Sqrrl Threat Hunting Framework Explained: Techniques and Best Practices
Published on Oct 23, 2025

The Sqrrl Threat Hunting Framework is a methodology that helps analysts move from reactive alert triage to proactive hunts. It was introduced in 2015 and is still referenced as a foundation for structured, hypothesis-driven hunts.
Recent reports underline why this approach matters. CrowdStrike's 2025 Threat Hunting Report found that more than 80% of intrusions did not involve traditional malware, which makes them harder to catch with signature-based defenses. At the same time, Trend Micro's Cloud Security Report revealed that only a 25% of companies fully trust their existing tools to detect advanced threats. This gap highlights the need for structured, hypothesis-driven hunting models like Sqrrl.
At its core, the framework gives teams a repeatable loop for forming hypotheses, testing them against available data, and turning findings into better detections. Instead of chasing alerts, hunters can follow a structured process that reduces dwell time and steadily improves visibility.
Sqrrl was a security company that created one of the first published threat hunting frameworks. While the product no longer exists, the methodology continues to influence how modern teams approach proactive hunting.
Takeaways
Sqrrl's threat hunting framework is a structured, hypothesis-driven process of preparation, detection, investigation, and action to help security teams find threats.
Sqrrl's threat hunting framework is still widely used as a methodology, even though the original Sqrrl platform is no longer active.
Integrating threat intelligence into the Sqrrl framework improves detection, so you can proactively manage threats by using multiple data sources and tools.
The Sqrrl Threat Hunting Model provides a maturity model to measure your threat hunting capabilities and guide you to improve your practices to address cyber threats.
What is Sqrrl's Threat Hunting Framework?

The Sqrrl threat hunting framework was introduced in 2015 and is considered one of the first frameworks of its kind. It's known for its flexibility, repeatability, and support for hypothesis testing with the best data.
Sqrrl was designed to help security teams build threat hunting programs and improve their response and mitigation during security incidents. It had such a major impact that the Threat Hunting Project notes that the Sqrrl team "published some of what are still foundational documents about threat hunting".
AWS acquired Sqrrl in 2018. The platform itself was absorbed into AWS services, but the framework lives on as a conceptual model referenced across the security community. Sqrrl is about exploration and inquiry, guiding hunters to look in areas that traditional methods miss. This is the key to its hypothesis-driven process and continuous learning and adaptation.
The hunting loop is the core of Sqrrl's framework, thanks to which each hunt should improve your security posture. By finding patterns in network data that traditional methods miss, Sqrrl helps security teams find and address threats better.
Is Sqrrl Still Active Today?
Sqrrl, the company behind the framework, was acquired by Amazon Web Services in 2018 and no longer exists as a standalone platform. What does remain is the Sqrrl framework as a conceptual model. It continues to be referenced across the security community and has influenced frameworks such as Splunk's PEAK and others.
For us at Hunt.io, Sqrrl's model has been a reference point when building out our own approaches to proactive threat hunting. While the original product is gone, the methodology lives on and still shapes how modern hunts are designed.
Now that we've looked at the origins and purpose of the Sqrrl framework, the next step is to understand what it's actually made of. The framework is not just a concept; it's built on a set of structured components that guide hunters through repeatable processes.
Sqrrl Framework Components
Sqrrl's framework is considered one of the first threat hunting strategies, known for its hypothesis-driven approach and structured methods. The purpose of threat hunting methodologies, including Sqrrl's, is to help security teams build threat hunting programs that improve their response and mitigation during security incidents.
The framework brings together different types of knowledge, such as organizational expertise and threat intelligence, into each stage of the threat hunting process.
Although Sqrrl is no longer an active product, the framework it introduced remains valuable as a structured, hypothesis-driven methodology. Its structured, unstructured, and situational methods provide a full threat hunting approach.
The following sections will go into more detail on the hypothesis-driven hunting process and the four stages of the hunting loop, which are part of Sqrrl's framework.
Hypothesis-Driven Hunting Process
Effective threat hunting is a proactive approach with hypotheses based on attacker behaviors. Sqrrl's hypothesis-driven process has four stages: hypothesis generation, investigation, attack pattern detection, and using evidence to refine investigations. This cyclical process ensures continuous refinement based on findings, adapting to new and emerging threats.
Hypothesis formation drives hunts for mature threat hunting teams to explore areas that traditional methods miss. This continuous cycle requires regular updates and refinements based on the latest threat intelligence and findings, so the threat hunting team can create hypotheses to investigate hidden patterns and potential threats.
Being hypothesis-driven ensures systematic and repeatable threat hunting. It also fosters continuous learning and improvement within the team, so they can stay ahead of threats.
Four Stages of Hunting Loop
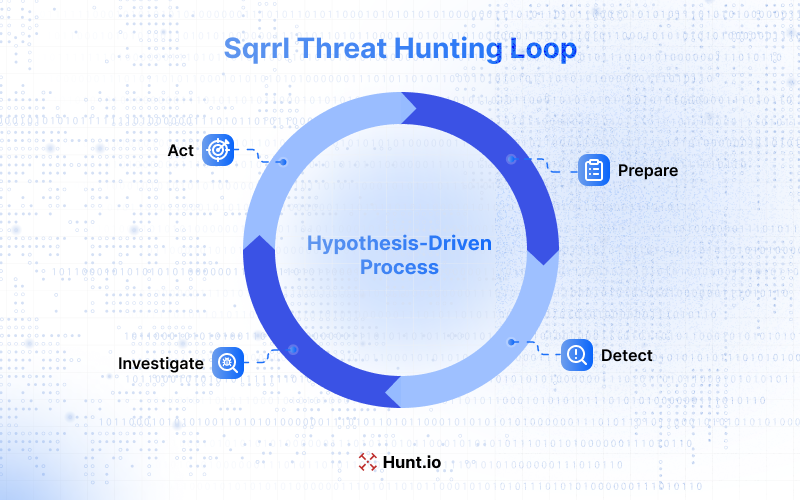
The Threat Hunting Loop in the Sqrrl framework is a conceptual model. It outlines the steps of a typical hunt. The four stages of the hunting process are Prepare, Detect, Investigate, and Act. Each of these phases brings together different types of knowledge, including organizational expertise and threat intelligence, to find and respond to threats.
In the Prepare stage, threat hunters gather the necessary data and tools, including endpoint data, network data, security data, and threat intelligence.
In the Detect stage, data is used to find potential threats and anomalies, using Sqrrl's visualization tools to explore data and find malicious behavior.
In the Investigate stage, the anomalies are dug deeper into, using link analysis to find hidden relationships between suspicious behaviors and alerts. In the Act stage, actions are taken based on findings, such as mitigating threats and improving security to prevent future incidents. Following these four stages is a full threat hunting process.
While the framework's stages and methods create a strong foundation, their effectiveness largely depends on the data feeding them. This is where threat intelligence comes in, turning the framework from a structured loop into a powerful, real-time tool for finding advanced threats.
Threat Intelligence with Sqrrl
Integrating data from threat intelligence feeds into the Sqrrl framework allows security teams to proactively manage threats and improve detection. Automation tools help correlate threat intelligence with hunting activities, so you can process and analyze large data volumes, essential for handling indicators of compromise and other relevant data.
Threat hunting requires gathering different types of data, including endpoint data, network data, and security data, all of which are key to finding and responding to threats. Structured threat hunting often involves focusing on known tactics, techniques, and procedures (TTPs) as outlined by frameworks like MITRE ATT&CK.
Organizations at different threat hunting maturity levels can improve by integrating a threat intelligence platform to enrich indicators of compromise. Emerging trends require visibility across different data sources, so threat intelligence integration is critical.
Bringing intelligence into the loop highlights why many teams have found Sqrrl so valuable.
Benefits of Using Sqrrl for Threat Hunting
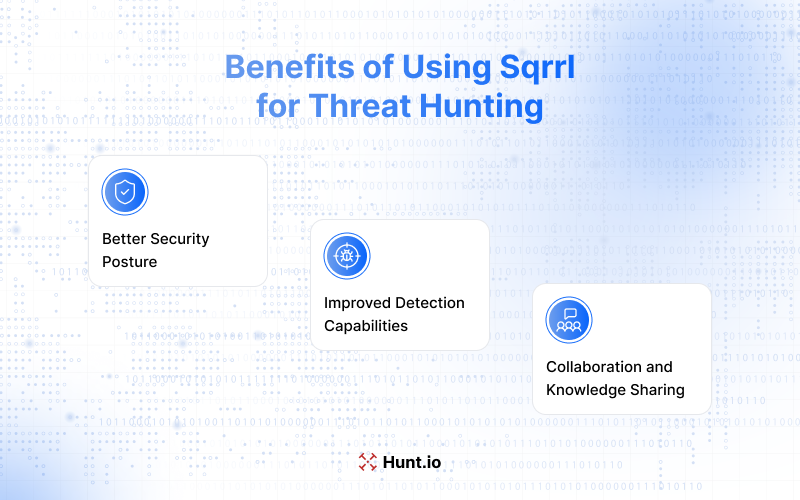
Teams that apply the Sqrrl framework often find they can detect advanced threats more effectively. The structure gives them a way to hunt without relying only on alerts, which means analysts with different levels of experience could contribute. The process is repeatable, clear, and can be used with whatever threat hunting tools and threat hunting platforms the team already has.
Better Security Posture
Threat hunting is a proactive approach that doesn't rely on alerts or whitelisting actions, so organizations can stay ahead of threats. Integrating threat hunting into security practices uncovers valuable insights, finds threats sooner, and reduces dwell time, so the overall security posture improves.
Improved Detection Capabilities
Using the Sqrrl framework encourages the creation of playbooks and processes that can be repeated and improved over time. By focusing hunts on hypotheses, patterns, and intelligence, security teams become better at spotting new techniques as they emerge. This cycle of refinement is why the framework is still taught and used today.
Collaboration and Knowledge Sharing
Because the framework is structured and repeatable, it creates a common language for analysts at different experience levels. This shared process makes it easier for junior analysts to contribute while allowing senior hunters to pass on their expertise. Over time, the framework becomes not just a hunting process but also a way to strengthen team collaboration and knowledge transfer.
Of course, not all teams will see the same results right away. The value of Sqrrl depends on how mature an organization's hunting capabilities are. That's why the framework includes a maturity model to help teams understand their current level and where to go next.
Sqrrl Threat Hunting Maturity
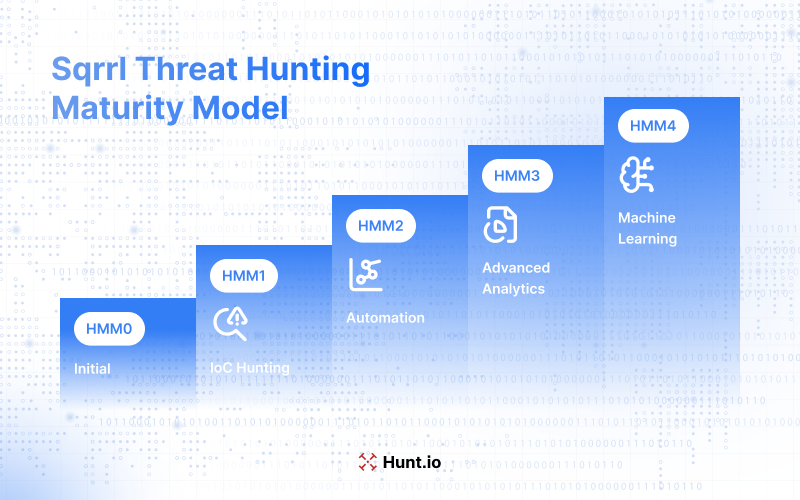
The Hunt Maturity Model (HMM), originally published by Sqrrl and the ThreatHunting.net project, outlines five levels of hunting capability that organizations can use to benchmark and improve their practices. It outlines the different stages of hunting competence so organizations can assess their threat hunting maturity model and improve over time. This model helps organizations understand where they are and provides a roadmap to improve their threat hunting.
The HMM stages describe the typical processes for each loop stage at different maturity levels, from initial to procedural and innovative to leading. Organizations at higher maturity levels can stop and detect adversary activity, often through automation and advanced data analysis.
Initial to Procedural Levels
Hunting for Indicators of Compromise (IoCs) on endpoints against recent intelligence feeds is where security teams start. Organizations at the initial maturity level (HMM0) mainly focus on alert resolution with limited practices beyond basic correlation.
As they move to HMM1, they start to use automated alerting for incident response and follow up on recent threat reports for intelligence-driven detection. At the procedural level (HMM2), organizations start to use analytical and hunting processes produced by others; this is a move towards a more structured methodology.
Increased visibility into environments allows these organizations to collect data and improve threat hunting. Diversifying SIEM content beyond basic correlations establishes a robust detection framework for more in-depth analysis.
Innovative to Leading Levels
At the innovative level (HMM3), organizations use advanced data analysis techniques, including machine learning for threat detection. They face scalability issues and overwhelming hunting processes as data grows. But they can develop and refine their own detection methods, reaching an advanced threat hunting state that sets them apart from less mature organizations.
At the leading level (HMM4), organizations automate threat hunting, and analysts can focus on developing new methods and improving existing ones. High automation allows them to stop and detect adversary activity; they have a big advantage in the evolving cyber landscape.
This is the top of the threat hunting maturity, where organizations are continuously improving and adapting to new threats.
Just keep in mind that knowing your maturity level is only half the battle. The real challenge is putting the framework into practice in a way that fits your organization. Practical implementation tips and methods for data collection, analysis, and playbook creation can make the difference between theory and impact.
Sqrrl Implementation Tips
Applying the Sqrrl framework takes planning, good data collection, and clear playbooks. Many teams used it as a reference when building their own threat hunting program, adapting it to the tools and data they already had. The important part is the methodology itself, not the old platform. It remains flexible enough to fit into almost any SOC.
Data Collection and Analysis Techniques
Keyword searching is a common technique in threat hunting. It involves scanning system logs and configuration files for specific terms that may indicate security incidents. Four data collection techniques are clustering, grouping, searching, and stack counting; each serves a different analysis purpose. Endpoint data should include process execution metadata, registry access data, and file metadata to provide insights into user activities.
Network data collection should focus on session data, monitoring tool logs, and firewall logs to track communication patterns. Using these data collection and analysis techniques will enhance an organization's ability to detect and mitigate threats.
Effective data collection and analysis are the foundation of a successful threat hunting program, as they allow hunters to find hidden patterns and potential threats.
Creating Playbooks
Creating threat hunting playbooks involves documenting repeatable processes that guide hunters through specific investigation scenarios. They should include clear roles and responsibilities to streamline team collaboration during investigations. Incorporating real-world scenarios and lessons from previous hunts will make playbooks more effective.
Threat hunting frameworks need plans for post-hunt actions; Sqrrl doesn't provide that. Addressing that gap will ensure threat hunting leads to actionable insights and continuous improvement. Effective playbooks are key to being prepared and responding to detected threats.
This is where Hunt.io helps. By enriching the Sqrrl process with automation and high-fidelity data, teams can keep the hunting loop running without being slowed down by manual bottlenecks.
Bring Sqrrl to Life with Hunt.io
Applying the Sqrrl framework effectively requires the right tools and actionable data. That's where the Hunt.io cutting-edge threat hunting platform can make a real difference.
Our platform combines globally distributed sensors with advanced analytics to help teams detect, investigate, and mitigate threats more efficiently.
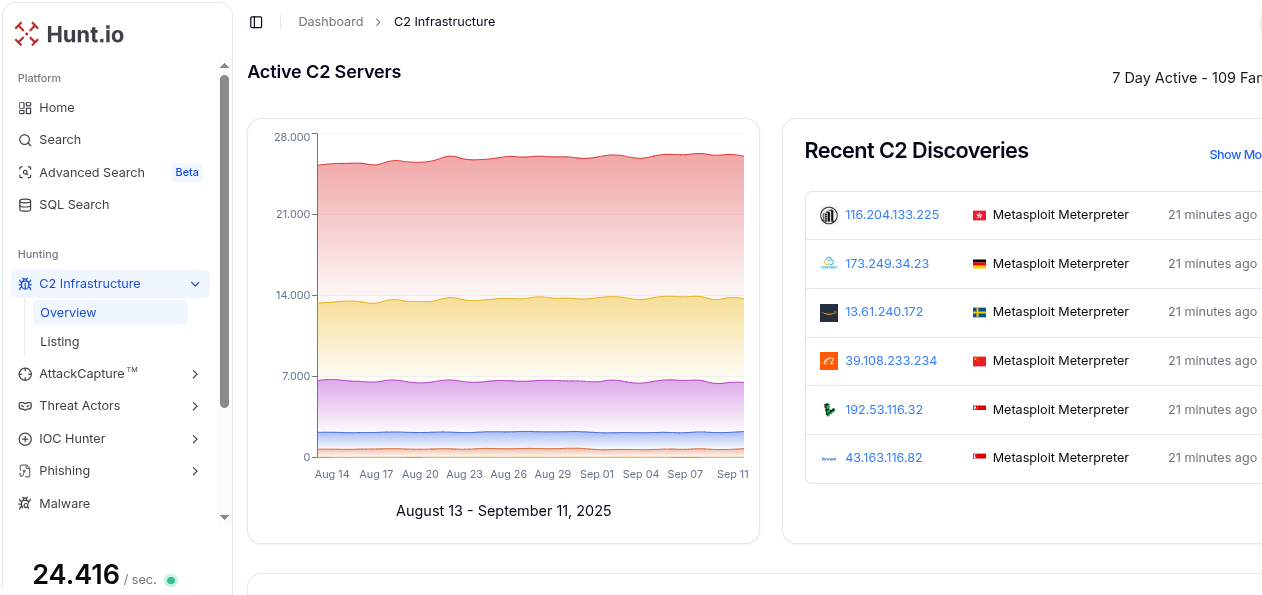
With solutions like C2 Infrastructure Feeds, IOC Hunter, AttackCapture™, and HuntSQL™, security teams can automate the collection and analysis of indicators of compromise, enrich threat intelligence, and streamline hunts.
By integrating these tools into a structured threat hunting program, teams gain deeper visibility into attacker behaviors, reduce dwell time, and ensure that each hunt produces meaningful, actionable insights. We don't simply support the Sqrrl methodology; we empower teams to stay ahead in an evolving threat landscape.
And while our tools provide the data, automation, and insights needed to make threat hunting more effective, even the best methodology and platform cannot eliminate all obstacles. Data overload, visibility gaps, and evolving threats all present challenges that teams must overcome if they want to get the most out of the Sqrrl methodology.
Sqrrl Threat Hunting Challenges
Let's now review what are the most common challenges for users adopting the Sqrrl threat hunting model:
Data quality and consistency
Security teams often have logs and telemetry coming from different places. If that data is not normalized and enriched, analysts spend too much time cleaning it instead of testing their hunting ideas.
Coming up with good hypotheses
Many teams fall back on chasing indicators they already know. The framework works best when hunters can form creative, intelligence-driven hypotheses about attacker behavior. That requires experience and context, which are not always available in smaller or less mature SOCs.
Keeping the loop alive
The idea of Prepare, Detect, Investigate, and Act is simple, but in reality many teams stop halfway. Lessons learned are not always turned into new detections or playbooks, which means the same gaps show up again in future hunts.
Scaling hunts
Sqrrl was developed at a time when hunting was still highly manual. At enterprise scale, that kind of approach can overwhelm analysts. Without automation and enrichment from high-fidelity intelligence, teams often hit a wall.
Measuring results
The maturity model is helpful, but it does not tell you exactly how to measure success. Leadership often asks what has improved after months of hunts, and without clear metrics, it can be difficult to prove the value of the effort.
Addressing these challenges will allow teams to get the most out of Sqrrl and their improve threat hunting.
Wrapping up
Even though the Sqrrl platform was discontinued after AWS's acquisition, its methodology continues to influence how threat hunters work today. The hunting loop, the maturity model, and the focus on hypothesis-driven inquiry remain some of the most practical tools for finding advanced threats.
At Hunt.io we extend these principles with automation, global adversary data, and enrichment that make the framework easier to put into practice. If you want to see how structured hunting can become a daily reality in your SOC, book a demo and explore our platform in action
Ready to see our platform in action? Book a demo now and experience proactive threat hunting for yourself.
The Sqrrl Threat Hunting Framework is a methodology that helps analysts move from reactive alert triage to proactive hunts. It was introduced in 2015 and is still referenced as a foundation for structured, hypothesis-driven hunts.
Recent reports underline why this approach matters. CrowdStrike's 2025 Threat Hunting Report found that more than 80% of intrusions did not involve traditional malware, which makes them harder to catch with signature-based defenses. At the same time, Trend Micro's Cloud Security Report revealed that only a 25% of companies fully trust their existing tools to detect advanced threats. This gap highlights the need for structured, hypothesis-driven hunting models like Sqrrl.
At its core, the framework gives teams a repeatable loop for forming hypotheses, testing them against available data, and turning findings into better detections. Instead of chasing alerts, hunters can follow a structured process that reduces dwell time and steadily improves visibility.
Sqrrl was a security company that created one of the first published threat hunting frameworks. While the product no longer exists, the methodology continues to influence how modern teams approach proactive hunting.
Takeaways
Sqrrl's threat hunting framework is a structured, hypothesis-driven process of preparation, detection, investigation, and action to help security teams find threats.
Sqrrl's threat hunting framework is still widely used as a methodology, even though the original Sqrrl platform is no longer active.
Integrating threat intelligence into the Sqrrl framework improves detection, so you can proactively manage threats by using multiple data sources and tools.
The Sqrrl Threat Hunting Model provides a maturity model to measure your threat hunting capabilities and guide you to improve your practices to address cyber threats.
What is Sqrrl's Threat Hunting Framework?

The Sqrrl threat hunting framework was introduced in 2015 and is considered one of the first frameworks of its kind. It's known for its flexibility, repeatability, and support for hypothesis testing with the best data.
Sqrrl was designed to help security teams build threat hunting programs and improve their response and mitigation during security incidents. It had such a major impact that the Threat Hunting Project notes that the Sqrrl team "published some of what are still foundational documents about threat hunting".
AWS acquired Sqrrl in 2018. The platform itself was absorbed into AWS services, but the framework lives on as a conceptual model referenced across the security community. Sqrrl is about exploration and inquiry, guiding hunters to look in areas that traditional methods miss. This is the key to its hypothesis-driven process and continuous learning and adaptation.
The hunting loop is the core of Sqrrl's framework, thanks to which each hunt should improve your security posture. By finding patterns in network data that traditional methods miss, Sqrrl helps security teams find and address threats better.
Is Sqrrl Still Active Today?
Sqrrl, the company behind the framework, was acquired by Amazon Web Services in 2018 and no longer exists as a standalone platform. What does remain is the Sqrrl framework as a conceptual model. It continues to be referenced across the security community and has influenced frameworks such as Splunk's PEAK and others.
For us at Hunt.io, Sqrrl's model has been a reference point when building out our own approaches to proactive threat hunting. While the original product is gone, the methodology lives on and still shapes how modern hunts are designed.
Now that we've looked at the origins and purpose of the Sqrrl framework, the next step is to understand what it's actually made of. The framework is not just a concept; it's built on a set of structured components that guide hunters through repeatable processes.
Sqrrl Framework Components
Sqrrl's framework is considered one of the first threat hunting strategies, known for its hypothesis-driven approach and structured methods. The purpose of threat hunting methodologies, including Sqrrl's, is to help security teams build threat hunting programs that improve their response and mitigation during security incidents.
The framework brings together different types of knowledge, such as organizational expertise and threat intelligence, into each stage of the threat hunting process.
Although Sqrrl is no longer an active product, the framework it introduced remains valuable as a structured, hypothesis-driven methodology. Its structured, unstructured, and situational methods provide a full threat hunting approach.
The following sections will go into more detail on the hypothesis-driven hunting process and the four stages of the hunting loop, which are part of Sqrrl's framework.
Hypothesis-Driven Hunting Process
Effective threat hunting is a proactive approach with hypotheses based on attacker behaviors. Sqrrl's hypothesis-driven process has four stages: hypothesis generation, investigation, attack pattern detection, and using evidence to refine investigations. This cyclical process ensures continuous refinement based on findings, adapting to new and emerging threats.
Hypothesis formation drives hunts for mature threat hunting teams to explore areas that traditional methods miss. This continuous cycle requires regular updates and refinements based on the latest threat intelligence and findings, so the threat hunting team can create hypotheses to investigate hidden patterns and potential threats.
Being hypothesis-driven ensures systematic and repeatable threat hunting. It also fosters continuous learning and improvement within the team, so they can stay ahead of threats.
Four Stages of Hunting Loop

The Threat Hunting Loop in the Sqrrl framework is a conceptual model. It outlines the steps of a typical hunt. The four stages of the hunting process are Prepare, Detect, Investigate, and Act. Each of these phases brings together different types of knowledge, including organizational expertise and threat intelligence, to find and respond to threats.
In the Prepare stage, threat hunters gather the necessary data and tools, including endpoint data, network data, security data, and threat intelligence.
In the Detect stage, data is used to find potential threats and anomalies, using Sqrrl's visualization tools to explore data and find malicious behavior.
In the Investigate stage, the anomalies are dug deeper into, using link analysis to find hidden relationships between suspicious behaviors and alerts. In the Act stage, actions are taken based on findings, such as mitigating threats and improving security to prevent future incidents. Following these four stages is a full threat hunting process.
While the framework's stages and methods create a strong foundation, their effectiveness largely depends on the data feeding them. This is where threat intelligence comes in, turning the framework from a structured loop into a powerful, real-time tool for finding advanced threats.
Threat Intelligence with Sqrrl
Integrating data from threat intelligence feeds into the Sqrrl framework allows security teams to proactively manage threats and improve detection. Automation tools help correlate threat intelligence with hunting activities, so you can process and analyze large data volumes, essential for handling indicators of compromise and other relevant data.
Threat hunting requires gathering different types of data, including endpoint data, network data, and security data, all of which are key to finding and responding to threats. Structured threat hunting often involves focusing on known tactics, techniques, and procedures (TTPs) as outlined by frameworks like MITRE ATT&CK.
Organizations at different threat hunting maturity levels can improve by integrating a threat intelligence platform to enrich indicators of compromise. Emerging trends require visibility across different data sources, so threat intelligence integration is critical.
Bringing intelligence into the loop highlights why many teams have found Sqrrl so valuable.
Benefits of Using Sqrrl for Threat Hunting

Teams that apply the Sqrrl framework often find they can detect advanced threats more effectively. The structure gives them a way to hunt without relying only on alerts, which means analysts with different levels of experience could contribute. The process is repeatable, clear, and can be used with whatever threat hunting tools and threat hunting platforms the team already has.
Better Security Posture
Threat hunting is a proactive approach that doesn't rely on alerts or whitelisting actions, so organizations can stay ahead of threats. Integrating threat hunting into security practices uncovers valuable insights, finds threats sooner, and reduces dwell time, so the overall security posture improves.
Improved Detection Capabilities
Using the Sqrrl framework encourages the creation of playbooks and processes that can be repeated and improved over time. By focusing hunts on hypotheses, patterns, and intelligence, security teams become better at spotting new techniques as they emerge. This cycle of refinement is why the framework is still taught and used today.
Collaboration and Knowledge Sharing
Because the framework is structured and repeatable, it creates a common language for analysts at different experience levels. This shared process makes it easier for junior analysts to contribute while allowing senior hunters to pass on their expertise. Over time, the framework becomes not just a hunting process but also a way to strengthen team collaboration and knowledge transfer.
Of course, not all teams will see the same results right away. The value of Sqrrl depends on how mature an organization's hunting capabilities are. That's why the framework includes a maturity model to help teams understand their current level and where to go next.
Sqrrl Threat Hunting Maturity

The Hunt Maturity Model (HMM), originally published by Sqrrl and the ThreatHunting.net project, outlines five levels of hunting capability that organizations can use to benchmark and improve their practices. It outlines the different stages of hunting competence so organizations can assess their threat hunting maturity model and improve over time. This model helps organizations understand where they are and provides a roadmap to improve their threat hunting.
The HMM stages describe the typical processes for each loop stage at different maturity levels, from initial to procedural and innovative to leading. Organizations at higher maturity levels can stop and detect adversary activity, often through automation and advanced data analysis.
Initial to Procedural Levels
Hunting for Indicators of Compromise (IoCs) on endpoints against recent intelligence feeds is where security teams start. Organizations at the initial maturity level (HMM0) mainly focus on alert resolution with limited practices beyond basic correlation.
As they move to HMM1, they start to use automated alerting for incident response and follow up on recent threat reports for intelligence-driven detection. At the procedural level (HMM2), organizations start to use analytical and hunting processes produced by others; this is a move towards a more structured methodology.
Increased visibility into environments allows these organizations to collect data and improve threat hunting. Diversifying SIEM content beyond basic correlations establishes a robust detection framework for more in-depth analysis.
Innovative to Leading Levels
At the innovative level (HMM3), organizations use advanced data analysis techniques, including machine learning for threat detection. They face scalability issues and overwhelming hunting processes as data grows. But they can develop and refine their own detection methods, reaching an advanced threat hunting state that sets them apart from less mature organizations.
At the leading level (HMM4), organizations automate threat hunting, and analysts can focus on developing new methods and improving existing ones. High automation allows them to stop and detect adversary activity; they have a big advantage in the evolving cyber landscape.
This is the top of the threat hunting maturity, where organizations are continuously improving and adapting to new threats.
Just keep in mind that knowing your maturity level is only half the battle. The real challenge is putting the framework into practice in a way that fits your organization. Practical implementation tips and methods for data collection, analysis, and playbook creation can make the difference between theory and impact.
Sqrrl Implementation Tips
Applying the Sqrrl framework takes planning, good data collection, and clear playbooks. Many teams used it as a reference when building their own threat hunting program, adapting it to the tools and data they already had. The important part is the methodology itself, not the old platform. It remains flexible enough to fit into almost any SOC.
Data Collection and Analysis Techniques
Keyword searching is a common technique in threat hunting. It involves scanning system logs and configuration files for specific terms that may indicate security incidents. Four data collection techniques are clustering, grouping, searching, and stack counting; each serves a different analysis purpose. Endpoint data should include process execution metadata, registry access data, and file metadata to provide insights into user activities.
Network data collection should focus on session data, monitoring tool logs, and firewall logs to track communication patterns. Using these data collection and analysis techniques will enhance an organization's ability to detect and mitigate threats.
Effective data collection and analysis are the foundation of a successful threat hunting program, as they allow hunters to find hidden patterns and potential threats.
Creating Playbooks
Creating threat hunting playbooks involves documenting repeatable processes that guide hunters through specific investigation scenarios. They should include clear roles and responsibilities to streamline team collaboration during investigations. Incorporating real-world scenarios and lessons from previous hunts will make playbooks more effective.
Threat hunting frameworks need plans for post-hunt actions; Sqrrl doesn't provide that. Addressing that gap will ensure threat hunting leads to actionable insights and continuous improvement. Effective playbooks are key to being prepared and responding to detected threats.
This is where Hunt.io helps. By enriching the Sqrrl process with automation and high-fidelity data, teams can keep the hunting loop running without being slowed down by manual bottlenecks.
Bring Sqrrl to Life with Hunt.io
Applying the Sqrrl framework effectively requires the right tools and actionable data. That's where the Hunt.io cutting-edge threat hunting platform can make a real difference.
Our platform combines globally distributed sensors with advanced analytics to help teams detect, investigate, and mitigate threats more efficiently.

With solutions like C2 Infrastructure Feeds, IOC Hunter, AttackCapture™, and HuntSQL™, security teams can automate the collection and analysis of indicators of compromise, enrich threat intelligence, and streamline hunts.
By integrating these tools into a structured threat hunting program, teams gain deeper visibility into attacker behaviors, reduce dwell time, and ensure that each hunt produces meaningful, actionable insights. We don't simply support the Sqrrl methodology; we empower teams to stay ahead in an evolving threat landscape.
And while our tools provide the data, automation, and insights needed to make threat hunting more effective, even the best methodology and platform cannot eliminate all obstacles. Data overload, visibility gaps, and evolving threats all present challenges that teams must overcome if they want to get the most out of the Sqrrl methodology.
Sqrrl Threat Hunting Challenges
Let's now review what are the most common challenges for users adopting the Sqrrl threat hunting model:
Data quality and consistency
Security teams often have logs and telemetry coming from different places. If that data is not normalized and enriched, analysts spend too much time cleaning it instead of testing their hunting ideas.
Coming up with good hypotheses
Many teams fall back on chasing indicators they already know. The framework works best when hunters can form creative, intelligence-driven hypotheses about attacker behavior. That requires experience and context, which are not always available in smaller or less mature SOCs.
Keeping the loop alive
The idea of Prepare, Detect, Investigate, and Act is simple, but in reality many teams stop halfway. Lessons learned are not always turned into new detections or playbooks, which means the same gaps show up again in future hunts.
Scaling hunts
Sqrrl was developed at a time when hunting was still highly manual. At enterprise scale, that kind of approach can overwhelm analysts. Without automation and enrichment from high-fidelity intelligence, teams often hit a wall.
Measuring results
The maturity model is helpful, but it does not tell you exactly how to measure success. Leadership often asks what has improved after months of hunts, and without clear metrics, it can be difficult to prove the value of the effort.
Addressing these challenges will allow teams to get the most out of Sqrrl and their improve threat hunting.
Wrapping up
Even though the Sqrrl platform was discontinued after AWS's acquisition, its methodology continues to influence how threat hunters work today. The hunting loop, the maturity model, and the focus on hypothesis-driven inquiry remain some of the most practical tools for finding advanced threats.
At Hunt.io we extend these principles with automation, global adversary data, and enrichment that make the framework easier to put into practice. If you want to see how structured hunting can become a daily reality in your SOC, book a demo and explore our platform in action
Ready to see our platform in action? Book a demo now and experience proactive threat hunting for yourself.
Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.

Hunt adversary infrastructure in real time. Surface C2 servers, enrich IOCs,
and map attacker activity at scale with our unified threat hunting platform.





