Unveiling the Power of Tag Cloud: Navigating the Digital Landscape with Precision
Unveiling the Power of Tag Cloud: Navigating the Digital Landscape with Precision
Published on
Feb 14, 2024


This statement may seem obvious, but cybersecurity is predominantly about establishing superiority over threat actors with as much efficacy and certainty as possible. This idea can also include aspects that evoke the need for resilience in the face of growing application complexity and its equally complex supporting infrastructure.
So when a detection mechanism comes along, revealing ways we can use it to increasingly explore and understand malware, vulnerabilities, and a salvo of additional security issues, its ultimate success remains inextricably linked to its seamless integration with existing workflows.
In keeping with this provision, we at Hunt have recently introduced Tag Cloud, an innovative visual representation that makes it easier for our users to identify patterns and relationships among various threat intelligence elements. Read on as we explore its potential place and value in the modern cyber defense arsenal, including its ability to revolutionize your hunting efforts.
What is Tag Cloud?
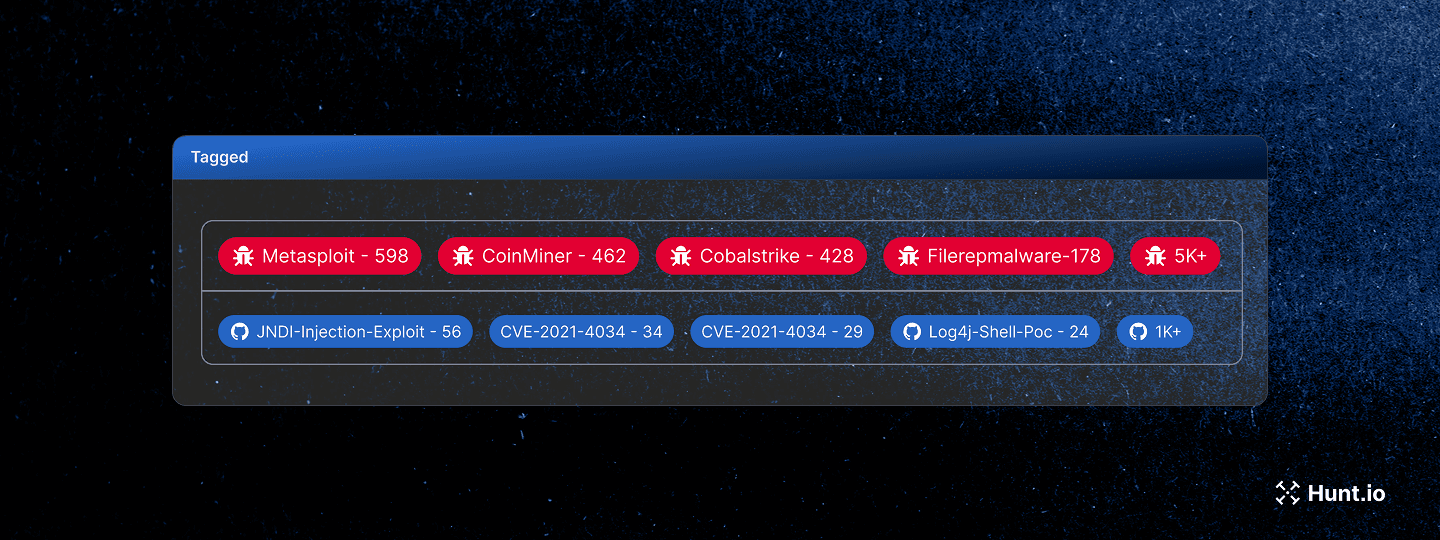
In a few words, Tag Cloud is the embodiment of labeling digital artifacts, namely exploit code, scanners, phishing kits, pentesting platforms, and even fuzzing templates, by taking aggregate counts based on malicious open directories.
The concept arises from the need to catalog potential security threats and tooling according to recurring factors within our data. This process can include everything from C2 scanning signatures to non-categorized services based on the SHA-256 of the reasons.md file or the actual exploit code.

By general definition, tag clouds are synonymous with visual simplicity and data accessibility, offering an intuitive and dynamic representation of information. The prominence of each tag reflects its significance within a dataset, providing a quick and effective way to augment critical insights at a glance. Notwithstanding, they must be readily consumable by security tools-for instance, during incident response, tag clouds can assist in quickly identifying and categorizing relevant Indicators of Compromise (IoCs).
Tag Cloud can also represent various attributes associated with threat actors. For example, certain tags may include the names or aliases of known APT (Advanced Persistent Threat) groups, specific malware families they employ, known geographic regions of operation, or industry sectors they frequently target.
Focus on the critical
How can a seemingly simple cataloging instrument make such a profound impact on cyber defense?
The solution lies in Tag Cloud's capability to expose features such as Malicious Exposed Open Directories, allowing threat hunters and other cybersecurity professionals to identify and evaluate potential risks quickly. Furthermore, by visualizing tags associated with exposed directories containing malicious content, security professionals can pinpoint vulnerable areas susceptible to exploitation.

Whether uncovering exposed sensitive data or identifying future attack vectors, Tag Cloud can help analysts visualize activity via the Exposed Shell History option-this can shed light on unauthorized access, lateral movement, or attempts to compromise critical assets. Tag Cloud's user-friendly interface can also guide you through Malware Sandbox Results, making it an invaluable resource for threat hunters beginning to navigate the intricacies of incident response.
Overall, the combination of visual simplicity and powerful functionality in Tag Cloud allows threat hunters to conceptualize and mitigate evolving cyber threats effectively. And we are constantly adding more tags!
Summing up
If there was ever a time to reinforce how we approach cyber threat hunting, that time is now, and Tag Cloud is here to guide you further along that path. After all, in this littered cat-and-mouse game called modern cybersecurity, having a clear and concise way to label threat actors' movement at the onset could be a formidable aid.
Embrace a new era of clarity, precision, and proactive threat mitigation by giving Tag Cloud a try today.
This statement may seem obvious, but cybersecurity is predominantly about establishing superiority over threat actors with as much efficacy and certainty as possible. This idea can also include aspects that evoke the need for resilience in the face of growing application complexity and its equally complex supporting infrastructure.
So when a detection mechanism comes along, revealing ways we can use it to increasingly explore and understand malware, vulnerabilities, and a salvo of additional security issues, its ultimate success remains inextricably linked to its seamless integration with existing workflows.
In keeping with this provision, we at Hunt have recently introduced Tag Cloud, an innovative visual representation that makes it easier for our users to identify patterns and relationships among various threat intelligence elements. Read on as we explore its potential place and value in the modern cyber defense arsenal, including its ability to revolutionize your hunting efforts.
What is Tag Cloud?
In a few words, Tag Cloud is the embodiment of labeling digital artifacts, namely exploit code, scanners, phishing kits, pentesting platforms, and even fuzzing templates, by taking aggregate counts based on malicious open directories.
The concept arises from the need to catalog potential security threats and tooling according to recurring factors within our data. This process can include everything from C2 scanning signatures to non-categorized services based on the SHA-256 of the reasons.md file or the actual exploit code.

By general definition, tag clouds are synonymous with visual simplicity and data accessibility, offering an intuitive and dynamic representation of information. The prominence of each tag reflects its significance within a dataset, providing a quick and effective way to augment critical insights at a glance. Notwithstanding, they must be readily consumable by security tools-for instance, during incident response, tag clouds can assist in quickly identifying and categorizing relevant Indicators of Compromise (IoCs).
Tag Cloud can also represent various attributes associated with threat actors. For example, certain tags may include the names or aliases of known APT (Advanced Persistent Threat) groups, specific malware families they employ, known geographic regions of operation, or industry sectors they frequently target.
Focus on the critical
How can a seemingly simple cataloging instrument make such a profound impact on cyber defense?
The solution lies in Tag Cloud's capability to expose features such as Malicious Exposed Open Directories, allowing threat hunters and other cybersecurity professionals to identify and evaluate potential risks quickly. Furthermore, by visualizing tags associated with exposed directories containing malicious content, security professionals can pinpoint vulnerable areas susceptible to exploitation.

Whether uncovering exposed sensitive data or identifying future attack vectors, Tag Cloud can help analysts visualize activity via the Exposed Shell History option-this can shed light on unauthorized access, lateral movement, or attempts to compromise critical assets. Tag Cloud's user-friendly interface can also guide you through Malware Sandbox Results, making it an invaluable resource for threat hunters beginning to navigate the intricacies of incident response.
Overall, the combination of visual simplicity and powerful functionality in Tag Cloud allows threat hunters to conceptualize and mitigate evolving cyber threats effectively. And we are constantly adding more tags!
Summing up
If there was ever a time to reinforce how we approach cyber threat hunting, that time is now, and Tag Cloud is here to guide you further along that path. After all, in this littered cat-and-mouse game called modern cybersecurity, having a clear and concise way to label threat actors' movement at the onset could be a formidable aid.
Embrace a new era of clarity, precision, and proactive threat mitigation by giving Tag Cloud a try today.
Related Posts
Related Posts
Related Posts
©2026 Hunt Intelligence, Inc.
©2026 Hunt Intelligence, Inc.
©2025 Hunt Intelligence, Inc.


