Top 7 Virustotal Alternatives for Threat Hunters in 2026
Published on Oct 23, 2025

VirusTotal has long been the go-to platform for malware detection and file analysis. But in 2026, Google announced the full integration of VirusTotal into its Google Threat Intelligence (GTI) product line. This move shifted many of the free and mid-tier features behind enterprise pricing models, with some users reporting on security forums that costs have risen by up to 4x compared to previous tiers.
This change comes at a time when the threat landscape is accelerating. As stated by RecordedFuture, in the first half of 2026, the total number of disclosed vulnerabilities (CVEs) increased by 16% compared to H1 2024, underscoring the growing need for accessible, actionable threat intelligence.
For many threat hunting teams, researchers, and SOCs, the GTI integration has created a clear gap: rising threats combined with restricted access to previously free VirusTotal features make relying solely on community uploads and antivirus detections costly and unsustainable. Finding practical VirusTotal alternatives has never been more important for teams needing deeper visibility and faster, proactive threat intelligence feeds.
As a result, security teams are now exploring other tools that can replicate (and in many cases surpass) what VirusTotal once offered. Below are seven platforms that combine open data, commercial data, automation, and proactive threat intelligence to help threat hunters fill that gap.
Top 7 Alternatives to VirusTotal to Consider
MalwareBazar
MalwareBazar, created by abuse.ch and Spamhaus, is a community-driven platform where you can share and access malware samples to enhance threat intelligence. This platform solves common problems faced by researchers, such as registration barriers and sample download limits on other platforms, making it a convenient resource for security researchers.
MalwareBazar provides insights into malware behavior and plays a key role in identifying and mitigating cyber threats related to malware families and botnets. The platform offers:
Integration with SIEM systems so you can feed its intelligence into your existing security framework.
Seamless integration for automated threat detection to improve your overall security posture.
Guarantee all samples are vetted and free from benign files, adware, or PUPs, so it's a reliable source for malware analysis.
One of the best features of MalwareBazar is its API, which allows automation for users who need to integrate malware sample retrieval into their workflow. Also, you can download unlimited malware samples and get fresh content daily. MalwareBazar is a great tool for security vendors and researchers to stay ahead of phishing threats and hidden malware.
Hunt.io
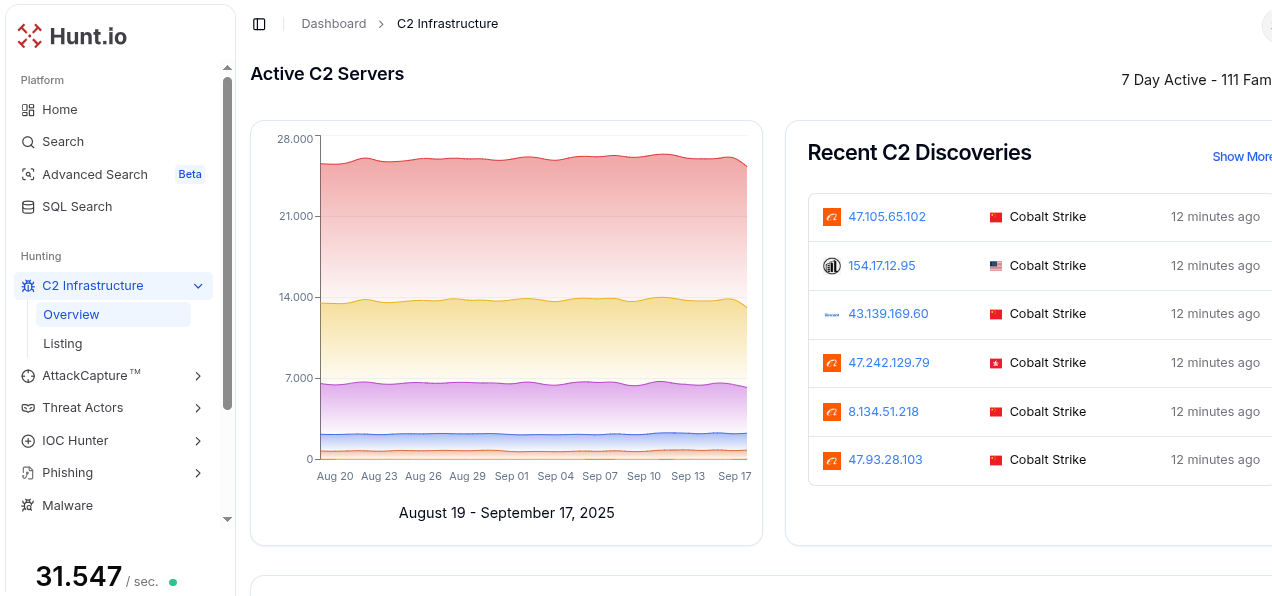
At Hunt.io, we offer a cutting-edge threat hunting tool that provides deep IP, domain, and hash intelligence so threat hunters can stay ahead of security threats. One of our key features is the C2 Infrastructure Feed, which uses first-party validation and its own scanning to discover malicious infrastructure proactively.
This proactive threat hunting approach means malicious infrastructure is identified before it can be used heavily by threat hunting tools.
In addition to the C2 Infrastructure Feed, we perform internet-wide scanning, monitoring for:
TLS/SSL certificates
JARM/JA4 hashes
HTTP/TCP banners
Domain naming conventions
This real-time monitoring catches malicious infrastructure early, giving you a big advantage in threat detection.
Our platform also has an IOC Hunter feature, allowing you to uncover IOCs from recent research and explore related infrastructure through multiple observables, such as:
Exposed directories
HTTP headers
Certificate info
By building a more complete picture of threat actor infrastructure, we help threat hunters identify and mitigate threats proactively.
OPSWAT MetaDefender Cloud: Multi-Engine Scanning
OPSWAT MetaDefender Cloud is a threat hunting tool with:
Integration with multiple security vendors for better threat detection.
Over 20 antivirus engines.
Significant improvement in detection and response time.
Comprehensive threat detection.
It uses multiple antivirus engines to scan files, domains, and IP addresses for comprehensive threat detection. The benefits of using multiple antivirus engines include:
Better detection
Faster malware outbreak detection
Thorough scanning
By combining malware analysis with user feedback, OPSWAT MetaDefender Cloud helps strengthen threat intelligence, making it easier to spot and adapt to evolving attacker TTPs.
User Feedback Integration
A key feature of MetaDefender is the ability to incorporate user feedback into its threat detection algorithms. Users can flag and comment on IPs, domains, or files to refine threat detection and improve the overall platform.
This collaborative approach ensures the platform stays up-to-date with the latest threats and continuously improves real-time threat detection.
Jotti's Malware Scan: Simple and Free

Jotti's Malware Scan is a simple and free online tool to scan files with multiple antivirus engines, making it easy to use for individuals and small-scale operations. Let's take a look at its features.
Multiple Antivirus Engines
Jotti's Malware Scan uses several antivirus programs to improve malware detection, giving you stronger protection than relying on just one. By combining different antivirus engines, it:
Defends against a wider range of malware.
Delivers more complete protection.
Increases the chances of catching threats.
Detects malware that might slip past a single scanner.
This multi-engine approach is crucial to maximizing malware detection and finding hidden malware.
For Small-Scale Use
Jotti's scan is perfect for individuals or small-scale operations. The user-friendly interface to scan files with multiple antivirus engines is ideal for basic malware detection. This tool is a powerful alternative for personal use to scan suspicious files with ease and confidence.
AlienVault: All-in-One Security
Level Blue's AlienVault is an all-in-one security solution with unified capabilities across multiple security domains. Its integrated threat detection allows for malware analysis and combines other security features for better threat response.
Community participation is key to AlienVault's threat detection. The database is updated through user reports, so the entries reflect current malicious activity. AlienVault's API makes it easy to integrate with other security solutions for better threat management.
AlienVault integrates malware analysis with other security features for threat hunting. This threat detection and response is a must-have for security teams and professionals.
For Organizations of All Sizes
AlienVault offers flexible solutions that fit individual analysts, small businesses, and growing organizations, while also scaling to support mid-sized companies and larger enterprises. Its customizable approach ensures that teams at different levels of threat hunting maturity can enhance their overall security posture efficiently and cost-effectively.
CAPE Sandbox
CAPE Sandbox is a powerful sandbox tool built for dissecting malware in depth. It originated as a fork of the older CAPE project, which itself came from the well-known Cuckoo Sandbox. What makes CAPEv2 stand out is how it mixes static and dynamic analysis to extract malware configuration, unpack hidden payloads, and detect evasive behaviour.
CAPEv2 can monitor API calls, capture network traffic, record file changes, and take memory dumps. It also includes a debugger programmed via YARA signatures, giving analysts tools to deal with countermeasures like anti-sandbox tricks.
When malware injects itself or compresses pieces of its payload, CAPEv2 works to uncover what's hidden, whether DLLs, shellcode, or other injected modules.
In practice, this means if you're trying to figure out exactly how malware works, its configuration, payloads, communication, or evasion, CAPEv2 delivers a clear, thorough view.
AbuseIPDB: Community IP Reputation Database
AbuseIPDB is a community-driven database that tracks reported malicious IP addresses to help identify potential threats. Users can report suspicious content directly to enhance the database of known threats and contribute to the fight against cyber threats.
Community Contributions
AbuseIPDB relies on community contributions to maintain and update its database of malicious IP addresses and domains. Users can provide feedback on detected threats to improve the accuracy and completeness of the database.
A community-driven approach means the database is updated regularly with the latest threat information, benefiting all users. AbuseIPDB integrates with many security systems to improve threat detection. Its API makes it easy to integrate AbuseIPDB's intelligence into your existing security stack.
Each of these platforms offers a unique angle (from community malware sharing to deep infrastructure mapping), proving that modern threat hunting no longer depends on a single data source. Together, they form a flexible ecosystem that empowers analysts to detect, correlate, and act faster.
Conclusion
As cyber threats become more sophisticated, traditional scanning tools just aren't enough. Platforms like MalwareBazar, CAPE Sandbox, and AbuseIPDB give you the means to uncover hidden malware, analyze suspicious files, and boost your threat intelligence.
Stay a step ahead of attackers and ensure your team can respond quickly with Hunt.io. Book a demo today and see proactive threat hunting in action.
VirusTotal has long been the go-to platform for malware detection and file analysis. But in 2026, Google announced the full integration of VirusTotal into its Google Threat Intelligence (GTI) product line. This move shifted many of the free and mid-tier features behind enterprise pricing models, with some users reporting on security forums that costs have risen by up to 4x compared to previous tiers.
This change comes at a time when the threat landscape is accelerating. As stated by RecordedFuture, in the first half of 2026, the total number of disclosed vulnerabilities (CVEs) increased by 16% compared to H1 2024, underscoring the growing need for accessible, actionable threat intelligence.
For many threat hunting teams, researchers, and SOCs, the GTI integration has created a clear gap: rising threats combined with restricted access to previously free VirusTotal features make relying solely on community uploads and antivirus detections costly and unsustainable. Finding practical VirusTotal alternatives has never been more important for teams needing deeper visibility and faster, proactive threat intelligence feeds.
As a result, security teams are now exploring other tools that can replicate (and in many cases surpass) what VirusTotal once offered. Below are seven platforms that combine open data, commercial data, automation, and proactive threat intelligence to help threat hunters fill that gap.
Top 7 Alternatives to VirusTotal to Consider
MalwareBazar

MalwareBazar, created by abuse.ch and Spamhaus, is a community-driven platform where you can share and access malware samples to enhance threat intelligence. This platform solves common problems faced by researchers, such as registration barriers and sample download limits on other platforms, making it a convenient resource for security researchers.
MalwareBazar provides insights into malware behavior and plays a key role in identifying and mitigating cyber threats related to malware families and botnets. The platform offers:
Integration with SIEM systems so you can feed its intelligence into your existing security framework.
Seamless integration for automated threat detection to improve your overall security posture.
Guarantee all samples are vetted and free from benign files, adware, or PUPs, so it's a reliable source for malware analysis.
One of the best features of MalwareBazar is its API, which allows automation for users who need to integrate malware sample retrieval into their workflow. Also, you can download unlimited malware samples and get fresh content daily. MalwareBazar is a great tool for security vendors and researchers to stay ahead of phishing threats and hidden malware.
Hunt.io

At Hunt.io, we offer a cutting-edge threat hunting tool that provides deep IP, domain, and hash intelligence so threat hunters can stay ahead of security threats. One of our key features is the C2 Infrastructure Feed, which uses first-party validation and its own scanning to discover malicious infrastructure proactively.
This proactive threat hunting approach means malicious infrastructure is identified before it can be used heavily by threat hunting tools.
In addition to the C2 Infrastructure Feed, we perform internet-wide scanning, monitoring for:
TLS/SSL certificates
JARM/JA4 hashes
HTTP/TCP banners
Domain naming conventions
This real-time monitoring catches malicious infrastructure early, giving you a big advantage in threat detection.
Our platform also has an IOC Hunter feature, allowing you to uncover IOCs from recent research and explore related infrastructure through multiple observables, such as:
Exposed directories
HTTP headers
Certificate info
By building a more complete picture of threat actor infrastructure, we help threat hunters identify and mitigate threats proactively.
OPSWAT MetaDefender Cloud: Multi-Engine Scanning

OPSWAT MetaDefender Cloud is a threat hunting tool with:
Integration with multiple security vendors for better threat detection.
Over 20 antivirus engines.
Significant improvement in detection and response time.
Comprehensive threat detection.
It uses multiple antivirus engines to scan files, domains, and IP addresses for comprehensive threat detection. The benefits of using multiple antivirus engines include:
Better detection
Faster malware outbreak detection
Thorough scanning
By combining malware analysis with user feedback, OPSWAT MetaDefender Cloud helps strengthen threat intelligence, making it easier to spot and adapt to evolving attacker TTPs.
User Feedback Integration
A key feature of MetaDefender is the ability to incorporate user feedback into its threat detection algorithms. Users can flag and comment on IPs, domains, or files to refine threat detection and improve the overall platform.
This collaborative approach ensures the platform stays up-to-date with the latest threats and continuously improves real-time threat detection.
Jotti's Malware Scan: Simple and Free

Jotti's Malware Scan is a simple and free online tool to scan files with multiple antivirus engines, making it easy to use for individuals and small-scale operations. Let's take a look at its features.
Multiple Antivirus Engines
Jotti's Malware Scan uses several antivirus programs to improve malware detection, giving you stronger protection than relying on just one. By combining different antivirus engines, it:
Defends against a wider range of malware.
Delivers more complete protection.
Increases the chances of catching threats.
Detects malware that might slip past a single scanner.
This multi-engine approach is crucial to maximizing malware detection and finding hidden malware.
For Small-Scale Use
Jotti's scan is perfect for individuals or small-scale operations. The user-friendly interface to scan files with multiple antivirus engines is ideal for basic malware detection. This tool is a powerful alternative for personal use to scan suspicious files with ease and confidence.
AlienVault: All-in-One Security

Level Blue's AlienVault is an all-in-one security solution with unified capabilities across multiple security domains. Its integrated threat detection allows for malware analysis and combines other security features for better threat response.
Community participation is key to AlienVault's threat detection. The database is updated through user reports, so the entries reflect current malicious activity. AlienVault's API makes it easy to integrate with other security solutions for better threat management.
AlienVault integrates malware analysis with other security features for threat hunting. This threat detection and response is a must-have for security teams and professionals.
For Organizations of All Sizes
AlienVault offers flexible solutions that fit individual analysts, small businesses, and growing organizations, while also scaling to support mid-sized companies and larger enterprises. Its customizable approach ensures that teams at different levels of threat hunting maturity can enhance their overall security posture efficiently and cost-effectively.
CAPE Sandbox

CAPE Sandbox is a powerful sandbox tool built for dissecting malware in depth. It originated as a fork of the older CAPE project, which itself came from the well-known Cuckoo Sandbox. What makes CAPEv2 stand out is how it mixes static and dynamic analysis to extract malware configuration, unpack hidden payloads, and detect evasive behaviour.
CAPEv2 can monitor API calls, capture network traffic, record file changes, and take memory dumps. It also includes a debugger programmed via YARA signatures, giving analysts tools to deal with countermeasures like anti-sandbox tricks.
When malware injects itself or compresses pieces of its payload, CAPEv2 works to uncover what's hidden, whether DLLs, shellcode, or other injected modules.
In practice, this means if you're trying to figure out exactly how malware works, its configuration, payloads, communication, or evasion, CAPEv2 delivers a clear, thorough view.
AbuseIPDB: Community IP Reputation Database

AbuseIPDB is a community-driven database that tracks reported malicious IP addresses to help identify potential threats. Users can report suspicious content directly to enhance the database of known threats and contribute to the fight against cyber threats.
Community Contributions
AbuseIPDB relies on community contributions to maintain and update its database of malicious IP addresses and domains. Users can provide feedback on detected threats to improve the accuracy and completeness of the database.
A community-driven approach means the database is updated regularly with the latest threat information, benefiting all users. AbuseIPDB integrates with many security systems to improve threat detection. Its API makes it easy to integrate AbuseIPDB's intelligence into your existing security stack.
Each of these platforms offers a unique angle (from community malware sharing to deep infrastructure mapping), proving that modern threat hunting no longer depends on a single data source. Together, they form a flexible ecosystem that empowers analysts to detect, correlate, and act faster.
Conclusion
As cyber threats become more sophisticated, traditional scanning tools just aren't enough. Platforms like MalwareBazar, CAPE Sandbox, and AbuseIPDB give you the means to uncover hidden malware, analyze suspicious files, and boost your threat intelligence.
Stay a step ahead of attackers and ensure your team can respond quickly with Hunt.io. Book a demo today and see proactive threat hunting in action.
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.





