Splunk Threat Hunting: A Beginner’s Guide with Hunt.io Feeds
Published on Oct 23, 2025

Threat hunting in Splunk is about connecting logs, alerts, and external intelligence to find malicious behavior. While Splunk offers powerful search and correlation, the quality of results depends on the data sources you bring in. According to the SANS 2024 Threat Hunting Survey, 51% of organizations now have formally defined threat hunting methodologies, up from 35% last year, which underlines how critical structure and live intel are for modern threat detection.
The Hunt.io Splunk Addon is a third-party integration that brings live command and control (C2) infrastructure and enriched IOC feeds into Splunk. This gives security teams and organizations up-to-date visibility into attacker infrastructure and supports faster investigations without leaving their Splunk environment.
If you are just getting ready to begin with Splunk threat hunting, this guide outlines a simple, accurate path. To make the most of Splunk, it helps to start with the basics before looking at frameworks and tools.
Splunk Threat Hunting Basics
Splunk can process large volumes of data and correlate across systems, but Splunk Threat Hunting depends on the quality of the intelligence you add. With the Hunt.io integration, hunts are powered by live C2 and IOC feeds instead of stale indicators. But for threat hunting to be effective, the intelligence must be accurate and current.
Relying only on open-source data sources can introduce noise, false positives, and stale indicators. Hunt.io reduces this problem by providing curated, high-fidelity C2 and IOC feeds that are automatically updated inside Splunk. This lets analysts focus on mitigating security risks rather than chasing outdated alerts.
These fundamentals lay the groundwork for structured threat hunts, which are best approached through a clear framework. That's where best practices and proven frameworks come into play.
Threat Hunting Framework: Applying Best Practices
Using a solid threat hunting framework ensures hunts are structured, repeatable, and focused on outcomes rather than ad-hoc queries. Here's how to apply best practices in Splunk using Hunt.io's third-party addon:
1. Set Clear Objectives
Every hunt should start with a defined hypothesis. Many teams use MITRE ATT&CK as their North Star because it organizes adversary behaviors into techniques and tactics. Without an objective, hunts risk becoming a random search activity that wastes effort.
2. Choose the Right Data Sources
Not all data sources are equal. OSINT can provide broad coverage, but it often suffers from stale or noisy indicators.
Commercial feeds like Hunt.io's are curated, frequently updated, and focused on active attacker infrastructure. Inside Splunk, the IOC Hunter dashboard and C2 feed dashboard give you direct access to these feeds, so your correlation work stays accurate and efficient.
Hunt.io delivers high-fidelity C2 infrastructure data designed for security operations teams that need reliability at scale:
Actor-linked detections that connect infrastructure back to adversary activity
Coverage of 150+ malware techniques to track real attack methods
Daily-validated intelligence to cut down false positives
Built for integration and scale, so it works seamlessly inside Splunk
Attackers also abuse legitimate services as a malware delivery platform, which makes curated feeds especially helpful for organizations under pressure.
3. Apply the PEAK Threat Hunting Framework
The PEAK Threat Hunting Framework (Prepare, Execute, and Act on Knowledge) brings structure to hunts:
Prepare - configure your Hunt.io API key so feeds update automatically in Splunk.
Execute - use dashboards and the provided saved queries to validate your hypothesis against Hunt.io feeds.
Act - enrich alerts, confirm suspicious activity, and escalate findings to incident response.
By following the PEAK threat hunting framework in Splunk, you align threat intelligence feeds with real security operations.
4. Track Metrics and Monitoring
A strong framework includes metrics. Track the number of hunts performed, how many detections were confirmed, and how much noise was reduced. Splunk dashboards make it easier to visualize events and see where hypotheses are paying off.
5. Document Runbooks and Creation Standards
When a hunt produces good results, document the steps. Save effective queries as Splunk Saved Searches, and record the fields or indicators that proved useful. Standardizing runbook creation ensures other analysts can repeat the hunt with consistency.
6. Commit to Continuous Improvement
Hunting is iterative. After each cycle, review what worked, identify gaps, and feed the lessons back into your framework. Over time, this continuous improvement cycle sharpens detection coverage and strengthens how your security operations team responds to threats.
With a framework in place, the next step is bringing it into action with Splunk Addons.
Splunk Addons: Extending Threat Hunting with Hunt.io
Splunk Addons extend Splunk with purpose-built applications, dashboards, and integrations.
The Hunt.io Splunk integration delivers:
C2 feed dashboard: visibility into Hunt.io's live C2 feed with useful metrics.
IOC Hunter dashboard: compare your Splunk logs with Hunt.io's enriched IOC content and fields.
Automatic updates: feeds refresh on a daily basis, without manual input.
Saved Searches: prebuilt searches to correlate Hunt.io intelligence with your Splunk events.
These features save you from building everything from scratch and act as building blocks that enhance threat hunting inside Splunk.
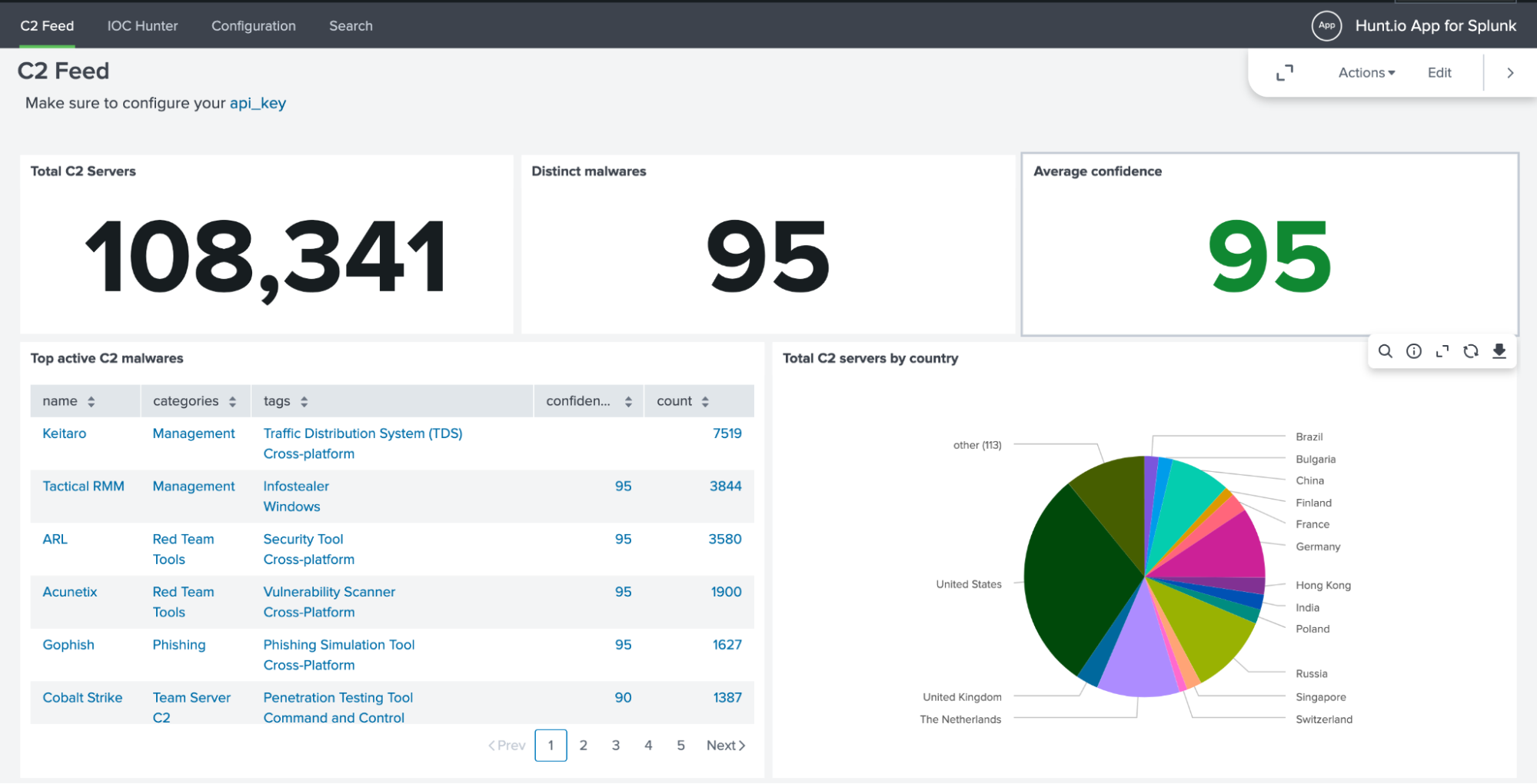
These building blocks make it easier to run hunts that align with your framework. The real value emerges once you start applying them in live Splunk searches.
Threat Hunting with Splunk and Hunt.io
Once installed, the Hunt.io integration connects your Splunk searches with curated intelligence. Instead of chasing stale indicators, you can validate activity against Hunt.io's live C2 and IOC feeds.
Example workflow:
Review outbound traffic (e.g., HTTP or TCP) in your logs for items of interest.
Use the IOC Hunter dashboard to check whether those indicators appear in Hunt.io's IOC feed.
Verify potential threats in the C2 feed dashboard to see if the activity maps to known attacker infrastructure.
Run the provided Saved Searches to enrich events and confirm what requires action.
When needed, pivot automatically on IPs or domains into the Hunt.io web interface for deeper context.
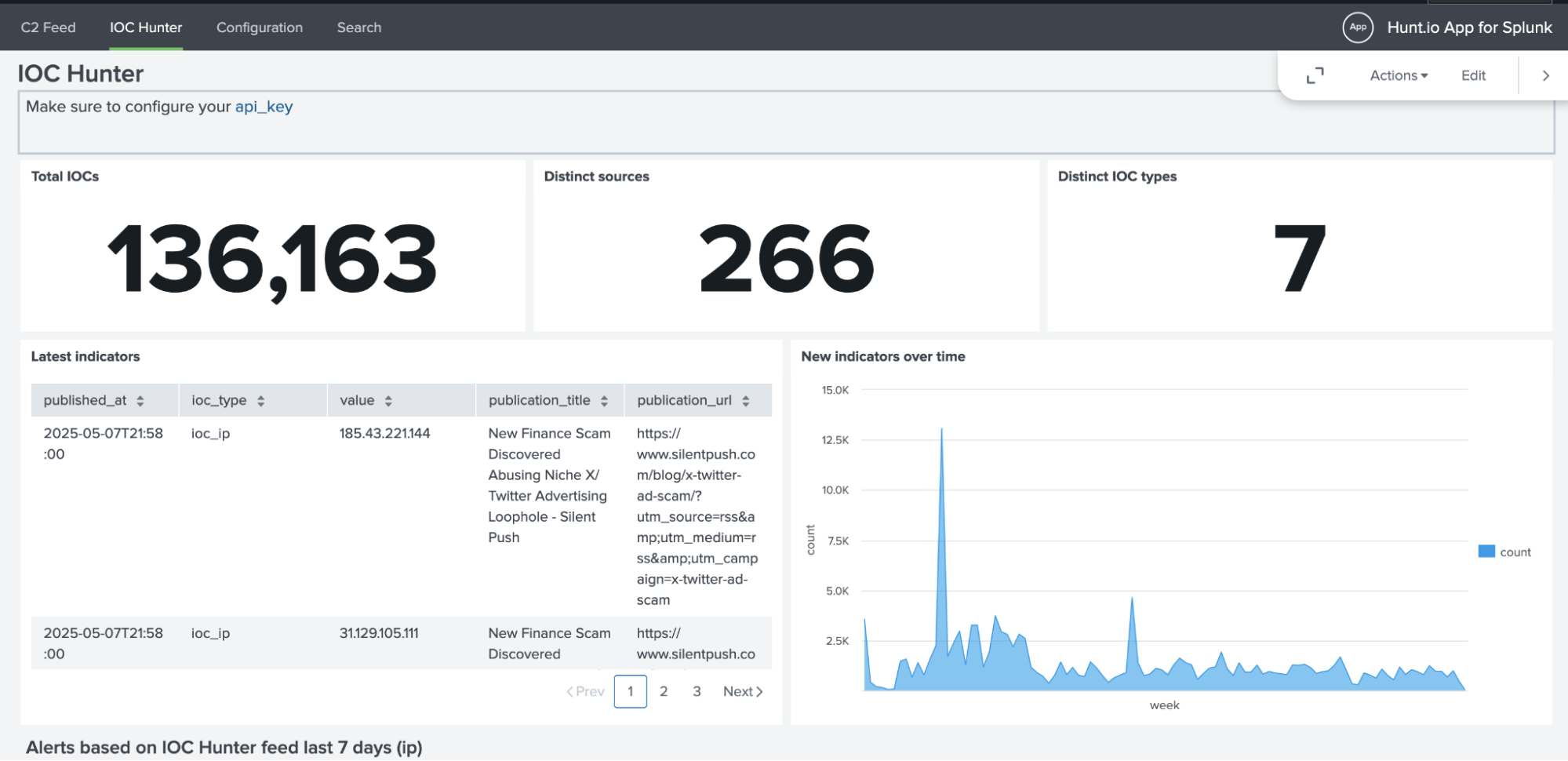
This process helps teams:
Detect active attacker infrastructure through the C2 feed dashboard.
Validate alerts by cross-referencing with enriched IOC data.
Repeat hunts reliably with prebuilt Saved Searches.
The balance of structured searches, scalable dashboards, and curated intelligence makes hunts repeatable and defensible inside Splunk. Keeping correlation tied to clear hypotheses ensures noise stays manageable for small and large teams alike, delivering insights that matter.
Getting Started with the Hunt.io Splunk App
Requirements
The Hunt.io App for Splunk contains detection rules that will match the indicators from Hunt.io with the data in your environment. In order to use these detections, you need to install and configure the Common Information Model (CIM). Make sure to enable the Network_Traffic and Web data model.
Splunk Enterprise Installation
Contact salesops@hunt.io to obtain a Hunt.io API key.
Top menu: click on 'Apps', then on 'Find more apps'
Search for "Hunt.io" - click on "Install"
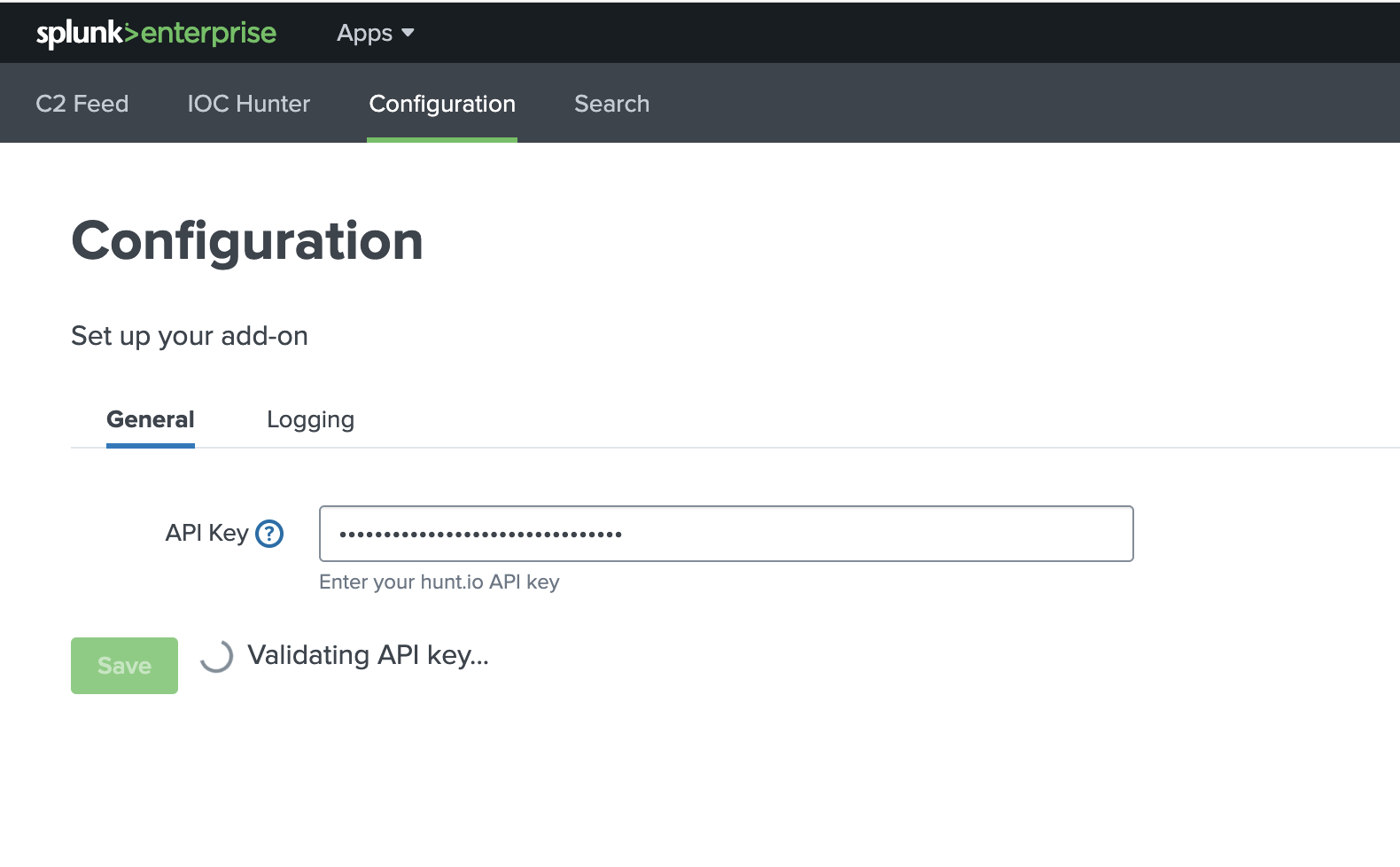
In Splunk, open the Hunt.io app's Configuration tab.
Enter your key and click Save.
Wait for validation to complete; remember to check that dashboards populate
Once your API key is validated, you should see this message:
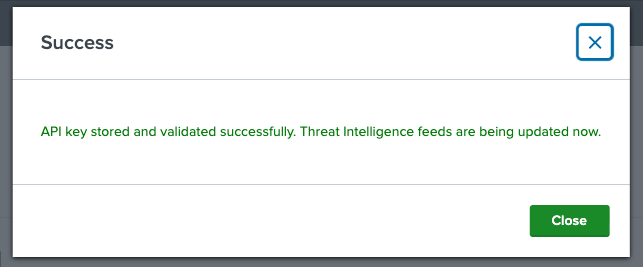
Immediately after that, you should see data flowing automatically in the "C2 Feeds" and "IOC Hunter" tabs
.png)
Splunk Cloud Installation
Log in to Splunk Web.
Go to Apps > Manage Apps > Browse more apps.
Search for Hunt.io and click Install.
Provide your Splunkbase credentials to continue.
In Splunk, open the Hunt.io app's Configuration tab.
Enter your key and click Save.
Wait for validation to complete
Once your API key is validated, you should see data flowing automatically in the "C2 Feeds" and "IOC Hunter" tabs.
With the addon installed, you can move from setup to action - turning Splunk into a high-fidelity hunting platform enhanced with Hunt.io intelligence.
Troubleshooting
If dashboards are empty, ensure the API key is valid and that feed inputs are properly scheduled.
If alerts based on saved searches in the C2 and IOC Hunter tabs are empty, it usually means there is no matching IOC data in the Hunt.io C2 or IOC Hunter datasets. These cards are populated based on network activity logs in your Splunk environment that match those IOCs. For example, if Hunt.io provides an IOC with a malicious IP such as 1.2.3.4, Splunk must contain a log with that same IP, normalized to the Network CIM data model, for it to appear in the alert cards.
👉 Download the Hunt.io Splunk Addon today to see how it works alongside Splunk in your workflows.
Summary
Splunk provides the scale and search power, but threat hunting depends on the quality of intelligence. The Hunt.io integration brings curated C2 and IOC feeds into Splunk environments, helping teams detect live threats and reduce noise.
Built independently by Hunt.io, the integration plugs seamlessly into Splunk, pairing Splunk's correlation engine with Hunt.io's high-fidelity feeds to give security operations a clearer view of attacker infrastructure - so your team can focus on real threats instead of wasting time on noise.
With Splunk's scale and Hunt.io's intelligence, your team can focus on detecting live threats, validating alerts, and staying ahead of adversaries.
Threat hunting in Splunk is about connecting logs, alerts, and external intelligence to find malicious behavior. While Splunk offers powerful search and correlation, the quality of results depends on the data sources you bring in. According to the SANS 2024 Threat Hunting Survey, 51% of organizations now have formally defined threat hunting methodologies, up from 35% last year, which underlines how critical structure and live intel are for modern threat detection.
The Hunt.io Splunk Addon is a third-party integration that brings live command and control (C2) infrastructure and enriched IOC feeds into Splunk. This gives security teams and organizations up-to-date visibility into attacker infrastructure and supports faster investigations without leaving their Splunk environment.
If you are just getting ready to begin with Splunk threat hunting, this guide outlines a simple, accurate path. To make the most of Splunk, it helps to start with the basics before looking at frameworks and tools.
Splunk Threat Hunting Basics
Splunk can process large volumes of data and correlate across systems, but Splunk Threat Hunting depends on the quality of the intelligence you add. With the Hunt.io integration, hunts are powered by live C2 and IOC feeds instead of stale indicators. But for threat hunting to be effective, the intelligence must be accurate and current.
Relying only on open-source data sources can introduce noise, false positives, and stale indicators. Hunt.io reduces this problem by providing curated, high-fidelity C2 and IOC feeds that are automatically updated inside Splunk. This lets analysts focus on mitigating security risks rather than chasing outdated alerts.
These fundamentals lay the groundwork for structured threat hunts, which are best approached through a clear framework. That's where best practices and proven frameworks come into play.
Threat Hunting Framework: Applying Best Practices
Using a solid threat hunting framework ensures hunts are structured, repeatable, and focused on outcomes rather than ad-hoc queries. Here's how to apply best practices in Splunk using Hunt.io's third-party addon:
1. Set Clear Objectives
Every hunt should start with a defined hypothesis. Many teams use MITRE ATT&CK as their North Star because it organizes adversary behaviors into techniques and tactics. Without an objective, hunts risk becoming a random search activity that wastes effort.
2. Choose the Right Data Sources
Not all data sources are equal. OSINT can provide broad coverage, but it often suffers from stale or noisy indicators.
Commercial feeds like Hunt.io's are curated, frequently updated, and focused on active attacker infrastructure. Inside Splunk, the IOC Hunter dashboard and C2 feed dashboard give you direct access to these feeds, so your correlation work stays accurate and efficient.
Hunt.io delivers high-fidelity C2 infrastructure data designed for security operations teams that need reliability at scale:
Actor-linked detections that connect infrastructure back to adversary activity
Coverage of 150+ malware techniques to track real attack methods
Daily-validated intelligence to cut down false positives
Built for integration and scale, so it works seamlessly inside Splunk
Attackers also abuse legitimate services as a malware delivery platform, which makes curated feeds especially helpful for organizations under pressure.
3. Apply the PEAK Threat Hunting Framework
The PEAK Threat Hunting Framework (Prepare, Execute, and Act on Knowledge) brings structure to hunts:
Prepare - configure your Hunt.io API key so feeds update automatically in Splunk.
Execute - use dashboards and the provided saved queries to validate your hypothesis against Hunt.io feeds.
Act - enrich alerts, confirm suspicious activity, and escalate findings to incident response.
By following the PEAK threat hunting framework in Splunk, you align threat intelligence feeds with real security operations.
4. Track Metrics and Monitoring
A strong framework includes metrics. Track the number of hunts performed, how many detections were confirmed, and how much noise was reduced. Splunk dashboards make it easier to visualize events and see where hypotheses are paying off.
5. Document Runbooks and Creation Standards
When a hunt produces good results, document the steps. Save effective queries as Splunk Saved Searches, and record the fields or indicators that proved useful. Standardizing runbook creation ensures other analysts can repeat the hunt with consistency.
6. Commit to Continuous Improvement
Hunting is iterative. After each cycle, review what worked, identify gaps, and feed the lessons back into your framework. Over time, this continuous improvement cycle sharpens detection coverage and strengthens how your security operations team responds to threats.
With a framework in place, the next step is bringing it into action with Splunk Addons.
Splunk Addons: Extending Threat Hunting with Hunt.io
Splunk Addons extend Splunk with purpose-built applications, dashboards, and integrations.
The Hunt.io Splunk integration delivers:
C2 feed dashboard: visibility into Hunt.io's live C2 feed with useful metrics.
IOC Hunter dashboard: compare your Splunk logs with Hunt.io's enriched IOC content and fields.
Automatic updates: feeds refresh on a daily basis, without manual input.
Saved Searches: prebuilt searches to correlate Hunt.io intelligence with your Splunk events.
These features save you from building everything from scratch and act as building blocks that enhance threat hunting inside Splunk.

These building blocks make it easier to run hunts that align with your framework. The real value emerges once you start applying them in live Splunk searches.
Threat Hunting with Splunk and Hunt.io
Once installed, the Hunt.io integration connects your Splunk searches with curated intelligence. Instead of chasing stale indicators, you can validate activity against Hunt.io's live C2 and IOC feeds.
Example workflow:
Review outbound traffic (e.g., HTTP or TCP) in your logs for items of interest.
Use the IOC Hunter dashboard to check whether those indicators appear in Hunt.io's IOC feed.
Verify potential threats in the C2 feed dashboard to see if the activity maps to known attacker infrastructure.
Run the provided Saved Searches to enrich events and confirm what requires action.
When needed, pivot automatically on IPs or domains into the Hunt.io web interface for deeper context.

This process helps teams:
Detect active attacker infrastructure through the C2 feed dashboard.
Validate alerts by cross-referencing with enriched IOC data.
Repeat hunts reliably with prebuilt Saved Searches.
The balance of structured searches, scalable dashboards, and curated intelligence makes hunts repeatable and defensible inside Splunk. Keeping correlation tied to clear hypotheses ensures noise stays manageable for small and large teams alike, delivering insights that matter.
Getting Started with the Hunt.io Splunk App
Requirements
The Hunt.io App for Splunk contains detection rules that will match the indicators from Hunt.io with the data in your environment. In order to use these detections, you need to install and configure the Common Information Model (CIM). Make sure to enable the Network_Traffic and Web data model.
Splunk Enterprise Installation
Contact salesops@hunt.io to obtain a Hunt.io API key.
Top menu: click on 'Apps', then on 'Find more apps'
Search for "Hunt.io" - click on "Install"
In Splunk, open the Hunt.io app's Configuration tab.
Enter your key and click Save.
Wait for validation to complete; remember to check that dashboards populate

Once your API key is validated, you should see this message:

Immediately after that, you should see data flowing automatically in the "C2 Feeds" and "IOC Hunter" tabs
.png)
Splunk Cloud Installation
Log in to Splunk Web.
Go to Apps > Manage Apps > Browse more apps.
Search for Hunt.io and click Install.
Provide your Splunkbase credentials to continue.
In Splunk, open the Hunt.io app's Configuration tab.
Enter your key and click Save.
Wait for validation to complete
Once your API key is validated, you should see data flowing automatically in the "C2 Feeds" and "IOC Hunter" tabs.
With the addon installed, you can move from setup to action - turning Splunk into a high-fidelity hunting platform enhanced with Hunt.io intelligence.
Troubleshooting
If dashboards are empty, ensure the API key is valid and that feed inputs are properly scheduled.
If alerts based on saved searches in the C2 and IOC Hunter tabs are empty, it usually means there is no matching IOC data in the Hunt.io C2 or IOC Hunter datasets. These cards are populated based on network activity logs in your Splunk environment that match those IOCs. For example, if Hunt.io provides an IOC with a malicious IP such as 1.2.3.4, Splunk must contain a log with that same IP, normalized to the Network CIM data model, for it to appear in the alert cards.
👉 Download the Hunt.io Splunk Addon today to see how it works alongside Splunk in your workflows.
Summary
Splunk provides the scale and search power, but threat hunting depends on the quality of intelligence. The Hunt.io integration brings curated C2 and IOC feeds into Splunk environments, helping teams detect live threats and reduce noise.
Built independently by Hunt.io, the integration plugs seamlessly into Splunk, pairing Splunk's correlation engine with Hunt.io's high-fidelity feeds to give security operations a clearer view of attacker infrastructure - so your team can focus on real threats instead of wasting time on noise.
With Splunk's scale and Hunt.io's intelligence, your team can focus on detecting live threats, validating alerts, and staying ahead of adversaries.
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.





