URLx Just Got Bigger: 10.6B URLs for Recon and Malicious Infrastructure Hunting
URLx Just Got Bigger: 10.6B URLs for Recon and Malicious Infrastructure Hunting
Published on
Mar 27, 2025
Malicious infrastructure doesn’t always hide deep in the dark web. Much of it lives in plain sight on the open internet—spread across countless URLs.
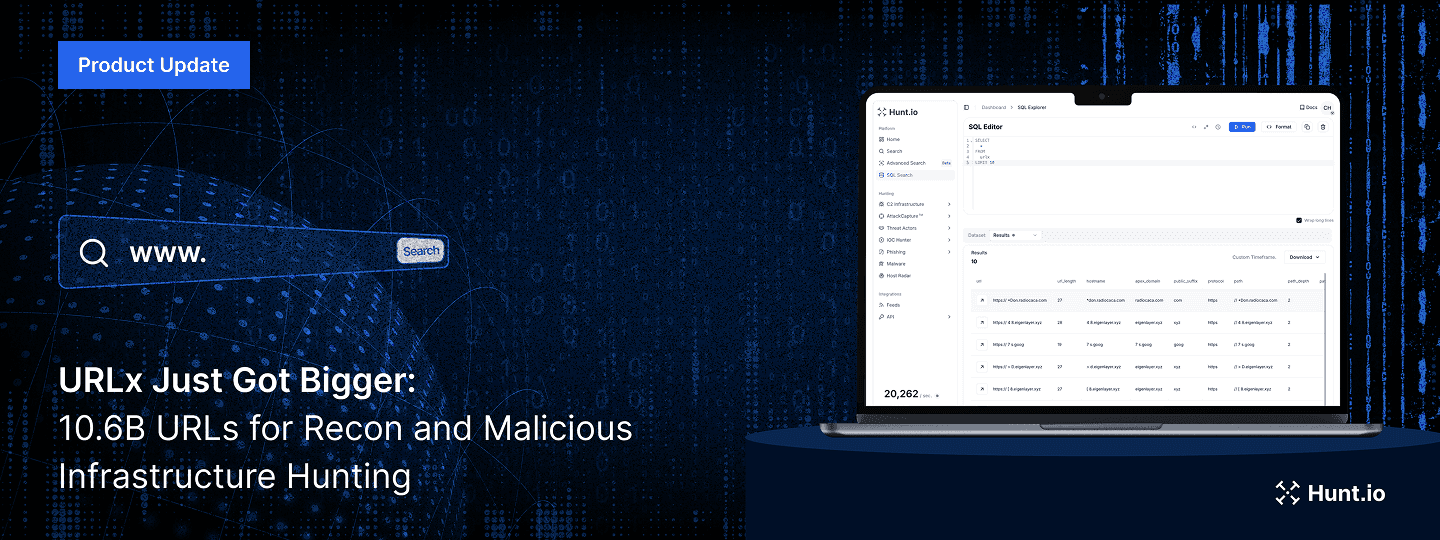
That’s why we’re excited to announce a major update to URLx, now available to all Hunt.io users.
URLx is our structured dataset of web URLs - and it's just been expanded to 10.6 billion entries, growing at a rate of 1 billion new URLs per month. More importantly, it's now easier to query, filter, and use for real threat hunting tasks.
What's New
Richer fields across SQL and Domain Search
More structured data per URL. You can now filter by domain, path, last seen, and more in both the SQL API and the URLs tab.
Massive scale
Data now covers 10.6B+ URLs from a wide range of sources - including domains frequently tied to malicious campaigns.
Why It Matters for Threat Hunting
URLx gives you the ability to quickly map the full surface of a target: exposed endpoints, forgotten assets, dev environments, and more.
But it also helps you hunt for active infrastructure being used in real-world campaigns - phishing kits, C2 panels, exploit pages - especially when combined with ProjectDiscovery's HTTPx and Hunt.io tools.

Use Case: Uncovering WordPress Sites Compromised and Leveraged by DPRK-Linked Actors
One example of URLx in action is identifying compromised WordPress sites serving paths linked to malicious activity. Since late 2024, researchers have associated a cluster of domains exposing the path
/wp-admin/js/widgets/hurryup/?rv=bear^&za=battle0 with phishing and malware delivery attributed to suspected North Korean operators.
To surface these URLs at scale, we'll first craft a query using the Hunt.io API and curl:
curl --request GET --url https://api.hunt.io/v1/sql\?query\=SELECT%20url%2C%20hostname%20FROM%20urlx%20WHERE%20path%20LIKE%20%27%25%2Fwp-admin%2Fjs%2Fwidgets%2Fhurryup%2F%25%27%20GROUP%20BY%20url%2C%20hostname --header 'accept: application/json' --header 'token: your_token_here'
CopyThe output contains a structured list of URLs and hostnames observed serving the path, aiding in identifying C2 infrastructure and expanding visibility into attacker-controlled assets.
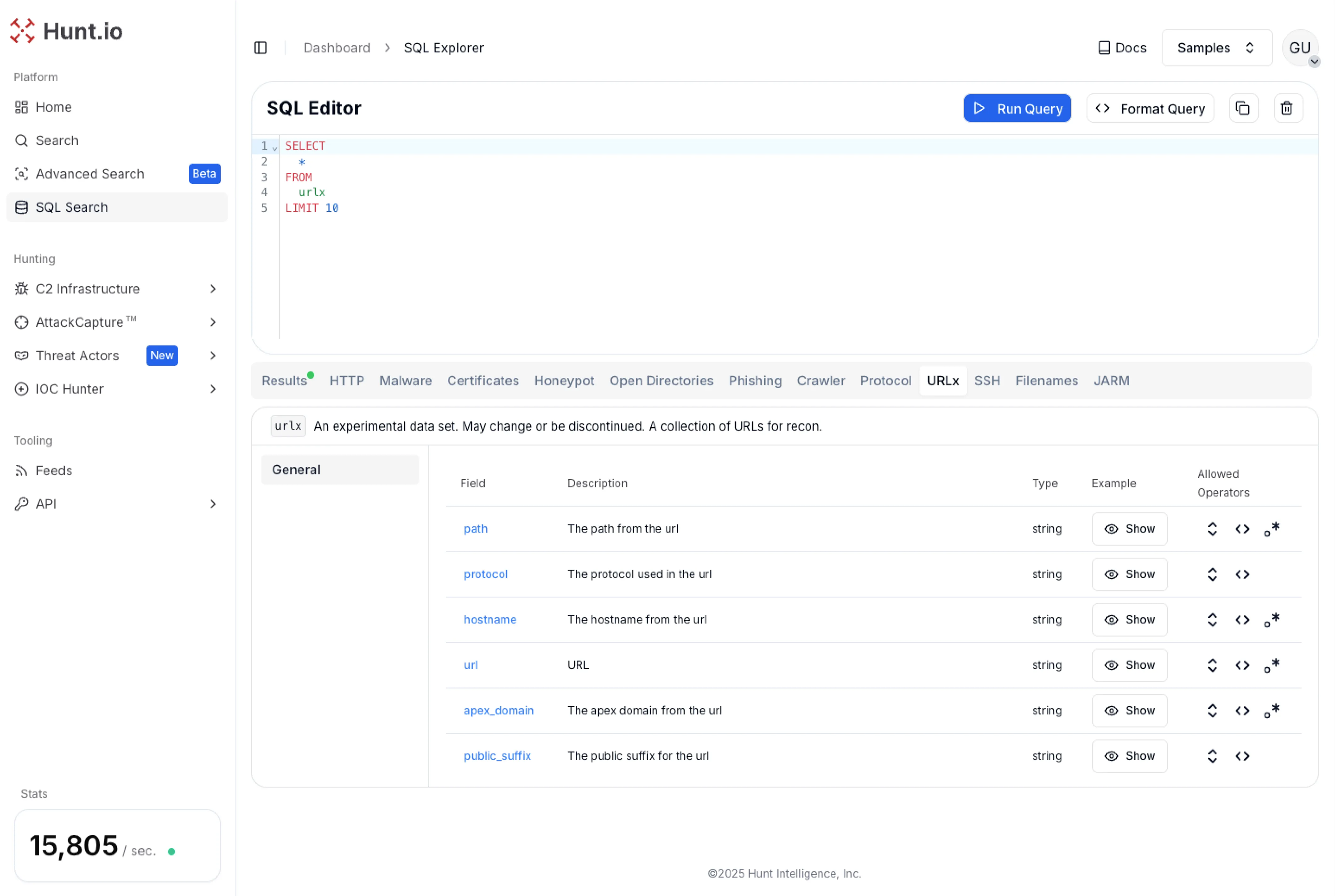
For users working within the Hunt app interface, the same results can be replicated by running the following SQL query against the URLx dataset:
SELECT url, hostname
FROM urlx
WHERE path LIKE '%/wp-admin/js/widgets/hurryup/%'
GROUP BY url, hostname
CopyAs the query above shows, we'll use the
LIKE operator to apply some simple pattern matching to a fragment of the malicious path rather than require an exact match. This approach allows defenders and researchers to validate confirmed indicators and cover new infrastructure or campaigns not publicly reported.
The SQL Search result returned several hostnames previously referenced across social media. However, one domain caught our attention-associated with a well-known lifestyle brand-that, based on our review, has not been mentioned in open sources.
Although the URL now returns a 404, we have hidden the domain in the screenshot below out of an abundance of caution for the site owners.

This is just one of many use cases for URLx. Unlike traditional web crawl data, Hunt's URLx offers structured, high-signal visibility into exposed infrastructure-built to support the workflows of defenders and researchers alike.
It's Live Now
You can use the new URLx table right now via the SQL tab or the URLs section in Hunt.io. It's a faster, deeper way to uncover exposed infrastructure and accelerate your investigations. Book a demo if you want to see it in action inside your environment.
Malicious infrastructure doesn’t always hide deep in the dark web. Much of it lives in plain sight on the open internet—spread across countless URLs.
That’s why we’re excited to announce a major update to URLx, now available to all Hunt.io users.
URLx is our structured dataset of web URLs - and it's just been expanded to 10.6 billion entries, growing at a rate of 1 billion new URLs per month. More importantly, it's now easier to query, filter, and use for real threat hunting tasks.
What's New
Richer fields across SQL and Domain Search
More structured data per URL. You can now filter by domain, path, last seen, and more in both the SQL API and the URLs tab.
Massive scale
Data now covers 10.6B+ URLs from a wide range of sources - including domains frequently tied to malicious campaigns.

Why It Matters for Threat Hunting
URLx gives you the ability to quickly map the full surface of a target: exposed endpoints, forgotten assets, dev environments, and more.
But it also helps you hunt for active infrastructure being used in real-world campaigns - phishing kits, C2 panels, exploit pages - especially when combined with ProjectDiscovery's HTTPx and Hunt.io tools.

Use Case: Uncovering WordPress Sites Compromised and Leveraged by DPRK-Linked Actors
One example of URLx in action is identifying compromised WordPress sites serving paths linked to malicious activity. Since late 2024, researchers have associated a cluster of domains exposing the path
/wp-admin/js/widgets/hurryup/?rv=bear^&za=battle0 with phishing and malware delivery attributed to suspected North Korean operators.
To surface these URLs at scale, we'll first craft a query using the Hunt.io API and curl:
curl --request GET --url https://api.hunt.io/v1/sql\?query\=SELECT%20url%2C%20hostname%20FROM%20urlx%20WHERE%20path%20LIKE%20%27%25%2Fwp-admin%2Fjs%2Fwidgets%2Fhurryup%2F%25%27%20GROUP%20BY%20url%2C%20hostname --header 'accept: application/json' --header 'token: your_token_here'
CopyThe output contains a structured list of URLs and hostnames observed serving the path, aiding in identifying C2 infrastructure and expanding visibility into attacker-controlled assets.
For users working within the Hunt app interface, the same results can be replicated by running the following SQL query against the URLx dataset:
SELECT url, hostname
FROM urlx
WHERE path LIKE '%/wp-admin/js/widgets/hurryup/%'
GROUP BY url, hostname
CopyAs the query above shows, we'll use the
LIKE operator to apply some simple pattern matching to a fragment of the malicious path rather than require an exact match. This approach allows defenders and researchers to validate confirmed indicators and cover new infrastructure or campaigns not publicly reported.
The SQL Search result returned several hostnames previously referenced across social media. However, one domain caught our attention-associated with a well-known lifestyle brand-that, based on our review, has not been mentioned in open sources.
Although the URL now returns a 404, we have hidden the domain in the screenshot below out of an abundance of caution for the site owners.

This is just one of many use cases for URLx. Unlike traditional web crawl data, Hunt's URLx offers structured, high-signal visibility into exposed infrastructure-built to support the workflows of defenders and researchers alike.
It's Live Now
You can use the new URLx table right now via the SQL tab or the URLs section in Hunt.io. It's a faster, deeper way to uncover exposed infrastructure and accelerate your investigations. Book a demo if you want to see it in action inside your environment.
Related Posts
Related Posts
Related Posts