Practical AWS Threat Hunting: Exposing C2s, Phishing Kits, and Open Directories with Hunt.io
Practical AWS Threat Hunting: Exposing C2s, Phishing Kits, and Open Directories with Hunt.io
Published on Oct 23, 2025

Amazon Web Services (AWS) powers much of the modern internet. Enterprises host critical workloads on AWS, startups build rapidly there, and governments trust it with sensitive systems. That same trust draws attackers.
Recently, researchers uncovered a campaign using AWS Lambda URLs as command-and-control infrastructure against government agencies, and another campaign where compromised AWS access keys were used to abuse Amazon SES for large-scale phishing. These cases highlight that AWS security is not just about protecting your own AWS account but also about understanding how adversaries exploit AWS services.
Attackers routinely spin up short-lived servers for C2, stage malware payloads in open buckets, and host phishing pages that imitate major brands.
To defend effectively, teams need visibility into more than just their own AWS environment. They need insights from external threat intelligence that expose malicious use of cloud environments. That is where Hunt.io's Host Radar comes in.
To understand how this works in practice, let's take a closer look at Host Radar itself.
What is Host Radar?
Host Radar is a Hunt.io feature that continuously scans the internet to identify malicious infrastructure at scale. It helps threat hunting teams track abused hosting providers, map adversary use of AWS services, and connect single indicators to larger campaigns.
For threat hunters, this means every suspicious IP, domain, or IOC from logs becomes the start of a pivot. By tying AWS activity to related infrastructure, Host Radar supports both threat detection and proactive response.
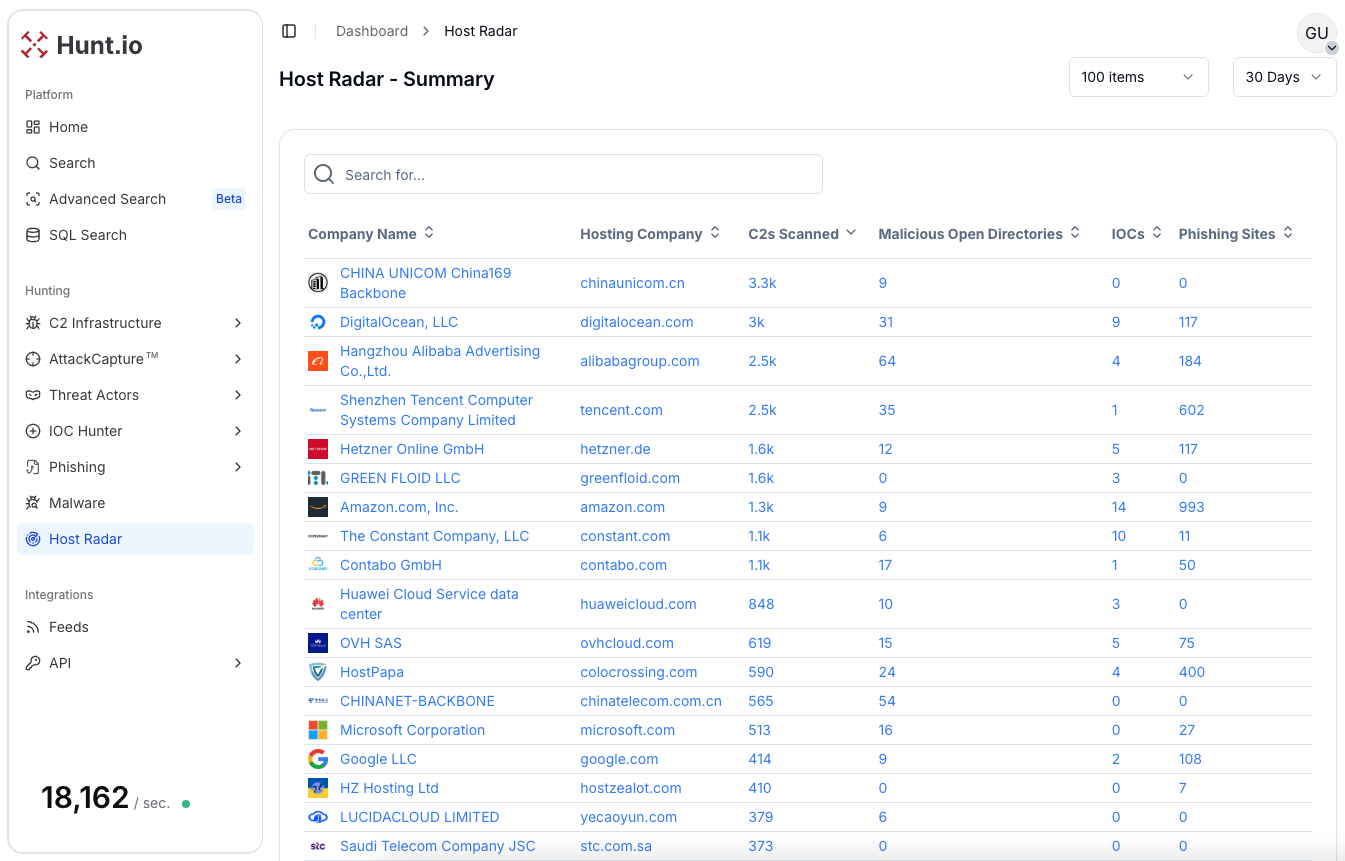
That foundation becomes more tangible when we look at the latest AWS-specific data Hunt.io has uncovered.
Host Radar Data: AWS in Focus
The latest dataset shows AWS is a hotspot for adversary operations. In just the last 30 days, we recorded:
1.3k active C2 servers hosted on AWS
9 malicious open directories staging attacker tools and payloads
14 fresh IOCs connected to AWS threat campaigns
993 phishing sites abusing AWS services
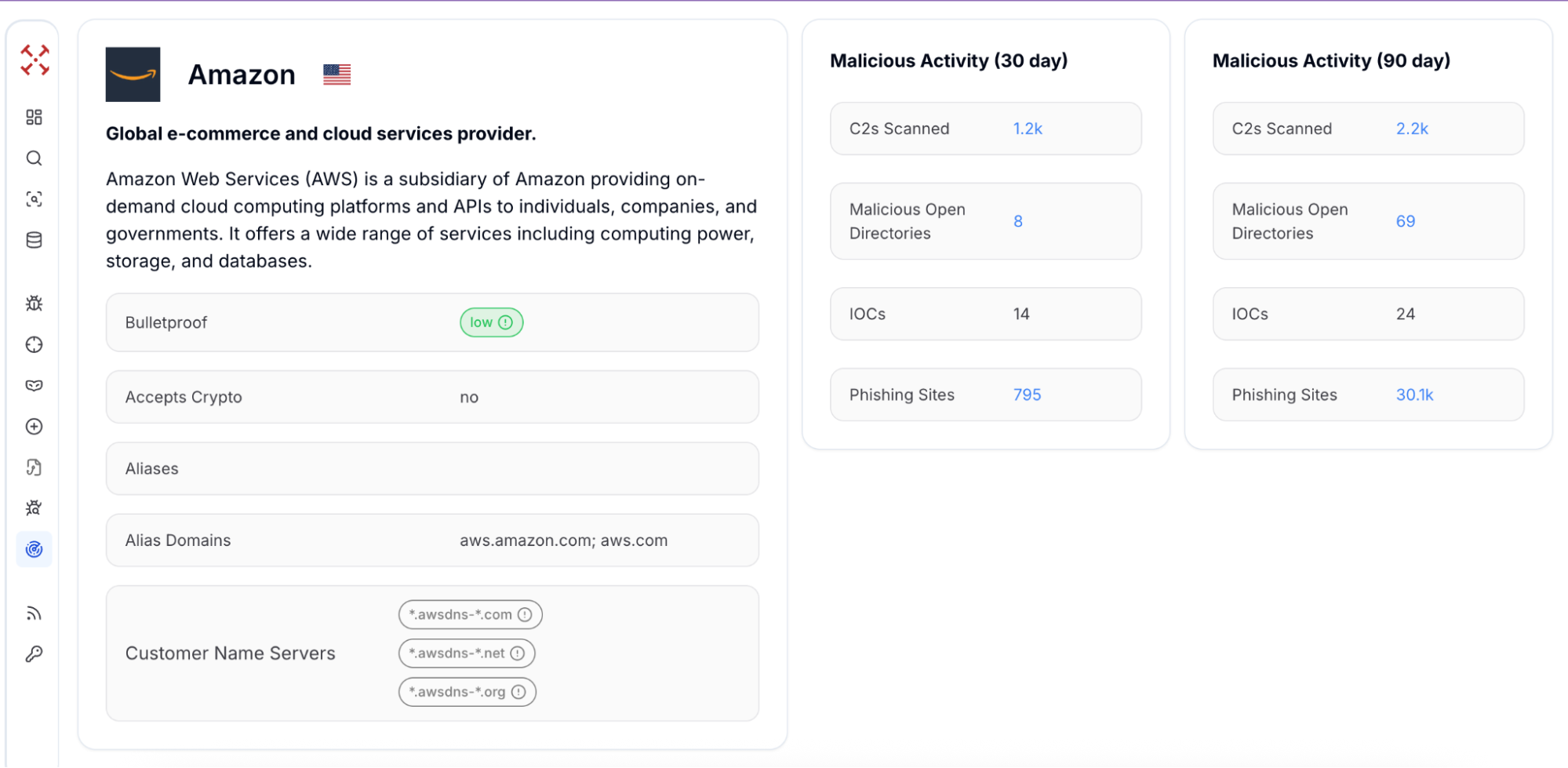
Every one of these findings can be pivoted on. For example, an IP from VPC Flow Logs can be expanded into related domains, certificates, and ports. A phishing site can be pivoted into a cluster of similar AWS-based domains. This workflow provides hunters with a real-world view of how adversaries utilize cloud infrastructure.
Numbers alone aren't enough, the value comes from turning this data into actionable workflows.
Actionable AWS Threat Hunting Workflows with Hunt.io
Enriching VPC Flow Logs for Threat Detection
When attackers spin up short-lived EC2 instances inside AWS, they often blend in with legitimate traffic. SOC analysts relying only on raw logs can miss the early signs of command and control communication.
VPC Flow Logs are one of the most valuable data sources for AWS threat hunting, but on their own, they don't provide enough context to separate benign traffic from adversary infrastructure.
Example Workflow Scenario:
AWS Signal: A SOC analyst sees suspicious outbound traffic in VPC Flow Logs.
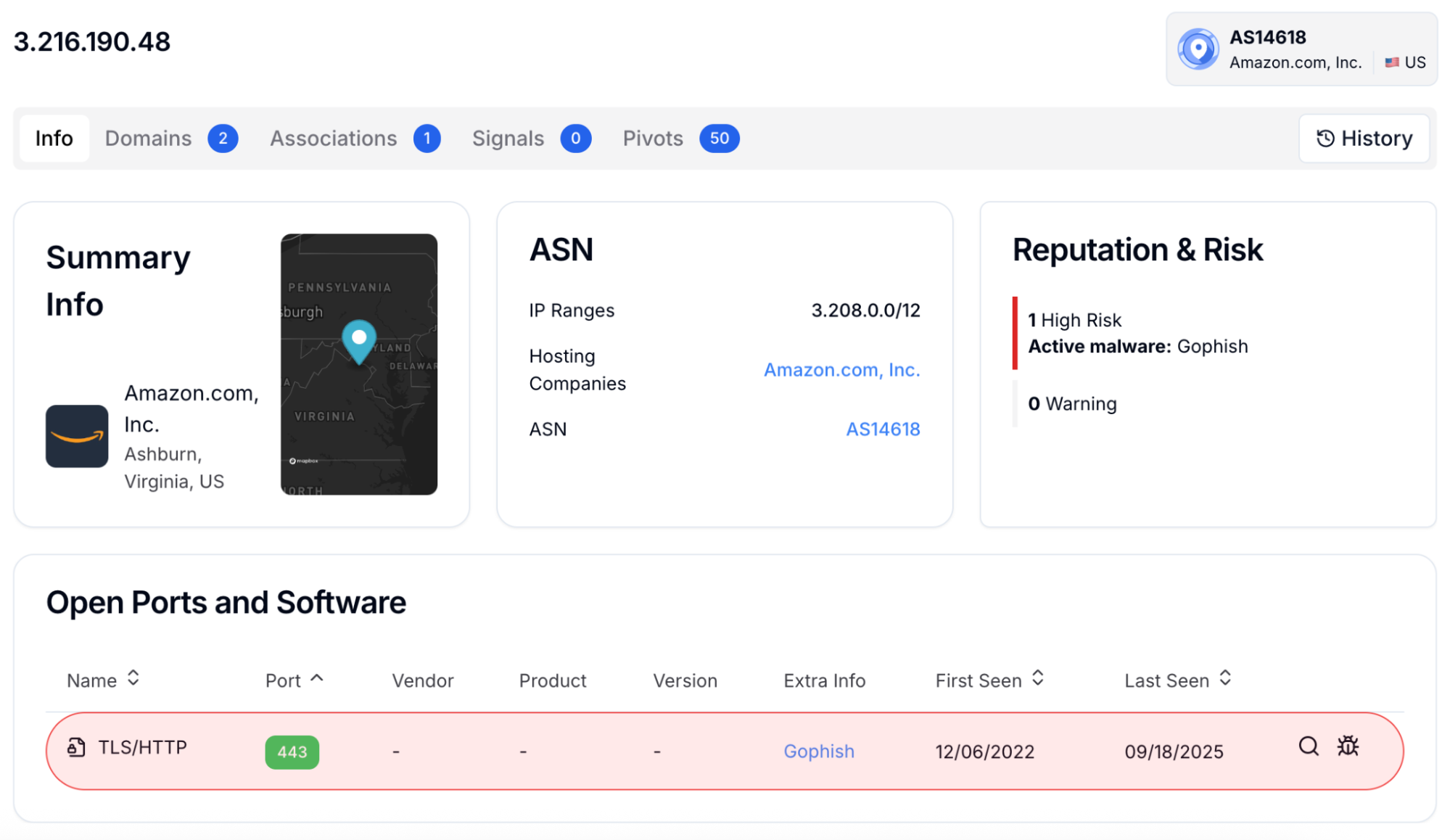
Hunt.io Pivot: The IP is enriched in Hunt.io and linked to one of the 1.3k C2 servers hosted in AWS: pivoting surfaces related domains, malware families, and even attacker TTPs.
Outcome: The team turns one event into a campaign map, enhancing threat detection rules within their SIEM.
Flow Logs are just one angle. Another common entry point for attackers is malicious open directories hosted in AWS.
Investigating Malicious Open Directories
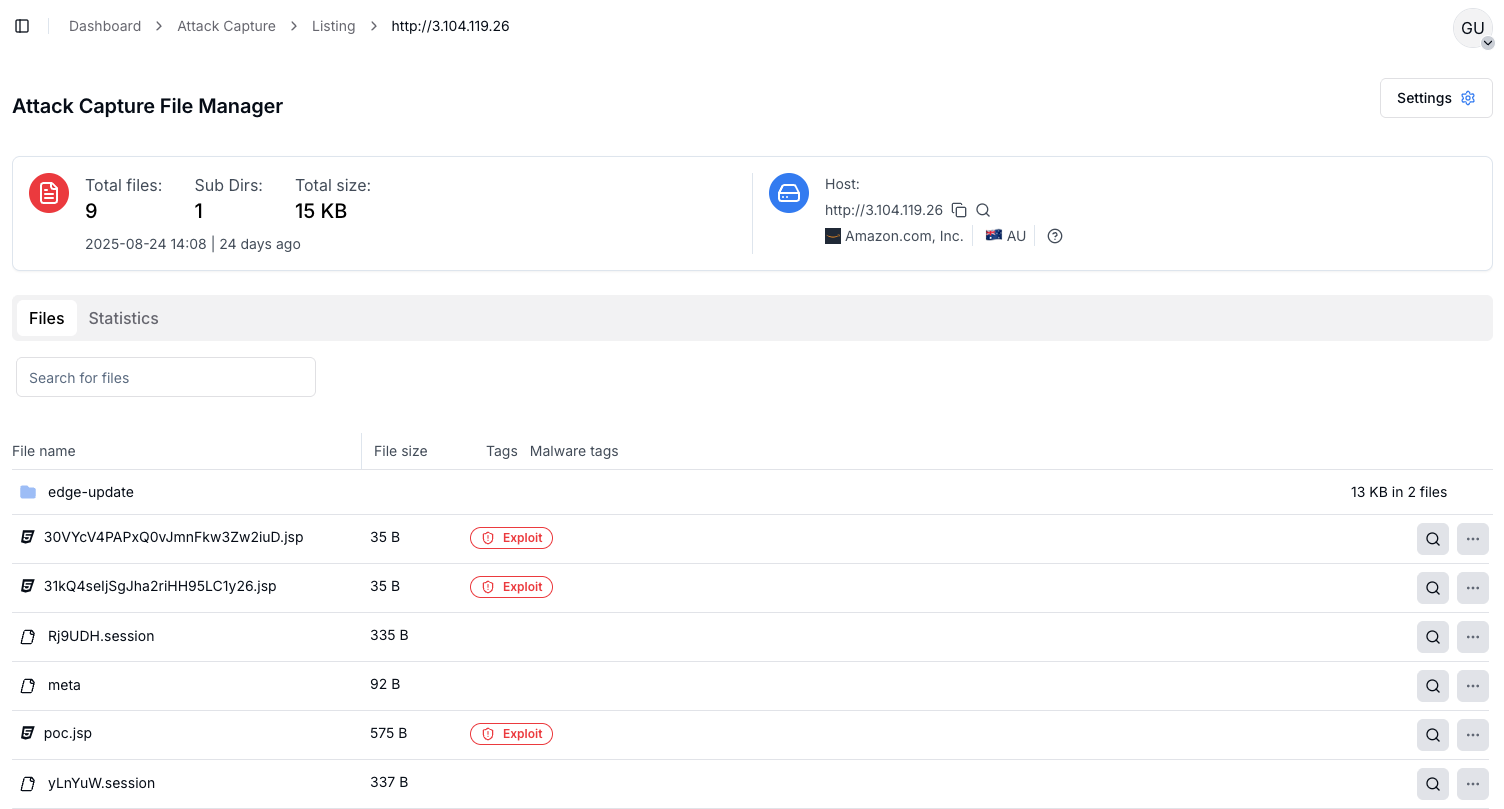
Attackers frequently use open directories hosted on AWS services to distribute malware or share stolen data. These directories can look like ordinary web servers until you inspect the files inside. Detecting them early is critical, since they often serve as staging points for larger campaigns.
Hunt.io's AttackCapture™ continuously scans for these exposed resources, making it easier to spot malicious payloads before they spread.
Example Workflow Scenario:
AWS Signal: GuardDuty generates an alert for repeated file downloads.
Hunt.io Pivot: AttackCapture™ reveals the host is an AWS-based open directory staging Redline Stealer. Analysts pivot to file hashes, malware families, and attacker tools.
Outcome: Instead of handling one file, the SOC responds to the entire campaign using AWS services for distribution.
Phishing kits are the next frontier, and AWS's credibility makes it a prime target for these operations.
Hunting AWS-Based Phishing Kits
Phishing campaigns increasingly rely on AWS hosting because it lends credibility and scale. A phishing page served from AWS can trick even cautious users, since the infrastructure appears legitimate. Identifying these kits quickly (and mapping out their related infrastructure) is essential for defending both employees and customers.
Example Workflow Scenario:
AWS Signal: A fake AWS login page is reported by users.
Hunt.io Pivot: The domain is enriched in Hunt.io and reveals dozens of related phishing sites hosted across AWS cloud environments.
Outcome: The SOC blocks not just one URL but the entire phishing cluster.
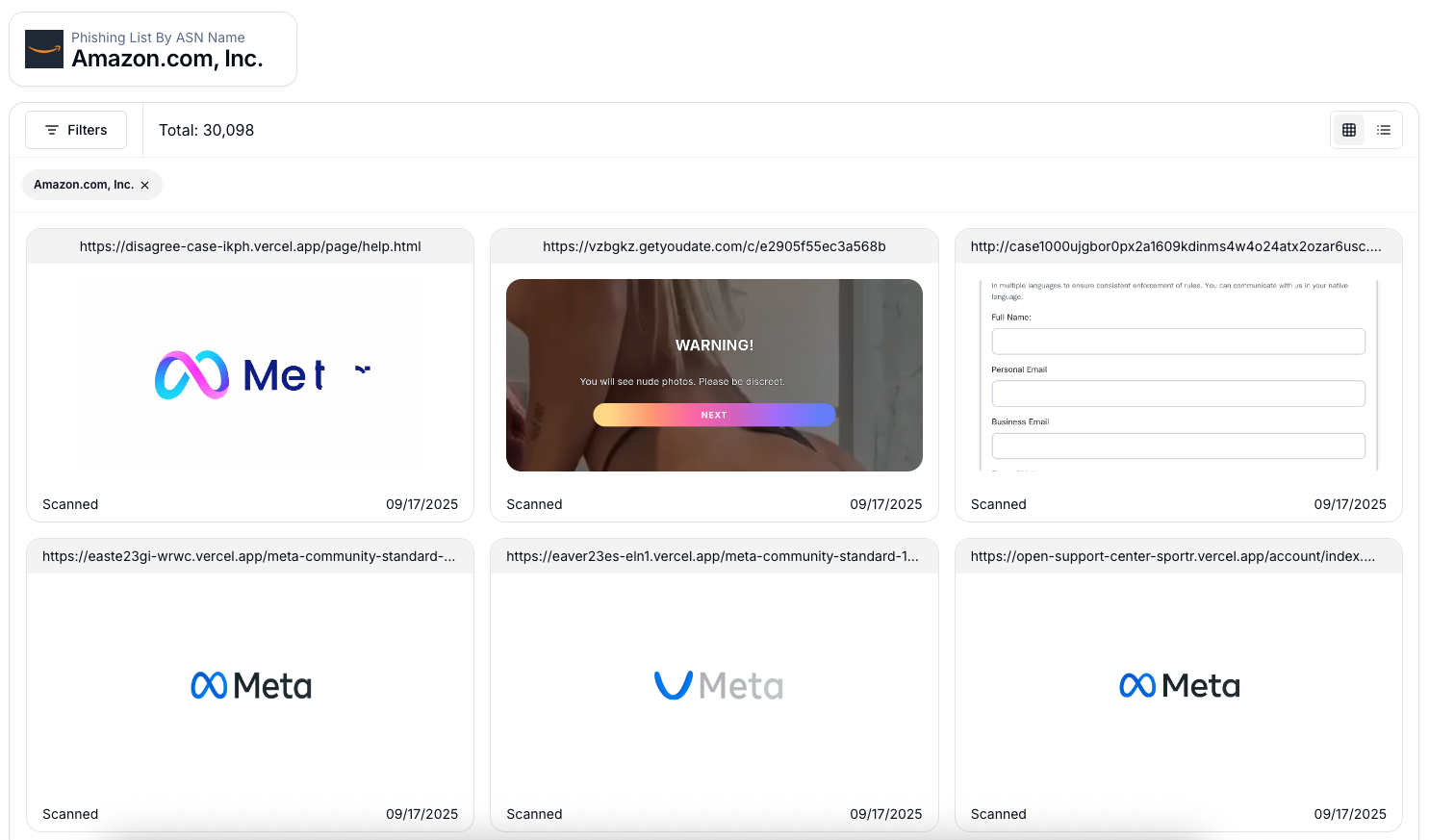
All of these examples point to the same reality: hunting in AWS isn't just about spotting single signals, it's about pivoting to reveal the bigger picture.
Why Pivoting is the Key to AWS Threat Hunting
Adversary infrastructure is rarely isolated. A single IP address might be tied to multiple domains, SSL certificates, or phishing kits, and each of those can reveal further connections. Without pivoting, defenders only see fragments of an operation.
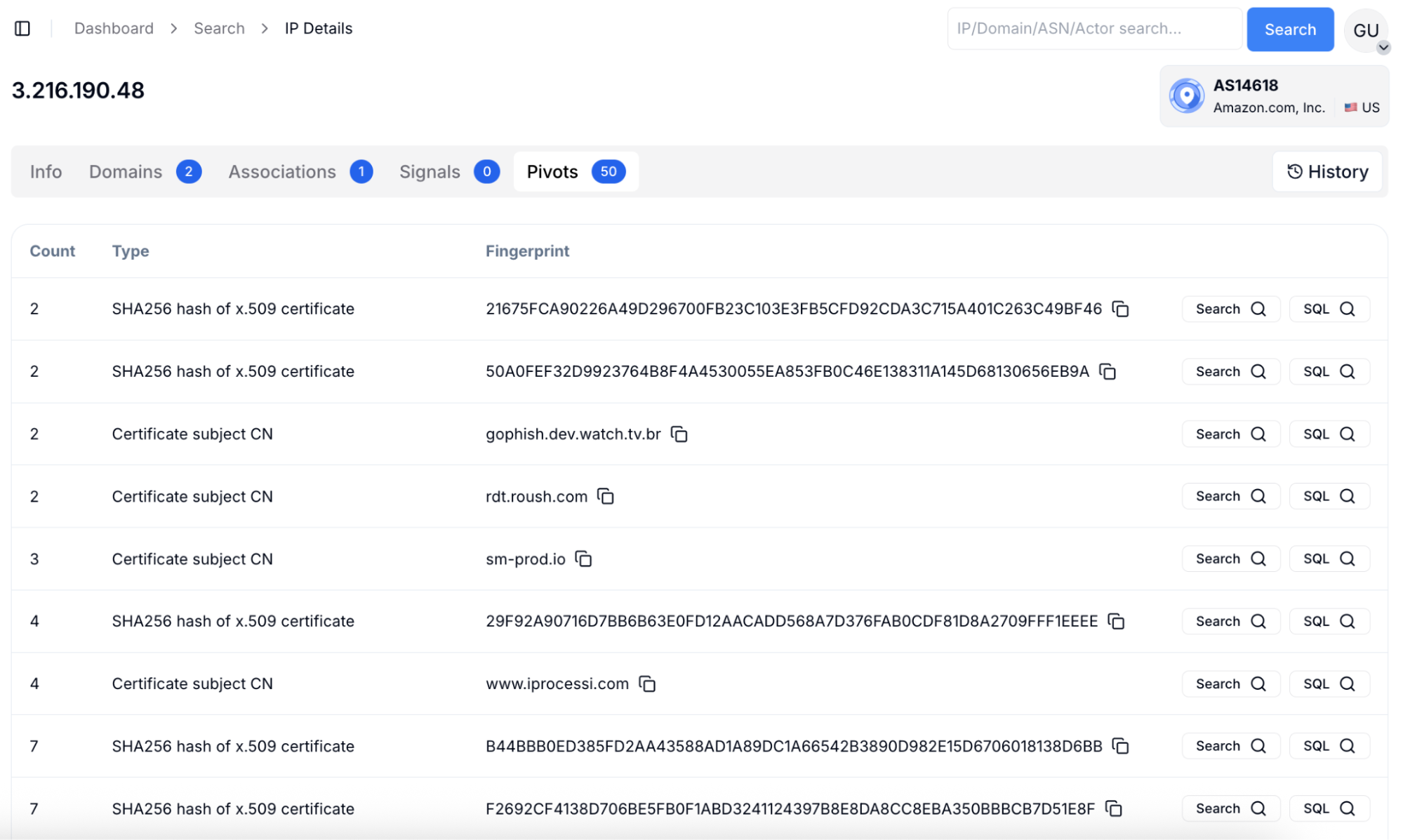
With Hunt.io, pivoting becomes the default workflow:
From IPs to Domains: An AWS-hosted IP can quickly expand into related domains or subdomains through SSL certificate fingerprints or reverse DNS records.
From Certificates to Infrastructure: A single SHA256 certificate hash might link multiple phishing sites, showing clusters that would otherwise go unnoticed.
From IOCs to Campaigns: One IOC in a GuardDuty alert can be enriched and expanded into attacker toolkits, open directories, or entire C2 networks.
From Associations to Actor Profiles: Tying domains, hashes, and certificates together builds the larger campaign picture, who is behind it, what tools they use, and how they move infrastructure across cloud providers.
The screenshot above shows this in action: starting from one AWS IP, pivots expose linked domains (gophish.dev.watch.tv.br, sm-prod.io, www.iprocessi.com) and certificate hashes that surface wider attacker campaigns.
This is the core of Hunt.io: giving threat hunters a way to start from any signal (an IP, domain, hash, or certificate subject) and pivot into a campaign view that reveals the adversary's infrastructure.
This is what makes AWS threat hunting effective. Instead of relying only on AWS services for monitoring, teams combine native data sources with Hunt.io to uncover the full scope of adversary campaigns.
Conclusion
AWS is one of the most trusted cloud environments, yet attackers consistently exploit it. From thousands of active C2 servers to phishing campaigns and malicious directories, AWS threats are on the rise.
Hunt.io bridges this gap by turning any signal into an entry point. Whether the starting point is an IP, domain, or file hash, Host Radar and AttackCapture™ expose the wider AWS infrastructure adversaries rely on. This pivot-driven approach gives security teams the visibility they need to move from isolated alerts to full campaign awareness.
See how Host Radar powers practical AWS threat hunting. Book a demo today.
Amazon Web Services (AWS) powers much of the modern internet. Enterprises host critical workloads on AWS, startups build rapidly there, and governments trust it with sensitive systems. That same trust draws attackers.
Recently, researchers uncovered a campaign using AWS Lambda URLs as command-and-control infrastructure against government agencies, and another campaign where compromised AWS access keys were used to abuse Amazon SES for large-scale phishing. These cases highlight that AWS security is not just about protecting your own AWS account but also about understanding how adversaries exploit AWS services.
Attackers routinely spin up short-lived servers for C2, stage malware payloads in open buckets, and host phishing pages that imitate major brands.
To defend effectively, teams need visibility into more than just their own AWS environment. They need insights from external threat intelligence that expose malicious use of cloud environments. That is where Hunt.io's Host Radar comes in.
To understand how this works in practice, let's take a closer look at Host Radar itself.
What is Host Radar?
Host Radar is a Hunt.io feature that continuously scans the internet to identify malicious infrastructure at scale. It helps threat hunting teams track abused hosting providers, map adversary use of AWS services, and connect single indicators to larger campaigns.
For threat hunters, this means every suspicious IP, domain, or IOC from logs becomes the start of a pivot. By tying AWS activity to related infrastructure, Host Radar supports both threat detection and proactive response.

That foundation becomes more tangible when we look at the latest AWS-specific data Hunt.io has uncovered.
Host Radar Data: AWS in Focus
The latest dataset shows AWS is a hotspot for adversary operations. In just the last 30 days, we recorded:
1.3k active C2 servers hosted on AWS
9 malicious open directories staging attacker tools and payloads
14 fresh IOCs connected to AWS threat campaigns
993 phishing sites abusing AWS services

Every one of these findings can be pivoted on. For example, an IP from VPC Flow Logs can be expanded into related domains, certificates, and ports. A phishing site can be pivoted into a cluster of similar AWS-based domains. This workflow provides hunters with a real-world view of how adversaries utilize cloud infrastructure.
Numbers alone aren't enough, the value comes from turning this data into actionable workflows.
Actionable AWS Threat Hunting Workflows with Hunt.io
Enriching VPC Flow Logs for Threat Detection
When attackers spin up short-lived EC2 instances inside AWS, they often blend in with legitimate traffic. SOC analysts relying only on raw logs can miss the early signs of command and control communication.
VPC Flow Logs are one of the most valuable data sources for AWS threat hunting, but on their own, they don't provide enough context to separate benign traffic from adversary infrastructure.
Example Workflow Scenario:
AWS Signal: A SOC analyst sees suspicious outbound traffic in VPC Flow Logs.
Hunt.io Pivot: The IP is enriched in Hunt.io and linked to one of the 1.3k C2 servers hosted in AWS: pivoting surfaces related domains, malware families, and even attacker TTPs.
Outcome: The team turns one event into a campaign map, enhancing threat detection rules within their SIEM.

Flow Logs are just one angle. Another common entry point for attackers is malicious open directories hosted in AWS.
Investigating Malicious Open Directories
Attackers frequently use open directories hosted on AWS services to distribute malware or share stolen data. These directories can look like ordinary web servers until you inspect the files inside. Detecting them early is critical, since they often serve as staging points for larger campaigns.
Hunt.io's AttackCapture™ continuously scans for these exposed resources, making it easier to spot malicious payloads before they spread.
Example Workflow Scenario:
AWS Signal: GuardDuty generates an alert for repeated file downloads.
Hunt.io Pivot: AttackCapture™ reveals the host is an AWS-based open directory staging Redline Stealer. Analysts pivot to file hashes, malware families, and attacker tools.
Outcome: Instead of handling one file, the SOC responds to the entire campaign using AWS services for distribution.

Phishing kits are the next frontier, and AWS's credibility makes it a prime target for these operations.
Hunting AWS-Based Phishing Kits
Phishing campaigns increasingly rely on AWS hosting because it lends credibility and scale. A phishing page served from AWS can trick even cautious users, since the infrastructure appears legitimate. Identifying these kits quickly (and mapping out their related infrastructure) is essential for defending both employees and customers.
Example Workflow Scenario:
AWS Signal: A fake AWS login page is reported by users.
Hunt.io Pivot: The domain is enriched in Hunt.io and reveals dozens of related phishing sites hosted across AWS cloud environments.
Outcome: The SOC blocks not just one URL but the entire phishing cluster.

All of these examples point to the same reality: hunting in AWS isn't just about spotting single signals, it's about pivoting to reveal the bigger picture.
Why Pivoting is the Key to AWS Threat Hunting
Adversary infrastructure is rarely isolated. A single IP address might be tied to multiple domains, SSL certificates, or phishing kits, and each of those can reveal further connections. Without pivoting, defenders only see fragments of an operation.

With Hunt.io, pivoting becomes the default workflow:
From IPs to Domains: An AWS-hosted IP can quickly expand into related domains or subdomains through SSL certificate fingerprints or reverse DNS records.
From Certificates to Infrastructure: A single SHA256 certificate hash might link multiple phishing sites, showing clusters that would otherwise go unnoticed.
From IOCs to Campaigns: One IOC in a GuardDuty alert can be enriched and expanded into attacker toolkits, open directories, or entire C2 networks.
From Associations to Actor Profiles: Tying domains, hashes, and certificates together builds the larger campaign picture, who is behind it, what tools they use, and how they move infrastructure across cloud providers.
The screenshot above shows this in action: starting from one AWS IP, pivots expose linked domains (gophish.dev.watch.tv.br, sm-prod.io, www.iprocessi.com) and certificate hashes that surface wider attacker campaigns.
This is the core of Hunt.io: giving threat hunters a way to start from any signal (an IP, domain, hash, or certificate subject) and pivot into a campaign view that reveals the adversary's infrastructure.
This is what makes AWS threat hunting effective. Instead of relying only on AWS services for monitoring, teams combine native data sources with Hunt.io to uncover the full scope of adversary campaigns.
Conclusion
AWS is one of the most trusted cloud environments, yet attackers consistently exploit it. From thousands of active C2 servers to phishing campaigns and malicious directories, AWS threats are on the rise.
Hunt.io bridges this gap by turning any signal into an entry point. Whether the starting point is an IP, domain, or file hash, Host Radar and AttackCapture™ expose the wider AWS infrastructure adversaries rely on. This pivot-driven approach gives security teams the visibility they need to move from isolated alerts to full campaign awareness.
See how Host Radar powers practical AWS threat hunting. Book a demo today.
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.





