Legacy Threat: PlugX Builder/Controller Discovered in Open Directory
Published on

As part of our continuous threat research and monitoring of open directories, the Hunt Research Team discovered an exposed server hosted in the Czech Republic that contained an outdated PlugX builder and controller.
The threat actor(s) built and controlled at least one of the binaries on the same server, granting us access to numerous critical files. These include logs, encrypted .dat files, and a folder that appears to contain data from victims infected by the malware.
A VBA script disguised as a text file further raised our suspicions. The script downloaded three files from a domain registered to a Nepalese government entity.
This post will describe the builder and controller's features and capabilities, examine the previously mentioned script, and discuss additional IP addresses identified as command and control infrastructure for Korplug samples on the server. Due to the sensitive nature of some of the server's files, we will obscure details that may identify the IP address.
*Hunt has shared the details of our findings with the Nepal Computer Emergency Response Team (CERT).
Open Directories in Hunt
The open directory that initiated this research is hosted at “Stark Industries Solutions,” a common provider for malicious actors seeking virtual private servers (VPS).
Assist us in analyzing over 6,000 exposed servers available through the Open Directories feature in Hunt (Access requires an account).
Figure 1 provides a snippet of the hosted files.
 Figure 1: Screenshot of Open Directory
Figure 1: Screenshot of Open DirectoryThere are 17 ports associated with the suspect IP. Many don’t give us much to pivot on regarding services except for one. The screenshot below shows an HTTP response on port 12345 with a server version of “Apache 1.3.27”, both indicators of PlugX activity.
 Figure 2: Port 12345 Apache 1.3.27 HTTP Response
Figure 2: Port 12345 Apache 1.3.27 HTTP ResponseLater in the post, we will revisit several other IP addresses that serve as command and control infrastructure for some of the server's files.
Let's examine what we believe to be a version 2 PlugX builder.
Version Two Builder
PlugX's source code allegedly leaked online some time ago, expanding its availability beyond the Chinese APT groups that have historically deployed it. This unknown version of the RAT is now accessible to a broader range of threat actors
The builder, similar to the one detailed in an Airbus blog post, enables operators to customize their tools by adding custom DNS servers and proxy infrastructure and adding or removing features such as keylogging, screen recording, and much more.
 Figure 3: Korplug Builder
Figure 3: Korplug BuilderAt the top of the builder window are a range of dates, starting with what appears to be August 2014 until early 2015, giving us a rough estimate of when the tool was developed.
Import/Export Config: The config files contain information such as the C2 domain/IP, port, network protocol, payload file names, etc.
First: Server password, server status, mutex (My_Name is the default), and customized MAC address.
Online: Input C2 domain/IP, port, and protocol (HTTP, TCP, UDP, ICMP, DNS).
Online(Web): C2 setting URL, port, and encoded C2 setting.
LanProxy: allows the operator to enable a TCP, UDP, ICMP, or RAW proxy port and a customized range of LAN IP addresses.
Install: Select a service for PlugX to masquerade as and choose a registry location for persistence.
Inject: Application process to inject into. The default is wmiplayer.exe.
DNS: Enable up to 4 custom DNS servers.
Proxy: Select a SOCKS4/5 or HTTP proxy server, port, username, and password.
ScreenRecorder: Enable/Disable a directory to save images. This feature is turned off by default.
Schedule: Online status of victims by hour and week.
Option: Additional options to include in the executable before compiling (all are enabled by default).
- Keylogger
- Hide Service
- Delete Self
- Show Error Message
- Check AVM By 60GB Disk Size
Screenshots of several key modules are included below to help understand the builder better.
 Figure 4: C2 Settings
Figure 4: C2 Settings Figure 5: Service Masquerading as McAfee AV and Registry Location
Figure 5: Service Masquerading as McAfee AV and Registry Location Figure 6: Process Injection Options
Figure 6: Process Injection Options Figure 7: EXE/Binary Options
Figure 7: EXE/Binary OptionsThe builder compiles a Windows executable named “m.exe.”
DeceptiController
In addition to providing remote control of the infected system, the controller supports the following commands:
DOS commands
Disk Management
File Transfer
Service Management
Registry Management
Screenshot
Local & Remote logs.
 Figure 8: PlugX Controller Listener Settings
Figure 8: PlugX Controller Listener SettingsExploring the Directory
The directory includes many well-known tools used in offensive security operations, such as Evil-WinRM, Proxifier, and FScan.
The first executable we encountered, 111.exe, follows the well-reported "PlugX trinity" execution workflow: a legitimate executable file vulnerable to DLL sideloading, an accompanying DLL, and a payload file.
As shown in Figure 5, the builder mimics the McAfee Antivirus service. When extracted, the executable drops Mc.cp, Mc.exe, and McUtil.dll. These filenames have been mentioned in public reporting, as seen here and here.
The ddd/ folder contains these files separately.
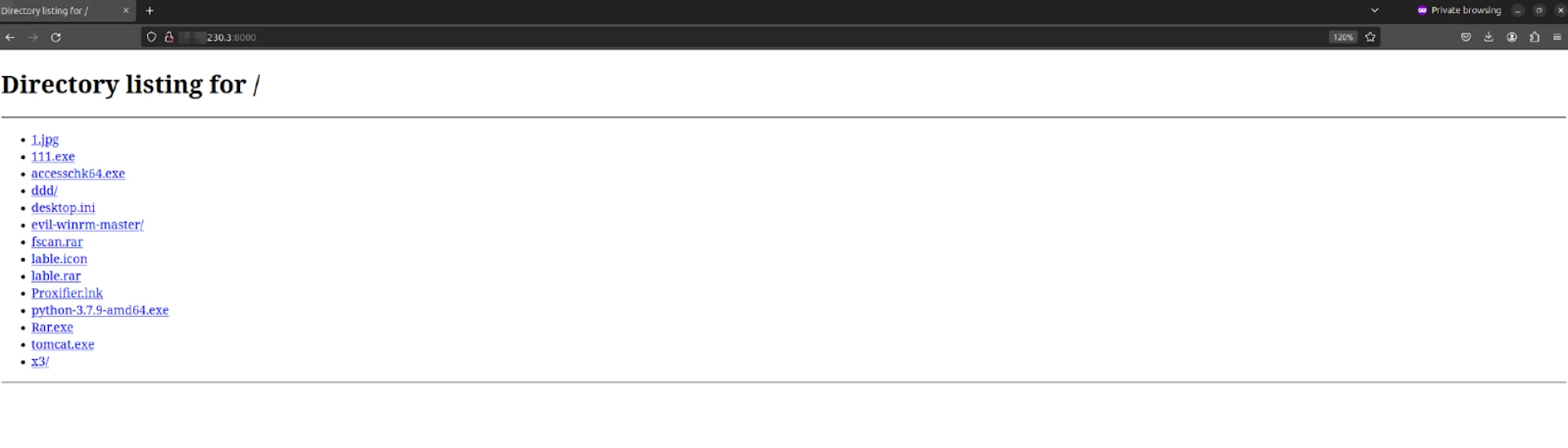 Figure 9: The Root Directory of Opendir
Figure 9: The Root Directory of OpendirThe x3/ folder contains both the controller and builder and most of the files we covered today, so we’ll start there.
Within the same directory under the x2/ folder is the builder referenced earlier, an additional folder named “data,” which contains backup configuration files, and a text file in Chinese, which translates roughly to “New text document.”
 Figure 10: Contents of “/x2” Folder
Figure 10: Contents of “/x2” FolderEvery sub-folder in the directory contains one of the text files mentioned above. All include the same content: a command to read a binary file, ‘payload.bin,’ encode it into a single-line Base64 string, and output the result to the terminal. The file also includes a domain name and LAN proxy port of 34675. Interestingly, the file payload.bin was not found on the server.
 Figure 11: Contents of “New Text Document.txt”
Figure 11: Contents of “New Text Document.txt”Moving to the following folder, /m/, we again encounter the trio of PlugX files. Additionally, we find a file named sweetpotatos.exe, which corresponds to the open-source project SweetPotato, as well as multiple other EXE and TXT files.
The remaining EXE files are detected as Korplug.
 Figure 12: Files and Folders within the “/m” Directory.
Figure 12: Files and Folders within the “/m” Directory.Mcd.txt, Mce.txt, and Mcp.txt contain a header and footer consistent with certificate data, but upon closer inspection, are, in reality, Base64 encoded strings beginning with TVq, which decodes to the Windows MZ header for applications.
As of 26 May, the files were still available on the web server.
 Figure 13: VBA Script within .txt File
Figure 13: VBA Script within .txt FileEven if you aren’t familiar with VBA, the code is relatively easy to comprehend and understand the author's intent.
The script downloads three files from specified URLs to local paths and then executes one of the files based on a pre-set choice. ‘DownloadFile’ handles the HTTP GET requests and saves the files locally using ‘ADODB.Stream.’ VBA scripts are a frequent occurrence for those who regularly analyze malicious files.
Where things become concerning is the domain from which the three files (our PlugX trinity) are downloaded. These files are hosted on a Nepalese government website, indicating that the web server has been compromised.
Several questions remain unanswered at this time: How did the files get onto the server? Was the threat actor running this open directory responsible for the initial compromise, or was access passed on to them?
The “computers” Directory
When a new user or computer connects to the controller, a folder with a randomly generated name is created. Within the computers folder, we found more than 50 entries. Some of these entries appear to be test runs of the malware, while others seem to represent infected hosts.
 Figure 14: Screenshot of /computers Folder
Figure 14: Screenshot of /computers FolderEach folder contains log files, the results of commands executed, and an encrypted or encoded .dat file.
 Figure 15: Contents of One of the Possible ‘victim’ Folders
Figure 15: Contents of One of the Possible ‘victim’ FoldersThe log files contain a timestamp, computer name, and the status of the infected host, indicating whether it is "online" or "offline."
Figure 16 shows an example log file from one of the many folders.
 Figure 16: Log File from One of the ‘victim’ Folders.
Figure 16: Log File from One of the ‘victim’ Folders.The .dat file, named "online.dat," is encoded/encrypted and contains the following message as a header: "####### PELEASE DO NOT CHANGE THE DOCAMENT!!! #######". The encoded/encrypted content follows this header.
 Figure 17: Contents of online.dat File
Figure 17: Contents of online.dat FileAdditional PlugX Command & Control IP
The directory contains several files, including instructions.exe, update_original.exe, encrypt_v3.2.exe, and lable.icon, which appears to be a modified version of the well-known Nmap network scanning tool.
All of these files are identified as variants of Korplug, beaconing to a Vultr Holdings VPS located in India. Similar to our initial findings, this VPS has many open ports, notably ports 80 and 443 running Apache 1.3.27, which is characteristic of Korplug/PlugX activity.
 Figure 18: Additional Korplug/PlugX Server
Figure 18: Additional Korplug/PlugX ServerWrap-Up
Defenders should not overlook open directories and older malware samples. Our findings reveal that these seemingly outdated tools, like the PlugX builder and controller, remain active threats capable of exploiting networks. Threat actors often use older samples to bypass modern defenses, underscoring the importance of continuous vigilance.
Hunt users can use the Open Directories feature to find exposed servers like the one discussed in this post and more, allowing them to track threat actor TTPs and protect their networks. Sign up for an account with Hunt to equip yourself with the necessary tools and insights for effective network protection.
Indicators
| IP Addresses |
|---|
| 77.75.230_3 |
| Filename | SHA-256 |
|---|---|
| 111.exe | 1c3954b25fe7d32b72c8c8d7d9b6a1a3b9ff4d175b55cbaade435e0c770d0595 |
| 1.jpg | 3a5088295708d3304f06de0499b9243bfbd68d14878615c531f0e346f47b389d |
| fscan.rar | 01f11f89c1ef84e60068e60a6d9dff2d2277341673a981ecbf864dcaf72e7f30 |
| lable.rar | 76d590c38387f6042ad39b20cd86ea5a0f2632889e4dd18d67d2a7a188d20890 |
| lable.icon | 285f9d4a3d5511e68ccc9ff14f209ac6cfdc0c3a51063d217190d5b8d49c2e47 |
| rar.exe | a9cec009503d067f241b5eddaea4e42c38edcb0b57c1b46e946c5281b7f1ea21 |
| x3avast.exe | b150773df7b525ce2b70822a06c06241f251eae96c9ee12fc97776d3826d36a7 |
Editor's Note: added IOC tables @ 8:00PM EST on Jun 5
As part of our continuous threat research and monitoring of open directories, the Hunt Research Team discovered an exposed server hosted in the Czech Republic that contained an outdated PlugX builder and controller.
The threat actor(s) built and controlled at least one of the binaries on the same server, granting us access to numerous critical files. These include logs, encrypted .dat files, and a folder that appears to contain data from victims infected by the malware.
A VBA script disguised as a text file further raised our suspicions. The script downloaded three files from a domain registered to a Nepalese government entity.
This post will describe the builder and controller's features and capabilities, examine the previously mentioned script, and discuss additional IP addresses identified as command and control infrastructure for Korplug samples on the server. Due to the sensitive nature of some of the server's files, we will obscure details that may identify the IP address.
*Hunt has shared the details of our findings with the Nepal Computer Emergency Response Team (CERT).
Open Directories in Hunt
The open directory that initiated this research is hosted at “Stark Industries Solutions,” a common provider for malicious actors seeking virtual private servers (VPS).
Assist us in analyzing over 6,000 exposed servers available through the Open Directories feature in Hunt (Access requires an account).
Figure 1 provides a snippet of the hosted files.
 Figure 1: Screenshot of Open Directory
Figure 1: Screenshot of Open DirectoryThere are 17 ports associated with the suspect IP. Many don’t give us much to pivot on regarding services except for one. The screenshot below shows an HTTP response on port 12345 with a server version of “Apache 1.3.27”, both indicators of PlugX activity.
 Figure 2: Port 12345 Apache 1.3.27 HTTP Response
Figure 2: Port 12345 Apache 1.3.27 HTTP ResponseLater in the post, we will revisit several other IP addresses that serve as command and control infrastructure for some of the server's files.
Let's examine what we believe to be a version 2 PlugX builder.
Version Two Builder
PlugX's source code allegedly leaked online some time ago, expanding its availability beyond the Chinese APT groups that have historically deployed it. This unknown version of the RAT is now accessible to a broader range of threat actors
The builder, similar to the one detailed in an Airbus blog post, enables operators to customize their tools by adding custom DNS servers and proxy infrastructure and adding or removing features such as keylogging, screen recording, and much more.
 Figure 3: Korplug Builder
Figure 3: Korplug BuilderAt the top of the builder window are a range of dates, starting with what appears to be August 2014 until early 2015, giving us a rough estimate of when the tool was developed.
Import/Export Config: The config files contain information such as the C2 domain/IP, port, network protocol, payload file names, etc.
First: Server password, server status, mutex (My_Name is the default), and customized MAC address.
Online: Input C2 domain/IP, port, and protocol (HTTP, TCP, UDP, ICMP, DNS).
Online(Web): C2 setting URL, port, and encoded C2 setting.
LanProxy: allows the operator to enable a TCP, UDP, ICMP, or RAW proxy port and a customized range of LAN IP addresses.
Install: Select a service for PlugX to masquerade as and choose a registry location for persistence.
Inject: Application process to inject into. The default is wmiplayer.exe.
DNS: Enable up to 4 custom DNS servers.
Proxy: Select a SOCKS4/5 or HTTP proxy server, port, username, and password.
ScreenRecorder: Enable/Disable a directory to save images. This feature is turned off by default.
Schedule: Online status of victims by hour and week.
Option: Additional options to include in the executable before compiling (all are enabled by default).
- Keylogger
- Hide Service
- Delete Self
- Show Error Message
- Check AVM By 60GB Disk Size
Screenshots of several key modules are included below to help understand the builder better.
 Figure 4: C2 Settings
Figure 4: C2 Settings Figure 5: Service Masquerading as McAfee AV and Registry Location
Figure 5: Service Masquerading as McAfee AV and Registry Location Figure 6: Process Injection Options
Figure 6: Process Injection Options Figure 7: EXE/Binary Options
Figure 7: EXE/Binary OptionsThe builder compiles a Windows executable named “m.exe.”
DeceptiController
In addition to providing remote control of the infected system, the controller supports the following commands:
DOS commands
Disk Management
File Transfer
Service Management
Registry Management
Screenshot
Local & Remote logs.
 Figure 8: PlugX Controller Listener Settings
Figure 8: PlugX Controller Listener SettingsExploring the Directory
The directory includes many well-known tools used in offensive security operations, such as Evil-WinRM, Proxifier, and FScan.
The first executable we encountered, 111.exe, follows the well-reported "PlugX trinity" execution workflow: a legitimate executable file vulnerable to DLL sideloading, an accompanying DLL, and a payload file.
As shown in Figure 5, the builder mimics the McAfee Antivirus service. When extracted, the executable drops Mc.cp, Mc.exe, and McUtil.dll. These filenames have been mentioned in public reporting, as seen here and here.
The ddd/ folder contains these files separately.
 Figure 9: The Root Directory of Opendir
Figure 9: The Root Directory of OpendirThe x3/ folder contains both the controller and builder and most of the files we covered today, so we’ll start there.
Within the same directory under the x2/ folder is the builder referenced earlier, an additional folder named “data,” which contains backup configuration files, and a text file in Chinese, which translates roughly to “New text document.”
 Figure 10: Contents of “/x2” Folder
Figure 10: Contents of “/x2” FolderEvery sub-folder in the directory contains one of the text files mentioned above. All include the same content: a command to read a binary file, ‘payload.bin,’ encode it into a single-line Base64 string, and output the result to the terminal. The file also includes a domain name and LAN proxy port of 34675. Interestingly, the file payload.bin was not found on the server.
 Figure 11: Contents of “New Text Document.txt”
Figure 11: Contents of “New Text Document.txt”Moving to the following folder, /m/, we again encounter the trio of PlugX files. Additionally, we find a file named sweetpotatos.exe, which corresponds to the open-source project SweetPotato, as well as multiple other EXE and TXT files.
The remaining EXE files are detected as Korplug.
 Figure 12: Files and Folders within the “/m” Directory.
Figure 12: Files and Folders within the “/m” Directory.Mcd.txt, Mce.txt, and Mcp.txt contain a header and footer consistent with certificate data, but upon closer inspection, are, in reality, Base64 encoded strings beginning with TVq, which decodes to the Windows MZ header for applications.
As of 26 May, the files were still available on the web server.
 Figure 13: VBA Script within .txt File
Figure 13: VBA Script within .txt FileEven if you aren’t familiar with VBA, the code is relatively easy to comprehend and understand the author's intent.
The script downloads three files from specified URLs to local paths and then executes one of the files based on a pre-set choice. ‘DownloadFile’ handles the HTTP GET requests and saves the files locally using ‘ADODB.Stream.’ VBA scripts are a frequent occurrence for those who regularly analyze malicious files.
Where things become concerning is the domain from which the three files (our PlugX trinity) are downloaded. These files are hosted on a Nepalese government website, indicating that the web server has been compromised.
Several questions remain unanswered at this time: How did the files get onto the server? Was the threat actor running this open directory responsible for the initial compromise, or was access passed on to them?
The “computers” Directory
When a new user or computer connects to the controller, a folder with a randomly generated name is created. Within the computers folder, we found more than 50 entries. Some of these entries appear to be test runs of the malware, while others seem to represent infected hosts.
 Figure 14: Screenshot of /computers Folder
Figure 14: Screenshot of /computers FolderEach folder contains log files, the results of commands executed, and an encrypted or encoded .dat file.
 Figure 15: Contents of One of the Possible ‘victim’ Folders
Figure 15: Contents of One of the Possible ‘victim’ FoldersThe log files contain a timestamp, computer name, and the status of the infected host, indicating whether it is "online" or "offline."
Figure 16 shows an example log file from one of the many folders.
 Figure 16: Log File from One of the ‘victim’ Folders.
Figure 16: Log File from One of the ‘victim’ Folders.The .dat file, named "online.dat," is encoded/encrypted and contains the following message as a header: "####### PELEASE DO NOT CHANGE THE DOCAMENT!!! #######". The encoded/encrypted content follows this header.
 Figure 17: Contents of online.dat File
Figure 17: Contents of online.dat FileAdditional PlugX Command & Control IP
The directory contains several files, including instructions.exe, update_original.exe, encrypt_v3.2.exe, and lable.icon, which appears to be a modified version of the well-known Nmap network scanning tool.
All of these files are identified as variants of Korplug, beaconing to a Vultr Holdings VPS located in India. Similar to our initial findings, this VPS has many open ports, notably ports 80 and 443 running Apache 1.3.27, which is characteristic of Korplug/PlugX activity.
 Figure 18: Additional Korplug/PlugX Server
Figure 18: Additional Korplug/PlugX ServerWrap-Up
Defenders should not overlook open directories and older malware samples. Our findings reveal that these seemingly outdated tools, like the PlugX builder and controller, remain active threats capable of exploiting networks. Threat actors often use older samples to bypass modern defenses, underscoring the importance of continuous vigilance.
Hunt users can use the Open Directories feature to find exposed servers like the one discussed in this post and more, allowing them to track threat actor TTPs and protect their networks. Sign up for an account with Hunt to equip yourself with the necessary tools and insights for effective network protection.
Indicators
| IP Addresses |
|---|
| 77.75.230_3 |
| Filename | SHA-256 |
|---|---|
| 111.exe | 1c3954b25fe7d32b72c8c8d7d9b6a1a3b9ff4d175b55cbaade435e0c770d0595 |
| 1.jpg | 3a5088295708d3304f06de0499b9243bfbd68d14878615c531f0e346f47b389d |
| fscan.rar | 01f11f89c1ef84e60068e60a6d9dff2d2277341673a981ecbf864dcaf72e7f30 |
| lable.rar | 76d590c38387f6042ad39b20cd86ea5a0f2632889e4dd18d67d2a7a188d20890 |
| lable.icon | 285f9d4a3d5511e68ccc9ff14f209ac6cfdc0c3a51063d217190d5b8d49c2e47 |
| rar.exe | a9cec009503d067f241b5eddaea4e42c38edcb0b57c1b46e946c5281b7f1ea21 |
| x3avast.exe | b150773df7b525ce2b70822a06c06241f251eae96c9ee12fc97776d3826d36a7 |
Editor's Note: added IOC tables @ 8:00PM EST on Jun 5
Related Posts
Related Posts
Related Posts


