Into the Viper’s Nest: Observations from Hunt’s Scanning
Into the Viper’s Nest: Observations from Hunt’s Scanning
Published on
May 8, 2024



Introduction
From initial access and privilege escalation to lateral movement and data collection, the open-source platform Viper boasts over 80 modules designed to streamline the stages of an attack, making it a preferred tool for red teams and threat actors alike.
Additional features like anti-virus bypass, intranet tunneling, command-line operations, and custom payload generation lower the technical barriers, allowing many bad actors to conduct network exploitation operations efficiently.
In this post, we'll look at Viper's widespread use across countries and ASNs, detail some approaches to detecting its login pages, and discuss other tools used alongside Viper, such as Cobalt Strike, Sliver, and Yakit.
Viper
 Figure 1: Viper README
Figure 1: Viper READMEThe introduction covered many of Viper's features; what's unique about this tool is that the operator is provided with a GUI similar to Cobalt Strike. The platform's administrative section is protected by a login page, which many have left open to the internet.
Hunt is tracking over 400 unique IP addresses hosting Viper login pages. Figure 2 below shows an example.
 Figure 2: Example Viper login page
Figure 2: Example Viper login pageHosting details for Viper are readily accessible through Hunt, revealing significant insights into its servers' geographical and infrastructural distribution. Most Viper servers are located in China, which aligns with the tool's origins. They were initially developed and released by a Chinese-speaking individual.
Furthermore, our scanning efforts indicate that over half of the Viper infrastructure observed by Hunt is hosted on Tencent's servers, predominantly utilizing the default port of 60000. This detail not only underscores the regional preferences for this tool but also highlights the specific network environments favored by its users.
 Figure 3: Viper hosting statistics in Hunt
Figure 3: Viper hosting statistics in HuntViper allows operators to construct payloads compatible with multiple operating systems, including Windows, Linux, and MacOS. The platform also extends its support to various scripting languages, facilitating the generation of Python, PowerShell, Ruby, and VBS payloads, as seen in Figure 4 below. This versatility enhances Viper's utility across different technological environments, enabling diverse and adaptable attack vectors.
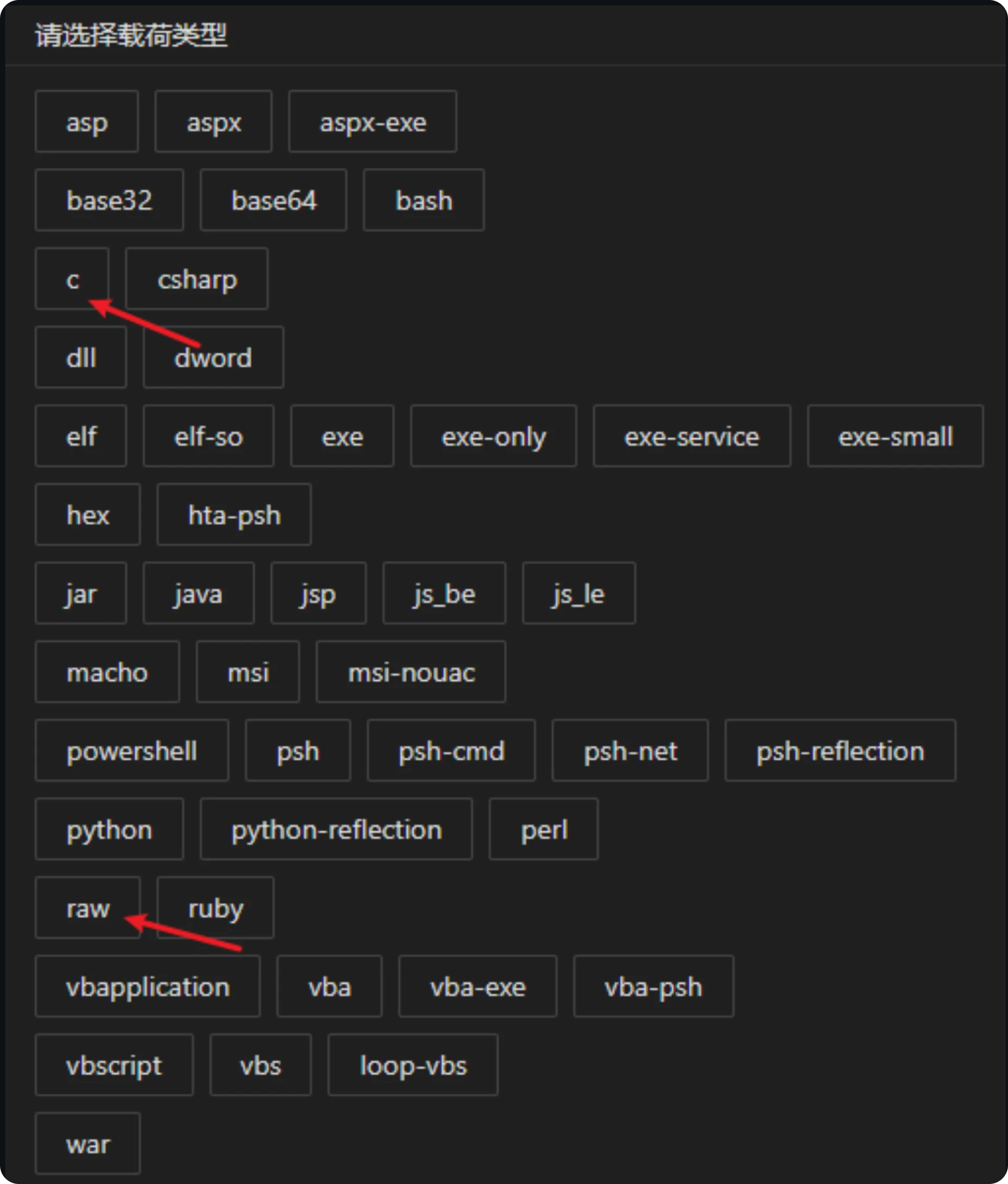 Figure 4: Viper payload options
Figure 4: Viper payload optionsDetecting Viper
Viper login pages, readily accessible online, offer a straightforward interaction and detection development opportunity. With a few lines of Python, researchers can capture headers from these pages and generate hashes of the login content, effectively detecting Viper deployments.
Using the login page in Figure 2 as an example, we are left with the below headers:
HTTP/1.1 200 OK
Server: nginx/1.24.0 (Ubuntu)
Date: varies
Content-Type: text/html
Content-Length: 692
Last-Modified: varies
Connection: keep-alive
ETag: varies
Accept-Ranges: bytes
Luckily for us, Viper ships with a default TLS certificate, as seen in Figure 5 below.
 Figure 5: Viper default certificate
Figure 5: Viper default certificateWith the above, we can start building queries to look for Viper login pages. As the headers "Server," "Date," and "Last-Modified" values can change and would break our rule, we'll just leave them as "varies" to cast a wide net and not limit ourselves to a specific date or server infrastructure.
HTTP/1.1 200 OK + Server: varies + Date: varies + Content-Length: 692 + title: "VIPER" + certificate subject common name: d1d38ec9
Favicon SHA1: f3d6b54a151c34b4931dc5a5a997afe96225569d *This can easily be removed from the code.
The default port could also be added to our rules above. I'll leave it up to the reader to experiment with changing the port numbers.
Interesting Observations
Before we get into some of the additional tools hosted alongside Viper and interesting servers our scanners have come across; we'll cover some suspicious domains we've encountered.
To view the domains for a set of active C2 servers, we can simply filter for them in Hunt.
 Figure 6: Snippet of Viper domains in Hunt
Figure 6: Snippet of Viper domains in HuntIn addition to the Viper platform, IP address 43.139.67[.]72, hosted by Tencent, also recently hosted two instances of Cobalt Strike on ports 80 & 443 (watermark: 391144938).
This server also resolves to two domains, one of which is likely attempting to spoof Microsoft update services, www.microsoftupdate[.]fun.
 Figure 7: Suspicious domains on Viper server
Figure 7: Suspicious domains on Viper serverPossibly related to our previous example (& also hosted on Tencent), IP 162.14.69.252, as of mid-April 2024, had a Cobalt Strike Team Server with the same watermark.
Unlike the previous IP, the domains at .252 spoof a flash drive app.
 Figure 8: Screenshot of suspicious domains
Figure 8: Screenshot of suspicious domainsIf you haven't noticed a recurring theme, many Viper servers are paired with Cobalt Strike. Our next IP is no different. The team servers still host a leaked version 9 of Cobalt Strike and use the well-known 987654321 watermark.
The IP in question, 111.231.146[.]154, resolves to several domains for the Chinese-developed game engine LayaBox.
 Figure 9: *.layabox[.]com domains at Viper & Cobalt Strike IP
Figure 9: *.layabox[.]com domains at Viper & Cobalt Strike IP Figure 10: Leaked certificate for Cobalt Strike
Figure 10: Leaked certificate for Cobalt StrikeMoving on, we'll look at Huawei IP address 124.71.84[.]65, which once again hosts a leaked version of Cobalt Strike (indicated by the "Pwn3rs Striked) certificate subject common name. Port 8899 hosts an instance of the open-source C2 framework, Sliver.
 Figure 11: Sliver (indicated by the red bug symbol) and Viper
Figure 11: Sliver (indicated by the red bug symbol) and ViperThe final domain we'll examine is model.tsmcai[.]com, hosted by Alibaba Cloud and resolving to 8.210.32[.]15. This domain is likely attempting to imitate an AI model website for the Taiwanese semiconductor manufacturing company TSMC.
Also found on port 28888 of the same IP is the open-source interactive HTTPS proxy, mitmproxy.
 Figure 12: Domain imitating TSMC on 8.210.32[.]15
Figure 12: Domain imitating TSMC on 8.210.32[.]15Touted as a replacement for BurpSuite, the team at Yaklang.io has developed Yak Lang, a language tailored for the cybersecurity community. Users can integrate various security tools and products using the programming language into Yaklang's other project, Yakit.
Some features of Yakit include MITM, web fuzzing, vulnerability scanning, subdomain crawling, and integration with Project Discovery's Nuclei tool.
 Figure 13: Yakit GitHub README
Figure 13: Yakit GitHub READMESifting through the many Viper instances found in Hunt, we stumbled upon Datacamp Limited IP address 185.230.228[.]136.
The server hosts a Yakit MITM certificate on port 61963 and a Yakit TeamServer certificate on port 9100. *Viper is hosted on port 60000.
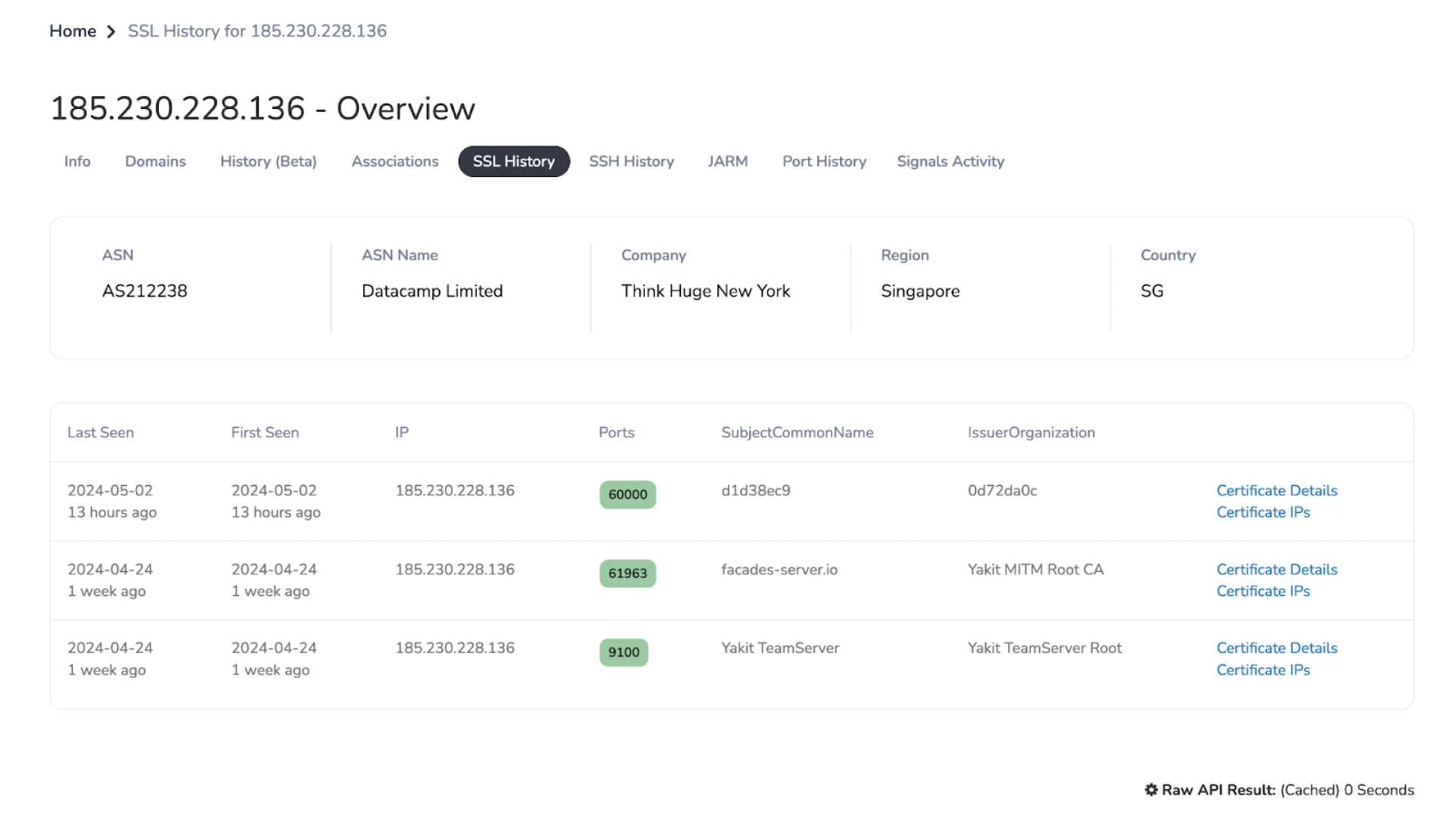 Figure 14: Yakit default certificates
Figure 14: Yakit default certificatesThe certificates in Figure 14 above are the default ones that ship with the tool when installed. Readers can use the subject common names in the above image to search for Yakit instances.
It should be noted that Yakit is a legitimate security tool developed for defenders; however, threat actors can also use these tools, as we see when paired with Viper or other exploitation platforms.
We can pivot on the Yakit MITM certificate to find additional infrastructure by clicking "Certificate IPs."
 Figure 15: Screenshot of additional IPs using the MITM certificate
Figure 15: Screenshot of additional IPs using the MITM certificateIn addition to .136, we find two more IPs:
185.230.228[.]140
185.230.228[.]141
Neither of the two newly found IPs hosts a Yakit team server. The IP ending in .140 has Viper running on the default port, while .141 only runs the Yakit MITM tool.
The close proximity of the IP addresses could suggest automation was used to obtain the infrastructure.
Conclusion
Throughout our analysis of the Viper platform, we have observed its extensive adoption and pairing with other prominent security tools such as Cobalt Strike, Sliver, and Yakit. These findings underline the platform's versatility and effectiveness in aiding threat actors in their campaigns.
The integration of Viper with these tools underscores a trend that is not slowing down anytime soon: adversaries utilize open-source solutions to establish or maintain access within target environments.
We encourage you to apply for an account with us to stay ahead of these threats and deepen your understanding of adversarial tactics. Join us in proactively identifying and mitigating emerging security challenges.
Introduction
From initial access and privilege escalation to lateral movement and data collection, the open-source platform Viper boasts over 80 modules designed to streamline the stages of an attack, making it a preferred tool for red teams and threat actors alike.
Additional features like anti-virus bypass, intranet tunneling, command-line operations, and custom payload generation lower the technical barriers, allowing many bad actors to conduct network exploitation operations efficiently.
In this post, we'll look at Viper's widespread use across countries and ASNs, detail some approaches to detecting its login pages, and discuss other tools used alongside Viper, such as Cobalt Strike, Sliver, and Yakit.
Viper
 Figure 1: Viper README
Figure 1: Viper READMEThe introduction covered many of Viper's features; what's unique about this tool is that the operator is provided with a GUI similar to Cobalt Strike. The platform's administrative section is protected by a login page, which many have left open to the internet.
Hunt is tracking over 400 unique IP addresses hosting Viper login pages. Figure 2 below shows an example.
 Figure 2: Example Viper login page
Figure 2: Example Viper login pageHosting details for Viper are readily accessible through Hunt, revealing significant insights into its servers' geographical and infrastructural distribution. Most Viper servers are located in China, which aligns with the tool's origins. They were initially developed and released by a Chinese-speaking individual.
Furthermore, our scanning efforts indicate that over half of the Viper infrastructure observed by Hunt is hosted on Tencent's servers, predominantly utilizing the default port of 60000. This detail not only underscores the regional preferences for this tool but also highlights the specific network environments favored by its users.
 Figure 3: Viper hosting statistics in Hunt
Figure 3: Viper hosting statistics in HuntViper allows operators to construct payloads compatible with multiple operating systems, including Windows, Linux, and MacOS. The platform also extends its support to various scripting languages, facilitating the generation of Python, PowerShell, Ruby, and VBS payloads, as seen in Figure 4 below. This versatility enhances Viper's utility across different technological environments, enabling diverse and adaptable attack vectors.
 Figure 4: Viper payload options
Figure 4: Viper payload optionsDetecting Viper
Viper login pages, readily accessible online, offer a straightforward interaction and detection development opportunity. With a few lines of Python, researchers can capture headers from these pages and generate hashes of the login content, effectively detecting Viper deployments.
Using the login page in Figure 2 as an example, we are left with the below headers:
HTTP/1.1 200 OK
Server: nginx/1.24.0 (Ubuntu)
Date: varies
Content-Type: text/html
Content-Length: 692
Last-Modified: varies
Connection: keep-alive
ETag: varies
Accept-Ranges: bytes
Luckily for us, Viper ships with a default TLS certificate, as seen in Figure 5 below.
 Figure 5: Viper default certificate
Figure 5: Viper default certificateWith the above, we can start building queries to look for Viper login pages. As the headers "Server," "Date," and "Last-Modified" values can change and would break our rule, we'll just leave them as "varies" to cast a wide net and not limit ourselves to a specific date or server infrastructure.
HTTP/1.1 200 OK + Server: varies + Date: varies + Content-Length: 692 + title: "VIPER" + certificate subject common name: d1d38ec9
Favicon SHA1: f3d6b54a151c34b4931dc5a5a997afe96225569d *This can easily be removed from the code.
The default port could also be added to our rules above. I'll leave it up to the reader to experiment with changing the port numbers.
Interesting Observations
Before we get into some of the additional tools hosted alongside Viper and interesting servers our scanners have come across; we'll cover some suspicious domains we've encountered.
To view the domains for a set of active C2 servers, we can simply filter for them in Hunt.
 Figure 6: Snippet of Viper domains in Hunt
Figure 6: Snippet of Viper domains in HuntIn addition to the Viper platform, IP address 43.139.67[.]72, hosted by Tencent, also recently hosted two instances of Cobalt Strike on ports 80 & 443 (watermark: 391144938).
This server also resolves to two domains, one of which is likely attempting to spoof Microsoft update services, www.microsoftupdate[.]fun.
 Figure 7: Suspicious domains on Viper server
Figure 7: Suspicious domains on Viper serverPossibly related to our previous example (& also hosted on Tencent), IP 162.14.69.252, as of mid-April 2024, had a Cobalt Strike Team Server with the same watermark.
Unlike the previous IP, the domains at .252 spoof a flash drive app.
 Figure 8: Screenshot of suspicious domains
Figure 8: Screenshot of suspicious domainsIf you haven't noticed a recurring theme, many Viper servers are paired with Cobalt Strike. Our next IP is no different. The team servers still host a leaked version 9 of Cobalt Strike and use the well-known 987654321 watermark.
The IP in question, 111.231.146[.]154, resolves to several domains for the Chinese-developed game engine LayaBox.
 Figure 9: *.layabox[.]com domains at Viper & Cobalt Strike IP
Figure 9: *.layabox[.]com domains at Viper & Cobalt Strike IP Figure 10: Leaked certificate for Cobalt Strike
Figure 10: Leaked certificate for Cobalt StrikeMoving on, we'll look at Huawei IP address 124.71.84[.]65, which once again hosts a leaked version of Cobalt Strike (indicated by the "Pwn3rs Striked) certificate subject common name. Port 8899 hosts an instance of the open-source C2 framework, Sliver.
 Figure 11: Sliver (indicated by the red bug symbol) and Viper
Figure 11: Sliver (indicated by the red bug symbol) and ViperThe final domain we'll examine is model.tsmcai[.]com, hosted by Alibaba Cloud and resolving to 8.210.32[.]15. This domain is likely attempting to imitate an AI model website for the Taiwanese semiconductor manufacturing company TSMC.
Also found on port 28888 of the same IP is the open-source interactive HTTPS proxy, mitmproxy.
 Figure 12: Domain imitating TSMC on 8.210.32[.]15
Figure 12: Domain imitating TSMC on 8.210.32[.]15Touted as a replacement for BurpSuite, the team at Yaklang.io has developed Yak Lang, a language tailored for the cybersecurity community. Users can integrate various security tools and products using the programming language into Yaklang's other project, Yakit.
Some features of Yakit include MITM, web fuzzing, vulnerability scanning, subdomain crawling, and integration with Project Discovery's Nuclei tool.
 Figure 13: Yakit GitHub README
Figure 13: Yakit GitHub READMESifting through the many Viper instances found in Hunt, we stumbled upon Datacamp Limited IP address 185.230.228[.]136.
The server hosts a Yakit MITM certificate on port 61963 and a Yakit TeamServer certificate on port 9100. *Viper is hosted on port 60000.
 Figure 14: Yakit default certificates
Figure 14: Yakit default certificatesThe certificates in Figure 14 above are the default ones that ship with the tool when installed. Readers can use the subject common names in the above image to search for Yakit instances.
It should be noted that Yakit is a legitimate security tool developed for defenders; however, threat actors can also use these tools, as we see when paired with Viper or other exploitation platforms.
We can pivot on the Yakit MITM certificate to find additional infrastructure by clicking "Certificate IPs."
 Figure 15: Screenshot of additional IPs using the MITM certificate
Figure 15: Screenshot of additional IPs using the MITM certificateIn addition to .136, we find two more IPs:
185.230.228[.]140
185.230.228[.]141
Neither of the two newly found IPs hosts a Yakit team server. The IP ending in .140 has Viper running on the default port, while .141 only runs the Yakit MITM tool.
The close proximity of the IP addresses could suggest automation was used to obtain the infrastructure.
Conclusion
Throughout our analysis of the Viper platform, we have observed its extensive adoption and pairing with other prominent security tools such as Cobalt Strike, Sliver, and Yakit. These findings underline the platform's versatility and effectiveness in aiding threat actors in their campaigns.
The integration of Viper with these tools underscores a trend that is not slowing down anytime soon: adversaries utilize open-source solutions to establish or maintain access within target environments.
We encourage you to apply for an account with us to stay ahead of these threats and deepen your understanding of adversarial tactics. Join us in proactively identifying and mitigating emerging security challenges.
Related Posts
Related Posts
Related Posts
©2026 Hunt Intelligence, Inc.
©2026 Hunt Intelligence, Inc.
©2025 Hunt Intelligence, Inc.


