Phish No More: A Hunt.io Guide to Gophish Detection
Phish No More: A Hunt.io Guide to Gophish Detection
Published on
Oct 12, 2023



Phishing is more than a social engineering technique; it's a harrowing threat landscape where deception, innovation, and vigilance collide. In 2022, according to some sources, phishing scams alone were responsible for over 500 million reported attacks spanning a considerable target audience, from individuals and small businesses to large enterprises and government entities.

For threat hunters, preemptively identifying infrastructure regularly coaxing unsuspecting users is crucial, and Gophish---the overriding phishing framework showcased in this article---is no exception. Gophish's prevalence and extended accessibility to pentesters and cyber practitioners make it a worthy tool for honing security awareness, testing defenses, and ultimately strengthening an organization's resilience against real-world phishing threats.
Let's dive in as we take Hunt for another spin, this time setting our sights on the phishing paradigm and how we've tackled its elusive challenges head-on.
Enter Gophish: The 10,000-ft View
Despite the growing cyber defense landscape of the last few years, phishing (as a semantic attack vector) continues to thrive and ultimately succeed. Key research areas decisively point to potential solutions using machine learning algorithms primarily based on feature selection methods to reduce the problem space to one that combines behavioral analysis and anomaly detection---a suboptimal approach in cases where the ability to classify infrastructure quickly is lacking or missing.
In response to probable detection gaps, red teams and similar stakeholders looking to train and influence user behavior often employ third-party phishing kits to simulate entire email campaigns in a controlled and secure environment.
One of these frameworks is Gophish, an open-source, component-rich phishing (or anti-phishing, depending on your view) platform that equips operators with the ability to craft convincing phishing emails, replicate websites, and monitor recipient interactions, such as email opens and link clicks, with minimal effort.

Running a Gophish server is a breeze: pull and extract the binary or release for your operating system of choice, and after flying through the install, you'll be up and running in no time---as seen above, the remaining output will indicate the status of the database setup as well as the web interfaces you can connect to as you initiate your campaigns.
Detecting Gophish
In response to the phishing onslaught, companies like Google have consistently employed crawling and data collection mechanisms to index and catalog URLs and content potentially associated with phishing and similar harmful behavior.
For example, Google Safe Browsing pays particular attention to the domain name, checking if the domain closely resembles that of legitimate and trusted entities, such as banks, online retailers, or social media platforms. Consequently, it might look for slight misspellings or variations of a legitimate domain, commonly exploited by phishing sites to deceive users.
Additionally, interstitial sites, also known as interstitial pages or warning pages, play a crucial role in the phishing detection process by Google Safe Browsing. When a user attempts to access a website known or suspected as a phishing site, Safe Browsing can trigger an interstitial page in the user's web browser or application, alerting the user of the prospective danger ahead.
Where does Hunt come in?
Glad you asked.
Google Safe Browsing and comparable approaches exhibit some real-time detection opportunities. Still, while excelling at identifying known threats, their reliance on database matching (including user and community contributions) may have limitations with rapidly evolving or less well-known phishing sites.
Conversely, Hunt aggregates data from multiple security providers, uses machine learning algorithms and analyzes a broader range of data sources. This process allows it to detect emerging and previously unknown phishing threats more effectively. For instance, Hunt will enable organizations to customize threat intelligence feeds and configurations based on their specific threat profiles, providing a more tailored strategy for phishing detection.
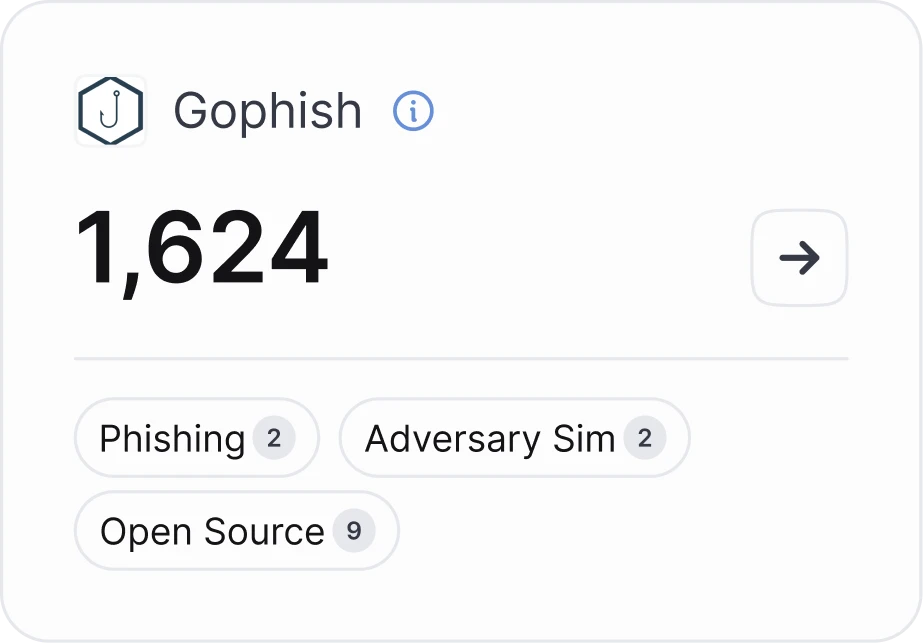
By default, Gophish exposes a limited amount of well-known identifiers (e.g., RID), but even these can be tampered with to avoid security controls.
By contrast, using our HTTP data, Hunt searches for potential Gophish candidates by looking for CSRF middleware in the form of _gorilla_csrf cookies and other "fingerprintable" URL elements such as /login?next=. By and large, integrating these elements into the detection model significantly reduces the number of false positives.

The above graph illustrates the fluctuations in the count of distinct active Gophish IP addresses over time. Similarly, we offer comparable metrics for active domains, which often mimic the profiles of reputable organizations, enticing potential victims into engaging with malicious content.

Summing It Up
Whether it's tracking C2 infrastructure or the latest Gophish campaign, coming to Hunt is the best decision you can make if you need fast, accurate, and reliable results. Even at an early stage, we're already dominating the threat-hunting and brand-protection fiefdoms, accounting for a substantial detection rate surpassing those of the most prominent players.
Adopting Hunt as your next hunting platform will confirm your commitment to staying one step ahead in the ever-changing landscape of digital threats.
Phishing is more than a social engineering technique; it's a harrowing threat landscape where deception, innovation, and vigilance collide. In 2022, according to some sources, phishing scams alone were responsible for over 500 million reported attacks spanning a considerable target audience, from individuals and small businesses to large enterprises and government entities.

For threat hunters, preemptively identifying infrastructure regularly coaxing unsuspecting users is crucial, and Gophish---the overriding phishing framework showcased in this article---is no exception. Gophish's prevalence and extended accessibility to pentesters and cyber practitioners make it a worthy tool for honing security awareness, testing defenses, and ultimately strengthening an organization's resilience against real-world phishing threats.
Let's dive in as we take Hunt for another spin, this time setting our sights on the phishing paradigm and how we've tackled its elusive challenges head-on.
Enter Gophish: The 10,000-ft View
Despite the growing cyber defense landscape of the last few years, phishing (as a semantic attack vector) continues to thrive and ultimately succeed. Key research areas decisively point to potential solutions using machine learning algorithms primarily based on feature selection methods to reduce the problem space to one that combines behavioral analysis and anomaly detection---a suboptimal approach in cases where the ability to classify infrastructure quickly is lacking or missing.
In response to probable detection gaps, red teams and similar stakeholders looking to train and influence user behavior often employ third-party phishing kits to simulate entire email campaigns in a controlled and secure environment.
One of these frameworks is Gophish, an open-source, component-rich phishing (or anti-phishing, depending on your view) platform that equips operators with the ability to craft convincing phishing emails, replicate websites, and monitor recipient interactions, such as email opens and link clicks, with minimal effort.

Running a Gophish server is a breeze: pull and extract the binary or release for your operating system of choice, and after flying through the install, you'll be up and running in no time---as seen above, the remaining output will indicate the status of the database setup as well as the web interfaces you can connect to as you initiate your campaigns.
Detecting Gophish
In response to the phishing onslaught, companies like Google have consistently employed crawling and data collection mechanisms to index and catalog URLs and content potentially associated with phishing and similar harmful behavior.
For example, Google Safe Browsing pays particular attention to the domain name, checking if the domain closely resembles that of legitimate and trusted entities, such as banks, online retailers, or social media platforms. Consequently, it might look for slight misspellings or variations of a legitimate domain, commonly exploited by phishing sites to deceive users.
Additionally, interstitial sites, also known as interstitial pages or warning pages, play a crucial role in the phishing detection process by Google Safe Browsing. When a user attempts to access a website known or suspected as a phishing site, Safe Browsing can trigger an interstitial page in the user's web browser or application, alerting the user of the prospective danger ahead.
Where does Hunt come in?
Glad you asked.
Google Safe Browsing and comparable approaches exhibit some real-time detection opportunities. Still, while excelling at identifying known threats, their reliance on database matching (including user and community contributions) may have limitations with rapidly evolving or less well-known phishing sites.
Conversely, Hunt aggregates data from multiple security providers, uses machine learning algorithms and analyzes a broader range of data sources. This process allows it to detect emerging and previously unknown phishing threats more effectively. For instance, Hunt will enable organizations to customize threat intelligence feeds and configurations based on their specific threat profiles, providing a more tailored strategy for phishing detection.

By default, Gophish exposes a limited amount of well-known identifiers (e.g., RID), but even these can be tampered with to avoid security controls.
By contrast, using our HTTP data, Hunt searches for potential Gophish candidates by looking for CSRF middleware in the form of _gorilla_csrf cookies and other "fingerprintable" URL elements such as /login?next=. By and large, integrating these elements into the detection model significantly reduces the number of false positives.

The above graph illustrates the fluctuations in the count of distinct active Gophish IP addresses over time. Similarly, we offer comparable metrics for active domains, which often mimic the profiles of reputable organizations, enticing potential victims into engaging with malicious content.

Summing It Up
Whether it's tracking C2 infrastructure or the latest Gophish campaign, coming to Hunt is the best decision you can make if you need fast, accurate, and reliable results. Even at an early stage, we're already dominating the threat-hunting and brand-protection fiefdoms, accounting for a substantial detection rate surpassing those of the most prominent players.
Adopting Hunt as your next hunting platform will confirm your commitment to staying one step ahead in the ever-changing landscape of digital threats.
Related Posts
Related Posts
Related Posts
©2026 Hunt Intelligence, Inc.
©2026 Hunt Intelligence, Inc.
©2025 Hunt Intelligence, Inc.


