Open Directories Expose Publicly Available Tools Targeting Asian Organizations
Open Directories Expose Publicly Available Tools Targeting Asian Organizations
Published on
Jun 18, 2024
Introduction
The Hunt Research Team recently identified an exposed web server used to target the Taiwanese Freeway Bureau and a local data center. The server's administrator utilized open-source tools such as Nmap, SQLMap, and the backdoor BlueShell to conduct their activities. The directory was only briefly available before the actor likely realized the mistake.
Using Hunt's Open Directory Search feature, we'll explore the files downloaded from this server (available to Hunt users) and examine a history of similarly misconfigured infrastructure targeting various Taiwanese government agencies over the past year.
The Initial Discovery: Exposed Web Server & Tools
Hunt researchers identified a publicly accessible web server at IP address 103.98.73_189:8080, located in Taiwan. The server's HTTP headers (SimpleHTTP/0.6 Python/3.8.2) suggested it was running a Python-based web server, serving a variety of files and folders.
Due to the brief exposure of the misconfigured server, we’ll be conducting our analysis using Hunt’s Open Directories feature. Our scanners continuously scour the internet, downloading files from misconfigured servers around the clock. This capability allows us to uncover hidden threats and provide insights into tactics used by threat actors.
The server in question was first captured in the Hunt platform on 31 May 2024.
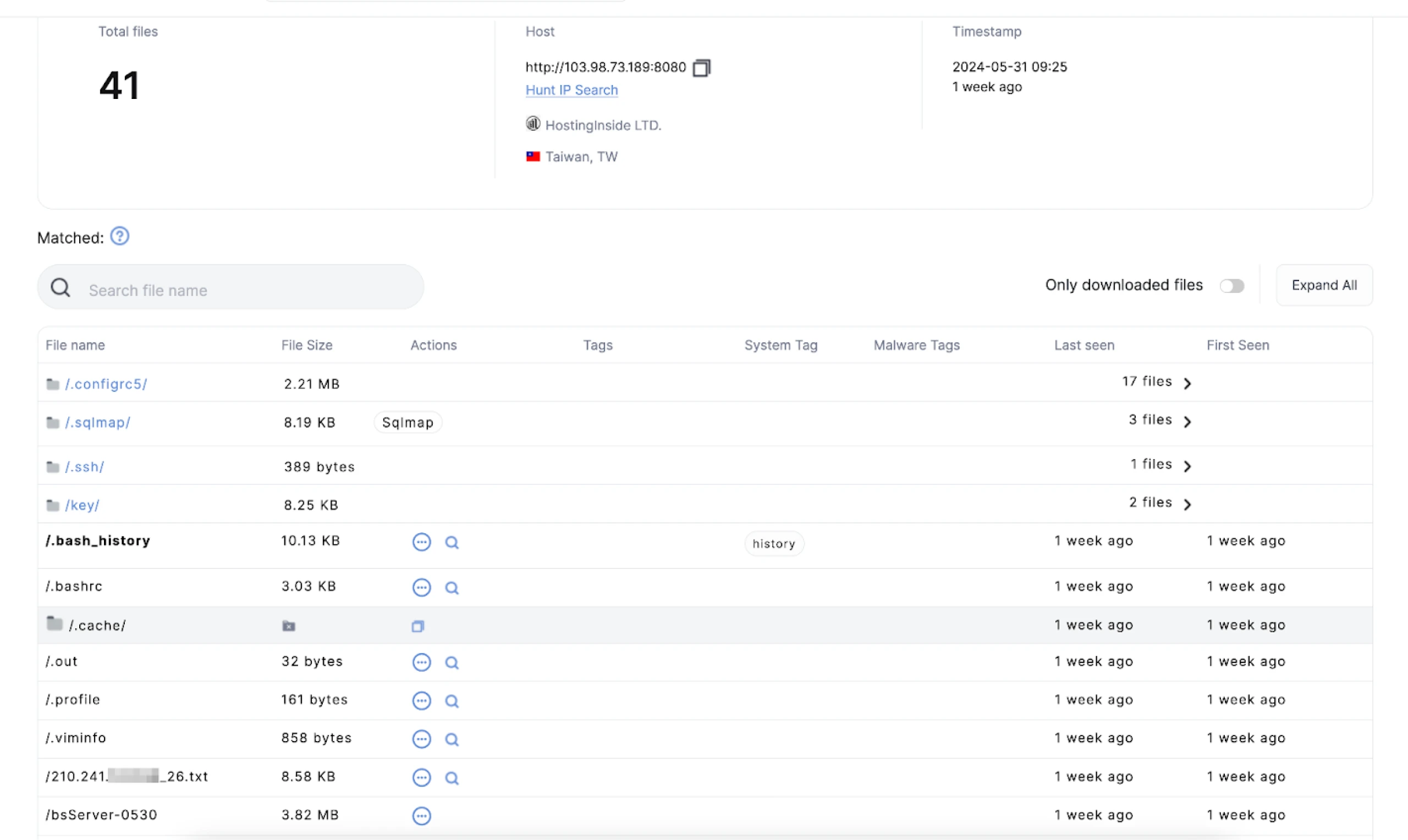 Figure 1: Screenshot of the open directory in Hunt and files readily available for download
Figure 1: Screenshot of the open directory in Hunt and files readily available for downloadThe threat actor employed SQLMap to scan for vulnerabilities within a subdomain of the freeway.gov_tw server. Our team confirmed that this targeted site is a legitimate government website for Taiwan. Although we could not retrieve the results from the history/ and output/ folders, as depicted in Figure 2, key files such as the log, session.sqlite, and target.txt files were successfully downloaded.
 Figure 2: File contents of exposed sqlmap/ folder
Figure 2: File contents of exposed sqlmap/ folderFigure 3 illustrates the contents of the target.txt file located in the .sqlmap/ folder. In a Linux system, the leading dot in the folder name indicates it was meant to be hidden.
 Figure 3: SQLMap command within target.txt file
Figure 3: SQLMap command within target.txt fileThe threat actor used Nmap to scan for open ports within a /26 network associated with a data center in Taiwan. To ensure the security and privacy of those affected, we have obfuscated the IP address in the file containing the scan results.
Next, we focus on the folder ./configrc5, which contains multiple bash files. One of these files checks the network connection to another IP address and looks for specific CPUs.
The most interesting of the bash scripts is simply named “a” and detects the CPU type (AMD Zen4, Zen3, Zen2/1, or Intel) and applies the corresponding Model-Specific Register (MSR) values to optimize performance specific to each CPU type.
Tailored scripts searching for certain CPU types suggest a well-informed and methodical threat actor with extensive knowledge of the target network.
Figure 4 shows a script snippet including a commented-out network connection check to the IP address 45.9.148_228.
 Figure 4: Snippet of ‘a’ bash script
Figure 4: Snippet of ‘a’ bash scriptWhile little is known about the IP used to check network connectivity, querying the address in Hunt reveals an overlap of SSH keys with multiple servers, as seen in Figure 5 below.
 Figure 5: SSH key overlaps from IP used for the connectivity check
Figure 5: SSH key overlaps from IP used for the connectivity checkThe last two files in the directory, written in Golang, are named bsServer-0530 and bsServerfinal. Sandbox analysis reveals that these files access server.pem from within the /key folder of the directory.
Figure 6 displays the certificate contents for both files, which match exactly with the open-source backdoor BlueShell. We can confidently conclude that both files are associated with the above malware.
 Figure 6: BlueShell certificate within /key folder of the directory
Figure 6: BlueShell certificate within /key folder of the directoryOpen Directory Patterns
We can uncover additional misconfigured servers targeting Taiwanese organizations using Hunt's Open Directories search function.
Surprisingly, as shown in Figure 7, our scanners identified 55 files matching the query "gov.tw." Notably, the last IP in the list, 156.251.172_194, stands out. This IP was previously highlighted in EclecticIQ's report on a Chinese threat actor using Cobalt Strike Cat to target Taiwanese critical infrastructure.
 Figure 7: Screenshot of files found in open directories with the term “gov.tw.” Try it!
Figure 7: Screenshot of files found in open directories with the term “gov.tw.” Try it!Notable Mentions
Instead of reiterating EclecticIQ's comprehensive analysis, we'll focus on some open directories that have yet to be publicly reported. These directories contain notable targets and a variety of offensive tools.
One example is IP address 35.229.211_35, which leverages various open-source tools such as SecurityTrails API, Acunetix, and ChatGPT. In Figure 8, you'll find an excerpt from a Python script named chatgpt.py, designed to automate web page content analysis. Interestingly, the script's comments are written in Chinese.
These findings highlight the range of tools attackers use and emphasize the significance of examining open directories to uncover potential security threats.
 Figure 8: Snippet of Python ChatGPT script
Figure 8: Snippet of Python ChatGPT scriptSimilar to our initial discovery, the IP address 202.182.105_104, located in Japan and hosted on The Constant Company network, contained a .sqlmap folder. This folder included scan results against the Cambodian Ministry of Foreign Affairs and a school teaching the Taiwanese Hakka dialect.
Although not shown in Figure 9, the folder also contained output targeting Paraguay's Ministry of Foreign Affairs.
 Figure 9: Contents of open directory targeting Taiwan and Paraguay
Figure 9: Contents of open directory targeting Taiwan and ParaguayWithin the same directory is a folder named "af/" containing the program Afrog, a vulnerability scanning tool. This subfolder also included a file named taef.org.txt. In this context, TAEF stands for Taiwan-Asia Exchange Foundation, a policy think tank focused on Taiwan and Southeast/South Asia.
As shown in Figure 10, the file contains multiple subdomains for the organization. These subdomains were likely used for further reconnaissance and identifying vulnerabilities.
 Figure 10: Subdomain enumeration results for taef_org.
Figure 10: Subdomain enumeration results for taef_org.Lastly, we discovered IP 45.8.146_29, which hosted several offensive tools, including Brute Ratel C4, JSFinder, ProxyShell, and Earthworm. Among the various folders was "OneForAll," a subdomain enumeration tool. This folder contained scan results targeting the National Taiwan University Hospital, an Indonesian immigration office, the Indian Railway office, and a Thai Consulate General website.
Refer to Figure 11 for the tags identifying files within these open directories.
 Figure 11: Snippet of tools used in open directory targeting Asian countries
Figure 11: Snippet of tools used in open directory targeting Asian countriesConclusion
This blog post has explored a handful of open directories, uncovering various offensive tools and targeted scans against government and institutional entities across Taiwan and beyond. From leveraging SQLMap and Nmap to deploying advanced tools like Brute Ratel C4 and OneForAll, the threat actors' methods demonstrate a low-cost, high-reward approach to targeting networks.
These discoveries underscore the importance of continuously monitoring and analyzing open directories to identify and mitigate potential threats.
Join us in our mission to track and thwart these threat actors. Request an account today to gain access to Hunt's powerful tools and collaborate with us to uncover and analyze malicious infrastructure.
Network Observables
| IP Address | Notes |
|---|---|
| 103.98.73_189:8080 | Initial open directory |
| 202.182.105_104:80 | Similar exposed server found through Hunt Open Directories |
| 35.229.211_35:8080 | Similar exposed server found through Hunt Open Directories |
| 45.8.146_29:80 | Similar exposed server found through Hunt Open Directories |
| 156.251.172_194 | Similar server/EclecticIQ report |
Introduction
The Hunt Research Team recently identified an exposed web server used to target the Taiwanese Freeway Bureau and a local data center. The server's administrator utilized open-source tools such as Nmap, SQLMap, and the backdoor BlueShell to conduct their activities. The directory was only briefly available before the actor likely realized the mistake.
Using Hunt's Open Directory Search feature, we'll explore the files downloaded from this server (available to Hunt users) and examine a history of similarly misconfigured infrastructure targeting various Taiwanese government agencies over the past year.
The Initial Discovery: Exposed Web Server & Tools
Hunt researchers identified a publicly accessible web server at IP address 103.98.73_189:8080, located in Taiwan. The server's HTTP headers (SimpleHTTP/0.6 Python/3.8.2) suggested it was running a Python-based web server, serving a variety of files and folders.
Due to the brief exposure of the misconfigured server, we’ll be conducting our analysis using Hunt’s Open Directories feature. Our scanners continuously scour the internet, downloading files from misconfigured servers around the clock. This capability allows us to uncover hidden threats and provide insights into tactics used by threat actors.
The server in question was first captured in the Hunt platform on 31 May 2024.
 Figure 1: Screenshot of the open directory in Hunt and files readily available for download
Figure 1: Screenshot of the open directory in Hunt and files readily available for downloadThe threat actor employed SQLMap to scan for vulnerabilities within a subdomain of the freeway.gov_tw server. Our team confirmed that this targeted site is a legitimate government website for Taiwan. Although we could not retrieve the results from the history/ and output/ folders, as depicted in Figure 2, key files such as the log, session.sqlite, and target.txt files were successfully downloaded.
 Figure 2: File contents of exposed sqlmap/ folder
Figure 2: File contents of exposed sqlmap/ folderFigure 3 illustrates the contents of the target.txt file located in the .sqlmap/ folder. In a Linux system, the leading dot in the folder name indicates it was meant to be hidden.
 Figure 3: SQLMap command within target.txt file
Figure 3: SQLMap command within target.txt fileThe threat actor used Nmap to scan for open ports within a /26 network associated with a data center in Taiwan. To ensure the security and privacy of those affected, we have obfuscated the IP address in the file containing the scan results.
Next, we focus on the folder ./configrc5, which contains multiple bash files. One of these files checks the network connection to another IP address and looks for specific CPUs.
The most interesting of the bash scripts is simply named “a” and detects the CPU type (AMD Zen4, Zen3, Zen2/1, or Intel) and applies the corresponding Model-Specific Register (MSR) values to optimize performance specific to each CPU type.
Tailored scripts searching for certain CPU types suggest a well-informed and methodical threat actor with extensive knowledge of the target network.
Figure 4 shows a script snippet including a commented-out network connection check to the IP address 45.9.148_228.
 Figure 4: Snippet of ‘a’ bash script
Figure 4: Snippet of ‘a’ bash scriptWhile little is known about the IP used to check network connectivity, querying the address in Hunt reveals an overlap of SSH keys with multiple servers, as seen in Figure 5 below.
 Figure 5: SSH key overlaps from IP used for the connectivity check
Figure 5: SSH key overlaps from IP used for the connectivity checkThe last two files in the directory, written in Golang, are named bsServer-0530 and bsServerfinal. Sandbox analysis reveals that these files access server.pem from within the /key folder of the directory.
Figure 6 displays the certificate contents for both files, which match exactly with the open-source backdoor BlueShell. We can confidently conclude that both files are associated with the above malware.
 Figure 6: BlueShell certificate within /key folder of the directory
Figure 6: BlueShell certificate within /key folder of the directoryOpen Directory Patterns
We can uncover additional misconfigured servers targeting Taiwanese organizations using Hunt's Open Directories search function.
Surprisingly, as shown in Figure 7, our scanners identified 55 files matching the query "gov.tw." Notably, the last IP in the list, 156.251.172_194, stands out. This IP was previously highlighted in EclecticIQ's report on a Chinese threat actor using Cobalt Strike Cat to target Taiwanese critical infrastructure.
 Figure 7: Screenshot of files found in open directories with the term “gov.tw.” Try it!
Figure 7: Screenshot of files found in open directories with the term “gov.tw.” Try it!Notable Mentions
Instead of reiterating EclecticIQ's comprehensive analysis, we'll focus on some open directories that have yet to be publicly reported. These directories contain notable targets and a variety of offensive tools.
One example is IP address 35.229.211_35, which leverages various open-source tools such as SecurityTrails API, Acunetix, and ChatGPT. In Figure 8, you'll find an excerpt from a Python script named chatgpt.py, designed to automate web page content analysis. Interestingly, the script's comments are written in Chinese.
These findings highlight the range of tools attackers use and emphasize the significance of examining open directories to uncover potential security threats.
 Figure 8: Snippet of Python ChatGPT script
Figure 8: Snippet of Python ChatGPT scriptSimilar to our initial discovery, the IP address 202.182.105_104, located in Japan and hosted on The Constant Company network, contained a .sqlmap folder. This folder included scan results against the Cambodian Ministry of Foreign Affairs and a school teaching the Taiwanese Hakka dialect.
Although not shown in Figure 9, the folder also contained output targeting Paraguay's Ministry of Foreign Affairs.
 Figure 9: Contents of open directory targeting Taiwan and Paraguay
Figure 9: Contents of open directory targeting Taiwan and ParaguayWithin the same directory is a folder named "af/" containing the program Afrog, a vulnerability scanning tool. This subfolder also included a file named taef.org.txt. In this context, TAEF stands for Taiwan-Asia Exchange Foundation, a policy think tank focused on Taiwan and Southeast/South Asia.
As shown in Figure 10, the file contains multiple subdomains for the organization. These subdomains were likely used for further reconnaissance and identifying vulnerabilities.
 Figure 10: Subdomain enumeration results for taef_org.
Figure 10: Subdomain enumeration results for taef_org.Lastly, we discovered IP 45.8.146_29, which hosted several offensive tools, including Brute Ratel C4, JSFinder, ProxyShell, and Earthworm. Among the various folders was "OneForAll," a subdomain enumeration tool. This folder contained scan results targeting the National Taiwan University Hospital, an Indonesian immigration office, the Indian Railway office, and a Thai Consulate General website.
Refer to Figure 11 for the tags identifying files within these open directories.
 Figure 11: Snippet of tools used in open directory targeting Asian countries
Figure 11: Snippet of tools used in open directory targeting Asian countriesConclusion
This blog post has explored a handful of open directories, uncovering various offensive tools and targeted scans against government and institutional entities across Taiwan and beyond. From leveraging SQLMap and Nmap to deploying advanced tools like Brute Ratel C4 and OneForAll, the threat actors' methods demonstrate a low-cost, high-reward approach to targeting networks.
These discoveries underscore the importance of continuously monitoring and analyzing open directories to identify and mitigate potential threats.
Join us in our mission to track and thwart these threat actors. Request an account today to gain access to Hunt's powerful tools and collaborate with us to uncover and analyze malicious infrastructure.
Network Observables
| IP Address | Notes |
|---|---|
| 103.98.73_189:8080 | Initial open directory |
| 202.182.105_104:80 | Similar exposed server found through Hunt Open Directories |
| 35.229.211_35:8080 | Similar exposed server found through Hunt Open Directories |
| 45.8.146_29:80 | Similar exposed server found through Hunt Open Directories |
| 156.251.172_194 | Similar server/EclecticIQ report |
Related Posts
Related Posts
Related Posts


