
Hunt.io proprietary technologies deliver actionable intelligence with greater speed and accuracy than any other platform.

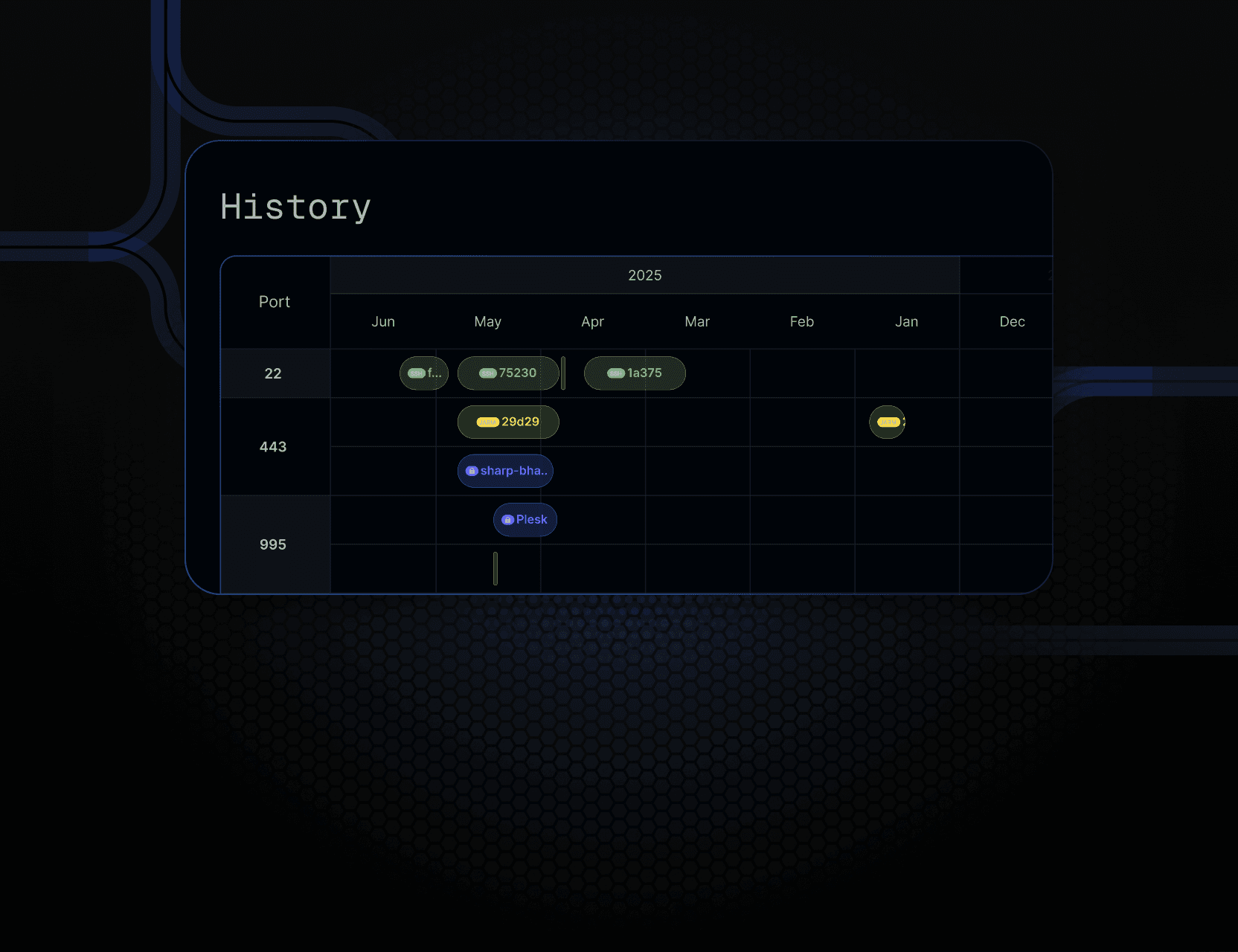
History
Track how JA4+ fingerprints appear, disappear, and shift over time across exposed services.

Search
Pivot from a single fingerprint to related infrastructure, services, and activity fast.

Your JA4+ Fingerprints
These fingerprints are unique to your session on this webpage
faq
What is JA4+ used for in Hunt?
JA4+ fingerprints are built into Hunt and exposed as pivots to help analyze and explore data across the platform.
How are JA4+ fingerprints added to Hunt?
JA4+ fingerprints are baked into Hunt through a partnership with Foxio, with ongoing collaboration to support modern pivots and fingerprints.
Where can JA4+ fingerprints be used?
JA4+ fingerprints are available across the Hunt platform wherever pivots and fingerprints are supported, such as our Historical timeline, our Search function, or by quering our datasets from HuntSQL.
What malicious activity can JA4+ fingerprints help uncover?
JA4+ fingerprints help uncover malicious infrastructure and activity such as command-and-control servers, malware networks, and related attacker assets by linking encrypted traffic patterns to known threat actor behaviour.
