Introducing the Hunt.io C2 Feed
Introducing the Hunt.io C2 Feed
Published on
Jan 15, 2024

Introduction
ShadowPad, Quasar RAT, HeadLace, Emotet, and SIGNBT (to name a few) often grab headlines and captivate readers, leading to a long day of scouring logs and network traffic for blue teamers.
Yet, within the mentally taxing assembly instructions lies an equally significant threat -- command and control (C2) infrastructure. Malicious software without a communication link back to the operator isn't beneficial.
In this post, I'll discuss how we at Hunt identify, track, and burn malicious servers, all while keeping defenders updated on the latest threats.
Infrastructure Tracking Methods
Currently, Hunt tracks 110 (85 that are daily active) unique "Families," including information stealers, C2 frameworks, open-source offensive security tools, vulnerability scanners, and many more.
The below figure depicts what users see when navigating to the Advanced Search page.
 Figure 1: Hunt Active C2s page & top tracked servers
Figure 1: Hunt Active C2s page & top tracked serversTo stay ahead of the operationalization of these servers, Hunt's researchers identify patterns or anomalies that cause the infrastructure to stick out amongst the 1 billion plus IPv4 addresses.
This process could begin with a blog post or vendor report, an IOC database like Hunt's IOC Hunter (shameless plug), or through internet scanning.
Some areas that assist in detecting malicious infrastructure:
TLS/SSL certificates
HTTP headers
HTML strings
SSH keys
Domain naming conventions
JARM hash
JA4x fingerprinting hashes
TCP banners
We're all creatures of habit, including attackers; even the most advanced actor(s) has a preferred hosting provider or server software they will consistently fall back on.
Plenty of great articles have been published regarding tracking adversary infrastructure, but you're here for the method behind the madness, right?
Let's dig into a few examples!
Gh0st With a Past
Gh0st RAT (Remote Administration Tool) emerged into the public domain in 2008 and has continued its eerie presence with unrelenting momentum. With numerous variants and a recognizable network protocol, attackers haven't ceased haunting networks.
Version 3.6 includes the five-byte packet flag "Gh0st" between the victim and controller. Sounds easy to detect, right? I'll guide you (quickly) through the initial flaws in my scanning process for this RAT.
I developed a Python script to read a file of IP addresses and ports from an internet scan, send a packet consisting of random data along with the 13-byte header (5-byte "Gh0st", 4-byes packet length, and 4-byte length of packet unzipped), and output which servers responded with the matching packet flag.
*Before scanning the internet, ensure you understand applicable laws and regulations. Additionally, be a good neighbor and limit your scans to specific IP ranges.
 Figure 2: Snippet of initial Gh0st scanner
Figure 2: Snippet of initial Gh0st scannerThe program successfully identified known Gh0st controllers without any false positives. All done, right? Not so fast.
After discussing my new detection with a teammate, I quickly realized I could condense my script (removing the custom packet) to just a few lines.
It isn't necessary to send a custom packet to obtain the expected response. A few bytes of random data will do the trick.
 Figure 3: New code to verify Gh0st servers (Courtesy of a helpful Hunt teammate)
Figure 3: New code to verify Gh0st servers (Courtesy of a helpful Hunt teammate) Figure 4: Output of the above code
Figure 4: Output of the above codeNot Your Normal ShadowPad Certificate
If tracking suspected Chinese threat actors isn't your thing, you may not know that one method to identify ShadowPad, a much-reported on RAT, is through the TLS certificate it routinely uses.
Avoiding reliance on a single indicator is essential to enhance the tracking of malicious servers. To provide the most accurate information to our users, we'll consider several factors, such as hosting provider, location, historical/recent reporting, 3rd-party detections, etc., before adding C2s to the feed.
 Figure 5: ShadowPad certificate data
Figure 5: ShadowPad certificate data Figure 6: HTTP headers (port 443)
Figure 6: HTTP headers (port 443)While hunting for suspicious servers, I stumbled upon the certificate intended to spoof Dell, which also shared HTTP headers similar to those seen in Figure 6.
 Figure 7: Odd certificate data
Figure 7: Odd certificate data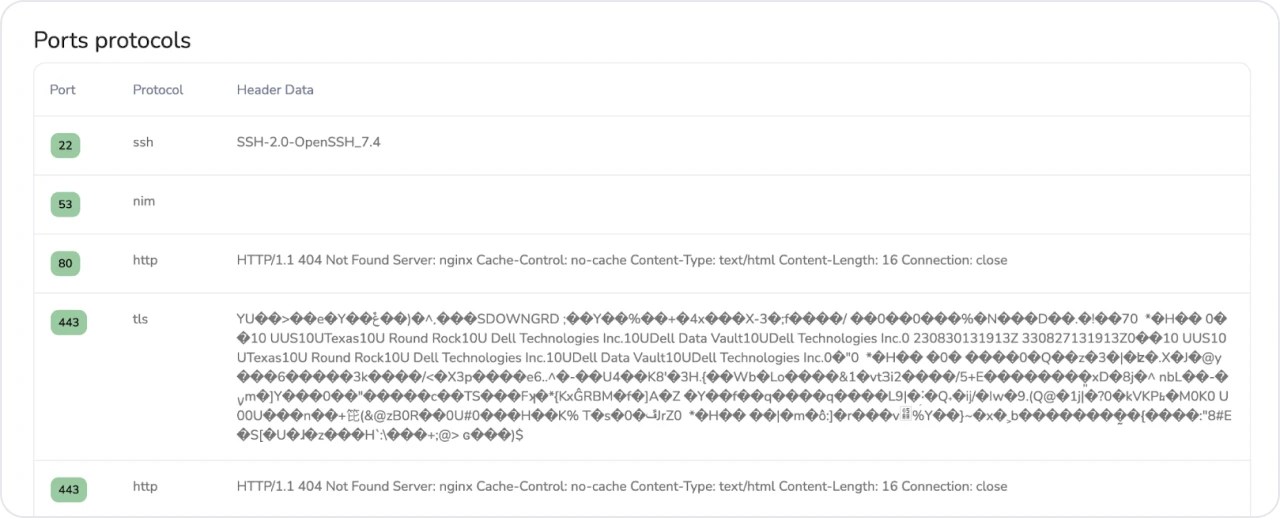 Figure 8: Snippet of HTTP response (ports 80 & 443)
Figure 8: Snippet of HTTP response (ports 80 & 443)Results from scanning the IP addresses confirmed this was a set of malicious servers, but to which malware family they were associated was unbeknownst to me.
After consulting with fellow researchers (thanks to the Slack Hunt users), we identified that this certificate, particularly, is associated with ShadowPad.
With that, we are ready to push a query combining the certificate fields and the HTTP response to Hunt, resulting in additional infrastructure for tracking/blocking.
Reeling in an Octopus, C2
Octopus is an initial access C2 server written in Python by mhaskar and is available on GitHub. The project is a bit older than other frameworks but is still in use and serves as a great example of detecting malicious servers by simply reading the source code.
Our first step will be to focus on portions of code dealing with network connections (sending or receiving) and any HTML files the operator will interact with. What better place to start than the file "weblistener.py".
It's been a while since we announced a new feature, and with 2024 already in full swing, it is time to highlight what's new and exciting in the world of Hunt.io!
To give you an idea of what our research team has been up to, we've been tirelessly exploring the malicious infrastructure landscape to bring you even more targeted solutions and insights. More precisely, this commitment to innovation has recently led to the development of C2 Feed, our latest effort in the near real-time identification of command and control (C2) frameworks. Designed to elevate your threat-hunting experience, C2 Feed centers on reliability and adoption speed to foster adequate visibility and efficient workflows.
Read on as we continue to pave the way for streamlined, cutting-edge detection opportunities and other innovative approaches to the problem of effectively incorporating context-aware indicators, thereby enabling more proactive and concerted responses to malicious activity across the enterprise.
What exactly are C2 feeds? We're glad you asked.
In general, C2 feeds enable early threat detection by revealing communication patterns associated with malicious entities. Analyzing this behavioral data also helps understand the tactics, techniques, and procedures (TTPs) employed by cyber adversaries, allowing for more effective mitigation practices.
Many organizations use C2 feeds tailored to their industry, sector, or technology stack. These customized threat feeds enhance the clarity and relevance of threat intelligence, allowing organizations to focus on the TTPs most pertinent to their environment.
Then, there is the question of efficiency; in this spirit, the contextual insights derived from C2 feeds enhance threat detection accuracy and streamline incident response workflows, empowering cybersecurity teams to navigate the complex threat landscape with agility and effectiveness.
How's our C2 Feed created?
Understanding the intricate process behind creating C2 Feed sheds light on its robustness and responsiveness to emerging threats, showcasing our commitment to delivering accurate and timely intelligence.

In short, our feature set entails:
High-Confidence Malicious Infrastructure Identification: C2 Feed delivers reliable data on malicious infrastructure through a new line JSON feed.
Comprehensive Internet Scanning: Utilizes extensive scanning of the entire internet to detect malware-related protocols, SSL certificates, and similar artifacts, including JARM/JA4 hashes.
Focused Monitoring of High-Risk Areas: Increases scanning frequency and thoroughness in internet hotspots known for previous malware activity or bulletproof hosting.
Rigorous Validation Process: Employs deep validation techniques to ensure the identified infrastructure is genuinely malicious, minimizing false positives.
Continuous Signature Updates by In-House Team: An in-house research team updates malware signatures weekly.
Diverse Threat Intelligence: As mentioned, the feed includes data on threats like C2 frameworks and reconnaissance tools.
Real-Time Data Generation: Offers real-time feed generation, encompassing data from the past seven days at the moment of request.
Choosing JSON in C2 Feed not only allows for the rapid dissemination of crucial threat intelligence but also ensures that it can be readily used by a diverse array of security solutions, significantly boosting cyber defense capabilities.

Summing up
Threat-hunting methodologies vary widely among organizations and depend on specific network environments, threat landscapes, and available resources---this refers to the well-known, quintessential "no one-size-fits-all" paradigm. However, the seamless integration capabilities and ample actionable intelligence that only tools like C2 Feed can deliver will help you prevail over malicious actors, allowing for more focused investigations and effective defensive strategies.
With features like C2 Feed, barriers to becoming an intelligence-driven, proactive security outfit are a thing of the past. Give it a try today and see how much you can improve your hunting game!
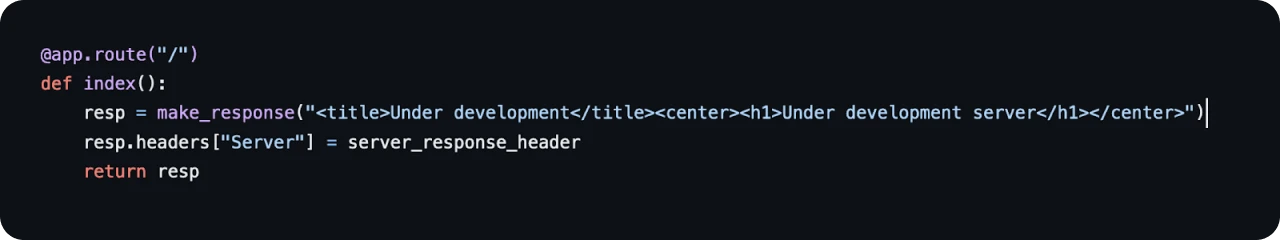
Figure 9: Octopus HTML title and header (https://github.com/mhaskar/Octopus)Within the above title and header tags, requests to the root directory return "Under development" and "Under development server." These tags are helpful, but many servers likely contain similar messages. We can use IOC Hunter or ThreatFox to find a few verified Octopus servers to gather additional information for detection..
 Figure 10: Octopus HTTP response headers
Figure 10: Octopus HTTP response headersThe HTML tags match the Python code in Figure 9. Adding the HTTP response and omitting any data for the Server and Date headers (as they are subject to change) to the two tags leaves us with a solid query to identify current and future Octopus infrastructure.
Conclusion
Developing a methodology that allows defenders to identify and neutralize attacker infrastructure before they have a chance to deploy their malware is critical to defending our networks. We at Hunt.io will continue unveiling these malicious networks, empowering defenders to stand up against ever-changing infrastructure procurement and employment tactics.
Introduction
ShadowPad, Quasar RAT, HeadLace, Emotet, and SIGNBT (to name a few) often grab headlines and captivate readers, leading to a long day of scouring logs and network traffic for blue teamers.
Yet, within the mentally taxing assembly instructions lies an equally significant threat -- command and control (C2) infrastructure. Malicious software without a communication link back to the operator isn't beneficial.
In this post, I'll discuss how we at Hunt identify, track, and burn malicious servers, all while keeping defenders updated on the latest threats.
Infrastructure Tracking Methods
Currently, Hunt tracks 110 (85 that are daily active) unique "Families," including information stealers, C2 frameworks, open-source offensive security tools, vulnerability scanners, and many more.
The below figure depicts what users see when navigating to the Advanced Search page.
 Figure 1: Hunt Active C2s page & top tracked servers
Figure 1: Hunt Active C2s page & top tracked serversTo stay ahead of the operationalization of these servers, Hunt's researchers identify patterns or anomalies that cause the infrastructure to stick out amongst the 1 billion plus IPv4 addresses.
This process could begin with a blog post or vendor report, an IOC database like Hunt's IOC Hunter (shameless plug), or through internet scanning.
Some areas that assist in detecting malicious infrastructure:
TLS/SSL certificates
HTTP headers
HTML strings
SSH keys
Domain naming conventions
JARM hash
JA4x fingerprinting hashes
TCP banners
We're all creatures of habit, including attackers; even the most advanced actor(s) has a preferred hosting provider or server software they will consistently fall back on.
Plenty of great articles have been published regarding tracking adversary infrastructure, but you're here for the method behind the madness, right?
Let's dig into a few examples!
Gh0st With a Past
Gh0st RAT (Remote Administration Tool) emerged into the public domain in 2008 and has continued its eerie presence with unrelenting momentum. With numerous variants and a recognizable network protocol, attackers haven't ceased haunting networks.
Version 3.6 includes the five-byte packet flag "Gh0st" between the victim and controller. Sounds easy to detect, right? I'll guide you (quickly) through the initial flaws in my scanning process for this RAT.
I developed a Python script to read a file of IP addresses and ports from an internet scan, send a packet consisting of random data along with the 13-byte header (5-byte "Gh0st", 4-byes packet length, and 4-byte length of packet unzipped), and output which servers responded with the matching packet flag.
*Before scanning the internet, ensure you understand applicable laws and regulations. Additionally, be a good neighbor and limit your scans to specific IP ranges.
 Figure 2: Snippet of initial Gh0st scanner
Figure 2: Snippet of initial Gh0st scannerThe program successfully identified known Gh0st controllers without any false positives. All done, right? Not so fast.
After discussing my new detection with a teammate, I quickly realized I could condense my script (removing the custom packet) to just a few lines.
It isn't necessary to send a custom packet to obtain the expected response. A few bytes of random data will do the trick.
 Figure 3: New code to verify Gh0st servers (Courtesy of a helpful Hunt teammate)
Figure 3: New code to verify Gh0st servers (Courtesy of a helpful Hunt teammate) Figure 4: Output of the above code
Figure 4: Output of the above codeNot Your Normal ShadowPad Certificate
If tracking suspected Chinese threat actors isn't your thing, you may not know that one method to identify ShadowPad, a much-reported on RAT, is through the TLS certificate it routinely uses.
Avoiding reliance on a single indicator is essential to enhance the tracking of malicious servers. To provide the most accurate information to our users, we'll consider several factors, such as hosting provider, location, historical/recent reporting, 3rd-party detections, etc., before adding C2s to the feed.
 Figure 5: ShadowPad certificate data
Figure 5: ShadowPad certificate data Figure 6: HTTP headers (port 443)
Figure 6: HTTP headers (port 443)While hunting for suspicious servers, I stumbled upon the certificate intended to spoof Dell, which also shared HTTP headers similar to those seen in Figure 6.
 Figure 7: Odd certificate data
Figure 7: Odd certificate data Figure 8: Snippet of HTTP response (ports 80 & 443)
Figure 8: Snippet of HTTP response (ports 80 & 443)Results from scanning the IP addresses confirmed this was a set of malicious servers, but to which malware family they were associated was unbeknownst to me.
After consulting with fellow researchers (thanks to the Slack Hunt users), we identified that this certificate, particularly, is associated with ShadowPad.
With that, we are ready to push a query combining the certificate fields and the HTTP response to Hunt, resulting in additional infrastructure for tracking/blocking.
Reeling in an Octopus, C2
Octopus is an initial access C2 server written in Python by mhaskar and is available on GitHub. The project is a bit older than other frameworks but is still in use and serves as a great example of detecting malicious servers by simply reading the source code.
Our first step will be to focus on portions of code dealing with network connections (sending or receiving) and any HTML files the operator will interact with. What better place to start than the file "weblistener.py".

It's been a while since we announced a new feature, and with 2024 already in full swing, it is time to highlight what's new and exciting in the world of Hunt.io!
To give you an idea of what our research team has been up to, we've been tirelessly exploring the malicious infrastructure landscape to bring you even more targeted solutions and insights. More precisely, this commitment to innovation has recently led to the development of C2 Feed, our latest effort in the near real-time identification of command and control (C2) frameworks. Designed to elevate your threat-hunting experience, C2 Feed centers on reliability and adoption speed to foster adequate visibility and efficient workflows.
Read on as we continue to pave the way for streamlined, cutting-edge detection opportunities and other innovative approaches to the problem of effectively incorporating context-aware indicators, thereby enabling more proactive and concerted responses to malicious activity across the enterprise.
What exactly are C2 feeds? We're glad you asked.
In general, C2 feeds enable early threat detection by revealing communication patterns associated with malicious entities. Analyzing this behavioral data also helps understand the tactics, techniques, and procedures (TTPs) employed by cyber adversaries, allowing for more effective mitigation practices.
Many organizations use C2 feeds tailored to their industry, sector, or technology stack. These customized threat feeds enhance the clarity and relevance of threat intelligence, allowing organizations to focus on the TTPs most pertinent to their environment.
Then, there is the question of efficiency; in this spirit, the contextual insights derived from C2 feeds enhance threat detection accuracy and streamline incident response workflows, empowering cybersecurity teams to navigate the complex threat landscape with agility and effectiveness.
How's our C2 Feed created?
Understanding the intricate process behind creating C2 Feed sheds light on its robustness and responsiveness to emerging threats, showcasing our commitment to delivering accurate and timely intelligence.

In short, our feature set entails:
High-Confidence Malicious Infrastructure Identification: C2 Feed delivers reliable data on malicious infrastructure through a new line JSON feed.
Comprehensive Internet Scanning: Utilizes extensive scanning of the entire internet to detect malware-related protocols, SSL certificates, and similar artifacts, including JARM/JA4 hashes.
Focused Monitoring of High-Risk Areas: Increases scanning frequency and thoroughness in internet hotspots known for previous malware activity or bulletproof hosting.
Rigorous Validation Process: Employs deep validation techniques to ensure the identified infrastructure is genuinely malicious, minimizing false positives.
Continuous Signature Updates by In-House Team: An in-house research team updates malware signatures weekly.
Diverse Threat Intelligence: As mentioned, the feed includes data on threats like C2 frameworks and reconnaissance tools.
Real-Time Data Generation: Offers real-time feed generation, encompassing data from the past seven days at the moment of request.
Choosing JSON in C2 Feed not only allows for the rapid dissemination of crucial threat intelligence but also ensures that it can be readily used by a diverse array of security solutions, significantly boosting cyber defense capabilities.

Summing up
Threat-hunting methodologies vary widely among organizations and depend on specific network environments, threat landscapes, and available resources---this refers to the well-known, quintessential "no one-size-fits-all" paradigm. However, the seamless integration capabilities and ample actionable intelligence that only tools like C2 Feed can deliver will help you prevail over malicious actors, allowing for more focused investigations and effective defensive strategies.
With features like C2 Feed, barriers to becoming an intelligence-driven, proactive security outfit are a thing of the past. Give it a try today and see how much you can improve your hunting game!
Figure 9: Octopus HTML title and header (https://github.com/mhaskar/Octopus)Within the above title and header tags, requests to the root directory return "Under development" and "Under development server." These tags are helpful, but many servers likely contain similar messages. We can use IOC Hunter or ThreatFox to find a few verified Octopus servers to gather additional information for detection..
 Figure 10: Octopus HTTP response headers
Figure 10: Octopus HTTP response headersThe HTML tags match the Python code in Figure 9. Adding the HTTP response and omitting any data for the Server and Date headers (as they are subject to change) to the two tags leaves us with a solid query to identify current and future Octopus infrastructure.
Conclusion
Developing a methodology that allows defenders to identify and neutralize attacker infrastructure before they have a chance to deploy their malware is critical to defending our networks. We at Hunt.io will continue unveiling these malicious networks, empowering defenders to stand up against ever-changing infrastructure procurement and employment tactics.
Related Posts
Related Posts
Related Posts


