A Treasure Trove of Trouble: Open Directory Exposes Red Team Tools
A Treasure Trove of Trouble: Open Directory Exposes Red Team Tools
Published on
Mar 21, 2024
Introduction
While open directories are often seen as a goldmine for security researchers and blue teams searching for malware or phishing campaigns, the very ease of access that makes them attractive can be a double-edged sword. Directory indexing can leave sensitive information from organizations wholly exposed to anyone online.
Red teamers and threat actors who neglect to secure the data they obtain during operations properly can inadvertently create a similar situation. They leave their tools and techniques exposed for all to see, compromising the effectiveness of their current efforts and potentially revealing their tactics for future attacks.
In this post, we'll examine a case involving multiple red team tools, certificates, and even what appears to be the kerberoasted hashes of a large organization.
The Discovery
Justin Elze, Twitter(X): @HackingLZ was the first to notice the exposed directory in Hunt. He commented on how directory indexing commonly trips up red team operations in his post.
 Figure 1: Post by Justin leading to this blog (https://twitter.com/HackingLZ/status/1767610924599578740)
Figure 1: Post by Justin leading to this blog (https://twitter.com/HackingLZ/status/1767610924599578740)Looking at the files and folders within Justin's post, we can see three well-known command and control (C2) frameworks, CobaltStrike, Havoc, and Villian. Additionally, we can see an exposed SSH directory, bash history, a BloodHound zip file, and probable 7Zip binaries (likely used for exfiltration). We can also see typical red team PowerShell scripts to analyze networks and Active Directory environments.
Justin has already provided us with a great deal of information. Below is a quick overview of the IP address and Python SimpleHTTPServer where the directory was hosted.
 Figure 2: Hunt overview of the open directory server and port history
Figure 2: Hunt overview of the open directory server and port historyLet's touch on the rest of the files in the directory before we revisit Cobalt Strike.
 Figure 3: Screenshot of remaining files
Figure 3: Screenshot of remaining filesThe filenames within the directory are pretty descriptive, suggesting their intended purpose for red team activities. While these names might be changed before use in an actual attack, it leads us to believe this server was likely part of a red team engagement but with questionable OPSEC practices.
Justin also pointed out that the directory contained a text file of kerberoasted hashes. 'Kerberoasting' targets the Kerberos protocol, allowing the attacker to grab the password hashes of any Active Directory account with a set of Service Principal Name (SPN) attributes. The attacker would then move the hashes offline for cracking.
For obvious reasons we won't show the password hashes, but this is not the type of document to leave accessible to everyone, red team, or threat actor.
Cracked Cobalt Strike
The folder named after the red team framework weighs in at a hefty 126 MB, with 20+ files and multiple sub-folders. If you see a magnifying glass next to a filename, you can preview the content without moving to a VM to download it. Many other files are available for download or searching other IPs hosting the same content. *This feature is always available to Hunt users; please apply for an account if you haven't already.
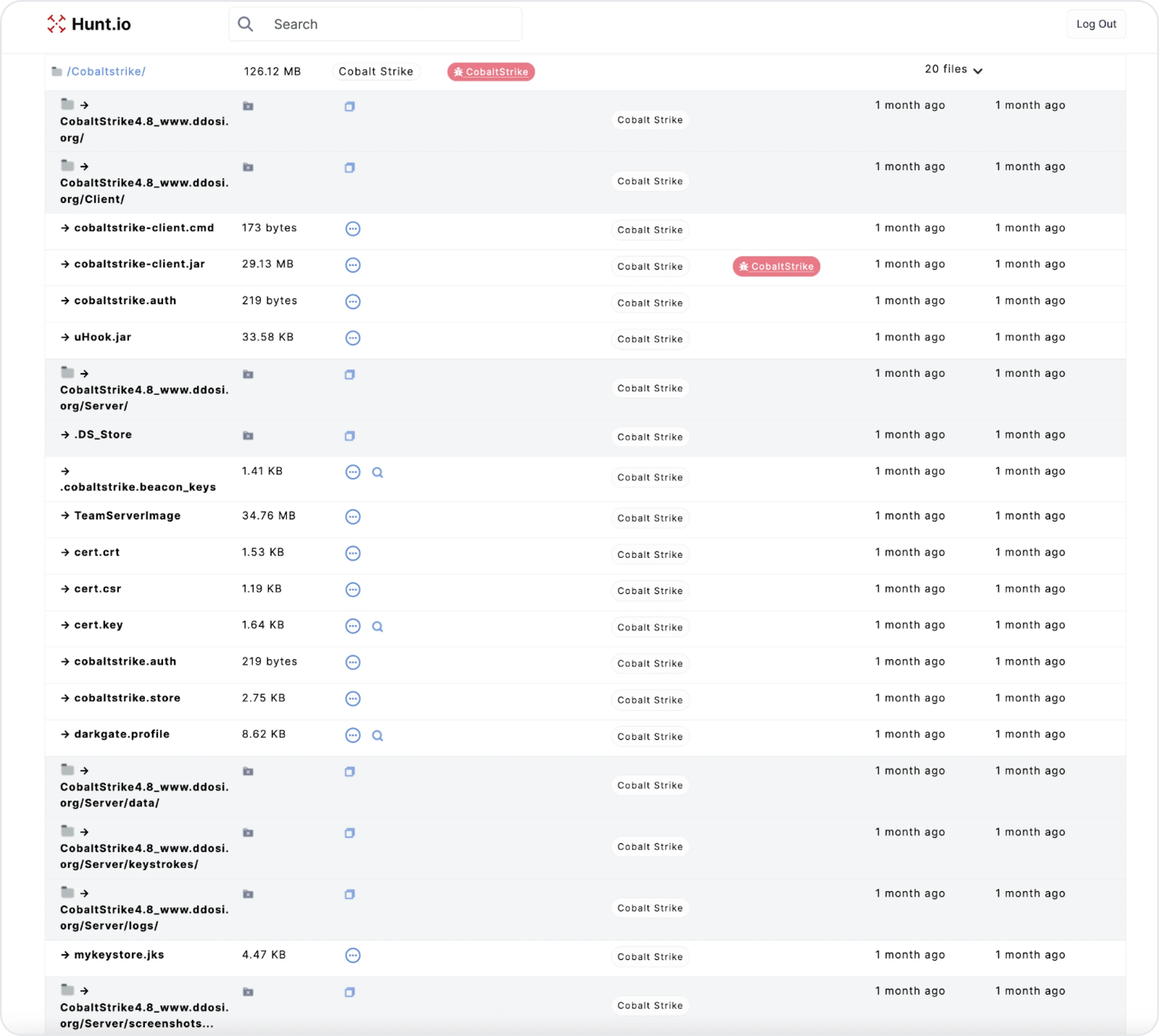 Figure 4: Snippet of files/folder hosted on the opendir
Figure 4: Snippet of files/folder hosted on the opendirThe directory hosts many files to analyze and understand how the operator uses Cobalt Strike and possibly find additional infrastructure. We can also see mentions of version 4.8 of the framework and ddosi[.]org. For those unaware, a cracked version of Cobalt Strike was hosted on the above website in April of last year.
So, in addition to the open directory, this individual(s) is also using cracked software to carry out attacks or testing.
The 'darkgate.profile file is likely a Malleable C2 configuration profile, allowing users to customize their communication channels with compromised machines. Analyzing this profile could provide valuable insights into the attacker's command and control infrastructure and techniques.
 Figure 5: Screenshot of Malleable C2 darkgate profile
Figure 5: Screenshot of Malleable C2 darkgate profileNot only do we see a file path to the encrypted keystore, but we also see TLS certificate information. As this is a cracked version of CS, we won't dig too much into the cobaltstrike.beacon_keys files or similar files.
We can use a few fields from the certificate using Hunt's Advanced Search feature to see if anyone else may be using this profile.
 Figure 6: Hunt result for C2 profile certificate
Figure 6: Hunt result for C2 profile certificateWe can see from the first and last seen timestamps that this server is relatively recent and likely still in use. Let's take a closer look.
 Figure 7: Hunt overview for matching IP address
Figure 7: Hunt overview for matching IP addressHunt has already indicated an instance of Cobalt Strike on port 50050, as indicated by the red arrow above.
The HTTP response on port 443 is routinely seen and associated with Cobalt Strike, and matching the certificate to the darkgate profile requires additional investigative work. At the time of writing, no beacon was associated with the port.
 Figure 8: HTTP response and certificate in Hunt
Figure 8: HTTP response and certificate in HuntConclusion
This open directory was a stark reminder of the dangers of insecure server configurations. Sensitive information, including red team tools and potentially a Malleable C2 profile for Cobalt Strike, were left completely exposed. This highlights the importance of strong security practices for organizations and emphasizes the need for red teams to prioritize operational security (OPSEC) during their engagements.
Further analysis of the "darkgate.profile" could reveal valuable insights into attacker techniques, but that's a story for another day.
Want to see what interesting items security researchers find in open directories? Apply for a Hunt account today and see how Hunt empowers organizations to actively defend their networks.
Introduction
While open directories are often seen as a goldmine for security researchers and blue teams searching for malware or phishing campaigns, the very ease of access that makes them attractive can be a double-edged sword. Directory indexing can leave sensitive information from organizations wholly exposed to anyone online.
Red teamers and threat actors who neglect to secure the data they obtain during operations properly can inadvertently create a similar situation. They leave their tools and techniques exposed for all to see, compromising the effectiveness of their current efforts and potentially revealing their tactics for future attacks.
In this post, we'll examine a case involving multiple red team tools, certificates, and even what appears to be the kerberoasted hashes of a large organization.
The Discovery
Justin Elze, Twitter(X): @HackingLZ was the first to notice the exposed directory in Hunt. He commented on how directory indexing commonly trips up red team operations in his post.
 Figure 1: Post by Justin leading to this blog (https://twitter.com/HackingLZ/status/1767610924599578740)
Figure 1: Post by Justin leading to this blog (https://twitter.com/HackingLZ/status/1767610924599578740)Looking at the files and folders within Justin's post, we can see three well-known command and control (C2) frameworks, CobaltStrike, Havoc, and Villian. Additionally, we can see an exposed SSH directory, bash history, a BloodHound zip file, and probable 7Zip binaries (likely used for exfiltration). We can also see typical red team PowerShell scripts to analyze networks and Active Directory environments.
Justin has already provided us with a great deal of information. Below is a quick overview of the IP address and Python SimpleHTTPServer where the directory was hosted.
 Figure 2: Hunt overview of the open directory server and port history
Figure 2: Hunt overview of the open directory server and port historyLet's touch on the rest of the files in the directory before we revisit Cobalt Strike.
 Figure 3: Screenshot of remaining files
Figure 3: Screenshot of remaining filesThe filenames within the directory are pretty descriptive, suggesting their intended purpose for red team activities. While these names might be changed before use in an actual attack, it leads us to believe this server was likely part of a red team engagement but with questionable OPSEC practices.
Justin also pointed out that the directory contained a text file of kerberoasted hashes. 'Kerberoasting' targets the Kerberos protocol, allowing the attacker to grab the password hashes of any Active Directory account with a set of Service Principal Name (SPN) attributes. The attacker would then move the hashes offline for cracking.
For obvious reasons we won't show the password hashes, but this is not the type of document to leave accessible to everyone, red team, or threat actor.
Cracked Cobalt Strike
The folder named after the red team framework weighs in at a hefty 126 MB, with 20+ files and multiple sub-folders. If you see a magnifying glass next to a filename, you can preview the content without moving to a VM to download it. Many other files are available for download or searching other IPs hosting the same content. *This feature is always available to Hunt users; please apply for an account if you haven't already.
 Figure 4: Snippet of files/folder hosted on the opendir
Figure 4: Snippet of files/folder hosted on the opendirThe directory hosts many files to analyze and understand how the operator uses Cobalt Strike and possibly find additional infrastructure. We can also see mentions of version 4.8 of the framework and ddosi[.]org. For those unaware, a cracked version of Cobalt Strike was hosted on the above website in April of last year.
So, in addition to the open directory, this individual(s) is also using cracked software to carry out attacks or testing.
The 'darkgate.profile file is likely a Malleable C2 configuration profile, allowing users to customize their communication channels with compromised machines. Analyzing this profile could provide valuable insights into the attacker's command and control infrastructure and techniques.
 Figure 5: Screenshot of Malleable C2 darkgate profile
Figure 5: Screenshot of Malleable C2 darkgate profileNot only do we see a file path to the encrypted keystore, but we also see TLS certificate information. As this is a cracked version of CS, we won't dig too much into the cobaltstrike.beacon_keys files or similar files.
We can use a few fields from the certificate using Hunt's Advanced Search feature to see if anyone else may be using this profile.
 Figure 6: Hunt result for C2 profile certificate
Figure 6: Hunt result for C2 profile certificateWe can see from the first and last seen timestamps that this server is relatively recent and likely still in use. Let's take a closer look.
 Figure 7: Hunt overview for matching IP address
Figure 7: Hunt overview for matching IP addressHunt has already indicated an instance of Cobalt Strike on port 50050, as indicated by the red arrow above.
The HTTP response on port 443 is routinely seen and associated with Cobalt Strike, and matching the certificate to the darkgate profile requires additional investigative work. At the time of writing, no beacon was associated with the port.
 Figure 8: HTTP response and certificate in Hunt
Figure 8: HTTP response and certificate in HuntConclusion
This open directory was a stark reminder of the dangers of insecure server configurations. Sensitive information, including red team tools and potentially a Malleable C2 profile for Cobalt Strike, were left completely exposed. This highlights the importance of strong security practices for organizations and emphasizes the need for red teams to prioritize operational security (OPSEC) during their engagements.
Further analysis of the "darkgate.profile" could reveal valuable insights into attacker techniques, but that's a story for another day.
Want to see what interesting items security researchers find in open directories? Apply for a Hunt account today and see how Hunt empowers organizations to actively defend their networks.
Related Posts
Related Posts
Related Posts


