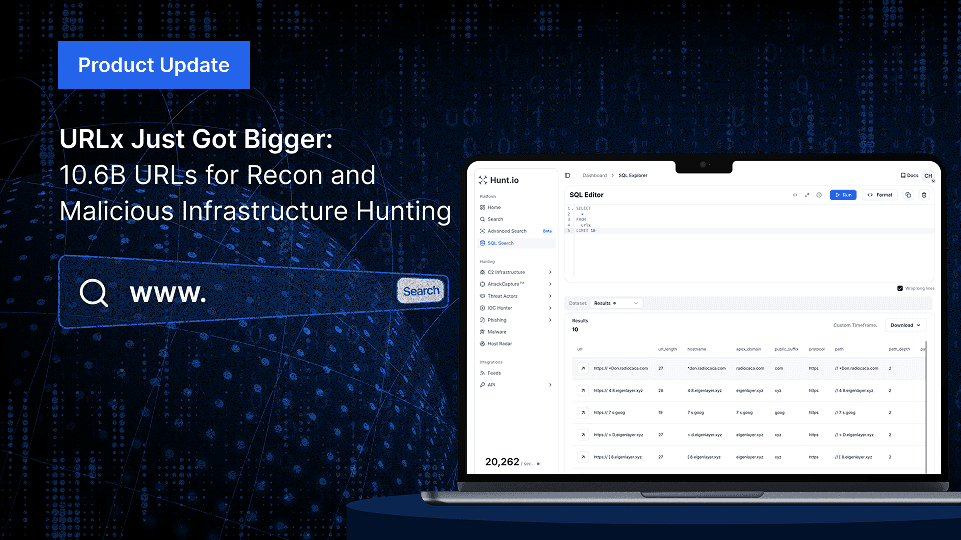
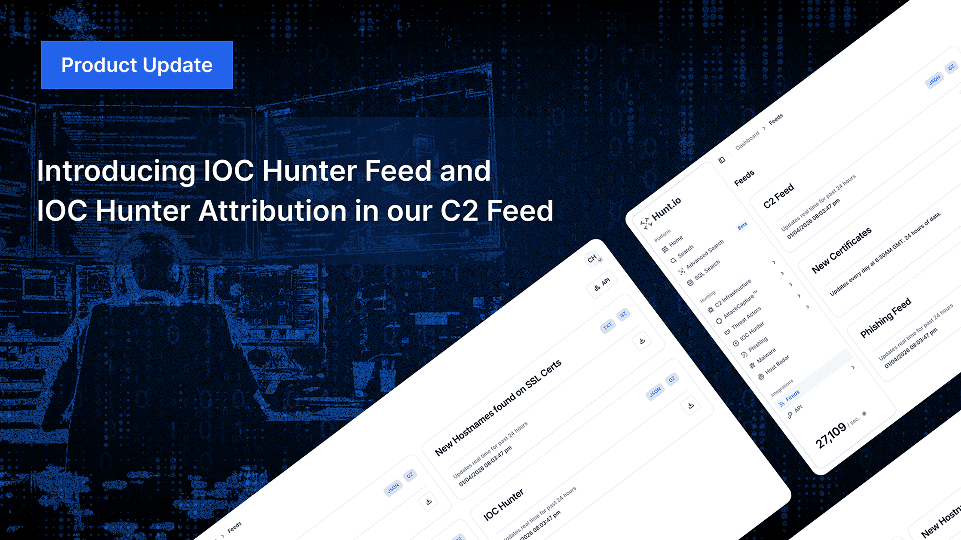
Introducing Hunt 2.1: Refinements to the Threat Hunting Experience
Published on

We're excited to announce Hunt 2.1, a new set of upgrades across Hunt.io, all built to help you cut through the noise and focus on what matters: identifying real threats faster. From smarter AI file analysis to more detailed IOC context, improved Threat Actor data, these updates are all about speeding up threat hunts and cutting out guesswork.
Here's a quick snapshot of what's new:
| Feature | What's New? |
|---|---|
| AttackCapture™ | Auto tagging of exploits, attacker configs and victim/targets, directory stats and better code search. |
| Updated Bulk Enrichment | Improved IP Enrichment to show historical C2, Attack Capture data and IOC Hunter enrichments. |
| SQL | New data sets, impoved documentation and UI. |
| Improved SSL Certificate Data | JA4X, fingerprinting, and issuer data shown cleanly, with pivot links. |
| Threat Actor Additions | Added ransomware and aliases by security vendor. |
| Integrations | Cyware integration updated with IOC Hunter. |
| Speed Improvments | Many speed improvments, UI Enhancments and bugf fixes. |
AttackCapture™ Updates
Automated file tagging: AttackCapture™ now tags key elements automatically, like exploits, target file paths, GitHub README references, and tools, surfacing what matters (target lists, external domains, tool usage) without digging through raw data.

UI Improvements: Number of UI updates, including a new Statistics modal for AttackCapture™ file extensions. The new Statistics tab shows counts and total sizes by file extension, giving you quick visibility into what types of files are being captured most often.
For example, .py, .txt, and .md are among the top file types collected, helping you spot trends in tooling, script usage, or dropped artifacts across campaigns.

Support for exclusions in Code Search: We've improved search behavior to reduce noise. Now, when searching for a domain or company name, results no longer include irrelevant dictionary files like the Alexa Top 1M or wordlists.

Deep Text File Analysis: One-click summaries to help you make faster sense of threat data, highlighting intent, language, function, malicious indicators, and scanning patterns.

Sub-directory Stats: Now you can see the number of subdirectories tracked in each capture, along with total file count and size. This gives you a quick sense of how deep the directory structure goes.
General Updates
SQL schemas are now better organized: We've improved the HuntSQL™ interface to make schema navigation more intuitive. Dataset selection is now grouped by category, including Malware, Certificates, HTTP, Phishing, Open Directories, SSH, and more, so you can query faster without digging through cluttered lists.
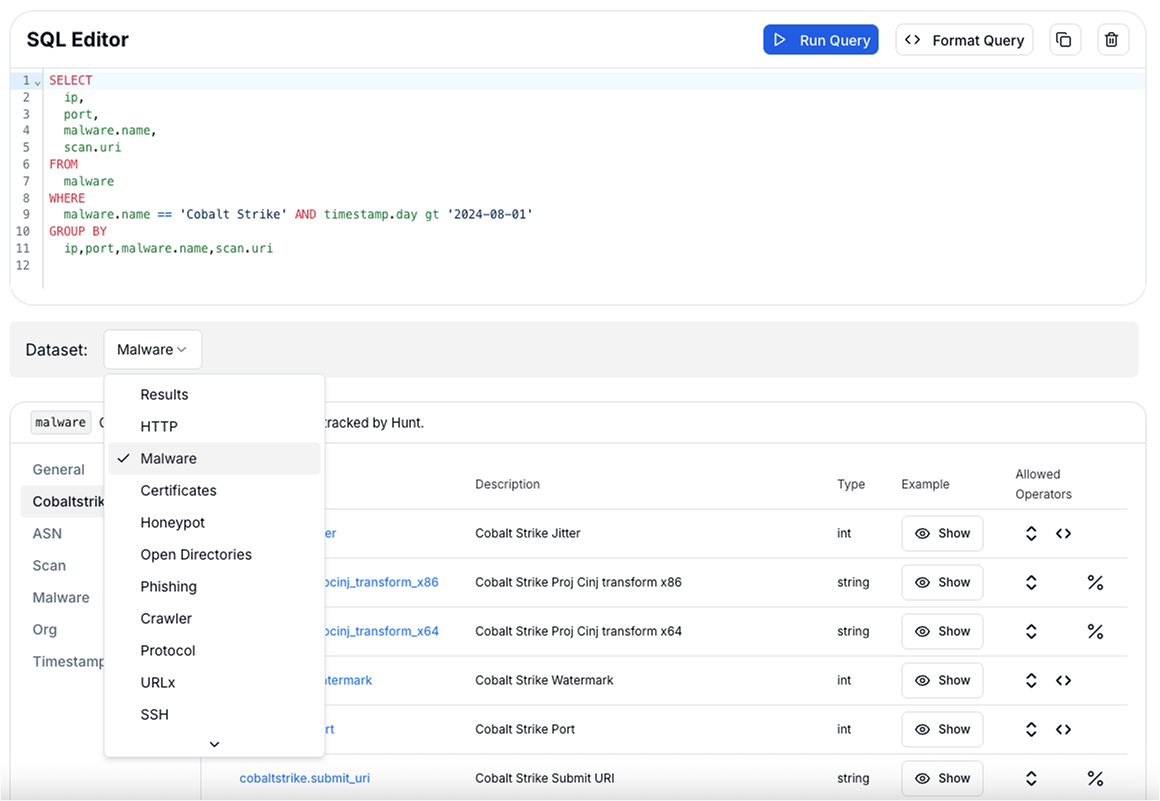
Improved Threat Actor Intelligence: We've made major upgrades to the Threat Actor data. You can now search across all known aliases, giving you a unified view of how different vendors refer to the same group.
For example, APT28 is mapped to aliases like Fancy Bear (CrowdStrike), Forest Blizzard (Microsoft), and ITG05 (IBM), so you don't miss context just because the name changed.

Every actor profile now includes:
Synonyms from across the industry
Country of origin
Linked infrastructure like IPs, hosts, and hashes
Reports and posts tied to the actor
Filters for industry targeting, type of incident, victim country, and more
You can search by adversary name, and for example, quickly pivot into ransomware groups like RansomHub, AlphVM, or Royal. These are just a few among dozens of actor profiles that surface known infrastructure, related IOCs (IPs, hosts, SHA256s), and source material in one place.

Whether you're tracking state-sponsored operations or extortion gangs, results adapt to show all relevant activity tied to the group.

Unified History View for IP Analysis: When viewing an IP, all historical data is now consolidated under a single History tab. This includes Timeline, SSL History, SSH History, Port History, and JARM History, so you can move between views without jumping around or losing track.
Each section shows relevant metadata such as ASN, company, country, and timestamps, along with detailed infrastructure insights like active ports, JARM fingerprints, certificate subjects, and SSH key reuse. This layout simplifies infrastructure investigations and speeds up threat analysis.

Expanded Platform Stats View: We now break out platform-wide stats in more detail. You can see real-time rates for key categories like parsed certificates, HTTP pages, protocol detections, JARM hashes, SSH keys, and open ports. This gives a quick snapshot of current detection activity across the entire Hunt.io infrastructure.

New Certificate Details and Pivots: We've introduced a redesigned certificate details page with clearer sections for JA4X, fingerprinting, validity periods, and issuer metadata.
You can now pivot directly from fingerprints and JA4X hashes to related infrastructure. More pivot options are on the way to help speed up investigations across SSL and certificate-based tracking.

Bulk Extractor Redesign and IP Search Upgrades: The Bulk Extractor has a new look, now live for IPs, with domain support coming soon. We've added sorting to all IP search fields and now highlight malware in red, including recent historical threats, so you can spot them without extra clicks.

Open Directory Filenames Dataset: We've added a new listing for files seen in exposed open directories that weren't downloaded by AttackCapture™. It includes filenames, full file URLs, and metadata like hostname and directory flags, useful for pivoting into related infrastructure directly from HuntSQL™.

Improved SQL Documentation: We've updated the HuntSQL™ docs with a clearer layout, better examples, and easier guidance for advanced queries like regex, time filters, and pivoting.

Open Directories Linked to Malware: You can now view exposed open directories connected to specific malware families. The following screenshot shows an example tied to RedLine Stealer, helping uncover infrastructure used for payload delivery or staging.

Cyware Integration Updated: This integration now supports our new IOC Hunter feed, so Cyware users can now pull in Hunt.io's IOC feed without extra steps.
API improvements
New fields added to the IOC Hunter feed: malware_name and description. We've added these new fields to each IOC, so you don't need to enrich them manually. This is a sample of what you'll get (notice the two fields at the bottom):
{ "value": "d9e52663715902e9ec51a7dd2fea5241c9714976e9541c02df66d1a42a3a7d2a", "ioc_type": "ioc_sha256", "threat_actor": { "id": 46, "uuid": "4f69ec6d-cb6b-42af-b8e2-920a2aa4be10", "name": "APT33", "origin": "APT33", ... ... "description": "The post discusses Shamoon malware, a wiper that targets devices on a shared network to erase operating systems. It details four waves of attacks since its emergence on August 15, 2012, primarily against Saudi organizations. Shamoon, also known as Disttrack and other aliases, is linked to the APT33 actor group and affects various Windows operating systems. The malware operates by overwriting the Master Boot Record (MBR), rendering systems inoperable. Notable victims include Saudi Aramco and Saipem, with Aramco suffering damage to 30,000 computers. The post lists several hashes associated with Shamoon's components, such as Spreader.exe and Trojan.Filerase.", "malware_name": "Shamoon" }CopyAdvanced search is faster now; we've removed the slower aggregations that were holding things up.
Bug Fixes
Session Timeout Bug Fix: We had an annoying timeout issue that affected some of our users. This has been fixed.
Protocol Mismatch on Collections: Around 400,000 collections per day were failing due to incorrect protocol handling, causing the error: "The plain HTTP request was sent to HTTPS port." This was fixed on May 19, and collections now run correctly.
As always, if you run into any issues or have ideas for what we should tackle next, reach out. We're building Hunt.io with real threat hunters in mind, and that means staying close to the people using it every day.
We're excited to announce Hunt 2.1, a new set of upgrades across Hunt.io, all built to help you cut through the noise and focus on what matters: identifying real threats faster. From smarter AI file analysis to more detailed IOC context, improved Threat Actor data, these updates are all about speeding up threat hunts and cutting out guesswork.
Here's a quick snapshot of what's new:
| Feature | What's New? |
|---|---|
| AttackCapture™ | Auto tagging of exploits, attacker configs and victim/targets, directory stats and better code search. |
| Updated Bulk Enrichment | Improved IP Enrichment to show historical C2, Attack Capture data and IOC Hunter enrichments. |
| SQL | New data sets, impoved documentation and UI. |
| Improved SSL Certificate Data | JA4X, fingerprinting, and issuer data shown cleanly, with pivot links. |
| Threat Actor Additions | Added ransomware and aliases by security vendor. |
| Integrations | Cyware integration updated with IOC Hunter. |
| Speed Improvments | Many speed improvments, UI Enhancments and bugf fixes. |
AttackCapture™ Updates
Automated file tagging: AttackCapture™ now tags key elements automatically, like exploits, target file paths, GitHub README references, and tools, surfacing what matters (target lists, external domains, tool usage) without digging through raw data.

UI Improvements: Number of UI updates, including a new Statistics modal for AttackCapture™ file extensions. The new Statistics tab shows counts and total sizes by file extension, giving you quick visibility into what types of files are being captured most often.
For example, .py, .txt, and .md are among the top file types collected, helping you spot trends in tooling, script usage, or dropped artifacts across campaigns.

Support for exclusions in Code Search: We've improved search behavior to reduce noise. Now, when searching for a domain or company name, results no longer include irrelevant dictionary files like the Alexa Top 1M or wordlists.

Deep Text File Analysis: One-click summaries to help you make faster sense of threat data, highlighting intent, language, function, malicious indicators, and scanning patterns.

Sub-directory Stats: Now you can see the number of subdirectories tracked in each capture, along with total file count and size. This gives you a quick sense of how deep the directory structure goes.
General Updates
SQL schemas are now better organized: We've improved the HuntSQL™ interface to make schema navigation more intuitive. Dataset selection is now grouped by category, including Malware, Certificates, HTTP, Phishing, Open Directories, SSH, and more, so you can query faster without digging through cluttered lists.

Improved Threat Actor Intelligence: We've made major upgrades to the Threat Actor data. You can now search across all known aliases, giving you a unified view of how different vendors refer to the same group.
For example, APT28 is mapped to aliases like Fancy Bear (CrowdStrike), Forest Blizzard (Microsoft), and ITG05 (IBM), so you don't miss context just because the name changed.

Every actor profile now includes:
Synonyms from across the industry
Country of origin
Linked infrastructure like IPs, hosts, and hashes
Reports and posts tied to the actor
Filters for industry targeting, type of incident, victim country, and more
You can search by adversary name, and for example, quickly pivot into ransomware groups like RansomHub, AlphVM, or Royal. These are just a few among dozens of actor profiles that surface known infrastructure, related IOCs (IPs, hosts, SHA256s), and source material in one place.

Whether you're tracking state-sponsored operations or extortion gangs, results adapt to show all relevant activity tied to the group.

Unified History View for IP Analysis: When viewing an IP, all historical data is now consolidated under a single History tab. This includes Timeline, SSL History, SSH History, Port History, and JARM History, so you can move between views without jumping around or losing track.
Each section shows relevant metadata such as ASN, company, country, and timestamps, along with detailed infrastructure insights like active ports, JARM fingerprints, certificate subjects, and SSH key reuse. This layout simplifies infrastructure investigations and speeds up threat analysis.

Expanded Platform Stats View: We now break out platform-wide stats in more detail. You can see real-time rates for key categories like parsed certificates, HTTP pages, protocol detections, JARM hashes, SSH keys, and open ports. This gives a quick snapshot of current detection activity across the entire Hunt.io infrastructure.

New Certificate Details and Pivots: We've introduced a redesigned certificate details page with clearer sections for JA4X, fingerprinting, validity periods, and issuer metadata.
You can now pivot directly from fingerprints and JA4X hashes to related infrastructure. More pivot options are on the way to help speed up investigations across SSL and certificate-based tracking.

Bulk Extractor Redesign and IP Search Upgrades: The Bulk Extractor has a new look, now live for IPs, with domain support coming soon. We've added sorting to all IP search fields and now highlight malware in red, including recent historical threats, so you can spot them without extra clicks.

Open Directory Filenames Dataset: We've added a new listing for files seen in exposed open directories that weren't downloaded by AttackCapture™. It includes filenames, full file URLs, and metadata like hostname and directory flags, useful for pivoting into related infrastructure directly from HuntSQL™.

Improved SQL Documentation: We've updated the HuntSQL™ docs with a clearer layout, better examples, and easier guidance for advanced queries like regex, time filters, and pivoting.

Open Directories Linked to Malware: You can now view exposed open directories connected to specific malware families. The following screenshot shows an example tied to RedLine Stealer, helping uncover infrastructure used for payload delivery or staging.

Cyware Integration Updated: This integration now supports our new IOC Hunter feed, so Cyware users can now pull in Hunt.io's IOC feed without extra steps.
API improvements
New fields added to the IOC Hunter feed: malware_name and description. We've added these new fields to each IOC, so you don't need to enrich them manually. This is a sample of what you'll get (notice the two fields at the bottom):
{ "value": "d9e52663715902e9ec51a7dd2fea5241c9714976e9541c02df66d1a42a3a7d2a", "ioc_type": "ioc_sha256", "threat_actor": { "id": 46, "uuid": "4f69ec6d-cb6b-42af-b8e2-920a2aa4be10", "name": "APT33", "origin": "APT33", ... ... "description": "The post discusses Shamoon malware, a wiper that targets devices on a shared network to erase operating systems. It details four waves of attacks since its emergence on August 15, 2012, primarily against Saudi organizations. Shamoon, also known as Disttrack and other aliases, is linked to the APT33 actor group and affects various Windows operating systems. The malware operates by overwriting the Master Boot Record (MBR), rendering systems inoperable. Notable victims include Saudi Aramco and Saipem, with Aramco suffering damage to 30,000 computers. The post lists several hashes associated with Shamoon's components, such as Spreader.exe and Trojan.Filerase.", "malware_name": "Shamoon" }CopyAdvanced search is faster now; we've removed the slower aggregations that were holding things up.
Bug Fixes
Session Timeout Bug Fix: We had an annoying timeout issue that affected some of our users. This has been fixed.
Protocol Mismatch on Collections: Around 400,000 collections per day were failing due to incorrect protocol handling, causing the error: "The plain HTTP request was sent to HTTPS port." This was fixed on May 19, and collections now run correctly.
As always, if you run into any issues or have ideas for what we should tackle next, reach out. We're building Hunt.io with real threat hunters in mind, and that means staying close to the people using it every day.
Related Posts
Related Posts
Related Posts