Hunting PrismX: Techniques for Network Discovery
Published on

Introduction
Described on its GitHub README as an "Integrated lightweight cross-platform penetration system," PrismX goes beyond basic vulnerability scanning, offering an exploitation engine, a shellcode generator, and even an SMTP server for sending emails. It also integrates with Qi An Xin's Hunter platform and allows users to develop and upload vulnerabilities via plugins.
Available for download on MacOS, Windows, and Linux through GitHub or their website, PrismX is a comprehensive toolkit for penetration testers on various platforms. However, it's important to remember that such powerful tools can be misused in the wrong hands.
This post will explore methods (maybe unconventional for an open-source project) to identify active PrismX deployments, empowering defenders and security researchers to stay ahead of potential threats.
PrismX
 Figure 1: PrismX GitHub README (https://github.com/yqcs/prismx)
Figure 1: PrismX GitHub README (https://github.com/yqcs/prismx)As this is an open-source project hosted on GitHub, our research typically starts with a source code review, identifying any text related to network communications. To delve deeper into PrismX's network footprint, we'll fire up a virtual machine, deploy the tool in a controlled environment, and leverage some Python to analyze its HTTP responses for potential identification methods.
Reading the project's guide, we see two options for using PrismX: webpage and command line. As seen below in Figure 2, the login page runs on port 443 by default, and the author has also included the username and password for first-time users.
 Figure 2: PrismX Guide (https://github.com/yqcs/prismx)
Figure 2: PrismX Guide (https://github.com/yqcs/prismx)While simply searching for port 443 connections, mentioning "PrismX" in the HTML might seem like a quick win, this approach has limitations. First, it may generate false positives due to similar project names. Second, bypassing the hands-on experience of running the software (in a safe environment) can lead to missed learning and detection opportunities.
If you're following along, remember to always run untrusted software in a fully patched, isolated VM with a clean snapshot for easy rollback. Before downloading or executing any software, a quick code review is recommended.
Let's move to a VM and see what we can find.
A Little Python Goes A Long Way
Getting PrismX up and running was relatively seamless, with no hidden dependencies on Ubuntu.
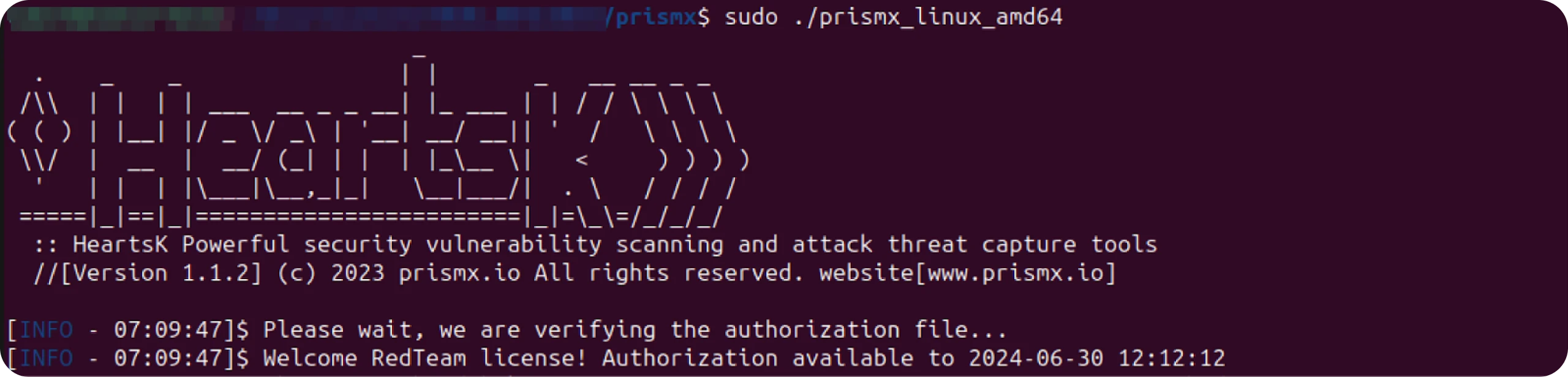 Figure 3: PrismX running in a lab environment
Figure 3: PrismX running in a lab environmentThis repo was previously under a different name, HeartsK, as seen in Figure 3. Running PrismX seems successful so far from the terminal; let's move to a browser and check out the login page.
 Figure 4: PrismX login page
Figure 4: PrismX login page Figure 5: Default self-signed certificate
Figure 5: Default self-signed certificateWhile a deeper dive into PrismX's functionalities might be on the horizon, for now, the self-signed certificate revealed by the lock symbol provides a valuable starting point. Let's leverage Python's Requests library to analyze the login page's HTTP response and webpage content for unique identifiers that could aid detection.
 Figure 6: Python Requests library results for the login page
Figure 6: Python Requests library results for the login pageBefore venturing further, let's pause and consolidate our findings. Here's a quick rundown of the potential detection points we've unearthed so far:
Login page title: Prism X
Self-signed certificate: Country AU, State/Province: Some-State, Organization: Internet Widgits Pty Ltd (JARM or JA4X hash)
No common name associated with the certificate
HTTP response headers hash
Hash of the login page HTML
I'm curious to see what creative search queries the community comes up with to pinpoint PrismX login pages. A pseudo query I am currently using:
"jarm = '3fd21b20d00000021c43d21b21b43d76e1f79b8645e08ae7fa8f07eb5e4202' and HTTP response headers SHA256 hash: 'cf8e3dfb6292ae09f55df22211db7de7bbbcd5a488bf2b21ec0a1af5598f01e7'"
The above has successfully identified relevant pages without generating false positives. One could also simply search for the hash of the HTTP headers and look for webpage titles containing "Prism X." Remember that with open-source projects, it is trivial for a red teamer (or attacker) to change the title and throw off your whole query.
Let's Fire Up Hunt!
To wrap things up, here are two examples of servers I found hosting PrismX login pages (DISCLAIMER: Do not attempt to access these servers without proper authorization). When interacting with malicious infrastructure, you should be quick and deliberate and try to blend in to avoid drawing attention.
 Figure 7: Hunt history tab for IP hosting PrismX
Figure 7: Hunt history tab for IP hosting PrismXAnalyzing the port and certificate history of the above IP, we can confirm the presence of the same JARM hash as earlier in our sample query. Additionally, the server appeared to be hosting a Cobalt Strike team server, suggesting a potential multi-tool deployment.
 Figure 8: Cobalt Strike associations by watermark
Figure 8: Cobalt Strike associations by watermarkMoving to the Associations tab, we can quickly identify additional infrastructure based on the Cobalt Strike watermark. Hunt finds 111 other instances of the red team framework. It is a large cluster, but more research is necessary to highlight possible relationships.
We'll quickly cover one more IP below and finish up this post.
 Figure 9: IP address tagged by Hunt as using Cobalt Strike
Figure 9: IP address tagged by Hunt as using Cobalt StrikeI wanted to include a screenshot of the HTTP response headers and HTML, readily available in Hunt, by simply clicking on the magnifying glass to the right of the identified port and service.
As with our previous server, we can see at the bottom of Figure 9 (indicated by the red arrow) that a deployment of Cobalt Strike was also identified.
Conclusion
In this post, I provided a glimpse into identifying potential PrismX deployments. We journeyed from a basic introduction to delving into the tool's inner workings within a secure lab environment. By leveraging Python's Requests library, we uncovered initial detection points through unique characteristics. We even stumbled upon real-world examples, highlighting the potential for multi-tool deployments alongside PrismX.
The security landscape is ever-evolving, and so should your defenses. For those who haven't already, consider applying for an account with Hunt. We're building a powerful platform to empower security professionals with advanced threat intelligence and hunting capabilities, aiding in the fight against ever-more sophisticated attacks.
Introduction
Described on its GitHub README as an "Integrated lightweight cross-platform penetration system," PrismX goes beyond basic vulnerability scanning, offering an exploitation engine, a shellcode generator, and even an SMTP server for sending emails. It also integrates with Qi An Xin's Hunter platform and allows users to develop and upload vulnerabilities via plugins.
Available for download on MacOS, Windows, and Linux through GitHub or their website, PrismX is a comprehensive toolkit for penetration testers on various platforms. However, it's important to remember that such powerful tools can be misused in the wrong hands.
This post will explore methods (maybe unconventional for an open-source project) to identify active PrismX deployments, empowering defenders and security researchers to stay ahead of potential threats.
PrismX
 Figure 1: PrismX GitHub README (https://github.com/yqcs/prismx)
Figure 1: PrismX GitHub README (https://github.com/yqcs/prismx)As this is an open-source project hosted on GitHub, our research typically starts with a source code review, identifying any text related to network communications. To delve deeper into PrismX's network footprint, we'll fire up a virtual machine, deploy the tool in a controlled environment, and leverage some Python to analyze its HTTP responses for potential identification methods.
Reading the project's guide, we see two options for using PrismX: webpage and command line. As seen below in Figure 2, the login page runs on port 443 by default, and the author has also included the username and password for first-time users.
 Figure 2: PrismX Guide (https://github.com/yqcs/prismx)
Figure 2: PrismX Guide (https://github.com/yqcs/prismx)While simply searching for port 443 connections, mentioning "PrismX" in the HTML might seem like a quick win, this approach has limitations. First, it may generate false positives due to similar project names. Second, bypassing the hands-on experience of running the software (in a safe environment) can lead to missed learning and detection opportunities.
If you're following along, remember to always run untrusted software in a fully patched, isolated VM with a clean snapshot for easy rollback. Before downloading or executing any software, a quick code review is recommended.
Let's move to a VM and see what we can find.
A Little Python Goes A Long Way
Getting PrismX up and running was relatively seamless, with no hidden dependencies on Ubuntu.
 Figure 3: PrismX running in a lab environment
Figure 3: PrismX running in a lab environmentThis repo was previously under a different name, HeartsK, as seen in Figure 3. Running PrismX seems successful so far from the terminal; let's move to a browser and check out the login page.
 Figure 4: PrismX login page
Figure 4: PrismX login page Figure 5: Default self-signed certificate
Figure 5: Default self-signed certificateWhile a deeper dive into PrismX's functionalities might be on the horizon, for now, the self-signed certificate revealed by the lock symbol provides a valuable starting point. Let's leverage Python's Requests library to analyze the login page's HTTP response and webpage content for unique identifiers that could aid detection.
 Figure 6: Python Requests library results for the login page
Figure 6: Python Requests library results for the login pageBefore venturing further, let's pause and consolidate our findings. Here's a quick rundown of the potential detection points we've unearthed so far:
Login page title: Prism X
Self-signed certificate: Country AU, State/Province: Some-State, Organization: Internet Widgits Pty Ltd (JARM or JA4X hash)
No common name associated with the certificate
HTTP response headers hash
Hash of the login page HTML
I'm curious to see what creative search queries the community comes up with to pinpoint PrismX login pages. A pseudo query I am currently using:
"jarm = '3fd21b20d00000021c43d21b21b43d76e1f79b8645e08ae7fa8f07eb5e4202' and HTTP response headers SHA256 hash: 'cf8e3dfb6292ae09f55df22211db7de7bbbcd5a488bf2b21ec0a1af5598f01e7'"
The above has successfully identified relevant pages without generating false positives. One could also simply search for the hash of the HTTP headers and look for webpage titles containing "Prism X." Remember that with open-source projects, it is trivial for a red teamer (or attacker) to change the title and throw off your whole query.
Let's Fire Up Hunt!
To wrap things up, here are two examples of servers I found hosting PrismX login pages (DISCLAIMER: Do not attempt to access these servers without proper authorization). When interacting with malicious infrastructure, you should be quick and deliberate and try to blend in to avoid drawing attention.
 Figure 7: Hunt history tab for IP hosting PrismX
Figure 7: Hunt history tab for IP hosting PrismXAnalyzing the port and certificate history of the above IP, we can confirm the presence of the same JARM hash as earlier in our sample query. Additionally, the server appeared to be hosting a Cobalt Strike team server, suggesting a potential multi-tool deployment.
 Figure 8: Cobalt Strike associations by watermark
Figure 8: Cobalt Strike associations by watermarkMoving to the Associations tab, we can quickly identify additional infrastructure based on the Cobalt Strike watermark. Hunt finds 111 other instances of the red team framework. It is a large cluster, but more research is necessary to highlight possible relationships.
We'll quickly cover one more IP below and finish up this post.
 Figure 9: IP address tagged by Hunt as using Cobalt Strike
Figure 9: IP address tagged by Hunt as using Cobalt StrikeI wanted to include a screenshot of the HTTP response headers and HTML, readily available in Hunt, by simply clicking on the magnifying glass to the right of the identified port and service.
As with our previous server, we can see at the bottom of Figure 9 (indicated by the red arrow) that a deployment of Cobalt Strike was also identified.
Conclusion
In this post, I provided a glimpse into identifying potential PrismX deployments. We journeyed from a basic introduction to delving into the tool's inner workings within a secure lab environment. By leveraging Python's Requests library, we uncovered initial detection points through unique characteristics. We even stumbled upon real-world examples, highlighting the potential for multi-tool deployments alongside PrismX.
The security landscape is ever-evolving, and so should your defenses. For those who haven't already, consider applying for an account with Hunt. We're building a powerful platform to empower security professionals with advanced threat intelligence and hunting capabilities, aiding in the fight against ever-more sophisticated attacks.
Related Posts
Related Posts
Related Posts


