SOC Threat Hunting Demystified: What You Need to Know
Published on Oct 23, 2025

SOC threat hunting proactively uncovers cyber threats that traditional security tools often miss. Instead of waiting for alerts, it works on the assumption that your systems may already be compromised and actively hunts for hidden risks.
This matters more than ever: according to EvolveSecurity, cybercrime is expected to cost the global economy more than $20 trillion by 2026. At the same time, a KPMG survey found that 73% of security leaders feel confident in their SOC's understanding of risks and vulnerabilities; however, confidence alone isn't enough if threats are slipping past detection.
That's where SOC threat hunting comes in, bridging the gap between confidence and real-world protection. In this article, we'll break down what it is, why it matters, and how your organization can use it to stay ahead of today's evolving cyber threats.
What is SOC Threat Hunting?
Threat hunting is a proactive way to find unknown or ongoing cyber threats. Unlike traditional security that reacts to incidents after they happen, cyber threat hunting takes the fight to the adversary. According to Cisco, threat hunting "involves looking beyond the known alerts or malicious threats to discover new potential threats and vulnerabilities."
It assumes threats can and do bypass traditional security tools, so it's essential to go looking for signs of compromise. This proactive approach reduces the time threats go undetected, reducing impact on the organisation.

The essence of this proactive hunting is to address threats that evade initial security controls. Threat hunting starts where threat intelligence ends, turning insights into action to find hidden threats. This continuous cycle of detection and action keeps security teams ahead of sophisticated threats.
SOC threat hunting is not just about finding existing threats but also about finding unique threats targeted at the organisation's network. It assumes a hacker has already breached the perimeter, so it goes looking for signs of compromise proactively. This approach allows organisations to detect threats early, prevent business disruption, and strengthen security.
Understanding what SOC threat hunting is about leads us to the people behind the process, so let's explore the role of threat hunters.
The Role of Threat Hunters in SOCs
Threat hunters in SOCs play a key role in finding and mitigating cyber threats using various tools and threat hunting techniques. These skilled professionals go looking for threats that automated systems miss, using their intuition and expertise.
A good threat hunting team has members with diverse skills, including data analytics and incident response, trying to achieve a comprehensive approach to threat detection. Threat hunters need to work with the broader security team, collaborating with other departments to improve threat detection.

This creates a threat hunting culture where every security team member contributes to finding and mitigating threats. Threat hunters need to have deep knowledge of networks and operating systems to navigate the complex cyber threat landscape.
Communication skills are key for threat hunters to convey their findings to technical and non-technical stakeholders, which keeps the whole organisation informed of potential threats. By working with other security analysts and teams, threat hunters improve the overall security of the organisation, making it more resilient to emerging threats.
Knowing the responsibilities and skills of threat hunters highlights the importance of a strong foundational framework. To empower these experts, a SOC needs certain elements that form the backbone of any successful threat hunting program.
Key Elements of a Successful SOC Threat Hunting Program
A SOC has six core elements:
Skilled people.
Established processes.
Advanced technology.
Threat intelligence.
Continuous monitoring.
Strong communication.
Each of these elements is critical to strong security. Skilled people include security analysts, engineers, and incident responders, each with different roles to address different aspects of cyber threats.
Continuous monitoring is key to detecting cyber threats at any time; this way, systems are protected 24/7. Automation tools manage repetitive tasks so human analysts can focus on complex security issues. Threat intelligence involves gathering and analysing data about potential cyber threats, proactively improving security.

Communication tools in the SOC enable collaboration, so responses to security threats can be rapid. Threat hunting tools balance automation with human input, so threat hunting is efficient and effective. A combination of threat intelligence resources and security technology is key to the threat hunting process.
With the right framework in place, the next question is: how do threat hunters actually operate? Let's check out the methodologies that they employ.
Threat Hunting Methodologies in SOCs
Threat hunting methodologies in SOCs cover a range of approaches to detect and mitigate threats. These methodologies include different types of threat hunting like structured hunting and unstructured hunting, as well as custom hunting, hypothesis-driven hunting, intelligence-based hunting, incident-based hunting, and anomaly detection. Each of these approaches has its advantages and can be tailored to the organisation's needs.
Structured hunting is systematic searching for specific threats or indicators of compromise. Unstructured hunting is more expertise and intuition-based, so more flexibility in the hunting process.
Hybrid methodologies combine intelligence and situational awareness, adapting hunting techniques for a comprehensive approach to threat detection.

Hypothesis-Driven Hunting
Hypothesis-driven hunting often starts with a hypothesis about potential threats. This approach explores whether attackers can use certain tactics, techniques, and procedures (TTPs) to get into the network. Investigating specific attacker behaviour in their environment allows threat hunters to find known patterns or TTPs.
Targeting specific patterns of behaviour based on past incidents helps to focus the investigation. Usually, during a threat hunting (or even a cybercrime investigation) investigation , threat hunters use known indicators of compromise. This helps to find hidden attacks or ongoing malicious activity. This focused approach ensures threat hunting is effective and efficient.
Intelligence-Based Hunting
Intelligence-based hunting is a technique for active threat hunting. It reacts to sources of intelligence. Common tools used with intelligence-based hunting are Security Information and Event Management (SIEM) and threat intelligence tools. Input sources for intelligence-based hunting can be indicators of compromise (IOCs), IP addresses, hash values, and domain names.
When threat hunters find IOCs, they investigate potential malicious activity to see if there is a threat. By incorporating threat intelligence feeds into hunting activities, hunters can gain more understanding of emerging threats.
Collaboration between threat hunters and the CTI team creates a symbiotic relationship that improves threat detection.
Behavioural Analysis and Anomaly Detection
Behavioral analysis involves tracking abnormal activity in the network to detect potential compromises. Anomalies in user behaviour can indicate potential security breaches. Using machine learning for anomaly detection can find threats that traditional security measures miss.
Threat hunting may start as a response to specific vulnerabilities or anomalies found in the system. By identifying and analysing these anomalies, security analysts can detect malicious activity and take action to neutralise the threat.
Methodologies provide the "why" and "how," but successful hunting requires a structured workflow. The SOC threat hunting process takes these methodologies and applies them step by step.
Steps in the SOC Threat Hunting Process
The threat hunting process has three stages: a trigger, an investigation, and a resolution. Skilled security professionals, lots of data, and powerful analytics are required to start threat hunting. Security analytics accelerates cyber threat hunting and provides detailed observability data, enhancing visibility and context of security threats.
Threat hunting tools are solutions that proactively look for unknown or unremediated threats in the network. Advanced threat hunting should be done full-time and not ad hoc. Threat hunters assume adversaries are already in the system, so proactive threat hunting is part of the organisation's security posture and part of the threat hunting framework.
Initial Trigger
A trigger in threat hunting means a specific system or area to investigate. Triggers can be a specific system, network area, vulnerability announcement, zero-day exploit, anomaly in data, or an internal request to investigate further. In the initial trigger step, a threat hunter collects information, raises hypotheses about threats, and chooses a trigger to investigate.
Preparation of baselines and understanding the normal structure of the environment is crucial in the threat hunting process. Threat hunters need to analyse existing data and logs to create baselines before starting proactive threat hunting.
Tactical threat intelligence helps to identify known indicators of compromise and indicators of attack during the initial phase of threat hunting.
Investigation
The investigation phase uses technologies like Endpoint Detection and Response (EDR) to look into potential threats. During the investigation, hunters differentiate between benign activity and real threats through analysis. Cyber threat hunters use EDR during the SOC threat hunting investigation phase.
After setting a hypothesis, analysts start hunting and validating the identified events. They focus on proactively looking for anomalies to prove or disprove their hypothesis.
By gathering information about the attacker's actions, methods, and goals, threat hunters can analyse trends, eliminate vulnerabilities, and make predictions to bolster security.
Resolution and Reporting
The resolution phase of SOC threat hunting means communicating malicious activity intelligence to teams for response and mitigation. When a threat is found, the hunters remove it and harden the defences against the threat actors.
Post resolution, it's important to provide feedback to improve the organisation's security posture and inform future hunting activities. This phase gathers information that can help predict trends, prioritize vulnerabilities, and improve overall security.
Even the most skilled threat hunters benefit from tools that amplify their capabilities. Automation and advanced security platforms help manage the immense volume of data and repetitive tasks.
Using Automated Security Tools in SOC Threat Hunting
Threat hunting is a combination of manual and automated techniques. Automated security tools enhance threat hunters' capabilities by providing real-time insights and reducing repetitive tasks. Threat Intelligence Platforms (TIPs) consolidate threat data from multiple sources and help threat hunters correlate this data with their organisation's activities.
Security Information and Event Management (SIEM) systems, such as Splunk, provide a centralized hub for threat hunters to correlate events and find suspicious activity. For many SOC teams, Splunk threat hunting has become a practical way to pivot across logs and events, turning raw data into actionable detections. Endpoint Detection and Response (EDR) tools provide real-time insights into endpoint activity and allow threat hunters to find and counter threats more efficiently.
Automated threat hunting platforms using AI and machine learning streamline the analysis of large data sets and find potential threats that would otherwise be missed. Network Traffic Analysis (NTA) tools help to find unusual patterns that may indicate a security threat.
AI and machine learning in SOC will become more important to quickly identify security threats through data analysis. Using these automated tools allows threat hunters to focus on complex tasks and improve the overall SOC efficiency and effectiveness.
While tools enhance efficiency, collaboration multiplies effectiveness. SOC teams and threat hunters must work in tandem.
SOC Teams and Threat Hunters Collaboration
A collaborative SOC environment enhances overall security intelligence by combining different expertise from various teams. Good communication between SOC teams and threat hunters creates a culture of proactive threat detection and response. Integrating efforts between different SOC functions and threat hunters will lead to faster response times during security incidents.
Collaborations can lead to the discovery of emerging threats that individual teams might miss. Improved threat intelligence sharing frameworks will allow SOCs to get real-time threat data and be more responsive.
Shared understanding of the threat landscape between threat hunters and SOC teams will lead to better risk management. By combining human intuition with machine precision, organisations can build a resilient defence against cyber adversaries.
Keep in mind that collaboration is only as valuable as its measurable outcomes. Tracking performance through metrics helps SOCs refine their processes, validate their strategies, and ensure that threat hunting delivers real benefits.
Measuring SOC Threat Hunting Success
Metrics like Mean Time to Detect (MTTD) help to measure how fast a SOC detects security incidents, which is key to minimizing the impact. Mean Time to Repair (MTTR) reflects the average time to fully resolve an incident, which is the efficiency of the incident response process. Monitoring the number of security incidents over time will uncover trends and highlight areas for security posture improvement.
False Positive Rates (FPR) and False Negative Rates (FNR) measure the accuracy of threat detection systems and guide threat detection methodology refinement. Understanding the cost of an incident, including direct and indirect costs, helps organisations to understand the financial impact of a breach.
Metrics and lessons learned point toward best practices. SOCs must establish a robust routine that keeps threat hunters ahead of adversaries and enhances the organization's overall security posture.
Best Practices
SOC threat hunting is about staying ahead of attackers, not just reacting to alerts.
Let's now review the top best practices for SOC threat hunting:
Start with clear goals, focusing on your most critical systems and likely attack paths.
Combine threat intelligence with internal data to turn observations into actionable insights.
Use a mix of structured methods, like predefined frameworks, and unstructured approaches that rely on intuition and exploration.
Document findings so each hunt strengthens the team's knowledge.
Collaboration across IT, incident response, and security teams uncovers patterns that might otherwise go unnoticed.
Automation can help speed up analysis, but it shouldn't replace human judgment.
Applying these best practices in the real world can be made easier with the right platform.
Hunt.io: High-Fidelity C2 Detection for SOC Threat Hunting
Hunt.io gives SOC teams visibility into the infrastructure attackers rely on. Our platform identifies and validates live Command and Control servers through continuous internet-wide scanning, so your team can act before threats escalate. Every finding is enriched with context such as IP history, TLS fingerprints, and links to malware families or threat actors, giving analysts the clarity they need to respond with confidence.
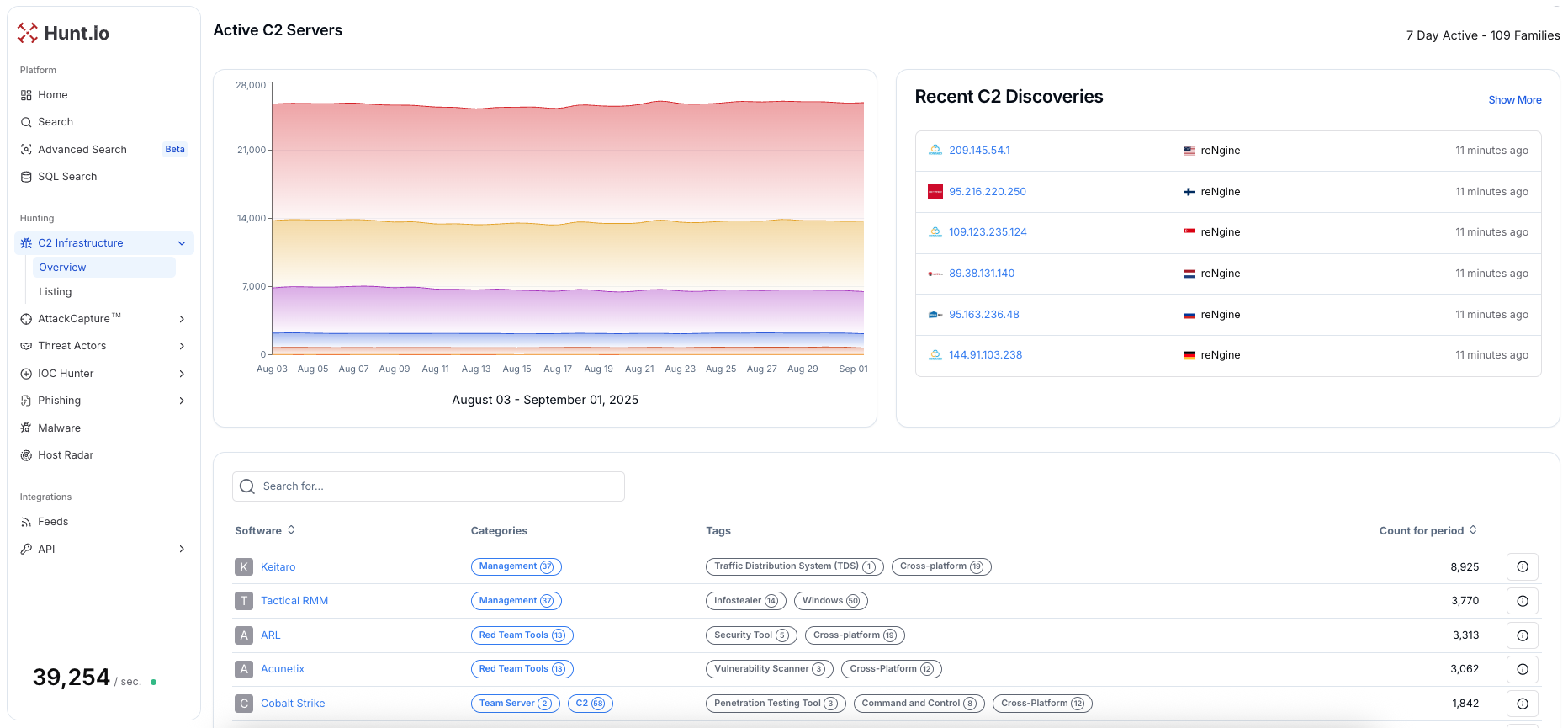
IOC Hunter automatically pulls indicators from trusted research sources, validates them, and connects them to related domains, IPs, and campaigns. AttackCapture™ surfaces attacker tools and payloads stored in open directories, while HuntSQL provides direct access to datasets like certificates, HTTP responses, WHOIS data, URLx, and others, allowing analysts to pivot across massive amounts of telemetry to uncover hidden endpoints and payload delivery paths. Together, these capabilities help your SOC reduce dwell time, cut false positives, and strengthen proactive threat hunting.
Best practices set the foundation, but real-world SOCs must still overcome challenges like false positives, resource limits, and fast-changing threats.
SOC Threat Hunting Challenges and How to Overcome Them
Threat hunting in the SOC comes with real obstacles that can slow down analysts and weaken defenses. The most common challenges include:
False positives that distract analysts from genuine threats and waste valuable time - refine detection systems and continuously tune rules to cut down noise.
24/7 operations that stretch SOC resources thin and impact work-life balance - balance workloads with smarter scheduling and automation.
Limited automation, leaving teams stuck in slow, manual workflows - introduce automation for repetitive tasks while keeping humans in control of high-level decisions.
Communication gaps between SOC and other departments that make incident response less effective - establish clear protocols and cross-team playbooks.
Noisy open-source C2 feeds that bury analysts in low-fidelity signals - switch to curated, high-fidelity C2 feeds like the one from Hunt.io for reliable visibility.
High data volumes that overwhelm analysts and complicate detection - use filtering, enrichment, and context to separate what matters from background noise.
Evolving threats that demand continuous upskilling to keep pace - invest in regular training and knowledge-sharing within the team.
Incomplete or fragmented data that makes it harder to assess risks accurately - integrate multiple data sources to build a more complete threat picture.
Tackling these challenges is not about a single fix but about combining automation, curated data, better communication, and continuous development. This balance allows SOC teams to hunt more effectively today and stay ready for the threats of tomorrow.
Wrapping Up
Mastering SOC threat hunting is about understanding its proactive nature, the role of threat hunters, and the different methodologies and tools used. By combining manual and automated techniques, collaboration within SOC teams and continuous measurement and refinement of threat hunting organisations can stay ahead of advanced threats.
Book a demo today to see how our platform empowers your SOC team to hunt threats proactively and efficiently.
SOC threat hunting proactively uncovers cyber threats that traditional security tools often miss. Instead of waiting for alerts, it works on the assumption that your systems may already be compromised and actively hunts for hidden risks.
This matters more than ever: according to EvolveSecurity, cybercrime is expected to cost the global economy more than $20 trillion by 2026. At the same time, a KPMG survey found that 73% of security leaders feel confident in their SOC's understanding of risks and vulnerabilities; however, confidence alone isn't enough if threats are slipping past detection.
That's where SOC threat hunting comes in, bridging the gap between confidence and real-world protection. In this article, we'll break down what it is, why it matters, and how your organization can use it to stay ahead of today's evolving cyber threats.
What is SOC Threat Hunting?
Threat hunting is a proactive way to find unknown or ongoing cyber threats. Unlike traditional security that reacts to incidents after they happen, cyber threat hunting takes the fight to the adversary. According to Cisco, threat hunting "involves looking beyond the known alerts or malicious threats to discover new potential threats and vulnerabilities."
It assumes threats can and do bypass traditional security tools, so it's essential to go looking for signs of compromise. This proactive approach reduces the time threats go undetected, reducing impact on the organisation.

The essence of this proactive hunting is to address threats that evade initial security controls. Threat hunting starts where threat intelligence ends, turning insights into action to find hidden threats. This continuous cycle of detection and action keeps security teams ahead of sophisticated threats.
SOC threat hunting is not just about finding existing threats but also about finding unique threats targeted at the organisation's network. It assumes a hacker has already breached the perimeter, so it goes looking for signs of compromise proactively. This approach allows organisations to detect threats early, prevent business disruption, and strengthen security.
Understanding what SOC threat hunting is about leads us to the people behind the process, so let's explore the role of threat hunters.
The Role of Threat Hunters in SOCs
Threat hunters in SOCs play a key role in finding and mitigating cyber threats using various tools and threat hunting techniques. These skilled professionals go looking for threats that automated systems miss, using their intuition and expertise.
A good threat hunting team has members with diverse skills, including data analytics and incident response, trying to achieve a comprehensive approach to threat detection. Threat hunters need to work with the broader security team, collaborating with other departments to improve threat detection.

This creates a threat hunting culture where every security team member contributes to finding and mitigating threats. Threat hunters need to have deep knowledge of networks and operating systems to navigate the complex cyber threat landscape.
Communication skills are key for threat hunters to convey their findings to technical and non-technical stakeholders, which keeps the whole organisation informed of potential threats. By working with other security analysts and teams, threat hunters improve the overall security of the organisation, making it more resilient to emerging threats.
Knowing the responsibilities and skills of threat hunters highlights the importance of a strong foundational framework. To empower these experts, a SOC needs certain elements that form the backbone of any successful threat hunting program.
Key Elements of a Successful SOC Threat Hunting Program
A SOC has six core elements:
Skilled people.
Established processes.
Advanced technology.
Threat intelligence.
Continuous monitoring.
Strong communication.
Each of these elements is critical to strong security. Skilled people include security analysts, engineers, and incident responders, each with different roles to address different aspects of cyber threats.
Continuous monitoring is key to detecting cyber threats at any time; this way, systems are protected 24/7. Automation tools manage repetitive tasks so human analysts can focus on complex security issues. Threat intelligence involves gathering and analysing data about potential cyber threats, proactively improving security.

Communication tools in the SOC enable collaboration, so responses to security threats can be rapid. Threat hunting tools balance automation with human input, so threat hunting is efficient and effective. A combination of threat intelligence resources and security technology is key to the threat hunting process.
With the right framework in place, the next question is: how do threat hunters actually operate? Let's check out the methodologies that they employ.
Threat Hunting Methodologies in SOCs
Threat hunting methodologies in SOCs cover a range of approaches to detect and mitigate threats. These methodologies include different types of threat hunting like structured hunting and unstructured hunting, as well as custom hunting, hypothesis-driven hunting, intelligence-based hunting, incident-based hunting, and anomaly detection. Each of these approaches has its advantages and can be tailored to the organisation's needs.
Structured hunting is systematic searching for specific threats or indicators of compromise. Unstructured hunting is more expertise and intuition-based, so more flexibility in the hunting process.
Hybrid methodologies combine intelligence and situational awareness, adapting hunting techniques for a comprehensive approach to threat detection.

Hypothesis-Driven Hunting
Hypothesis-driven hunting often starts with a hypothesis about potential threats. This approach explores whether attackers can use certain tactics, techniques, and procedures (TTPs) to get into the network. Investigating specific attacker behaviour in their environment allows threat hunters to find known patterns or TTPs.
Targeting specific patterns of behaviour based on past incidents helps to focus the investigation. Usually, during a threat hunting (or even a cybercrime investigation) investigation , threat hunters use known indicators of compromise. This helps to find hidden attacks or ongoing malicious activity. This focused approach ensures threat hunting is effective and efficient.
Intelligence-Based Hunting
Intelligence-based hunting is a technique for active threat hunting. It reacts to sources of intelligence. Common tools used with intelligence-based hunting are Security Information and Event Management (SIEM) and threat intelligence tools. Input sources for intelligence-based hunting can be indicators of compromise (IOCs), IP addresses, hash values, and domain names.
When threat hunters find IOCs, they investigate potential malicious activity to see if there is a threat. By incorporating threat intelligence feeds into hunting activities, hunters can gain more understanding of emerging threats.
Collaboration between threat hunters and the CTI team creates a symbiotic relationship that improves threat detection.
Behavioural Analysis and Anomaly Detection
Behavioral analysis involves tracking abnormal activity in the network to detect potential compromises. Anomalies in user behaviour can indicate potential security breaches. Using machine learning for anomaly detection can find threats that traditional security measures miss.
Threat hunting may start as a response to specific vulnerabilities or anomalies found in the system. By identifying and analysing these anomalies, security analysts can detect malicious activity and take action to neutralise the threat.
Methodologies provide the "why" and "how," but successful hunting requires a structured workflow. The SOC threat hunting process takes these methodologies and applies them step by step.
Steps in the SOC Threat Hunting Process
The threat hunting process has three stages: a trigger, an investigation, and a resolution. Skilled security professionals, lots of data, and powerful analytics are required to start threat hunting. Security analytics accelerates cyber threat hunting and provides detailed observability data, enhancing visibility and context of security threats.
Threat hunting tools are solutions that proactively look for unknown or unremediated threats in the network. Advanced threat hunting should be done full-time and not ad hoc. Threat hunters assume adversaries are already in the system, so proactive threat hunting is part of the organisation's security posture and part of the threat hunting framework.
Initial Trigger
A trigger in threat hunting means a specific system or area to investigate. Triggers can be a specific system, network area, vulnerability announcement, zero-day exploit, anomaly in data, or an internal request to investigate further. In the initial trigger step, a threat hunter collects information, raises hypotheses about threats, and chooses a trigger to investigate.
Preparation of baselines and understanding the normal structure of the environment is crucial in the threat hunting process. Threat hunters need to analyse existing data and logs to create baselines before starting proactive threat hunting.
Tactical threat intelligence helps to identify known indicators of compromise and indicators of attack during the initial phase of threat hunting.
Investigation
The investigation phase uses technologies like Endpoint Detection and Response (EDR) to look into potential threats. During the investigation, hunters differentiate between benign activity and real threats through analysis. Cyber threat hunters use EDR during the SOC threat hunting investigation phase.
After setting a hypothesis, analysts start hunting and validating the identified events. They focus on proactively looking for anomalies to prove or disprove their hypothesis.
By gathering information about the attacker's actions, methods, and goals, threat hunters can analyse trends, eliminate vulnerabilities, and make predictions to bolster security.
Resolution and Reporting
The resolution phase of SOC threat hunting means communicating malicious activity intelligence to teams for response and mitigation. When a threat is found, the hunters remove it and harden the defences against the threat actors.
Post resolution, it's important to provide feedback to improve the organisation's security posture and inform future hunting activities. This phase gathers information that can help predict trends, prioritize vulnerabilities, and improve overall security.
Even the most skilled threat hunters benefit from tools that amplify their capabilities. Automation and advanced security platforms help manage the immense volume of data and repetitive tasks.
Using Automated Security Tools in SOC Threat Hunting
Threat hunting is a combination of manual and automated techniques. Automated security tools enhance threat hunters' capabilities by providing real-time insights and reducing repetitive tasks. Threat Intelligence Platforms (TIPs) consolidate threat data from multiple sources and help threat hunters correlate this data with their organisation's activities.
Security Information and Event Management (SIEM) systems, such as Splunk, provide a centralized hub for threat hunters to correlate events and find suspicious activity. For many SOC teams, Splunk threat hunting has become a practical way to pivot across logs and events, turning raw data into actionable detections. Endpoint Detection and Response (EDR) tools provide real-time insights into endpoint activity and allow threat hunters to find and counter threats more efficiently.
Automated threat hunting platforms using AI and machine learning streamline the analysis of large data sets and find potential threats that would otherwise be missed. Network Traffic Analysis (NTA) tools help to find unusual patterns that may indicate a security threat.
AI and machine learning in SOC will become more important to quickly identify security threats through data analysis. Using these automated tools allows threat hunters to focus on complex tasks and improve the overall SOC efficiency and effectiveness.
While tools enhance efficiency, collaboration multiplies effectiveness. SOC teams and threat hunters must work in tandem.
SOC Teams and Threat Hunters Collaboration
A collaborative SOC environment enhances overall security intelligence by combining different expertise from various teams. Good communication between SOC teams and threat hunters creates a culture of proactive threat detection and response. Integrating efforts between different SOC functions and threat hunters will lead to faster response times during security incidents.
Collaborations can lead to the discovery of emerging threats that individual teams might miss. Improved threat intelligence sharing frameworks will allow SOCs to get real-time threat data and be more responsive.
Shared understanding of the threat landscape between threat hunters and SOC teams will lead to better risk management. By combining human intuition with machine precision, organisations can build a resilient defence against cyber adversaries.
Keep in mind that collaboration is only as valuable as its measurable outcomes. Tracking performance through metrics helps SOCs refine their processes, validate their strategies, and ensure that threat hunting delivers real benefits.
Measuring SOC Threat Hunting Success
Metrics like Mean Time to Detect (MTTD) help to measure how fast a SOC detects security incidents, which is key to minimizing the impact. Mean Time to Repair (MTTR) reflects the average time to fully resolve an incident, which is the efficiency of the incident response process. Monitoring the number of security incidents over time will uncover trends and highlight areas for security posture improvement.
False Positive Rates (FPR) and False Negative Rates (FNR) measure the accuracy of threat detection systems and guide threat detection methodology refinement. Understanding the cost of an incident, including direct and indirect costs, helps organisations to understand the financial impact of a breach.
Metrics and lessons learned point toward best practices. SOCs must establish a robust routine that keeps threat hunters ahead of adversaries and enhances the organization's overall security posture.
Best Practices
SOC threat hunting is about staying ahead of attackers, not just reacting to alerts.
Let's now review the top best practices for SOC threat hunting:
Start with clear goals, focusing on your most critical systems and likely attack paths.
Combine threat intelligence with internal data to turn observations into actionable insights.
Use a mix of structured methods, like predefined frameworks, and unstructured approaches that rely on intuition and exploration.
Document findings so each hunt strengthens the team's knowledge.
Collaboration across IT, incident response, and security teams uncovers patterns that might otherwise go unnoticed.
Automation can help speed up analysis, but it shouldn't replace human judgment.
Applying these best practices in the real world can be made easier with the right platform.
Hunt.io: High-Fidelity C2 Detection for SOC Threat Hunting
Hunt.io gives SOC teams visibility into the infrastructure attackers rely on. Our platform identifies and validates live Command and Control servers through continuous internet-wide scanning, so your team can act before threats escalate. Every finding is enriched with context such as IP history, TLS fingerprints, and links to malware families or threat actors, giving analysts the clarity they need to respond with confidence.

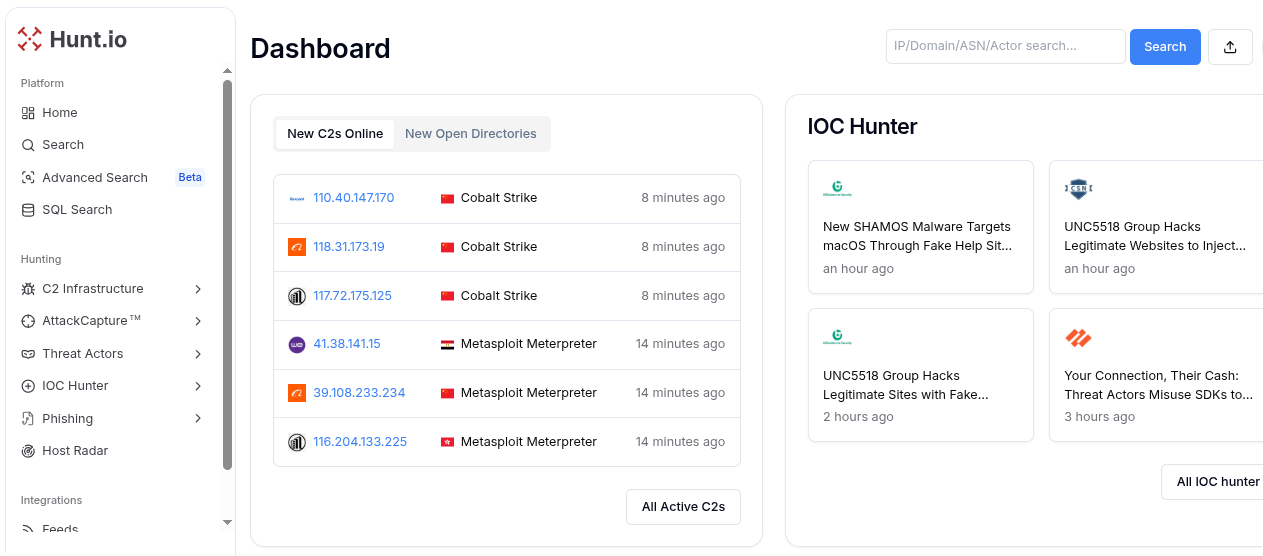
IOC Hunter automatically pulls indicators from trusted research sources, validates them, and connects them to related domains, IPs, and campaigns. AttackCapture™ surfaces attacker tools and payloads stored in open directories, while HuntSQL provides direct access to datasets like certificates, HTTP responses, WHOIS data, URLx, and others, allowing analysts to pivot across massive amounts of telemetry to uncover hidden endpoints and payload delivery paths. Together, these capabilities help your SOC reduce dwell time, cut false positives, and strengthen proactive threat hunting.

Best practices set the foundation, but real-world SOCs must still overcome challenges like false positives, resource limits, and fast-changing threats.
SOC Threat Hunting Challenges and How to Overcome Them
Threat hunting in the SOC comes with real obstacles that can slow down analysts and weaken defenses. The most common challenges include:
False positives that distract analysts from genuine threats and waste valuable time - refine detection systems and continuously tune rules to cut down noise.
24/7 operations that stretch SOC resources thin and impact work-life balance - balance workloads with smarter scheduling and automation.
Limited automation, leaving teams stuck in slow, manual workflows - introduce automation for repetitive tasks while keeping humans in control of high-level decisions.
Communication gaps between SOC and other departments that make incident response less effective - establish clear protocols and cross-team playbooks.
Noisy open-source C2 feeds that bury analysts in low-fidelity signals - switch to curated, high-fidelity C2 feeds like the one from Hunt.io for reliable visibility.
High data volumes that overwhelm analysts and complicate detection - use filtering, enrichment, and context to separate what matters from background noise.
Evolving threats that demand continuous upskilling to keep pace - invest in regular training and knowledge-sharing within the team.
Incomplete or fragmented data that makes it harder to assess risks accurately - integrate multiple data sources to build a more complete threat picture.
Tackling these challenges is not about a single fix but about combining automation, curated data, better communication, and continuous development. This balance allows SOC teams to hunt more effectively today and stay ready for the threats of tomorrow.
Wrapping Up
Mastering SOC threat hunting is about understanding its proactive nature, the role of threat hunters, and the different methodologies and tools used. By combining manual and automated techniques, collaboration within SOC teams and continuous measurement and refinement of threat hunting organisations can stay ahead of advanced threats.
Book a demo today to see how our platform empowers your SOC team to hunt threats proactively and efficiently.
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.





