Tales from the Hunt: A Look at Yakit Security Tool
Published on

Introduction
In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
First released on GitHub in late 2021, the Yakit developers describe the tool as an "all-in-one platform based on Yaklang," a cybersecurity domain-specific language that offers man-in-the-middle interception capabilities, web fuzzing and scanning, and a plugin store.
 Figure 1: Yakit GitHub README
Figure 1: Yakit GitHub READMEThe Yakit platform ships with a team server and server for the man-in-the-middle function. The Yakit Team Server and the interception platform ship with default TLS certificates, which can be leveraged to identify Yakit instances in the wild.
Examples of the standard certificates can be seen below in Figure 2.
 Figure 2: Example Yakit certificates
Figure 2: Example Yakit certificatesIdentifying Yakit Infrastructure With Hunt
Following the Viper post, we initiated scans for Yakit installations, identifying 34 unique IP addresses across the internet. It should be noted that this count does not include instances where operators have replaced the default certificates with their own. Figure 3 below shows a snippet of the addresses discovered and available to our customers.
 Figure 3: Screenshot of Yakit instancesGive it a try
Figure 3: Screenshot of Yakit instancesGive it a tryAccording to our visibility, the most popular port for Yakit is 8087, with nearly half of the IP addresses identified using that port. The remaining ports are in the same range, including some in the 60-thousand range. Interestingly, we have not observed any instances using well-known ports such as 443 or 8443.
Given that the group behind Yakit, Yaklang, appears to be based in China, it is unsurprising that many companies hosting the tool are commonly used across Asia. Figure 4 shows the top hosts and the most popular countries for Yakit.
 Figure 4: Hunt findings for Yakit hosting
Figure 4: Hunt findings for Yakit hostingYakit Infrastructure: What We Found
It is important to note that using Yakit does not necessarily indicate malicious activity. Red teamers and researchers often use this tool for legitimate purposes. Below, we'll examine some additional tools we found alongside Yakit, including ARL, Viper, SuperShell, Cobalt Strike (CS) with watermarks associated with malicious operations, and a few Cobalt Strike Cat servers.
We'll start with IP address 111.229.186_39, hosted by Tencent and located in China.
 Figure 5: Yakit Team Server IP
Figure 5: Yakit Team Server IPThis IP address currently hosts a Yakit Team Server and, a few weeks ago, the open-source tool Asset Reconnaissance Lighthouse (ARL). You may have also noticed a wildcard certificate for chinaunicom[.]xyz, likely spoofing the legitimate China Unicom telecommunications company.
Users familiar with the Hunt platform can quickly unearth infrastructure using the same certificate by clicking the "Certificate IPs" button, as seen in the above image. Figure 6 shows the results of that pivot, identifying a single IP address using the spoofed certificate. 124.223.189_15 also previously hosted a Cobalt Strike team server using the commonly seen "Major Cobalt Strike" in its certificate.
 Figure 6: Certificate pivot in Hunt
Figure 6: Certificate pivot in HuntNext, let's examine some of the Cobalt Strike watermarks we've encountered. The first, 987654321, needs no introduction and has been linked to numerous intrusions. Additional IPs using the watermark and Yakit:
154.12.31_24
116.205.188_138.
If you want to analyze samples using this configuration, check out ThreatFox.
 Figure 7: Screenshot of Cobalt Strike watermark associations
Figure 7: Screenshot of Cobalt Strike watermark associationsThe IP address ending in .24 is also likely hosting Cobalt Strike Cat, a modified version of the original Red Team tool. Cat's default certificate is C=US, ST=WA, L=Redmond, O=Microsoft Corporation, OU=Microsoft Corporation, CN=*.microsoft. com.
I covered this finding in a tweet earlier this year:
https://twitter.com/nahamike01/status/1744479244275818893
See Figure 8 for the certificate below.
 Figure 8: Possible Cobalt Strike Cat certificate
Figure 8: Possible Cobalt Strike Cat certificateThe following IP address, 64.176.168_194, uses the "Major Cobalt Strike" certificate common name for the team server. However, this certificate is less common than you might think. Clicking on "Certificate IPs," Hunt identifies three additional IP addresses.
In addition to Cobalt Strike, these IP addresses hosted ARL and mitmproxy, an open-source HTTPS proxy.
 Figure 9: Cobalt Strike & Yakit team servers
Figure 9: Cobalt Strike & Yakit team servers Figure 10: Certificate pivot in Hunt
Figure 10: Certificate pivot in HuntMultiple security vendors have linked watermark 391144938 (see this Dec 2023 post/tweet by Group-IB) to malicious activity, including HsHarada/Rapture ransomware. The final Yakit/CS server to be covered is 47.98.251_131.
Hunt's scanners have found 169 IPs sharing the same configuration. All of which can be analyzed with a simple mouse click.
 Figure 11: CS watermark IP
Figure 11: CS watermark IPFinally, we'll examine a server that, as of May 9, was hosting a SuperShell C2 server, an open-source platform we covered not too long ago. Using Hunt's Port History feature, we can see how different ports and protocols responded to our scans. The SuperShell login can be seen in Figure 12 below at port 8888.
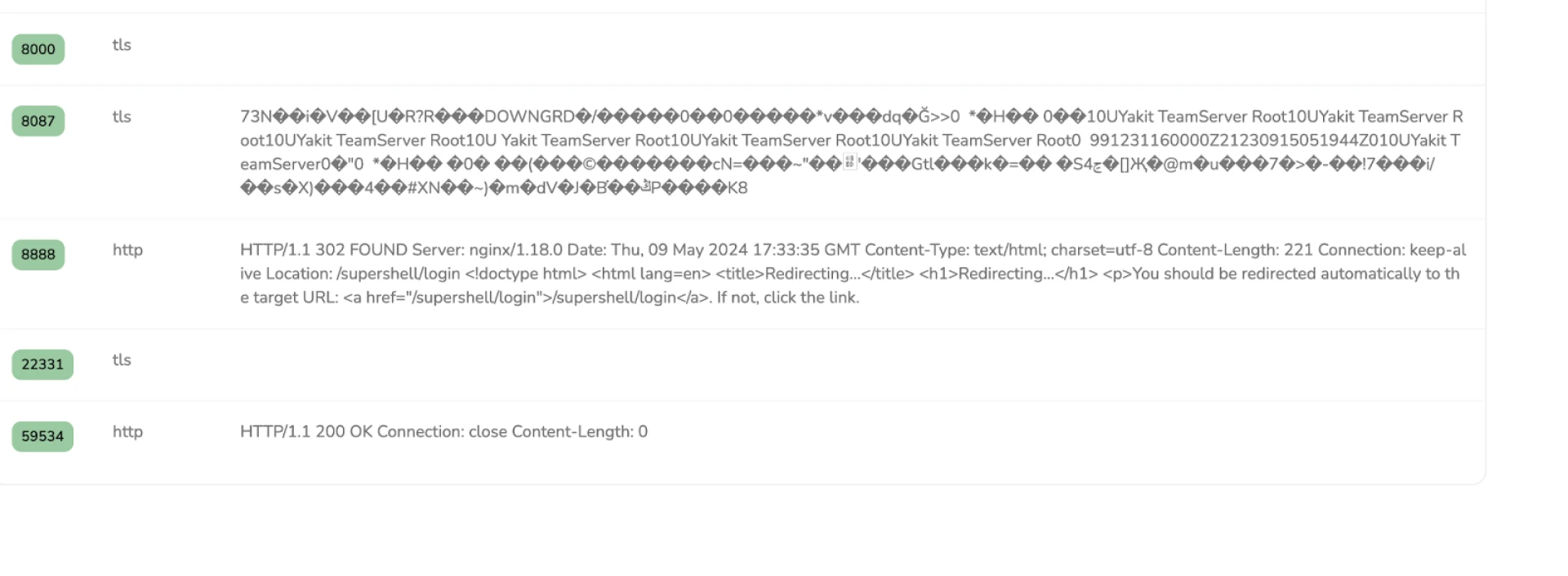 Figure 12: SuperShell login at port 8888
Figure 12: SuperShell login at port 8888First seen in November 2023, this same IP recently hosted a Cobalt Strike Cat team server, as shown below, using the SSL History feature.
 Figure 13: Possible Cobalt Strike Cat certificate
Figure 13: Possible Cobalt Strike Cat certificateStay Ahead of Threats With Hunt
Hunt's scans have revealed a range of tools and activities associated with Yakit infrastructure. While the presence of Yakit and related tools like ARL, Viper, and Cobalt Strike can indicate legitimate red teaming and research efforts, they also highlight the need for vigilant monitoring.
Our findings underscore the importance of thorough reconnaissance and continuous analysis to stay ahead of potential threats. To stay ahead of emerging threats, we encourage defenders and researchers alike to apply for an account with Hunt and gain access to comprehensive scans and detailed insights to highlight adversary infrastructure.
Introduction
In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
First released on GitHub in late 2021, the Yakit developers describe the tool as an "all-in-one platform based on Yaklang," a cybersecurity domain-specific language that offers man-in-the-middle interception capabilities, web fuzzing and scanning, and a plugin store.
 Figure 1: Yakit GitHub README
Figure 1: Yakit GitHub READMEThe Yakit platform ships with a team server and server for the man-in-the-middle function. The Yakit Team Server and the interception platform ship with default TLS certificates, which can be leveraged to identify Yakit instances in the wild.
Examples of the standard certificates can be seen below in Figure 2.
 Figure 2: Example Yakit certificates
Figure 2: Example Yakit certificatesIdentifying Yakit Infrastructure With Hunt
Following the Viper post, we initiated scans for Yakit installations, identifying 34 unique IP addresses across the internet. It should be noted that this count does not include instances where operators have replaced the default certificates with their own. Figure 3 below shows a snippet of the addresses discovered and available to our customers.
 Figure 3: Screenshot of Yakit instancesGive it a try
Figure 3: Screenshot of Yakit instancesGive it a tryAccording to our visibility, the most popular port for Yakit is 8087, with nearly half of the IP addresses identified using that port. The remaining ports are in the same range, including some in the 60-thousand range. Interestingly, we have not observed any instances using well-known ports such as 443 or 8443.
Given that the group behind Yakit, Yaklang, appears to be based in China, it is unsurprising that many companies hosting the tool are commonly used across Asia. Figure 4 shows the top hosts and the most popular countries for Yakit.
 Figure 4: Hunt findings for Yakit hosting
Figure 4: Hunt findings for Yakit hostingYakit Infrastructure: What We Found
It is important to note that using Yakit does not necessarily indicate malicious activity. Red teamers and researchers often use this tool for legitimate purposes. Below, we'll examine some additional tools we found alongside Yakit, including ARL, Viper, SuperShell, Cobalt Strike (CS) with watermarks associated with malicious operations, and a few Cobalt Strike Cat servers.
We'll start with IP address 111.229.186_39, hosted by Tencent and located in China.
 Figure 5: Yakit Team Server IP
Figure 5: Yakit Team Server IPThis IP address currently hosts a Yakit Team Server and, a few weeks ago, the open-source tool Asset Reconnaissance Lighthouse (ARL). You may have also noticed a wildcard certificate for chinaunicom[.]xyz, likely spoofing the legitimate China Unicom telecommunications company.
Users familiar with the Hunt platform can quickly unearth infrastructure using the same certificate by clicking the "Certificate IPs" button, as seen in the above image. Figure 6 shows the results of that pivot, identifying a single IP address using the spoofed certificate. 124.223.189_15 also previously hosted a Cobalt Strike team server using the commonly seen "Major Cobalt Strike" in its certificate.
 Figure 6: Certificate pivot in Hunt
Figure 6: Certificate pivot in HuntNext, let's examine some of the Cobalt Strike watermarks we've encountered. The first, 987654321, needs no introduction and has been linked to numerous intrusions. Additional IPs using the watermark and Yakit:
154.12.31_24
116.205.188_138.
If you want to analyze samples using this configuration, check out ThreatFox.
 Figure 7: Screenshot of Cobalt Strike watermark associations
Figure 7: Screenshot of Cobalt Strike watermark associationsThe IP address ending in .24 is also likely hosting Cobalt Strike Cat, a modified version of the original Red Team tool. Cat's default certificate is C=US, ST=WA, L=Redmond, O=Microsoft Corporation, OU=Microsoft Corporation, CN=*.microsoft. com.
I covered this finding in a tweet earlier this year:
https://twitter.com/nahamike01/status/1744479244275818893
See Figure 8 for the certificate below.
 Figure 8: Possible Cobalt Strike Cat certificate
Figure 8: Possible Cobalt Strike Cat certificateThe following IP address, 64.176.168_194, uses the "Major Cobalt Strike" certificate common name for the team server. However, this certificate is less common than you might think. Clicking on "Certificate IPs," Hunt identifies three additional IP addresses.
In addition to Cobalt Strike, these IP addresses hosted ARL and mitmproxy, an open-source HTTPS proxy.
 Figure 9: Cobalt Strike & Yakit team servers
Figure 9: Cobalt Strike & Yakit team servers Figure 10: Certificate pivot in Hunt
Figure 10: Certificate pivot in HuntMultiple security vendors have linked watermark 391144938 (see this Dec 2023 post/tweet by Group-IB) to malicious activity, including HsHarada/Rapture ransomware. The final Yakit/CS server to be covered is 47.98.251_131.
Hunt's scanners have found 169 IPs sharing the same configuration. All of which can be analyzed with a simple mouse click.
 Figure 11: CS watermark IP
Figure 11: CS watermark IPFinally, we'll examine a server that, as of May 9, was hosting a SuperShell C2 server, an open-source platform we covered not too long ago. Using Hunt's Port History feature, we can see how different ports and protocols responded to our scans. The SuperShell login can be seen in Figure 12 below at port 8888.
 Figure 12: SuperShell login at port 8888
Figure 12: SuperShell login at port 8888First seen in November 2023, this same IP recently hosted a Cobalt Strike Cat team server, as shown below, using the SSL History feature.
 Figure 13: Possible Cobalt Strike Cat certificate
Figure 13: Possible Cobalt Strike Cat certificateStay Ahead of Threats With Hunt
Hunt's scans have revealed a range of tools and activities associated with Yakit infrastructure. While the presence of Yakit and related tools like ARL, Viper, and Cobalt Strike can indicate legitimate red teaming and research efforts, they also highlight the need for vigilant monitoring.
Our findings underscore the importance of thorough reconnaissance and continuous analysis to stay ahead of potential threats. To stay ahead of emerging threats, we encourage defenders and researchers alike to apply for an account with Hunt and gain access to comprehensive scans and detailed insights to highlight adversary infrastructure.
Related Posts
Related Posts
Related Posts


