TTP Threat Hunting: How to Identify and Stop Cyber Threats Before They Strike
Published on Oct 23, 2025

Attackers aren't just exploiting vulnerabilities-they're following patterns, refining techniques, and adapting their methods to evade detection. The best way to stop them? Think like them.
TTP threat hunting shifts the focus from reacting to breaches to actively uncovering the tactics, techniques, and procedures attackers rely on. It's about recognizing their behaviors before they can strike, strengthening your defenses, and staying ahead of evolving threats.
A SANS survey revealed that many organizations lack a formal threat-hunting methodology. Specifically, 27.1% of organizations define their methods internally, while 45.1% operate without a documented process, highlighting the need for structured approaches in threat-hunting practices.
This guide dives into the mindset, methods, and real-world applications of TTP threat hunting, equipping you with the tools to anticipate and disrupt attacks before they cause damage.
What is TTP Threat Hunting?
TTP threat hunting is a proactive way to find cyber threats. It's about specific behaviors, attack patterns, and techniques used by threat actors. Unlike reactive methods that respond to incidents after they've happened, threat hunting is about preventing attacks before they can cause significant damage. It's done by human analysts who use their expertise to find undiscovered threats.
Most threat hunters know that understanding Tactics, Techniques, and Procedures (TTPs) is key to finding incidents, understanding threat actors, and contextualizing attack patterns.

One key advantage of TTP threat hunting is its ability to detect threats that traditional security tools might overlook. While automated detection focuses on known signatures and anomalies, threat hunters analyze behavioral patterns that indicate emerging threats.
For example, a company might not detect a low-and-slow attack spreading laterally, but by recognizing an adversary's TTPs, a hunter can spot early warning signs before damage is done.
Unlike traditional security methods that rely on alerts from intrusion detection systems, TTP threat hunting takes a more investigative approach. By proactively searching through security data, analysts can uncover hidden threats that haven't triggered alerts yet.
Since TTP threat hunting is proactive, it's not just about finding threats but about improving your organization's security overall. Thanks to understanding how attackers work and what they do, threat hunters can develop better defenses, reduce dwell time, and protect sensitive data and systems.
According to the 2024 Mandiant M-Trends Report, the average dwell time (the period an attacker remains undetected in a system) was 10 days, a significant decrease from 21 and 16 days in the previous years.
With a clear understanding of TTP threat hunting and its core elements (tactics, techniques, and procedures), we now turn our attention to how these concepts are applied in real-world threat hunting or cybercrime investigations. In the next section, we’ll explore practical methodologies that put this theory into action.
TTP Key Components
To master TTP threat hunting you need to understand the three key components of TTP: Tactics, Techniques, and Procedures. These are the blocks that make up an attacker's strategy, so threat hunters can make sense of incidents, find threat actors, and decode attack patterns in cyber.
TTPs provide a blueprint for how cyberattacks unfold. A single attack rarely relies on just one method - adversaries layer tactics, techniques, and procedures in a sequence to maximize impact. It is about specific behaviors and attack patterns used by threat actors so it's a key part of proactive cyber threat hunting. By looking into these components, threat hunters can defend against new and advanced threats.

Tactics
In cyber, tactics refer to the high-level plans and strategic methods used by cybercriminals to achieve their goals. These adversary tactics are the overall objectives that attackers want to achieve, such as initial access, persistence, or data exfiltration. Understanding these tactics is key for threat hunters as it gives you a framework to anticipate and counter the threats.
Techniques
Techniques are the various methods used by adversaries to execute their attack tactics. These intermediate methods give you a more detailed view of how attackers compromise systems and evade detection. Common techniques include malware deployment, phishing, and brute force attacks, each a threat to your network. By looking at these techniques, you can respond to threats more effectively.
Procedures
Procedures are the detailed steps used by cybercriminals. These sequences of actions help them achieve their goals. These procedures outline the actions taken to exploit vulnerabilities and ensure the attack is executed consistently. By understanding these procedures, you can anticipate the attacker's next move and develop countermeasures.
Proactive Defense: Why TTP Threat Hunting Matters
TTP threat hunting is a game-changer because it helps detect threats that automated threat hunting tools might miss. Unlike reactive security methods that wait for alerts, TTP-based hunting identifies adversary behavior before an attack escalates. This approach is particularly effective against advanced persistent threats (APTs)-stealthy attackers who infiltrate networks and linger undetected for months.
APTs often rely on techniques like living-off-the-land (LOTL) attacks, where they use legitimate system tools to blend in. Since these tactics don't trigger traditional security alerts, organizations that depend solely on automated defenses are often left vulnerable. By analyzing behavioral indicators and mapping them to known TTPs, security teams can spot subtle anomalies that indicate an attack is in progress.
In our previous research into Flax Typhoon, we showcased how TTPs from the Microsoft report on this issue gave us a way to identify additional Cobalt Strike Cat infrastructure that was not previously reported on.
Threat hunting also significantly reduces dwell time - the period between an initial compromise and detection. The longer an attacker stays inside a network, the more time they have to escalate privileges, move laterally, and exfiltrate data.
Whether it's stopping ransomware attacks in finance or protecting patient data in healthcare, the ability to anticipate and disrupt attacker tactics is what separates resilient security teams from those constantly playing catch-up.
TTP Threat Hunting Methodologies
Building on our understanding of TTP threat hunting, this section breaks down the practical methods used to uncover hidden threats. From hypothesis-driven techniques to advanced analytics, each approach is designed to turn theory into a tangible strategy for detecting and stopping cyber attacks.
Human expertise is key to effective detection and hunting. Threat hunters need to know enterprise technologies, security tooling, and attacker methodologies. By using analytics and research-based approaches, threat hunters can collect granular system events data to detect threats better.
Effective threat hunting is a blend of technology and intuition. While automated tools provide valuable data, it's human expertise that connects the dots.
Experienced threat hunters develop a deep understanding of attacker behaviors, allowing them to recognize subtle signs of compromise that machines might miss. This expertise is especially crucial in cases where adversaries use advanced evasion techniques to bypass traditional security controls.

Hypothesis Driven
The hypothesis-driven approach involves forming hypotheses based on the hunter's expertise and understanding of industry attack patterns. Threat hunters create models of possible attack vectors and scenarios and then test against collected data to validate threats.
Threat hunting isn't just about finding threats-it's about learning from them. Every investigation provides valuable intelligence that can be fed back into security tools, refining detection rules and improving future threat identification. Organizations that threat hunting as an iterative process, rather than a one-time activity, continuously strengthen their defenses against evolving threats.
This method uses empirical evidence and is used by the most advanced threat-hunting teams.
IOC and IOA Based
Indicators of Compromise (IOCs) and Indicators of Attack (IOAs) are digital evidence of a breach. They come into play after a cyber incident. DFIR analysts use digital artifacts left behind by a breach and correlate them with known IOCs and IOAs to find hidden attacks or ongoing malicious activity.
Using tactical threat intelligence and combining multiple log sources improves threat assessment and reduces false positives.
Advanced Analytics, Machine Learning, and Threat Detection
Advanced analytics and machine learning help to analyze large amounts of data to find anomalies that indicate threats. These technologies define anomalies as hunting leads that human analysts investigate to find stealthy security threats.
Cyber Threat Hunting vs. TTP Hunting
So what is the difference between Cyber Threat Hunting and TTP Hunting? While both aim to detect and mitigate threats, they differ in focus and methodology.
Cyber Threat Hunting is a proactive approach that involves searching for hidden threats within a network before they cause harm. This process is broad, focusing on identifying anomalies, indicators of compromise (IOCs), and potential breaches using tools like SIEM systems, threat intelligence feeds, and behavioral analysis.
TTP Hunting, on the other hand, narrows the scope by focusing on the specific behaviors and methods attackers use. Instead of looking for known signatures or anomalies, TTP hunting investigates patterns aligned with frameworks like MITRE ATT&CK to detect how adversaries operate. This allows security teams to anticipate future moves and build defenses tailored to specific threat actor behaviors.
TTP Threat Hunting Steps
TTP threat hunting is a process that consists of three steps: Trigger the Hunt, Investigate and Resolve, and Report. Each step is important in finding, analyzing, and mitigating threats.
Trigger the hunt is to identify unusual system behavior or new threat intelligence that requires further investigation. Investigation is data collection, analysis, and validation of threats.
Finally, resolve is remediation, sharing intelligence, and reporting to improve security.

Remember, every step in this process is driven by the methodologies we just discussed, ensuring that our investigations are rooted in a deep understanding of TTP components and tailored strategies.
Step 1: Trigger the Hunt
Common triggers to start a threat hunt are anomalies detected by security tools and new threat intelligence. Unusual activity detected by advanced detection tools requires further investigation by threat hunters.
Hypotheses about new threats can also be a trigger for proactive threat hunting.
Step 2: Investigate
During the investigation phase threat hunters want to know if the activity is benign or to get a complete picture of malicious activity. EDR (Endpoint Detection and Response) is often used to analyze data and find threats. A constantly updated threat intelligence lifecycle is key to threat hunting to eliminate false positives and validate threats.
Step 3: Resolve and Report
In the resolve phase intelligence is shared with relevant teams for response and mitigation. Sharing findings improves overall security and eliminates vulnerabilities.
The purpose of DFIR in cybersecurity is to improve cybersecurity to reduce future attack surfaces.
Now that we’ve covered the methodologies and outlined the step-by-step process of threat hunting, it’s time to introduce the essential tools that make it all possible. The next section will show how SIEM, EDR, and threat intelligence platforms work together to bridge the gap between strategy and real-time defense
Tools and Technologies for TTP Threat Hunting
TTP threat hunting requires various tools and technologies that enable threat hunters to analyze data, detect anomalies, and respond to threats. Integrating these security tools improves the threat-hunting process.
Collecting data from multiple sources allows hunters to filter out benign activity and focus on finding advanced threats. By using TTP-based threat-hunting techniques organizations can correlate logs, traces, and alerts from multiple security tools to find complex attack patterns.
Integrating multiple security tools into a cohesive hunting strategy is key. Security Information and Event Management (SIEM) solutions provide visibility across an organization's infrastructure, while Endpoint Detection and Response (EDR) tools offer granular insights into system activity.
When combined with threat hunting platforms, threat intelligence platforms, and machine learning analytics, these tools create a powerful ecosystem for detecting and mitigating threats in real-time.
Some of the tools and technologies are EDR solutions and SIEM systems for data collection and analysis. Threat intelligence platforms aggregate data from multiple sources to provide context for TTP analysis.
These tools and technologies are key to building a threat-hunting program that can find and mitigate cyber threats.
EDR and SIEM
Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM) are key to threat hunting. Next-gen SIEM like Securonix provides proactive threat detection and response. Traditional log management solutions lack analytics which hinders threat detection.
EDR solutions collect data from endpoints and help threat hunters find and respond to advanced threats more efficiently.
Threat Hunting Platforms
Threat-hunting platforms provide tools and frameworks that help security teams proactively search for threats in their networks. These platforms often integrate data analytics, threat intelligence, and automation to streamline the detection and investigation process. They enhance visibility into network activity, making it easier to spot anomalies and potential threats.
Hunt.io gives security teams the edge they need to stay ahead of evolving threats. By combining real-time intelligence, high-fidelity scanning, and IOC enrichment, it helps analysts cut through the noise and focus on what matters-identifying and stopping malicious infrastructure before it becomes a problem. With AI-driven detection and intuitive workflows, teams can move faster, pivot investigations with ease, and uncover hidden connections that might otherwise go unnoticed.

Built for security teams who need accuracy and speed, Hunt.io simplifies the hunt with active C2 tracking, bulk enrichment, and JA4+ fingerprinting to expose threats in real-time. Whether it's mapping adversary infrastructure, digging deeper into indicators, or leveraging open-source hunting signatures, Hunt.io makes threat hunting more efficient, giving teams the visibility and automation they need to take a proactive stance against cyber threats.
Threat Intelligence
Threat intelligence platforms aggregate data about threats from multiple sources and enrich the context for TTP analysis. These platforms provide valuable insights that add to TTP analysis by bringing in diverse threat data. Enriched security telemetry provides visibility and context for investigation and helps security teams find and respond to threats better.
Using threat intelligence platforms helps organizations stay ahead of emerging threats and improve overall security.
Read more about the intersection of Threat Hunting and Threat Intelligence in our article: Threat Hunting vs. Threat Intelligence: What's the Difference?
AI and Machine
AI and machine learning are key to threat hunting by improving detection. These technologies analyze large data to find unusual patterns that may be threats. By integrating AI and machine learning in threat hunting, organizations can detect and respond to advanced threats. This enables more accurate and faster anomaly detection and reduces false positives and overall security.
Hunt.io leverages advanced large language models (LLMs) and machine learning capabilities through its IOC Hunter feature. IOC Hunter automates the process of identifying, correlating, and analyzing indicators of compromise (IOCs) across vast datasets. This integration enhances the accuracy of threat detection, allowing security teams to quickly uncover complex attack patterns while significantly reducing false positives.
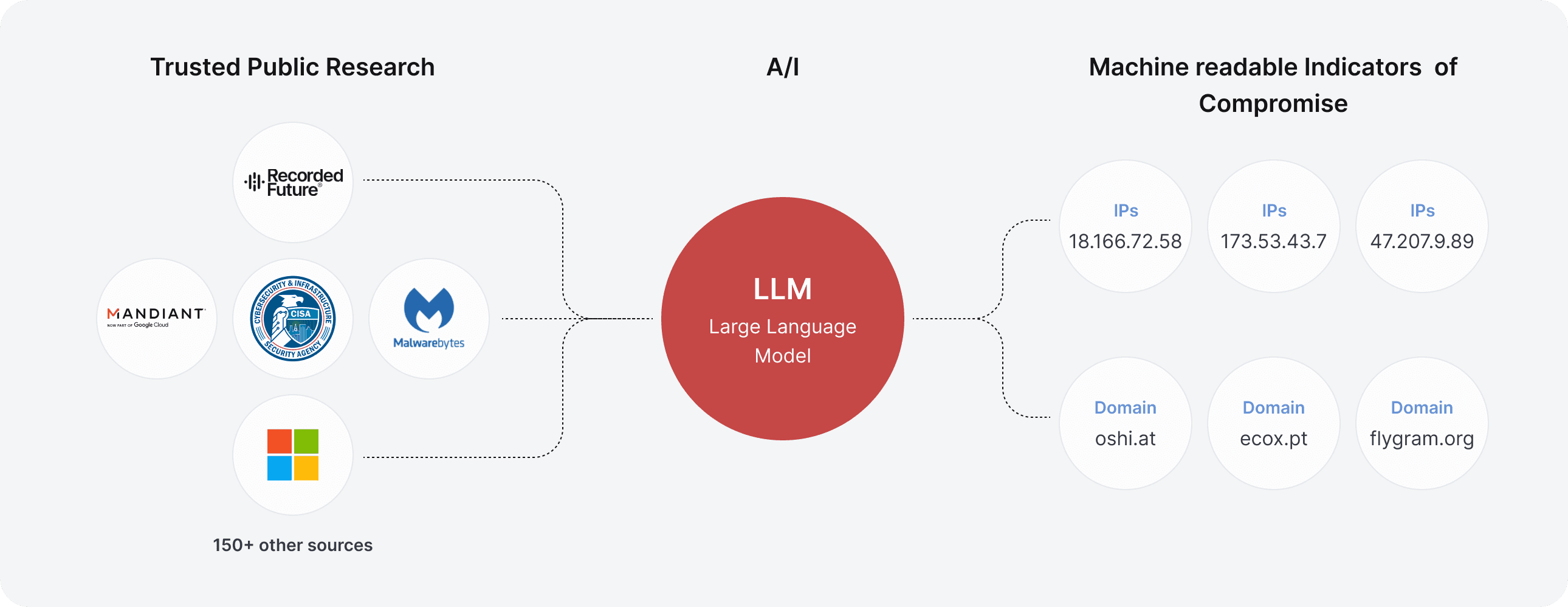
TTP Threat Hunting in the Real-World
Threat hunting examples based on real-world TTPs demonstrate its effectiveness across industries and highlight the need for adaptive security. The impact of TTP threat hunting is evident in major cybersecurity incidents.
The SolarWinds Supply Chain Attack
For example, during the SolarWinds supply chain attack, security teams that actively hunted for unusual authentication behaviors were able to detect and contain the threat before widespread damage occurred. This is why organizations need a proactive approach, not just to detect known threats, but to uncover the unknown.
Detecting SmokeLoader Malware in Open Directories
In a recent case titled: "SmokeLoader Malware Found in Open Directories Targeting Ukraine's Auto & Banking Industries", our researchers found cybercriminals hosting SmokeLoader malware in publicly available directories. These directories contained malicious files and malicious documents for Ukraine's automotive and banking sectors. By looking into these directories, the researchers learned how the attackers prepared and spread the malware. This is a great example of TTP threat hunting where security professionals anticipate and look for threats by studying known attacker behaviors and patterns as per MITRE ATT&CK framework.
Proactive Detection of Credential Dumping via MITRE ATT&CK Framework
A security team noticed suspicious activity on a vital server. By consulting the MITRE ATT&CK framework, they recognized the behavior as matching the "OS Credential Dumping" technique (Technique ID: T1003), a method attackers use to extract login credentials. This proactive approach allowed them to identify and neutralize the threat before it escalated.
These case studies help to see how different sectors use TTP threat hunting to protect sensitive data and mitigate cyber threats.
FAQs
What is TTP threat hunting?
TTP threat hunting is the analysis of tactics, techniques, and procedures used by cyber attackers to find and counter threats proactively. This helps the organization to stay ahead of malicious activities.
Why is TTP threat hunting important?
TTP threat hunting is important to find and mitigate advanced cyber threats which improves detection and overall security posture. This is part of good cybersecurity management.
What are the methods of TTP threat hunting?
Methods in TTP threat hunting include a hypothesis-driven approach, IOC/IOA-based investigations, and advanced analytics with machine learning for proactive detection. These methods improve the speed and accuracy of threat detection.
What tools are needed for TTP threat hunting?
For TTP threat hunting you need to use Endpoint Detection and Response (EDR) solutions, Security Information and Event Management (SIEM) systems, threat intelligence platforms, and AI/ML technologies. These tools allow for full detection and analysis of threats.
How do small teams implement TTP threat hunting?
Even without dedicated threat-hunting teams, smaller organizations can start by leveraging existing security tools more effectively. By setting up basic hypothesis-driven hunts using SIEM and EDR data, security analysts can look for anomalies and refine detection over time. Partnering with external threat intelligence providers can also help smaller teams stay ahead of emerging TTPs.
Final thoughts
Throughout this guide, we’ve linked the theory behind TTP threat hunting with practical methods, clear operational steps, and powerful technological tools. This integrated approach not only explains what TTP threat hunting is but also shows how to effectively implement it to stay ahead of cyber threats.
Attackers are always evolving, the only way to stay ahead is to evolve faster. TTP threat hunting isn't just another security measure-it's a mindset shift: the more you anticipate, the less you react.
Start refining your threat-hunting process today, and turn attacker tactics into your biggest advantage. Discover how Hunt.io's threat-hunting features can strengthen your organization's security. Book your demo today.
Attackers aren't just exploiting vulnerabilities-they're following patterns, refining techniques, and adapting their methods to evade detection. The best way to stop them? Think like them.
TTP threat hunting shifts the focus from reacting to breaches to actively uncovering the tactics, techniques, and procedures attackers rely on. It's about recognizing their behaviors before they can strike, strengthening your defenses, and staying ahead of evolving threats.
A SANS survey revealed that many organizations lack a formal threat-hunting methodology. Specifically, 27.1% of organizations define their methods internally, while 45.1% operate without a documented process, highlighting the need for structured approaches in threat-hunting practices.
This guide dives into the mindset, methods, and real-world applications of TTP threat hunting, equipping you with the tools to anticipate and disrupt attacks before they cause damage.
What is TTP Threat Hunting?
TTP threat hunting is a proactive way to find cyber threats. It's about specific behaviors, attack patterns, and techniques used by threat actors. Unlike reactive methods that respond to incidents after they've happened, threat hunting is about preventing attacks before they can cause significant damage. It's done by human analysts who use their expertise to find undiscovered threats.
Most threat hunters know that understanding Tactics, Techniques, and Procedures (TTPs) is key to finding incidents, understanding threat actors, and contextualizing attack patterns.

One key advantage of TTP threat hunting is its ability to detect threats that traditional security tools might overlook. While automated detection focuses on known signatures and anomalies, threat hunters analyze behavioral patterns that indicate emerging threats.
For example, a company might not detect a low-and-slow attack spreading laterally, but by recognizing an adversary's TTPs, a hunter can spot early warning signs before damage is done.
Unlike traditional security methods that rely on alerts from intrusion detection systems, TTP threat hunting takes a more investigative approach. By proactively searching through security data, analysts can uncover hidden threats that haven't triggered alerts yet.
Since TTP threat hunting is proactive, it's not just about finding threats but about improving your organization's security overall. Thanks to understanding how attackers work and what they do, threat hunters can develop better defenses, reduce dwell time, and protect sensitive data and systems.
According to the 2024 Mandiant M-Trends Report, the average dwell time (the period an attacker remains undetected in a system) was 10 days, a significant decrease from 21 and 16 days in the previous years.
With a clear understanding of TTP threat hunting and its core elements (tactics, techniques, and procedures), we now turn our attention to how these concepts are applied in real-world threat hunting or cybercrime investigations. In the next section, we’ll explore practical methodologies that put this theory into action.
TTP Key Components
To master TTP threat hunting you need to understand the three key components of TTP: Tactics, Techniques, and Procedures. These are the blocks that make up an attacker's strategy, so threat hunters can make sense of incidents, find threat actors, and decode attack patterns in cyber.
TTPs provide a blueprint for how cyberattacks unfold. A single attack rarely relies on just one method - adversaries layer tactics, techniques, and procedures in a sequence to maximize impact. It is about specific behaviors and attack patterns used by threat actors so it's a key part of proactive cyber threat hunting. By looking into these components, threat hunters can defend against new and advanced threats.

Tactics
In cyber, tactics refer to the high-level plans and strategic methods used by cybercriminals to achieve their goals. These adversary tactics are the overall objectives that attackers want to achieve, such as initial access, persistence, or data exfiltration. Understanding these tactics is key for threat hunters as it gives you a framework to anticipate and counter the threats.
Techniques
Techniques are the various methods used by adversaries to execute their attack tactics. These intermediate methods give you a more detailed view of how attackers compromise systems and evade detection. Common techniques include malware deployment, phishing, and brute force attacks, each a threat to your network. By looking at these techniques, you can respond to threats more effectively.
Procedures
Procedures are the detailed steps used by cybercriminals. These sequences of actions help them achieve their goals. These procedures outline the actions taken to exploit vulnerabilities and ensure the attack is executed consistently. By understanding these procedures, you can anticipate the attacker's next move and develop countermeasures.
Proactive Defense: Why TTP Threat Hunting Matters
TTP threat hunting is a game-changer because it helps detect threats that automated threat hunting tools might miss. Unlike reactive security methods that wait for alerts, TTP-based hunting identifies adversary behavior before an attack escalates. This approach is particularly effective against advanced persistent threats (APTs)-stealthy attackers who infiltrate networks and linger undetected for months.
APTs often rely on techniques like living-off-the-land (LOTL) attacks, where they use legitimate system tools to blend in. Since these tactics don't trigger traditional security alerts, organizations that depend solely on automated defenses are often left vulnerable. By analyzing behavioral indicators and mapping them to known TTPs, security teams can spot subtle anomalies that indicate an attack is in progress.
In our previous research into Flax Typhoon, we showcased how TTPs from the Microsoft report on this issue gave us a way to identify additional Cobalt Strike Cat infrastructure that was not previously reported on.
Threat hunting also significantly reduces dwell time - the period between an initial compromise and detection. The longer an attacker stays inside a network, the more time they have to escalate privileges, move laterally, and exfiltrate data.
Whether it's stopping ransomware attacks in finance or protecting patient data in healthcare, the ability to anticipate and disrupt attacker tactics is what separates resilient security teams from those constantly playing catch-up.
TTP Threat Hunting Methodologies
Building on our understanding of TTP threat hunting, this section breaks down the practical methods used to uncover hidden threats. From hypothesis-driven techniques to advanced analytics, each approach is designed to turn theory into a tangible strategy for detecting and stopping cyber attacks.
Human expertise is key to effective detection and hunting. Threat hunters need to know enterprise technologies, security tooling, and attacker methodologies. By using analytics and research-based approaches, threat hunters can collect granular system events data to detect threats better.
Effective threat hunting is a blend of technology and intuition. While automated tools provide valuable data, it's human expertise that connects the dots.
Experienced threat hunters develop a deep understanding of attacker behaviors, allowing them to recognize subtle signs of compromise that machines might miss. This expertise is especially crucial in cases where adversaries use advanced evasion techniques to bypass traditional security controls.

Hypothesis Driven
The hypothesis-driven approach involves forming hypotheses based on the hunter's expertise and understanding of industry attack patterns. Threat hunters create models of possible attack vectors and scenarios and then test against collected data to validate threats.
Threat hunting isn't just about finding threats-it's about learning from them. Every investigation provides valuable intelligence that can be fed back into security tools, refining detection rules and improving future threat identification. Organizations that threat hunting as an iterative process, rather than a one-time activity, continuously strengthen their defenses against evolving threats.
This method uses empirical evidence and is used by the most advanced threat-hunting teams.
IOC and IOA Based
Indicators of Compromise (IOCs) and Indicators of Attack (IOAs) are digital evidence of a breach. They come into play after a cyber incident. DFIR analysts use digital artifacts left behind by a breach and correlate them with known IOCs and IOAs to find hidden attacks or ongoing malicious activity.
Using tactical threat intelligence and combining multiple log sources improves threat assessment and reduces false positives.
Advanced Analytics, Machine Learning, and Threat Detection
Advanced analytics and machine learning help to analyze large amounts of data to find anomalies that indicate threats. These technologies define anomalies as hunting leads that human analysts investigate to find stealthy security threats.
Cyber Threat Hunting vs. TTP Hunting
So what is the difference between Cyber Threat Hunting and TTP Hunting? While both aim to detect and mitigate threats, they differ in focus and methodology.
Cyber Threat Hunting is a proactive approach that involves searching for hidden threats within a network before they cause harm. This process is broad, focusing on identifying anomalies, indicators of compromise (IOCs), and potential breaches using tools like SIEM systems, threat intelligence feeds, and behavioral analysis.
TTP Hunting, on the other hand, narrows the scope by focusing on the specific behaviors and methods attackers use. Instead of looking for known signatures or anomalies, TTP hunting investigates patterns aligned with frameworks like MITRE ATT&CK to detect how adversaries operate. This allows security teams to anticipate future moves and build defenses tailored to specific threat actor behaviors.
TTP Threat Hunting Steps
TTP threat hunting is a process that consists of three steps: Trigger the Hunt, Investigate and Resolve, and Report. Each step is important in finding, analyzing, and mitigating threats.
Trigger the hunt is to identify unusual system behavior or new threat intelligence that requires further investigation. Investigation is data collection, analysis, and validation of threats.
Finally, resolve is remediation, sharing intelligence, and reporting to improve security.

Remember, every step in this process is driven by the methodologies we just discussed, ensuring that our investigations are rooted in a deep understanding of TTP components and tailored strategies.
Step 1: Trigger the Hunt
Common triggers to start a threat hunt are anomalies detected by security tools and new threat intelligence. Unusual activity detected by advanced detection tools requires further investigation by threat hunters.
Hypotheses about new threats can also be a trigger for proactive threat hunting.
Step 2: Investigate
During the investigation phase threat hunters want to know if the activity is benign or to get a complete picture of malicious activity. EDR (Endpoint Detection and Response) is often used to analyze data and find threats. A constantly updated threat intelligence lifecycle is key to threat hunting to eliminate false positives and validate threats.
Step 3: Resolve and Report
In the resolve phase intelligence is shared with relevant teams for response and mitigation. Sharing findings improves overall security and eliminates vulnerabilities.
The purpose of DFIR in cybersecurity is to improve cybersecurity to reduce future attack surfaces.
Now that we’ve covered the methodologies and outlined the step-by-step process of threat hunting, it’s time to introduce the essential tools that make it all possible. The next section will show how SIEM, EDR, and threat intelligence platforms work together to bridge the gap between strategy and real-time defense
Tools and Technologies for TTP Threat Hunting
TTP threat hunting requires various tools and technologies that enable threat hunters to analyze data, detect anomalies, and respond to threats. Integrating these security tools improves the threat-hunting process.
Collecting data from multiple sources allows hunters to filter out benign activity and focus on finding advanced threats. By using TTP-based threat-hunting techniques organizations can correlate logs, traces, and alerts from multiple security tools to find complex attack patterns.
Integrating multiple security tools into a cohesive hunting strategy is key. Security Information and Event Management (SIEM) solutions provide visibility across an organization's infrastructure, while Endpoint Detection and Response (EDR) tools offer granular insights into system activity.
When combined with threat hunting platforms, threat intelligence platforms, and machine learning analytics, these tools create a powerful ecosystem for detecting and mitigating threats in real-time.
Some of the tools and technologies are EDR solutions and SIEM systems for data collection and analysis. Threat intelligence platforms aggregate data from multiple sources to provide context for TTP analysis.
These tools and technologies are key to building a threat-hunting program that can find and mitigate cyber threats.
EDR and SIEM
Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM) are key to threat hunting. Next-gen SIEM like Securonix provides proactive threat detection and response. Traditional log management solutions lack analytics which hinders threat detection.
EDR solutions collect data from endpoints and help threat hunters find and respond to advanced threats more efficiently.
Threat Hunting Platforms
Threat-hunting platforms provide tools and frameworks that help security teams proactively search for threats in their networks. These platforms often integrate data analytics, threat intelligence, and automation to streamline the detection and investigation process. They enhance visibility into network activity, making it easier to spot anomalies and potential threats.
Hunt.io gives security teams the edge they need to stay ahead of evolving threats. By combining real-time intelligence, high-fidelity scanning, and IOC enrichment, it helps analysts cut through the noise and focus on what matters-identifying and stopping malicious infrastructure before it becomes a problem. With AI-driven detection and intuitive workflows, teams can move faster, pivot investigations with ease, and uncover hidden connections that might otherwise go unnoticed.

Built for security teams who need accuracy and speed, Hunt.io simplifies the hunt with active C2 tracking, bulk enrichment, and JA4+ fingerprinting to expose threats in real-time. Whether it's mapping adversary infrastructure, digging deeper into indicators, or leveraging open-source hunting signatures, Hunt.io makes threat hunting more efficient, giving teams the visibility and automation they need to take a proactive stance against cyber threats.
Threat Intelligence
Threat intelligence platforms aggregate data about threats from multiple sources and enrich the context for TTP analysis. These platforms provide valuable insights that add to TTP analysis by bringing in diverse threat data. Enriched security telemetry provides visibility and context for investigation and helps security teams find and respond to threats better.
Using threat intelligence platforms helps organizations stay ahead of emerging threats and improve overall security.
Read more about the intersection of Threat Hunting and Threat Intelligence in our article: Threat Hunting vs. Threat Intelligence: What's the Difference?
AI and Machine
AI and machine learning are key to threat hunting by improving detection. These technologies analyze large data to find unusual patterns that may be threats. By integrating AI and machine learning in threat hunting, organizations can detect and respond to advanced threats. This enables more accurate and faster anomaly detection and reduces false positives and overall security.
Hunt.io leverages advanced large language models (LLMs) and machine learning capabilities through its IOC Hunter feature. IOC Hunter automates the process of identifying, correlating, and analyzing indicators of compromise (IOCs) across vast datasets. This integration enhances the accuracy of threat detection, allowing security teams to quickly uncover complex attack patterns while significantly reducing false positives.

TTP Threat Hunting in the Real-World
Threat hunting examples based on real-world TTPs demonstrate its effectiveness across industries and highlight the need for adaptive security. The impact of TTP threat hunting is evident in major cybersecurity incidents.
The SolarWinds Supply Chain Attack
For example, during the SolarWinds supply chain attack, security teams that actively hunted for unusual authentication behaviors were able to detect and contain the threat before widespread damage occurred. This is why organizations need a proactive approach, not just to detect known threats, but to uncover the unknown.
Detecting SmokeLoader Malware in Open Directories
In a recent case titled: "SmokeLoader Malware Found in Open Directories Targeting Ukraine's Auto & Banking Industries", our researchers found cybercriminals hosting SmokeLoader malware in publicly available directories. These directories contained malicious files and malicious documents for Ukraine's automotive and banking sectors. By looking into these directories, the researchers learned how the attackers prepared and spread the malware. This is a great example of TTP threat hunting where security professionals anticipate and look for threats by studying known attacker behaviors and patterns as per MITRE ATT&CK framework.
Proactive Detection of Credential Dumping via MITRE ATT&CK Framework
A security team noticed suspicious activity on a vital server. By consulting the MITRE ATT&CK framework, they recognized the behavior as matching the "OS Credential Dumping" technique (Technique ID: T1003), a method attackers use to extract login credentials. This proactive approach allowed them to identify and neutralize the threat before it escalated.
These case studies help to see how different sectors use TTP threat hunting to protect sensitive data and mitigate cyber threats.
FAQs
What is TTP threat hunting?
TTP threat hunting is the analysis of tactics, techniques, and procedures used by cyber attackers to find and counter threats proactively. This helps the organization to stay ahead of malicious activities.
Why is TTP threat hunting important?
TTP threat hunting is important to find and mitigate advanced cyber threats which improves detection and overall security posture. This is part of good cybersecurity management.
What are the methods of TTP threat hunting?
Methods in TTP threat hunting include a hypothesis-driven approach, IOC/IOA-based investigations, and advanced analytics with machine learning for proactive detection. These methods improve the speed and accuracy of threat detection.
What tools are needed for TTP threat hunting?
For TTP threat hunting you need to use Endpoint Detection and Response (EDR) solutions, Security Information and Event Management (SIEM) systems, threat intelligence platforms, and AI/ML technologies. These tools allow for full detection and analysis of threats.
How do small teams implement TTP threat hunting?
Even without dedicated threat-hunting teams, smaller organizations can start by leveraging existing security tools more effectively. By setting up basic hypothesis-driven hunts using SIEM and EDR data, security analysts can look for anomalies and refine detection over time. Partnering with external threat intelligence providers can also help smaller teams stay ahead of emerging TTPs.
Final thoughts
Throughout this guide, we’ve linked the theory behind TTP threat hunting with practical methods, clear operational steps, and powerful technological tools. This integrated approach not only explains what TTP threat hunting is but also shows how to effectively implement it to stay ahead of cyber threats.
Attackers are always evolving, the only way to stay ahead is to evolve faster. TTP threat hunting isn't just another security measure-it's a mindset shift: the more you anticipate, the less you react.
Start refining your threat-hunting process today, and turn attacker tactics into your biggest advantage. Discover how Hunt.io's threat-hunting features can strengthen your organization's security. Book your demo today.
Related Posts
Related Posts
Related Posts
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.





