Track APT34-Like Infrastructure Before It Strikes
Track APT34-Like Infrastructure Before It Strikes
Published on
Apr 22, 2025

The earliest signs of an operation aren't in a payload but in the infrastructure decisions made weeks or months before.
Between November 2024 and April 2025, we tracked a set of domains and servers configured to impersonate an academic organization in Iraq and several fictitious UK-based technology firms. While the infrastructure remains dormant from a payload perspective, its setup offers defenders a rare early warning opportunity.
Shared SSH keys, similarly structured websites, and decoy HTTP behavior were observed across infrastructure hosted on M247. These characteristics-particularly the use of port 8080 for fake 404 responses and the consistent reuse of a single SSH fingerprint-closely mirror tradecraft previously attributed to APT34 (OilRig).
This post details the infrastructure timeline, highlights observable behaviors defenders can hunt for today, and explains why early visibility into pre-operational staging remains critical for anticipating adversary activity.
Infrastructure Setup and Domain Behavior
In late 2024, the domain
biam-iraq[.]org was first identified resolving to infrastructure hosted by Host Sailor. The name closely mirrored that of a legitimate academic institute in Iraq. Within ten days, the domain transitioned to an M247 IP (
38.180.18[.]189), remaining for over four months-a timeline suggesting pre-operational staging.
On March 18, 2025, it moved to
38.180.140[.]30, also under M247. This server responded to HTTP requests on port
8080 with a 404 Not Found page and the title "Document".
The port was last seen on 16 April.
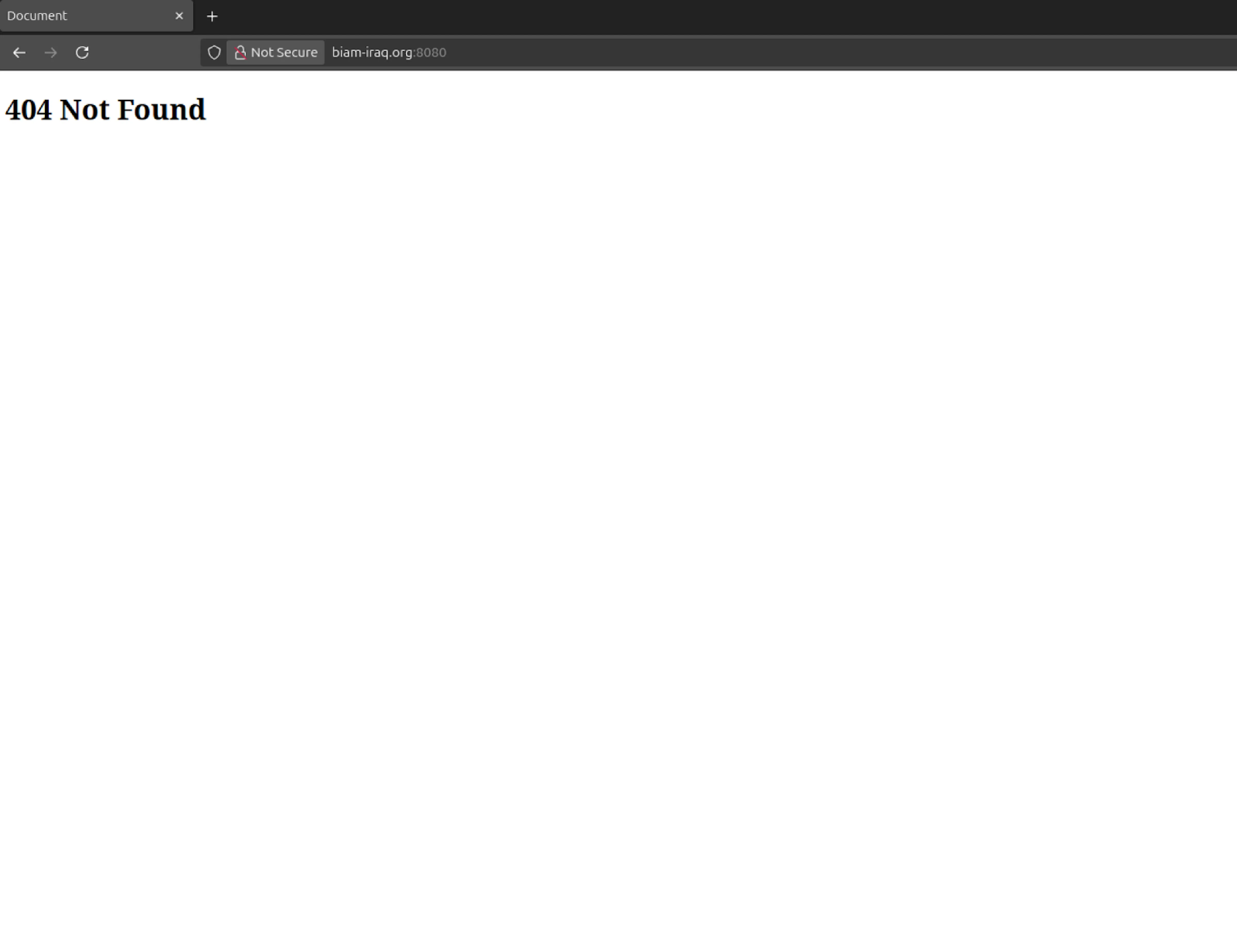 Figure 1: Port 8080 decoy response served from
Figure 1: Port 8080 decoy response served from
38.180.140.30This behavior wasn't unique to this server. A March 2025 ThreatBook report linked the same 404 "Document" pattern to APT34 infrastructure. While the page is functionally inert, its consistency across unrelated campaigns suggests the use of a preferred server template or toolkit-one that can be proactively monitored.
Passive DNS records from this period show multiple subdomains under
biam-iraq[.]org, including
mail.,
webmail.,
cpanel., and
cpcontacts. While these subdomains did not serve active content at the time of analysis, the naming conventions suggest preparation for credential collection or webmail impersonation-tactics commonly used to support phishing or initial access.
![Figure 2: Subdomains observed under biam-iraq[.]org while resolving to 38.180.140[.]30](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/4-2025/figure_2_subdomains_observed_under_biam_iraq_org_while_resolving_to_38_180_140_30_3x.webp) Figure 2: Subdomains observed under
Figure 2: Subdomains observed under
biam-iraq[.]org while resolving to
38.180.140[.]30BIAM, the British Institute for Accounting and Management, offers training programs and international certification in finance and business administration. While there's no indication the organization was directly targeted, its name and academic positioning make it a plausible fit for infrastructure intended to blend into trusted contexts.
APT34, also known as OilRig, is a suspected Iranian threat group linked to access operations against educational institutions, government agencies, energy firms, telecom providers, and NGOs. Past campaigns have featured custom infrastructure, long-term staging, and domain theming aligned to the target's sector.
The infrastructure remained hosted within M247 Europe SRL for the duration of the domain's staging activity, including both the
.189 and
.140.30 IPs. As of this writing, the final server remains reachable. Around the time of its transition to the new IP, a parallel set of domains was observed-this time using .eu TLDs and branding themselves as UK-based technology firms.
SSH Key Reuse Across Infrastructure
Shortly after
biam-iraq[.]org moved to its final IP, a unique SSH fingerprint was observed across four additional servers hosted on the same M247 network. The fingerprint,
05ce787de86117596a65fff0bab767df2846d6b7fa782b605daeff70a6332eb0, had already been seen on the earlier M247 IP,
38.180.18[.]189, where the domain had previously resolved.
All four IPs began returning the same fingerprint on March 21, 2025, with activity continuing through March 29. Each exposed an identical SSH banner:
SSH-2.0-OpenSSH_8.0. The reuse of this fingerprint across separate ASNs indicates a shared provisioning routine.
Monitoring for this fingerprint-both historically and moving forward-can help surface related infrastructure regardless of DNS resolution or active payload delivery.
![Figure 3: SSH fingerprint and overlapping IPs observed on 38.180.18[.]189](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/4-2025/figure_3_ssh_fingerprint_and_overlapping_ips_observed_on_38_180_18_189_3x.webp) Figure 3: SSH fingerprint and overlapping IPs observed on 38.180.18[.]189.
Figure 3: SSH fingerprint and overlapping IPs observed on 38.180.18[.]189.SSH key reuse becomes especially useful when tracked across time and infrastructure layers. Combined with other traits like domain structure or HTTP behavior, it can support clustering, prioritization, and early-stage detection of future assets likely configured by the same operator.
Related .eu Infrastructure and Thematic Patterns
Multiple .eu domains began resolving to
38.180.18[.]189, the same M247 server previously linked to long-term staging infrastructure. These domains include
plenoryvantyx[.]eu,
zyverantova[.]eu,
valtryventyx[.]eu,
valtorynexon[.]eu, and
axoryvexity[.]eu.
Each uses a seemingly random name with no clear links to real-world organizations or thematic references.
![Figure 4: .eu domains resolving to 38.180.18[.]189 in March 2025](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/4-2025/figure_4_eu_domains_resolving_to_38_180_18_189_in_march_2025_3x.webp) Figure 4: .eu domains resolving to 38.180.18[.]189 in March 2025
Figure 4: .eu domains resolving to 38.180.18[.]189 in March 2025All domains were registered through P.D.R. Solutions (US) LLC and pointed to regway[.]com as their nameserver. TLS certificates were issued via Let's Encrypt, using each domain as the subject common name.
When combined, these indicators-domain names, registrar, DNS infrastructure, and certificate patterns-can support the identification of additional infrastructure using similar provisioning behavior.
Fabricated Company Profiles and Public Visibility
Only one of the domains,
plenoryventyx[.]eu, returned a live webpage at the time of analysis. The page presented as a digital marketing firm called Sphere Spark, featuring generic branding language and stock imagery. The site included headings such as "Welcome to Sphere Spark," a description of its supposed marketing capabilities, and references to digital transformation strategies tailored to corporate clients.
![Figure 5: Web content hosted at plenoryventyx[.]eu in April 2025](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/4-2025/figure_5_web_content_hosted_at_plenoryventyx_eu_in_april_2025_3x.webp) Figure 5: Web content hosted at plenoryventyx[.]eu in April 2025
Figure 5: Web content hosted at plenoryventyx[.]eu in April 2025Google search results for this domain surfaced two separate site labels: Sphere Spark and BioVersa Dynamics. The latter claimed to be a science and research organization also based in England, indicating inconsistent branding across indexed subpages.
Other domains associated with the infrastructure, such as
valtorynexon[.]eu and
zyverantova[.]eu, returned search results pointing to fictional software development firms, including "ZenStack Technologies" and "Dynamic Byte Systems." All claimed to operate out of England and featured typical industry buzzwords like "customized solutions," "cutting-edge innovation," and "digital transformation," though no corporate registration records, business listings, or contact information could be found to validate their presence.
 Figure 6: Search engine indexing reveals fabricated branding for science, marketing, and software entities in the UK
Figure 6: Search engine indexing reveals fabricated branding for science, marketing, and software entities in the UK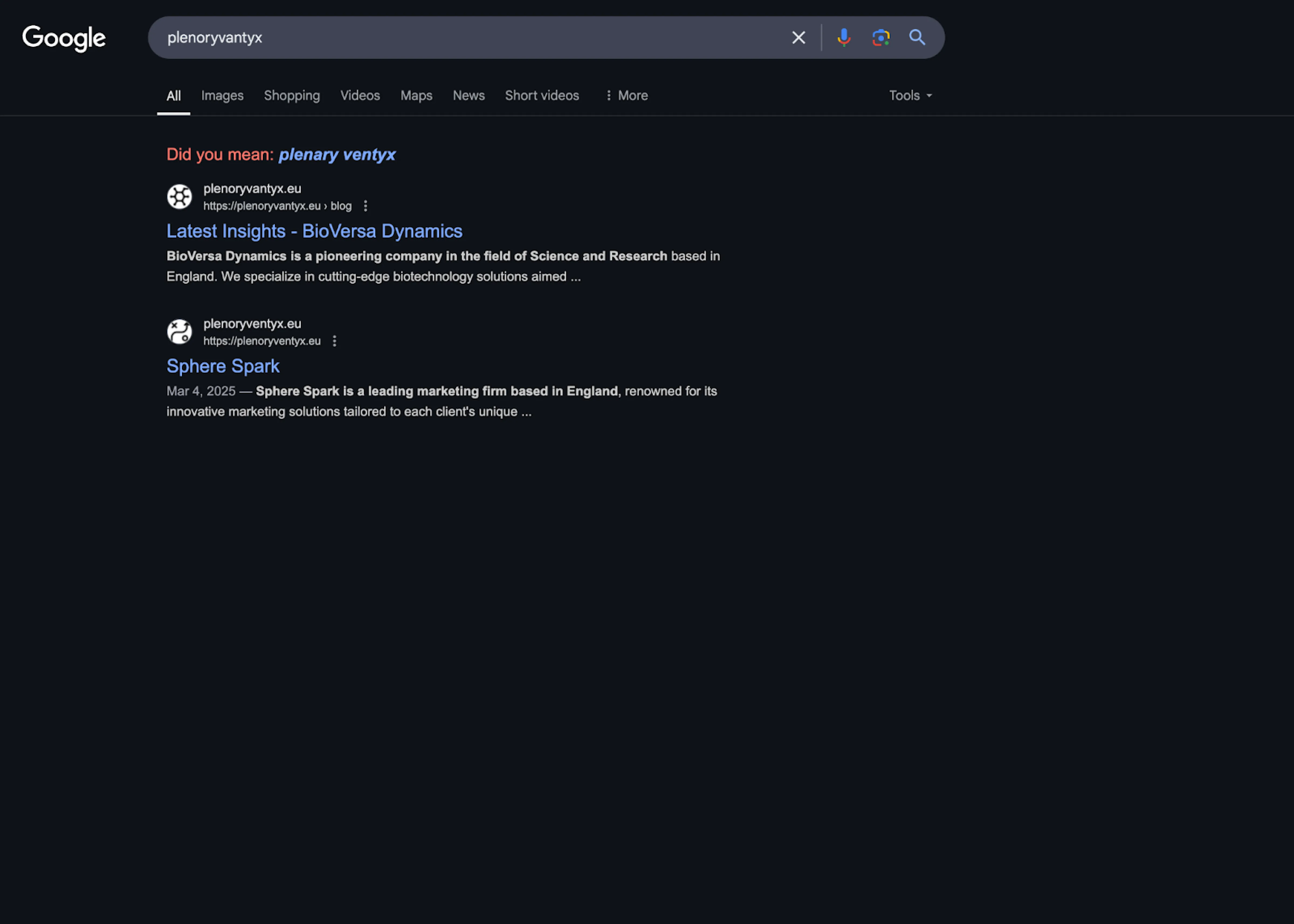 Figure 7: Search engine results for plenoryvantyx.
Figure 7: Search engine results for plenoryvantyx.Only one domain returned live web content, but across the cluster, several sites appeared in search engines with matching branding and language. Each posed as a different type of company, ranging from science and research to marketing and software development. These fronts helped give the domains an appearance of legitimacy despite their synthetic nature.
With these characteristics in mind, coherent but fabricated branding, shared SSH keys, consistent certificate patterns, and registrar choices, defenders have a useful set of indicator patterns for proactively tracking similar malicious infrastructure.
The next section outlines specific monitoring opportunities and detection strategies to surface related assets before they're activated operationally.
Detection and Monitoring Opportunities
The infrastructure outlined throughout this post presents multiple opportunities for detection and long-term monitoring. While the servers involved did not actively distribute malware at the time of analysis, several technical traits: HTTP response behavior, SSH fingerprint reuse, and naming conventions, offer defenders durable signals that can surface similar assets before they become operational.
Below are two HuntSQL™ queries that defenders can use immediately within Hunt.io to begin pivoting on these behaviors.
HTTP Title and 404 Body Pattern
The server associated with
biam-iraq[.]org responded to HTTP requests on port 8080 with a static HTML page displaying the message "404 Not Found" and the title Document. The page also included a fixed Content-Length value. While not a functional error page, the above items can be used to uncover similar command-and-control infrastructure.
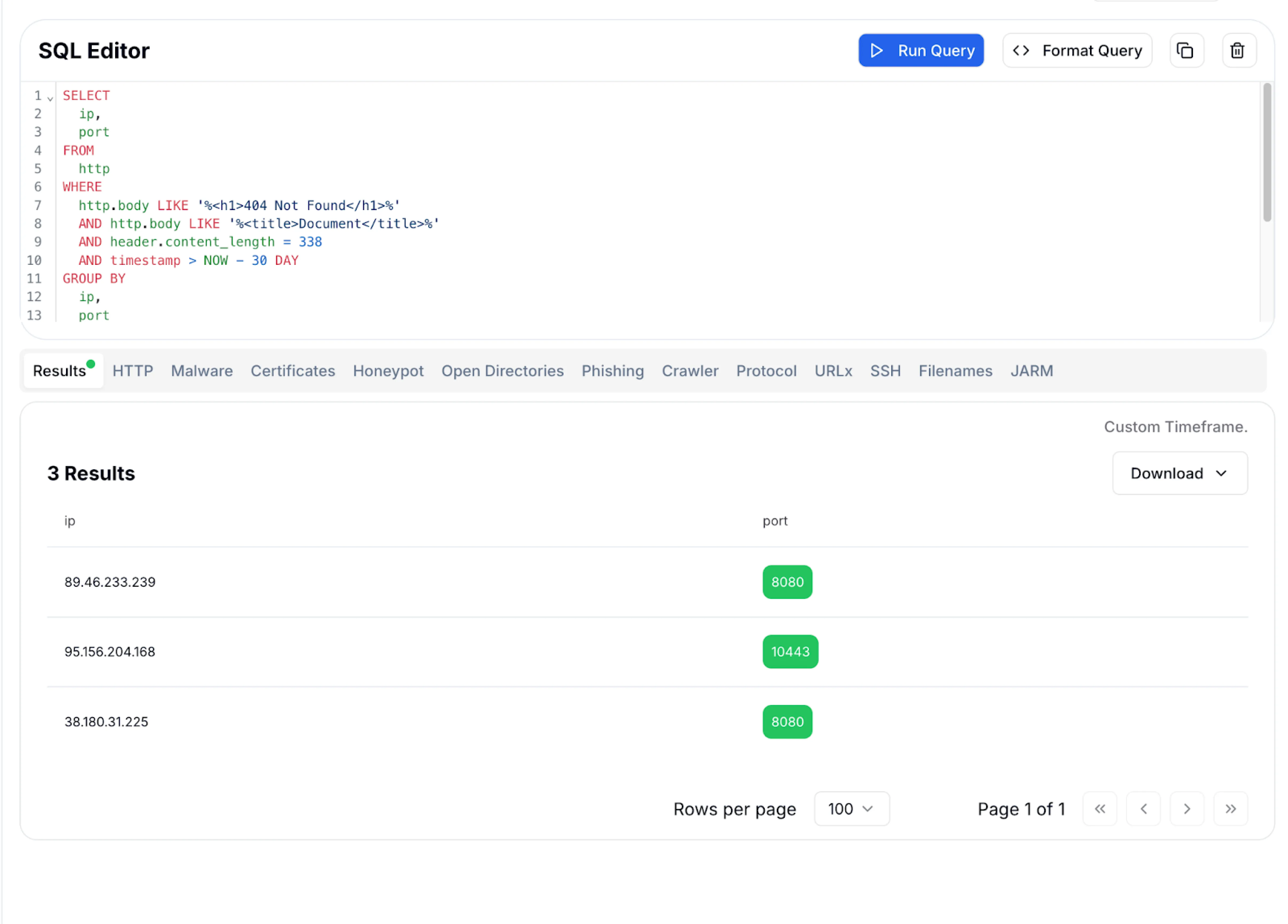 Figure 8: Hunt.io results showing historical matches for the same HTTP structure
Figure 8: Hunt.io results showing historical matches for the same HTTP structureTo search for servers presenting the same structure, the following HuntSQL™ query can be used. Updating the timestamp range will return more recent results:
SELECT ip, port, http.body
FROM http
WHERE http.title == 'Document' AND http.body LIKE '%<h1>404 Not Found</h1>%' AND header.content_length == '338'
GROUP BY ip, port, http.body
CopySSH Fingerprint Reuse Across Providers
The SSH key fingerprint
05ce787de86117596a65fff0bab767df2846d6b7fa782b605daeff70a6332eb0 was reused across five servers, all hosted on the M247 network. This behavior, often reflective of shared provisioning workflows, can be used to uncover additional infrastructure managed by the same operator.
The following HuntSQL query identifies other IPs currently exposing the same fingerprint:
SELECT ip, port
FROM ssh
WHERE rsa_sha256 == 'CE25B9D48B7F04AE2C1C3D729C10F41C4D5D2E7C260AD6D5446E3CC5E9F61281'
GROUP BY ip, port
CopyThe infrastructure tied to this activity followed a repeatable pattern. Domains were registered through the same provider, pointed to a shared nameserver, and resolved to IPs that reused a single SSH key across multiple hosting providers.
HTTP behavior on port 8080, returning a generic "404 Not Found" page with the title Document appears designed to deter further inspection and obscure underlying command-and-control activity.
Final Thoughts
The infrastructure detailed in this report reflects deliberate setup choices-reused SSH keys, consistent domain provisioning, and generic HTTP responses on nonstandard ports. These aren't one-off artifacts but part of a repeatable process. Recognizing these patterns early gives defenders a way to track infrastructure before it's operational, rather than responding after the fact.
Indicators and behaviors worth monitoring for future tracking:
SSH key fingerprint reuse across unrelated IP ranges or ASNs
Domains registered through P.D.R. Solutions (US) LLC using regway[.]com nameservers
Web servers responding on nonstandard ports (e.g., 8080) with Document as the HTML title and 404 Not Found in the body
Random-looking .eu domains with no search visibility or placeholder content mimicking tech or research firms
Together, these signals offer a practical blueprint for tracking similar infrastructure before it becomes operational.
APT34-Like Infrastructure Network Observables and Indicators of Compromise (IOCs)
| IP Address | Domain(s) | Hosting Company | Location |
|---|---|---|---|
| 38.180.140[.]30 | biam-iraq[.]org mail.biam-iraq[.]org cpanel.biam-iraq[.]org webmail.biam-iraq[.]org webdisk.biam-iraq[.]org cpcalendars.biam-iraq[.]org cpcontacts.biam-iraq[.]org | M247 Europe SRL | GB |
| 38.180.18.189 | plenoryvantyx[.]eu | M247 Europe SRL | BE |
| 38.180.18[.]18 | axoryvexity[.]eu | M247 Europe SRL | BE |
| 38.180.18[.]173 | valtorynexon[.]eu | M247 Europe SRL | BE |
| 38.180.18[.]249 | zyverantova[.]eu | M247 Europe SRL | BE |
| 38.180.18[.]253 | valtryventyx[.]eu | M247 Europe SRL | BE |
The earliest signs of an operation aren't in a payload but in the infrastructure decisions made weeks or months before.
Between November 2024 and April 2025, we tracked a set of domains and servers configured to impersonate an academic organization in Iraq and several fictitious UK-based technology firms. While the infrastructure remains dormant from a payload perspective, its setup offers defenders a rare early warning opportunity.
Shared SSH keys, similarly structured websites, and decoy HTTP behavior were observed across infrastructure hosted on M247. These characteristics-particularly the use of port 8080 for fake 404 responses and the consistent reuse of a single SSH fingerprint-closely mirror tradecraft previously attributed to APT34 (OilRig).
This post details the infrastructure timeline, highlights observable behaviors defenders can hunt for today, and explains why early visibility into pre-operational staging remains critical for anticipating adversary activity.
Infrastructure Setup and Domain Behavior
In late 2024, the domain
biam-iraq[.]org was first identified resolving to infrastructure hosted by Host Sailor. The name closely mirrored that of a legitimate academic institute in Iraq. Within ten days, the domain transitioned to an M247 IP (
38.180.18[.]189), remaining for over four months-a timeline suggesting pre-operational staging.
On March 18, 2025, it moved to
38.180.140[.]30, also under M247. This server responded to HTTP requests on port
8080 with a 404 Not Found page and the title "Document".
The port was last seen on 16 April.
 Figure 1: Port 8080 decoy response served from
Figure 1: Port 8080 decoy response served from
38.180.140.30This behavior wasn't unique to this server. A March 2025 ThreatBook report linked the same 404 "Document" pattern to APT34 infrastructure. While the page is functionally inert, its consistency across unrelated campaigns suggests the use of a preferred server template or toolkit-one that can be proactively monitored.
Passive DNS records from this period show multiple subdomains under
biam-iraq[.]org, including
mail.,
webmail.,
cpanel., and
cpcontacts. While these subdomains did not serve active content at the time of analysis, the naming conventions suggest preparation for credential collection or webmail impersonation-tactics commonly used to support phishing or initial access.
![Figure 2: Subdomains observed under biam-iraq[.]org while resolving to 38.180.140[.]30](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/4-2025/figure_2_subdomains_observed_under_biam_iraq_org_while_resolving_to_38_180_140_30_3x.webp) Figure 2: Subdomains observed under
Figure 2: Subdomains observed under
biam-iraq[.]org while resolving to
38.180.140[.]30BIAM, the British Institute for Accounting and Management, offers training programs and international certification in finance and business administration. While there's no indication the organization was directly targeted, its name and academic positioning make it a plausible fit for infrastructure intended to blend into trusted contexts.
APT34, also known as OilRig, is a suspected Iranian threat group linked to access operations against educational institutions, government agencies, energy firms, telecom providers, and NGOs. Past campaigns have featured custom infrastructure, long-term staging, and domain theming aligned to the target's sector.
The infrastructure remained hosted within M247 Europe SRL for the duration of the domain's staging activity, including both the
.189 and
.140.30 IPs. As of this writing, the final server remains reachable. Around the time of its transition to the new IP, a parallel set of domains was observed-this time using .eu TLDs and branding themselves as UK-based technology firms.
SSH Key Reuse Across Infrastructure
Shortly after
biam-iraq[.]org moved to its final IP, a unique SSH fingerprint was observed across four additional servers hosted on the same M247 network. The fingerprint,
05ce787de86117596a65fff0bab767df2846d6b7fa782b605daeff70a6332eb0, had already been seen on the earlier M247 IP,
38.180.18[.]189, where the domain had previously resolved.
All four IPs began returning the same fingerprint on March 21, 2025, with activity continuing through March 29. Each exposed an identical SSH banner:
SSH-2.0-OpenSSH_8.0. The reuse of this fingerprint across separate ASNs indicates a shared provisioning routine.
Monitoring for this fingerprint-both historically and moving forward-can help surface related infrastructure regardless of DNS resolution or active payload delivery.
![Figure 3: SSH fingerprint and overlapping IPs observed on 38.180.18[.]189](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/4-2025/figure_3_ssh_fingerprint_and_overlapping_ips_observed_on_38_180_18_189_3x.webp) Figure 3: SSH fingerprint and overlapping IPs observed on 38.180.18[.]189.
Figure 3: SSH fingerprint and overlapping IPs observed on 38.180.18[.]189.SSH key reuse becomes especially useful when tracked across time and infrastructure layers. Combined with other traits like domain structure or HTTP behavior, it can support clustering, prioritization, and early-stage detection of future assets likely configured by the same operator.
Related .eu Infrastructure and Thematic Patterns
Multiple .eu domains began resolving to
38.180.18[.]189, the same M247 server previously linked to long-term staging infrastructure. These domains include
plenoryvantyx[.]eu,
zyverantova[.]eu,
valtryventyx[.]eu,
valtorynexon[.]eu, and
axoryvexity[.]eu.
Each uses a seemingly random name with no clear links to real-world organizations or thematic references.
![Figure 4: .eu domains resolving to 38.180.18[.]189 in March 2025](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/4-2025/figure_4_eu_domains_resolving_to_38_180_18_189_in_march_2025_3x.webp) Figure 4: .eu domains resolving to 38.180.18[.]189 in March 2025
Figure 4: .eu domains resolving to 38.180.18[.]189 in March 2025All domains were registered through P.D.R. Solutions (US) LLC and pointed to regway[.]com as their nameserver. TLS certificates were issued via Let's Encrypt, using each domain as the subject common name.
When combined, these indicators-domain names, registrar, DNS infrastructure, and certificate patterns-can support the identification of additional infrastructure using similar provisioning behavior.
Fabricated Company Profiles and Public Visibility
Only one of the domains,
plenoryventyx[.]eu, returned a live webpage at the time of analysis. The page presented as a digital marketing firm called Sphere Spark, featuring generic branding language and stock imagery. The site included headings such as "Welcome to Sphere Spark," a description of its supposed marketing capabilities, and references to digital transformation strategies tailored to corporate clients.
![Figure 5: Web content hosted at plenoryventyx[.]eu in April 2025](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/4-2025/figure_5_web_content_hosted_at_plenoryventyx_eu_in_april_2025_3x.webp) Figure 5: Web content hosted at plenoryventyx[.]eu in April 2025
Figure 5: Web content hosted at plenoryventyx[.]eu in April 2025Google search results for this domain surfaced two separate site labels: Sphere Spark and BioVersa Dynamics. The latter claimed to be a science and research organization also based in England, indicating inconsistent branding across indexed subpages.
Other domains associated with the infrastructure, such as
valtorynexon[.]eu and
zyverantova[.]eu, returned search results pointing to fictional software development firms, including "ZenStack Technologies" and "Dynamic Byte Systems." All claimed to operate out of England and featured typical industry buzzwords like "customized solutions," "cutting-edge innovation," and "digital transformation," though no corporate registration records, business listings, or contact information could be found to validate their presence.
 Figure 6: Search engine indexing reveals fabricated branding for science, marketing, and software entities in the UK
Figure 6: Search engine indexing reveals fabricated branding for science, marketing, and software entities in the UK Figure 7: Search engine results for plenoryvantyx.
Figure 7: Search engine results for plenoryvantyx.Only one domain returned live web content, but across the cluster, several sites appeared in search engines with matching branding and language. Each posed as a different type of company, ranging from science and research to marketing and software development. These fronts helped give the domains an appearance of legitimacy despite their synthetic nature.
With these characteristics in mind, coherent but fabricated branding, shared SSH keys, consistent certificate patterns, and registrar choices, defenders have a useful set of indicator patterns for proactively tracking similar malicious infrastructure.
The next section outlines specific monitoring opportunities and detection strategies to surface related assets before they're activated operationally.
Detection and Monitoring Opportunities
The infrastructure outlined throughout this post presents multiple opportunities for detection and long-term monitoring. While the servers involved did not actively distribute malware at the time of analysis, several technical traits: HTTP response behavior, SSH fingerprint reuse, and naming conventions, offer defenders durable signals that can surface similar assets before they become operational.
Below are two HuntSQL™ queries that defenders can use immediately within Hunt.io to begin pivoting on these behaviors.
HTTP Title and 404 Body Pattern
The server associated with
biam-iraq[.]org responded to HTTP requests on port 8080 with a static HTML page displaying the message "404 Not Found" and the title Document. The page also included a fixed Content-Length value. While not a functional error page, the above items can be used to uncover similar command-and-control infrastructure.
 Figure 8: Hunt.io results showing historical matches for the same HTTP structure
Figure 8: Hunt.io results showing historical matches for the same HTTP structureTo search for servers presenting the same structure, the following HuntSQL™ query can be used. Updating the timestamp range will return more recent results:
SELECT ip, port, http.body
FROM http
WHERE http.title == 'Document' AND http.body LIKE '%<h1>404 Not Found</h1>%' AND header.content_length == '338'
GROUP BY ip, port, http.body
CopySSH Fingerprint Reuse Across Providers
The SSH key fingerprint
05ce787de86117596a65fff0bab767df2846d6b7fa782b605daeff70a6332eb0 was reused across five servers, all hosted on the M247 network. This behavior, often reflective of shared provisioning workflows, can be used to uncover additional infrastructure managed by the same operator.
The following HuntSQL query identifies other IPs currently exposing the same fingerprint:
SELECT ip, port
FROM ssh
WHERE rsa_sha256 == 'CE25B9D48B7F04AE2C1C3D729C10F41C4D5D2E7C260AD6D5446E3CC5E9F61281'
GROUP BY ip, port
CopyThe infrastructure tied to this activity followed a repeatable pattern. Domains were registered through the same provider, pointed to a shared nameserver, and resolved to IPs that reused a single SSH key across multiple hosting providers.
HTTP behavior on port 8080, returning a generic "404 Not Found" page with the title Document appears designed to deter further inspection and obscure underlying command-and-control activity.
Final Thoughts
The infrastructure detailed in this report reflects deliberate setup choices-reused SSH keys, consistent domain provisioning, and generic HTTP responses on nonstandard ports. These aren't one-off artifacts but part of a repeatable process. Recognizing these patterns early gives defenders a way to track infrastructure before it's operational, rather than responding after the fact.
Indicators and behaviors worth monitoring for future tracking:
SSH key fingerprint reuse across unrelated IP ranges or ASNs
Domains registered through P.D.R. Solutions (US) LLC using regway[.]com nameservers
Web servers responding on nonstandard ports (e.g., 8080) with Document as the HTML title and 404 Not Found in the body
Random-looking .eu domains with no search visibility or placeholder content mimicking tech or research firms
Together, these signals offer a practical blueprint for tracking similar infrastructure before it becomes operational.
APT34-Like Infrastructure Network Observables and Indicators of Compromise (IOCs)
| IP Address | Domain(s) | Hosting Company | Location |
|---|---|---|---|
| 38.180.140[.]30 | biam-iraq[.]org mail.biam-iraq[.]org cpanel.biam-iraq[.]org webmail.biam-iraq[.]org webdisk.biam-iraq[.]org cpcalendars.biam-iraq[.]org cpcontacts.biam-iraq[.]org | M247 Europe SRL | GB |
| 38.180.18.189 | plenoryvantyx[.]eu | M247 Europe SRL | BE |
| 38.180.18[.]18 | axoryvexity[.]eu | M247 Europe SRL | BE |
| 38.180.18[.]173 | valtorynexon[.]eu | M247 Europe SRL | BE |
| 38.180.18[.]249 | zyverantova[.]eu | M247 Europe SRL | BE |
| 38.180.18[.]253 | valtryventyx[.]eu | M247 Europe SRL | BE |
Related Posts
Related Posts
Related Posts