How Hunt.io Identifies Services on Non-Standard Ports
Published on

Internet Scanning is challenging. With 3.7 billion usable IPV4 addresses and 65,000 ports, identifying running services and processes would take considerable time and bandwidth for all but the most prominent companies.
As defenders, we often approach scanning by focusing on the most commonly used ports (22 -- SSH, 80 - HTTP, etc.) where services usually reside. This approach allows for insights into a significant portion of the internet promptly while still respecting other networks.
To understand the services running, we need an innovative approach to explore every port while conserving bandwidth and not becoming a nuisance to network operators.
Join me as I delve into how Hunt uncovers services on non-standard ports, removing the constraints of traditional scanning and revealing malicious infrastructure.
Introducing GPS: The Scanning Platform
This section will provide a high-level overview of the GPS platform. Attempting to summarize the fantastic research by authors Liz Izhikevich, Renata Teixeira, & Zakir Durumericn would not do the paper justice. Please give the whitepaper a read and check out GPS' GitHub page.
Hunt does not merely identify malicious infrastructure through search engine queries alone but uses a powerful scanning platform named GPS (Graph Processing System).
Where GPS stands out is its ability to recognize services across all ports.According to the paper, "GPS employs an innovative predictive framework that showcases remarkable efficiency. It can effectively learn from extremely small sample sizes, making it a valuable tool for identifying patterns across all 65,000 ports and various features" [Izhikevich et al. 2022].
 Image 1: GPS Equations 2 & 3 For Finding Services. [Izhikevich et al. 2022]
Image 1: GPS Equations 2 & 3 For Finding Services. [Izhikevich et al. 2022]Our customized GPS implementation uses an expanded range of application, transport, and network layer features, which construct a predictive model of service presence through probabilistic analysis. Instead of the first stage scan GPS requires we simply stream in all the data that comes in from our standard data collection pipeline into the GPS prediction algorithms.
Liz Izhikevich, Renata Teixeira, and Zakir Durumeric. 2022. Predicting IPv4 Services Across All Ports. In ACM SIGCOMM 2022 Conference (SIGCOMM '22), August 22--26, 2022, Amsterdam, Netherlands. ACM, New York, NY, USA, 13 pages. https://doi.org/10.1145/3544216.3544249 , Accessed 15 October, 2023
Are you still with me? GPS represents a game-changing advancement for defenders investigating malicious/vulnerable infrastructure.
Utilizing this scanning system, defenders can now detect services running on obscure ports, leaving little room for the adversary to hide.
Hunt Plus GPS: A Real-World Example
Just last month, Hunt.io, with the help of GPS predictive scanning, identified a short-lived cluster of Cobalt Strike infrastructure running a beacon server on port 1799 and the team server on port 1788.
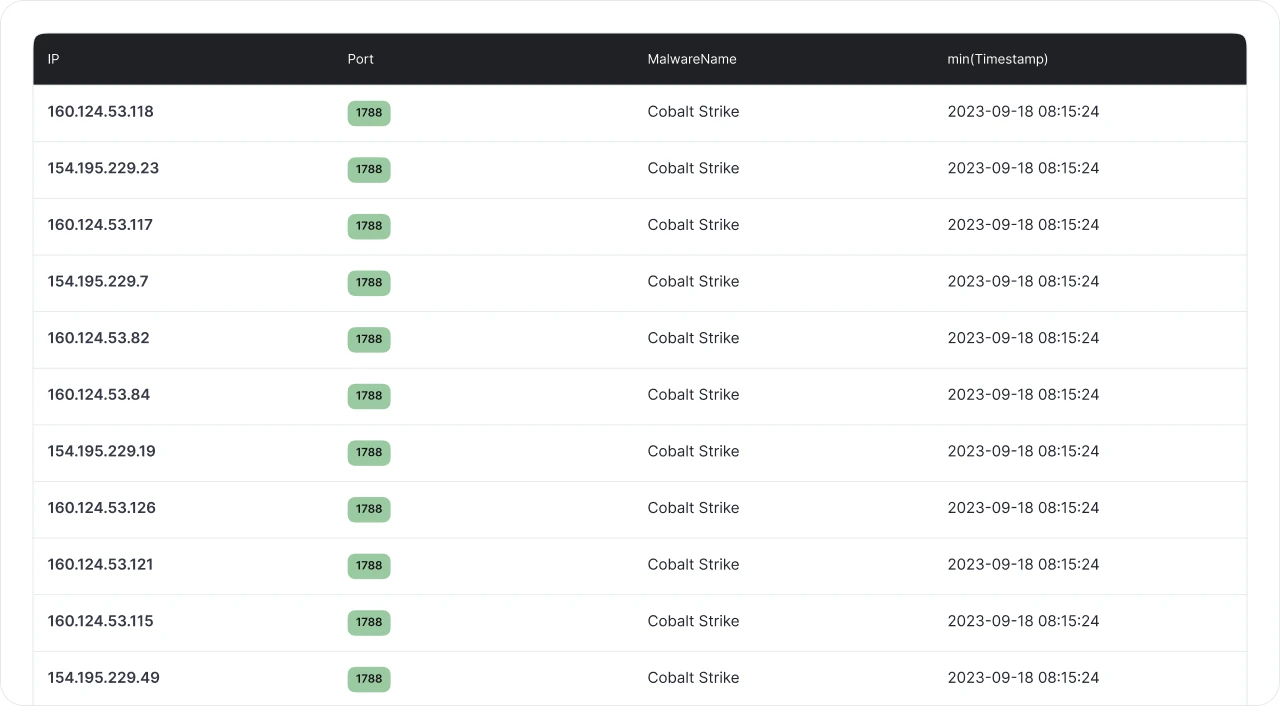 Image 2: Sample of the identified Cobalt Strike infrastructure
Image 2: Sample of the identified Cobalt Strike infrastructureAs GPS identifies services running on obscure ports, Hunt takes action and starts interrogating the service for known malware indicators (in this case, the default HTTP response for Cobalt Strike).
Let's head over to Hunt and query for malware using port 1788 using Advanced Search.
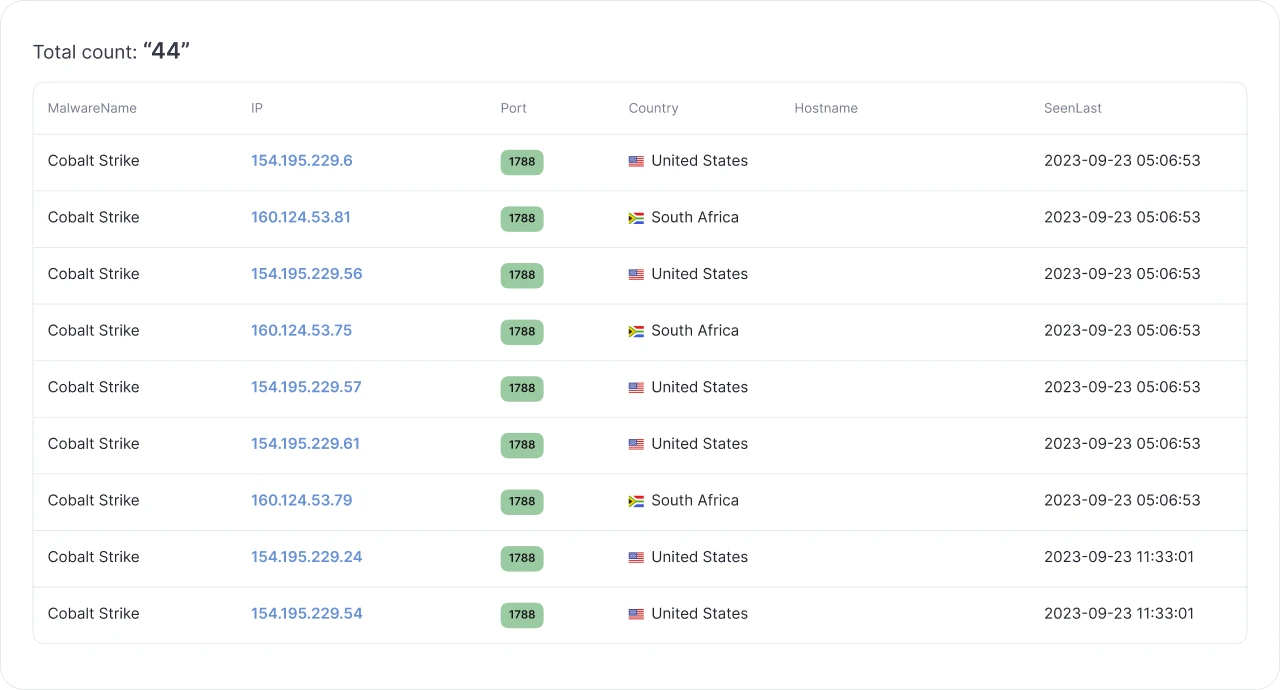 Image 3: Sample run of port 1788 (results as of 20 Oct 23)
Image 3: Sample run of port 1788 (results as of 20 Oct 23)Hunt returns 44 individual IP addresses already identified as Cobalt Strike, last seen September 23. As I alluded to earlier, Hunt first observed this group of IP addresses in the middle of September. Both the beacon and team servers disappeared on the 23rd.
While most IP addresses may no longer be running Cobalt Strike, Hunt has already captured a lengthy history of these servers available to us in just a few clicks.
 Image 4: Timeline of hosted certificates and malware
Image 4: Timeline of hosted certificates and malwareIn the above image, Hunt observed Cobalt Strike for ten (10) days. In addition to tracking possible malicious campaign timelines on a server, users can also view TLS certificates, which contain links to pivot on for additional threat hunting.
Conclusion
Malicious actors will continue to evolve in concealing their malicious infrastructure, including using non-standard ports. As defenders, we must adapt by looking beyond the standard ports and unmasking these services before they enter our networks.
Sign up, try Hunt today, and see what you can find!
Internet Scanning is challenging. With 3.7 billion usable IPV4 addresses and 65,000 ports, identifying running services and processes would take considerable time and bandwidth for all but the most prominent companies.
As defenders, we often approach scanning by focusing on the most commonly used ports (22 -- SSH, 80 - HTTP, etc.) where services usually reside. This approach allows for insights into a significant portion of the internet promptly while still respecting other networks.
To understand the services running, we need an innovative approach to explore every port while conserving bandwidth and not becoming a nuisance to network operators.
Join me as I delve into how Hunt uncovers services on non-standard ports, removing the constraints of traditional scanning and revealing malicious infrastructure.
Introducing GPS: The Scanning Platform
This section will provide a high-level overview of the GPS platform. Attempting to summarize the fantastic research by authors Liz Izhikevich, Renata Teixeira, & Zakir Durumericn would not do the paper justice. Please give the whitepaper a read and check out GPS' GitHub page.
Hunt does not merely identify malicious infrastructure through search engine queries alone but uses a powerful scanning platform named GPS (Graph Processing System).
Where GPS stands out is its ability to recognize services across all ports.According to the paper, "GPS employs an innovative predictive framework that showcases remarkable efficiency. It can effectively learn from extremely small sample sizes, making it a valuable tool for identifying patterns across all 65,000 ports and various features" [Izhikevich et al. 2022].
 Image 1: GPS Equations 2 & 3 For Finding Services. [Izhikevich et al. 2022]
Image 1: GPS Equations 2 & 3 For Finding Services. [Izhikevich et al. 2022]Our customized GPS implementation uses an expanded range of application, transport, and network layer features, which construct a predictive model of service presence through probabilistic analysis. Instead of the first stage scan GPS requires we simply stream in all the data that comes in from our standard data collection pipeline into the GPS prediction algorithms.
Liz Izhikevich, Renata Teixeira, and Zakir Durumeric. 2022. Predicting IPv4 Services Across All Ports. In ACM SIGCOMM 2022 Conference (SIGCOMM '22), August 22--26, 2022, Amsterdam, Netherlands. ACM, New York, NY, USA, 13 pages. https://doi.org/10.1145/3544216.3544249 , Accessed 15 October, 2023
Are you still with me? GPS represents a game-changing advancement for defenders investigating malicious/vulnerable infrastructure.
Utilizing this scanning system, defenders can now detect services running on obscure ports, leaving little room for the adversary to hide.
Hunt Plus GPS: A Real-World Example
Just last month, Hunt.io, with the help of GPS predictive scanning, identified a short-lived cluster of Cobalt Strike infrastructure running a beacon server on port 1799 and the team server on port 1788.
 Image 2: Sample of the identified Cobalt Strike infrastructure
Image 2: Sample of the identified Cobalt Strike infrastructureAs GPS identifies services running on obscure ports, Hunt takes action and starts interrogating the service for known malware indicators (in this case, the default HTTP response for Cobalt Strike).
Let's head over to Hunt and query for malware using port 1788 using Advanced Search.
 Image 3: Sample run of port 1788 (results as of 20 Oct 23)
Image 3: Sample run of port 1788 (results as of 20 Oct 23)Hunt returns 44 individual IP addresses already identified as Cobalt Strike, last seen September 23. As I alluded to earlier, Hunt first observed this group of IP addresses in the middle of September. Both the beacon and team servers disappeared on the 23rd.
While most IP addresses may no longer be running Cobalt Strike, Hunt has already captured a lengthy history of these servers available to us in just a few clicks.
 Image 4: Timeline of hosted certificates and malware
Image 4: Timeline of hosted certificates and malwareIn the above image, Hunt observed Cobalt Strike for ten (10) days. In addition to tracking possible malicious campaign timelines on a server, users can also view TLS certificates, which contain links to pivot on for additional threat hunting.
Conclusion
Malicious actors will continue to evolve in concealing their malicious infrastructure, including using non-standard ports. As defenders, we must adapt by looking beyond the standard ports and unmasking these services before they enter our networks.
Sign up, try Hunt today, and see what you can find!
Related Posts
Related Posts
Related Posts


