Top 10 Threat Hunting Tools (Updated 2026)
Published on Oct 23, 2025
Cyber threats are becoming more sophisticated, and threat hunting tools are essential for staying ahead of attackers. These tools actively monitor for suspicious activity, providing a crucial layer of defense.
According to a recent study by SANS, in 2024, 61% of organizations rely on commercial threat intelligence tools, while 47% use open-source intelligence (OSINT) tools to track changes in the threat landscape. These stats highlight the growing importance of robust and flexible tools in modern threat hunting strategies.
In this post, we'll cover the best threat hunting tools for 2024, focusing on how they empower organizations to enhance their security posture with greater visibility and responsiveness.
Quick Facts
Cyber threat hunting tools proactively detect and stop threats by continuously scanning and analyzing network data, not reactive security.
Good threat hunting tools have advanced analytics, machine learning, and threat intelligence integration to improve detection and response, alongside external threat intelligence to identify and mitigate potential security threats proactively.
Choosing the right threat hunting tool means assessing business needs, evaluating features, and ensuring compatibility with the existing security stack for threat mitigation.
What are Threat Hunting Tools?
Threat hunting tools are designed to detect and stop threats before they can do damage. Unlike traditional security that reacts to known threats, cyber threat hunting tools continuously scan, identify, log, nullify, and monitor the network for suspicious activity. With the rise of cyber attacks, we need proactive defense, these tools are a must-have in today's security landscape. A threat hunter uses these tools to get better at threat hunting.

These tools work by collecting and analyzing different types of data, logs, events, endpoint telemetry, and network traffic. Using security analytics they identify unknown threats by statistical patterns. This proactive search and identification process is what differentiates threat hunting tools from other security. The threat hunting process is crucial in enhancing security analysis by integrating various open-source security tools effectively.
Using multiple threat hunting tools gives you the best chance of stopping cyber attacks. Each tool has unique capabilities and together they make a strong defense. Advanced threat hunting tools give you an extra layer of security against threats, so you have coverage across all surfaces.
Also, these tools give you attack analysis, so security teams can understand the threat and where it came from. This security data is key to developing countermeasures and overall security posture. By addressing threats proactively you can reduce the risk of security incidents and data breaches.
Features of Good Threat Hunting Tools
Good threat hunting tools should provide comprehensive coverage and capabilities to improve detection and response and stay ahead of emerging threats. Three key features that define good threat hunting tools are advanced analytics, machine learning, and threat intelligence integration.
Advanced analytics allows you to analyze large amounts of data to find patterns of threats. This is key to identifying unknown threats and real-time threat intelligence.
Machine learning and AI help in threat detection by automating network data analysis and identifying anomalies that indicate threats. Integrating with threat intelligence platforms allows automated gathering and analysis of threat data so you can respond faster and have comprehensive threat analysis.
Advanced Analytics
Advanced analytics is key in threat hunting. It analyzes data at scale from multiple sources to proactively detect attacks. A good threat hunting tool should be able to monitor multiple data sources for overall security visibility. This includes real-time monitoring and advanced threat detection capabilities to identify and stop threats before they can do damage.
Advanced analytics gives security analysts visibility into threats so they can identify and respond. This proactive detection approach keeps you ahead of advanced and emerging threats and a strong security posture.
Machine Learning
Machine learning improves threat detection by automating network data analysis and identifying anomalies that indicate threats. Tools like these have features like network forensics, NIDS (Network Intrusion Detection System), and DNS domain classification which all contribute to its threat detection capabilities.
Machine learning tools are further improved by support for multiple languages like Python, Ruby, Java, and Lua. This allows for easy integration and deployment in different environments so organizations can deploy these tools and improve their threat hunting.
Threat Intelligence Integration
Integrating threat intelligence into threat hunting tools is key to comprehensive threat analysis so you can stay ahead of attacks. Seamless connections to multiple sources through integration allow threat hunting tools to identify and respond to threats faster.
Customization options allow security teams to tailor the threat intelligence integration according to their needs so the tools can provide real-time threat intelligence and actionable insights to detect and mitigate security threats.
Data Collection and Analysis for Threat Detection
Data collection and analysis are crucial components of threat detection in threat hunting. Threat hunting tools gather and aggregate vast amounts of data from various sources, such as logs, events, endpoint telemetry, and network traffic. This data is then analyzed using advanced analytics and machine learning to identify unusual patterns and anomalies that may indicate potential security threats. By leveraging data collection and analysis, threat hunters can gain a deeper understanding of their organization's security posture and identify potential threats before they become incidents.
Effective data collection and analysis for threat detection involve several key steps:
Data Collection: Gathering data from various sources, including logs, events, endpoint telemetry, and network traffic.
Data Aggregation: Combining data from multiple sources into a single, unified view.
Data Analysis: Using advanced analytics and machine learning to identify unusual patterns and anomalies in the data.
Threat Identification: Identifying potential security threats based on the analysis of the data.
By following these steps, threat hunters can use data collection and analysis to detect potential security threats and prevent incidents. This proactive approach ensures that security teams are always one step ahead of cyber threats, enhancing the overall security posture of the organization.
Proactive Search and Identification of Cyber Threats
Proactive search and identification of cyber threats is a critical component of threat hunting. Threat hunting tools use advanced analytics and machine learning to proactively search for potential security threats in an organization's network and systems. This involves analyzing data from various sources, such as logs, events, endpoint telemetry, and network traffic, to identify unusual patterns and anomalies that may indicate potential security threats.
Effective proactive search and identification of cyber threats involve several key steps:
Threat Intelligence: Gathering and analyzing threat intelligence from various sources, including external threat feeds and internal security data.
Anomaly Detection: Using advanced analytics and machine learning to identify unusual patterns and anomalies in the data.
Threat Identification: Identifying potential security threats based on the analysis of the data.
Incident Response: Responding to identified threats and preventing incidents.
By following these steps, threat hunters can proactively search for and identify potential security threats, preventing incidents and protecting their organization's security. This proactive approach ensures that security teams are always vigilant and ready to respond to emerging threats, enhancing the overall security posture of the organization.
A great example of proactive threat hunting was the discovery of SuperShell and Cobalt Strike malware during a scan of public infrastructure. By analyzing suspicious files and traffic, Hunt.io researchers identified malicious infrastructure, including command-and-control servers.
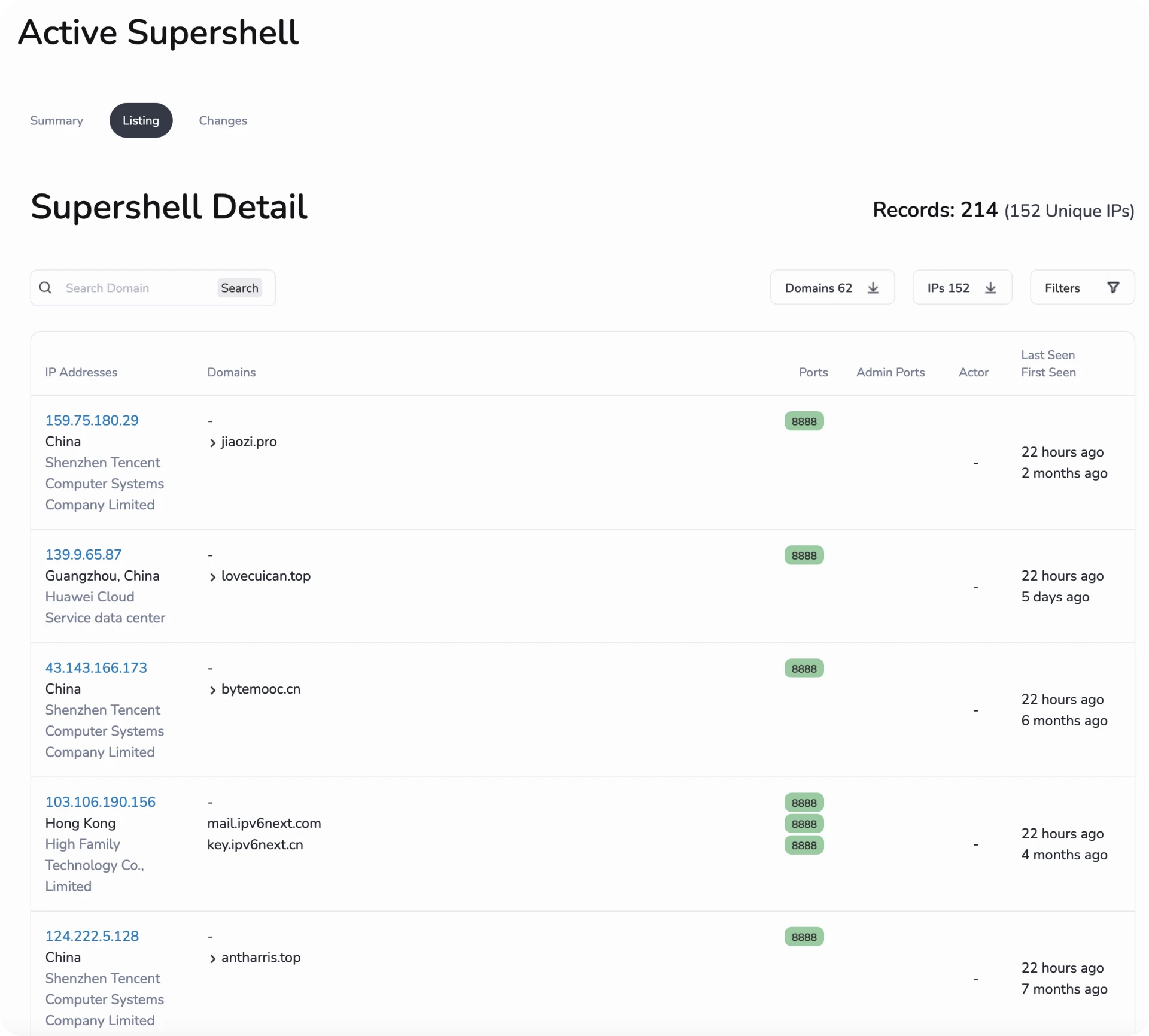
This approach demonstrates how continuous monitoring, anomaly detection, and real-time data analysis enable organizations to stay ahead of potential threats and mitigate risks before attackers can escalate their operations
Behavioral Analysis
Behavioral analysis is a critical component of threat hunting. Threat hunting tools use behavioral analysis to identify unusual patterns and anomalies in user and system behavior that may indicate potential security threats. This involves analyzing data from various sources, such as logs, events, endpoint telemetry, and network traffic, to identify behavior that is outside the norm.
Effective behavioral analysis involves several key steps:
Baseline Establishment: Establishing a baseline of normal user and system behavior.
Anomaly Detection: Using advanced analytics and machine learning to identify unusual patterns and anomalies in the data.
Threat Identification: Identifying potential security threats based on the analysis of the data.
Incident Response: Responding to identified threats and preventing incidents.
By following these steps, threat hunters can use behavioral analysis to identify potential security threats and prevent incidents. This approach allows security teams to detect insider threats and other sophisticated attacks that may bypass traditional security measures, enhancing the organization's overall security posture.
10 Popular Threat Hunting Tools in 2026
Here are the top threat hunting tools that stand out. These tools have advanced threat detection capabilities so you need proactive cybersecurity. Let's see the top threat hunting tools, each with its unique features.

APT-Hunter
APT-Hunter is designed to track advanced persistent threats through event log analysis. This tool created by Ahmed Khlief supports the Windows operating system and has robust features to identify and stop advanced threats.
Attacker KB
The Attacker Knowledge Base (KB) is a treasure trove of information that contains various exploits and attack methods so security teams can have insights for proactive threat detection and vulnerability management. By integrating Attacker KB insights, organizations can prioritize vulnerabilities based on exploit information and overall security posture.
Hunt SQL
Hunt SQL is our query language designed to make threat hunting more efficient and customizable. With Hunt SQL, you can easily extract and analyze data from our threat intelligence platform, allowing you to create precise queries that match your unique needs. Whether you're investigating indicators of compromise, suspicious domains, or malicious C2 server activity, Hunt SQL gives you the flexibility to dig deeper into the data.
This level of control is critical for identifying hidden threats and responding faster to potential attacks, streamlining your threat-hunting process and improving overall security defenses.
Automater
Automater is a tool that analyzes URLs and hashes for intrusion analysis so it's perfect for beginners in cybersecurity. This user-friendly and open-source tool is available on GitHub so it's a great starting point for those who are new to threat hunting.
CrowdFMS
CrowdFMS automates phishing email detection using VirusTotal's Private API. This automation makes threat detection and response faster so phishing attempts are detected and mitigated faster.
Cuckoo Sandbox
Cuckoo Sandbox is a customizable malware analysis tool that supports multiple file types and operating systems. By analyzing various file types Cuckoo Sandbox helps security teams understand malware behavior and plan countermeasures.
DeepBlue CLI
DeepBlue CLI can detect specific events in Windows logs. This tool can detect specific events in Windows event logs faster so threat detection and response are faster.
CyberChef
CyberChef is to help users encode and decode data and supports multiple formats. This tool is for technical and non-technical analysts and is licensed under Apache 2.0.
Phishing Catcher
Phishing Catcher detects phishing domains through TLS certificate checks. Written in Python, this tool uses a YAML configuration file and with default configuration, you can see immediate results without much setup.
Intercept.io Phishing API
Intercept.io offers rapid and accurate detection of phishing sites, empowering brands and MSSPs to safeguard their assets more effectively. By leveraging these automated analysis tools, you can quickly identify and neutralize phishing threats with high confidence.
Pick the Right Threat Hunting Tool for Your Business
Choosing the right threat hunting tool for your business is key to good cybersecurity. The first step is to know your business challenges and requirements. A tool's success in threat hunting depends on its compatibility with existing security setups and overall security posture.
A good threat hunting tool should provide centralized data management to give you complete visibility into your network and applications. Having a structured threat hunting methodology makes threat hunting more effective and better detection.
Identify Business Needs
Knowing your business needs helps you choose the right threat hunting solution. Knowing your business requirements is key to tailoring your threat hunting strategy to address your vulnerabilities. Knowing what threats are unique to your business allows security teams to focus on what matters most.
Check Features
Checking the features of threat hunting tools is important to align them with your business security goals. Advanced query and search are crucial for data analysis in these tools, also, aggregate threat data and automated processes make it more operational.
Consider Integration
A good threat hunting solution should integrate smoothly with existing security systems to make it more efficient. Integration with current security tools makes a threat hunting tool more effective by having complete coverage and data sharing.
Different providers aggregate threat data from multiple sources to automate response actions so security operations are more efficient.
Threat Hunting with User and Entity Behavior Analytics (UEBA)
Proactive threat hunting helps detect advanced threats that bypass automated cybersecurity measures. User and Entity Behavior Analytics (UEBA) tools create baseline behavioral profiles from entities to detect unusual activities, enabling the identification of insider threats. These tools monitor deviations from user behavior patterns to uncover potential risks.
Some of these solutions use machine learning to enhance threat detection, automatically identifying and analyzing anomalies to assist security professionals in spotting insider threats.
Other advanced threat-hunting tools combine UEBA with Identity and Access Management (IAM) for a deeper understanding of security risks. This integration provides complete visibility into security events and user behavior, improving threat detection capabilities.
Real-time alerts are crucial, as they enable early threat detection. The advanced analytics provide insights to identify threats proactively, enhancing team collaboration and response.
Open Source Intelligence (OSINT) in Threat Hunting
Open Source Intelligence (OSINT) is key to threat hunting. OSINT tools help analysts to collect and analyze data from publicly available sources to detect threats. These tools are for threat hunters to identify risks through publicly available data analysis.
The OSINT threat intelligence cycle is to determine the purpose, harvest data, categorize information and refine the analysis, so organizations can get timely and actionable insights.
Maltego
Maltego visualizes networks by showing relationships between domains, IP addresses, and other entities. Its analytical features allow users to dig deep into network relationships so they can identify threats and investigate cyber threats.
TheHarvester
TheHarvester is a reconnaissance tool that helps security professionals to gather publicly available information. It's good at finding subdomains associated with a domain so security assessments are more accurate. TheHarvester can also gather email addresses associated with a target domain so social engineering assessments can be done.
Best Practices for Threat Hunting
Best practices for threat hunting are key to having a strong cybersecurity posture. Undetected threats can stay in the network for about 280 days before it's discovered so threat hunting is proactive. Cyber threat hunters use their expertise to find hidden malware and suspicious activities (like C2 servers) that automated systems will miss, so continuous monitoring and regular updates are a must.
Train your employees to do threat hunting. Machine learning-driven tools can automate the triage of alerts so they can be prioritized for faster response and reduce false positives by understanding normal behavior patterns. Early threat detection includes behavioral analysis, UEBA, machine learning algorithms, and continuous monitoring.
Regular Updates and Patching
Keep your systems updated to minimize the risk of exploitation from known vulnerabilities. Regular system updates and patching reduce the risk of exploitation so security incidents are minimized.
Continuous Monitoring
Continuous monitoring is key to early threat detection and response in cybersecurity. Many tools use artificial intelligence for real-time threat detection, monitoring continuously to find hidden attackers.
Collaboration and Information Sharing
Sharing threat intelligence across organizations improves overall threat hunting. Collaborating with other organizations for information exchange strengthens threat detection and response to security incidents.
Related Questions
What are threat hunting tools?
Threat hunting tools are needed to detect and neutralize potential threats by scanning and monitoring the network. They help in finding and logging suspicious activities to enhance security.
Why threat hunting tools in 2024?
Threat hunting tools are needed in 2024 because of the increasing frequency and complexity of attacks, so organizations can detect and mitigate threats earlier. Using these tools is a proactive defense strategy that is necessary in this digital age.
How do advanced analytics help in threat hunting?
Advanced analytics helps in threat hunting by analyzing big data to find patterns that indicate potential threats so you can proactively identify and respond in time. This will strengthen your overall security posture.
What does machine learning do in threat detection?
Machine learning automates the analysis of network data to find anomalies that will enhance threat detection and overall security. This will strengthen threat detection.
How to choose the right threat hunting tool?
To choose the right threat hunting tool, organizations must define what they need, evaluate the key features, and see how the tool integrates with their existing security infrastructure. This will ensure the chosen tool will enhance their threat detection.
Conclusion
In summary, threat hunting tools are essential for detecting and neutralizing cyber threats. Key features such as advanced analytics, machine learning, and integration with threat intelligence make these tools more effective. The top threat hunting tools reviewed here offer unique features tailored to different security needs. When selecting the right tool for your organization, consider your specific requirements, evaluate key features, and ensure it integrates smoothly with your existing systems.
While free tools offer some advantages, relying on them may not always be the best option. Professional tools developed by companies typically provide advanced threat-hunting capabilities and support that many organizations value.
If you're ready to elevate your threat hunting efforts, book a demo with us to discover how our tools can help you achieve your threat detection goals.
Cyber threats are becoming more sophisticated, and threat hunting tools are essential for staying ahead of attackers. These tools actively monitor for suspicious activity, providing a crucial layer of defense.
According to a recent study by SANS, in 2024, 61% of organizations rely on commercial threat intelligence tools, while 47% use open-source intelligence (OSINT) tools to track changes in the threat landscape. These stats highlight the growing importance of robust and flexible tools in modern threat hunting strategies.
In this post, we'll cover the best threat hunting tools for 2024, focusing on how they empower organizations to enhance their security posture with greater visibility and responsiveness.
Quick Facts
Cyber threat hunting tools proactively detect and stop threats by continuously scanning and analyzing network data, not reactive security.
Good threat hunting tools have advanced analytics, machine learning, and threat intelligence integration to improve detection and response, alongside external threat intelligence to identify and mitigate potential security threats proactively.
Choosing the right threat hunting tool means assessing business needs, evaluating features, and ensuring compatibility with the existing security stack for threat mitigation.
What are Threat Hunting Tools?
Threat hunting tools are designed to detect and stop threats before they can do damage. Unlike traditional security that reacts to known threats, cyber threat hunting tools continuously scan, identify, log, nullify, and monitor the network for suspicious activity. With the rise of cyber attacks, we need proactive defense, these tools are a must-have in today's security landscape. A threat hunter uses these tools to get better at threat hunting.

These tools work by collecting and analyzing different types of data, logs, events, endpoint telemetry, and network traffic. Using security analytics they identify unknown threats by statistical patterns. This proactive search and identification process is what differentiates threat hunting tools from other security. The threat hunting process is crucial in enhancing security analysis by integrating various open-source security tools effectively.
Using multiple threat hunting tools gives you the best chance of stopping cyber attacks. Each tool has unique capabilities and together they make a strong defense. Advanced threat hunting tools give you an extra layer of security against threats, so you have coverage across all surfaces.
Also, these tools give you attack analysis, so security teams can understand the threat and where it came from. This security data is key to developing countermeasures and overall security posture. By addressing threats proactively you can reduce the risk of security incidents and data breaches.
Features of Good Threat Hunting Tools
Good threat hunting tools should provide comprehensive coverage and capabilities to improve detection and response and stay ahead of emerging threats. Three key features that define good threat hunting tools are advanced analytics, machine learning, and threat intelligence integration.
Advanced analytics allows you to analyze large amounts of data to find patterns of threats. This is key to identifying unknown threats and real-time threat intelligence.
Machine learning and AI help in threat detection by automating network data analysis and identifying anomalies that indicate threats. Integrating with threat intelligence platforms allows automated gathering and analysis of threat data so you can respond faster and have comprehensive threat analysis.
Advanced Analytics
Advanced analytics is key in threat hunting. It analyzes data at scale from multiple sources to proactively detect attacks. A good threat hunting tool should be able to monitor multiple data sources for overall security visibility. This includes real-time monitoring and advanced threat detection capabilities to identify and stop threats before they can do damage.
Advanced analytics gives security analysts visibility into threats so they can identify and respond. This proactive detection approach keeps you ahead of advanced and emerging threats and a strong security posture.
Machine Learning
Machine learning improves threat detection by automating network data analysis and identifying anomalies that indicate threats. Tools like these have features like network forensics, NIDS (Network Intrusion Detection System), and DNS domain classification which all contribute to its threat detection capabilities.
Machine learning tools are further improved by support for multiple languages like Python, Ruby, Java, and Lua. This allows for easy integration and deployment in different environments so organizations can deploy these tools and improve their threat hunting.
Threat Intelligence Integration
Integrating threat intelligence into threat hunting tools is key to comprehensive threat analysis so you can stay ahead of attacks. Seamless connections to multiple sources through integration allow threat hunting tools to identify and respond to threats faster.
Customization options allow security teams to tailor the threat intelligence integration according to their needs so the tools can provide real-time threat intelligence and actionable insights to detect and mitigate security threats.
Data Collection and Analysis for Threat Detection
Data collection and analysis are crucial components of threat detection in threat hunting. Threat hunting tools gather and aggregate vast amounts of data from various sources, such as logs, events, endpoint telemetry, and network traffic. This data is then analyzed using advanced analytics and machine learning to identify unusual patterns and anomalies that may indicate potential security threats. By leveraging data collection and analysis, threat hunters can gain a deeper understanding of their organization's security posture and identify potential threats before they become incidents.
Effective data collection and analysis for threat detection involve several key steps:
Data Collection: Gathering data from various sources, including logs, events, endpoint telemetry, and network traffic.
Data Aggregation: Combining data from multiple sources into a single, unified view.
Data Analysis: Using advanced analytics and machine learning to identify unusual patterns and anomalies in the data.
Threat Identification: Identifying potential security threats based on the analysis of the data.
By following these steps, threat hunters can use data collection and analysis to detect potential security threats and prevent incidents. This proactive approach ensures that security teams are always one step ahead of cyber threats, enhancing the overall security posture of the organization.
Proactive Search and Identification of Cyber Threats
Proactive search and identification of cyber threats is a critical component of threat hunting. Threat hunting tools use advanced analytics and machine learning to proactively search for potential security threats in an organization's network and systems. This involves analyzing data from various sources, such as logs, events, endpoint telemetry, and network traffic, to identify unusual patterns and anomalies that may indicate potential security threats.
Effective proactive search and identification of cyber threats involve several key steps:
Threat Intelligence: Gathering and analyzing threat intelligence from various sources, including external threat feeds and internal security data.
Anomaly Detection: Using advanced analytics and machine learning to identify unusual patterns and anomalies in the data.
Threat Identification: Identifying potential security threats based on the analysis of the data.
Incident Response: Responding to identified threats and preventing incidents.
By following these steps, threat hunters can proactively search for and identify potential security threats, preventing incidents and protecting their organization's security. This proactive approach ensures that security teams are always vigilant and ready to respond to emerging threats, enhancing the overall security posture of the organization.
A great example of proactive threat hunting was the discovery of SuperShell and Cobalt Strike malware during a scan of public infrastructure. By analyzing suspicious files and traffic, Hunt.io researchers identified malicious infrastructure, including command-and-control servers.

This approach demonstrates how continuous monitoring, anomaly detection, and real-time data analysis enable organizations to stay ahead of potential threats and mitigate risks before attackers can escalate their operations
Behavioral Analysis
Behavioral analysis is a critical component of threat hunting. Threat hunting tools use behavioral analysis to identify unusual patterns and anomalies in user and system behavior that may indicate potential security threats. This involves analyzing data from various sources, such as logs, events, endpoint telemetry, and network traffic, to identify behavior that is outside the norm.
Effective behavioral analysis involves several key steps:
Baseline Establishment: Establishing a baseline of normal user and system behavior.
Anomaly Detection: Using advanced analytics and machine learning to identify unusual patterns and anomalies in the data.
Threat Identification: Identifying potential security threats based on the analysis of the data.
Incident Response: Responding to identified threats and preventing incidents.
By following these steps, threat hunters can use behavioral analysis to identify potential security threats and prevent incidents. This approach allows security teams to detect insider threats and other sophisticated attacks that may bypass traditional security measures, enhancing the organization's overall security posture.
10 Popular Threat Hunting Tools in 2026
Here are the top threat hunting tools that stand out. These tools have advanced threat detection capabilities so you need proactive cybersecurity. Let's see the top threat hunting tools, each with its unique features.

APT-Hunter
APT-Hunter is designed to track advanced persistent threats through event log analysis. This tool created by Ahmed Khlief supports the Windows operating system and has robust features to identify and stop advanced threats.
Attacker KB
The Attacker Knowledge Base (KB) is a treasure trove of information that contains various exploits and attack methods so security teams can have insights for proactive threat detection and vulnerability management. By integrating Attacker KB insights, organizations can prioritize vulnerabilities based on exploit information and overall security posture.
Hunt SQL
Hunt SQL is our query language designed to make threat hunting more efficient and customizable. With Hunt SQL, you can easily extract and analyze data from our threat intelligence platform, allowing you to create precise queries that match your unique needs. Whether you're investigating indicators of compromise, suspicious domains, or malicious C2 server activity, Hunt SQL gives you the flexibility to dig deeper into the data.
This level of control is critical for identifying hidden threats and responding faster to potential attacks, streamlining your threat-hunting process and improving overall security defenses.
Automater
Automater is a tool that analyzes URLs and hashes for intrusion analysis so it's perfect for beginners in cybersecurity. This user-friendly and open-source tool is available on GitHub so it's a great starting point for those who are new to threat hunting.
CrowdFMS
CrowdFMS automates phishing email detection using VirusTotal's Private API. This automation makes threat detection and response faster so phishing attempts are detected and mitigated faster.
Cuckoo Sandbox
Cuckoo Sandbox is a customizable malware analysis tool that supports multiple file types and operating systems. By analyzing various file types Cuckoo Sandbox helps security teams understand malware behavior and plan countermeasures.
DeepBlue CLI
DeepBlue CLI can detect specific events in Windows logs. This tool can detect specific events in Windows event logs faster so threat detection and response are faster.
CyberChef
CyberChef is to help users encode and decode data and supports multiple formats. This tool is for technical and non-technical analysts and is licensed under Apache 2.0.
Phishing Catcher
Phishing Catcher detects phishing domains through TLS certificate checks. Written in Python, this tool uses a YAML configuration file and with default configuration, you can see immediate results without much setup.
Intercept.io Phishing API
Intercept.io offers rapid and accurate detection of phishing sites, empowering brands and MSSPs to safeguard their assets more effectively. By leveraging these automated analysis tools, you can quickly identify and neutralize phishing threats with high confidence.
Pick the Right Threat Hunting Tool for Your Business
Choosing the right threat hunting tool for your business is key to good cybersecurity. The first step is to know your business challenges and requirements. A tool's success in threat hunting depends on its compatibility with existing security setups and overall security posture.
A good threat hunting tool should provide centralized data management to give you complete visibility into your network and applications. Having a structured threat hunting methodology makes threat hunting more effective and better detection.
Identify Business Needs
Knowing your business needs helps you choose the right threat hunting solution. Knowing your business requirements is key to tailoring your threat hunting strategy to address your vulnerabilities. Knowing what threats are unique to your business allows security teams to focus on what matters most.
Check Features
Checking the features of threat hunting tools is important to align them with your business security goals. Advanced query and search are crucial for data analysis in these tools, also, aggregate threat data and automated processes make it more operational.
Consider Integration
A good threat hunting solution should integrate smoothly with existing security systems to make it more efficient. Integration with current security tools makes a threat hunting tool more effective by having complete coverage and data sharing.
Different providers aggregate threat data from multiple sources to automate response actions so security operations are more efficient.
Threat Hunting with User and Entity Behavior Analytics (UEBA)
Proactive threat hunting helps detect advanced threats that bypass automated cybersecurity measures. User and Entity Behavior Analytics (UEBA) tools create baseline behavioral profiles from entities to detect unusual activities, enabling the identification of insider threats. These tools monitor deviations from user behavior patterns to uncover potential risks.
Some of these solutions use machine learning to enhance threat detection, automatically identifying and analyzing anomalies to assist security professionals in spotting insider threats.
Other advanced threat-hunting tools combine UEBA with Identity and Access Management (IAM) for a deeper understanding of security risks. This integration provides complete visibility into security events and user behavior, improving threat detection capabilities.
Real-time alerts are crucial, as they enable early threat detection. The advanced analytics provide insights to identify threats proactively, enhancing team collaboration and response.
Open Source Intelligence (OSINT) in Threat Hunting
Open Source Intelligence (OSINT) is key to threat hunting. OSINT tools help analysts to collect and analyze data from publicly available sources to detect threats. These tools are for threat hunters to identify risks through publicly available data analysis.
The OSINT threat intelligence cycle is to determine the purpose, harvest data, categorize information and refine the analysis, so organizations can get timely and actionable insights.
Maltego
Maltego visualizes networks by showing relationships between domains, IP addresses, and other entities. Its analytical features allow users to dig deep into network relationships so they can identify threats and investigate cyber threats.
TheHarvester
TheHarvester is a reconnaissance tool that helps security professionals to gather publicly available information. It's good at finding subdomains associated with a domain so security assessments are more accurate. TheHarvester can also gather email addresses associated with a target domain so social engineering assessments can be done.
Best Practices for Threat Hunting
Best practices for threat hunting are key to having a strong cybersecurity posture. Undetected threats can stay in the network for about 280 days before it's discovered so threat hunting is proactive. Cyber threat hunters use their expertise to find hidden malware and suspicious activities (like C2 servers) that automated systems will miss, so continuous monitoring and regular updates are a must.
Train your employees to do threat hunting. Machine learning-driven tools can automate the triage of alerts so they can be prioritized for faster response and reduce false positives by understanding normal behavior patterns. Early threat detection includes behavioral analysis, UEBA, machine learning algorithms, and continuous monitoring.
Regular Updates and Patching
Keep your systems updated to minimize the risk of exploitation from known vulnerabilities. Regular system updates and patching reduce the risk of exploitation so security incidents are minimized.
Continuous Monitoring
Continuous monitoring is key to early threat detection and response in cybersecurity. Many tools use artificial intelligence for real-time threat detection, monitoring continuously to find hidden attackers.
Collaboration and Information Sharing
Sharing threat intelligence across organizations improves overall threat hunting. Collaborating with other organizations for information exchange strengthens threat detection and response to security incidents.
Related Questions
What are threat hunting tools?
Threat hunting tools are needed to detect and neutralize potential threats by scanning and monitoring the network. They help in finding and logging suspicious activities to enhance security.
Why threat hunting tools in 2024?
Threat hunting tools are needed in 2024 because of the increasing frequency and complexity of attacks, so organizations can detect and mitigate threats earlier. Using these tools is a proactive defense strategy that is necessary in this digital age.
How do advanced analytics help in threat hunting?
Advanced analytics helps in threat hunting by analyzing big data to find patterns that indicate potential threats so you can proactively identify and respond in time. This will strengthen your overall security posture.
What does machine learning do in threat detection?
Machine learning automates the analysis of network data to find anomalies that will enhance threat detection and overall security. This will strengthen threat detection.
How to choose the right threat hunting tool?
To choose the right threat hunting tool, organizations must define what they need, evaluate the key features, and see how the tool integrates with their existing security infrastructure. This will ensure the chosen tool will enhance their threat detection.
Conclusion
In summary, threat hunting tools are essential for detecting and neutralizing cyber threats. Key features such as advanced analytics, machine learning, and integration with threat intelligence make these tools more effective. The top threat hunting tools reviewed here offer unique features tailored to different security needs. When selecting the right tool for your organization, consider your specific requirements, evaluate key features, and ensure it integrates smoothly with your existing systems.
While free tools offer some advantages, relying on them may not always be the best option. Professional tools developed by companies typically provide advanced threat-hunting capabilities and support that many organizations value.
If you're ready to elevate your threat hunting efforts, book a demo with us to discover how our tools can help you achieve your threat detection goals.
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.





