SolarMarker: Hunt Insights and Findings
SolarMarker: Hunt Insights and Findings
Published on
May 30, 2024



Introduction
Following Recorded Future's (RF) report, "Exploring the Depths of SolarMarker's Multi-tiered Infrastructure," the Hunt Research Team leveraged the IOCs provided to discover a method of identifying clusters of SolarMarker servers in the wild.
Our scanning has uncovered 20 servers we believe with moderate confidence are associated with SolarMarker. While the RF report extensively covers SolarMarker's info-stealing capabilities, our focus here will be on the malware's infrastructure.
We will hold off on providing detection queries for SolarMarker servers for now. However, we will cover some observations, including the threat actor's choice of hosting providers, reused SSH keys associated with over 100 servers, and likely phishing domains consistent with SolarMarker targeting.
Overview of Infrastructure
Most of the servers we've identified align with the above report's configuration description for tier 1 servers (Nginx server, ports 22 & 80). One IP deviated from this pattern using port 443 and a Let's Encrypt TLS certificate.
The tier 1 servers are responsible for relaying victim data to higher-tier servers. The below image from the report provides an example of SolarMarkers C2 infrastructure.
 Image 1: SolarMarker's Tiered Infrastructure (Source: Recorded Future, accessed 21 May 2024)
Image 1: SolarMarker's Tiered Infrastructure (Source: Recorded Future, accessed 21 May 2024)SolarMarker Infrastructure in Hunt
As detailed in various blog posts and vendor reports, SolarMarker not only engages in information stealing but is also capable of executing commands via a backdoor and utilizing hidden virtual network computing (hVNC).
Figure 1 illustrates the most popular ports, hosting companies, and hosting locations based on our scans.
 Figure 1: Distribution of Popular Ports, Hosting Companies, and Hosting Locations for SolarMarker IPs
Figure 1: Distribution of Popular Ports, Hosting Companies, and Hosting Locations for SolarMarker IPsIt should come as no surprise that port 80 constitutes the bulk of SolarMarker detections. Infected devices communicate via HTTP POST requests on this port.
If you track malicious infrastructure, you are likely familiar with the M247 network. This ASN accounts for the majority of our findings across SolarMarker's infrastructure. Most of the malicious servers are located in Europe, with the U.S. following closely behind, which again aligns with threat reporting.
Figure 2 shows a snippet of the IPs readily available to Hunt users for deeper analysis.
The Insikt Group identified many of the servers shown in the image. However, we have also found a few that have not been publicly reported.
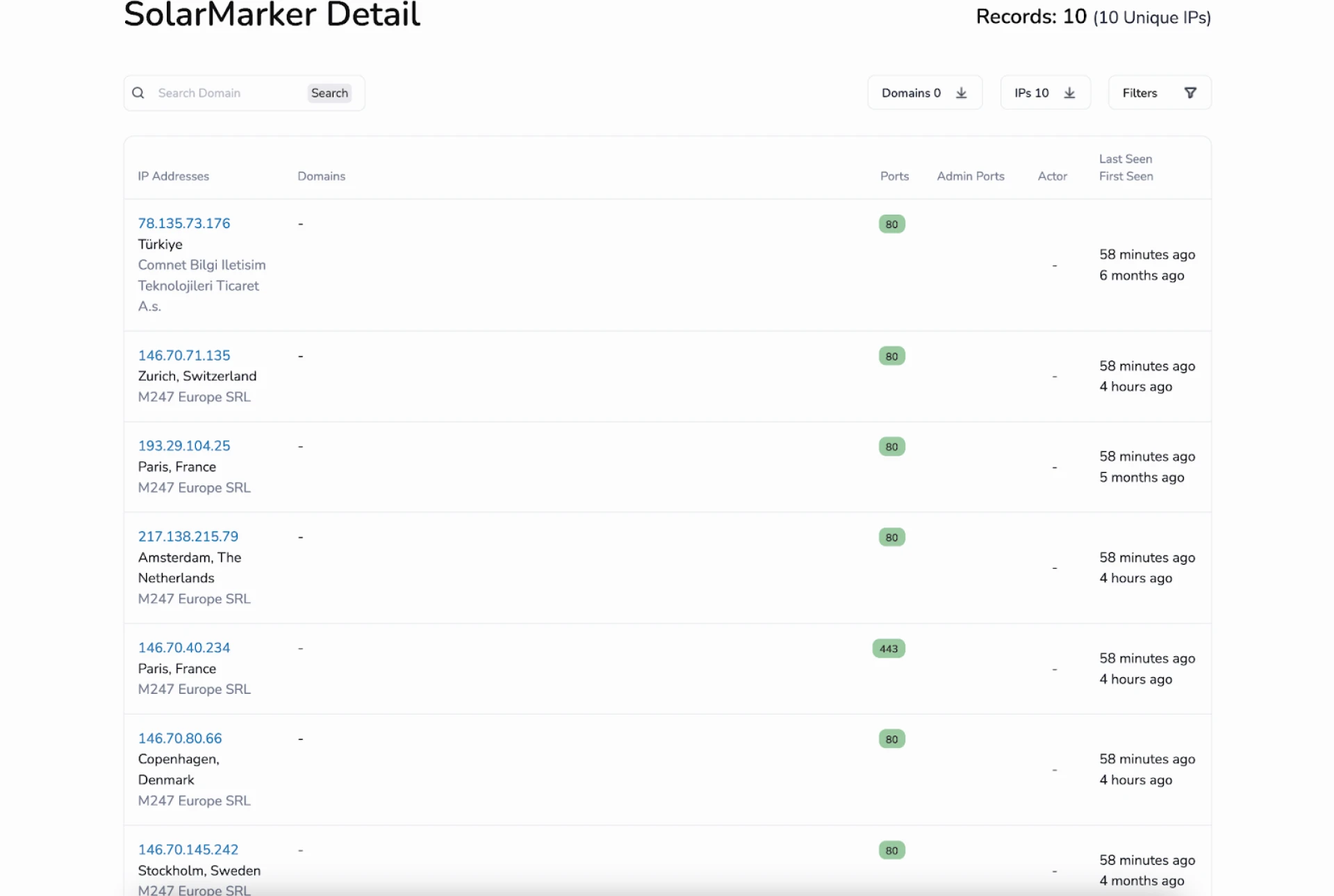 Figure 2: Snippet of SolarMarker Associated IP Addresses
Figure 2: Snippet of SolarMarker Associated IP AddressesFindings and Observations
Our first notable finding is that, although many servers operate on the M247 Europe SRL ASN, these servers are hosted on different subsidiaries, such as the one shown in Figure 3, hosted at M247 LTD Paris Infrastructure.
The threat actor's choice to use different M247 European subsidiaries, such as M247 Europe SRL, appears to be a strategic decision aligned with their targeting objectives. This approach could allow for targeting victims in specific regions by blending in so as not to raise the suspicions of network defenders.
Conversely, the preference for M247, a network known to host malicious content, may reflect the threat actor's tactic of leveraging a reliable and familiar infrastructure to maintain and expand their operations.
In either case, using various subsidiaries showcases a deliberate tactic in infrastructure management. This strategy potentially enhances the actor's ability to evade detection and sustain their malicious activities across multiple regions.
 Figure 3: SolarMarker Servers Hosted on M247 Subsidiaries
Figure 3: SolarMarker Servers Hosted on M247 SubsidiariesAdditional M247 locations were observed in Stockholm, Amsterdam, Copenhagen, and Zurich.
The Oddball
Out of the 20 results for SolarMarker infrastructure, our query found only one IP that did not use the standard port 80. The IP, 146.70.40_234, has a C2 configuration match on port 443 and has ports 22, 80, and 3306 open.
This IP hosts a Let's Encrypt TLS certificate with the domain barekaz[.]com as the issuer common name.
 Figure 4: Suspected SolarMarker Infrastructure on Port 443
Figure 4: Suspected SolarMarker Infrastructure on Port 443Figure 5 shows data for the certificate, including the JA4X hash and fingerprints.
 Figure 5: TLS Certificate for 146.70.40_234
Figure 5: TLS Certificate for 146.70.40_234Little information was available for the domain, and attempts to contact it resulted in an HTTP 404 Not Found error.
 Figure 6: 404 Error For Certificate Domain
Figure 6: 404 Error For Certificate DomainShared SSH Keys
With an infrastructure of multiple tiers that handle various infection operations, a lone individual is unlikely to conduct server management.
The actor maintained solid operational security (OPSEC) by using separate SSH keys for many of the C2 servers, except for one instance. One of those servers, 217.138.215_79, hosted an SSH key that we pivoted on and found over 100 other servers using the same key.
The below view is an example of using the "Associations" tab in Hunt.
 Figure 7: Snippet of IPs Sharing the Same SSH Keys
Figure 7: Snippet of IPs Sharing the Same SSH KeysSimilarly, the SSH History tab provides detailed information, including the SSH version, first and last seen dates/times, and similar IPs.
This particular instance uses SSH-2.0-OpenSSH_8.4p1 Debian-5+deb11u1.
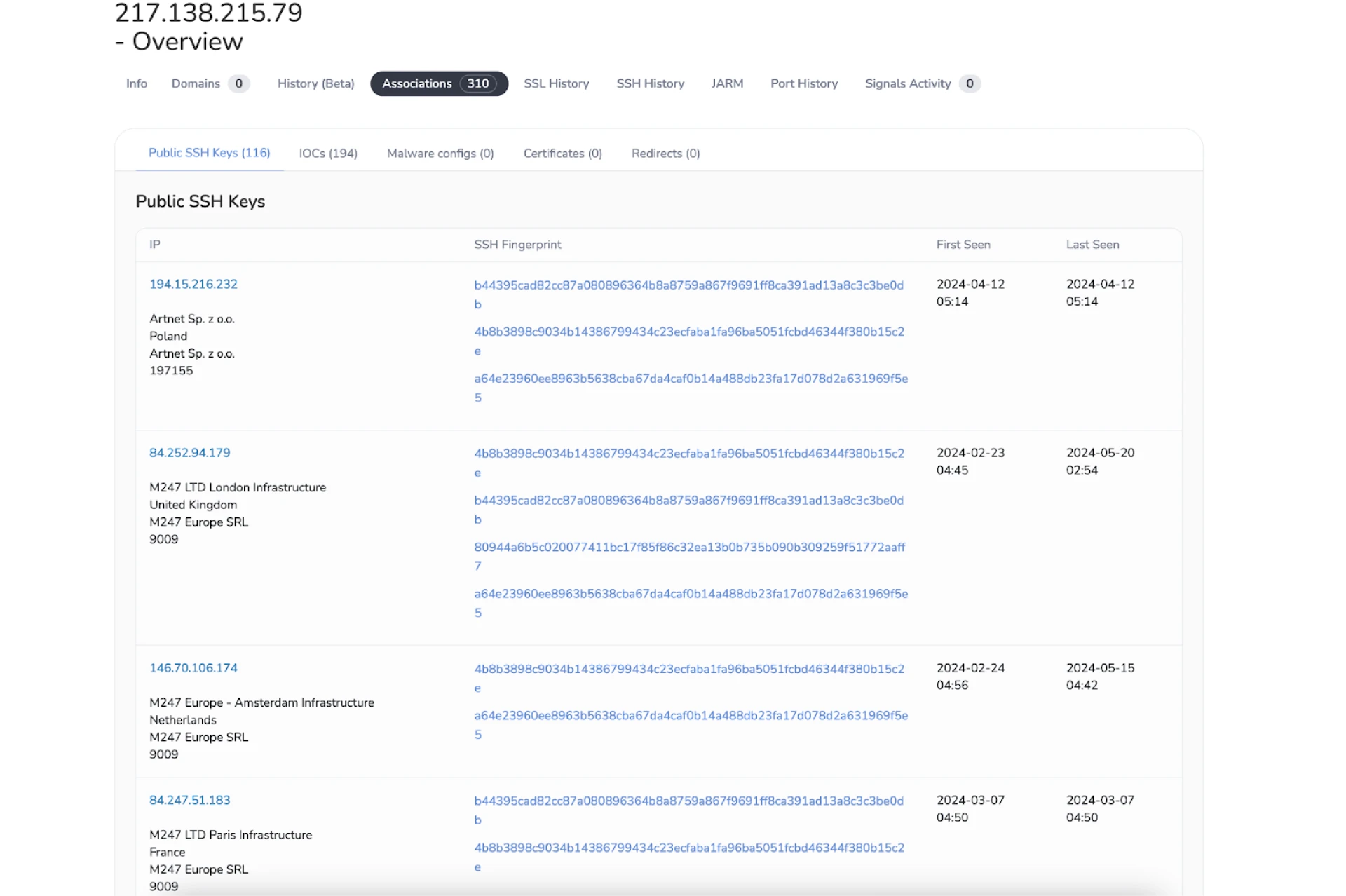 Figure 8: Screenshot of SSH History tab in Hunt
Figure 8: Screenshot of SSH History tab in HuntWe won't cover all 100+ servers, but we will examine a few that caught my eye during the research and are still active as of this writing.
Sliver & Raccoon Stealer
IP addresses 185.17.40_153 and 146.70.106_171 hosted instances of the open-source adversary emulation framework Sliver (https://github.com/BishopFox/sliver) during the same period as the shared SSH key.
In early 2023, the IP ending in .171 also hosted Raccoon Stealer on port 80. We will use the History feature to examine the timeline of the ports and services to understand how they overlap.
*The SSH hash beginning with "354408..." is the shared key.
 Figure 9: SSH Associated IP Hosting Sliver and Raccoon Stealer
Figure 9: SSH Associated IP Hosting Sliver and Raccoon Stealer Figure 10: SSH Associated IP Hosting Sliver
Figure 10: SSH Associated IP Hosting SliverInteresting Domains
 Figure 11: Domain previously Associated With Lycantrox Infrastructure
Figure 11: Domain previously Associated With Lycantrox Infrastructuregrvnews.live was previously identified as associated with Lycantrox infrastructure, as detailed in this SEKOIA blog post: https://blog.sekoia.io/active-lycantrox-infrastructure-illumination/.
Hunt first detected the SSH key on the server in July 2023, and according to PDNS records, the domain began resolving to the IP shortly after that in August.
It is important to clarify that this is not an attempt to link Lycantrox and SolarMarker but to highlight different actors' reuse of IP addresses.
Interac Spoofed Domain
188.116.34_204 currently hosts two domains, interac-financial[.]com and colminek[.]com. The former is likely an attempt to impersonate a legitimate Canadian company that facilitates electronic financial transactions between businesses and banks.
 Figure 12: IP Hosting Likely Phishing Domain
Figure 12: IP Hosting Likely Phishing DomainSimilar to the previously mentioned domain, this domain also returns a 404 error.
E-Payment Provider Spoofed Domain
Three domains were found on IP address 2.58.15_58: mail.myfawry[.]net, myfawry[.]net, and www.myfawry[.]net. These domains are likely attempting to spoof Fawry, an e-payment and digital finance solutions provider in Egypt. In an ongoing theme, all three domains return a 404 error.
 Figure 13: SSH Key Linked IP Hosting Suspicious Domains
Figure 13: SSH Key Linked IP Hosting Suspicious DomainsWe have some work to do with so many IPs to pivot on for the shared SSH key. If we find anything significant, we'll consider an additional blog post or post on X to keep the community informed.
Please follow our X/Twitter account, @Huntio, to stay updated on our findings and future blogs.
Wrap-Up
In this blog post, we explored SolarMarker's infrastructure, uncovering key IP addresses, domains, and server configurations associated with the malware. Our findings revealed intriguing patterns, such as the reuse of IP addresses and SSH keys by different threat actors and the strategic use of various hosting providers.
Join us in uncovering more
links to SolarMarker
Apply for an account today and gain access to our comprehensive tools and scan data to detect and mitigate the threat SolarMarker poses.
Indicators
| SolarMarker IP Addresses |
|---|
| 2.58.14_183 |
| 2.58.15_58 |
| 2.58.15_214 |
| 23.29.115_186 |
| 45.86.163_163 |
| 46.17.96_139 |
| 46.30.188_221 |
| 68.233.238_123 |
| 78.135.73_176 |
| 146.70.40_234 |
| 146.70.71_135 |
| 146.70.80_66 |
| 146.70.80_83 |
| 146.70.145_242 |
| 185.243.115_88 |
| 193.29.104_25 |
| 212_237.217_133 |
| 217.138.215_79 |
| 217.138.215_105 |
| SSH Key SHA-256 Fingerprint |
|---|
| Vktfcw/Kyybnc6sIHBv3WSdmVZzb3/4QFfxUUfPCEQ4= |
| TLS Cert SHA-256 Fingerprint |
|---|
| efbfbd6116690a61efbfbd601f6c0cefbfbd58efbfbd0e4e582c3fefbfbd30efbfbd36efbfbd6a27 |
Introduction
Following Recorded Future's (RF) report, "Exploring the Depths of SolarMarker's Multi-tiered Infrastructure," the Hunt Research Team leveraged the IOCs provided to discover a method of identifying clusters of SolarMarker servers in the wild.
Our scanning has uncovered 20 servers we believe with moderate confidence are associated with SolarMarker. While the RF report extensively covers SolarMarker's info-stealing capabilities, our focus here will be on the malware's infrastructure.
We will hold off on providing detection queries for SolarMarker servers for now. However, we will cover some observations, including the threat actor's choice of hosting providers, reused SSH keys associated with over 100 servers, and likely phishing domains consistent with SolarMarker targeting.
Overview of Infrastructure
Most of the servers we've identified align with the above report's configuration description for tier 1 servers (Nginx server, ports 22 & 80). One IP deviated from this pattern using port 443 and a Let's Encrypt TLS certificate.
The tier 1 servers are responsible for relaying victim data to higher-tier servers. The below image from the report provides an example of SolarMarkers C2 infrastructure.
 Image 1: SolarMarker's Tiered Infrastructure (Source: Recorded Future, accessed 21 May 2024)
Image 1: SolarMarker's Tiered Infrastructure (Source: Recorded Future, accessed 21 May 2024)SolarMarker Infrastructure in Hunt
As detailed in various blog posts and vendor reports, SolarMarker not only engages in information stealing but is also capable of executing commands via a backdoor and utilizing hidden virtual network computing (hVNC).
Figure 1 illustrates the most popular ports, hosting companies, and hosting locations based on our scans.
 Figure 1: Distribution of Popular Ports, Hosting Companies, and Hosting Locations for SolarMarker IPs
Figure 1: Distribution of Popular Ports, Hosting Companies, and Hosting Locations for SolarMarker IPsIt should come as no surprise that port 80 constitutes the bulk of SolarMarker detections. Infected devices communicate via HTTP POST requests on this port.
If you track malicious infrastructure, you are likely familiar with the M247 network. This ASN accounts for the majority of our findings across SolarMarker's infrastructure. Most of the malicious servers are located in Europe, with the U.S. following closely behind, which again aligns with threat reporting.
Figure 2 shows a snippet of the IPs readily available to Hunt users for deeper analysis.
The Insikt Group identified many of the servers shown in the image. However, we have also found a few that have not been publicly reported.
 Figure 2: Snippet of SolarMarker Associated IP Addresses
Figure 2: Snippet of SolarMarker Associated IP AddressesFindings and Observations
Our first notable finding is that, although many servers operate on the M247 Europe SRL ASN, these servers are hosted on different subsidiaries, such as the one shown in Figure 3, hosted at M247 LTD Paris Infrastructure.
The threat actor's choice to use different M247 European subsidiaries, such as M247 Europe SRL, appears to be a strategic decision aligned with their targeting objectives. This approach could allow for targeting victims in specific regions by blending in so as not to raise the suspicions of network defenders.
Conversely, the preference for M247, a network known to host malicious content, may reflect the threat actor's tactic of leveraging a reliable and familiar infrastructure to maintain and expand their operations.
In either case, using various subsidiaries showcases a deliberate tactic in infrastructure management. This strategy potentially enhances the actor's ability to evade detection and sustain their malicious activities across multiple regions.
 Figure 3: SolarMarker Servers Hosted on M247 Subsidiaries
Figure 3: SolarMarker Servers Hosted on M247 SubsidiariesAdditional M247 locations were observed in Stockholm, Amsterdam, Copenhagen, and Zurich.
The Oddball
Out of the 20 results for SolarMarker infrastructure, our query found only one IP that did not use the standard port 80. The IP, 146.70.40_234, has a C2 configuration match on port 443 and has ports 22, 80, and 3306 open.
This IP hosts a Let's Encrypt TLS certificate with the domain barekaz[.]com as the issuer common name.
 Figure 4: Suspected SolarMarker Infrastructure on Port 443
Figure 4: Suspected SolarMarker Infrastructure on Port 443Figure 5 shows data for the certificate, including the JA4X hash and fingerprints.
 Figure 5: TLS Certificate for 146.70.40_234
Figure 5: TLS Certificate for 146.70.40_234Little information was available for the domain, and attempts to contact it resulted in an HTTP 404 Not Found error.
 Figure 6: 404 Error For Certificate Domain
Figure 6: 404 Error For Certificate DomainShared SSH Keys
With an infrastructure of multiple tiers that handle various infection operations, a lone individual is unlikely to conduct server management.
The actor maintained solid operational security (OPSEC) by using separate SSH keys for many of the C2 servers, except for one instance. One of those servers, 217.138.215_79, hosted an SSH key that we pivoted on and found over 100 other servers using the same key.
The below view is an example of using the "Associations" tab in Hunt.
 Figure 7: Snippet of IPs Sharing the Same SSH Keys
Figure 7: Snippet of IPs Sharing the Same SSH KeysSimilarly, the SSH History tab provides detailed information, including the SSH version, first and last seen dates/times, and similar IPs.
This particular instance uses SSH-2.0-OpenSSH_8.4p1 Debian-5+deb11u1.
 Figure 8: Screenshot of SSH History tab in Hunt
Figure 8: Screenshot of SSH History tab in HuntWe won't cover all 100+ servers, but we will examine a few that caught my eye during the research and are still active as of this writing.
Sliver & Raccoon Stealer
IP addresses 185.17.40_153 and 146.70.106_171 hosted instances of the open-source adversary emulation framework Sliver (https://github.com/BishopFox/sliver) during the same period as the shared SSH key.
In early 2023, the IP ending in .171 also hosted Raccoon Stealer on port 80. We will use the History feature to examine the timeline of the ports and services to understand how they overlap.
*The SSH hash beginning with "354408..." is the shared key.
 Figure 9: SSH Associated IP Hosting Sliver and Raccoon Stealer
Figure 9: SSH Associated IP Hosting Sliver and Raccoon Stealer Figure 10: SSH Associated IP Hosting Sliver
Figure 10: SSH Associated IP Hosting SliverInteresting Domains
 Figure 11: Domain previously Associated With Lycantrox Infrastructure
Figure 11: Domain previously Associated With Lycantrox Infrastructuregrvnews.live was previously identified as associated with Lycantrox infrastructure, as detailed in this SEKOIA blog post: https://blog.sekoia.io/active-lycantrox-infrastructure-illumination/.
Hunt first detected the SSH key on the server in July 2023, and according to PDNS records, the domain began resolving to the IP shortly after that in August.
It is important to clarify that this is not an attempt to link Lycantrox and SolarMarker but to highlight different actors' reuse of IP addresses.
Interac Spoofed Domain
188.116.34_204 currently hosts two domains, interac-financial[.]com and colminek[.]com. The former is likely an attempt to impersonate a legitimate Canadian company that facilitates electronic financial transactions between businesses and banks.
 Figure 12: IP Hosting Likely Phishing Domain
Figure 12: IP Hosting Likely Phishing DomainSimilar to the previously mentioned domain, this domain also returns a 404 error.
E-Payment Provider Spoofed Domain
Three domains were found on IP address 2.58.15_58: mail.myfawry[.]net, myfawry[.]net, and www.myfawry[.]net. These domains are likely attempting to spoof Fawry, an e-payment and digital finance solutions provider in Egypt. In an ongoing theme, all three domains return a 404 error.
 Figure 13: SSH Key Linked IP Hosting Suspicious Domains
Figure 13: SSH Key Linked IP Hosting Suspicious DomainsWe have some work to do with so many IPs to pivot on for the shared SSH key. If we find anything significant, we'll consider an additional blog post or post on X to keep the community informed.
Please follow our X/Twitter account, @Huntio, to stay updated on our findings and future blogs.
Wrap-Up
In this blog post, we explored SolarMarker's infrastructure, uncovering key IP addresses, domains, and server configurations associated with the malware. Our findings revealed intriguing patterns, such as the reuse of IP addresses and SSH keys by different threat actors and the strategic use of various hosting providers.
Join us in uncovering more
links to SolarMarker
Apply for an account today and gain access to our comprehensive tools and scan data to detect and mitigate the threat SolarMarker poses.
Indicators
| SolarMarker IP Addresses |
|---|
| 2.58.14_183 |
| 2.58.15_58 |
| 2.58.15_214 |
| 23.29.115_186 |
| 45.86.163_163 |
| 46.17.96_139 |
| 46.30.188_221 |
| 68.233.238_123 |
| 78.135.73_176 |
| 146.70.40_234 |
| 146.70.71_135 |
| 146.70.80_66 |
| 146.70.80_83 |
| 146.70.145_242 |
| 185.243.115_88 |
| 193.29.104_25 |
| 212_237.217_133 |
| 217.138.215_79 |
| 217.138.215_105 |
| SSH Key SHA-256 Fingerprint |
|---|
| Vktfcw/Kyybnc6sIHBv3WSdmVZzb3/4QFfxUUfPCEQ4= |
| TLS Cert SHA-256 Fingerprint |
|---|
| efbfbd6116690a61efbfbd601f6c0cefbfbd58efbfbd0e4e582c3fefbfbd30efbfbd36efbfbd6a27 |
Related Posts
Related Posts
Related Posts
©2026 Hunt Intelligence, Inc.
©2026 Hunt Intelligence, Inc.
©2025 Hunt Intelligence, Inc.


