Hunting C2 Panels: Beginner’s Guide for Identifying Command and Control Dashboards
Hunting C2 Panels: Beginner’s Guide for Identifying Command and Control Dashboards
Published on
Sep 25, 2025



Exposed command and control (C2) panels are active dashboards used by attackers to run their campaigns. They give operators a central place to watch infected devices, move stolen data, and send new instructions. Finding these panels early can help security teams cut off activity before it grows.
In practice, these panels work like the control rooms of an operation. Through a simple web interface, attackers can see victims, gather details such as location or system info, collect credentials or cryptocurrency wallets, and push out new payloads. Panels like these are a standard part of modern malware families.
This guide looks at some of the most common panels seen online today: Supershell, HookBot, Chaos RAT, UnamWebPanel, Metasploit, and Mythic. Each one has fingerprints that give it away, whether it's a URL path, a title, a favicon hash, or even a code reference. Learning to recognize those clues makes it easier to track attacker infrastructure and close off exposure before it's abused.
HuntSQL™: a key part of the C2 panel hunting process
HuntSQL™ is Hunt.io's SQL-driven interface built for defenders who need to move quickly across large security datasets. Instead of juggling multiple tools, analysts can pivot, correlate, and validate clues within a single environment. This makes it possible to move from a URL path to a TLS certificate to a page snapshot in one workflow, which is especially useful when exposing attacker infrastructure.
In this guide, we focus on three datasets that are most valuable for hunting C2 panels:
httpv2 provides detailed web-scan telemetry, including response headers and page content. It helps surface suspicious login pages and unique response patterns tied to control dashboards.
urlx works as a broad URL index for reconnaissance, letting analysts test hunting ideas and uncover patterns across billions of internet-facing endpoints.
crawler captures page snapshots and artifacts such as scripts, favicons, and embedded resources. These details confirm whether a candidate page is a real control panel and help link related infrastructure through shared assets.
Other HuntSQL™ datasets, such as Malware, Certificates, Honeypot, Open Directories, and Phishing, add important context for broader threat hunting. They cover confirmed C2 servers, reused TLS certificates, reconnaissance activity, and exposed staging directories. While we will not rely on them here, they highlight how HuntSQL™ brings together diverse sources into one place for mapping and disrupting adversary operations.
With this foundation in place, we can move into practical examples. Let's start with one of the most common frameworks seen online today: Supershell, and how to spot its panels using URL paths and titles.
Hunting Supershell Panels by URL Path & Title
One example of a control panel that can be discovered in the wild is Supershell, an open-source post-exploitation framework written in Go. Supershell gives attackers a web-based dashboard where they can manage compromised hosts, run commands, and maintain persistence across infected systems.
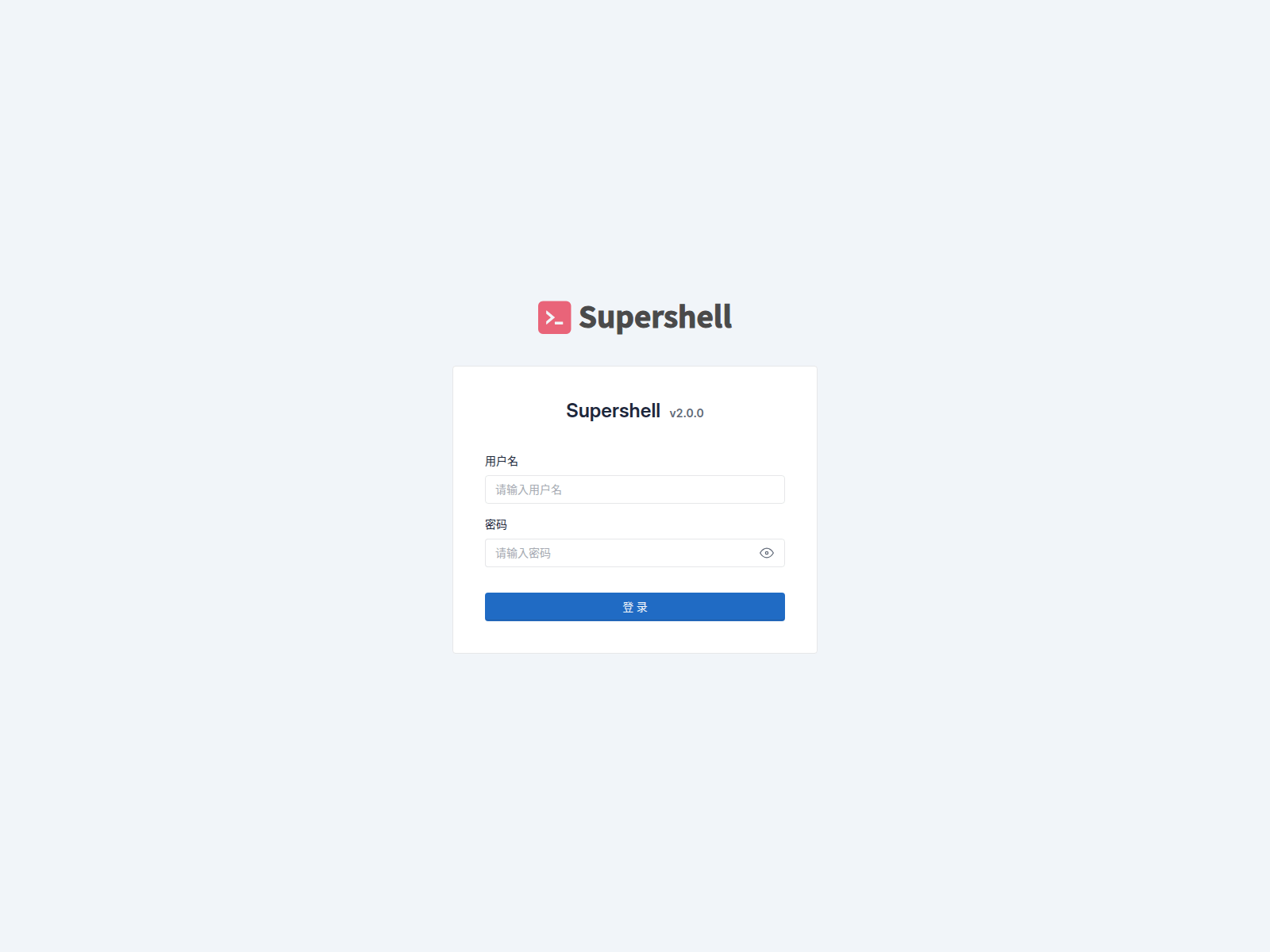 Figure 1: Supershell login page exposed on port 8888
Figure 1: Supershell login page exposed on port 8888Identifying Supershell Control Panels
Its login page, which prominently displays the "Supershell" branding and version number, makes it easy to identify and hunt. For instance, the URL
http://134.122.207.42:8888/supershell/login/ exposes a Supershell login panel directly on the internet.
By examining the URL of a control panel, we can often extract useful indicators for threat hunting. In the case of Supershell, the last part of the URL /supershell/login/ is a strong and unique pattern that can be used to identify other exposed panels.
SELECT
*
FROM
urlx
WHERE
url LIKE '%/supershell/login%'
CopyOutput:
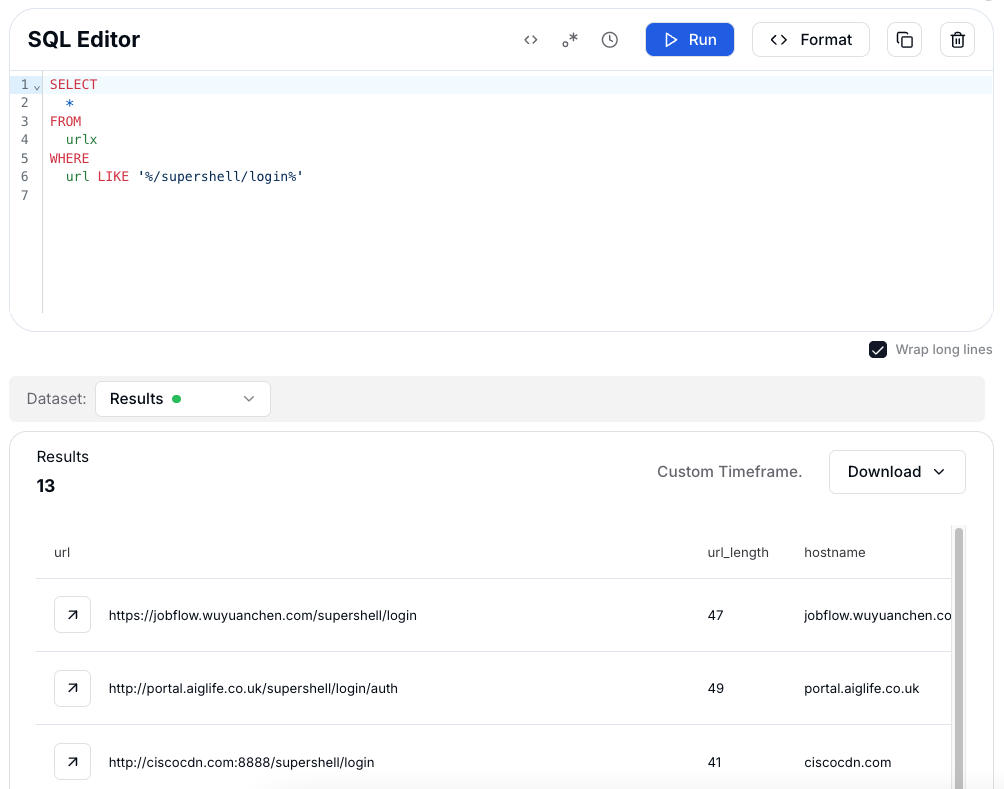 Figure 2: Hunting Supershell panels via URL path.
Figure 2: Hunting Supershell panels via URL path.With Hunt.io, we can craft a hunting query that searches for all URLs containing this path, allowing us to collect and map multiple instances of Supershell control panels across different IPs and domains.
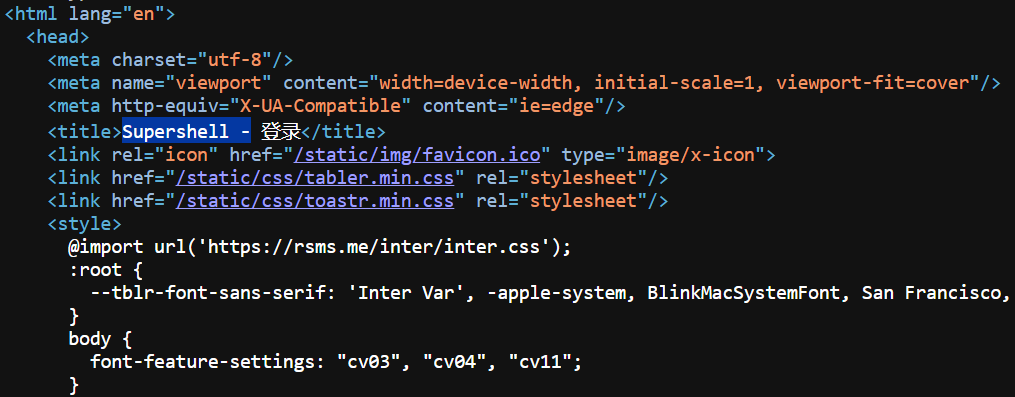 Figure 3: HTML snippet with "Supershell" in page title
Figure 3: HTML snippet with "Supershell" in page titleTo extend our coverage even further, we can pivot on another indicator found in the panel's code: the HTML title, which clearly contains the name "Supershell." This gives us an additional fingerprint to expand our hunt and catch more exposed panels.
SELECT
*
FROM
httpv2
WHERE
html.head.title LIKE '%Supershell -%'
CopyOutput:
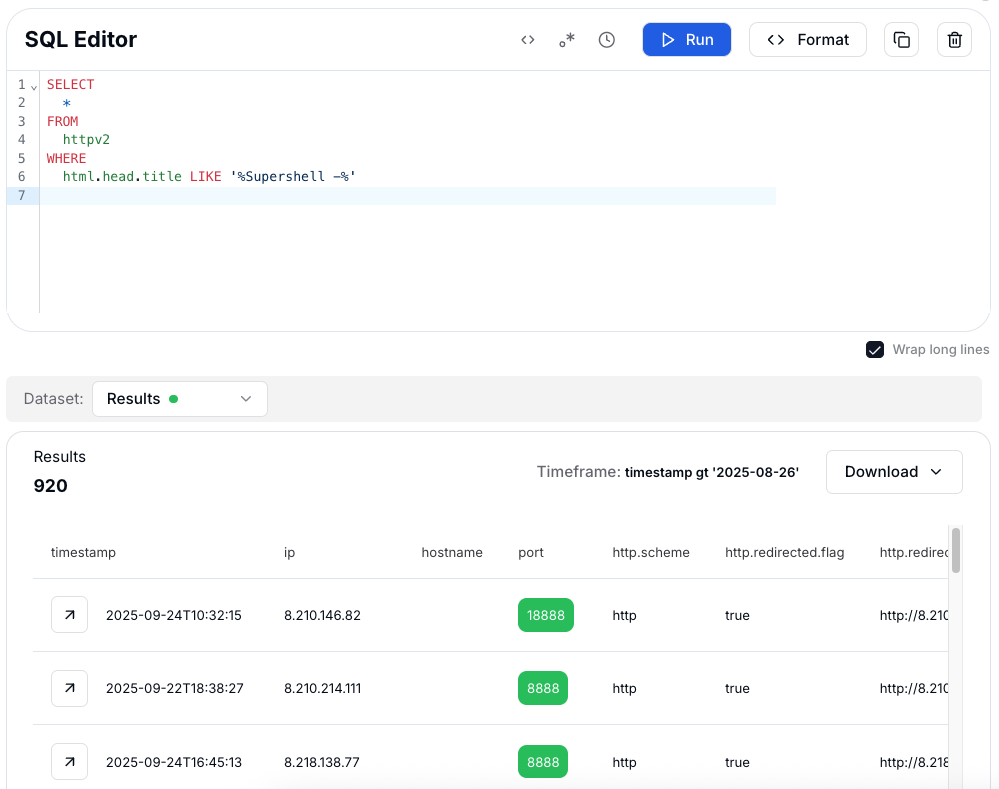 Figure 4: Hunting Supershell panels via the title of the HTML page
Figure 4: Hunting Supershell panels via the title of the HTML pageAfter Supershell, another family that often exposes its infrastructure is HookBot, which can be recognized through simple but reliable fingerprints.
Identifying HookBot Panels via Titles & Favicons
HookBot is a powerful Android banking trojan designed to steal credentials, intercept SMS messages, and bypass multi-factor authentication (MFA). Once installed on a victim's device, HookBot can overlay fake login screens on top of legitimate apps to harvest sensitive information from banking, email, and cryptocurrency services.
The malware communicates with a web-based control panel, giving attackers the ability to manage infected devices, issue commands, and monitor stolen data in real time.
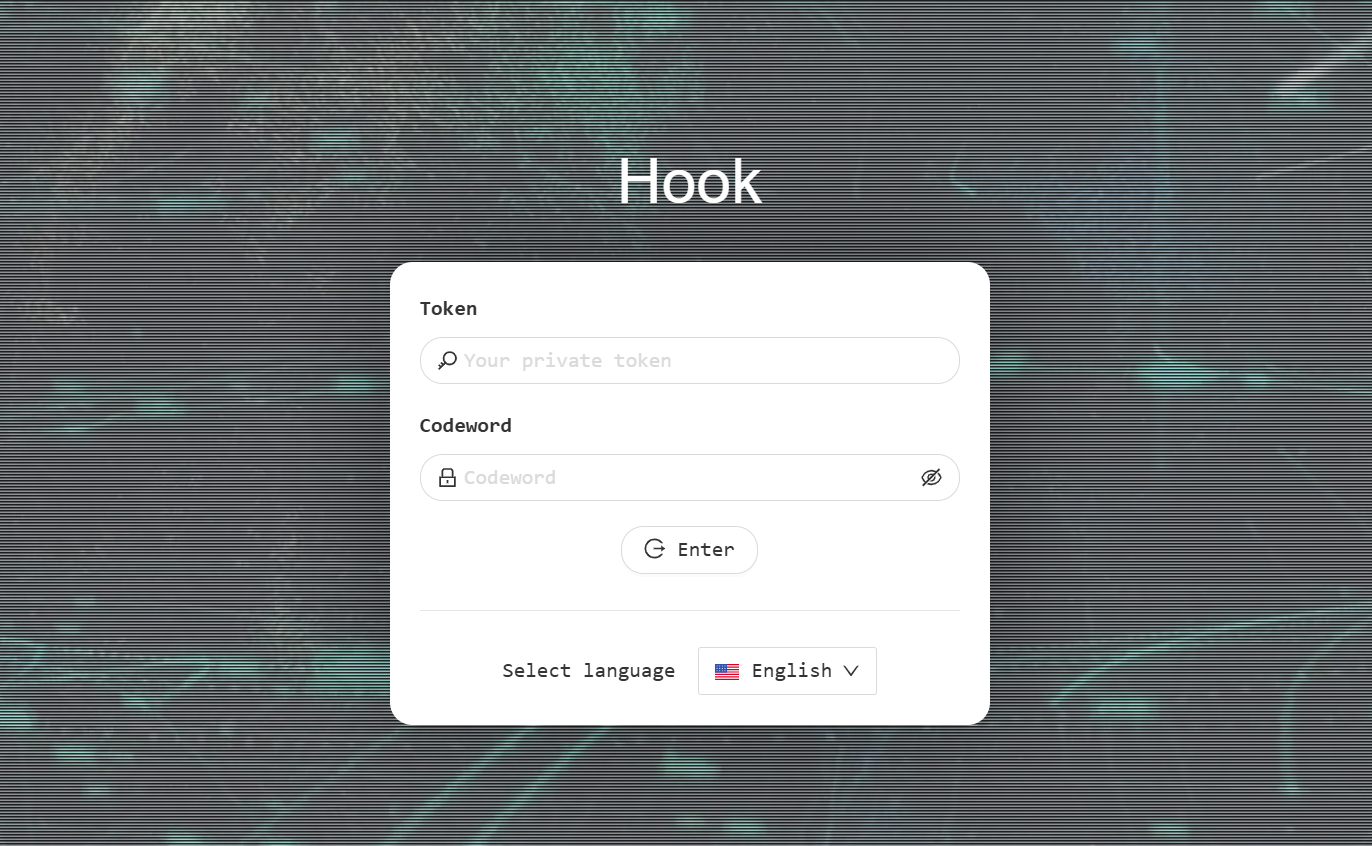 Figure 5: HookBot control panel login screenshot.
Figure 5: HookBot control panel login screenshot.Detecting HookBot Control Panels
By examining the source code of a control panel, we can often extract valuable indicators that help us expand our hunt. One strong example is the HTML title, which many panels display consistently across deployments. For HookBot, the panel title includes the string "HOOKBOT PANEL", making it a reliable fingerprint. Using Hunt.io, we can craft a query to collect all sites where this title appears:
SELECT
*
FROM
httpv2
WHERE
html.head.title LIKE '%HOOKBOT PANEL%'
CopyOutput:
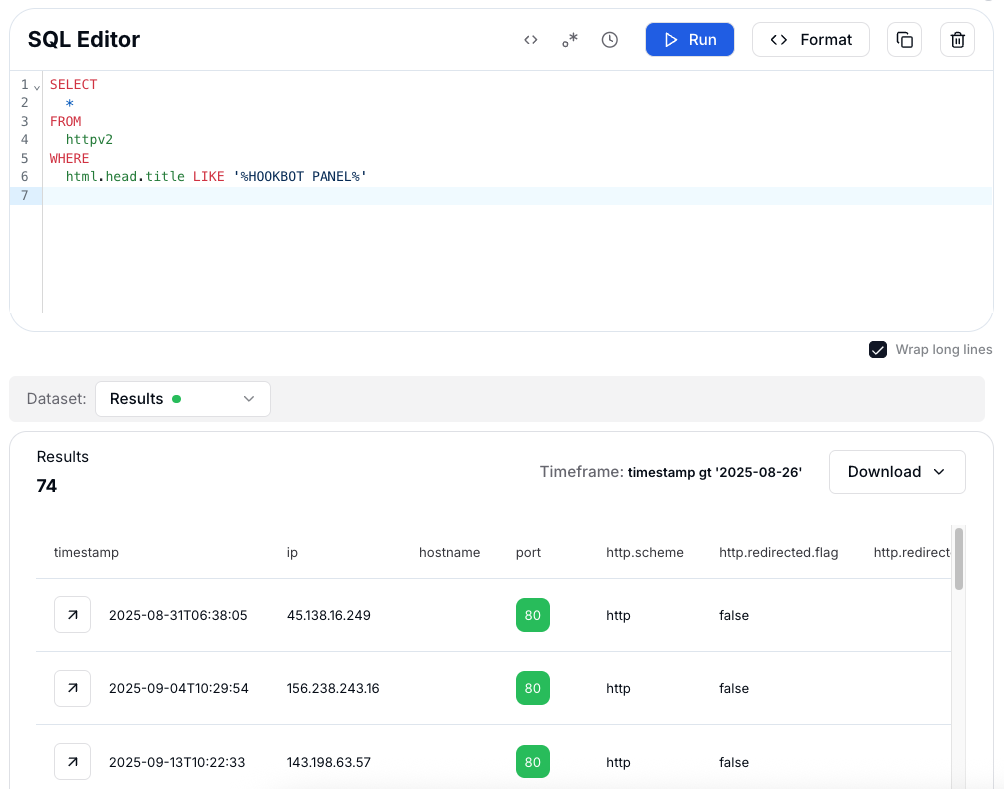 Figure 6: HuntSQL™ results for "HOOKBOT PANEL" title
Figure 6: HuntSQL™ results for "HOOKBOT PANEL" titleAnother effective way to hunt for control panels is by analyzing their favicon. Many malware panels reuse the same favicon image across different deployments, making it a strong and consistent fingerprint. To extract the favicon hash locally on Windows, we can first download the file and then compute its MD5 hash
This gives us the following MD5 hash: 5d17fbecdbd631b16214c7d7d0d71ff9. With this value, we can pivot in Hunt.io to search for other websites using the same favicon. A simple query would look like this
SELECT
*
FROM
crawler
WHERE
favicon_md5 LIKE '5d17fbecdbd631b16214c7d7d0d71ff9'
AND timestamp > '2024-08-07'
CopyOutput:
Beyond mobile banking malware, open-source frameworks like Chaos RAT also leave behind telltale control panels that defenders can track.
Detecting Chaos RAT Panels with Hashes & Repo Links
Chaos RAT (Remote Administration Tool) is an open-source C2 framework written in Golang that was originally developed as a legitimate remote administration tool but has since been weaponized by threat actors.
It works on both Windows and Linux systems, making it attractive for attackers. First observed in malicious campaigns around 2022, we have observed Chaos RAT distributed via phishing campaigns that mimic utilities like "NetworkAnalyzer," though distribution methods vary between campaigns."
Once executed, the tool provides a wide range of capabilities, including establishing reverse shells, uploading and downloading files, executing commands, taking screenshots, gathering system information, and even restarting or shutting down the victim's machine.
On Linux, persistence is often achieved by modifying /etc/crontab to regularly fetch payloads, while on Windows, attackers are believed to use scheduled tasks or registry run keys. Chaos RAT has also been linked to cryptomining campaigns, often deploying Monero miners after reconnaissance.
Its web-based admin panel allows operators to build custom payloads, manage infected clients, and control sessions. However, it has been plagued by vulnerabilities such as command injection (CVE-2024-30850) and XSS flaws (CVE-2024-31839) that could be exploited against the operators themselves.
In recent years, new variants have incorporated evasion features and been distributed through supply chain attacks, such as malicious Arch Linux AUR packages that secretly installed the Chaos RAT.
Because of its growing abuse, defenders are advised to monitor for persistence mechanisms like suspicious crontab entries or scheduled tasks, watch for abnormal reverse shell activity, and use behavioral detection methods instead of relying solely on static signatures. Chaos RAT is a strong example of how open-source tools can evolve into powerful cyber threats when abused by malicious actors.
Chaos RAT control panel
It's a web-based interface that provides attackers with centralized management over compromised systems. We often observe instances on port 8080 and occasionally find weak or default credentials (for example, admin:admin), making it easy to deploy.
Through the dashboard, operators can build custom payloads for both Windows and Linux, track infected hosts with details like IP and operating system, and control sessions in real time. The panel allows attackers to execute commands, open reverse shells, upload or download files, capture screenshots, and even open URLs remotely.
It also provides payload management features, letting operators generate and disguise malicious binaries to evade detection. However, the control panel itself has been found to contain vulnerabilities, including command injection and cross-site scripting flaws, which could be exploited against the operators.
Overall, the Chaos RAT control panel lowers the barrier to entry for cybercriminals by offering a simple login page and an intuitive dashboard that transforms a powerful malware framework into an easy-to-use command-and-control platform.
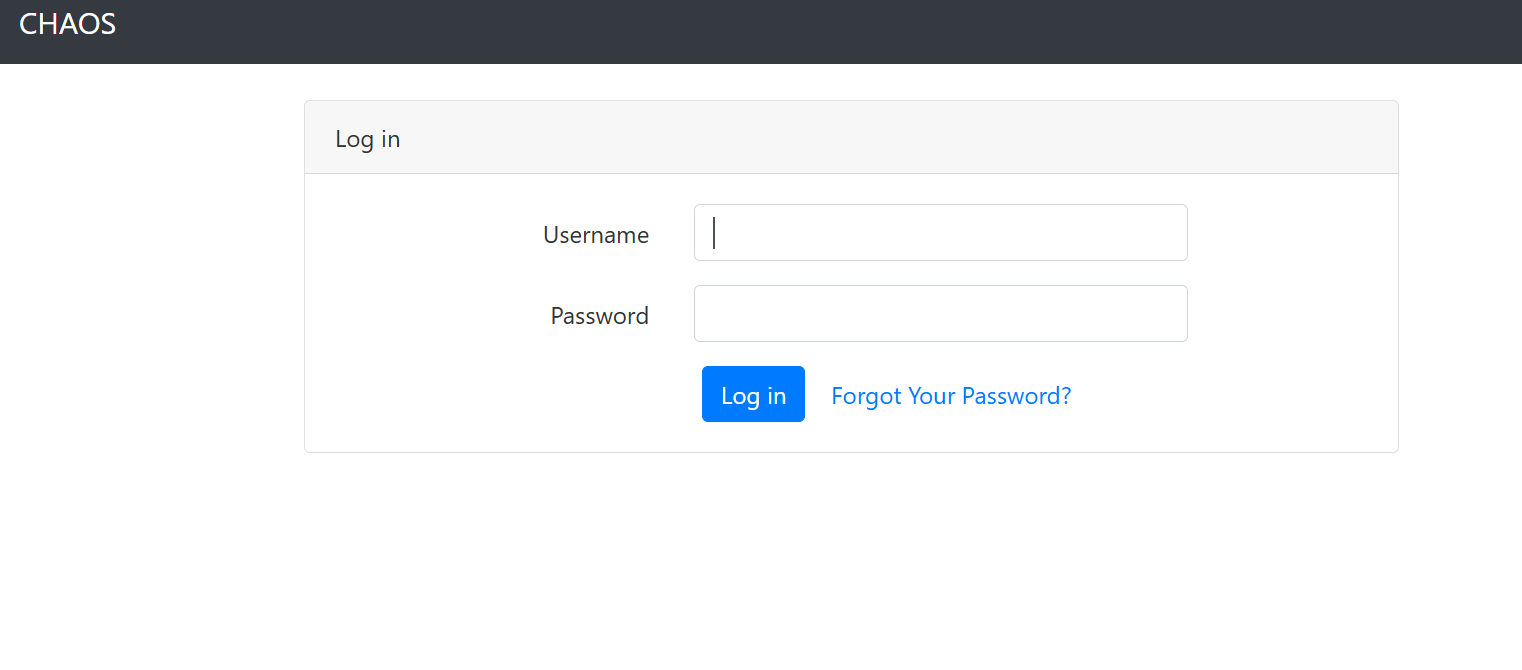 Figure 9: Chaos RAT dashboard on port 8080
Figure 9: Chaos RAT dashboard on port 8080Finding Chaos Control Panels
This query searches the httpv2 dataset for all web pages where the SHA-256 hash of the HTML body matches a known value (b78ec7d301f2d25c974800c136c583b7b5a25ec5ec13dbf04cae9817fa8045aa). By applying the timestamp > '2024-08-07' filter, the hunt is limited to pages observed after August 7, 2024.
In practice, I used the HTML body hash as a hunting pivot to identify other pages hosting the same or similar content
SELECT
*
FROM
httpv2
WHERE
html.body.hash.sha256 = 'b78ec7d301f2d25c974800c136c583b7b5a25ec5ec13dbf04cae9817fa8045aa'
AND timestamp > '2024-08-07'
CopyOutput:
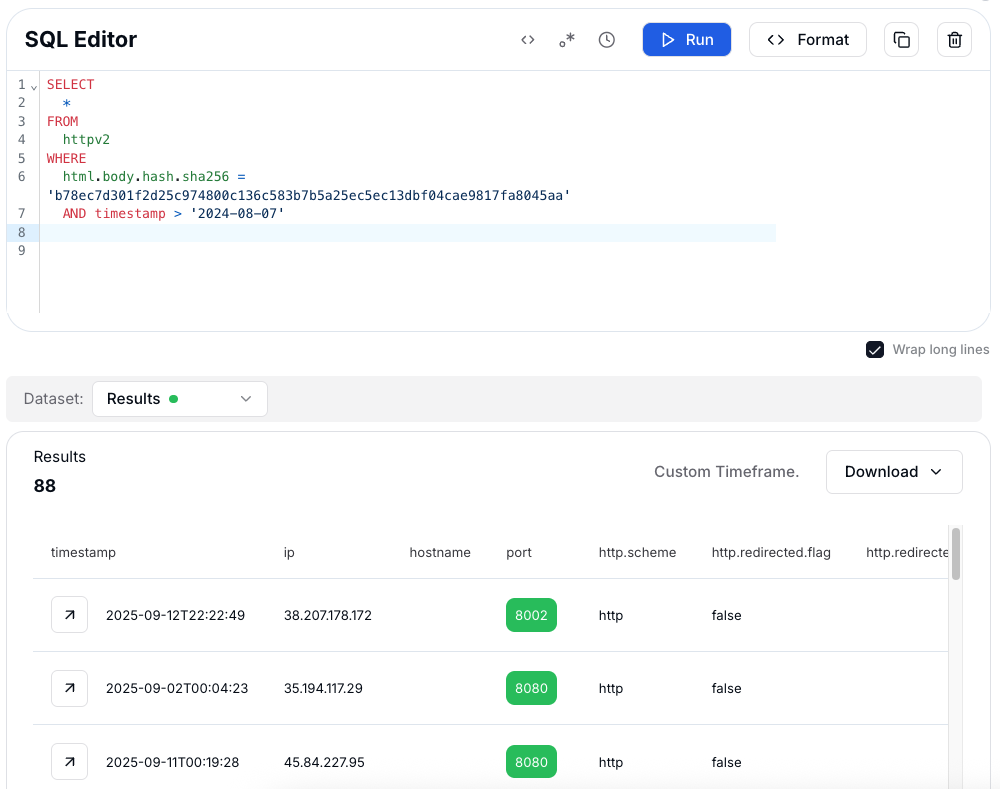 Figure 10: HuntSQL™ search using Chaos HTML body hash
Figure 10: HuntSQL™ search using Chaos HTML body hashAfter examining the code, we can find that the developer references this GitHub repository (linked directly in the HTML content). This indicates that websites or control panels are associated with the CHAOS Remote Administration Tool (RAT). I can uncover related infrastructure, cloned control panels that reference the same repository.
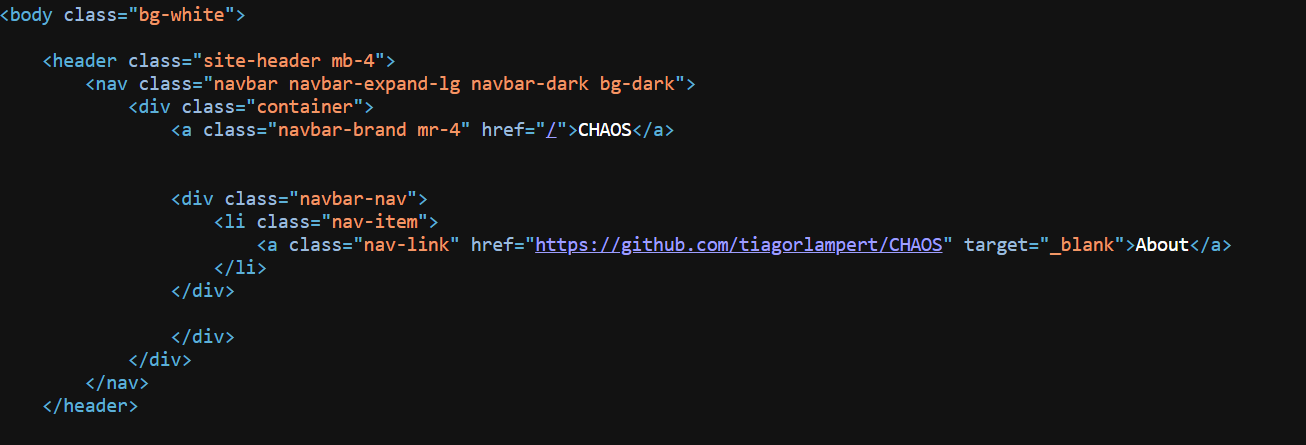 Figure 11: Chaos panel code referencing GitHub repo.
Figure 11: Chaos panel code referencing GitHub repo.This query retrieves all web pages from the httpv2 dataset whose HTML body contains the GitHub link github.com/tiagorlampert/CHAOS, with results limited to pages observed after August 7, 2024. This helps narrow the focus to recent activity and potentially active infrastructure.
SELECT
*
FROM
httpv2
WHERE
html.body.content like '%github.com/tiagorlampert/CHAOS%'
AND timestamp gt '2024-08-07'
CopyOutput:
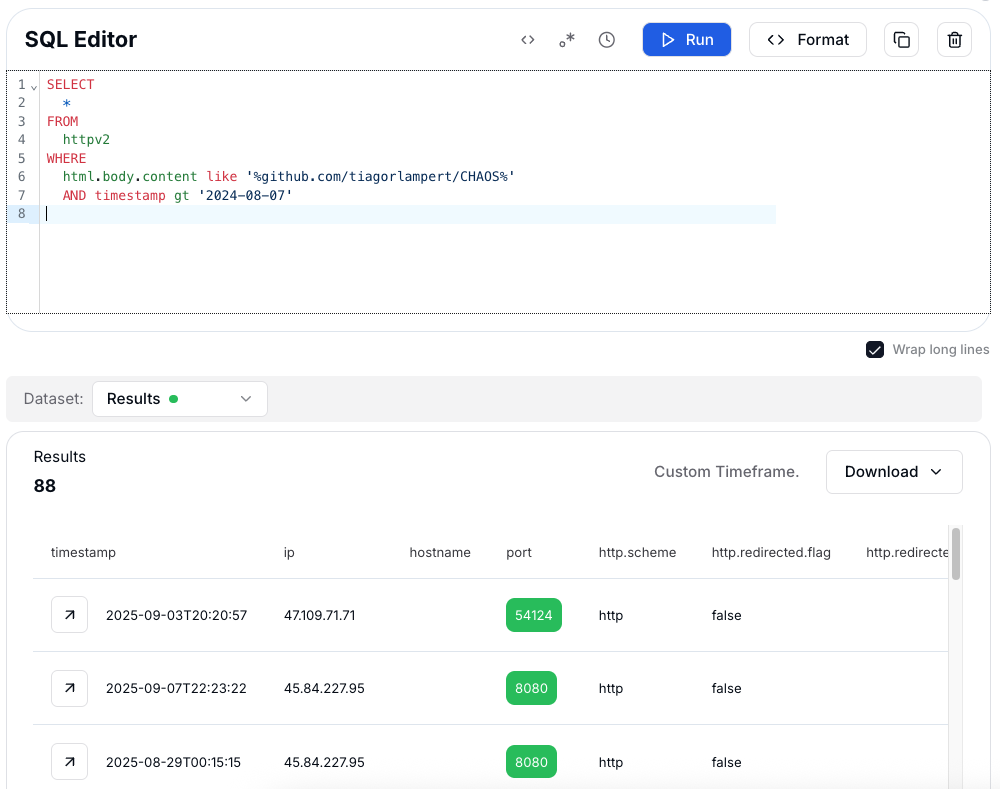 Figure 12: Hunting Chaos control panels via the link to the repository on GitHub
Figure 12: Hunting Chaos control panels via the link to the repository on GitHubMining-related dashboards such as UnamWebPanel add another example of how default titles and simple patterns can reveal active panels.
UnamWebPanel Hunting through Default Titles
UnamWebPanel is an open-source PHP-based web control panel developed by Unam Sanctam for monitoring and managing cryptocurrency mining operations, primarily the SilentCryptoMiner.
The panel is lightweight and easy to deploy on any PHP-enabled web server, allowing operators to view miner statistics, manage connections, and access detailed performance graphs through a browser interface. Version 1.8.0 introduced multiple security and usability enhancements, including IP blocking, session-based password verification, stricter headers for browser security, improved error logging, and new visualizations such as line and pie charts for miner activity.
It uses an SQLite database by default, supports multiple languages, and features role-based protections to reduce exposure risks. While the developer highlights that the project is for educational purposes only, its design demonstrates how centralized dashboards can simplify the oversight of distributed mining clients.
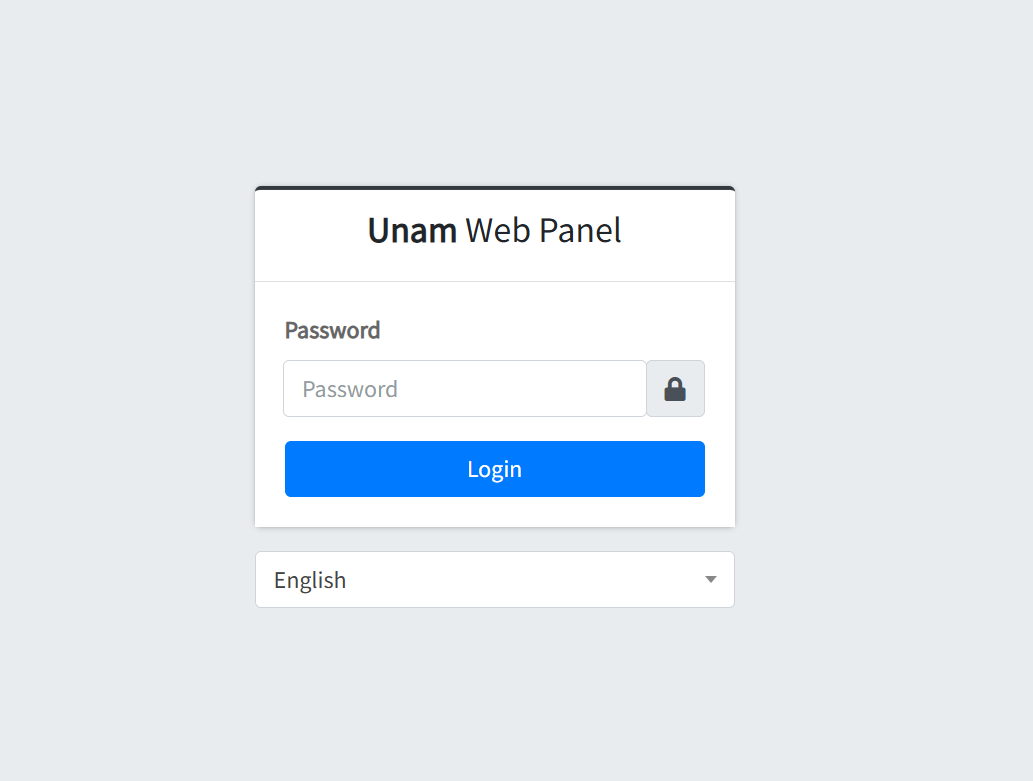 Figure 13: Default UnamWebPanel login page
Figure 13: Default UnamWebPanel login pageDiscovering Unam Control Panels
When hunting for UnamWebPanel servers, one of the easiest things to look for is the page title. By default, the login page shows "Unam Web Panel - Login" in the
<title> tag, and most attackers don't bother changing it.
So we crafted a query to detect this panel:
SELECT
*
FROM
httpv2
WHERE
html.head.title LIKE '%Unam Web Panel%'
AND timestamp gt '2024-08-01'
CopyThis query looks through the httpv2 dataset and returns all records where the page title in the HTML header contains "Unam Web Panel". By filtering on the html.head.title field, we're specifically targeting systems that expose the UnamWebPanel login page.
The query also includes a time filter (timestamp gt '2024-08-01'), which ensures we only see results discovered after August 1st, 2024. This way, we can focus on the most recent and potentially still active panels when hunting for exposed UnamWebPanel instances across the internet.
Output:
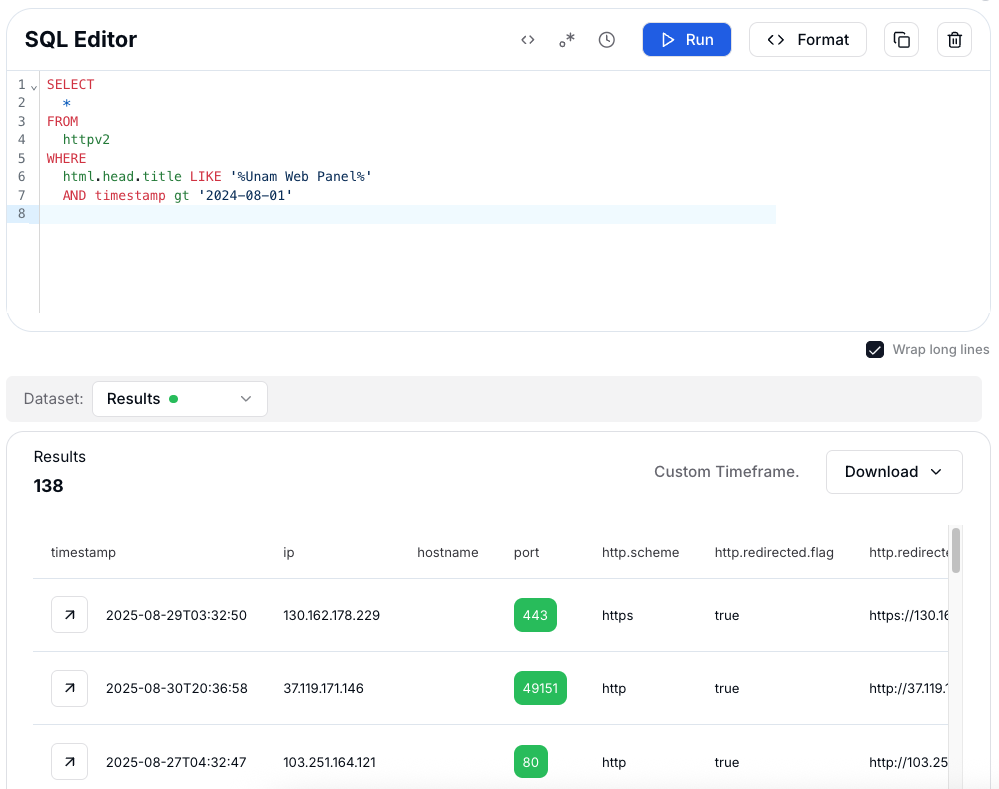 Figure 14: HuntSQL™ results for "Unam Web Panel" title
Figure 14: HuntSQL™ results for "Unam Web Panel" titleNot all panels are tied to pure malware; widely used security tools like Metasploit can also surface in the wild, sometimes unintentionally exposed.
Hunting Metasploit Web Panels in the Wild
Metasploit web panels are browser-based interfaces, either the official Metasploit Pro UI or third-party/front-end wrappers that put Metasploit's exploitation, payload-generation, and session-management features into a single dashboard.
Through these panels, users (or attackers) can build and configure payloads, launch exploits, manage active sessions, and upload or download binaries from a central, web-accessible console. Because they make complex tasks much easier, they're useful tools for red teams and penetration testers, but they're also attractive to malicious actors who can expose them publicly to stage attacks or control compromised hosts.
When hunting for these panels, look at page titles, repository links, payload filenames, and hosting metadata to help distinguish legitimate test environments from suspicious or abused installations.
 Figure 15: Example of Metasploit web UI
Figure 15: Example of Metasploit web UIIdentifying Metasploit Control Panels
After looking at the code of the web panel, we can focus on the page title to locate other instances.
SELECT
*
FROM
httpv2
WHERE
html.head.title LIKE '%Metasploit%'
AND
http.redirected.url like '%/login'
CopyThis query searches the httpv2 dataset for HTTP responses whose HTML
<title> contains the string "Metasploit" and that redirect to a /login path. In practice, this surfaces pages that reference Metasploit in their title and also expose a login interface, which is a stronger indicator of active Metasploit web consoles or related deployments rather than just documentation, demos, or test labs.
Output:
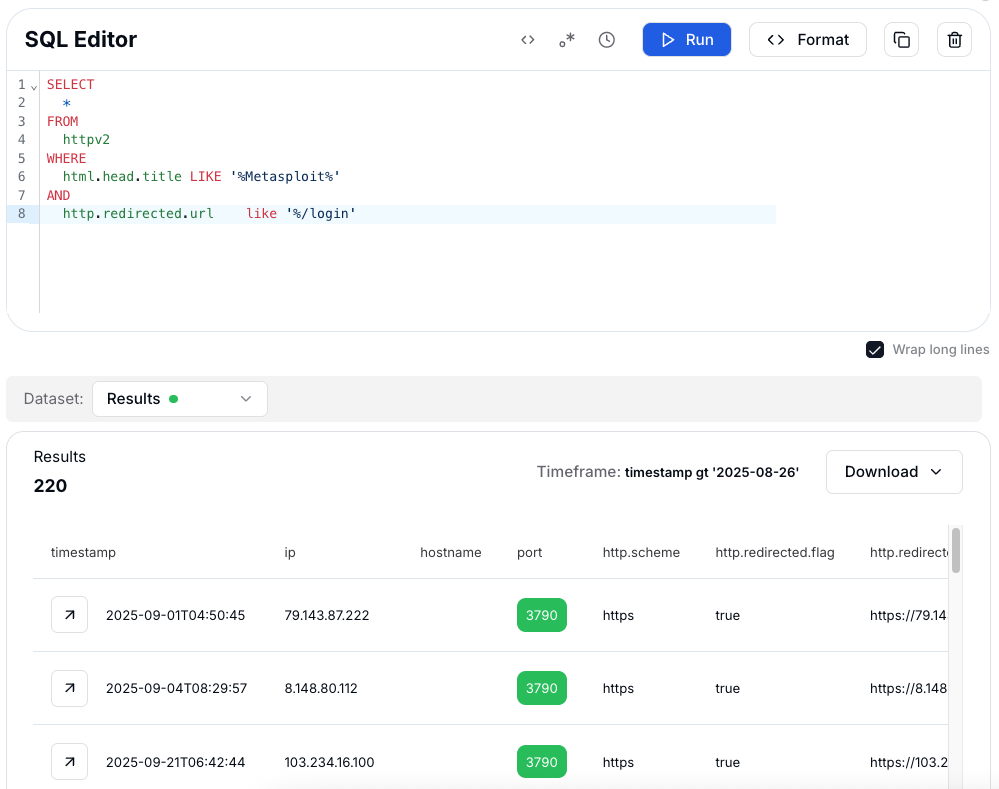 Figure 16: HuntSQL results where title contains "Metasploit" and the server redirects to /login
Figure 16: HuntSQL results where title contains "Metasploit" and the server redirects to /loginFinally, let's look at Mythic, a modern C2 framework whose powerful web interface makes exposed instances particularly risky when left unsecured.
Tracking Mythic C2 Panels & Active Deployments
Mythic web panels are the browser-based front end for the Mythic command-and-control (C2) framework. They provide operators with a centralized dashboard to generate and configure payloads (agents), manage active callbacks, issue tasks and commands to compromised hosts, and transfer files all through an intuitive web UI.
Mythic separates the web UI, the C2 backend, and agent payloads, which makes it easy to plug in different agent implementations (Python, Go, C#, Rust, etc.) and to extend functionality via plugins and payload-type modules.
Because it streamlines payload building, operator tasking, and multi-host session management, Mythic is popular with red teams, adversary emulation teams, and researchers; however, the same features make exposed or poorly secured Mythic panels attractive to malicious actors if deployed publicly.
Typical uses include automated payload generation, interactive command execution, scheduled tasks, lateral-movement support, and integration with other tooling (e.g., Sliver, Cobalt Strike, or custom tooling) for workflow automation.
 Figure 17: Mythic C2 control panel
Figure 17: Mythic C2 control panelUncovering Mythic Control Panels
By examining the web panel code, we can look for more specific traits than just the title. A reliable signal is the login redirect path that Mythic uses.
The following query checks for HTTP responses where the
<title> contains "Mythic" and the server redirects to /new/login, which is characteristic of exposed Mythic dashboards.
SELECT
*
FROM
httpv2
WHERE
html.head.title LIKE '%Mythic%'
AND
http.redirected.url LIKE '%/new/login'
CopyOutput:
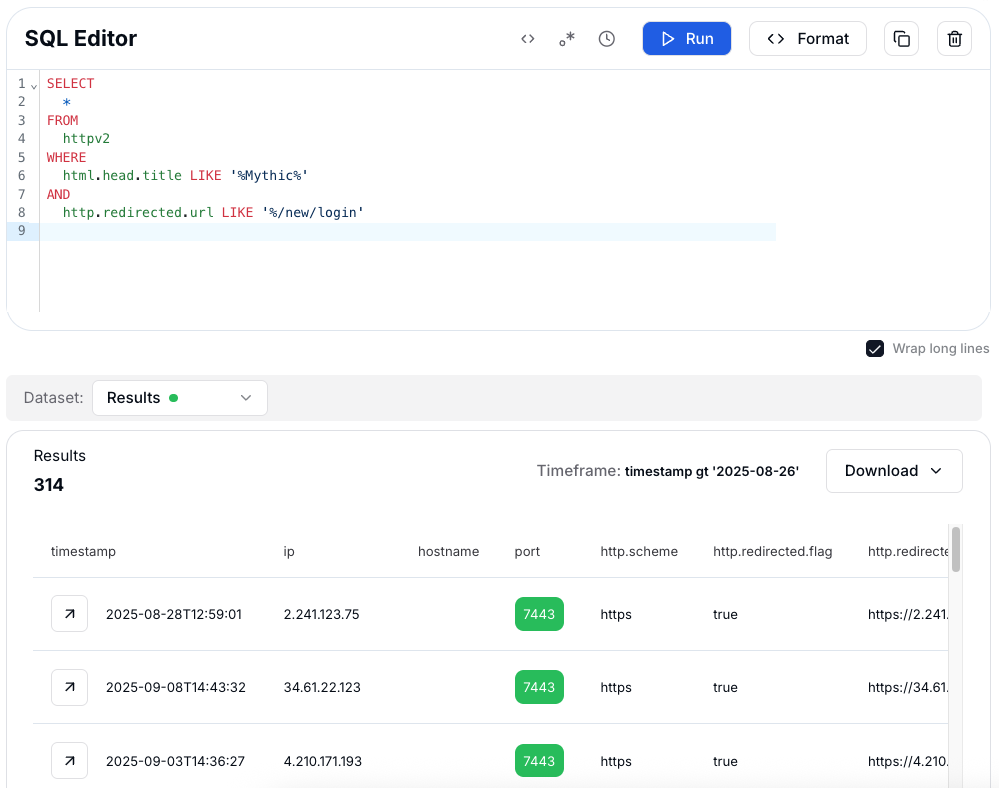 Figure 18: HuntSQL™ results where title contains "Mythic" and the server redirects to /new/login
Figure 18: HuntSQL™ results where title contains "Mythic" and the server redirects to /new/loginMitigation Strategies
Exposed panels like Supershell, HookBot, Chaos RAT, UnamWebPanel, Metasploit, and Mythic can be abused if left unchecked. Defenders should focus on spotting their fingerprints in traffic, blocking them at the edge, and escalating to the right channels.
Supershell: Watch for requests to /supershell/login/ and block them with WAF or firewall rules. Add detections for the Supershell title and for panels exposed on ports like 8888.
HookBot: Detect HookBot panels by matching the "HOOKBOT PANEL" title or the known favicon hash. Add these to IDS/IPS signatures, SIEM rules, and blocklists.
Chaos RAT: Detect HookBot panels by matching the "HOOKBOT PANEL" title or the known favicon hash. Add these to IDS/IPS signatures, SIEM rules, and blocklists.
UnamWebPanel: Alert on pages with the default title "Unam Web Panel - Login." Add this fingerprint to monitoring pipelines and block traffic to identified hosts. Enrich detections with ASN or IP metadata for follow-up.
Metasploit: Detect panels where the title contains "Metasploit" and the server redirects to /login. Block these URLs with WAF rules and alert in SIEM to track possible exposed web consoles.
Mythic: Look for titles containing "Mythic" combined with redirects to /new/login. Add this pattern to detection rules, block it at the edge, and monitor callback activity for spikes linked to Mythic deployments.
Other panels: Combine fingerprints such as login paths (/login, /new/login, /supershell/login/), titles, favicon hashes, and repo links into composite detection rules.
Important: If you find an exposed control panel, do not attempt to log in or interact with it. Record passive evidence, note the exact timestamp and URL, and report the finding to the hosting provider or relevant CERT. If you plan to share IOCs publicly, redact sensitive details or distribute them through controlled channels to avoid enabling abuse.
Conclusion
Hunting exposed C2 panels is one of the most direct ways to spot attacker infrastructure on the internet. Simple clues like page titles, favicon hashes, URL paths, or code references can reveal panels that operators rely on every day.
Using datasets such as httpv2, urlx, and crawler in HuntSQL™ makes it possible to pivot across thousands of records quickly, confirm findings with snapshots, and connect related servers. This approach helps security teams find infrastructure early, limit exposure, and cut down the time attackers have to operate.
C2 Panels IOCs
The following indicators were collected during the hunts for Supershell, HookBot, Chaos RAT, UnamWebPanel, Metasploit, and Mythic panels. These IPs were observed hosting or linked to exposed dashboards. Reviewing them can help with enrichment, blocklisting, or retrospective searches in your own telemetry.
| IP | C2/Malware History | City | Country | ASN |
|---|---|---|---|---|
| 134.122.207[.]42 | 2 | Tung Chung | HK | AS152194 |
| 4.210.171[.]193 | 1 | Amsterdam | NL | AS8075 |
| 62.60.245[.]136 | 1 | Frankfurt am Main | DE | AS211522 |
| 74.48.140[.]110 | 1 | Los Angeles | US | AS35916 |
| 103.234.16[.]100 | 4 | Dhaka | BD | AS151488 |
| 38.55.199[.]160 | 1 | Tung Chung | HK | AS139659 |
Exposed command and control (C2) panels are active dashboards used by attackers to run their campaigns. They give operators a central place to watch infected devices, move stolen data, and send new instructions. Finding these panels early can help security teams cut off activity before it grows.
In practice, these panels work like the control rooms of an operation. Through a simple web interface, attackers can see victims, gather details such as location or system info, collect credentials or cryptocurrency wallets, and push out new payloads. Panels like these are a standard part of modern malware families.
This guide looks at some of the most common panels seen online today: Supershell, HookBot, Chaos RAT, UnamWebPanel, Metasploit, and Mythic. Each one has fingerprints that give it away, whether it's a URL path, a title, a favicon hash, or even a code reference. Learning to recognize those clues makes it easier to track attacker infrastructure and close off exposure before it's abused.
HuntSQL™: a key part of the C2 panel hunting process
HuntSQL™ is Hunt.io's SQL-driven interface built for defenders who need to move quickly across large security datasets. Instead of juggling multiple tools, analysts can pivot, correlate, and validate clues within a single environment. This makes it possible to move from a URL path to a TLS certificate to a page snapshot in one workflow, which is especially useful when exposing attacker infrastructure.
In this guide, we focus on three datasets that are most valuable for hunting C2 panels:
httpv2 provides detailed web-scan telemetry, including response headers and page content. It helps surface suspicious login pages and unique response patterns tied to control dashboards.
urlx works as a broad URL index for reconnaissance, letting analysts test hunting ideas and uncover patterns across billions of internet-facing endpoints.
crawler captures page snapshots and artifacts such as scripts, favicons, and embedded resources. These details confirm whether a candidate page is a real control panel and help link related infrastructure through shared assets.
Other HuntSQL™ datasets, such as Malware, Certificates, Honeypot, Open Directories, and Phishing, add important context for broader threat hunting. They cover confirmed C2 servers, reused TLS certificates, reconnaissance activity, and exposed staging directories. While we will not rely on them here, they highlight how HuntSQL™ brings together diverse sources into one place for mapping and disrupting adversary operations.
With this foundation in place, we can move into practical examples. Let's start with one of the most common frameworks seen online today: Supershell, and how to spot its panels using URL paths and titles.
Hunting Supershell Panels by URL Path & Title
One example of a control panel that can be discovered in the wild is Supershell, an open-source post-exploitation framework written in Go. Supershell gives attackers a web-based dashboard where they can manage compromised hosts, run commands, and maintain persistence across infected systems.
 Figure 1: Supershell login page exposed on port 8888
Figure 1: Supershell login page exposed on port 8888Identifying Supershell Control Panels
Its login page, which prominently displays the "Supershell" branding and version number, makes it easy to identify and hunt. For instance, the URL
http://134.122.207.42:8888/supershell/login/ exposes a Supershell login panel directly on the internet.
By examining the URL of a control panel, we can often extract useful indicators for threat hunting. In the case of Supershell, the last part of the URL /supershell/login/ is a strong and unique pattern that can be used to identify other exposed panels.
SELECT
*
FROM
urlx
WHERE
url LIKE '%/supershell/login%'
CopyOutput:
 Figure 2: Hunting Supershell panels via URL path.
Figure 2: Hunting Supershell panels via URL path.With Hunt.io, we can craft a hunting query that searches for all URLs containing this path, allowing us to collect and map multiple instances of Supershell control panels across different IPs and domains.
 Figure 3: HTML snippet with "Supershell" in page title
Figure 3: HTML snippet with "Supershell" in page titleTo extend our coverage even further, we can pivot on another indicator found in the panel's code: the HTML title, which clearly contains the name "Supershell." This gives us an additional fingerprint to expand our hunt and catch more exposed panels.
SELECT
*
FROM
httpv2
WHERE
html.head.title LIKE '%Supershell -%'
CopyOutput:
 Figure 4: Hunting Supershell panels via the title of the HTML page
Figure 4: Hunting Supershell panels via the title of the HTML pageAfter Supershell, another family that often exposes its infrastructure is HookBot, which can be recognized through simple but reliable fingerprints.
Identifying HookBot Panels via Titles & Favicons
HookBot is a powerful Android banking trojan designed to steal credentials, intercept SMS messages, and bypass multi-factor authentication (MFA). Once installed on a victim's device, HookBot can overlay fake login screens on top of legitimate apps to harvest sensitive information from banking, email, and cryptocurrency services.
The malware communicates with a web-based control panel, giving attackers the ability to manage infected devices, issue commands, and monitor stolen data in real time.
 Figure 5: HookBot control panel login screenshot.
Figure 5: HookBot control panel login screenshot.Detecting HookBot Control Panels
By examining the source code of a control panel, we can often extract valuable indicators that help us expand our hunt. One strong example is the HTML title, which many panels display consistently across deployments. For HookBot, the panel title includes the string "HOOKBOT PANEL", making it a reliable fingerprint. Using Hunt.io, we can craft a query to collect all sites where this title appears:
SELECT
*
FROM
httpv2
WHERE
html.head.title LIKE '%HOOKBOT PANEL%'
CopyOutput:
 Figure 6: HuntSQL™ results for "HOOKBOT PANEL" title
Figure 6: HuntSQL™ results for "HOOKBOT PANEL" titleAnother effective way to hunt for control panels is by analyzing their favicon. Many malware panels reuse the same favicon image across different deployments, making it a strong and consistent fingerprint. To extract the favicon hash locally on Windows, we can first download the file and then compute its MD5 hash
This gives us the following MD5 hash: 5d17fbecdbd631b16214c7d7d0d71ff9. With this value, we can pivot in Hunt.io to search for other websites using the same favicon. A simple query would look like this
SELECT
*
FROM
crawler
WHERE
favicon_md5 LIKE '5d17fbecdbd631b16214c7d7d0d71ff9'
AND timestamp > '2024-08-07'
CopyOutput:
Beyond mobile banking malware, open-source frameworks like Chaos RAT also leave behind telltale control panels that defenders can track.
Detecting Chaos RAT Panels with Hashes & Repo Links
Chaos RAT (Remote Administration Tool) is an open-source C2 framework written in Golang that was originally developed as a legitimate remote administration tool but has since been weaponized by threat actors.
It works on both Windows and Linux systems, making it attractive for attackers. First observed in malicious campaigns around 2022, we have observed Chaos RAT distributed via phishing campaigns that mimic utilities like "NetworkAnalyzer," though distribution methods vary between campaigns."
Once executed, the tool provides a wide range of capabilities, including establishing reverse shells, uploading and downloading files, executing commands, taking screenshots, gathering system information, and even restarting or shutting down the victim's machine.
On Linux, persistence is often achieved by modifying /etc/crontab to regularly fetch payloads, while on Windows, attackers are believed to use scheduled tasks or registry run keys. Chaos RAT has also been linked to cryptomining campaigns, often deploying Monero miners after reconnaissance.
Its web-based admin panel allows operators to build custom payloads, manage infected clients, and control sessions. However, it has been plagued by vulnerabilities such as command injection (CVE-2024-30850) and XSS flaws (CVE-2024-31839) that could be exploited against the operators themselves.
In recent years, new variants have incorporated evasion features and been distributed through supply chain attacks, such as malicious Arch Linux AUR packages that secretly installed the Chaos RAT.
Because of its growing abuse, defenders are advised to monitor for persistence mechanisms like suspicious crontab entries or scheduled tasks, watch for abnormal reverse shell activity, and use behavioral detection methods instead of relying solely on static signatures. Chaos RAT is a strong example of how open-source tools can evolve into powerful cyber threats when abused by malicious actors.
Chaos RAT control panel
It's a web-based interface that provides attackers with centralized management over compromised systems. We often observe instances on port 8080 and occasionally find weak or default credentials (for example, admin:admin), making it easy to deploy.
Through the dashboard, operators can build custom payloads for both Windows and Linux, track infected hosts with details like IP and operating system, and control sessions in real time. The panel allows attackers to execute commands, open reverse shells, upload or download files, capture screenshots, and even open URLs remotely.
It also provides payload management features, letting operators generate and disguise malicious binaries to evade detection. However, the control panel itself has been found to contain vulnerabilities, including command injection and cross-site scripting flaws, which could be exploited against the operators.
Overall, the Chaos RAT control panel lowers the barrier to entry for cybercriminals by offering a simple login page and an intuitive dashboard that transforms a powerful malware framework into an easy-to-use command-and-control platform.
 Figure 9: Chaos RAT dashboard on port 8080
Figure 9: Chaos RAT dashboard on port 8080Finding Chaos Control Panels
This query searches the httpv2 dataset for all web pages where the SHA-256 hash of the HTML body matches a known value (b78ec7d301f2d25c974800c136c583b7b5a25ec5ec13dbf04cae9817fa8045aa). By applying the timestamp > '2024-08-07' filter, the hunt is limited to pages observed after August 7, 2024.
In practice, I used the HTML body hash as a hunting pivot to identify other pages hosting the same or similar content
SELECT
*
FROM
httpv2
WHERE
html.body.hash.sha256 = 'b78ec7d301f2d25c974800c136c583b7b5a25ec5ec13dbf04cae9817fa8045aa'
AND timestamp > '2024-08-07'
CopyOutput:
 Figure 10: HuntSQL™ search using Chaos HTML body hash
Figure 10: HuntSQL™ search using Chaos HTML body hashAfter examining the code, we can find that the developer references this GitHub repository (linked directly in the HTML content). This indicates that websites or control panels are associated with the CHAOS Remote Administration Tool (RAT). I can uncover related infrastructure, cloned control panels that reference the same repository.
 Figure 11: Chaos panel code referencing GitHub repo.
Figure 11: Chaos panel code referencing GitHub repo.This query retrieves all web pages from the httpv2 dataset whose HTML body contains the GitHub link github.com/tiagorlampert/CHAOS, with results limited to pages observed after August 7, 2024. This helps narrow the focus to recent activity and potentially active infrastructure.
SELECT
*
FROM
httpv2
WHERE
html.body.content like '%github.com/tiagorlampert/CHAOS%'
AND timestamp gt '2024-08-07'
CopyOutput:
 Figure 12: Hunting Chaos control panels via the link to the repository on GitHub
Figure 12: Hunting Chaos control panels via the link to the repository on GitHubMining-related dashboards such as UnamWebPanel add another example of how default titles and simple patterns can reveal active panels.
UnamWebPanel Hunting through Default Titles
UnamWebPanel is an open-source PHP-based web control panel developed by Unam Sanctam for monitoring and managing cryptocurrency mining operations, primarily the SilentCryptoMiner.
The panel is lightweight and easy to deploy on any PHP-enabled web server, allowing operators to view miner statistics, manage connections, and access detailed performance graphs through a browser interface. Version 1.8.0 introduced multiple security and usability enhancements, including IP blocking, session-based password verification, stricter headers for browser security, improved error logging, and new visualizations such as line and pie charts for miner activity.
It uses an SQLite database by default, supports multiple languages, and features role-based protections to reduce exposure risks. While the developer highlights that the project is for educational purposes only, its design demonstrates how centralized dashboards can simplify the oversight of distributed mining clients.
 Figure 13: Default UnamWebPanel login page
Figure 13: Default UnamWebPanel login pageDiscovering Unam Control Panels
When hunting for UnamWebPanel servers, one of the easiest things to look for is the page title. By default, the login page shows "Unam Web Panel - Login" in the
<title> tag, and most attackers don't bother changing it.
So we crafted a query to detect this panel:
SELECT
*
FROM
httpv2
WHERE
html.head.title LIKE '%Unam Web Panel%'
AND timestamp gt '2024-08-01'
CopyThis query looks through the httpv2 dataset and returns all records where the page title in the HTML header contains "Unam Web Panel". By filtering on the html.head.title field, we're specifically targeting systems that expose the UnamWebPanel login page.
The query also includes a time filter (timestamp gt '2024-08-01'), which ensures we only see results discovered after August 1st, 2024. This way, we can focus on the most recent and potentially still active panels when hunting for exposed UnamWebPanel instances across the internet.
Output:
 Figure 14: HuntSQL™ results for "Unam Web Panel" title
Figure 14: HuntSQL™ results for "Unam Web Panel" titleNot all panels are tied to pure malware; widely used security tools like Metasploit can also surface in the wild, sometimes unintentionally exposed.
Hunting Metasploit Web Panels in the Wild
Metasploit web panels are browser-based interfaces, either the official Metasploit Pro UI or third-party/front-end wrappers that put Metasploit's exploitation, payload-generation, and session-management features into a single dashboard.
Through these panels, users (or attackers) can build and configure payloads, launch exploits, manage active sessions, and upload or download binaries from a central, web-accessible console. Because they make complex tasks much easier, they're useful tools for red teams and penetration testers, but they're also attractive to malicious actors who can expose them publicly to stage attacks or control compromised hosts.
When hunting for these panels, look at page titles, repository links, payload filenames, and hosting metadata to help distinguish legitimate test environments from suspicious or abused installations.
 Figure 15: Example of Metasploit web UI
Figure 15: Example of Metasploit web UIIdentifying Metasploit Control Panels
After looking at the code of the web panel, we can focus on the page title to locate other instances.
SELECT
*
FROM
httpv2
WHERE
html.head.title LIKE '%Metasploit%'
AND
http.redirected.url like '%/login'
CopyThis query searches the httpv2 dataset for HTTP responses whose HTML
<title> contains the string "Metasploit" and that redirect to a /login path. In practice, this surfaces pages that reference Metasploit in their title and also expose a login interface, which is a stronger indicator of active Metasploit web consoles or related deployments rather than just documentation, demos, or test labs.
Output:
 Figure 16: HuntSQL results where title contains "Metasploit" and the server redirects to /login
Figure 16: HuntSQL results where title contains "Metasploit" and the server redirects to /loginFinally, let's look at Mythic, a modern C2 framework whose powerful web interface makes exposed instances particularly risky when left unsecured.
Tracking Mythic C2 Panels & Active Deployments
Mythic web panels are the browser-based front end for the Mythic command-and-control (C2) framework. They provide operators with a centralized dashboard to generate and configure payloads (agents), manage active callbacks, issue tasks and commands to compromised hosts, and transfer files all through an intuitive web UI.
Mythic separates the web UI, the C2 backend, and agent payloads, which makes it easy to plug in different agent implementations (Python, Go, C#, Rust, etc.) and to extend functionality via plugins and payload-type modules.
Because it streamlines payload building, operator tasking, and multi-host session management, Mythic is popular with red teams, adversary emulation teams, and researchers; however, the same features make exposed or poorly secured Mythic panels attractive to malicious actors if deployed publicly.
Typical uses include automated payload generation, interactive command execution, scheduled tasks, lateral-movement support, and integration with other tooling (e.g., Sliver, Cobalt Strike, or custom tooling) for workflow automation.
 Figure 17: Mythic C2 control panel
Figure 17: Mythic C2 control panelUncovering Mythic Control Panels
By examining the web panel code, we can look for more specific traits than just the title. A reliable signal is the login redirect path that Mythic uses.
The following query checks for HTTP responses where the
<title> contains "Mythic" and the server redirects to /new/login, which is characteristic of exposed Mythic dashboards.
SELECT
*
FROM
httpv2
WHERE
html.head.title LIKE '%Mythic%'
AND
http.redirected.url LIKE '%/new/login'
CopyOutput:
 Figure 18: HuntSQL™ results where title contains "Mythic" and the server redirects to /new/login
Figure 18: HuntSQL™ results where title contains "Mythic" and the server redirects to /new/loginMitigation Strategies
Exposed panels like Supershell, HookBot, Chaos RAT, UnamWebPanel, Metasploit, and Mythic can be abused if left unchecked. Defenders should focus on spotting their fingerprints in traffic, blocking them at the edge, and escalating to the right channels.
Supershell: Watch for requests to /supershell/login/ and block them with WAF or firewall rules. Add detections for the Supershell title and for panels exposed on ports like 8888.
HookBot: Detect HookBot panels by matching the "HOOKBOT PANEL" title or the known favicon hash. Add these to IDS/IPS signatures, SIEM rules, and blocklists.
Chaos RAT: Detect HookBot panels by matching the "HOOKBOT PANEL" title or the known favicon hash. Add these to IDS/IPS signatures, SIEM rules, and blocklists.
UnamWebPanel: Alert on pages with the default title "Unam Web Panel - Login." Add this fingerprint to monitoring pipelines and block traffic to identified hosts. Enrich detections with ASN or IP metadata for follow-up.
Metasploit: Detect panels where the title contains "Metasploit" and the server redirects to /login. Block these URLs with WAF rules and alert in SIEM to track possible exposed web consoles.
Mythic: Look for titles containing "Mythic" combined with redirects to /new/login. Add this pattern to detection rules, block it at the edge, and monitor callback activity for spikes linked to Mythic deployments.
Other panels: Combine fingerprints such as login paths (/login, /new/login, /supershell/login/), titles, favicon hashes, and repo links into composite detection rules.
Important: If you find an exposed control panel, do not attempt to log in or interact with it. Record passive evidence, note the exact timestamp and URL, and report the finding to the hosting provider or relevant CERT. If you plan to share IOCs publicly, redact sensitive details or distribute them through controlled channels to avoid enabling abuse.
Conclusion
Hunting exposed C2 panels is one of the most direct ways to spot attacker infrastructure on the internet. Simple clues like page titles, favicon hashes, URL paths, or code references can reveal panels that operators rely on every day.
Using datasets such as httpv2, urlx, and crawler in HuntSQL™ makes it possible to pivot across thousands of records quickly, confirm findings with snapshots, and connect related servers. This approach helps security teams find infrastructure early, limit exposure, and cut down the time attackers have to operate.
C2 Panels IOCs
The following indicators were collected during the hunts for Supershell, HookBot, Chaos RAT, UnamWebPanel, Metasploit, and Mythic panels. These IPs were observed hosting or linked to exposed dashboards. Reviewing them can help with enrichment, blocklisting, or retrospective searches in your own telemetry.
| IP | C2/Malware History | City | Country | ASN |
|---|---|---|---|---|
| 134.122.207[.]42 | 2 | Tung Chung | HK | AS152194 |
| 4.210.171[.]193 | 1 | Amsterdam | NL | AS8075 |
| 62.60.245[.]136 | 1 | Frankfurt am Main | DE | AS211522 |
| 74.48.140[.]110 | 1 | Los Angeles | US | AS35916 |
| 103.234.16[.]100 | 4 | Dhaka | BD | AS151488 |
| 38.55.199[.]160 | 1 | Tung Chung | HK | AS139659 |
Related Posts
Related Posts
Related Posts
©2026 Hunt Intelligence, Inc.
©2026 Hunt Intelligence, Inc.
©2025 Hunt Intelligence, Inc.