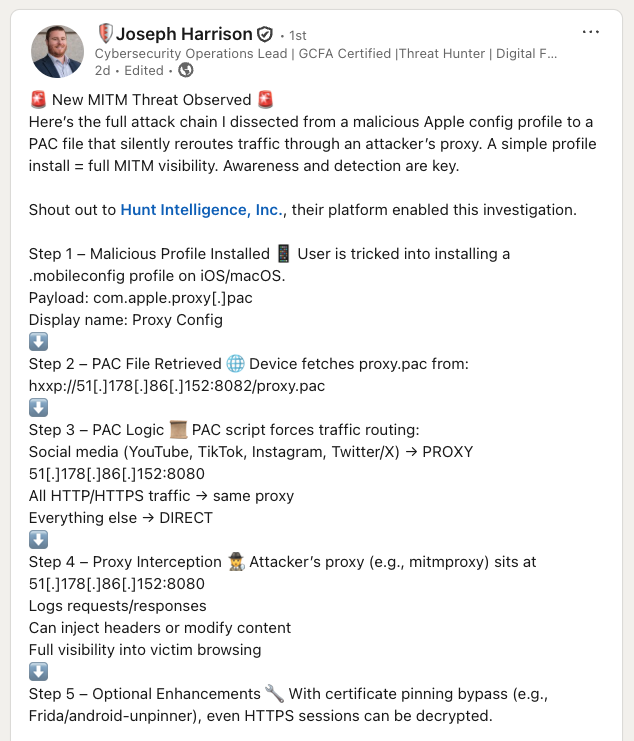
Joseph: A recent investigation involved a malicious PowerShell script executed on a system. Our EDR solution generated an alert indicating that a PowerShell command had been initiated by a user and was successfully blocked. Upon review, the command was identified as a typical PowerShell download cradle designed to retrieve malicious files.
When the alert was discussed with the user, they denied any knowledge of the command or suspicious activity on their device, including email or other channels. At this point, the client requested further guidance regarding the appropriate response. With the script and associated URL already blocked, determining the root cause became essential for complete containment and remediation.
Analysis of the process tree in the EDR alert revealed that the grandparent process was explorer.exe, followed by CMD, which subsequently launched PowerShell. This progression suggested manual user interaction, as explorer.exe being involved typically indicates direct input.
Additionally, seeing CMD as a parent process of PowerShell is atypical and rarely occurs autonomously, supporting the likelihood of manual execution. This hypothesis was validated through additional data points, effectively ruling out automated causes. The observed process chain is consistent with ClickFix attacks, where users are tricked into pasting commands into the Win+R dialog box, part of explorer.exe.
With evidence pointing to a phishing attempt leveraging ClickFix, I proceeded to analyze network traffic from the affected user's machine corresponding to the timeframe of the incident.
This analysis surfaced a single suspicious domain and URL. Further exploration in a sandbox environment confirmed that the site was a sophisticated phishing page impersonating a well-known brand. This strengthened confidence in the assessment that a ClickFix-based phishing attack had occurred.
The investigation continued by extracting new indicators, specifically the domain and hosting IP address, and enriching this information using tools such as Hunt.io. Hunt.io corroborated that the site was indeed associated with phishing activities.
Additional research linked the threat to a recognized RAT deployment campaign utilizing ClickFix tactics, as documented in various tools and social media reports. Further connections were identified, revealing other phishing-related domains and URLs associated with the offending IP and domain.
A comprehensive search for these new indicators across the environment found no additional threats. The findings were promptly communicated to the client, who subsequently blocked the newly discovered indicators to mitigate future risks.
How do you approach collecting and analyzing digital evidence in high-pressure incident response situations?
Joseph: When responding to an incident, containment and scoping are key once you understand the threat. Focus on collecting logs that reveal the threat's actions and movements in your environment to determine the extent of compromise.
We gather all necessary telemetry and logs for our clients' tech stacks, but if any data is missing, various collection methods are available to supplement logging. You will want to do these actions without alerting the actors that you are now onto their actions. This is to prevent them from changing tactics and once again evading detection.
How do you incorporate Hunt.io into your standard workflow?
Joseph: As mentioned previously, I frequently use Hunt.io to look up indicators and gather related information. When indicators have open directories that Hunt.io reveals, it provides a unique access to view hosted files and obtain further details about the nature of potential threats.
Additionally, I use this platform to send intelligence to my personal CTI platform, where I collect threat intelligence for review, analysis, and application in investigations or for developing threat hunts for my team.
Could you share an example of how Hunt.io helped uncover a threat that other tools might have missed?
Joseph: Years ago, I joined early testing for Hunt.io and quickly realized the platform tracked JA4 signatures, rare indicators of application use. After spotting alerts for a malicious IP, I matched its JA4 signatures to those in my environment, which led to discovering possible malware. My team then compiled a list of known malicious signatures, blocked them, and set up monitoring rules. I still rely on Hunt.io's JA4 data in investigations, as it highlights encrypted traffic patterns that help pinpoint malicious infrastructure faster and with greater confidence - often surfacing activity that other platforms overlook.
For security professionals new to Hunt.io, what are the first three things they should learn or set up to get the most out of it?
Joseph: For security professionals who are new to Hunt.io, the initial steps should include reviewing the API integrations and functions compatible with existing technology stacks to enable effective data integration. I would recommend navigating through all available sections of the platform to become familiar with its features and the different methods for expanding or pivoting investigations, especially HuntSQL™, and the C2 detection listing, which are key areas for uncovering active infrastructure.
You do not have to be an expert in each part, but knowing what is possible will be helpful, so that you know where to go when you need it. Additionally, understanding how open directories function within Hunt.io can be beneficial, as they represent a significant feature of the platform that I think sets this tool apart from others.
I still rely on Hunt.io's JA4 data in investigations, as it highlights encrypted traffic patterns that help pinpoint malicious infrastructure faster and with greater confidence - often surfacing activity that other platforms overlook.
Are there any advanced Hunt.io features or workflows you've developed that you'd consider "power tips"?
Joseph: Beyond previously mentioned workflows, don't hesitate to explore the platform frequently, as it provides valuable information for expanding threat investigations. For instance, a client discovered a vendor's script connecting to a malicious IP. After initial actions, I used Hunt.io to investigate further, uncovering that the IP hosted legitimate and fraudulent GitHub sites as well as StealC malware. I searched related domains in our environment, gathered StealC IOCs, and conducted a threat hunt with my team.
How do you balance automation with human analysis in your threat detection work?
Joseph: The degree of human involvement required in automation depends on the specific use case and its requirements.
For example, certain alerts that clients have requested involve sending a notification ticket to inform other teams and facilitate workflow processes and action tracking; These situations do not require a SOC investigation and are ideal candidates for full automation, since the task involves only transmitting relevant alert data. In contrast, actions such as implementing IOC blocks undergo manual review by an analyst prior to automated enforcement across the technology stack.
High-impact activities such as blocking a valid domain should always include a human checkpoint within the automation process. Conversely, tasks that carry lower risk or demand maximum speed may be effectively managed through end-to-end automation. This also depends on your team's level of expertise in automation. If you can fine-tune automation triggers and workflows seamlessly, you are able to automate more tasks without a human involved.
What advice would you give to aspiring cybersecurity professionals who want to specialize in threat hunting or digital forensics?
Joseph: Understanding the current threat landscape helps threat hunters and digital forensics professionals identify key data and uncover leads during investigations. However, too many leads can distract from finding relevant threats, so it's important to work with knowledgeable peers and leaders to stay focused.
Always ask questions and pay attention to details, as these often lead to valuable insights in threat hunting and forensic work. I would also be remiss if I did not include advice to set up your own home lab. It's said often, but that is for a reason. Setting up your own lab to explore detections, artifacts, processes, etc., is extremely valuable.
Recently, I have been exploring attack automation tools and seeing what detections I can get to fire in my lab and then investigate or hunt for artifacts that were not detected, as well as conduct forensics on the target system. Another great example from my home lab is that for the last few years, I have been working on PowerShell logging and detections. I did all my testing for this in my home lab before taking it to clients, and the list goes on. Feel free to reach out to me if you have any questions on setting up a lab or anything else!
Cybersecurity threats rarely show themselves in obvious ways. They hide inside ordinary activity, borrowing legitimate tools, and waiting for the right moment to strike. Finding those traces requires not only strong technical skills but also the persistence to keep digging and the judgment to know when something doesn't quite add up.
That's the space Joseph Harrison works in every day. As a threat lead, he guides investigations, shapes detection strategies, and helps organizations stay one step ahead of adversaries who are constantly evolving their tactics. Part of his intuition comes from years of hands-on technical work, but another part traces back to his Air Force days, where attention to detail and discipline were not optional but essential.
In this interview, Joseph walks us through what that looks like in practice, from the challenges of separating signal from noise to the ways he and his team turn clues into defenses.

Can you share your earliest exposure to forensics and how your father influenced your transition from traditional to digital forensics?
Joseph: My earliest introduction to forensics was through my father, who worked as a detective. That, combined with my interest in technology and helping people, made me start thinking seriously about a career in criminal forensics. Over time, an increasing interest in computing led to an exploration of digital forensics, with guidance from my father regarding its place within the broader forensic discipline. As I dug deeper into digital forensics, I realized cybersecurity was where I really wanted to focus my career.
What led you to join the United States Air Force, and what role did you serve there?
Joseph: My primary motivation for joining the Air Force was to further my education. I was committed to pursuing a career in Cybersecurity, which required me to gain additional knowledge and earn a degree. The Air Force also provided valuable opportunities to develop essential soft skills such as followership, leadership, and other essential skills that continue to benefit me professionally.
During my service, I worked within the Munitions Systems career field, where I was responsible for building, inspecting, maintaining, and delivering all the munitions used by the base. Concurrently, I was studying Information Technology with a focus on Cybersecurity. My dedication to these studies was recognized by my superiors, who subsequently assigned me to a systems administration position within my unit in addition to my primary duties.
How did your experience as a Systems Administrator in the Air Force prepare you for your later work in cybersecurity and digital forensics?
Joseph: Two key experiences that contributed significantly were the development of attention to detail and a strong security mindset. In this position, responsibilities extended beyond system maintenance to precise tracking of munitions, regardless of quantity or size. This meticulous approach is directly applicable to cybersecurity and digital forensics, where identifying specific data among vast amounts of information is essential.
Additionally, the role reinforced the importance of a security-oriented perspective. Every user's credentials and access levels required verification, whether they were familiar or not. This practice aligns closely with established cybersecurity methodologies such as least privilege and zero trust principles.
Are there any particular lessons from your military service that you still apply to your work today?
Joseph: Beyond technical abilities, I consider the soft skills gained in the military my most valuable lessons. I attended leadership courses, led operations, mentored and trained others, and learned to work effectively within a diverse team.

You've been at EY for over three years. Can you walk us through what your typical day looks like as a Threat Detection Operations Lead?
Joseph: During my tenure at EY, I have gained over three years of experience as a Threat Detection & Response Senior Analyst. In my current capacity, I serve as the Operations Lead for a major healthcare client and provide senior analytical support to a government client. My day typically begins with reviewing emails and messages received overnight from our 24/7 monitoring operations. These communications often involve queries concerning investigation procedures, ticket management, triage issues, and technical challenges related to tools or log sources.
Subsequently, I address client deliverables and prepare presentations as required. In addition, I routinely conduct investigations into complex alerts and support clients with ticket resolutions. When clients' security teams face uncertainty regarding next steps after initial triage and investigation, I provide in-depth technical analysis and recommendations for remediation.
I lead threat hunting operations for my client, leveraging internal, open source, and client-provided threat intelligence to gather IOCs. Our team conducts at least two hunts weekly, using automation to process large volumes of IOCs, followed by manual review of findings. We also perform ad-hoc investigations to address emerging threats and ensure client risks are promptly managed.
A portion of my responsibilities includes developing and refining detection signatures, as well as tuning them according to client feedback and validation. I continuously develop new detections to address emerging threats.
Furthermore, I am dedicated to continuous improvement initiatives aimed at enhancing our clients' security posture, ranging from implementing new logging mechanisms to integrating advanced machine learning solutions such as UEBA. Notably, following our work piloting Splunk UEBA for a client, my senior manager and I presented on this topic at Splunk Conf25. You can find that talk here.
What are the biggest challenges you face in leading and optimizing SOC operations?
Joseph: Visibility is essential in SOC activities. The more detailed the logs, the stronger our detection and response capabilities become. However, enabling verbose logging can be costly for organizations, representing an ongoing challenge. Our objective is to prioritize and ingest logs that offer high value while maintaining low volume to manage costs efficiently, though this balance is not always achievable. We frequently collaborate with clients to reduce unnecessary log collection and optimize cost savings. Additionally, we offer recommendations and support for implementing solutions to enhance log source management.
From a technical standpoint, one persistent challenge within SOC operations across all organizations is addressing "Living off the Land" threats. These threats leverage native tools or legitimate applications for malicious purposes, enabling attackers to blend seamlessly with standard business operations.
This poses significant detection difficulties; for example, monitoring PowerShell usage often results in identifying numerous system administrators and backend processes employing the tool appropriately. Differentiating genuine activity from anomalies and suspicious behavior is complex and often requires extensive manual analysis, machine learning models, and other similar efforts.
Currently, we are partnering with a client on a large-scale initiative focused on threat hunting, detection development, and establishing future-oriented detection and prevention capabilities. I have identified nearly 250 unique indicators for our hunt and detection efforts, covering the most prevalent and high-risk activities. Nevertheless, there remain countless other tactics available to threat actors.

In your view, what distinguishes a great threat hunter from a good one?
Joseph: Standing out in threat hunting, digital forensics, SOC operations, and other cybersecurity tasks requires understanding the current threat landscape. My key advice to anyone is to stay updated on threats relevant to your sector.
This awareness helps you spot unusual data that may warrant deeper investigation, a crucial but challenging step. Focus on likely or emerging threats to your organization; as you learn their tactics, suspicious patterns will become more apparent and guide your investigations. You will start coming across things that just "feel off", and once you pull on those threads, you will be more likely to find malicious or suspicious activity.
You will start coming across things that just "feel off", and once you pull on those threads, you will be more likely to find malicious or suspicious activity.
Can you walk us through an example of a particularly challenging threat hunt you've conducted?
Joseph: A recent investigation involved a malicious PowerShell script executed on a system. Our EDR solution generated an alert indicating that a PowerShell command had been initiated by a user and was successfully blocked. Upon review, the command was identified as a typical PowerShell download cradle designed to retrieve malicious files.
When the alert was discussed with the user, they denied any knowledge of the command or suspicious activity on their device, including email or other channels. At this point, the client requested further guidance regarding the appropriate response. With the script and associated URL already blocked, determining the root cause became essential for complete containment and remediation.
Analysis of the process tree in the EDR alert revealed that the grandparent process was explorer.exe, followed by CMD, which subsequently launched PowerShell. This progression suggested manual user interaction, as explorer.exe being involved typically indicates direct input.
Additionally, seeing CMD as a parent process of PowerShell is atypical and rarely occurs autonomously, supporting the likelihood of manual execution. This hypothesis was validated through additional data points, effectively ruling out automated causes. The observed process chain is consistent with ClickFix attacks, where users are tricked into pasting commands into the Win+R dialog box, part of explorer.exe.
With evidence pointing to a phishing attempt leveraging ClickFix, I proceeded to analyze network traffic from the affected user's machine corresponding to the timeframe of the incident.
This analysis surfaced a single suspicious domain and URL. Further exploration in a sandbox environment confirmed that the site was a sophisticated phishing page impersonating a well-known brand. This strengthened confidence in the assessment that a ClickFix-based phishing attack had occurred.
The investigation continued by extracting new indicators, specifically the domain and hosting IP address, and enriching this information using tools such as Hunt.io. Hunt.io corroborated that the site was indeed associated with phishing activities.
Additional research linked the threat to a recognized RAT deployment campaign utilizing ClickFix tactics, as documented in various tools and social media reports. Further connections were identified, revealing other phishing-related domains and URLs associated with the offending IP and domain.
A comprehensive search for these new indicators across the environment found no additional threats. The findings were promptly communicated to the client, who subsequently blocked the newly discovered indicators to mitigate future risks.
How do you approach collecting and analyzing digital evidence in high-pressure incident response situations?
Joseph: When responding to an incident, containment and scoping are key once you understand the threat. Focus on collecting logs that reveal the threat's actions and movements in your environment to determine the extent of compromise.
We gather all necessary telemetry and logs for our clients' tech stacks, but if any data is missing, various collection methods are available to supplement logging. You will want to do these actions without alerting the actors that you are now onto their actions. This is to prevent them from changing tactics and once again evading detection.
How do you incorporate Hunt.io into your standard workflow?
Joseph: As mentioned previously, I frequently use Hunt.io to look up indicators and gather related information. When indicators have open directories that Hunt.io reveals, it provides a unique access to view hosted files and obtain further details about the nature of potential threats.
Additionally, I use this platform to send intelligence to my personal CTI platform, where I collect threat intelligence for review, analysis, and application in investigations or for developing threat hunts for my team.
Could you share an example of how Hunt.io helped uncover a threat that other tools might have missed?
Joseph: Years ago, I joined early testing for Hunt.io and quickly realized the platform tracked JA4 signatures, rare indicators of application use. After spotting alerts for a malicious IP, I matched its JA4 signatures to those in my environment, which led to discovering possible malware. My team then compiled a list of known malicious signatures, blocked them, and set up monitoring rules. I still rely on Hunt.io's JA4 data in investigations, as it highlights encrypted traffic patterns that help pinpoint malicious infrastructure faster and with greater confidence - often surfacing activity that other platforms overlook.
For security professionals new to Hunt.io, what are the first three things they should learn or set up to get the most out of it?
Joseph: For security professionals who are new to Hunt.io, the initial steps should include reviewing the API integrations and functions compatible with existing technology stacks to enable effective data integration. I would recommend navigating through all available sections of the platform to become familiar with its features and the different methods for expanding or pivoting investigations, especially HuntSQL™, and the C2 detection listing, which are key areas for uncovering active infrastructure.
You do not have to be an expert in each part, but knowing what is possible will be helpful, so that you know where to go when you need it. Additionally, understanding how open directories function within Hunt.io can be beneficial, as they represent a significant feature of the platform that I think sets this tool apart from others.
I still rely on Hunt.io's JA4 data in investigations, as it highlights encrypted traffic patterns that help pinpoint malicious infrastructure faster and with greater confidence - often surfacing activity that other platforms overlook.
Are there any advanced Hunt.io features or workflows you've developed that you'd consider "power tips"?
Joseph: Beyond previously mentioned workflows, don't hesitate to explore the platform frequently, as it provides valuable information for expanding threat investigations. For instance, a client discovered a vendor's script connecting to a malicious IP. After initial actions, I used Hunt.io to investigate further, uncovering that the IP hosted legitimate and fraudulent GitHub sites as well as StealC malware. I searched related domains in our environment, gathered StealC IOCs, and conducted a threat hunt with my team.
How do you balance automation with human analysis in your threat detection work?
Joseph: The degree of human involvement required in automation depends on the specific use case and its requirements.
For example, certain alerts that clients have requested involve sending a notification ticket to inform other teams and facilitate workflow processes and action tracking; These situations do not require a SOC investigation and are ideal candidates for full automation, since the task involves only transmitting relevant alert data. In contrast, actions such as implementing IOC blocks undergo manual review by an analyst prior to automated enforcement across the technology stack.
High-impact activities such as blocking a valid domain should always include a human checkpoint within the automation process. Conversely, tasks that carry lower risk or demand maximum speed may be effectively managed through end-to-end automation. This also depends on your team's level of expertise in automation. If you can fine-tune automation triggers and workflows seamlessly, you are able to automate more tasks without a human involved.
What advice would you give to aspiring cybersecurity professionals who want to specialize in threat hunting or digital forensics?
Joseph: Understanding the current threat landscape helps threat hunters and digital forensics professionals identify key data and uncover leads during investigations. However, too many leads can distract from finding relevant threats, so it's important to work with knowledgeable peers and leaders to stay focused.
Always ask questions and pay attention to details, as these often lead to valuable insights in threat hunting and forensic work. I would also be remiss if I did not include advice to set up your own home lab. It's said often, but that is for a reason. Setting up your own lab to explore detections, artifacts, processes, etc., is extremely valuable.
Recently, I have been exploring attack automation tools and seeing what detections I can get to fire in my lab and then investigate or hunt for artifacts that were not detected, as well as conduct forensics on the target system. Another great example from my home lab is that for the last few years, I have been working on PowerShell logging and detections. I did all my testing for this in my home lab before taking it to clients, and the list goes on. Feel free to reach out to me if you have any questions on setting up a lab or anything else!
Related Posts
Related Posts
Related Posts