Top 7 Threat Hunting Frameworks: Techniques and Best Practices (Updated 2026)
Published on Oct 23, 2025

At Hunt.io, we've spent years tracking live command and control (C2) servers, pivoting on odd anomalies, and surfacing attacker infrastructure hidden in plain sight. One thing has always stood out: without a solid framework, even the most experienced threat hunters lose time and visibility.
Threat hunting frameworks bring structure to that uncertainty. They help security teams detect threats that traditional security measures often miss. And in a world where a single breach can cost nearly $4.9 million on average (according to IBM's 2024 Cost of a Data Breach Report), structure isn't just helpful, it's non-negotiable.
The good news? Organizations are catching on. Industry research shows that 75% of companies now rely on threat intelligence regularly to strengthen their defenses, as stated by Fortune Business Insights. Frameworks are what make that intelligence actionable. They reduce dwell time, expose threats, and allow teams to act before damage is done.
In this post, we'll walk you through the top threat hunting frameworks, the hunting process they support, and how to apply them in 2026. Whether you're just getting started or refining your threat hunting techniques, this guide will help.
Understanding Threat Hunting Frameworks

Threat hunting frameworks give shape to a complex task. They define how the threat hunting process unfolds, from building an initial hypothesis to analyzing data and validating results.
According to ChaosSearch, threat hunting frameworks "help security teams focus the threat hunt process on uncovering traces of the most meaningful activity patterns."
By using them, security teams ensure that hunting activities are systematic and repeatable. This is essential when your goal is to uncover hidden threats, particularly those that involve lateral movement or data exfiltration.
The best frameworks are built to evolve. They incorporate lessons learned from past investigations, adapt to new tactics, techniques, and procedures (TTPs), and integrate threat intelligence reports. Whether your team is small or operating across cloud environments, a good framework brings consistency and focus.
With a clear understanding of why threat hunting frameworks matter, let's explore the core elements that make these frameworks truly effective in practice.
What Makes a Solid Threat Hunting Framework?

Every successful threat hunting program rests on three pillars: structure, context, and coordination. Let's see what each one implies:
Structure defines roles, data sources, and workflows. It ensures that threat hunting activities are consistent across teams and aligned with the organization's specific risk profile.
Context gives depth to your findings. Without it, threat hunters waste time chasing false positives. Frameworks help provide that context by incorporating threat intelligence, normal behavior baselines, and historical patterns.
Coordination ensures the process scales. When security teams speak the same language and use the same playbooks, it is easier to connect signals across cloud infrastructure, endpoints, and network traffic.
Now that we've identified the key pillars of a strong threat hunting framework, let's take a closer look at some of the most widely adopted frameworks in the industry.
Popular Threat Hunting Frameworks
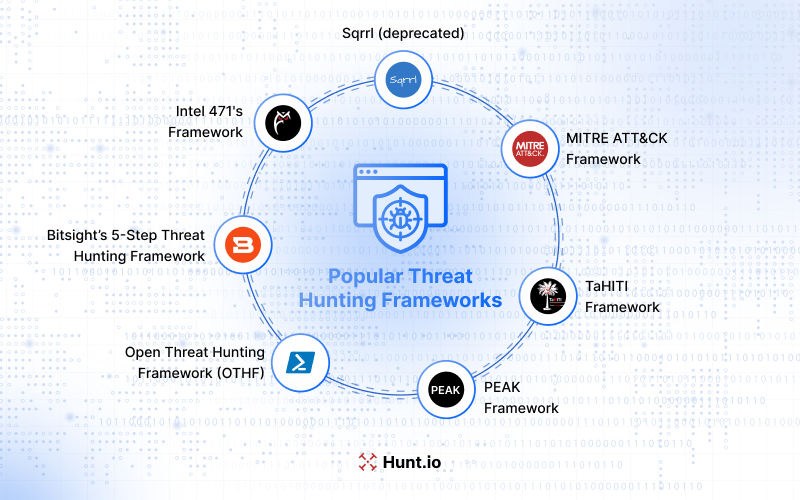
Several widely adopted frameworks support different aspects of the threat hunting process. Each offers a structured approach for improving threat detection and response.
MITRE ATT&CK Framework
MITRE ATT&CK is one of the most trusted frameworks in the industry. It breaks down attacker behavior into tactics, techniques, and procedures, giving threat hunters a blueprint to guide investigations.
Security teams use it to test hypotheses, align alerts with known threats, and strengthen their hunting process. It supports structured threat hunting by helping teams identify and respond to potential threats with greater precision.

Bitsight's 5-Step Threat Hunting Framework
BitSight's 5-Step Framework advocates for proactive, hypothesis-driven threat hunting, where hunters test theories based on current threat intelligence. This approach uncovers hidden threats that traditional tools might miss. It also stresses prioritizing hunts using intelligence to focus on emerging threats or specific attacker tactics.
This framework also highlights the importance of understanding baseline behaviors to quickly spot deviations and recommends enriching data with behavioral analytics to provide more context for better detection. The goal is to make threat hunting more targeted, efficient, and integrated into an organization's security processes.
Open Threat Hunting Framework (OTHF)
The Open Threat Hunting Framework (OTHF) is a flexible, community-driven approach designed to help security teams find hidden threats faster. By providing a clear structure for collecting and analyzing data, threat hunting becomes more organized and repeatable.
OTHF encourages collaboration and sharing of techniques, so teams can stay ahead of attackers with smarter, more efficient investigations. It's a great tool for anyone serious about proactive security.
.png)
Intel 471
Intel 471's Framework provides a structured, intelligence-driven approach to proactively detect threats that evade traditional defenses. Built around behavioral analysis, it helps reduce adversary dwell time through hypothesis-driven investigations and continuous improvement of detection capabilities.
Central to the framework is Intel 471's platform, offering pre-validated hunt packages and dashboards that accelerate and scale hunts across major EDR, SIEM, and XDR tools.

TaHITI Framework
The TaHITI framework begins with threat intelligence. Rather than starting blind, teams use known indicators, threat intelligence feeds, and historical data to guide the hunt.
Its connection with platforms like ChaosLake DB helps correlate existing threats with past attacker behavior. This makes threat hunting more efficient and aligns teams around a more comprehensive understanding of what is happening in their environment.

PEAK Framework
PEAK is a hunting framework that focuses on program maturity. It helps organizations prioritize hunting techniques, measure progress, and ensure that the hunting process is scalable and sustainable.
What sets PEAK apart is its structured approach to aligning hunt activities with business risk and operational reality. Rather than just throwing detections at a SIEM, PEAK encourages organizations to develop repeatable hunting processes that evolve alongside the threat landscape and internal capabilities.

Sqrrl (deprecated)
As an honorable mention, Sqrrl was once a powerful threat hunting platform known for its strong analytics and graph-based approach to uncovering threats. Although it no longer exists as an independent product, Sqrrl's ideas and innovations have influenced modern threat hunting tools, helping shape how security teams connect the dots and detect complex attack patterns today. Its legacy lives on in the field.
.png)
Having reviewed some of the leading frameworks, the next step is to understand how to effectively implement and tailor these models to fit your organization's unique environment and needs.
Best Practices for Implementing Threat Hunting Frameworks
To implement a framework effectively, it must match your environment. Start with a clear understanding of your threat landscape, then select a model that fits your infrastructure, tools, and goals.
More organizations are finding success by customizing frameworks to their needs, aligning them with threat hunting methodologies, and building internal playbooks that support detection and response.
Incorporating contextual information from past hunts and using threat intelligence reports strengthens each cycle. Teams should document lessons learned after each hunt to improve the next one.
Wrapping up
Threat hunting frameworks are essential for modern cybersecurity, offering structure and consistency to a process that often involves uncovering deeply hidden threats. Whether your team is scaling operations or starting from scratch, these frameworks can help reduce dwell time, cut false positives, and improve your security posture.
Put Frameworks into Action with Hunt.io
Use what you’ve just learned, apply top frameworks like ATT&CK, PEAK, and OTHF directly inside our platform. Book your demo now and see how Hunt.io supports structured threat hunting with real-time infrastructure detection and hypothesis-driven workflows.
At Hunt.io, we've spent years tracking live command and control (C2) servers, pivoting on odd anomalies, and surfacing attacker infrastructure hidden in plain sight. One thing has always stood out: without a solid framework, even the most experienced threat hunters lose time and visibility.
Threat hunting frameworks bring structure to that uncertainty. They help security teams detect threats that traditional security measures often miss. And in a world where a single breach can cost nearly $4.9 million on average (according to IBM's 2024 Cost of a Data Breach Report), structure isn't just helpful, it's non-negotiable.
The good news? Organizations are catching on. Industry research shows that 75% of companies now rely on threat intelligence regularly to strengthen their defenses, as stated by Fortune Business Insights. Frameworks are what make that intelligence actionable. They reduce dwell time, expose threats, and allow teams to act before damage is done.
In this post, we'll walk you through the top threat hunting frameworks, the hunting process they support, and how to apply them in 2026. Whether you're just getting started or refining your threat hunting techniques, this guide will help.
Understanding Threat Hunting Frameworks

Threat hunting frameworks give shape to a complex task. They define how the threat hunting process unfolds, from building an initial hypothesis to analyzing data and validating results.
According to ChaosSearch, threat hunting frameworks "help security teams focus the threat hunt process on uncovering traces of the most meaningful activity patterns."
By using them, security teams ensure that hunting activities are systematic and repeatable. This is essential when your goal is to uncover hidden threats, particularly those that involve lateral movement or data exfiltration.
The best frameworks are built to evolve. They incorporate lessons learned from past investigations, adapt to new tactics, techniques, and procedures (TTPs), and integrate threat intelligence reports. Whether your team is small or operating across cloud environments, a good framework brings consistency and focus.
With a clear understanding of why threat hunting frameworks matter, let's explore the core elements that make these frameworks truly effective in practice.
What Makes a Solid Threat Hunting Framework?

Every successful threat hunting program rests on three pillars: structure, context, and coordination. Let's see what each one implies:
Structure defines roles, data sources, and workflows. It ensures that threat hunting activities are consistent across teams and aligned with the organization's specific risk profile.
Context gives depth to your findings. Without it, threat hunters waste time chasing false positives. Frameworks help provide that context by incorporating threat intelligence, normal behavior baselines, and historical patterns.
Coordination ensures the process scales. When security teams speak the same language and use the same playbooks, it is easier to connect signals across cloud infrastructure, endpoints, and network traffic.
Now that we've identified the key pillars of a strong threat hunting framework, let's take a closer look at some of the most widely adopted frameworks in the industry.
Popular Threat Hunting Frameworks

Several widely adopted frameworks support different aspects of the threat hunting process. Each offers a structured approach for improving threat detection and response.
MITRE ATT&CK Framework
MITRE ATT&CK is one of the most trusted frameworks in the industry. It breaks down attacker behavior into tactics, techniques, and procedures, giving threat hunters a blueprint to guide investigations.
Security teams use it to test hypotheses, align alerts with known threats, and strengthen their hunting process. It supports structured threat hunting by helping teams identify and respond to potential threats with greater precision.

Bitsight's 5-Step Threat Hunting Framework
BitSight's 5-Step Framework advocates for proactive, hypothesis-driven threat hunting, where hunters test theories based on current threat intelligence. This approach uncovers hidden threats that traditional tools might miss. It also stresses prioritizing hunts using intelligence to focus on emerging threats or specific attacker tactics.
This framework also highlights the importance of understanding baseline behaviors to quickly spot deviations and recommends enriching data with behavioral analytics to provide more context for better detection. The goal is to make threat hunting more targeted, efficient, and integrated into an organization's security processes.

Open Threat Hunting Framework (OTHF)
The Open Threat Hunting Framework (OTHF) is a flexible, community-driven approach designed to help security teams find hidden threats faster. By providing a clear structure for collecting and analyzing data, threat hunting becomes more organized and repeatable.
OTHF encourages collaboration and sharing of techniques, so teams can stay ahead of attackers with smarter, more efficient investigations. It's a great tool for anyone serious about proactive security.
.png)
Intel 471
Intel 471's Framework provides a structured, intelligence-driven approach to proactively detect threats that evade traditional defenses. Built around behavioral analysis, it helps reduce adversary dwell time through hypothesis-driven investigations and continuous improvement of detection capabilities.
Central to the framework is Intel 471's platform, offering pre-validated hunt packages and dashboards that accelerate and scale hunts across major EDR, SIEM, and XDR tools.

TaHITI Framework
The TaHITI framework begins with threat intelligence. Rather than starting blind, teams use known indicators, threat intelligence feeds, and historical data to guide the hunt.
Its connection with platforms like ChaosLake DB helps correlate existing threats with past attacker behavior. This makes threat hunting more efficient and aligns teams around a more comprehensive understanding of what is happening in their environment.

PEAK Framework
PEAK is a hunting framework that focuses on program maturity. It helps organizations prioritize hunting techniques, measure progress, and ensure that the hunting process is scalable and sustainable.
What sets PEAK apart is its structured approach to aligning hunt activities with business risk and operational reality. Rather than just throwing detections at a SIEM, PEAK encourages organizations to develop repeatable hunting processes that evolve alongside the threat landscape and internal capabilities.

Sqrrl (deprecated)
As an honorable mention, Sqrrl was once a powerful threat hunting platform known for its strong analytics and graph-based approach to uncovering threats. Although it no longer exists as an independent product, Sqrrl's ideas and innovations have influenced modern threat hunting tools, helping shape how security teams connect the dots and detect complex attack patterns today. Its legacy lives on in the field.
.png)
Having reviewed some of the leading frameworks, the next step is to understand how to effectively implement and tailor these models to fit your organization's unique environment and needs.
Best Practices for Implementing Threat Hunting Frameworks
To implement a framework effectively, it must match your environment. Start with a clear understanding of your threat landscape, then select a model that fits your infrastructure, tools, and goals.
More organizations are finding success by customizing frameworks to their needs, aligning them with threat hunting methodologies, and building internal playbooks that support detection and response.
Incorporating contextual information from past hunts and using threat intelligence reports strengthens each cycle. Teams should document lessons learned after each hunt to improve the next one.
Wrapping up
Threat hunting frameworks are essential for modern cybersecurity, offering structure and consistency to a process that often involves uncovering deeply hidden threats. Whether your team is scaling operations or starting from scratch, these frameworks can help reduce dwell time, cut false positives, and improve your security posture.
Put Frameworks into Action with Hunt.io
Use what you’ve just learned, apply top frameworks like ATT&CK, PEAK, and OTHF directly inside our platform. Book your demo now and see how Hunt.io supports structured threat hunting with real-time infrastructure detection and hypothesis-driven workflows.
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.





