Abusing Paste.ee to Deploy XWorm and AsyncRAT Across Global C2 Infrastructure
Abusing Paste.ee to Deploy XWorm and AsyncRAT Across Global C2 Infrastructure
Published on
Jun 5, 2025

While reviewing recent malware submissions from a public repository, we flagged a small JavaScript file packed with unusual Unicode characters and broken syntax. At first glance, it looked like malformed or incomplete code, but it was actually a disguised downloader contacting paste.ee, a legitimate service often abused to host staged payloads.
What appeared to be a standalone script turned out to be part of a broader campaign involving obfuscation, paste sites, and globally distributed C2 infrastructure tied to known remote access tools.
Further analysis revealed links to XWorm, a stealthy RAT with capabilities like keystroke logging, data exfiltration, and persistent remote access. In this report, we detail how we traced the activity, extracted IOCs, and built regex and SSL fingerprinting techniques to help defenders detect similar threats.
Technical Analysis
Our research team discovered this script while monitoring newly uploaded samples to MalwareBazaar.
It was immediately flagged with the RemcosRAT signature and caught our attention due to its deceptive filename: "DOCUMENT FOR DELIVERY INFORMATION.js". At just under 3KB, it may look harmless, but its behavior and indicators revealed a clear link to a known remote access trojan.
This sample became the starting point for our investigation, and what we found next shows how attackers continue to rely on small, weaponized scripts to deliver powerful malware.
 Fig 01. Obfuscated JavaScript on MalwareBaazer
Fig 01. Obfuscated JavaScript on MalwareBaazerThis JavaScript code is an obfuscated malicious script designed to download and execute code from a paste.ee. It hides its true functionality by inserting a long sequence of unusual Unicode characters
(ᙓೇᰖ∛ᩕዀ╬ᤳK⨀Ḣڑ⦝〒) throughout strings. These characters are later removed to reveal the actual commands and object names.
The script dynamically reconstructs the name of the
MSXML2.XMLHTTP ActiveX object, which is used to make an HTTP request. It then builds a hidden URL by removing the same junk characters from an obfuscated string, ultimately forming a complete address like
http://paste.ee/d/s1uVin8i/0.
The script sends a GET request to this URL, retrieves the response (typically malicious code), and immediately executes it using the
Function constructor.
 Fig 02: Deobfuscate JavaScript Code
Fig 02: Deobfuscate JavaScript CodeWe started by scanning the domain paste.ee using the Hunt.io web interface to uncover any IOCs or malicious activity associated with it.
 Fig 03: Resolved IP Related to paste.ee on the Hunt.io Platform
Fig 03: Resolved IP Related to paste.ee on the Hunt.io PlatformAccording to the results we got, this is an apex domain with the hostname paste.ee and resolves to the IP address 23.186.113.60. Hunt.io currently links the domain to
230 phishing URLs, 12 IOCs, and over 9,500 URLs in total.
 Fig 04: Phishing URLs Related to passte.ee on the Hunt.io platform
Fig 04: Phishing URLs Related to passte.ee on the Hunt.io platformRegex Hunting Based on Phishing URL Structure
After analyzing the phishing URLs associated with the domain
paste.ee, we observed recurring patterns in their structure. Due to these similarities, we decided to craft a regex
https:\/\/paste\.ee\/[a-z]\/[A-Za-z0-9]+\/0$ to hunt and detect related malicious URLs.
 Fig 05: Phishing URLs Regex Hunting Using Hunt.io SQL
Fig 05: Phishing URLs Regex Hunting Using Hunt.io SQLWe want to analyze potentially malicious infrastructure or check out web assets found in malware data, the first step is to pull out the relevant URLs from an NDJSON file. This NDJSON file usually contains a bunch of JSON objects, each with URLs and some extra info. To get just the URLs, we use a handy command-line tool called jq. Running this command:
jq -r ".url" export.ndjson > urls.txt
Copytakes the NDJSON file (
export.ndjson), grabs the URLs from each entry, and saves them into a simple text file (
urls.txt). This ensures the URLs are clean (no quotes or extra characters) so they're ready for the next steps.
After we have this clean list, we use another tool called httpx from ProjectDiscovery to check the status of each URL. Basically, we want to see which sites are up and responding with a 200 OK status, because these could be admin pages, command-and-control servers, or other important parts of the malware infrastructure. The command we use is:
httpx -l urls.txt -mc 200 -o 200urls.txt
CopyThis reads the URLs from
urls.txt, filters out the ones that respond with HTTP 200, and saves those into
200urls.txt. That way, we can focus on the live targets.
 Fig 06: Malicious Responses from paste.ee URLs
Fig 06: Malicious Responses from paste.ee URLsDuring our investigation of the provided URLs, we discovered several malicious PE files that were both encoded and reversed. After decoding a file and loading it into dnSpy for analysis. Upon decrypting the encrypted configuration, we identified the malware as XWorm.
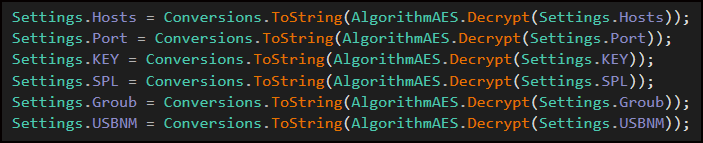 Fig 07: XWorm Configuration
Fig 07: XWorm ConfigurationXWorm captures all keyboard input across the entire system, recording keystrokes in all programs. It tracks active windows, monitors Shift and Caps Lock states, handles special keys, and supports international keyboards.
The program silently saves all captured data to a file on disk, gradually building a collection of passwords, private messages, and other sensitive information. XWorm includes a command-and-control (C2) module that keeps a persistent backdoor open on infected systems. The
ClientSocket class handles connections to remote C2 servers, giving attackers full remote access. It supports multiple backup servers and randomly selects one from a list of IP addresses or domain names in its settings.
Once connected, it collects detailed system information, including a unique machine ID, username, OS version and architecture, hardware specs, installed antivirus software, and whether a webcam is present. To stay connected, it sends regular "PING" messages every few seconds, each including the title of the active window, all over an AES-encrypted channel.
After decrypting the domain
abuwire123[.]ddns[.]net used by XWorm, we scanned it using VirusTotal and found that it resolves to the IP address
45.145.43.244.
 Fig 08: Resolved IP Related to the Domain Hosting XWorm
Fig 08: Resolved IP Related to the Domain Hosting XWormThe IP address
45.145.43.244, based in Frankfurt am Main, Germany, and registered to dataforest GmbH (ASN: AS58212), shows signs of being part of a malicious infrastructure.
It falls within the 45.145.43.0/24 subnet and has several open ports, including port 22 (SSH) and port 80, which is running Nginx 1.24.0. More concerning are ports 6606 and 7707, both flagged for hosting AsyncRAT, a well-known remote access trojan. These ports were first detected in February 2025.
AsyncRAT is an open-source remote access trojan written in C# that has been available on GitHub since around 2018. Because its source code is publicly available, many threat actors have forked, modified, and rebranded it to create their custom variants while retaining the core functionality.
SSL Certificate Activity for 45.145.43.244
The IP address 45.145.43.244, operated by dataforest GmbH in Hesse, Germany (ASN: AS58212), has shown suspicious behavior across multiple ports over the last two years.
Early 2025: SSL certificates observed on ports 6606 and 7707 were linked to AsyncRAT, a known remote access trojan. These certificates first appeared in February 2025, indicating the setup of a fresh command-and-control (C2) infrastructure.
Throughout 2024: The same IP hosted RDP services on port 3389, using certificates with hostnames like
WIN-RI8CECQIG28andWIN-HRF8D3OM84N, suggesting that compromised Windows systems may have been used as relay nodes.March-May 2024: SSL certs on port 30120 were issued by
do-not-trust.citizenfx.tls.invalid, typically associated with FiveM game servers. These are occasionally abused to host unauthorized or malicious services.June-August 2023: The IP was used to host multiple HTTPS websites on port 443, including suspicious domains like
carosnews.comand
Further investigation of SSL certificate patterns linked to AsyncRAT revealed a broader C2 network. Notably:
U.S.-based nodes hosted by QuadraNet Enterprises LLC include:
66.63.187.154 (port 6606)
66.63.187.232 (ports 8808, 6606)
196.251.118.41 (port 8808)
European infrastructure operated by SC ITNS.NET SRL includes:
45.145.43.244in Germany, with active ports:6606 (as of March 3, 2025)
7707 (as of February 24, 2025)
Using SSL certificates labeled "AsyncRAT" can help detect various AsyncRAT variants. And we can see an example in the next figure.
 Fig 09: Open Ports Related to 66.63.187.154 on Hunt.io
Fig 09: Open Ports Related to 66.63.187.154 on Hunt.ioSo, we need to check the extracted IOCs. After scanning the IP address 45.145.43.244 on VirusTotal, we can see that it's related to the XWorm malware.
 Fig 10: VirusTotal XWorm C2 Community Comment
Fig 10: VirusTotal XWorm C2 Community CommentWe will also scan 66.63.187.232 with VirusTotal. From the community, we see comments that confirm that this IP address is related to XWorm C2.
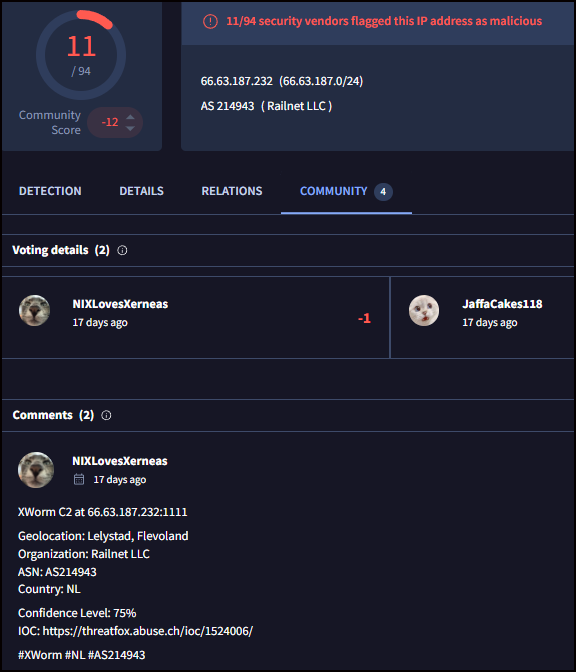 Fig 11: VirusTotal XWorm C2 Community Comments
Fig 11: VirusTotal XWorm C2 Community CommentsAfter checking the community for this IP 196.251.118.41 we can see that this is related to AsyncRAT.
 Fig 12: VirusTotal AsyncRAT C2 Community Information
Fig 12: VirusTotal AsyncRAT C2 Community InformationWhen checking 66.63.187.154, we couldn't find any attributed information related to it, but when we went back to check information from our project, we found that this is also related to the AsyncRAT variant or itself.
 Fig 13: Open Ports Related to 66.63.187.154
Fig 13: Open Ports Related to 66.63.187.154Summary
This campaign shows how attackers are evolving their methods to better hide their tracks. They’re using paste.ee, a legitimate website where people share text snippets, as their starting point to spread dangerous malware.
What caught our attention was the sneaky way they hide their code using weird Unicode characters that most people wouldn't recognize as suspicious.
Recommended Mitigation Strategies
To protect yourself from these sneaky attacks, block all identified domains and suspicious paste.ee URLs mentioned in the report. Specifically weird paste.ee links that follow a specific pattern like https://paste.ee/d/something/0
Keep an eye out for weird connections to unusual ports like 6606 or 7707, which are where the attackers control their malware from.
Ensure your security software is up to date and can detect unusual behavior, not just known viruses. Be extra careful with emails containing links to paste services, and watch out for messy or highly obfuscated JavaScript can indicate an attempt to hide downloader logic or embedded payloads.
If you're responsible for security at your organization, regularly check your systems for these warning signs and suspicious activities that might indicate you've been targeted.
XWorm and AsyncRat Indicators of Compromise (IOCs)
IP addresses and Domain Names
| IP Address | Domain | Hosting Company | Location |
|---|---|---|---|
| 45.145.43.244 | abuwire123[.]ddns[.]net | dataforest GmbH (ASN: AS58212) | Frankfurt, Germany |
| 66.63.187.154 | Not Available | QuadraNet Enterprises LLC | United States |
| 66.63.187.232 | abuwire123h[.]ddns[.]net abuwire123[.]duckdns[.]org | QuadraNet Enterprises LLC | United States |
| 196.251.118.41 | Not Available | Not Available | Not Available |
| 23.186.113.60 | paste.ee | Not Available | Not Available |
IP Addresses and C2 Ports
| IP Address | Port | Service | Certificate | First Observed |
|---|---|---|---|---|
| 45.145.43.244 | 6606 | XWorm C2 | AsyncRAT | February 24, 2025 |
| 66.63.187.154 | 6606 | AsyncRAT C2 | AsyncRAT | February 2025 |
| 66.63.187.232 | 8808 | XWorm C2 | AsyncRAT | February 2025 |
| 196.251.118.41 | 8808 | AsyncRAT C2 | AsyncRAT | February 2025 |
Malicious URLs and Patterns
| URL/Pattern | Description | Type |
|---|---|---|
| https://paste.ee/d/s1uVin8i/0 | Malicious code hosting | Payload hosting |
| https://paste.ee/[a-z]/[A-Za-z0-9]+/0 | Generic paste.ee pattern | IOC Pattern |
File hashes
| File type | Hash |
|---|---|
| Javascript | bd4952489685f6a76fe36fc220821515 |
| xworm | 6e976623d02e20d1b83e89fecd31215b |
While reviewing recent malware submissions from a public repository, we flagged a small JavaScript file packed with unusual Unicode characters and broken syntax. At first glance, it looked like malformed or incomplete code, but it was actually a disguised downloader contacting paste.ee, a legitimate service often abused to host staged payloads.
What appeared to be a standalone script turned out to be part of a broader campaign involving obfuscation, paste sites, and globally distributed C2 infrastructure tied to known remote access tools.
Further analysis revealed links to XWorm, a stealthy RAT with capabilities like keystroke logging, data exfiltration, and persistent remote access. In this report, we detail how we traced the activity, extracted IOCs, and built regex and SSL fingerprinting techniques to help defenders detect similar threats.
Technical Analysis
Our research team discovered this script while monitoring newly uploaded samples to MalwareBazaar.
It was immediately flagged with the RemcosRAT signature and caught our attention due to its deceptive filename: "DOCUMENT FOR DELIVERY INFORMATION.js". At just under 3KB, it may look harmless, but its behavior and indicators revealed a clear link to a known remote access trojan.
This sample became the starting point for our investigation, and what we found next shows how attackers continue to rely on small, weaponized scripts to deliver powerful malware.
 Fig 01. Obfuscated JavaScript on MalwareBaazer
Fig 01. Obfuscated JavaScript on MalwareBaazerThis JavaScript code is an obfuscated malicious script designed to download and execute code from a paste.ee. It hides its true functionality by inserting a long sequence of unusual Unicode characters
(ᙓೇᰖ∛ᩕዀ╬ᤳK⨀Ḣڑ⦝〒) throughout strings. These characters are later removed to reveal the actual commands and object names.
The script dynamically reconstructs the name of the
MSXML2.XMLHTTP ActiveX object, which is used to make an HTTP request. It then builds a hidden URL by removing the same junk characters from an obfuscated string, ultimately forming a complete address like
http://paste.ee/d/s1uVin8i/0.
The script sends a GET request to this URL, retrieves the response (typically malicious code), and immediately executes it using the
Function constructor.
 Fig 02: Deobfuscate JavaScript Code
Fig 02: Deobfuscate JavaScript CodeWe started by scanning the domain paste.ee using the Hunt.io web interface to uncover any IOCs or malicious activity associated with it.
 Fig 03: Resolved IP Related to paste.ee on the Hunt.io Platform
Fig 03: Resolved IP Related to paste.ee on the Hunt.io PlatformAccording to the results we got, this is an apex domain with the hostname paste.ee and resolves to the IP address 23.186.113.60. Hunt.io currently links the domain to
230 phishing URLs, 12 IOCs, and over 9,500 URLs in total.
 Fig 04: Phishing URLs Related to passte.ee on the Hunt.io platform
Fig 04: Phishing URLs Related to passte.ee on the Hunt.io platformRegex Hunting Based on Phishing URL Structure
After analyzing the phishing URLs associated with the domain
paste.ee, we observed recurring patterns in their structure. Due to these similarities, we decided to craft a regex
https:\/\/paste\.ee\/[a-z]\/[A-Za-z0-9]+\/0$ to hunt and detect related malicious URLs.
 Fig 05: Phishing URLs Regex Hunting Using Hunt.io SQL
Fig 05: Phishing URLs Regex Hunting Using Hunt.io SQLWe want to analyze potentially malicious infrastructure or check out web assets found in malware data, the first step is to pull out the relevant URLs from an NDJSON file. This NDJSON file usually contains a bunch of JSON objects, each with URLs and some extra info. To get just the URLs, we use a handy command-line tool called jq. Running this command:
jq -r ".url" export.ndjson > urls.txt
Copytakes the NDJSON file (
export.ndjson), grabs the URLs from each entry, and saves them into a simple text file (
urls.txt). This ensures the URLs are clean (no quotes or extra characters) so they're ready for the next steps.
After we have this clean list, we use another tool called httpx from ProjectDiscovery to check the status of each URL. Basically, we want to see which sites are up and responding with a 200 OK status, because these could be admin pages, command-and-control servers, or other important parts of the malware infrastructure. The command we use is:
httpx -l urls.txt -mc 200 -o 200urls.txt
CopyThis reads the URLs from
urls.txt, filters out the ones that respond with HTTP 200, and saves those into
200urls.txt. That way, we can focus on the live targets.
 Fig 06: Malicious Responses from paste.ee URLs
Fig 06: Malicious Responses from paste.ee URLsDuring our investigation of the provided URLs, we discovered several malicious PE files that were both encoded and reversed. After decoding a file and loading it into dnSpy for analysis. Upon decrypting the encrypted configuration, we identified the malware as XWorm.
 Fig 07: XWorm Configuration
Fig 07: XWorm ConfigurationXWorm captures all keyboard input across the entire system, recording keystrokes in all programs. It tracks active windows, monitors Shift and Caps Lock states, handles special keys, and supports international keyboards.
The program silently saves all captured data to a file on disk, gradually building a collection of passwords, private messages, and other sensitive information. XWorm includes a command-and-control (C2) module that keeps a persistent backdoor open on infected systems. The
ClientSocket class handles connections to remote C2 servers, giving attackers full remote access. It supports multiple backup servers and randomly selects one from a list of IP addresses or domain names in its settings.
Once connected, it collects detailed system information, including a unique machine ID, username, OS version and architecture, hardware specs, installed antivirus software, and whether a webcam is present. To stay connected, it sends regular "PING" messages every few seconds, each including the title of the active window, all over an AES-encrypted channel.
After decrypting the domain
abuwire123[.]ddns[.]net used by XWorm, we scanned it using VirusTotal and found that it resolves to the IP address
45.145.43.244.
 Fig 08: Resolved IP Related to the Domain Hosting XWorm
Fig 08: Resolved IP Related to the Domain Hosting XWormThe IP address
45.145.43.244, based in Frankfurt am Main, Germany, and registered to dataforest GmbH (ASN: AS58212), shows signs of being part of a malicious infrastructure.
It falls within the 45.145.43.0/24 subnet and has several open ports, including port 22 (SSH) and port 80, which is running Nginx 1.24.0. More concerning are ports 6606 and 7707, both flagged for hosting AsyncRAT, a well-known remote access trojan. These ports were first detected in February 2025.
AsyncRAT is an open-source remote access trojan written in C# that has been available on GitHub since around 2018. Because its source code is publicly available, many threat actors have forked, modified, and rebranded it to create their custom variants while retaining the core functionality.
SSL Certificate Activity for 45.145.43.244
The IP address 45.145.43.244, operated by dataforest GmbH in Hesse, Germany (ASN: AS58212), has shown suspicious behavior across multiple ports over the last two years.
Early 2025: SSL certificates observed on ports 6606 and 7707 were linked to AsyncRAT, a known remote access trojan. These certificates first appeared in February 2025, indicating the setup of a fresh command-and-control (C2) infrastructure.
Throughout 2024: The same IP hosted RDP services on port 3389, using certificates with hostnames like
WIN-RI8CECQIG28andWIN-HRF8D3OM84N, suggesting that compromised Windows systems may have been used as relay nodes.March-May 2024: SSL certs on port 30120 were issued by
do-not-trust.citizenfx.tls.invalid, typically associated with FiveM game servers. These are occasionally abused to host unauthorized or malicious services.June-August 2023: The IP was used to host multiple HTTPS websites on port 443, including suspicious domains like
carosnews.comand
Further investigation of SSL certificate patterns linked to AsyncRAT revealed a broader C2 network. Notably:
U.S.-based nodes hosted by QuadraNet Enterprises LLC include:
66.63.187.154 (port 6606)
66.63.187.232 (ports 8808, 6606)
196.251.118.41 (port 8808)
European infrastructure operated by SC ITNS.NET SRL includes:
45.145.43.244in Germany, with active ports:6606 (as of March 3, 2025)
7707 (as of February 24, 2025)
Using SSL certificates labeled "AsyncRAT" can help detect various AsyncRAT variants. And we can see an example in the next figure.
 Fig 09: Open Ports Related to 66.63.187.154 on Hunt.io
Fig 09: Open Ports Related to 66.63.187.154 on Hunt.ioSo, we need to check the extracted IOCs. After scanning the IP address 45.145.43.244 on VirusTotal, we can see that it's related to the XWorm malware.
 Fig 10: VirusTotal XWorm C2 Community Comment
Fig 10: VirusTotal XWorm C2 Community CommentWe will also scan 66.63.187.232 with VirusTotal. From the community, we see comments that confirm that this IP address is related to XWorm C2.
 Fig 11: VirusTotal XWorm C2 Community Comments
Fig 11: VirusTotal XWorm C2 Community CommentsAfter checking the community for this IP 196.251.118.41 we can see that this is related to AsyncRAT.
 Fig 12: VirusTotal AsyncRAT C2 Community Information
Fig 12: VirusTotal AsyncRAT C2 Community InformationWhen checking 66.63.187.154, we couldn't find any attributed information related to it, but when we went back to check information from our project, we found that this is also related to the AsyncRAT variant or itself.
 Fig 13: Open Ports Related to 66.63.187.154
Fig 13: Open Ports Related to 66.63.187.154Summary
This campaign shows how attackers are evolving their methods to better hide their tracks. They’re using paste.ee, a legitimate website where people share text snippets, as their starting point to spread dangerous malware.
What caught our attention was the sneaky way they hide their code using weird Unicode characters that most people wouldn't recognize as suspicious.
Recommended Mitigation Strategies
To protect yourself from these sneaky attacks, block all identified domains and suspicious paste.ee URLs mentioned in the report. Specifically weird paste.ee links that follow a specific pattern like https://paste.ee/d/something/0
Keep an eye out for weird connections to unusual ports like 6606 or 7707, which are where the attackers control their malware from.
Ensure your security software is up to date and can detect unusual behavior, not just known viruses. Be extra careful with emails containing links to paste services, and watch out for messy or highly obfuscated JavaScript can indicate an attempt to hide downloader logic or embedded payloads.
If you're responsible for security at your organization, regularly check your systems for these warning signs and suspicious activities that might indicate you've been targeted.
XWorm and AsyncRat Indicators of Compromise (IOCs)
IP addresses and Domain Names
| IP Address | Domain | Hosting Company | Location |
|---|---|---|---|
| 45.145.43.244 | abuwire123[.]ddns[.]net | dataforest GmbH (ASN: AS58212) | Frankfurt, Germany |
| 66.63.187.154 | Not Available | QuadraNet Enterprises LLC | United States |
| 66.63.187.232 | abuwire123h[.]ddns[.]net abuwire123[.]duckdns[.]org | QuadraNet Enterprises LLC | United States |
| 196.251.118.41 | Not Available | Not Available | Not Available |
| 23.186.113.60 | paste.ee | Not Available | Not Available |
IP Addresses and C2 Ports
| IP Address | Port | Service | Certificate | First Observed |
|---|---|---|---|---|
| 45.145.43.244 | 6606 | XWorm C2 | AsyncRAT | February 24, 2025 |
| 66.63.187.154 | 6606 | AsyncRAT C2 | AsyncRAT | February 2025 |
| 66.63.187.232 | 8808 | XWorm C2 | AsyncRAT | February 2025 |
| 196.251.118.41 | 8808 | AsyncRAT C2 | AsyncRAT | February 2025 |
Malicious URLs and Patterns
| URL/Pattern | Description | Type |
|---|---|---|
| https://paste.ee/d/s1uVin8i/0 | Malicious code hosting | Payload hosting |
| https://paste.ee/[a-z]/[A-Za-z0-9]+/0 | Generic paste.ee pattern | IOC Pattern |
File hashes
| File type | Hash |
|---|---|
| Javascript | bd4952489685f6a76fe36fc220821515 |
| xworm | 6e976623d02e20d1b83e89fecd31215b |
Related Posts
Related Posts
Related Posts


