Product Update: Introducing IOC Hunter Feed & Attribution in our C2 Feed
Published on

Tracking adversary infrastructure is a constant challenge for security teams. With evolving tactics, defenders need enriched intelligence to stay ahead. That's why Hunt.io is introducing two powerful updates: IOC Hunter Feed and IOC Hunter Attribution in our C2 Feed.
What's New?
With these enhancements, we now offer:
IOC Hunter Feed: a dedicated feed enriched with indicators of compromise (IOCs), pulling from various publications and reports.
IOC Hunter Attribution in the C2 Feed: provides potential attribution for detected C2 servers, linking them to known threat actors and malware campaigns.
How These Feeds Work
Let’s dive into how these feeds function and what data they provide.
IOC Hunter Feed
IOC Hunter Feed aggregates IOCs from open-source intelligence reports and security research. It includes:
Publication metadata: source, title, date, and URL.
Threat actor attribution: aliases, description, country, ransomware associations.
Associated IOCs: IPs, hosts, file hashes, and more.
IOC Hunter Attribution in the C2 Feed
Hunt.io's C2 Feed goes beyond merely identifying active command and control servers. It connects these servers to known threat actors and malware campaigns using enriched metadata. Here are the key points:
Continuously scans the internet for malware protocols, SSL certificates, and JARM/JA4 fingerprinting hashes.
Includes additional scanning on bulletproof hosting providers.
Uses custom validation logic to reduce false positives.
Receives regular updates from the Hunt Research team for improved accuracy.
Covers C2 servers, recon tools, phishing, and other malicious infrastructure from the last 7 days.

Accessing the Feeds
To retrieve the IOC Hunter Feed, run the following:
curl -o ioc-hunter.json.gz 'https://api.hunt.io/v1/feeds/ioc-hunter' -H 'token: <API_TOKEN_GOES_HERE>'
To retrieve the C2 Feed with IOC Hunter Attribution, use:
curl -o c2.json.gz 'https://api.hunt.io/v1/feeds/c2' -H 'token: <API_TOKEN_GOES_HERE>'
Replace
<API_TOKEN_GOES_HERE> with your actual API key. The response will be in a compressed JSON format.
Key Data Fields
Each entry in these feeds includes:
IP address and hostname
Port and timestamp
Malware name and subsystem
Threat actor attribution (via IOC Hunter Metadata)
Confidence score and additional data
Example Entry from IOC Hunter Feed:
{
"value": "d9e52663715902e9ec51a7dd2fea5241c9714976e9541c02df66d1a42a3a7d2a",
"ioc_type": "ioc_sha256",
"publication_name": "medium.com",
"publication_title": "Shamoon Malware. Shamoon Malware is a wiper that spread...",
"publication_url": "https://medium.com/@cyberecht/shamoon-malware-e24823501b10",
"published_at": "2025-02-28T18:33:00",
"threat_actor": {
"id": 46,
"uuid": "4f69ec6d-cb6b-42af-b8e2-920a2aa4be10",
"name": "APT33",
"origin": "APT33",
"synonyms": "APT 33, Elfin, MAGNALLIUM, Refined Kitten, HOLMIUM, COBALT TRINITY, G0064, ATK35, Peach Sandstorm, TA451",
"description": "Our analysis reveals that APT33 is a capable group that has carried out cyber espionage operations since at least 2013. We assess APT33 works at the behest of the Iranian government.",
"meta": {
"sponsor": "Iran (Islamic Republic of)",
"victims": [
"United States",
"Saudi Arabia",
"South Korea"
],
"category": [
"Private sector"
],
"incident": [
"Espionage"
]
},
"ransomware_group": false,
"country_code": "IR",
"country": "Iran",
}
}
CopyEnriched C2 Feed JSON Example with IOC Hunter Metadata:
{
"ip": "172.64.80.1",
"port": 80,
"hostname": "api.inmediavault.com",
"timestamp": "2025-03-07T12:11:06",
"scan_uri": "http://api.inmediavault.com/PEoX",
"confidence": 100,
"extra": {
"status_code": 200,
"geoip_city": null,
"geoip_country": null,
"geoip_asn": "CLOUDFLARENET",
"geoip_asn_num": 13335,
"geoip_subnetwork": "172.64.0.0/15",
"domain_private_name": "inmediavault.com",
"domain_type": "REGULAR"
},
"malware_name": "Cobalt Strike",
"malware_subsystem": "C2",
"ioc_hunter_metadata": [
{
"value": "d9e52663715902e9ec51a7dd2fea5241c9714976e9541c02df66d1a42a3a7d2a",
"ioc_type": "ioc_sha256",
"publication_name": "medium.com",
"publication_title": "Shamoon Malware. Shamoon Malware is a wiper that spread...",
"publication_url": "https://medium.com/@cyberecht/shamoon-malware-e24823501b10",
"published_at": "2025-02-28T18:33:00",
"threat_actor": {
"id": 46,
"uuid": "4f69ec6d-cb6b-42af-b8e2-920a2aa4be10",
"name": "APT33",
"origin": "APT33",
"synonyms": "APT 33, Elfin, MAGNALLIUM, Refined Kitten, HOLMIUM, COBALT TRINITY, G0064, ATK35, Peach Sandstorm, TA451",
"description": "Our analysis reveals that APT33 is a capable group that has carried out cyber espionage operations since at least 2013. We assess APT33 works at the behest of the Iranian government.",
"meta": {
"sponsor": "Iran (Islamic Republic of)",
"victims": [
"United States",
"Saudi Arabia",
"South Korea"
],
"category": [
"Private sector"
],
"incident": [
"Espionage"
]
},
"ransomware_group": false,
"country_code": "IR",
"country": "Iran",
}
}
]
}
CopyHow Security Teams Can Use The IOC Hunter Feed
Here are some brief examples of how to use IOC Hunter Feeds to pivot on and uncover additional adversary infrastructure:
Expanding on XCSSET Infrastructure
For this section, we'll move to IOC Hunter's web interface. A recent Microsoft blog post detailed XCSSET malware activity infecting Xcode projects, including a command-and-control (C2) domain. This indicator appeared in the feed, allowing us to analyze its metadata and explore additional connections quickly.
 Figure 1: IOC Hunter feed information for Microsoft's XCSSET research.
Figure 1: IOC Hunter feed information for Microsoft's XCSSET research.Querying the domain, we find it resolves to
95.142.38[.]107, hosted on the EuroByte LLC network in Russia. The server overview lists 54 domains tied to this IP, many matching indicators in Microsoft's report. However, the Associations tab in Hunt reveals a more interesting connection-an unreported IP address,
95.142.38[.]79, which shared SSH keys with the original C2 from mid-February to March 9, 2025.
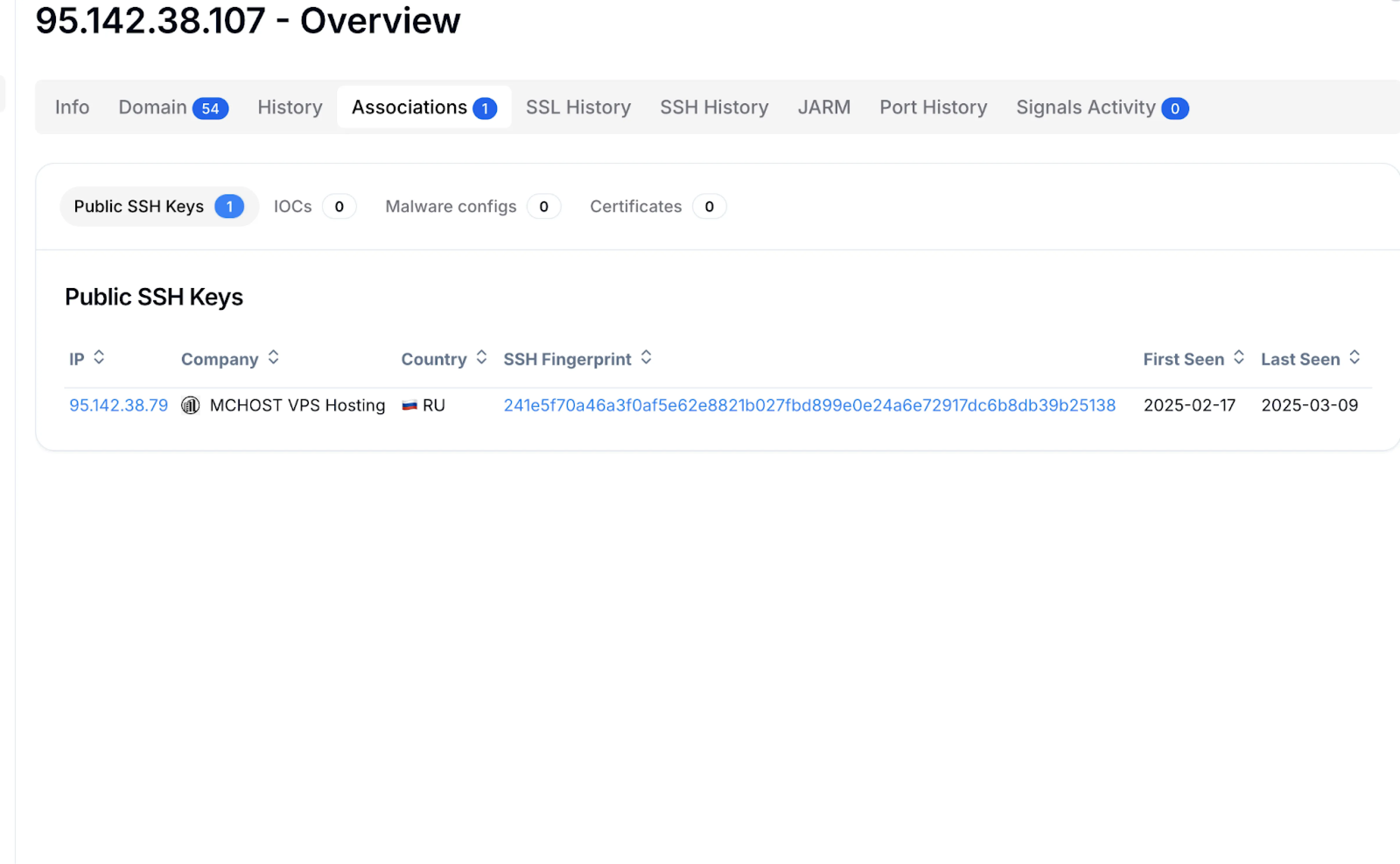 Figure 2: IP overview for the initial C2 server, showing a second associated server in Hunt.
Figure 2: IP overview for the initial C2 server, showing a second associated server in Hunt.Pivoting further, a review of the SSH key SHA-256 hash (
3FE88378D4EBDD3F27063D41DA0D4E69A0D3AAB549AEA28A0B8CD73DD9606891), reveals yet another IP address,
178.208.92[.]187, last seen in December 2024.
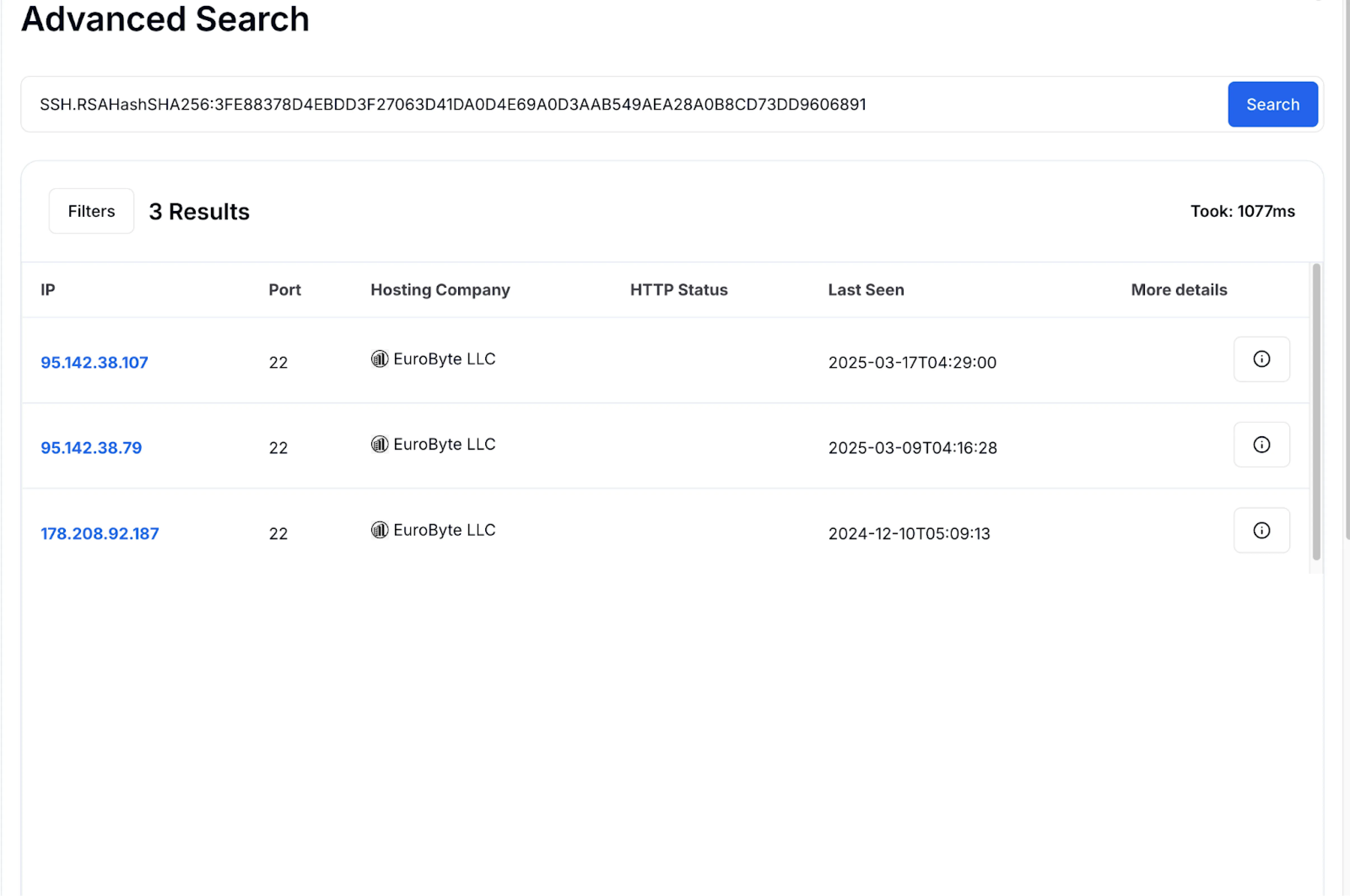 Figure 3: Pivoting made easy with Advanced Search in Hunt querying for the SSH key hash.
Figure 3: Pivoting made easy with Advanced Search in Hunt querying for the SSH key hash.Starting with a C2 domain in IOC Hunter, we identified two additional IP addresses linked to the same infrastructure-neither mentioned in the original reporting. Historical metadata showed overlaps between these IPs and other macOS-targeting malware, pointing to a broader network of activity.
By extending the investigation beyond known indicators, defenders can connect related malicious infrastructure, strengthen detection coverage, and stay ahead of evolving threats.
Tracking GhostSocks Proxies
GhostSocks, a Golang-based SOCKS5 proxy, is sold as malware-as-a-service (MaaS) and integrated with Cobalt Strike, LummaC2, and Zloader.
While the blog provided several network indicators also captured in our IOC Hunter Feed, we can use Hunt.io to view an updated list of active GhostSocks proxy servers, including their hosting locations and first-seen timestamps. Some align with previously reported infrastructure, while others point to ongoing activity and further distribution.
 Figure 4: Snippet of GhostSocks servers currently being tracked in Hunt.
Figure 4: Snippet of GhostSocks servers currently being tracked in Hunt.Defender Considerations
Track hosting trends to identify shifts in attacker infrastructure and new deployments.
Analyze hosting country data to assess preferences in regions and ASNs.
Monitor for GhostSocks being used alongside other malware as part of broader efforts to evade network defenses.
GhostSocks infrastructure is not static. Understanding hosting patterns over time provides better visibility into its operations and helps defenders respond to threats more effectively.
These examples show how IOC Hunter Feeds uncover hidden infrastructure, lead researchers to link unknown indicators, and enhance attribution-giving defenders the insight needed to anticipate and counter evolving threats.
Why These Feeds Matter
Threat detection isn't just about spotting malicious activity. Knowing who is behind an attack helps organizations respond more effectively. With the IOC Hunter Feed and C2 Feed with Attribution, users can:
Identify threat actors behind malicious campaigns
Prioritize threats based on adversary activity
Strengthen incident response with better context
These features are now available for all Hunt.io users. If you're already using our feeds, start integrating threat actor attribution into your workflow today. If not, book a demo with our team to get started.
Tracking adversary infrastructure is a constant challenge for security teams. With evolving tactics, defenders need enriched intelligence to stay ahead. That's why Hunt.io is introducing two powerful updates: IOC Hunter Feed and IOC Hunter Attribution in our C2 Feed.
What's New?
With these enhancements, we now offer:
IOC Hunter Feed: a dedicated feed enriched with indicators of compromise (IOCs), pulling from various publications and reports.
IOC Hunter Attribution in the C2 Feed: provides potential attribution for detected C2 servers, linking them to known threat actors and malware campaigns.
How These Feeds Work
Let’s dive into how these feeds function and what data they provide.
IOC Hunter Feed
IOC Hunter Feed aggregates IOCs from open-source intelligence reports and security research. It includes:
Publication metadata: source, title, date, and URL.
Threat actor attribution: aliases, description, country, ransomware associations.
Associated IOCs: IPs, hosts, file hashes, and more.
IOC Hunter Attribution in the C2 Feed
Hunt.io's C2 Feed goes beyond merely identifying active command and control servers. It connects these servers to known threat actors and malware campaigns using enriched metadata. Here are the key points:
Continuously scans the internet for malware protocols, SSL certificates, and JARM/JA4 fingerprinting hashes.
Includes additional scanning on bulletproof hosting providers.
Uses custom validation logic to reduce false positives.
Receives regular updates from the Hunt Research team for improved accuracy.
Covers C2 servers, recon tools, phishing, and other malicious infrastructure from the last 7 days.

Accessing the Feeds
To retrieve the IOC Hunter Feed, run the following:
curl -o ioc-hunter.json.gz 'https://api.hunt.io/v1/feeds/ioc-hunter' -H 'token: <API_TOKEN_GOES_HERE>'
To retrieve the C2 Feed with IOC Hunter Attribution, use:
curl -o c2.json.gz 'https://api.hunt.io/v1/feeds/c2' -H 'token: <API_TOKEN_GOES_HERE>'
Replace
<API_TOKEN_GOES_HERE> with your actual API key. The response will be in a compressed JSON format.
Key Data Fields
Each entry in these feeds includes:
IP address and hostname
Port and timestamp
Malware name and subsystem
Threat actor attribution (via IOC Hunter Metadata)
Confidence score and additional data
Example Entry from IOC Hunter Feed:
{
"value": "d9e52663715902e9ec51a7dd2fea5241c9714976e9541c02df66d1a42a3a7d2a",
"ioc_type": "ioc_sha256",
"publication_name": "medium.com",
"publication_title": "Shamoon Malware. Shamoon Malware is a wiper that spread...",
"publication_url": "https://medium.com/@cyberecht/shamoon-malware-e24823501b10",
"published_at": "2025-02-28T18:33:00",
"threat_actor": {
"id": 46,
"uuid": "4f69ec6d-cb6b-42af-b8e2-920a2aa4be10",
"name": "APT33",
"origin": "APT33",
"synonyms": "APT 33, Elfin, MAGNALLIUM, Refined Kitten, HOLMIUM, COBALT TRINITY, G0064, ATK35, Peach Sandstorm, TA451",
"description": "Our analysis reveals that APT33 is a capable group that has carried out cyber espionage operations since at least 2013. We assess APT33 works at the behest of the Iranian government.",
"meta": {
"sponsor": "Iran (Islamic Republic of)",
"victims": [
"United States",
"Saudi Arabia",
"South Korea"
],
"category": [
"Private sector"
],
"incident": [
"Espionage"
]
},
"ransomware_group": false,
"country_code": "IR",
"country": "Iran",
}
}
CopyEnriched C2 Feed JSON Example with IOC Hunter Metadata:
{
"ip": "172.64.80.1",
"port": 80,
"hostname": "api.inmediavault.com",
"timestamp": "2025-03-07T12:11:06",
"scan_uri": "http://api.inmediavault.com/PEoX",
"confidence": 100,
"extra": {
"status_code": 200,
"geoip_city": null,
"geoip_country": null,
"geoip_asn": "CLOUDFLARENET",
"geoip_asn_num": 13335,
"geoip_subnetwork": "172.64.0.0/15",
"domain_private_name": "inmediavault.com",
"domain_type": "REGULAR"
},
"malware_name": "Cobalt Strike",
"malware_subsystem": "C2",
"ioc_hunter_metadata": [
{
"value": "d9e52663715902e9ec51a7dd2fea5241c9714976e9541c02df66d1a42a3a7d2a",
"ioc_type": "ioc_sha256",
"publication_name": "medium.com",
"publication_title": "Shamoon Malware. Shamoon Malware is a wiper that spread...",
"publication_url": "https://medium.com/@cyberecht/shamoon-malware-e24823501b10",
"published_at": "2025-02-28T18:33:00",
"threat_actor": {
"id": 46,
"uuid": "4f69ec6d-cb6b-42af-b8e2-920a2aa4be10",
"name": "APT33",
"origin": "APT33",
"synonyms": "APT 33, Elfin, MAGNALLIUM, Refined Kitten, HOLMIUM, COBALT TRINITY, G0064, ATK35, Peach Sandstorm, TA451",
"description": "Our analysis reveals that APT33 is a capable group that has carried out cyber espionage operations since at least 2013. We assess APT33 works at the behest of the Iranian government.",
"meta": {
"sponsor": "Iran (Islamic Republic of)",
"victims": [
"United States",
"Saudi Arabia",
"South Korea"
],
"category": [
"Private sector"
],
"incident": [
"Espionage"
]
},
"ransomware_group": false,
"country_code": "IR",
"country": "Iran",
}
}
]
}
CopyHow Security Teams Can Use The IOC Hunter Feed
Here are some brief examples of how to use IOC Hunter Feeds to pivot on and uncover additional adversary infrastructure:
Expanding on XCSSET Infrastructure
For this section, we'll move to IOC Hunter's web interface. A recent Microsoft blog post detailed XCSSET malware activity infecting Xcode projects, including a command-and-control (C2) domain. This indicator appeared in the feed, allowing us to analyze its metadata and explore additional connections quickly.
 Figure 1: IOC Hunter feed information for Microsoft's XCSSET research.
Figure 1: IOC Hunter feed information for Microsoft's XCSSET research.Querying the domain, we find it resolves to
95.142.38[.]107, hosted on the EuroByte LLC network in Russia. The server overview lists 54 domains tied to this IP, many matching indicators in Microsoft's report. However, the Associations tab in Hunt reveals a more interesting connection-an unreported IP address,
95.142.38[.]79, which shared SSH keys with the original C2 from mid-February to March 9, 2025.
 Figure 2: IP overview for the initial C2 server, showing a second associated server in Hunt.
Figure 2: IP overview for the initial C2 server, showing a second associated server in Hunt.Pivoting further, a review of the SSH key SHA-256 hash (
3FE88378D4EBDD3F27063D41DA0D4E69A0D3AAB549AEA28A0B8CD73DD9606891), reveals yet another IP address,
178.208.92[.]187, last seen in December 2024.
 Figure 3: Pivoting made easy with Advanced Search in Hunt querying for the SSH key hash.
Figure 3: Pivoting made easy with Advanced Search in Hunt querying for the SSH key hash.Starting with a C2 domain in IOC Hunter, we identified two additional IP addresses linked to the same infrastructure-neither mentioned in the original reporting. Historical metadata showed overlaps between these IPs and other macOS-targeting malware, pointing to a broader network of activity.
By extending the investigation beyond known indicators, defenders can connect related malicious infrastructure, strengthen detection coverage, and stay ahead of evolving threats.
Tracking GhostSocks Proxies
GhostSocks, a Golang-based SOCKS5 proxy, is sold as malware-as-a-service (MaaS) and integrated with Cobalt Strike, LummaC2, and Zloader.
While the blog provided several network indicators also captured in our IOC Hunter Feed, we can use Hunt.io to view an updated list of active GhostSocks proxy servers, including their hosting locations and first-seen timestamps. Some align with previously reported infrastructure, while others point to ongoing activity and further distribution.
 Figure 4: Snippet of GhostSocks servers currently being tracked in Hunt.
Figure 4: Snippet of GhostSocks servers currently being tracked in Hunt.Defender Considerations
Track hosting trends to identify shifts in attacker infrastructure and new deployments.
Analyze hosting country data to assess preferences in regions and ASNs.
Monitor for GhostSocks being used alongside other malware as part of broader efforts to evade network defenses.
GhostSocks infrastructure is not static. Understanding hosting patterns over time provides better visibility into its operations and helps defenders respond to threats more effectively.
These examples show how IOC Hunter Feeds uncover hidden infrastructure, lead researchers to link unknown indicators, and enhance attribution-giving defenders the insight needed to anticipate and counter evolving threats.
Why These Feeds Matter
Threat detection isn't just about spotting malicious activity. Knowing who is behind an attack helps organizations respond more effectively. With the IOC Hunter Feed and C2 Feed with Attribution, users can:
Identify threat actors behind malicious campaigns
Prioritize threats based on adversary activity
Strengthen incident response with better context
These features are now available for all Hunt.io users. If you're already using our feeds, start integrating threat actor attribution into your workflow today. If not, book a demo with our team to get started.
Related Posts
Related Posts
Related Posts


