Suspected DPRK Phishing Campaign Targets Naver; Separate Apple Domain Spoofing Cluster Identified
Suspected DPRK Phishing Campaign Targets Naver; Separate Apple Domain Spoofing Cluster Identified
Suspected DPRK Phishing Campaign Targets Naver; Separate Apple Domain Spoofing Cluster Identified
Published on
Oct 29, 2024
Hunt researchers recently uncovered evidence of a suspected North Korean-linked phishing campaign targeting Naver, a major South Korean tech platform. The initial discovery involved an open directory containing phishing pages crafted to steal Naver users' login credentials.
Separately, an unrelated infrastructure cluster was found using domains and certificates that impersonated Apple. Both findings align with tactics commonly linked to cyber operations by Democratic People's Republic of Korea (DPRK) actors.
Details of the Phishing Server
During a routine hunt for malicious infrastructure in AttackCapture™, our team identified an exposed directory at
https://158.247.238[.]155/naver, hosted on The Constant Company ASN and located in Seoul. The server's file path, geographical location, and open directory prompted a deeper examination.
 Figure 1: Open directory and snippet of file contents on the server. (Hunt)
Figure 1: Open directory and snippet of file contents on the server. (Hunt)A closer look at the IP revealed that the server hosts more than 200 domains-a detail that will be covered later. Notably, HTTP services on ports 80 and 443 run Apache 2.4.62 (Debian).
 Figure 2: Open directory IP address overview, including domains and ports. (Hunt)
Figure 2: Open directory IP address overview, including domains and ports. (Hunt)Further investigation revealed that port 80 redirects visitors to the legitimate Naver website, suggesting an attempt to deceive users by leading to what appears to be authentic content.
 Figure 3: HTTP headers of port 80 after clicking the magnifying glass on the IP Overview page.
Figure 3: HTTP headers of port 80 after clicking the magnifying glass on the IP Overview page.Phishing Campaign Targeting Naver Users
The naver directory contains three folders-
change,
cookie, and
login. Each folder aligns with typical patterns seen in credential-stealing campaigns and with actors like Kimsuky, who routinely leave their phishing servers exposed.
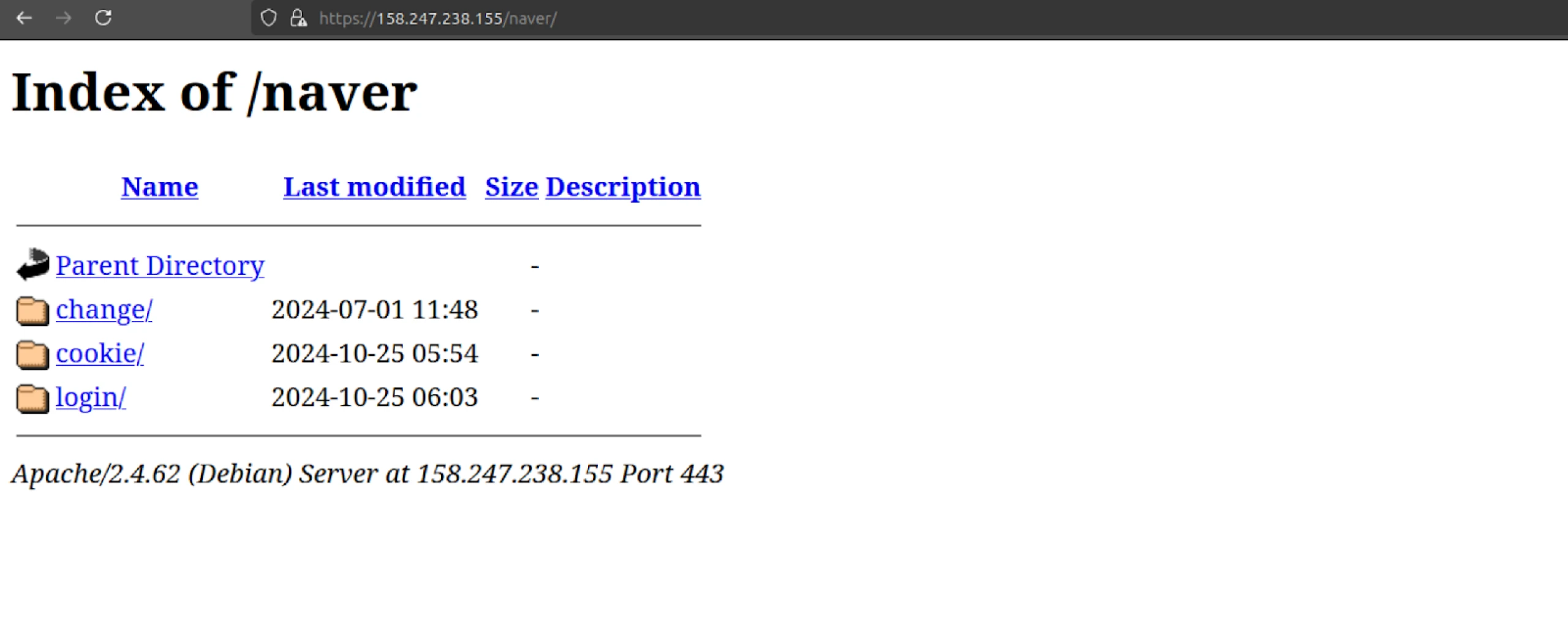 Figure 4: Screenshot of the open directory displaying the change, cookie, and login folders.
Figure 4: Screenshot of the open directory displaying the change, cookie, and login folders.Multiple IP addresses, consisting of VPN endpoints, visitors accessing the directory, and potential victims, were found within the cookie and login directories. The IP logs suggest the threat actor actively tracks incoming connections, potentially monitors for researchers, or identifies future targets.
A breakdown of the folder contents is as follows:
The login folder contains three files:
index_login.php,recon.htm, andrtnurl.Cookie includes two files:
index_c.phpand recon.htm.Finally, change holds
index_ch.phpand recon.htm.
Each file contributes to the overall phishing operation, serving a specific function. The following section will explore how these pages are designed to deceive users and extract credentials.
Technical Analysis of Phishing Pages
An examination of the PHP files found that the scripts currently return blank pages, suggesting they might be placeholders or have a purpose not directly tied to visible user interaction. Their specific role remains uncertain at this time.
Of greater interest is the file recon.htm, which mimics a Naver "My Info" password change page. Above the username and password fields is a message (in Korean) that translates to:
Deleting Cookies
You'll need to verify your identity to block suspicious devices.
CopyThis text is likely designed to instill a sense of urgency and encourage potential users to provide their credentials.
The page, however, appears incomplete. The username field does not function, and submitting a password yields no response, indicating that information exfiltration may still be in development.
 Figure 5: Suspicious recon.htm change password page.
Figure 5: Suspicious recon.htm change password page.The rtnurl file is a plain text document that displays a single URL when viewed in a browser:
https://visitnhisserver[.]store/success.html.
 Figure 6: Screenshot of rtnurl when opened in a browser.
Figure 6: Screenshot of rtnurl when opened in a browser.Upon navigating to the site, users are presented with a customized Naver page stating: "
Your mail account has been converted from dormant to active" and advising them to "
Check your security settings to make sure your account is protected."
 Figure 7: Screenshot of the success.html file.
Figure 7: Screenshot of the success.html file.An HTTP 302 redirect is then performed, opening a login page at:
https://nid.naver.com/nidlogin.login?mode=form&url=https%3A%2F%2Fnid.naver.com%2Fuser2%2Fhelp%2FmyInfoV2%3Flang%3Dko_KR.
CopyAn interesting detail in the HTTP request is a different domain in the referer field:
https://nextonlinecom[.]store/.
![Naver sign-in page after redirect from visitnhisserver[.]store/success.html](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/legacy/suspected-dprk/figure_8_naver_sign_in_page_after_redirect_from_visitnhisserver_store_success_html.webp) Figure 8: Naver sign-in page after redirect from visitnhisserver[.]store/success.html.
Figure 8: Naver sign-in page after redirect from visitnhisserver[.]store/success.html.The use of .store top-level domains and the targeting of Naver closely align with methods often reported as linked to North Korean threat actors. Groups like Lazarus and Kimsuky have a documented history of focusing on South Korean entities, frequently using low-cost domains to host malicious infrastructure while attempting to maintain a legitimate appearance.
While the attribution isn't definitive, these indicators suggest a possible link to known North Korean threat actors.
Infrastructure Analysis: Domains and Certificates
According to Hunt telemetry, 231 domains resolve to the server at 158.247.238[.]155. Many use uncommon top-level domains besides .store, like
.cfd and
.info. The majority of the domains display a technical theme, incorporating terms such as "
online," "
server," "
json," "
mail," and "
hosting."
One domain-
www.fnsc-law[.]info-deviates from this pattern, indicating it may serve a different purpose from the others.
 Figure 9: Snippet of domains resolving to the suspicious IP in Hunt.
Figure 9: Snippet of domains resolving to the suspicious IP in Hunt.Registration data shows that most domains were secured through registrars Namecheap and Namesilo. The primary nameservers include
ns1,
ns2, and
ns3.dnsowl.com, as well as
DNS1 and
DNS2.REGISTRAR-SERVERS.COM.
Next, we'll examine the certificates associated with this IP.
Analysis of the SSL history in Hunt shows that the server administrators frequently updated or replaced TLS certificates issued by Let's Encrypt every few days.
Our scanners last observed the most recent certificate, with a SHA-256 hash of
35A101941F438A7D072B31EB3B666E2C31A070DD7CF8099D20B738778FBD3458, on October 25, 2024.
Threat actors frequently utilize Let's Encrypt to add legitimacy to malicious infrastructure while keeping costs low--a tactic also observed in DPRK-associated campaigns.
 Figure 10: Screenshot of the SSL history associated with the suspicious IP in Hunt.
Figure 10: Screenshot of the SSL history associated with the suspicious IP in Hunt.An independent research effort by the team uncovered a separate cluster of IPs distributed across multiple countries that share TLS certificates and domains spoofing Apple. The TLDs and use of Let's Encrypt certificates are consistent with the campaign mentioned above.
A researcher recently linked one of the IPs to Talos' UAT-5394, indicating connections to related threat activity.
Identification of Suspicious Apple-Themed Certificates
In late September, while analyzing new hostnames found in TLS certificates via Hunt's Threat Intelligence Feeds, the domain
ulta.appleplus[.]store, hosted on
185.239.0[.]42, was seen as a common name for a certificate. This IP is part of the Web Dadeh Paydar Co (Ltd) ASN and is hosted in Iran.
The domain's clear attempt to mimic an Apple-related name prompted us to scrutinize the services and behavior of the server further. The certificate remains active as of this post's publication.
Further investigation into historical TLS records for this IP revealed a short-lived certificate with the common name
appleplus[.]shop, which was hosted on port 8443 for a single day-September 13, 2024.
Mirroring the activity in the previous section, both domains were registered using Namecheap; however, this set of domains used CloudFlare for their name servers,
newt.ns.cloudflare.com and
penny.ns.cloudflare.com.
 Figure 11: SSL History in Hunt showing domain names spoofing Apple.
Figure 11: SSL History in Hunt showing domain names spoofing Apple.A unique HTTP response was also observed on port 2052, which did not appear on the other ports associated with the certificate.
![HTTP/0.0 response for ulta.appleplus[.]store](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/legacy/suspected-dprk/figure_12_http_0_0_response_for_ulta_appleplus_store.webp) Figure 12: HTTP/0.0 response for ulta.appleplus[.]store.
Figure 12: HTTP/0.0 response for ulta.appleplus[.]store.These two certificates were the starting point of our investigation. The domain
ulta.appleplus[.]store is likely a typosquat targeting the word "ultra," intended to trick users browsing for legitimate Apple-related content.
Using the above as pivot points, we identified eight additional IP addresses sharing one or both of the above subject common names.
We will highlight a few of the more notable servers identified during this analysis, accompanied by a timeline and key findings to conclude the post.
A comprehensive table containing all discovered IPs and their relevant details is available at the end of this post.
107.189.16[.]65
We'll begin with the older of the two certificates, identified by its SHA-256 fingerprint
3201FA0F5D8269E556AEC50F820F17E1AE760CD86E5084BDCCDFE0AFF6430E06. This certificate was found on just two IP addresses: the previously analyzed server and
107.189.16[.]65, hosted by RouterHosting LLC in the U.S. As with the first IP, it was active for only a single day-September 18, 2024.
The threat actor appears to be rotating certificates between different IP addresses, suggesting an effort to change infrastructure frequently and potentially avoid straightforward detection.
 Figure 13: Screenshot showing only two IPs associated with the suspicious certificate in Hunt.
Figure 13: Screenshot showing only two IPs associated with the suspicious certificate in Hunt.This IP was recently discussed in an extensive thread by Researcher and X user @eastside_nci, who found connections to Talos' UAT-5394.
We'd encourage readers to check out the posts for an in-depth analysis of this IP, the domains, and their potential connections to what Talos describes as a "state-sponsored North Korean threat actor."
Network scan results for 107.189.16[.]65 revealed a similar pattern of numbered ports as 185.239.0[.]42 and HTTP/0.0 307 redirects on ports 2083, 2096, and 8443.
Similarly noted by @eastside_nci, we also identified an HTTP 302 redirect with a location header of
https://mail.naver[.]com.
185.239.0[.]43
We didn't have to look far for the next IP in this cluster:
185.239.0[.]43 falls within the same ASN space as the server that initially caught our attention. Once again, we see the exact domains (appleplus[.]shop and ulta.appleplus[.]store) as .42 associated with TLS fields.
Interestingly, during February and March of this year, the domain
applelplus1.hydadhybidad2[.]xyz was a common name for two certificates.
At this time, there is no information to confirm whether appleplus1.hydadhybidad2[.]xyz is directly linked to the current activity being analyzed.
 Figure 14: SSL History overview in Hunt for 185.239.0[.]43.
Figure 14: SSL History overview in Hunt for 185.239.0[.]43.The timeline below illustrates the overlaps in using certificates across different IP addresses. The dates shown are based on Hunt's scanning data, marking when each certificate was first and last observed.
 Figure 15: Timeline of certificate activity. (Built using Aeon Timeline.)
Figure 15: Timeline of certificate activity. (Built using Aeon Timeline.)The activity illustrated in the above figure spans from late June until Oct 26, 2024, with several notable discoveries:
Iran-Based Servers: Several additional servers were identified in Iran, including
185.239.0[.]39, and185.239.2[.]170. If this cluster is confirmed to be linked to a DPRK threat actor, it would represent a shift from previously observed hosting practices.More Appleplus CNs: Two more subject common names spoofing Apple were discovered:
appleplus.dnbaletmigardam[.]topon 185.239.0[.]39, andappleplus[.]sbs, hosted on206.206.125[.]237.
These findings indicate tactics and infrastructure choices consistent with DPRK threat actors, particularly the rotation of certificates across multiple IPs. This behavior highlights the importance of monitoring these shifting patterns closely to detect potential threats early and adapt defenses accordingly.
Conclusion
This research sheds light on two separate infrastructures exhibiting potential ties to DPRK threat actors, emphasizing the varied tactics often seen in North Korean malicious cyber operations. In both cases, the similarities in TLDs and the use of free certificate authorities point to likely broader malicious activities aimed at data theft and network compromise.
We'll continue to monitor this activity as it develops, and we encourage the community to use Hunt's tools to identify further indicators that could result in the attribution of this activity to a specific threat group.
Phishing Campaign Observables
| IP Address + Path | Hosting Country | ASN | Domain(s) | Ports |
|---|---|---|---|---|
| 158.247.238[.]155/naver | KR | The Constant Company, LLC | 200+ Domains directly linked to the open directory: visitnhisserver[.]store hostingnhisserver[.]store | 22 80 443 |
Apple Domain Spoofing Observables
| IP Address | Hosting Country | ASN | Domain(s) | Certificate Common Name | Ports |
|---|---|---|---|---|---|
| 185.239.0[.]42 | IR | Web Dadeh Paydar Co (Ltd) | ulta.appleplus[.]store | ulta.appleplus[.]store appleplus[.]shop | 22 2052 2083 2086 2087 2096 8080 8443 8880 |
| 107.189.16[.]65 | NL | RouterHosting | ecolekoenig[.]top topseven[.]top westwindmotorinn.xyz yarzzk[.]link schulen-horw[.]com wrightechltd[.]link file-explorer-aerocenter[.]org gyvan3-ppfhg[.]link shelby-cp-ecole[.]org vinetro[.]info tarifaconcursodeacreedores[.]top | appleplus[.]shop | 80 443 3389 |
| 84.32.186[.]252 | NL | UAB Cherry Servers | N/A | ulta.appleplus[.]store | 22 2083 2086 2087 8080 8443 8888 |
| 185.239.0[.]43 | IR | Web Dadeh Paydar Co (Ltd) | appleplus[.]shop | appleplus[.]shop ulta.appleplus[.]store | 22 2086 2087 8880 |
| 159.253.4[.]64 | NL | LeaseWeb Netherlands B.V. | N/A | ulta.appleplus[.]store x2 | 22 |
| 206.206.125[.]237 | GB | Datacamp Limited | N/A | appleplus[.]shop appleplus[.]sbs | 22 2053 2083 2086 2087 2096 8880 |
| 185.239.2[.]170 | IR | Web Dadeh Paydar Co (Ltd) | N/A | ulta.appleplus[.]store | 22 |
| 192.121.17[.]63 | NL | EDIS GmbH | N/A | ulta.appleplus[.]store | N/A |
| 185.239.0[.]39 | IR | Web Dadeh Paydar Co (Ltd) | N/A | ulta.appleplus[.]store x2 | N/A |
| 159.253.4[.]70 | NL | LeaseWeb Netherlands B.V. | N/A | ulta.appleplus[.]store | N/A |
Hunt researchers recently uncovered evidence of a suspected North Korean-linked phishing campaign targeting Naver, a major South Korean tech platform. The initial discovery involved an open directory containing phishing pages crafted to steal Naver users' login credentials.
Separately, an unrelated infrastructure cluster was found using domains and certificates that impersonated Apple. Both findings align with tactics commonly linked to cyber operations by Democratic People's Republic of Korea (DPRK) actors.
Details of the Phishing Server
During a routine hunt for malicious infrastructure in AttackCapture™, our team identified an exposed directory at
https://158.247.238[.]155/naver, hosted on The Constant Company ASN and located in Seoul. The server's file path, geographical location, and open directory prompted a deeper examination.
 Figure 1: Open directory and snippet of file contents on the server. (Hunt)
Figure 1: Open directory and snippet of file contents on the server. (Hunt)A closer look at the IP revealed that the server hosts more than 200 domains-a detail that will be covered later. Notably, HTTP services on ports 80 and 443 run Apache 2.4.62 (Debian).
 Figure 2: Open directory IP address overview, including domains and ports. (Hunt)
Figure 2: Open directory IP address overview, including domains and ports. (Hunt)Further investigation revealed that port 80 redirects visitors to the legitimate Naver website, suggesting an attempt to deceive users by leading to what appears to be authentic content.
 Figure 3: HTTP headers of port 80 after clicking the magnifying glass on the IP Overview page.
Figure 3: HTTP headers of port 80 after clicking the magnifying glass on the IP Overview page.Phishing Campaign Targeting Naver Users
The naver directory contains three folders-
change,
cookie, and
login. Each folder aligns with typical patterns seen in credential-stealing campaigns and with actors like Kimsuky, who routinely leave their phishing servers exposed.
 Figure 4: Screenshot of the open directory displaying the change, cookie, and login folders.
Figure 4: Screenshot of the open directory displaying the change, cookie, and login folders.Multiple IP addresses, consisting of VPN endpoints, visitors accessing the directory, and potential victims, were found within the cookie and login directories. The IP logs suggest the threat actor actively tracks incoming connections, potentially monitors for researchers, or identifies future targets.
A breakdown of the folder contents is as follows:
The login folder contains three files:
index_login.php,recon.htm, andrtnurl.Cookie includes two files:
index_c.phpand recon.htm.Finally, change holds
index_ch.phpand recon.htm.
Each file contributes to the overall phishing operation, serving a specific function. The following section will explore how these pages are designed to deceive users and extract credentials.
Technical Analysis of Phishing Pages
An examination of the PHP files found that the scripts currently return blank pages, suggesting they might be placeholders or have a purpose not directly tied to visible user interaction. Their specific role remains uncertain at this time.
Of greater interest is the file recon.htm, which mimics a Naver "My Info" password change page. Above the username and password fields is a message (in Korean) that translates to:
Deleting Cookies
You'll need to verify your identity to block suspicious devices.
CopyThis text is likely designed to instill a sense of urgency and encourage potential users to provide their credentials.
The page, however, appears incomplete. The username field does not function, and submitting a password yields no response, indicating that information exfiltration may still be in development.
 Figure 5: Suspicious recon.htm change password page.
Figure 5: Suspicious recon.htm change password page.The rtnurl file is a plain text document that displays a single URL when viewed in a browser:
https://visitnhisserver[.]store/success.html.
 Figure 6: Screenshot of rtnurl when opened in a browser.
Figure 6: Screenshot of rtnurl when opened in a browser.Upon navigating to the site, users are presented with a customized Naver page stating: "
Your mail account has been converted from dormant to active" and advising them to "
Check your security settings to make sure your account is protected."
 Figure 7: Screenshot of the success.html file.
Figure 7: Screenshot of the success.html file.An HTTP 302 redirect is then performed, opening a login page at:
https://nid.naver.com/nidlogin.login?mode=form&url=https%3A%2F%2Fnid.naver.com%2Fuser2%2Fhelp%2FmyInfoV2%3Flang%3Dko_KR.
CopyAn interesting detail in the HTTP request is a different domain in the referer field:
https://nextonlinecom[.]store/.
![Naver sign-in page after redirect from visitnhisserver[.]store/success.html](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/legacy/suspected-dprk/figure_8_naver_sign_in_page_after_redirect_from_visitnhisserver_store_success_html.webp) Figure 8: Naver sign-in page after redirect from visitnhisserver[.]store/success.html.
Figure 8: Naver sign-in page after redirect from visitnhisserver[.]store/success.html.The use of .store top-level domains and the targeting of Naver closely align with methods often reported as linked to North Korean threat actors. Groups like Lazarus and Kimsuky have a documented history of focusing on South Korean entities, frequently using low-cost domains to host malicious infrastructure while attempting to maintain a legitimate appearance.
While the attribution isn't definitive, these indicators suggest a possible link to known North Korean threat actors.
Infrastructure Analysis: Domains and Certificates
According to Hunt telemetry, 231 domains resolve to the server at 158.247.238[.]155. Many use uncommon top-level domains besides .store, like
.cfd and
.info. The majority of the domains display a technical theme, incorporating terms such as "
online," "
server," "
json," "
mail," and "
hosting."
One domain-
www.fnsc-law[.]info-deviates from this pattern, indicating it may serve a different purpose from the others.
 Figure 9: Snippet of domains resolving to the suspicious IP in Hunt.
Figure 9: Snippet of domains resolving to the suspicious IP in Hunt.Registration data shows that most domains were secured through registrars Namecheap and Namesilo. The primary nameservers include
ns1,
ns2, and
ns3.dnsowl.com, as well as
DNS1 and
DNS2.REGISTRAR-SERVERS.COM.
Next, we'll examine the certificates associated with this IP.
Analysis of the SSL history in Hunt shows that the server administrators frequently updated or replaced TLS certificates issued by Let's Encrypt every few days.
Our scanners last observed the most recent certificate, with a SHA-256 hash of
35A101941F438A7D072B31EB3B666E2C31A070DD7CF8099D20B738778FBD3458, on October 25, 2024.
Threat actors frequently utilize Let's Encrypt to add legitimacy to malicious infrastructure while keeping costs low--a tactic also observed in DPRK-associated campaigns.
 Figure 10: Screenshot of the SSL history associated with the suspicious IP in Hunt.
Figure 10: Screenshot of the SSL history associated with the suspicious IP in Hunt.An independent research effort by the team uncovered a separate cluster of IPs distributed across multiple countries that share TLS certificates and domains spoofing Apple. The TLDs and use of Let's Encrypt certificates are consistent with the campaign mentioned above.
A researcher recently linked one of the IPs to Talos' UAT-5394, indicating connections to related threat activity.
Identification of Suspicious Apple-Themed Certificates
In late September, while analyzing new hostnames found in TLS certificates via Hunt's Threat Intelligence Feeds, the domain
ulta.appleplus[.]store, hosted on
185.239.0[.]42, was seen as a common name for a certificate. This IP is part of the Web Dadeh Paydar Co (Ltd) ASN and is hosted in Iran.
The domain's clear attempt to mimic an Apple-related name prompted us to scrutinize the services and behavior of the server further. The certificate remains active as of this post's publication.
Further investigation into historical TLS records for this IP revealed a short-lived certificate with the common name
appleplus[.]shop, which was hosted on port 8443 for a single day-September 13, 2024.
Mirroring the activity in the previous section, both domains were registered using Namecheap; however, this set of domains used CloudFlare for their name servers,
newt.ns.cloudflare.com and
penny.ns.cloudflare.com.
 Figure 11: SSL History in Hunt showing domain names spoofing Apple.
Figure 11: SSL History in Hunt showing domain names spoofing Apple.A unique HTTP response was also observed on port 2052, which did not appear on the other ports associated with the certificate.
![HTTP/0.0 response for ulta.appleplus[.]store](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/legacy/suspected-dprk/figure_12_http_0_0_response_for_ulta_appleplus_store.webp) Figure 12: HTTP/0.0 response for ulta.appleplus[.]store.
Figure 12: HTTP/0.0 response for ulta.appleplus[.]store.These two certificates were the starting point of our investigation. The domain
ulta.appleplus[.]store is likely a typosquat targeting the word "ultra," intended to trick users browsing for legitimate Apple-related content.
Using the above as pivot points, we identified eight additional IP addresses sharing one or both of the above subject common names.
We will highlight a few of the more notable servers identified during this analysis, accompanied by a timeline and key findings to conclude the post.
A comprehensive table containing all discovered IPs and their relevant details is available at the end of this post.
107.189.16[.]65
We'll begin with the older of the two certificates, identified by its SHA-256 fingerprint
3201FA0F5D8269E556AEC50F820F17E1AE760CD86E5084BDCCDFE0AFF6430E06. This certificate was found on just two IP addresses: the previously analyzed server and
107.189.16[.]65, hosted by RouterHosting LLC in the U.S. As with the first IP, it was active for only a single day-September 18, 2024.
The threat actor appears to be rotating certificates between different IP addresses, suggesting an effort to change infrastructure frequently and potentially avoid straightforward detection.
 Figure 13: Screenshot showing only two IPs associated with the suspicious certificate in Hunt.
Figure 13: Screenshot showing only two IPs associated with the suspicious certificate in Hunt.This IP was recently discussed in an extensive thread by Researcher and X user @eastside_nci, who found connections to Talos' UAT-5394.
We'd encourage readers to check out the posts for an in-depth analysis of this IP, the domains, and their potential connections to what Talos describes as a "state-sponsored North Korean threat actor."
Network scan results for 107.189.16[.]65 revealed a similar pattern of numbered ports as 185.239.0[.]42 and HTTP/0.0 307 redirects on ports 2083, 2096, and 8443.
Similarly noted by @eastside_nci, we also identified an HTTP 302 redirect with a location header of
https://mail.naver[.]com.
185.239.0[.]43
We didn't have to look far for the next IP in this cluster:
185.239.0[.]43 falls within the same ASN space as the server that initially caught our attention. Once again, we see the exact domains (appleplus[.]shop and ulta.appleplus[.]store) as .42 associated with TLS fields.
Interestingly, during February and March of this year, the domain
applelplus1.hydadhybidad2[.]xyz was a common name for two certificates.
At this time, there is no information to confirm whether appleplus1.hydadhybidad2[.]xyz is directly linked to the current activity being analyzed.
 Figure 14: SSL History overview in Hunt for 185.239.0[.]43.
Figure 14: SSL History overview in Hunt for 185.239.0[.]43.The timeline below illustrates the overlaps in using certificates across different IP addresses. The dates shown are based on Hunt's scanning data, marking when each certificate was first and last observed.
 Figure 15: Timeline of certificate activity. (Built using Aeon Timeline.)
Figure 15: Timeline of certificate activity. (Built using Aeon Timeline.)The activity illustrated in the above figure spans from late June until Oct 26, 2024, with several notable discoveries:
Iran-Based Servers: Several additional servers were identified in Iran, including
185.239.0[.]39, and185.239.2[.]170. If this cluster is confirmed to be linked to a DPRK threat actor, it would represent a shift from previously observed hosting practices.More Appleplus CNs: Two more subject common names spoofing Apple were discovered:
appleplus.dnbaletmigardam[.]topon 185.239.0[.]39, andappleplus[.]sbs, hosted on206.206.125[.]237.
These findings indicate tactics and infrastructure choices consistent with DPRK threat actors, particularly the rotation of certificates across multiple IPs. This behavior highlights the importance of monitoring these shifting patterns closely to detect potential threats early and adapt defenses accordingly.
Conclusion
This research sheds light on two separate infrastructures exhibiting potential ties to DPRK threat actors, emphasizing the varied tactics often seen in North Korean malicious cyber operations. In both cases, the similarities in TLDs and the use of free certificate authorities point to likely broader malicious activities aimed at data theft and network compromise.
We'll continue to monitor this activity as it develops, and we encourage the community to use Hunt's tools to identify further indicators that could result in the attribution of this activity to a specific threat group.
Phishing Campaign Observables
| IP Address + Path | Hosting Country | ASN | Domain(s) | Ports |
|---|---|---|---|---|
| 158.247.238[.]155/naver | KR | The Constant Company, LLC | 200+ Domains directly linked to the open directory: visitnhisserver[.]store hostingnhisserver[.]store | 22 80 443 |
Apple Domain Spoofing Observables
| IP Address | Hosting Country | ASN | Domain(s) | Certificate Common Name | Ports |
|---|---|---|---|---|---|
| 185.239.0[.]42 | IR | Web Dadeh Paydar Co (Ltd) | ulta.appleplus[.]store | ulta.appleplus[.]store appleplus[.]shop | 22 2052 2083 2086 2087 2096 8080 8443 8880 |
| 107.189.16[.]65 | NL | RouterHosting | ecolekoenig[.]top topseven[.]top westwindmotorinn.xyz yarzzk[.]link schulen-horw[.]com wrightechltd[.]link file-explorer-aerocenter[.]org gyvan3-ppfhg[.]link shelby-cp-ecole[.]org vinetro[.]info tarifaconcursodeacreedores[.]top | appleplus[.]shop | 80 443 3389 |
| 84.32.186[.]252 | NL | UAB Cherry Servers | N/A | ulta.appleplus[.]store | 22 2083 2086 2087 8080 8443 8888 |
| 185.239.0[.]43 | IR | Web Dadeh Paydar Co (Ltd) | appleplus[.]shop | appleplus[.]shop ulta.appleplus[.]store | 22 2086 2087 8880 |
| 159.253.4[.]64 | NL | LeaseWeb Netherlands B.V. | N/A | ulta.appleplus[.]store x2 | 22 |
| 206.206.125[.]237 | GB | Datacamp Limited | N/A | appleplus[.]shop appleplus[.]sbs | 22 2053 2083 2086 2087 2096 8880 |
| 185.239.2[.]170 | IR | Web Dadeh Paydar Co (Ltd) | N/A | ulta.appleplus[.]store | 22 |
| 192.121.17[.]63 | NL | EDIS GmbH | N/A | ulta.appleplus[.]store | N/A |
| 185.239.0[.]39 | IR | Web Dadeh Paydar Co (Ltd) | N/A | ulta.appleplus[.]store x2 | N/A |
| 159.253.4[.]70 | NL | LeaseWeb Netherlands B.V. | N/A | ulta.appleplus[.]store | N/A |
Related Posts
Related Posts
Related Posts


